Network Reconnaissance and Enumeration Section 3 2192021 Outline


















- Slides: 54

Network Reconnaissance and Enumeration Section 3 2/19/2021

Outline – Passive Enumeration • ARP • Network Sniffing 2/19/2021

Outline – Active Enumeration • • Ping Traceroute Port/Service Scanning Banner Grabbing OS Fingerprinting Firewalking SNMP Routing Daemons 2/19/2021

Objective • Targeted Network Reconnaissance – Network topology – Host systems – Host applications/services – Host configuration – Host users accounts – Naming conventions 2/19/2021

Passive Enumeration • Generally LAN based • Generally undetectable 2/19/2021

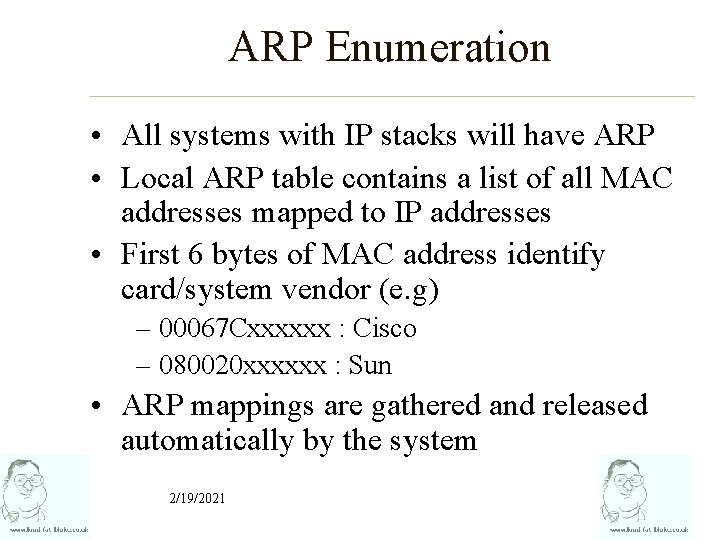
ARP Enumeration • All systems with IP stacks will have ARP • Local ARP table contains a list of all MAC addresses mapped to IP addresses • First 6 bytes of MAC address identify card/system vendor (e. g) – 00067 Cxxxxxx : Cisco – 080020 xxxxxx : Sun • ARP mappings are gathered and released automatically by the system 2/19/2021

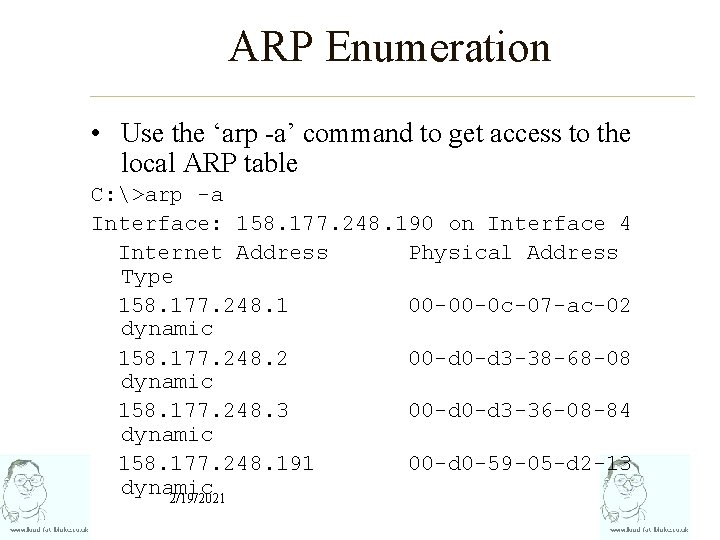
ARP Enumeration • Use the ‘arp -a’ command to get access to the local ARP table C: >arp -a Interface: 158. 177. 248. 190 on Interface 4 Internet Address Physical Address Type 158. 177. 248. 1 00 -00 -0 c-07 -ac-02 dynamic 158. 177. 248. 2 00 -d 3 -38 -68 -08 dynamic 158. 177. 248. 3 00 -d 3 -36 -08 -84 dynamic 158. 177. 248. 191 00 -d 0 -59 -05 -d 2 -13 dynamic 2/19/2021

