Automatic Generation and Analysis of Attack Graphs Written












- Slides: 35

Automatic Generation and Analysis of Attack Graphs Written by Oleg Sheyner, Joshua Haines, Somesh Jha, Richard Lippmann, and Jeannette M. Wing IEEE Symposium on Security and Privacy 2002 Presented by HAN Jin Singapore Management University September 2008

Outline • Preliminaries • Motivation – Attack Graph Definition • Automated Generation – An Illustrative Example • Automated Analysis • Limitations

Outline • Preliminaries • Motivation – Attack Graph Definition • Automated Generation – An Illustrative Example • Automated Analysis • Limitations

Vulnerability • In computer security, the term vulnerability is applied to a weakness in a system which allows an attacker to violate the integrity of that system. • Vulnerabilities may result from weak passwords, software bugs, a computer virus or other malware, a script code injection, or a SQL injection.

Common Vulnerabilities and Exposures • http: //cve. mitre. org/ – CVE is a list or dictionary that provides common names for publicly known information security vulnerabilities and exposures – Every vulnerability is assigned with a CVE Number: E. g. CVE-2008 -0075: Unspecified vulnerability in Microsoft Internet Information Services (IIS) 5. 1 through 6. 0 allows remote attackers to execute arbitrary code via crafted inputs to ASP pages.

Exploit • An exploit is a piece of software, a chunk of data, or sequence of commands that take advantage of a vulnerability in order to cause unintended or unanticipated behavior to occur on computer software & hardware. • Commonly categorized and named by the type of vulnerability they utilize: E. g. SQL Injection Vulnerability SQL Inj. Exploit Buffer Overflows Vulnerability B. O. Exploit

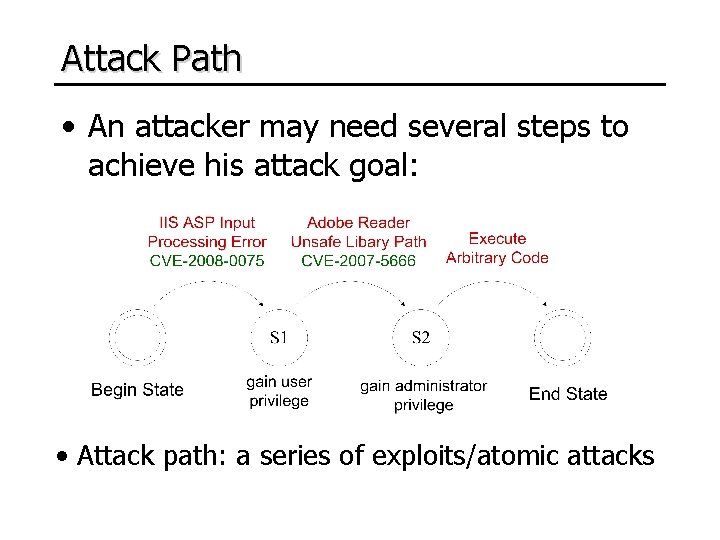
Attack Path • An attacker may need several steps to achieve his attack goal: • Attack path: a series of exploits/atomic attacks

Outline • Preliminaries • Motivation – Attack Graph Definition • Automated Generation – An Illustrative Example • Automated Analysis • Limitations

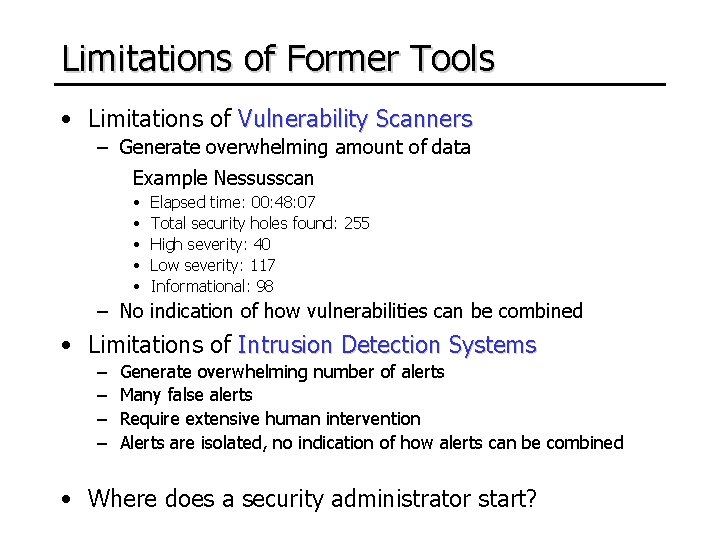
Limitations of Former Tools • Limitations of Vulnerability Scanners – Generate overwhelming amount of data Example Nessusscan • • • Elapsed time: 00: 48: 07 Total security holes found: 255 High severity: 40 Low severity: 117 Informational: 98 – No indication of how vulnerabilities can be combined • Limitations of Intrusion Detection Systems – – Generate overwhelming number of alerts Many false alerts Require extensive human intervention Alerts are isolated, no indication of how alerts can be combined • Where does a security administrator start?

