Network Security Welcome and introduction Network security at






- Slides: 8

Network Security — Welcome and introduction Network security at TKK, Nov-Dec 2009 Tuomas Aura

My background Lecturer: Tuomas Aura, tuomas. aura@tkk. fi Ph. D from Helsinki University of Technology in 2000 Microsoft Research, UK, 2001–Sep 2009 Professor at TKK 2008–, full time since 1 Nov 2009 Research: Network security Security protocol engineering Security of mobility protocols (Mobile IPv 6, SEND, etc. ) Privacy of mobile users Do. S resistance 2

Course arrangements Tuesdays and Wednesdays 13: 15– 16: 00 T 4 Period II in year autumn 2009 10 lectures (6 th week in reserve) Exercises Fridays 14: 15 -16 T 4 First exercise session on 13 Nov, last on 11 Dec Mandatory exercises Course assistants: Jyry Suvilehto Elena Reshetova Examination 18 Dec 2009 3

Recommended reading Lecture handouts Preliminary versions on my old Microsoft homepage Final versions in Noppa after the lectures William Stallings, Network security essentials: applications and standards, 3 rd ed. , Pearson Prentice Hall, 2007 Kaufman, Perlman, and Speciner, Network security: PRIVATE communication in a PUBLIC world, Prentice -Hall, 2002 Wikipedia, web, RFCs and standards 4

Exercises Mandatory exercises Pass/fail, must pass at least 4 out of 5 rounds Problems in Noppa by Friday each week Solutions to be submitted by Thursday midnight before the Friday exercise session Keep solutions to 2 pages per round Submission instructions will be in Noppa Try to solve all problems at least partly The goal is not to have all right answers; the goal is to learn how to find information Individual work; do not copy or even look at the written answers of other students; write your own 5

Network security Security goals: Data confidentiality, data integrity and authentication Access control for network access Integrity of signalling protocols and routing systems Denial-of-service (Do. S) protection Software security Application-level security goals, e. g. non-repudiation Security is not cryptography Cryptography is seen as an abstract building block Protocol design assuming the most common crypto primitives Network technology Must know about TCP/IP, 802. 11, UMTS etc. 6

Goals Know common communications systems, classic security mechanisms, and some of the latest ideas Understand network security technologies, their properties and limitations to use them right Be aware of the pitfalls in security engineering: security is not just mathematics or just code Starting point for learning more on the job or in further studies Learn the adversarial mindset of security engineering 7

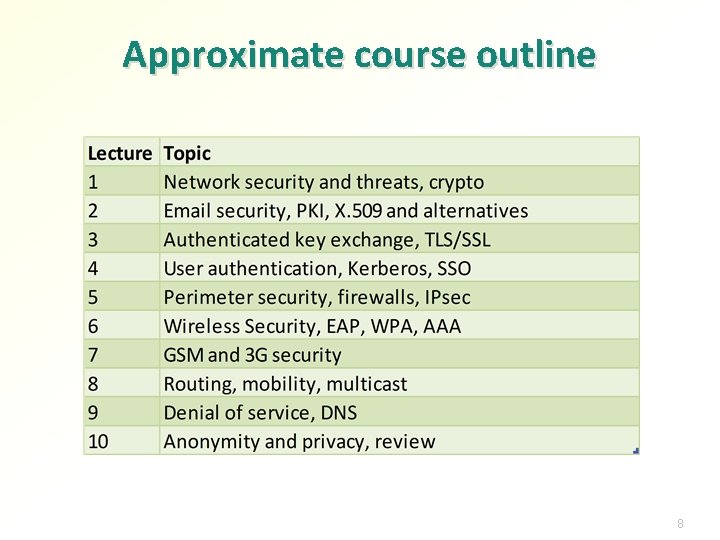
Approximate course outline 8