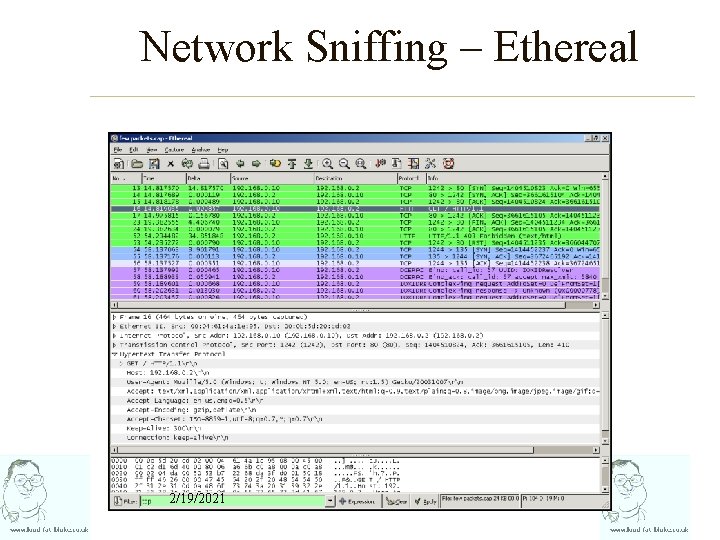
Network Sniffing • Placing a network adapter in ‘promiscuous mode’ enables the reception of all network traffic passing the adapter. • Most effective on non-switched networks • Even on switched networks all broadcast traffic may be received • No valid IP address required 2/19/2021

Network Sniffing – What do we get? • MAC addresses • IP addresses and IP structure – RIP, OSPF packets • System names – Net. BIOS broadcasts – Cisco Discovery Protocol – IPX service announcements • Default gateways • Not to mention usernames, passwords and data…but more on that later 2/19/2021

Network Sniffing – The Tools • Windows – Net. Mon (Microsoft) – Sniffer Pro (NAI) – Tcpdump + winpcap (GPL) • UNIX – Tcpdump (GPL) – Etherreal (GPL) – Dsniff (more attack than recon – GPL) 2/19/2021

Network Sniffing - Filtering • On high throughput networks use capture filters – Whole packet is usually not needed – just headers and start of data portion – Any IP or TCP/UDP protocol may be included or excluded from a capture filter – ‘Noisy’ addresses may be filtered out • All network sniffing tools support filtering to some degree • For extended periods of sniffing filters will be essential 2/19/2021

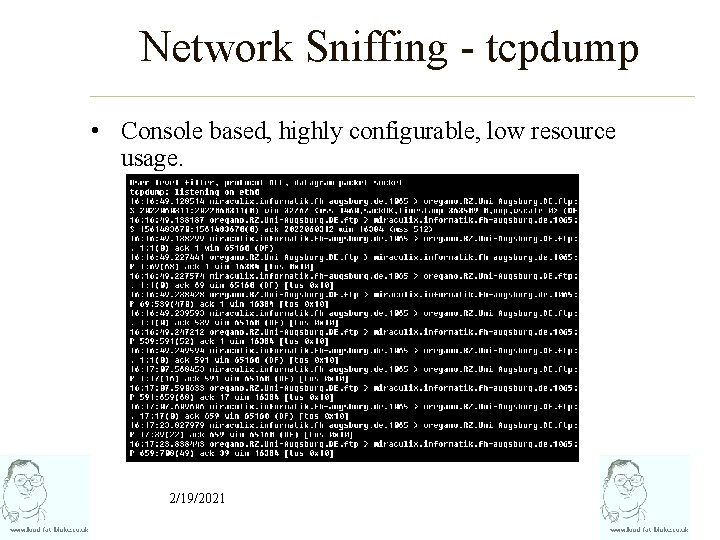
Network Sniffing - tcpdump • Console based, highly configurable, low resource usage. 2/19/2021

Network Sniffing – Ethereal 2/19/2021

Active Enumeration • Can yield a great deal of data • Can be detected • May require specialised software/OS 2/19/2021

The Mighty Ping • Used to determine host reachability • Nearly all systems with an IP stack have a ping facility • Uses the ICMP protocol • Provides – Round trip time (RTT) – Time to live (TTL) – indicates hop-count • Generally unnoticed if used in moderation 2/19/2021

