Analysis Techniques for a Secure NAS Shankar Sastry


















- Slides: 58

Analysis Techniques for a Secure NAS Shankar Sastry Department of EECS University of California, Berkeley JUP Kickoff, Nov 23 rd, 2002 Sastry@eecs. berkeley. edu 510 -642 -0253

Prequel: The Impact of Sept. 11 on Air Transportation Prof. R. John Hansman, Director MIT International Center for Air Transportation rjhans@mit. edu 617 -253 -2271

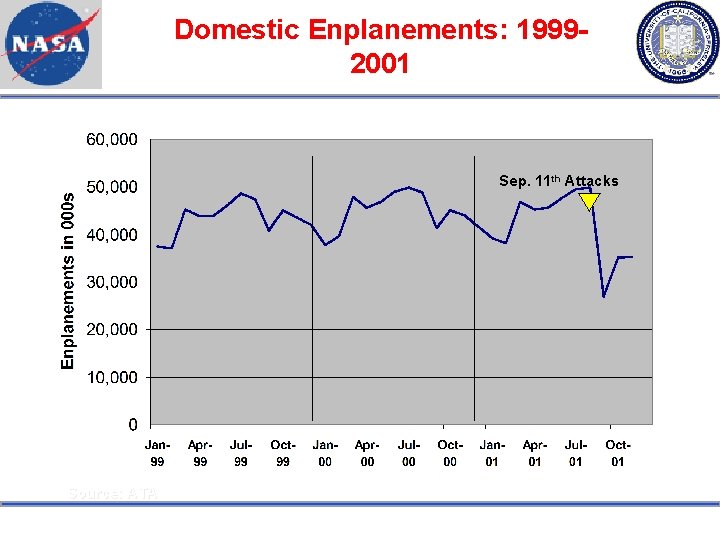
Domestic Enplanements: 19992001 Sep. 11 th Attacks Source: ATA

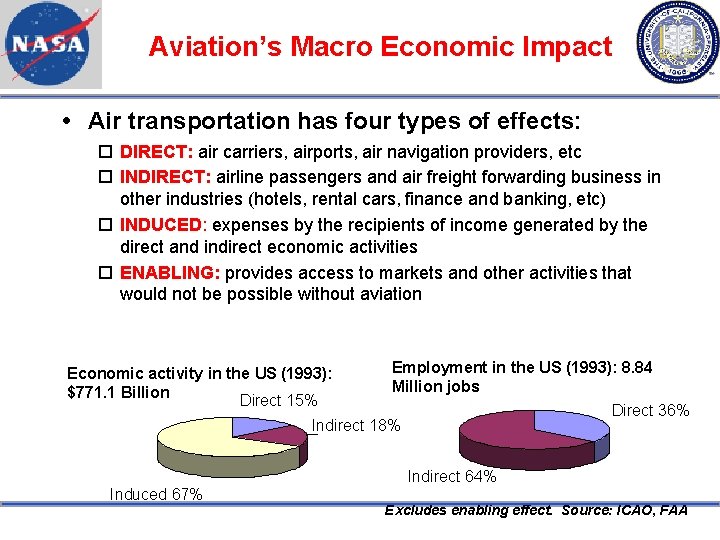
Aviation’s Macro Economic Impact Air transportation has four types of effects: DIRECT: air carriers, airports, air navigation providers, etc INDIRECT: airline passengers and air freight forwarding business in other industries (hotels, rental cars, finance and banking, etc) INDUCED: expenses by the recipients of income generated by the direct and indirect economic activities ENABLING: provides access to markets and other activities that would not be possible without aviation Employment in the US (1993): 8. 84 Million jobs Direct 36% Indirect 18% Economic activity in the US (1993): $771. 1 Billion Direct 15% Indirect 64% Induced 67% Excludes enabling effect. Source: ICAO, FAA

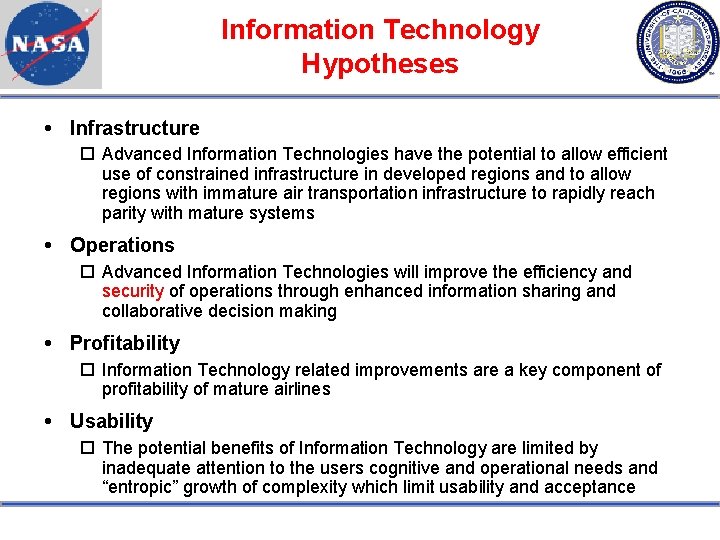
Information Technology Hypotheses Infrastructure Advanced Information Technologies have the potential to allow efficient use of constrained infrastructure in developed regions and to allow regions with immature air transportation infrastructure to rapidly reach parity with mature systems Operations Advanced Information Technologies will improve the efficiency and security of operations through enhanced information sharing and collaborative decision making Profitability Information Technology related improvements are a key component of profitability of mature airlines Usability The potential benefits of Information Technology are limited by inadequate attention to the users cognitive and operational needs and “entropic” growth of complexity which limit usability and acceptance

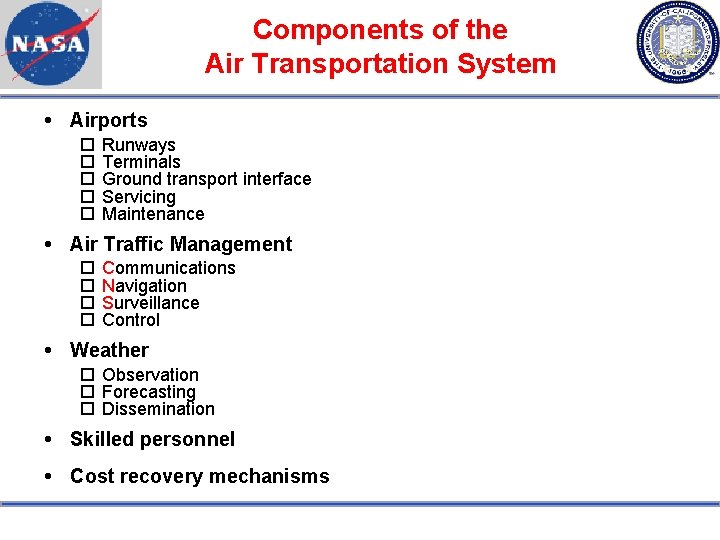
Components of the Air Transportation System Airports Runways Terminals Ground transport interface Servicing Maintenance Air Traffic Management Communications Navigation Surveillance Control Weather Observation Forecasting Dissemination Skilled personnel Cost recovery mechanisms