What is lacking? • Context for total network security • How outsiders penetrate firewalls and launch attacks from compromised hosts • Insider attacks

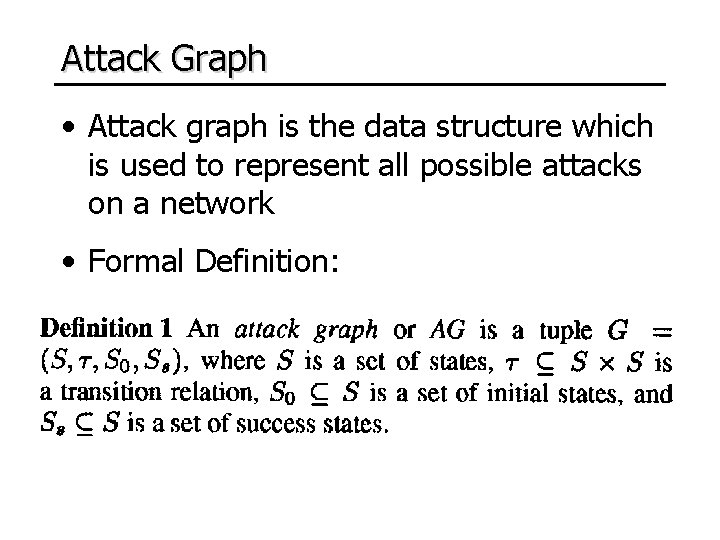
Attack Graph • Attack graph is the data structure which is used to represent all possible attacks on a network • Formal Definition:

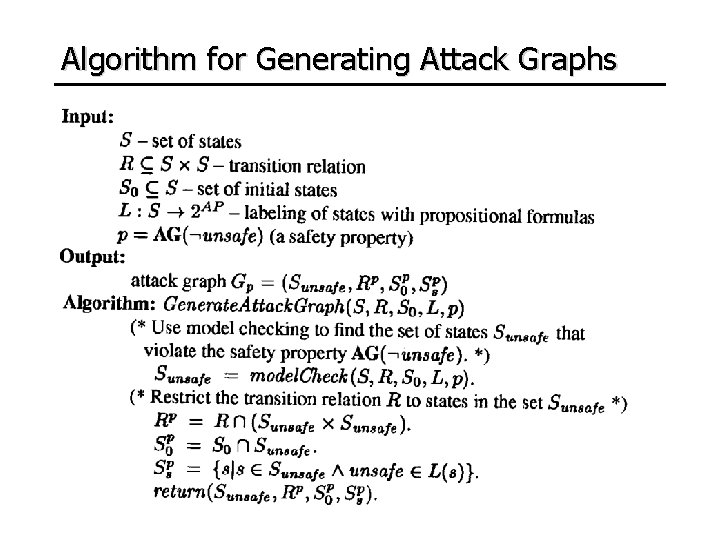
Algorithm for Generating Attack Graphs

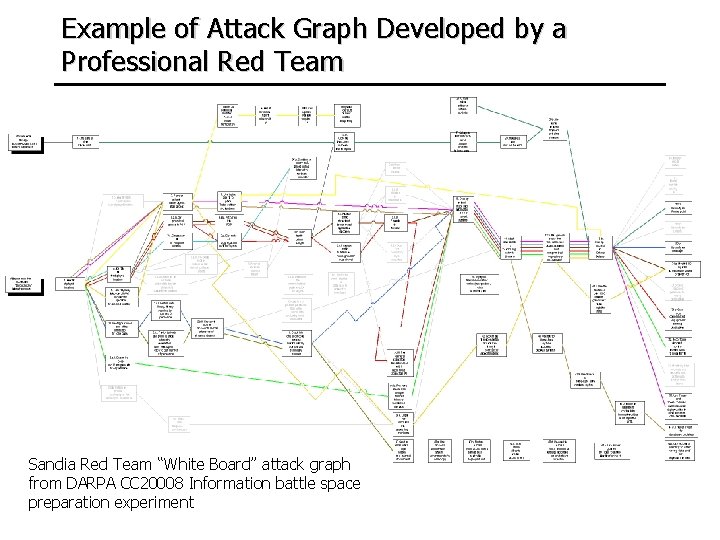
Example of Attack Graph Developed by a Professional Red Team Sandia Red Team “White Board” attack graph from DARPA CC 20008 Information battle space preparation experiment