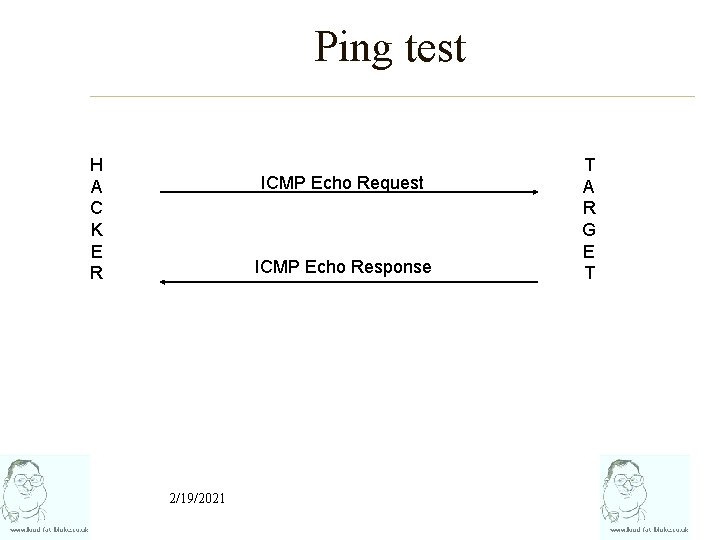
Ping test H A C K E R ICMP Echo Request ICMP Echo Response 2/19/2021 T A R G E T

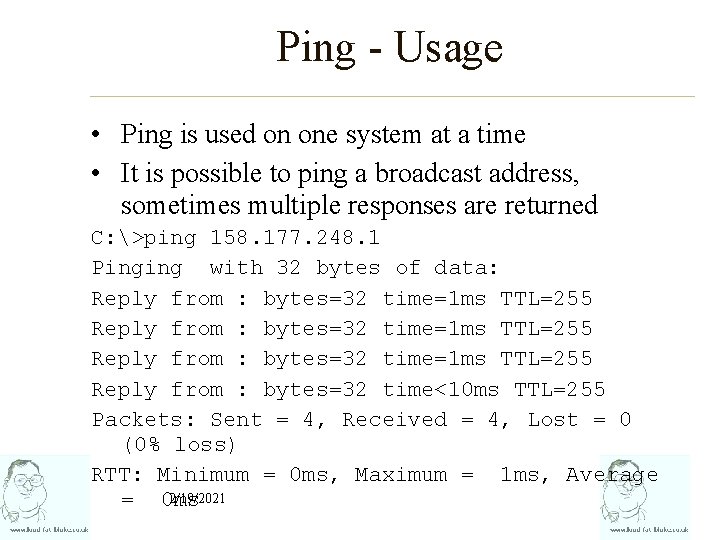
Ping - Usage • Ping is used on one system at a time • It is possible to ping a broadcast address, sometimes multiple responses are returned C: >ping 158. 177. 248. 1 Pinging with 32 bytes of data: Reply from : bytes=32 time=1 ms TTL=255 Reply from : bytes=32 time<10 ms TTL=255 Packets: Sent = 4, Received = 4, Lost = 0 (0% loss) RTT: Minimum = 0 ms, Maximum = 1 ms, Average 2/19/2021 = 0 ms

Ping – Sweeping • Ping-sweeping is a term for sweeping multiple addresses with a ping query to determine host reachability. • Used for finding targets within a network range. • Will not work on targets that have ICMP traffic filtered or blocked. • Tools such as NMAP, Ming. Sweeper and Pinger will perform a ping-sweep. 2/19/2021

More with ping Identifying the Firewall Good commercial firewalls block time stamp requests and source routed packets. Use ping to send them, and it will show there is a firewall in the way # ping -v -T tsandaddr 10. 0. 0. 120 PING 10. 0. 0. 120 (10. 0. 0. 120) from 10. 0. 0. 1 : 56(124) bytes of data. --- 10. 0. 0. 120 ping statistics --16 packets transmitted, 0 received, 100% loss # ping -v -T tsandaddr 10. 0. 0. 125 PING 10. 0. 0. 125 (10. 0. 0. 125) from 10. 0. 0. 1 : 56(124) bytes of data. --- 10. 0. 0. 125 ping statistics --8 packets transmitted, 0 received, 100% loss 2/19/2021

More fun with ICMP Identifying the Firewall W Richard Stevens – a god amongst men and author of TCP/IP Illustrated etc left us with the ability to to generate ICMP address mask requests and ICMP time requests # icmpaddrmask 10. 0. 0. 120 Received mask fffff 00, from 10. 0. 0. 120 # 2/19/2021

Traceroute • Used to determine both connectivity AND the IP route used to reach the target. • Available on most but not all systems that have an IP stack. • Relies on the fact that routers should always decrement the TTL of a packet as it passes. • Generally uses ICMP packets on Windows and UDP packets on UNIX systems. However any IP protocol could be used in theory. 2/19/2021

