Differential Distinguishing Attack of Shannon Stream Cipher Yaser


![Differential Distinguishing Attack of Shannon Stream Cipher Keystream Generation Mode 1) rt+1[i] ← rt[i+1] Differential Distinguishing Attack of Shannon Stream Cipher Keystream Generation Mode 1) rt+1[i] ← rt[i+1]](https://slidetodoc.com/presentation_image/0c296652c258673fd121ebb4e5aa8629/image-5.jpg)
![Differential Distinguishing Attack of Shannon Stream Cipher Differential properties of the output IS‘[11]=IS[11] 31 Differential Distinguishing Attack of Shannon Stream Cipher Differential properties of the output IS‘[11]=IS[11] 31](https://slidetodoc.com/presentation_image/0c296652c258673fd121ebb4e5aa8629/image-11.jpg)

- Slides: 15

Differential Distinguishing Attack of Shannon Stream Cipher Yaser Esmaeili Elham Shakour Zaeim Electronic Ind. R&D Department {yesmaeili, shakour}@zaeim. co. ir Mehdi Hassanzadeh University of Bergen Selmer Center, Norway Mehdi. hassanzadeh@ii. uib. no

Differential Distinguishing Attack of Shannon Stream Cipher Outline Introduction n Description of the Shannon n Differential Properties of the f 2 Function n Our Differential Distinguishing Attack n Conclusion n Hassanzadeh Cryptology 2008, Malaysia 2/16

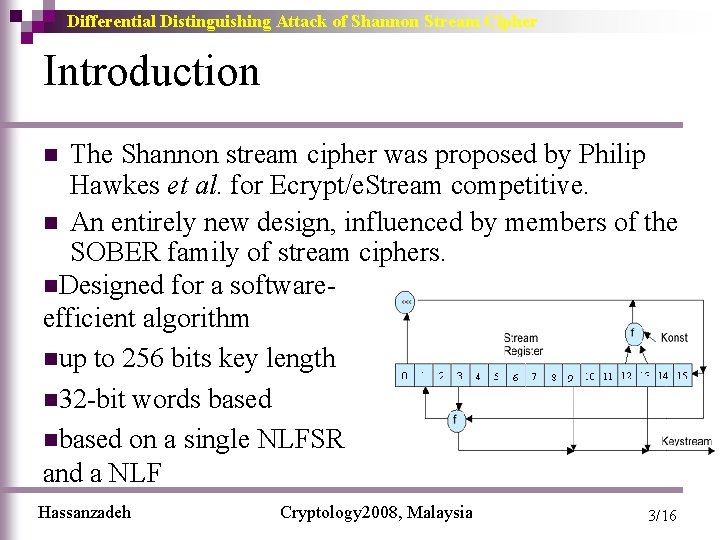
Differential Distinguishing Attack of Shannon Stream Cipher Introduction The Shannon stream cipher was proposed by Philip Hawkes et al. for Ecrypt/e. Stream competitive. n An entirely new design, influenced by members of the SOBER family of stream ciphers. n. Designed for a softwareefficient algorithm nup to 256 bits key length n 32 -bit words based nbased on a single NLFSR and a NLF n Hassanzadeh Cryptology 2008, Malaysia 3/16