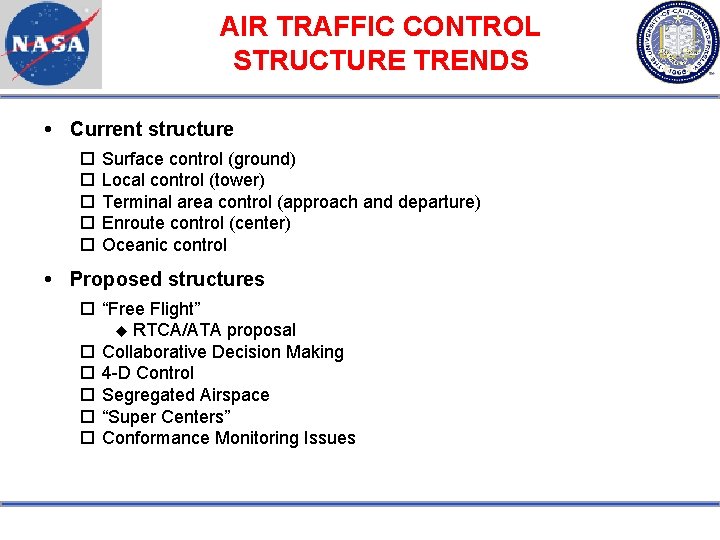
AIR TRAFFIC CONTROL STRUCTURE TRENDS Current structure Surface control (ground) Local control (tower) Terminal area control (approach and departure) Enroute control (center) Oceanic control Proposed structures “Free Flight” RTCA/ATA proposal Collaborative Decision Making 4 -D Control Segregated Airspace “Super Centers” Conformance Monitoring Issues

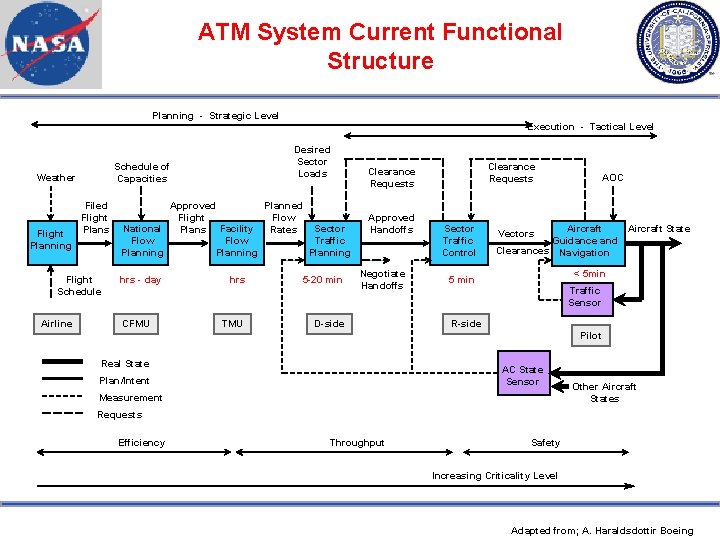
ATM System Current Functional Structure Planning - Strategic Level Execution - Tactical Level Schedule of Capacities Weather Flight Planning Filed Flight Plans Flight Schedule Airline Desired Sector Loads Approved Planned Flight Flow National Sector Plans Facility Rates Flow Traffic Planning hrs - day CFMU hrs TMU 5 -20 min Clearance Requests Approved Handoffs Negotiate Handoffs D-side Sector Traffic Control AOC Aircraft State Aircraft Guidance and Clearances Navigation Vectors < 5 min 5 min Traffic Sensor R-side Pilot Real State AC State Sensor Plan/Intent Measurement Other Aircraft States Requests Efficiency Throughput Safety Increasing Criticality Level Adapted from; A. Haraldsdottir Boeing

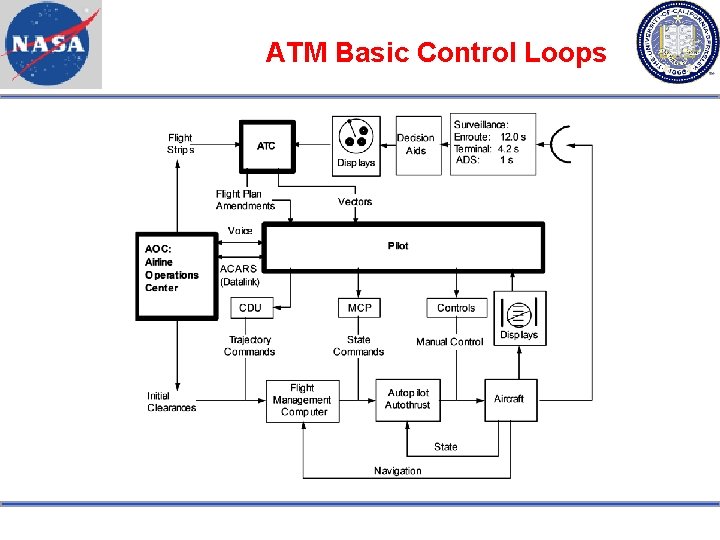
ATM Basic Control Loops

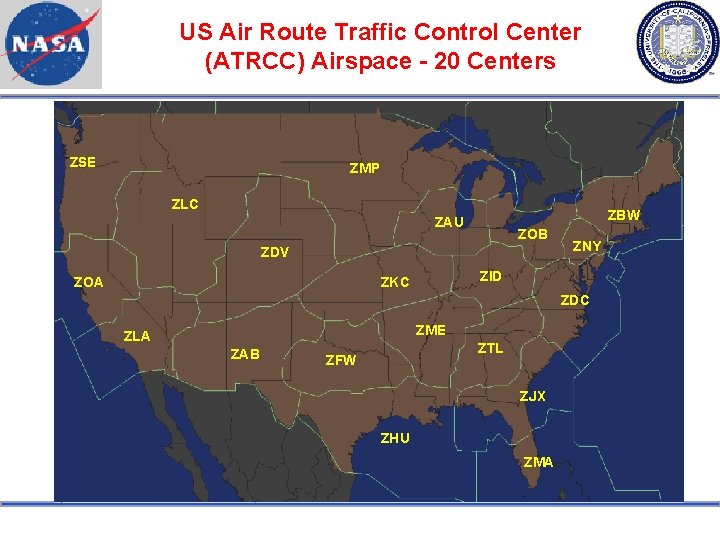
US Air Route Traffic Control Center (ATRCC) Airspace - 20 Centers ZSE ZMP ZLC ZBW ZAU ZOB ZDV ZOA ZNY ZID ZKC ZDC ZME ZLA ZAB ZTL ZFW ZJX ZHU ZMA