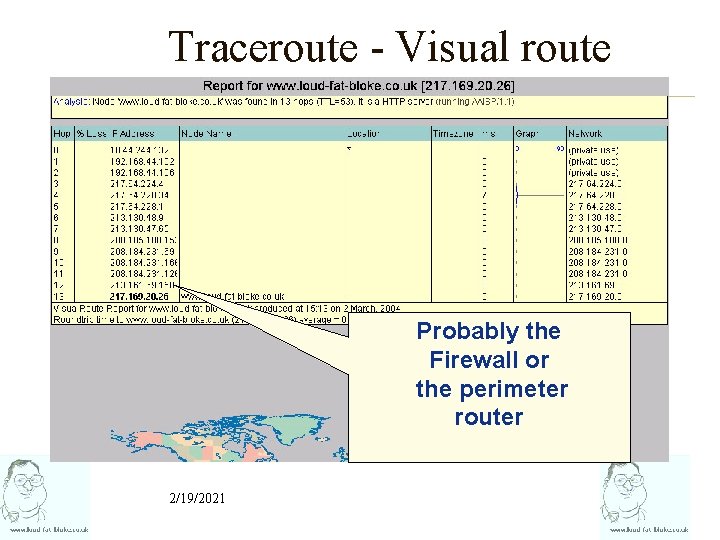
Traceroute - Visual route Probably the Firewall or the perimeter router 2/19/2021

Port/Service Scanning • Used to determine what TCP or UDP ports are available on a target system. • The scanner will attempt to connect to each port on the target. • The scanner should detect the port in one of three states: – Closed – port reachable but no service present – Open – port is reachable and service is present – Filtered – port is non-reachable, possible firewall or packet filter is present 2/19/2021

Background to TCP scanning • Determine what ports of a host are listening for connections • 4 main types of TCP scans 1. TCP connect() 2. SYN scan 3. FIN scan + Null + ACK + XMAS 4. Fragmentation scanning 2/19/2021

TCP Connect Scan • Uses a system call provided by the operating system • If the port is listening, connect will succeed • Does not require any special privileges • Easily detectable • Most reliable • Cannot usually detect filtered ports 2/19/2021

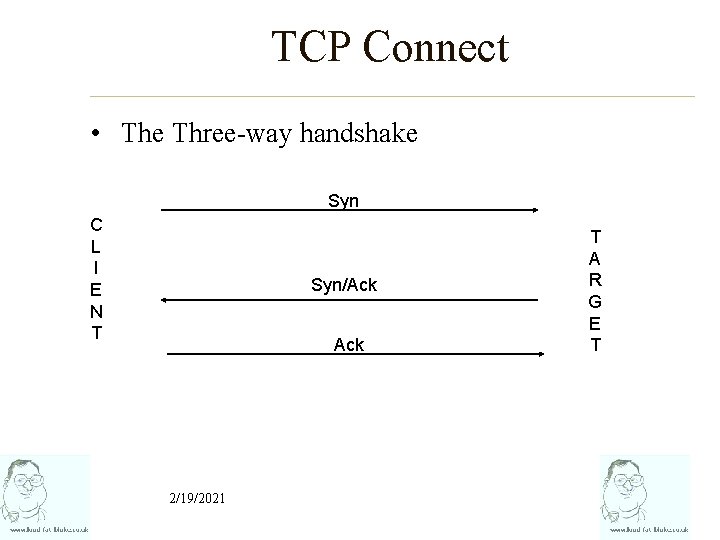
TCP Connect • The Three-way handshake Syn C L I E N T Syn/Ack 2/19/2021 T A R G E T

SYN Scan • • Commonly referred to a half open scanning Sends a SYN packet and waits for a response A SYN/ACK response indicates port is listening A RST packet indicates the port is not listening Less likely to be logged No response indicates port is filtered Requires raw sockets requiring root or Administrator privileges • Some IDS confuse this with a SYN flood 2/19/2021

FIN Scan + Null + XMAS • More stealthy than a SYN scan • Reply with a proper RST packet indicates that the port is closed • Open ports tend to ignore the FIN packet • However Microsoft boxes tend to send a RST packet regardless • Can be used to differentiate a Unix box from a Microsoft box 2/19/2021

ACK Scan • Not used to identify open and closed ports • Used to identify filtered ports • Can be useful for mapping packet filter rules 2/19/2021