Problem Statement • Problem: Generating attack graphs by hand is tedious, error-prone, and impractical for large systems. • Goal: Automate the generation and analysis of attack graphs. – Generation • Must be fast and completely automatic • Must handle large, realistic examples • Should guarantee properties of attack graphs – Analysis • Must enable security analysis by system administrators • Should support incremental, partial specification

Outline • Preliminaries • Motivation – Attack Graph Definition • Automated Generation – An Illustrative Example • Automated Analysis • Limitations

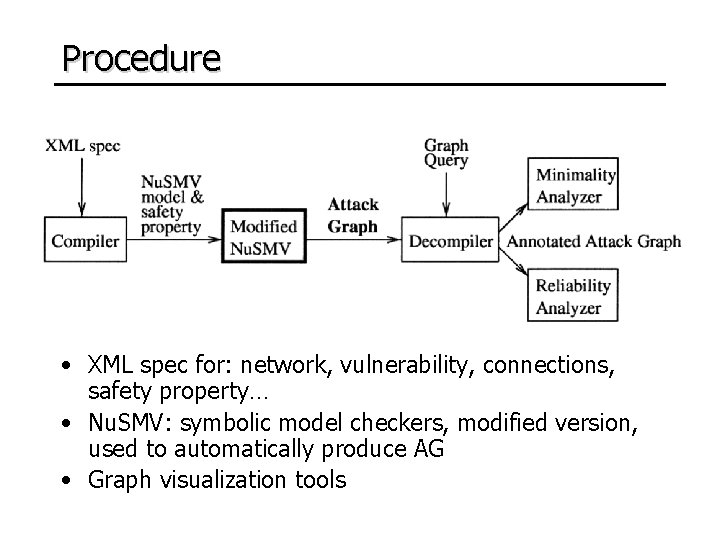
Procedure • XML spec for: network, vulnerability, connections, safety property… • Nu. SMV: symbolic model checkers, modified version, used to automatically produce AG • Graph visualization tools

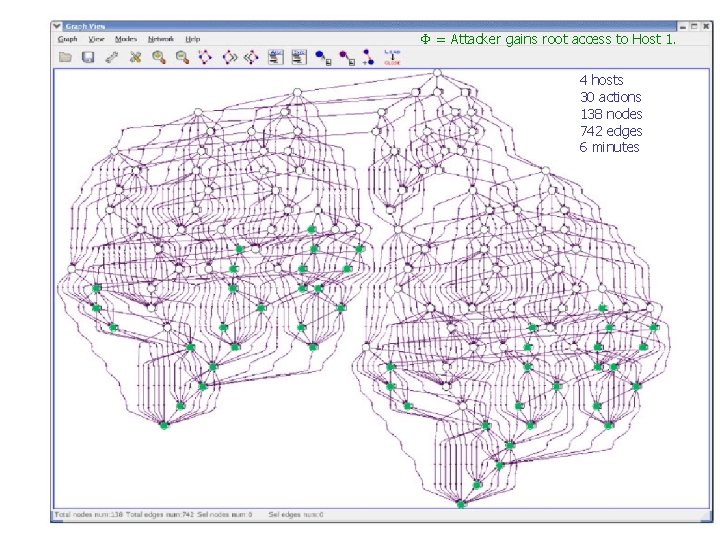
= Attacker gains root access to Host 1. 4 hosts 30 actions 138 nodes 742 edges 6 minutes