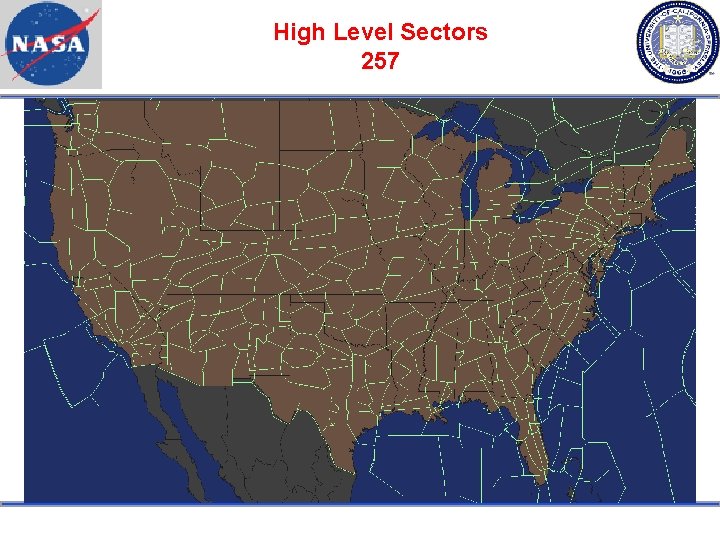
High Level Sectors 257

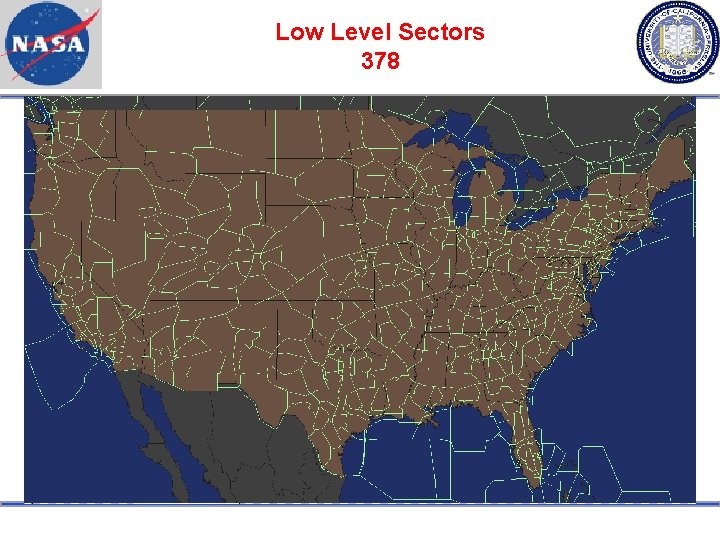
Low Level Sectors 378

TRACONS

COMMUNICATION TRENDS Voice VHF (line of sight) HF (over the horizon) Ground lines Datalink (line of sight) ACARS (VHF) Mode S Satellite Geosynchronous (data, voice, images) Air-ground Ground-ground LEO and MEO Networks Aeronautical Telecommunications Network (ATN) CDMA, TDMA TCP/IP Voice Data Link (VDL-2, VDL-3)

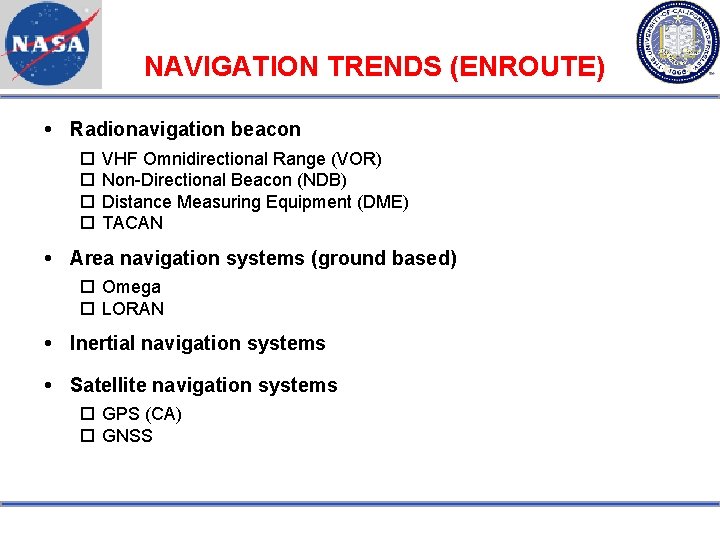
NAVIGATION TRENDS (ENROUTE) Radionavigation beacon VHF Omnidirectional Range (VOR) Non-Directional Beacon (NDB) Distance Measuring Equipment (DME) TACAN Area navigation systems (ground based) Omega LORAN Inertial navigation systems Satellite navigation systems GPS (CA) GNSS

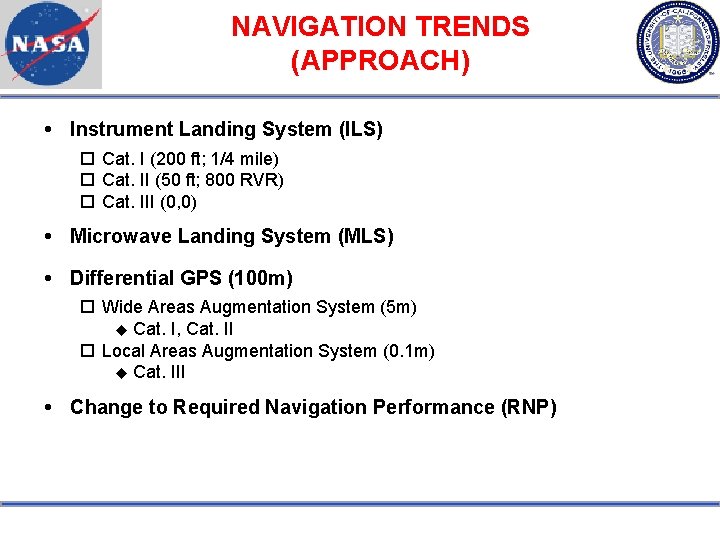
NAVIGATION TRENDS (APPROACH) Instrument Landing System (ILS) Cat. I (200 ft; 1/4 mile) Cat. II (50 ft; 800 RVR) Cat. III (0, 0) Microwave Landing System (MLS) Differential GPS (100 m) Wide Areas Augmentation System (5 m) Cat. I, Cat. II Local Areas Augmentation System (0. 1 m) Cat. III Change to Required Navigation Performance (RNP)