Fragmentation scanning • A modification of other techniques of scanning • Breaks the probe packet into a couple of small IP fragments • Breaking up the TCP header into several smaller packets makes it harder to detect and some packet filters will pass the packet unchecked rather than wait for all of the fragments to arrive. 2/19/2021

UDP Port Scanning • Single UDP packet to each port being tested • Closed ports respond with an ICMP unreachable message. • Open ports will NOT respond • Filtered ports will NOT respond • Results can be ambiguous on filtered targets • Can be very slow due to ICMP message rate limiting which is specified within the RFC’s describing IP & ICMP. Some systems do not implement this (e. g. all Windows systems. ) 2/19/2021

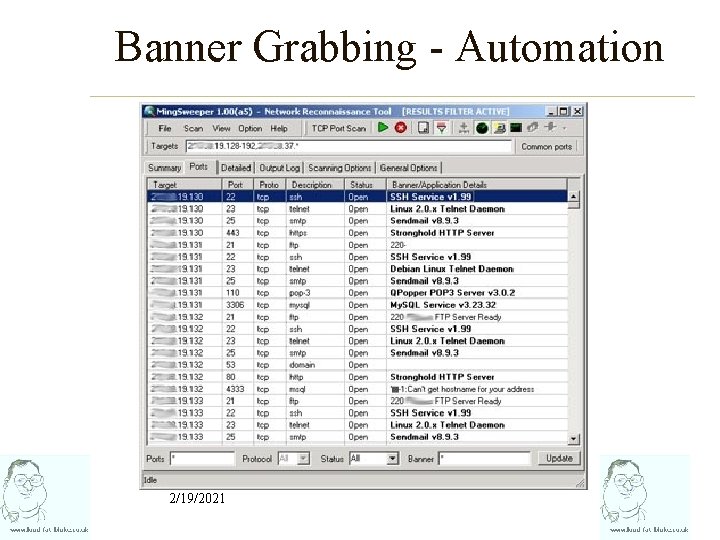
Banner Grabbing • The process of examining banner strings returned by services bound to open TCP ports • Enables identification of service applications including software version. • Not effective for non-character based services (e. g. SMB, HTTPS) • Some service applications will not send banner information until prompted (e. g. HTTP) • Useful for identification of service applications on non-standard ports 2/19/2021

Banner Grabbing – Manual Testing • Use netcat or telnet to connect to the port : C: nc 10. 0. 0. 120 25 220 Sendmail/8. 8. 8 ESMTP Looks like Sendmail 8. 8. 8 mail server - easy 2/19/2021

Banner Grabbing - Automation 2/19/2021

Fingerprinting • Stack fingerprinting is used to determine the operating system of a target host • Utilises differences in the implementation of the IP stacks • Involves sending non-standard packets to the target and examining any responses • Not always accurate • Very easy to spot for IDS 2/19/2021

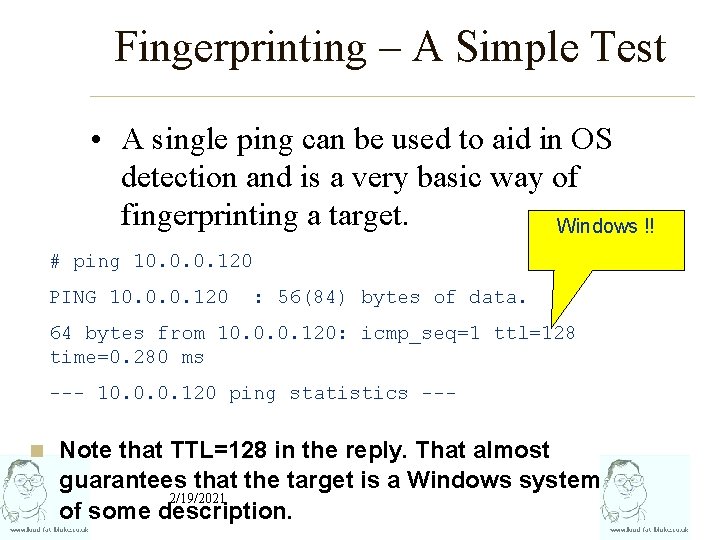
Fingerprinting – A Simple Test • A single ping can be used to aid in OS detection and is a very basic way of fingerprinting a target. Windows !! # ping 10. 0. 0. 120 PING 10. 0. 0. 120 : 56(84) bytes of data. 64 bytes from 10. 0. 0. 120: icmp_seq=1 ttl=128 time=0. 280 ms --- 10. 0. 0. 120 ping statistics --n Note that TTL=128 in the reply. That almost guarantees that the target is a Windows system 2/19/2021 of some description.

