Network Security Do S Attacks Smurf Attack Worms










- Slides: 18

Network Security: Do. S Attacks, Smurf Attack, & Worms Team 4 Jessica Waleski, Nicolas Keeton, Griffith Knoop, Richard Luthringshauser, & Samuel Rodriguez

Do. S Attack What is a Do. S Attack? ● ● Do. S stands for Denial of Service. Do. S attack is when an attacker prevents a user or computer from accessing a site or service by flooding the network with traffic. Common Tools for Do. S Attacks: ● TFN & TFN 2 K ● Stacheldraht Popular & Common Attacks: ● SYN flood ● ICMP flood ○ Smurf attack ○ UDP flood ○ Ping flood ● Ping of death (Po. D)

DDo. S Attack What is a DDo. S Attack? ● ● ● DDo. S stands for Distributed Denial of Service. It is a subclass of the Do. S. DDo. S attack is when a botnet (multiple connected devices that are usually connected through illicit means) is used to overwhelm a target host with fake traffic. Main Difference Between Do. S and DDo. S: ● Do. S Attack - a single internet connection. ● DDo. S Attack - multiple connected devices.

Do. S & DDo. S Attack - Weakness From the Attacker’s Point of View: ● Flood of packets must be sustained. ○ When packets stop sending, the target system is backed up. ● Often used with another form of attack, such as: ○ Disabling a connection in TCP hijacking ○ Preventing authentication ● Administrators/owners realize their machine is infected, remove the issue, and stop the attack. ● Must be aware that each packet can be traced back to its source. ○ For this reason, DDo. S is the most common type of Do. S attack.

Common Tools for Do. S Attacks - TFN & TFN 2 K ● ● TFN stands for Tribal Flood Network and TFN 2 K stands for Tribal Flood Network 2000. Can not be used to perform a DDo. S attack. TFN 2 K is a Newer Version of TFN: ○ More difficult to detect than its predecessor. ○ Can use a number of agents (other hosts) to coordinate an attack against one or more targets. TFN & TFN 2 K - Perform Various Attacks: ○ UDP flood attacks ○ ICMP flood attacks ○ TCP SYN flood attacks

TFN 2 K - How It Works & Advantages TFN 2 K Works on Two Fronts: 1. Command-driven client on the attacker’s system. 2. A daemon process (runs as a background process and the user has no direct control) operating on an agent system. How It Works: ● Attacker instructs its agents to attack a list of designated targets. ● Agents respond by flooding the targets with a large amount of packets. Advantages: ● Attacker-to-agent communications are encrypted and can be mixed with decoy packets. ● The attack and attacker-to-agent communications can be be randomly sent via TCP, UDP, and ICMP packets. ● Attacker can falsify (spoof) its IP address.

Common Tools for Do. S Attacks - Stacheldraht ● ● German for “barbed wire. ” Combines features of the Trinoo DDo. S tool with the source code from the TFN Do. S attack tool. Advantages: ● Adds encryption of communication, like TFN 2 K. ○ It also adds an automatic updating of the agents. ● Detects and automatically enables source address forgery. Performs Various Attacks: ● UDP flood ● ICMP flood ● TCP SYN flood ● Smurf attacks.

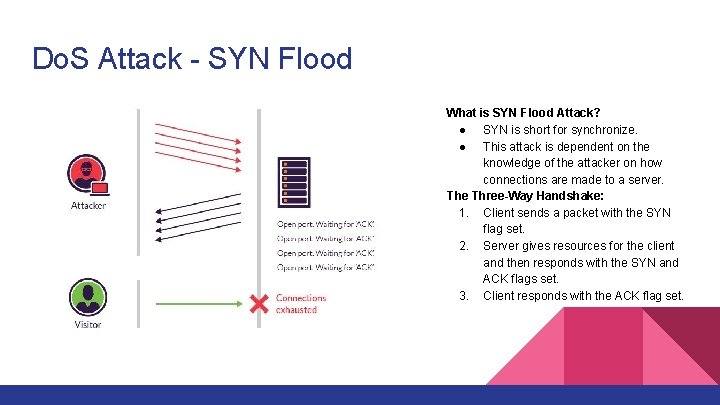
Do. S Attack - SYN Flood What is SYN Flood Attack? ● SYN is short for synchronize. ● This attack is dependent on the knowledge of the attacker on how connections are made to a server. The Three-Way Handshake: 1. Client sends a packet with the SYN flag set. 2. Server gives resources for the client and then responds with the SYN and ACK flags set. 3. Client responds with the ACK flag set.

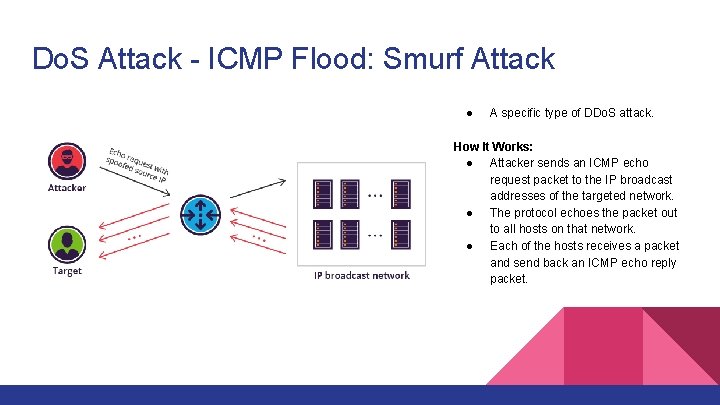
Do. S Attack - ICMP Flood: Smurf Attack ● A specific type of DDo. S attack. How It Works: ● Attacker sends an ICMP echo request packet to the IP broadcast addresses of the targeted network. ● The protocol echoes the packet out to all hosts on that network. ● Each of the hosts receives a packet and send back an ICMP echo reply packet.