GPS ISSUES Precision Ionosphere Clock Errors Availability Integrity RAIM Differential Vulnerability Jamming Trust Control by US Do. D International concerns Selective Availability, turned off 1999 Continuity US guarantee of service free to world through 2005

SURVEILLANCE TRENDS Primary radar Enroute (12 sec scan) Terminal area (4. 2 sec scan) Secondary radar Transponders Mode C (altitude) Mode S (2 -way data exchange) Onboard surveillance TCAS Automatic Dependent Surveillance (ADS) Oceanic (INS Based) Broadcast (ADS-B)

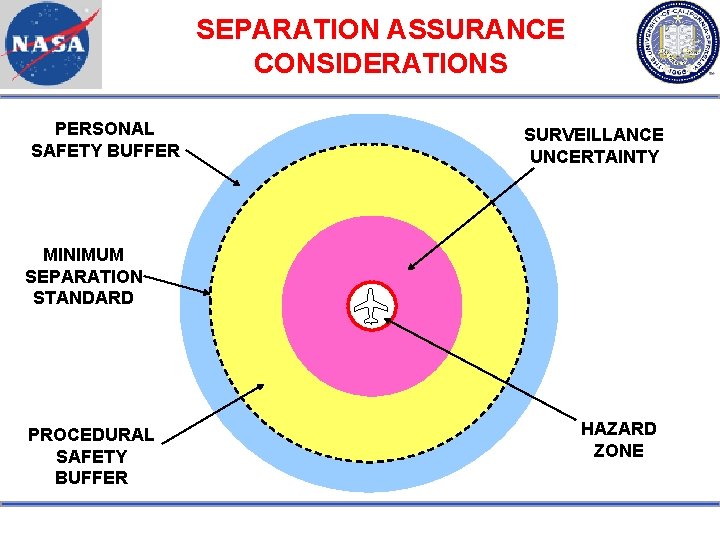
SEPARATION ASSURANCE CONSIDERATIONS PERSONAL SAFETY BUFFER SURVEILLANCE UNCERTAINTY MINIMUM SEPARATION STANDARD PROCEDURAL SAFETY BUFFER HAZARD ZONE

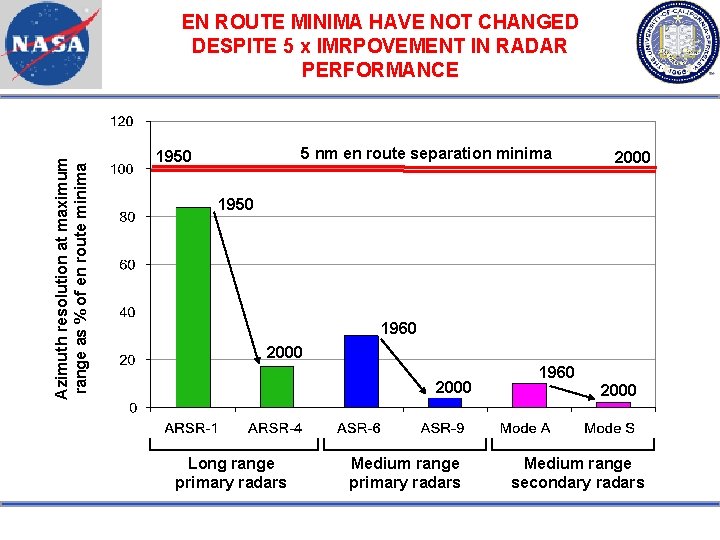
Azimuth resolution at maximum range as % of en route minima EN ROUTE MINIMA HAVE NOT CHANGED DESPITE 5 x IMRPOVEMENT IN RADAR PERFORMANCE 5 nm en route separation minima 1950 2000 1950 1960 2000 Long range primary radars Medium range primary radars 1960 2000 Medium range secondary radars

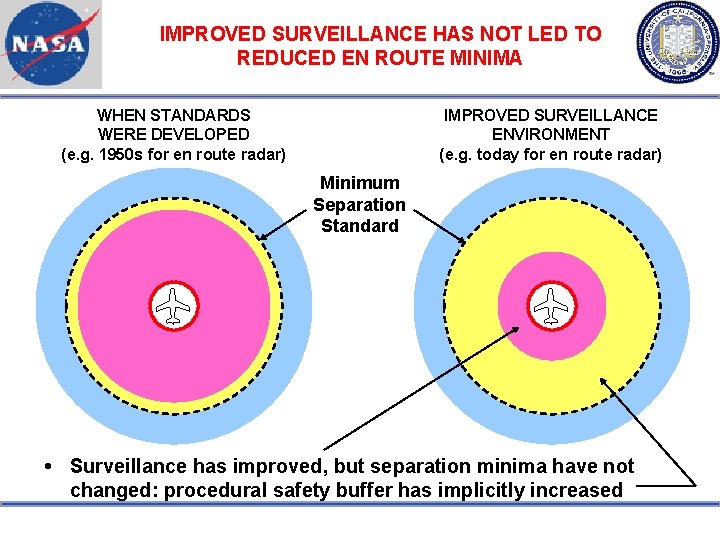
IMPROVED SURVEILLANCE HAS NOT LED TO REDUCED EN ROUTE MINIMA WHEN STANDARDS WERE DEVELOPED (e. g. 1950 s for en route radar) IMPROVED SURVEILLANCE ENVIRONMENT (e. g. today for en route radar) Minimum Separation Standard Surveillance has improved, but separation minima have not changed: procedural safety buffer has implicitly increased

Critical Infrastructure Protection for ATM Shankar Sastry

Increased use of Software in Critical Applications Potential for common mode software failure (not present in h/w) Lack of metrics and evaluation methods: How to measure 10 -8 Human factors problems: induced human errors Today we control the lifecycle (process) since we don’t know how to evaluate the product Unknown efficacy Expensive. Industry attributes 60% of avionics development cost to V&V Doesn’t scale to very large systems: more automation is needed to reduce errors and for increased reuse (e. g. , code synthesis)

