Detecting and Responding to Data Link Layer Attacks







- Slides: 15

Detecting and Responding to Data Link Layer Attacks With Scapy TJ OConnor September 2011 GIAC (GSE, GSEC, GCFW, GCIA, GCIH, GCFA, GREM, GPEN, GWAPT, GCFE) SANS Technology Institute - Candidate for Master of Science Degree 1 1

The Hotel Area Network Dilemma • About 1 year ago, sitting in a hotel room in Washington D. C. – “Free” Wireless Internet starts working intermittently – Users start complaining of Facebook posts they didn’t make • Fire up IDS toolkit – IDS doesn’t see anything happening at Layer 3 – IPS isn’t seeing any attacks against the hotel either • What’s happening? – As incident responders, need the ability to quickly write tools to parse data… in this case, Layer 2 traffic SANS Technology Institute - Candidate for Master of Science Degree 2

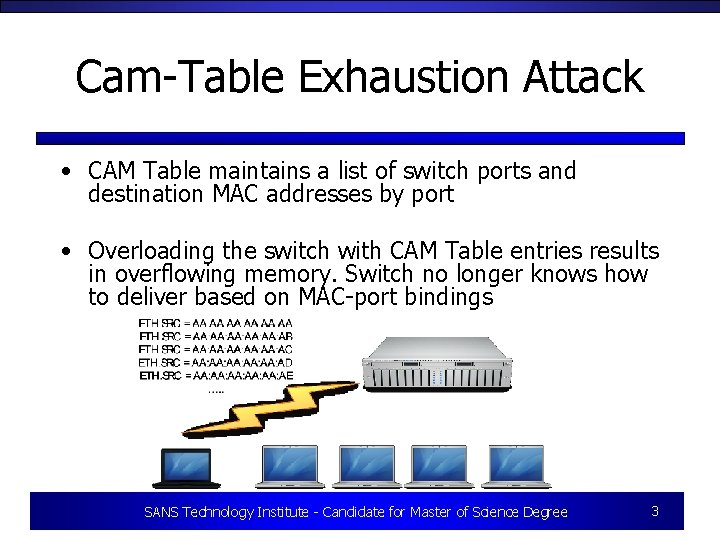
Cam-Table Exhaustion Attack • CAM Table maintains a list of switch ports and destination MAC addresses by port • Overloading the switch with CAM Table entries results in overflowing memory. Switch no longer knows how to deliver based on MAC-port bindings SANS Technology Institute - Candidate for Master of Science Degree 3

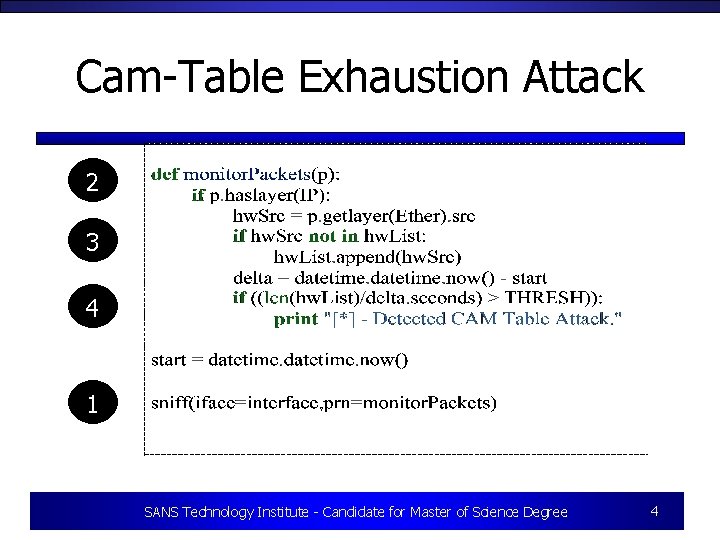
Cam-Table Exhaustion Attack 2 3 4 1 SANS Technology Institute - Candidate for Master of Science Degree 4

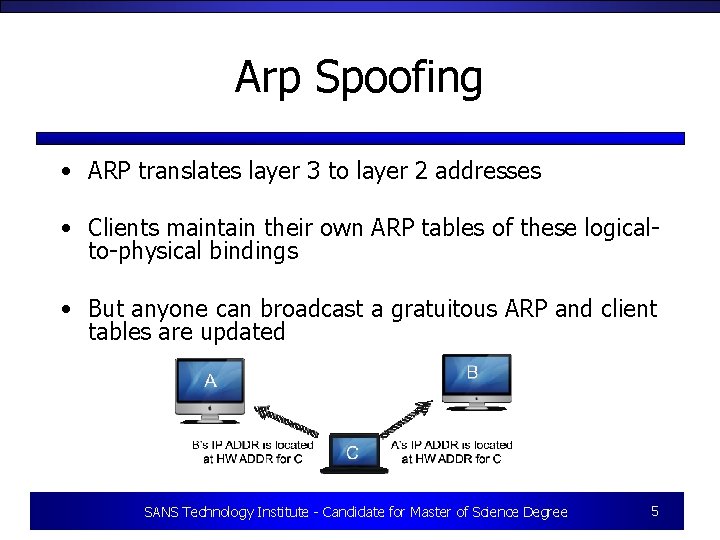
Arp Spoofing • ARP translates layer 3 to layer 2 addresses • Clients maintain their own ARP tables of these logicalto-physical bindings • But anyone can broadcast a gratuitous ARP and client tables are updated SANS Technology Institute - Candidate for Master of Science Degree 5