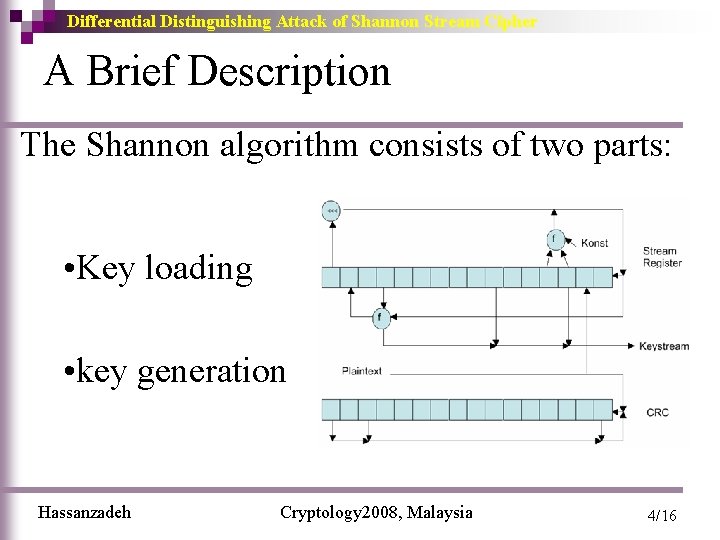
Differential Distinguishing Attack of Shannon Stream Cipher A Brief Description The Shannon algorithm consists of two parts: • Key loading • key generation Hassanzadeh Cryptology 2008, Malaysia 4/16
![Differential Distinguishing Attack of Shannon Stream Cipher Keystream Generation Mode 1 rt1i rti1 Differential Distinguishing Attack of Shannon Stream Cipher Keystream Generation Mode 1) rt+1[i] ← rt[i+1]](https://slidetodoc.com/presentation_image/0c296652c258673fd121ebb4e5aa8629/image-5.jpg)
Differential Distinguishing Attack of Shannon Stream Cipher Keystream Generation Mode 1) rt+1[i] ← rt[i+1] for i = 1. . . 14 2) rt+1[15] ← f 1(rt[12] rt[13] Konst) (rt[0] <<<1) 3) temp ← f 2(rt+1[2] rt+1[15]) 4) rt+1[0]← rt[1] temp(“feed forward” to the new lowest element) 5) vt ← temp rt+1[8] rt+1[12]. Hassanzadeh Cryptology 2008, Malaysia 5/16

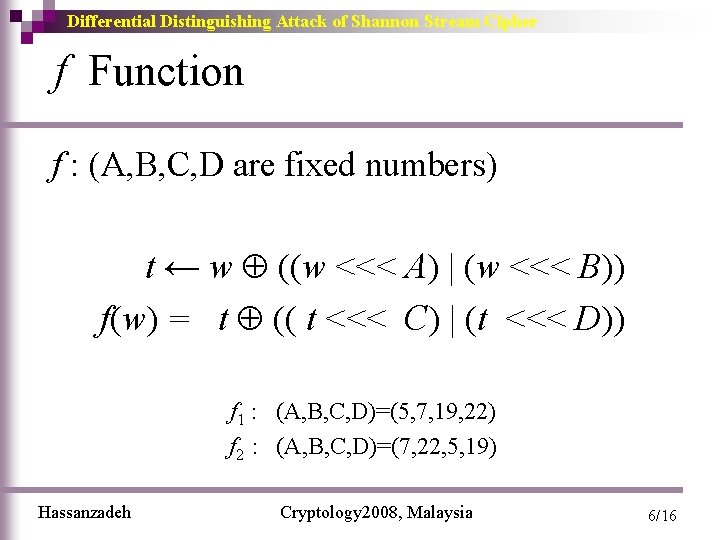
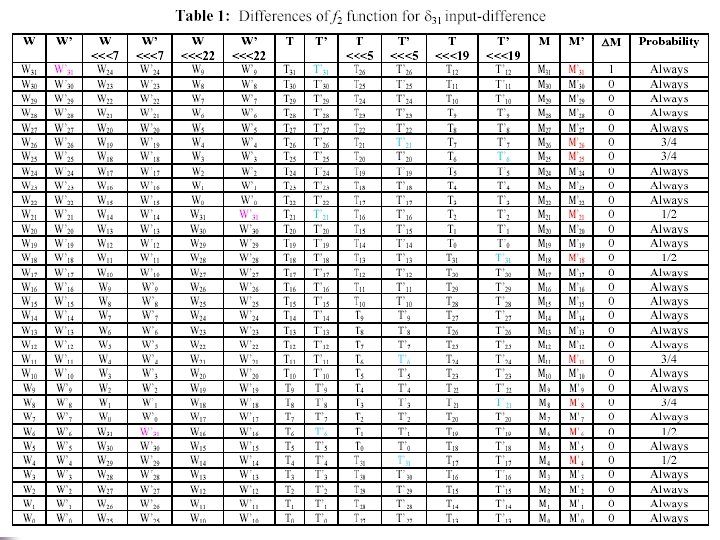
Differential Distinguishing Attack of Shannon Stream Cipher f Function f : (A, B, C, D are fixed numbers) t ← w ((w <<< A) | (w <<< B)) f(w) = t (( t <<< C) | (t <<< D)) f 1 : (A, B, C, D)=(5, 7, 19, 22) f 2 : (A, B, C, D)=(7, 22, 5, 19) Hassanzadeh Cryptology 2008, Malaysia 6/16