Security Challenges Terrorists may employ highly malicious attacks much worse than those seen to date Current technology is not designed nor intended to withstand such attacks Vulnerabilities in our networked systems can be exploited by anyone anywhere in the world Successful attacks may not be detected Critical systems must be designed to provide continuous correct operation even under successful attack

What is missing Strong enough barriers to penetration Accurate intrusion detection Ability to fuse incident reports across a global area and deduce possible plans and intentions For warning To guide interventions Systems that tolerate attacks and keep on ticking And, because the above will never be perfect:

Tolerating attacks System designs that give some inherent resistance to attack Diversity Redundancy Decentralization Detect and repair damage Biological models

Diversity Economic forces have turned the global computing environment into a monoculture Diversity can reduce overall losses from attack Hedges against unknown means of attack Surviving elements support continued operation Obtaining diversity manually is expensive (e. g. , n-version programming) Could explore automatic artificial diversity

Redundancy Current uses of redundancy are expensive and do not scale E. g. , replication of servers Scalable methods provide weaker guarantees Probabilistic Eventual consistency E. g. , epidemic and gossip protocols Information exchanges involve randomly or opportunistically chosen gossip partners E. g. , Quorum systems Operations access quorums (subsets) of servers

Decentralization Behavior is the result of autonomous activity by member entities Undetected error states are tolerated Stateless: State is regenerated Can tolerate loss of some components No single points of failure Control, management, gateway, etc, functions redundant and/or migratable Trend toward decentralized design for maximum utilization

Get inspiration from nature Robustness Highly mechanisms at many levels decentralized and redundant Widespread Automated Adaptive use of diversity damage detection and repair and evolving Dispensable components

A Solution Strategy for the Conflict Resolution Problem in 2 D and 3 D Airspaces Jianghai Hu with Maria Prandini, Arnab Nilim, Shankar Sastry Department of EECS University of California, Berkeley

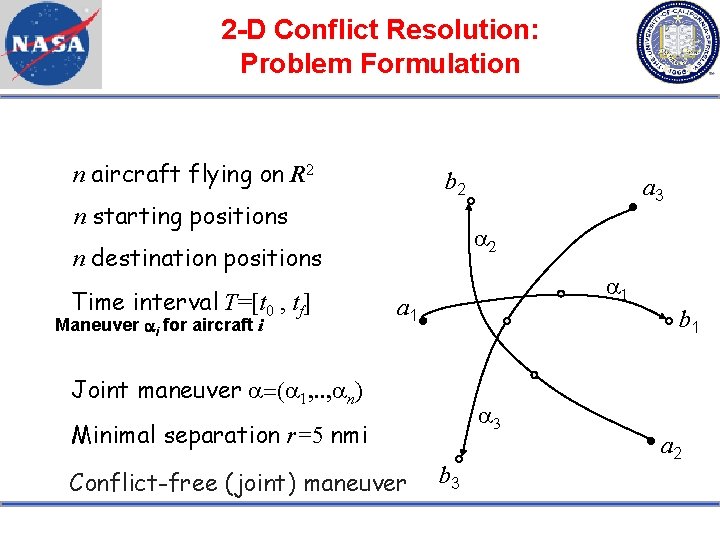
2 -D Conflict Resolution: Problem Formulation n aircraft flying on R 2 b 2 n starting positions a 2 n destination positions Time interval T=[t 0 , tf] Maneuver ai for aircraft i a 3 a 1 b 1 Joint maneuver a=(a 1, . . , an) a 3 Minimal separation r=5 nmi Conflict-free (joint) maneuver b 3 a 2

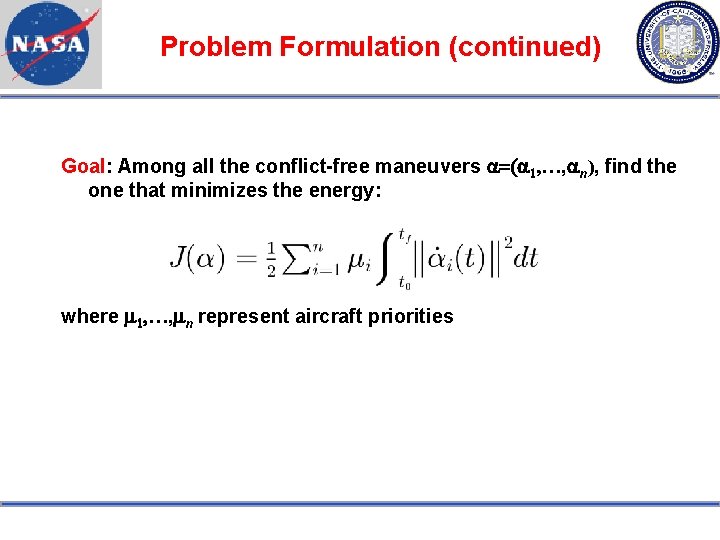
Problem Formulation (continued) Goal: Among all the conflict-free maneuvers a=(a 1, …, an), find the one that minimizes the energy: where m 1, …, mn represent aircraft priorities

An Example of Optimal Maneuvers

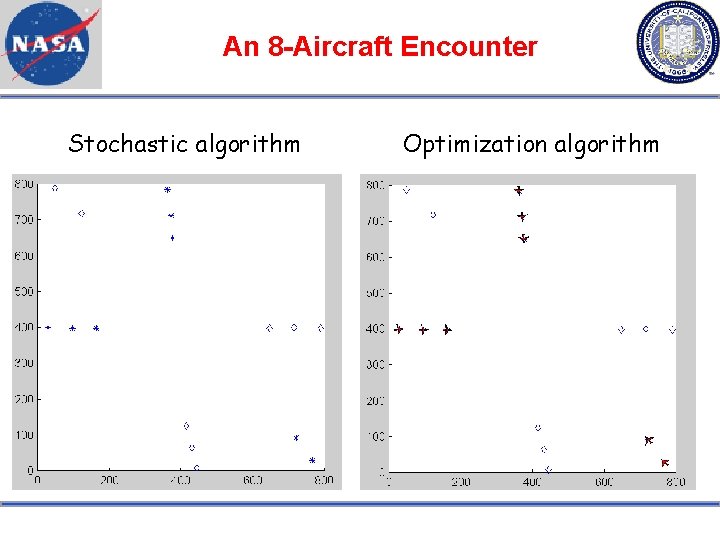
An 8 -Aircraft Encounter Stochastic algorithm Optimization algorithm