Arp Spoofing 2 3 4 1 SANS Technology Institute - Candidate for Master of Science Degree 6

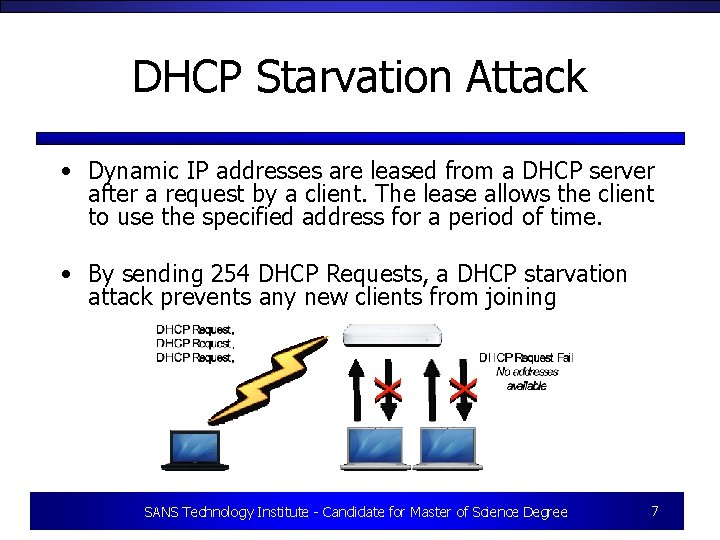
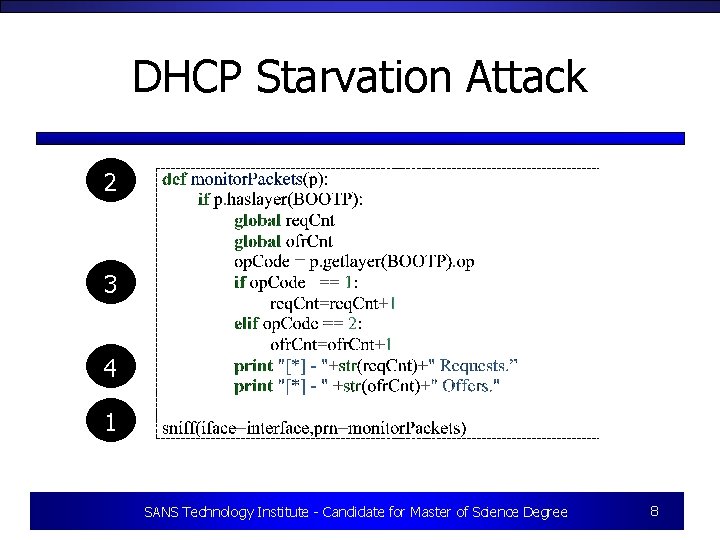
DHCP Starvation Attack • Dynamic IP addresses are leased from a DHCP server after a request by a client. The lease allows the client to use the specified address for a period of time. • By sending 254 DHCP Requests, a DHCP starvation attack prevents any new clients from joining SANS Technology Institute - Candidate for Master of Science Degree 7

DHCP Starvation Attack 2 3 4 1 SANS Technology Institute - Candidate for Master of Science Degree 8

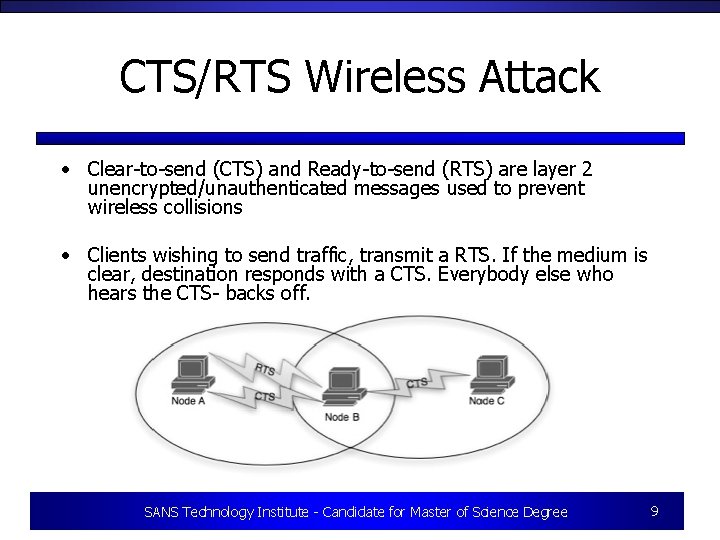
CTS/RTS Wireless Attack • Clear-to-send (CTS) and Ready-to-send (RTS) are layer 2 unencrypted/unauthenticated messages used to prevent wireless collisions • Clients wishing to send traffic, transmit a RTS. If the medium is clear, destination responds with a CTS. Everybody else who hears the CTS- backs off. SANS Technology Institute - Candidate for Master of Science Degree 9