Differential Distinguishing Attack of Shannon Stream Cipher Differential Analysis for Stream Ciphers A differential of a stream cipher is a prediction that a given input difference (it can be the key, IV or internal state) produce some output difference (it can be the keystream or internal state) Hassanzadeh Cryptology 2008, Malaysia 7/16

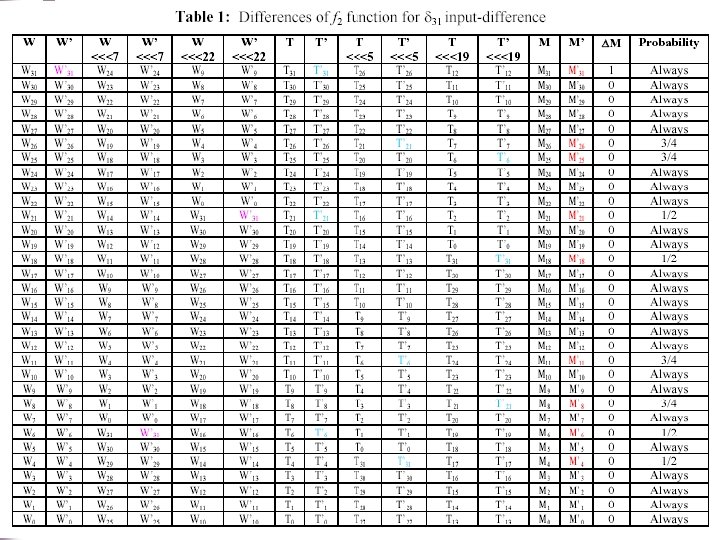
Differential Distinguishing Attack of Shannon Stream Cipher Differential Property of f 2 n Suppose that 31 st bit of input is activated. ¨ W, W 31 9 bits of output from f 2 function will be impressed by 31 n The output differential of f 2 function is determined bit by bit. n Hassanzadeh Cryptology 2008, Malaysia 8/16

Differential Distinguishing Attack of Shannon Stream Cipher Differential Property of f 2 n n n Theoretically: Shannon is a RNG, therefore the output bits of the Shannon are independent The output is generated by the output of f 2 function the differential output bits of f 2 function are 32 bit word M (i. e. 0 x 80000000 from Table ) with the probability of Hassanzadeh Cryptology 2008, Malaysia 9/16