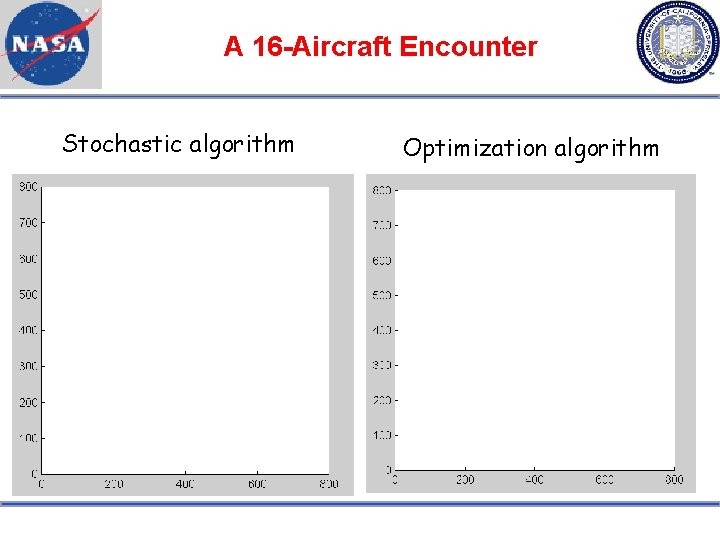
A 16 -Aircraft Encounter Stochastic algorithm Optimization algorithm

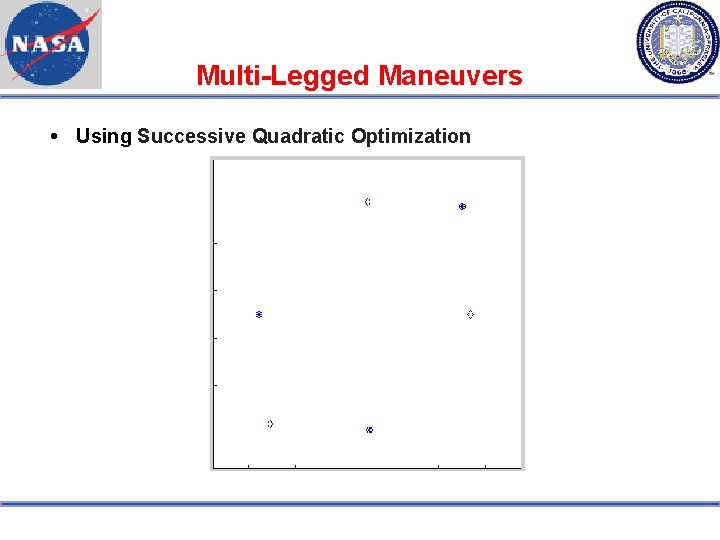
Multi-Legged Maneuvers Using Successive Quadratic Optimization

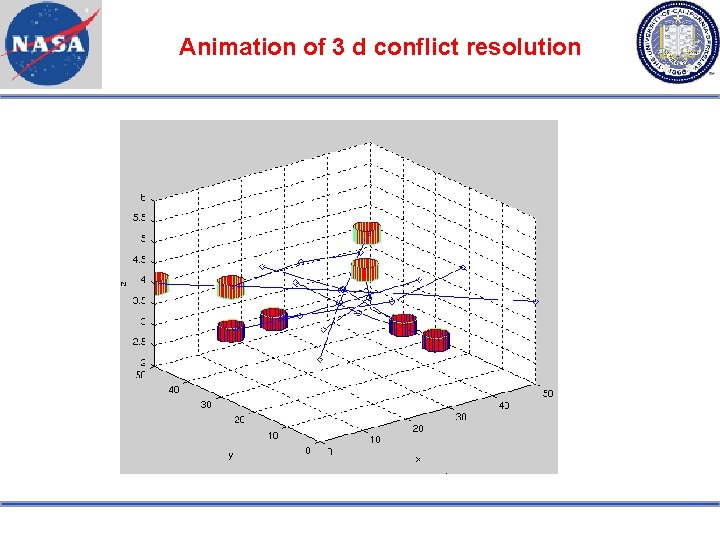
Animation of 3 d conflict resolution

Collision Avoidance and Tracking using Nonlinear Model Predictive Tracking • Five helicopters given a straight line trajectory that will lead to a collision. • Each vehicle can detect other vehicles position within the sensing/communication region. • Each vehicle dynamically replans safe trajectory under input/state constraints in real-time.

Hybrid Systems Modeling, Analysis, Control Datta Godbole, John Lygeros, Claire Tomlin, Gerardo Lafferiere, George Pappas, John Koo Jianghai Hu, Rene Vidal, Shawn Shaffert, Jun Zhang, Slobodan Simic, Kalle Johansson, Maria Prandini (with the interference of) Shankar Sastry

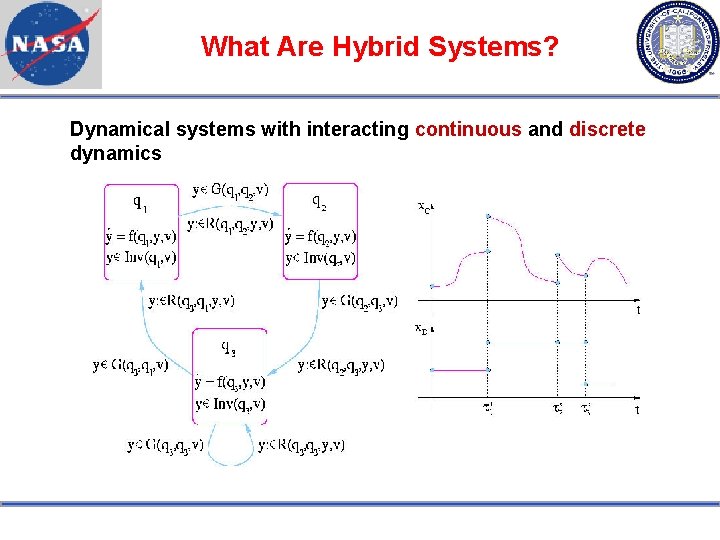
What Are Hybrid Systems? Dynamical systems with interacting continuous and discrete dynamics