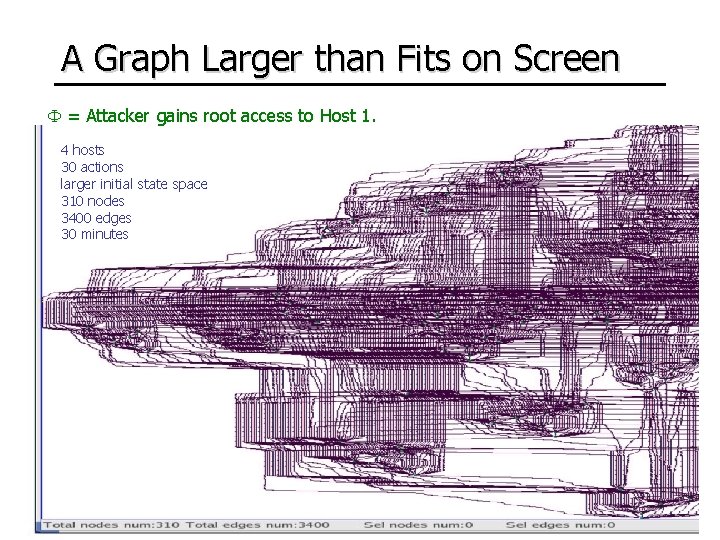
A Graph Larger than Fits on Screen = Attacker gains root access to Host 1. 4 hosts 30 actions larger initial state space 310 nodes 3400 edges 30 minutes

Outline • Preliminaries • Motivation – Attack Graph Definition • Automated Generation – An Illustrative Example • Automated Analysis • Limitations

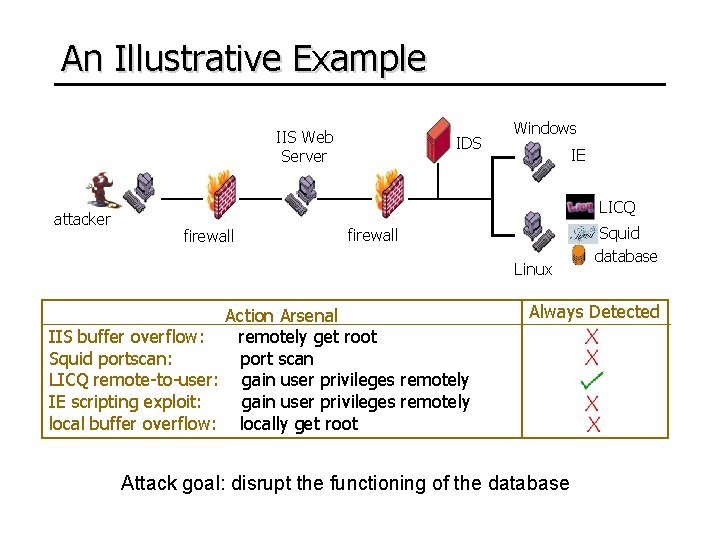
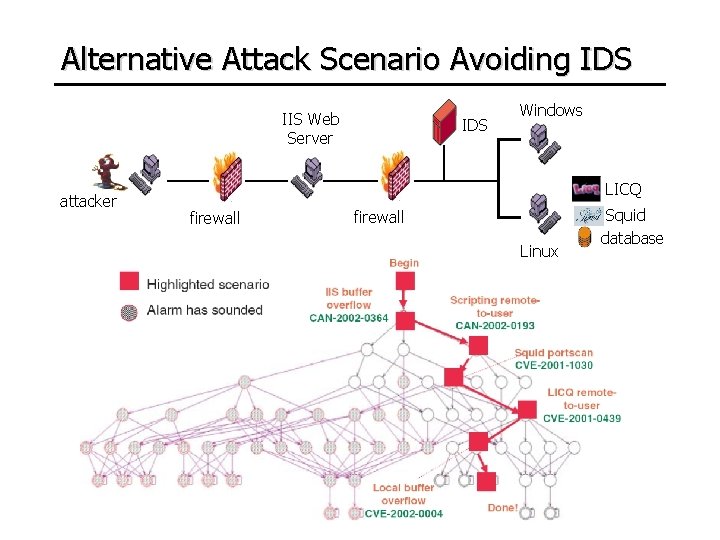
An Illustrative Example IIS Web Server attacker IDS Windows IE LICQ firewall Linux Action Arsenal IIS buffer overflow: remotely get root Squid portscan: port scan LICQ remote-to-user: gain user privileges remotely IE scripting exploit: gain user privileges remotely local buffer overflow: locally get root Squid database Always Detected Attack goal: disrupt the functioning of the database