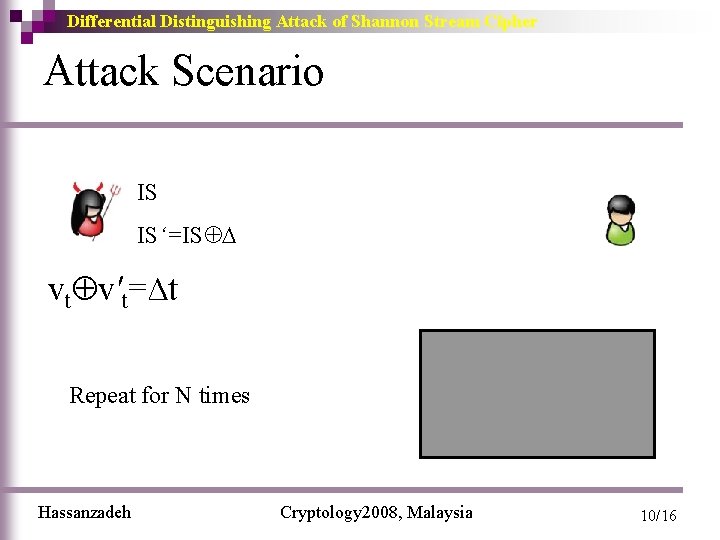
Differential Distinguishing Attack of Shannon Stream Cipher Attack Scenario IS IS‘=IS vt v't=∆t vt , v't TRNG Repeat for N times Hassanzadeh Cryptology 2008, Malaysia 10/16
![Differential Distinguishing Attack of Shannon Stream Cipher Differential properties of the output IS11IS11 31 Differential Distinguishing Attack of Shannon Stream Cipher Differential properties of the output IS‘[11]=IS[11] 31](https://slidetodoc.com/presentation_image/0c296652c258673fd121ebb4e5aa8629/image-11.jpg)
Differential Distinguishing Attack of Shannon Stream Cipher Differential properties of the output IS‘[11]=IS[11] 31 n n n N differential outputs are generated by black box (scenario is repeated N times) In each repeatation, 9 th output word is exracted. A sequence consisting of N 32 -bit differential words is provided (O 9) Hassanzadeh Cryptology 2008, Malaysia 11/16

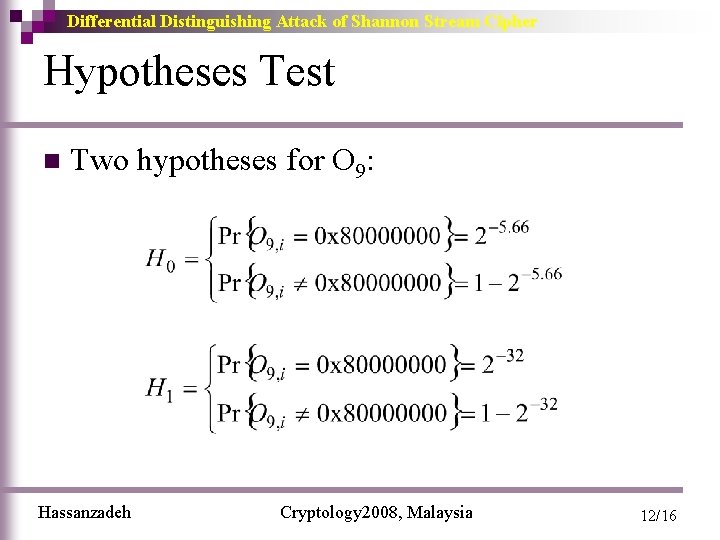
Differential Distinguishing Attack of Shannon Stream Cipher Hypotheses Test n Two hypotheses for O 9: Hassanzadeh Cryptology 2008, Malaysia 12/16