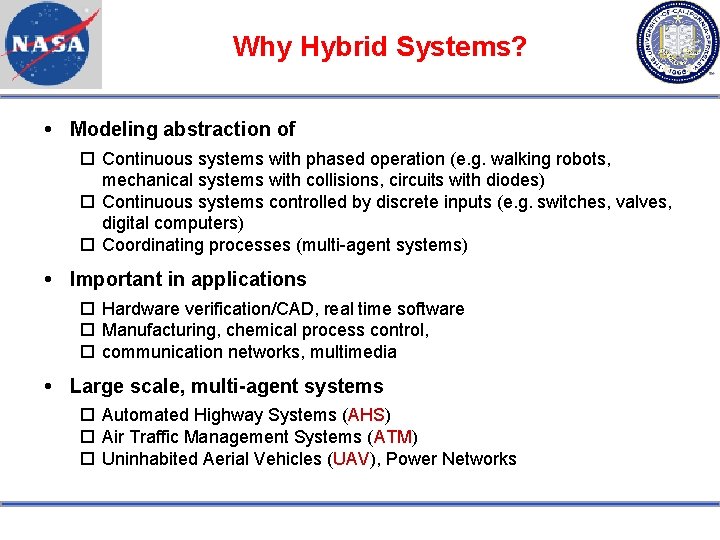
Why Hybrid Systems? Modeling abstraction of Continuous systems with phased operation (e. g. walking robots, mechanical systems with collisions, circuits with diodes) Continuous systems controlled by discrete inputs (e. g. switches, valves, digital computers) Coordinating processes (multi-agent systems) Important in applications Hardware verification/CAD, real time software Manufacturing, chemical process control, communication networks, multimedia Large scale, multi-agent systems Automated Highway Systems (AHS) Air Traffic Management Systems (ATM) Uninhabited Aerial Vehicles (UAV), Power Networks

Control Challenges Large number of semiautonomous agents Coordinate to Make efficient use of common resource Achieve a common goal Individual agents have various modes of operation Agents optimize locally, coordinate to resolve conflicts System architecture is hierarchical and distributed Safety critical systems Challenge: Develop models, analysis, and synthesis tools for designing and verifying the safety of multi-agent systems

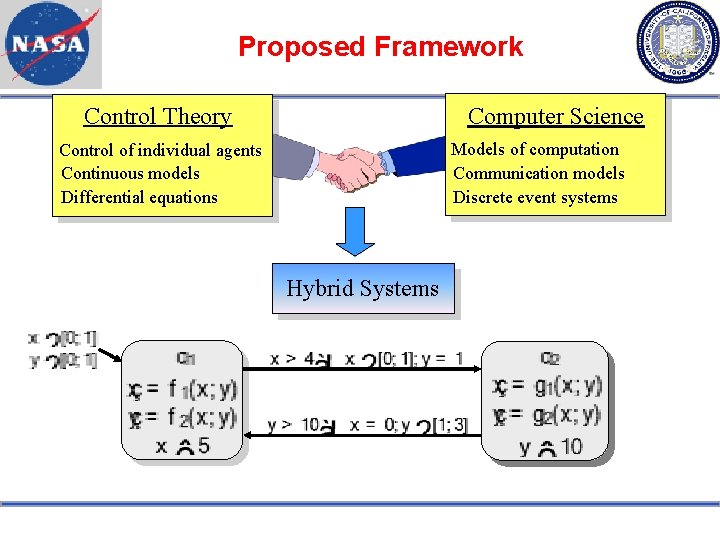
Proposed Framework Control Theory Computer Science Models of computation Communication models Discrete event systems Control of individual agents Continuous models Differential equations Hybrid Systems

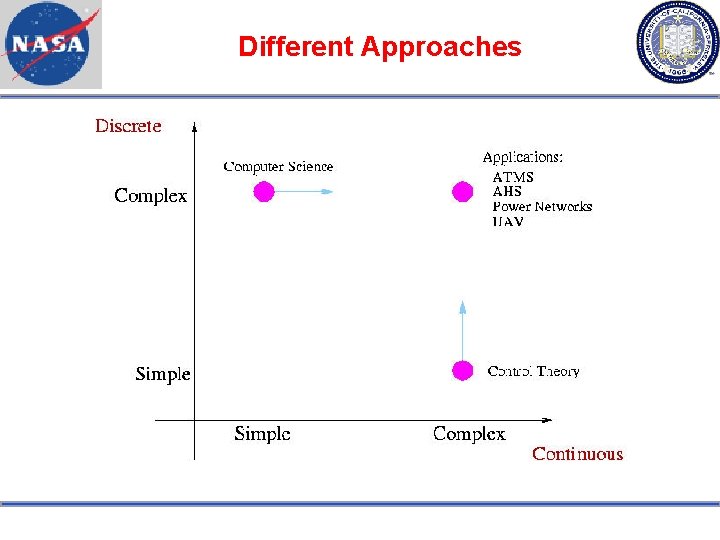
Different Approaches

Air Traffic Management Systems Studied by NEXTOR and NASA Increased demand for air travel Higher aircraft density/operator workload Severe degradation in adverse conditions High business volume Technological advances: Guidance, Navigation & Control GPS, advanced avionics, on-board electronics Communication capabilities Air Traffic Controller (ATC) computation capabilities Greater demand possibilities for automation Operator assistance Decentralization Free flight

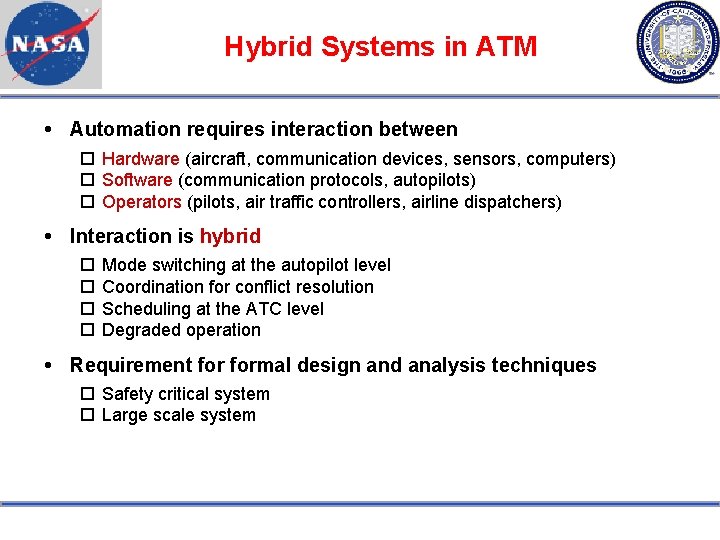
Hybrid Systems in ATM Automation requires interaction between Hardware (aircraft, communication devices, sensors, computers) Software (communication protocols, autopilots) Operators (pilots, air traffic controllers, airline dispatchers) Interaction is hybrid Mode switching at the autopilot level Coordination for conflict resolution Scheduling at the ATC level Degraded operation Requirement formal design and analysis techniques Safety critical system Large scale system