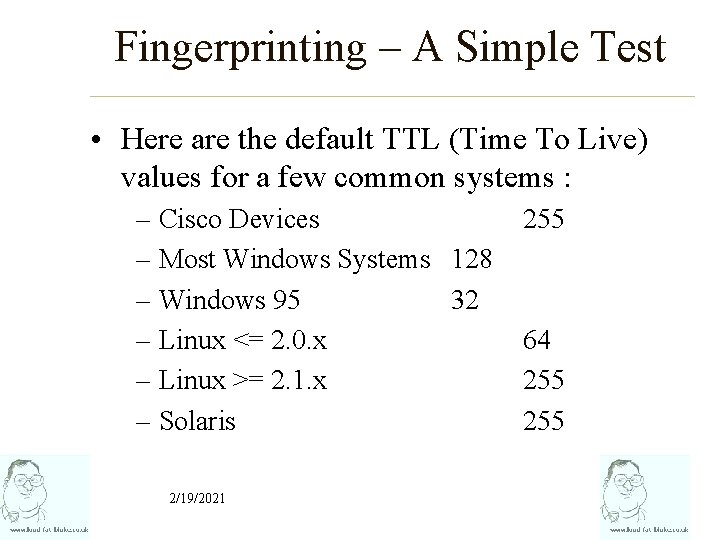
Fingerprinting – A Simple Test • Here are the default TTL (Time To Live) values for a few common systems : – Cisco Devices – Most Windows Systems 128 – Windows 95 32 – Linux <= 2. 0. x – Linux >= 2. 1. x – Solaris 2/19/2021 255 64 255

Advanced IP Stack Fingerprinting • Involves sending crafted packets to the target • Ideally requires >=1 open port and >=1 closed port • Packet filters, firewalls and transparent proxies can render IP stack fingerprinting useless when using automated tools such as NMAP, Queso or Ming. Sweeper because they sometimes re-write packets. 2/19/2021

Advanced IP Stack Fingerprinting • Tools for automated stack fingerprinting – NMAP stack fingerprinting – Xprobe ICMP stack fingerprinting – Ming. Sweeper combined NMAP+ICMP – Queso – early stack fingerprinting, NMAP draws tests from this software. 2/19/2021

NMAP • “Network Mapper” • Open source utility for network exploration • Its functions include a wide variety of port scanning mechanisms, OS detection and ping sweeps. • Runs on most Unix based operating systems • Has a graphical user interface • Its FREE! 2/19/2021

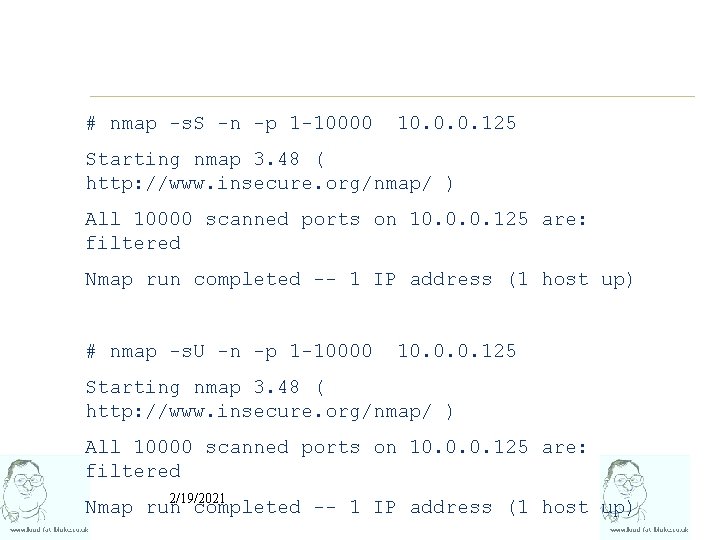
# nmap -s. S -n -p 1 -10000 10. 0. 0. 125 Starting nmap 3. 48 ( http: //www. insecure. org/nmap/ ) All 10000 scanned ports on 10. 0. 0. 125 are: filtered Nmap run completed -- 1 IP address (1 host up) # nmap -s. U -n -p 1 -10000 10. 0. 0. 125 Starting nmap 3. 48 ( http: //www. insecure. org/nmap/ ) All 10000 scanned ports on 10. 0. 0. 125 are: filtered 2/19/2021 Nmap run completed -- 1 IP address (1 host up)