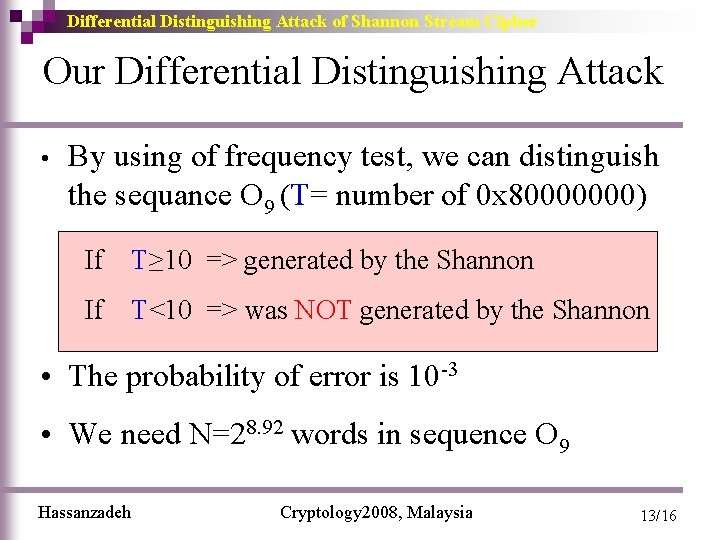
Differential Distinguishing Attack of Shannon Stream Cipher Our Differential Distinguishing Attack • By using of frequency test, we can distinguish the sequance O 9 (T= number of 0 x 80000000) If T≥ 10 => generated by the Shannon If T<10 => was NOT generated by the Shannon • The probability of error is 10 -3 • We need N=28. 92 words in sequence O 9 Hassanzadeh Cryptology 2008, Malaysia 13/16

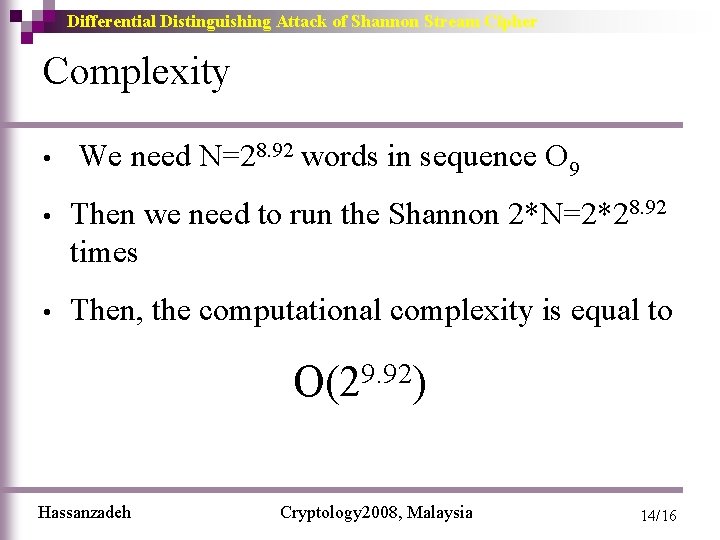
Differential Distinguishing Attack of Shannon Stream Cipher Complexity • We need N=28. 92 words in sequence O 9 • Then we need to run the Shannon 2*N=2*28. 92 times • Then, the computational complexity is equal to 9. 92 O(2 ) Hassanzadeh Cryptology 2008, Malaysia 14/16

Differential Distinguishing Attack of Shannon Stream Cipher Conclusion n We showed that the keystream generator part of the Shannon stream cipher is not strong. n It should be replaced by stronger one. n The Key loading part is strong. Hassanzadeh Cryptology 2008, Malaysia 15/16
 Block cipher vs stream cipher example
Block cipher vs stream cipher example Cipher
Cipher Cipher
Cipher Yaser fallah
Yaser fallah Dış ticaret işlemleri yönetimi yaser gürsoy
Dış ticaret işlemleri yönetimi yaser gürsoy Cipher yang termasuk ke dalam cipher abjad-majemuk adalah
Cipher yang termasuk ke dalam cipher abjad-majemuk adalah Mono substitution
Mono substitution Affine cipher brute force
Affine cipher brute force Self synchronizing stream cipher
Self synchronizing stream cipher Contoh kriptografi modern
Contoh kriptografi modern Cipher
Cipher Active attack and passive attack
Active attack and passive attack Active attack and passive attack
Active attack and passive attack Differentiate byte stream and character stream
Differentiate byte stream and character stream Differential fault attack
Differential fault attack Distinguishing features of managerial accounting
Distinguishing features of managerial accounting