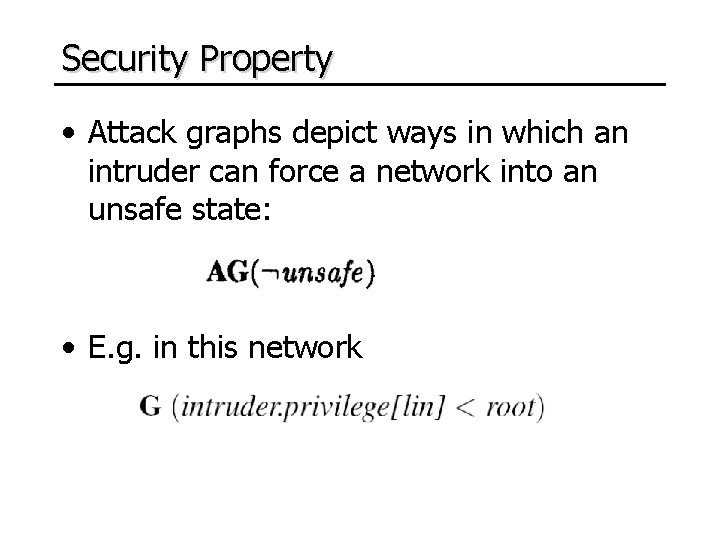
Security Property • Attack graphs depict ways in which an intruder can force a network into an unsafe state: • E. g. in this network

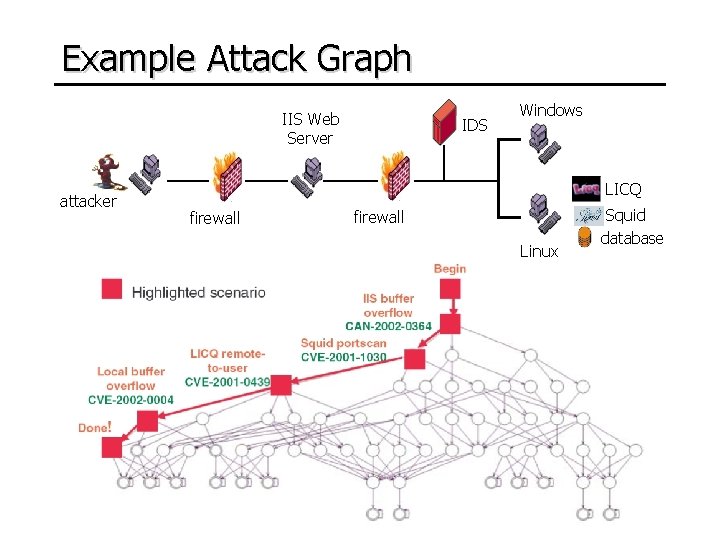
Example Attack Graph IIS Web Server attacker IDS Windows LICQ firewall Linux Squid database

Alternative Attack Scenario Avoiding IDS IIS Web Server attacker IDS Windows LICQ firewall Linux Squid database

Outline • Preliminaries • Motivation – Attack Graph Definition • Automated Generation – An Illustrative Example • Automated Analysis • Limitations

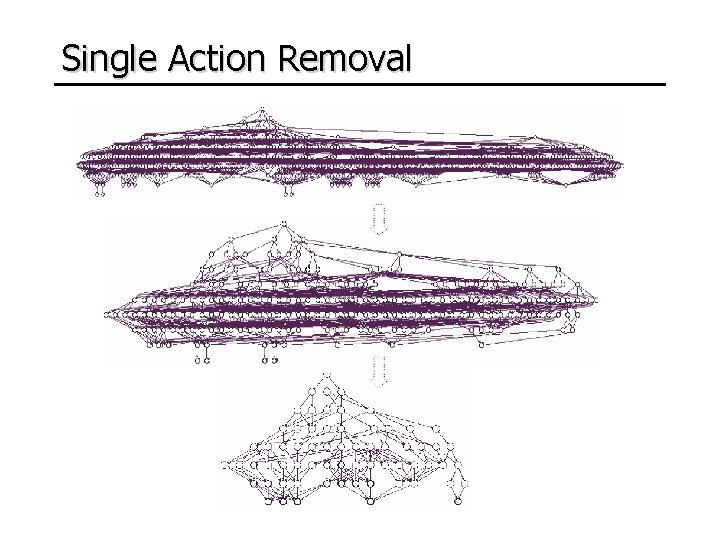
Single Action Removal

Minimization Analyzer • What actions are necessary for the intruder to succeed? – Given a fixed set of atomic attacks, not all of them may be available to the intruder – Nondeterministically decide which subset of atomic attacks to choose initially