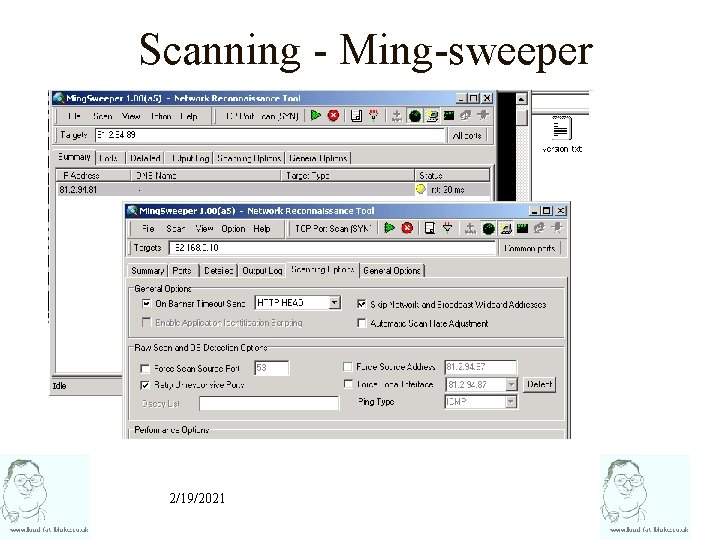
Mingsweeper • Windows based network reconnaissance utility • Performs ping sweeps, Reverse DNS sweeps, TCP & UDP port scans, OS identification and application identification. • It is also FREE! 2/19/2021

Scanning - Ming-sweeper 2/19/2021

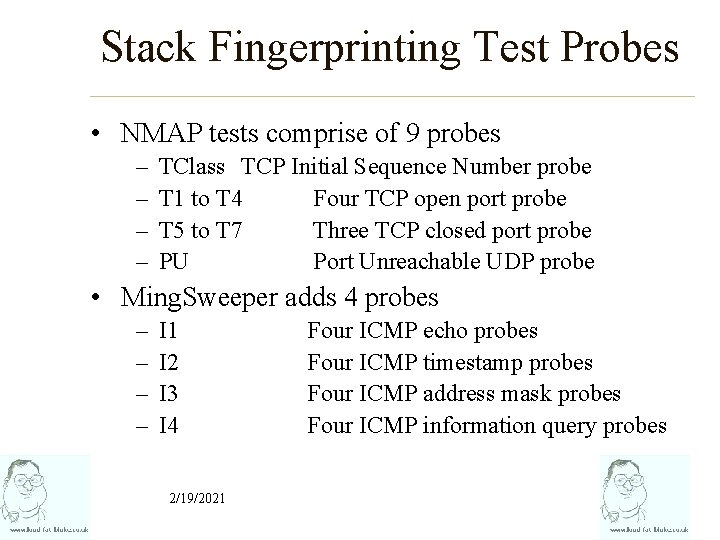
Stack Fingerprinting Test Probes • NMAP tests comprise of 9 probes – – TClass TCP Initial Sequence Number probe T 1 to T 4 Four TCP open port probe T 5 to T 7 Three TCP closed port probe PU Port Unreachable UDP probe • Ming. Sweeper adds 4 probes – – I 1 I 2 I 3 I 4 2/19/2021 Four ICMP echo probes Four ICMP timestamp probes Four ICMP address mask probes Four ICMP information query probes

Firewalking • Attempting to route packets through firewall • Vary IP protocol, TCP/UDP port numbers • Use decrementing TTL values to illicit responses from devices behind firewall • Not particularly successful on modern firewall systems 2/19/2021

Firewalking • Hping – useful tool for generating many types of hand-crafted IP packets. UNIX only. • Mptraceroute – performs traceroutes using multiple IP protocols and allowing port specifications. Win 2000/XP only. 2/19/2021