CTS/RTS Wireless Attack 2 3 4 1 1 SANS Technology Institute - Candidate for Master of Science Degree 10

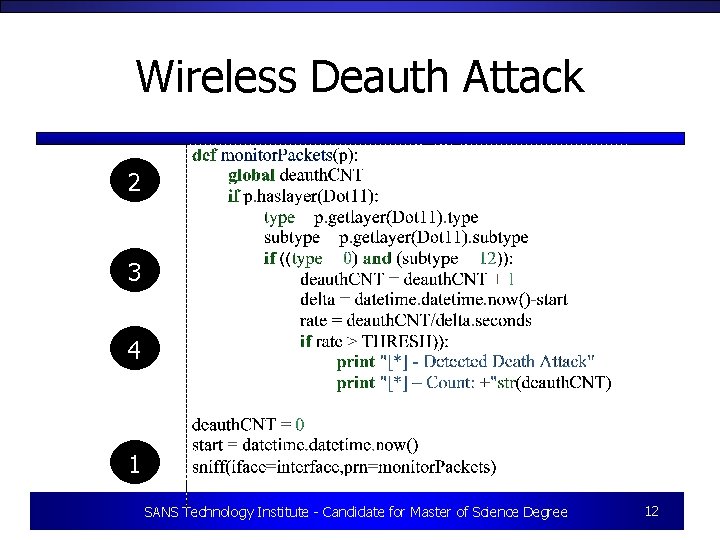
Wireless Deauth Attack • Clients authenticate themselves to access points prior to association with the network • Authentication typically occurs over unencrypted layer 2 management frames • De-authentication also occurs over unencrypted layer 2 management frames • Tools such as aircrack-NG can spoof a deauthentication SANS Technology Institute - Candidate for Master of Science Degree 11

Wireless Deauth Attack 2 3 4 1 SANS Technology Institute - Candidate for Master of Science Degree 12

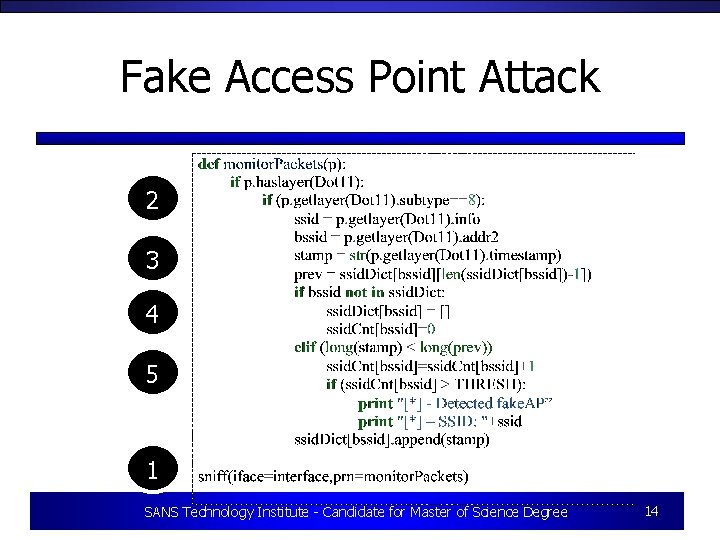
Fake Access Point Attack • Wireless access points are advertised over an 802. 11 beacon frame • Clients use the information in the 802. 11 beacon frame to connect to the wireless AP • Anyone can broadcast an 802. 11 beacon, impersonating a network • Combined with tools like karmetasploit, an attacker can instantly attack a client that joins a fake AP. SANS Technology Institute - Candidate for Master of Science Degree 13

Fake Access Point Attack 2 3 4 5 1 SANS Technology Institute - Candidate for Master of Science Degree 14

Conclusions • Layer two attacks still present a threat to modern networks • Typically these threats go unnoticed by intrusion detection systems • Scapy and a little creativity can be used to automate detecting layer two attacks • For more information, see “Detecting and Responding to Data Link Layer Attacks” published in SANS GCIA Reading Room SANS Technology Institute - Candidate for Master of Science Degree 15