Minimum Critical Set of Actions A = the set of actions available to the intruder Def 1: A set of actions C is critical if the intruder cannot achieve his goal using only actions in A C. Def 2: A critical set of actions C is minimum if there is no critical action set of smaller size. Def 3: A set of actions A’ A is realizable if the intruder can achieve his goal using only actions in A’. Minimum Critical Set of Actions (MCSA): Given a set of actions A and an attack graph G, find a minimum critical action subset C A. Finding a minimum set: NP-complete

Reliability Analyzer • What is the likelihood that the intruder goes undetected? – Interpret as a Markov Decision Process – Assign probability for detecting each atomic attack • Each attack has both detectable and stealthy variants Probabilistic Attack Graph

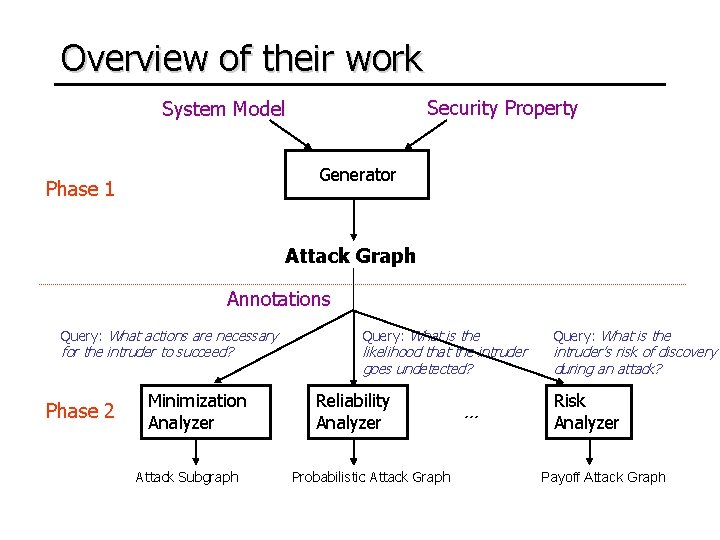
Overview of their work Security Property System Model Generator Phase 1 Attack Graph Annotations Query: What actions are necessary for the intruder to succeed? Phase 2 Minimization Analyzer Attack Subgraph Query: What is the likelihood that the intruder goes undetected? Reliability Analyzer Probabilistic Attack Graph … Query: What is the intruder’s risk of discovery during an attack? Risk Analyzer Payoff Attack Graph

Outline • Preliminaries • Motivation – Attack Graph Definition • Automated Generation – An Illustrative Example • Automated Analysis • Limitations

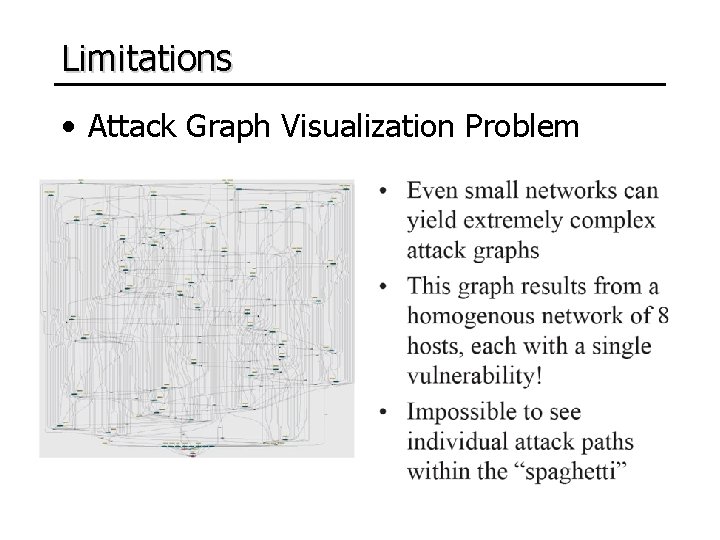
Limitations • Attack Graph Visualization Problem


Scalability Problem Too complex and difficult to use for large network One possible solution: Ou, X. , Boyer, W. F. , and Mc. Queen, M. A. A scalable approach to attack graph generation. In Proceedings of the 13 th ACM Conference on Computer and Communications Security (CCS '06). ACM, New York, NY, 336 -345.

Zero-day exploit • A zero-day (or zero-hour) attack or threat is a computer threat that tries to exploit unknown, undisclosed or unpatched computer application vulnerabilities • Current attack graph analysis is based completely on known vulnerability info

Q&A Thanks