Do. S Attack - ICMP Flood: UDP Flood Attack: ● An attacker will use the UDP (User Datagram Protocol) packets to overwhelm the targeted host. The targeted host: 1. Determine what application is at that port. 2. Finds no application waiting at that port. 3. Reply back with an ICMP Destination Unreachable packet.

Do. S Attack - ICMP Flood: Ping Flood Three Categories Based on the Target’s IP Address: ● Targeted local disclosed ping flood: targets a known IP address of the host. ● Router disclosed ping flood: targets a known internal IP address of a local router. ● Blind ping flood: targets a chosen IP address of the host from an external program. How It Works: ● Attacker sends continuous ICMP echo request packets ○ Does not wait for replies ● Host attempts to reply back with the ICMP echo reply packets.

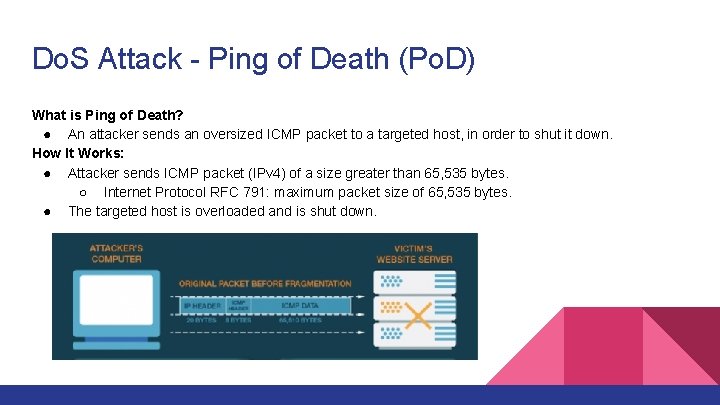
Do. S Attack - Ping of Death (Po. D) What is Ping of Death? ● An attacker sends an oversized ICMP packet to a targeted host, in order to shut it down. How It Works: ● Attacker sends ICMP packet (IPv 4) of a size greater than 65, 535 bytes. ○ Internet Protocol RFC 791: maximum packet size of 65, 535 bytes. ● The targeted host is overloaded and is shut down.

The First Computer Worm The Morris Internet Worm: ● Written by Robert Tappan Morris Jr, a student at Cornell University in 1988 from an MIT system. ● Intended for the worm to reveal bugs in programs ○ The worm was used in order to spread, not to cause actual harm. ● However, due to bugs in the worm’s code, it allowed a machine to be infected many times over. ○ Each additional infection created a new process in the infected system. ■ At least 6, 000 UNIX machines were infected. ○ Led to the creation of the Computer Emergency Response Team (CERT).

Worms - Propagation ● Worms do not require direct human interaction to propagate, unlike a virus. Propagation (Two primary ways): 1. Spreads through the network of the infected host. Copying itself onto any other hosts that the infected host has access to. ○ Most efficient, but harder to program. ○ Example: The ILOVEYOU worm 2. Scan your email address book and emails a copy of itself to everyone in your address book. ○ Easier to program, much more common.

Worms - Harmful Effects Negative Effects: ● Worms could: ○ Potentially delete/modify files. ○ Degrade your Internet connection and overall system performance. ○ Open a backdoor for a malicious attacker to use ■ Used to send spam or performing Do. S attacks. ● Least harm: consume bandwidth via its growth.

Any Questions? ?

Works Cited ● ● ● Mc. Afee. “What is a Computer Worm? ” Mc. Afee Blogs, Mc. Afee, 17 Nov 2014, https: //securingtomorrow. mcafee. com/consumer/identity-protection/what-is-worm/ “Denial of Service Attacks. ” Computer Security Fundamentals, by Chuck Easttom, 2 nd ed. , Pearson, 2012, pp. 72– 84. “Distributed Denial of Service Attacks. ” Incapsula. com, Imperva, https: //www. incapsula. com/ddos/denial-of-service. html “In Unix, What Is a Daemon? ” Knowledge Base, Indiana University, 16 May 2017, kb. iu. edu/d/aiau. Kabachinski, Jeff. "Viruses, Worms, and Trojans. " Biomedical Instrumentation & Technology, vol. 39, no. 1, Jan. 2005, pp. 46 -48. EBSCOhost, proxy. kennesaw. edu/login? url=http: //search. ebscohost. com/login. aspx? direct=true&db=mnh&AN=1 5742846&site=eds-live&scope=site

Works Cited Cont’d ● ● ● “Malware. ” Computer Security Fundamentals, by Chuck Easttom, 2 nd ed. , Pearson, 2012, pp. 92– 106. “Ping Flood (ICMP Flood). ” Incapsula. com, Imperva, www. incapsula. com/ddos/attack-glossary/Pingicmp-flood. html Ping of Death (Po. D). ” Incapsula. com, Imperva, https: //www. incapsula. com/ddos/attackglossary/ping-of-death. html “Smurf DDo. S Attack. ” Incapsula. com, Imperva, www. incapsula. com/ddos/attack-glossary/smurfattack-ddos. html “TCP SYN Flood. ” Incapsula. com, Imperva, www. incapsula. com/ddos/attack-glossary/syn-flood. html