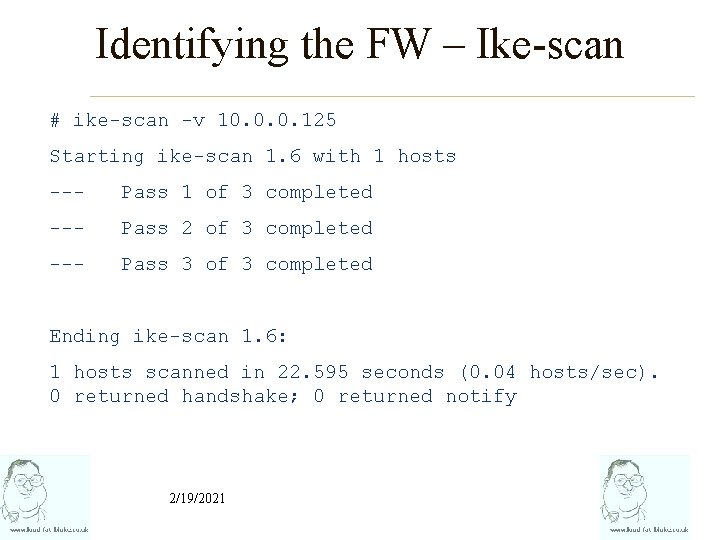
Identifying the FW – Ike-scan # ike-scan -v 10. 0. 0. 125 Starting ike-scan 1. 6 with 1 hosts --- Pass 1 of 3 completed --- Pass 2 of 3 completed --- Pass 3 of 3 completed Ending ike-scan 1. 6: 1 hosts scanned in 22. 595 seconds (0. 04 hosts/sec). 0 returned handshake; 0 returned notify 2/19/2021

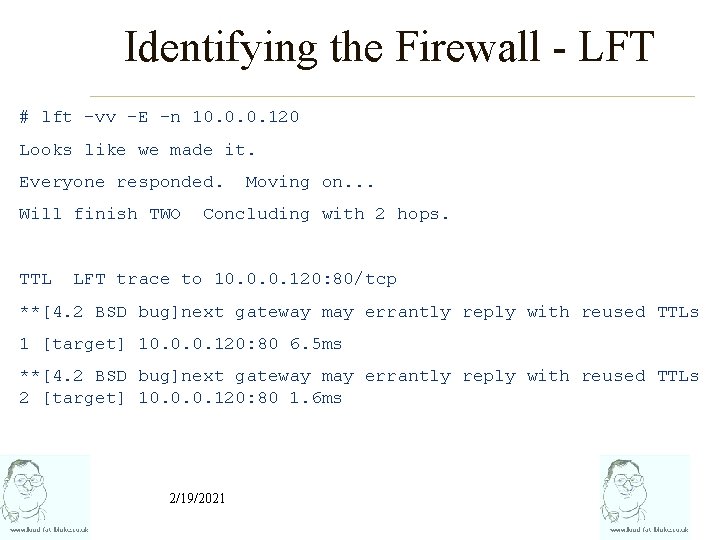
Identifying the Firewall - LFT # lft -vv –E -n 10. 0. 0. 120 Looks like we made it. Everyone responded. Will finish TWO TTL Moving on. . . Concluding with 2 hops. LFT trace to 10. 0. 0. 120: 80/tcp **[4. 2 BSD bug]next gateway may errantly reply with reused TTLs 1 [target] 10. 0. 0. 120: 80 6. 5 ms **[4. 2 BSD bug]next gateway may errantly reply with reused TTLs 2 [target] 10. 0. 0. 120: 80 1. 6 ms 2/19/2021

SNMP Enumeration • Community string is equivalent to a password used to control access to node information • Very often set to ‘public’ and ‘private’ • All transmissions are in clear text • SNMP daemons found on many network devices and hosts systems. • Generally all SNMP nodes in a network share the same community name 2/19/2021

SNMP Enumeration • SNMP community names can be brute forced easily • SNMP can yield a huge amount of information – – ARP tables Routing tables Device specific information Traffic statistics • Host based SNMP daemons may yield process, service and user information (e. g. Windows NT SNMP service) 2/19/2021

SNMP Enumeration Tools • Snmpget – Unix and Win 32 tool for enumerating individual SNMP keys • Snmpwalk – unix and Win 32 tool for enumerating whole or partial MIB trees 2/19/2021

Routing Daemons • Network topology is broadcast and may be obtained by network sniffing • Routers may be queried directly for routing and topology information • Network topology maps may be built using data obtained from routing daemons on hosts and routers • Can be more thorough and less intrusive than multiple traceroute queries 2/19/2021

Route Analysis Tools • Ripquery – A diagnostic tool for interrogating RIP gateways – Have a look on the Net for a RIP Spoofing tool I wrote a decade ago • BGP – looking glass servers divulge BGP information about routes • Ospf_monitor – A diagnostic tools for interrogating OSPF routers 2/19/2021

Network Reconnaissance and Enumeration Section 3 2/19/2021