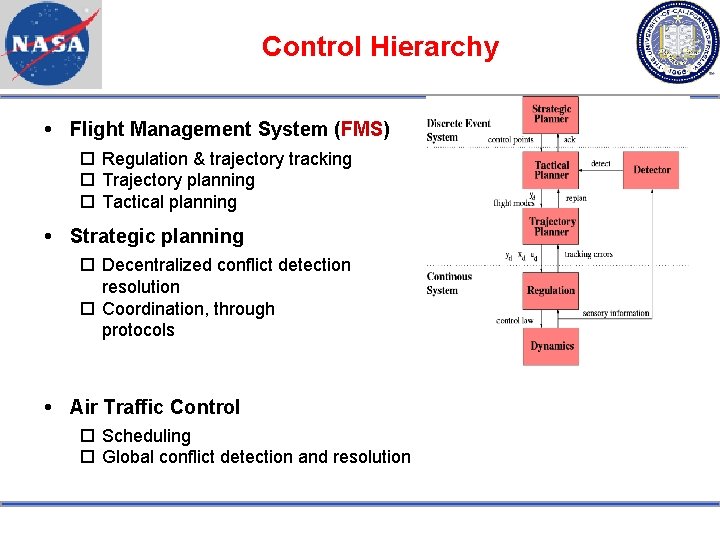
Control Hierarchy Flight Management System (FMS) Regulation & trajectory tracking Trajectory planning Tactical planning Strategic planning Decentralized conflict detection resolution Coordination, through protocols Air Traffic Control Scheduling Global conflict detection and resolution and communication

Hybrid Research Issues Hierarchy design FMS level Mode switching Aerodynamic envelope protection Strategic level Design of conflict resolution maneuvers Implementation by communication protocols ATC level Scheduling algorithms (e. g. for take-offs and landings) Global conflict resolution algorithms Software verification Probabilistic analysis and degraded modes of operation

Softwalls Adam Cataldo, Edward Lee and group

Outline Soft Walls Overview Current Research Reachability Approach Simulation Interface Crazyboard Current Results Controller for Simplified Dynamics Model

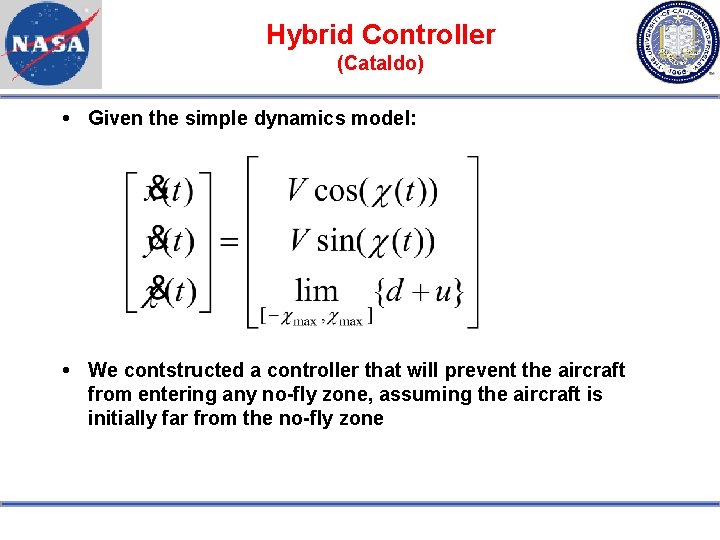
Hybrid Controller (Cataldo) Given the simple dynamics model: We contstructed a controller that will prevent the aircraft from entering any no-fly zone, assuming the aircraft is initially far from the no-fly zone

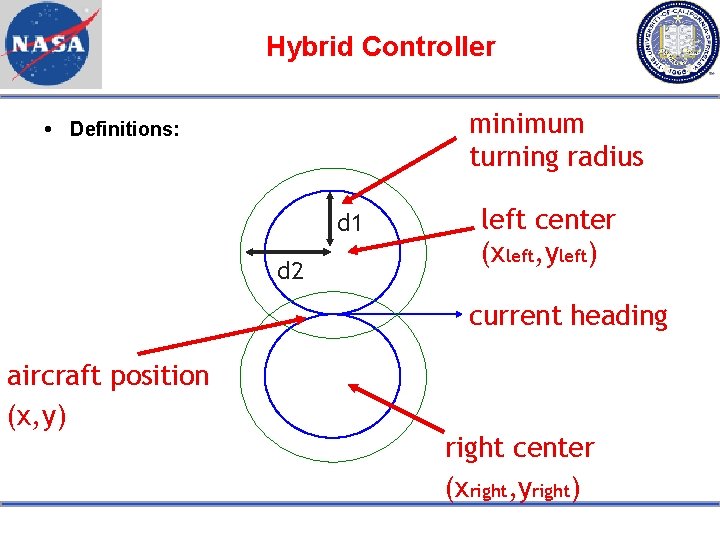
Hybrid Controller minimum turning radius Definitions: d 1 d 2 left center (xleft, yleft) current heading aircraft position (x, y) right center (xright, yright)

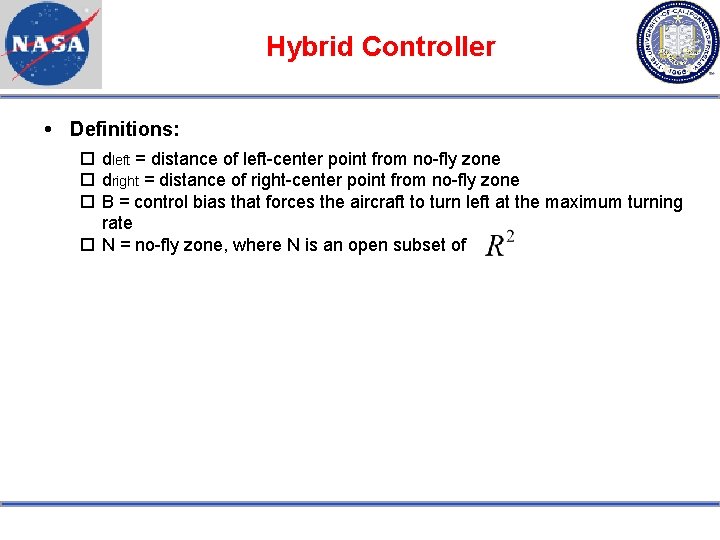
Hybrid Controller Definitions: dleft = distance of left-center point from no-fly zone dright = distance of right-center point from no-fly zone B = control bias that forces the aircraft to turn left at the maximum turning rate N = no-fly zone, where N is an open subset of

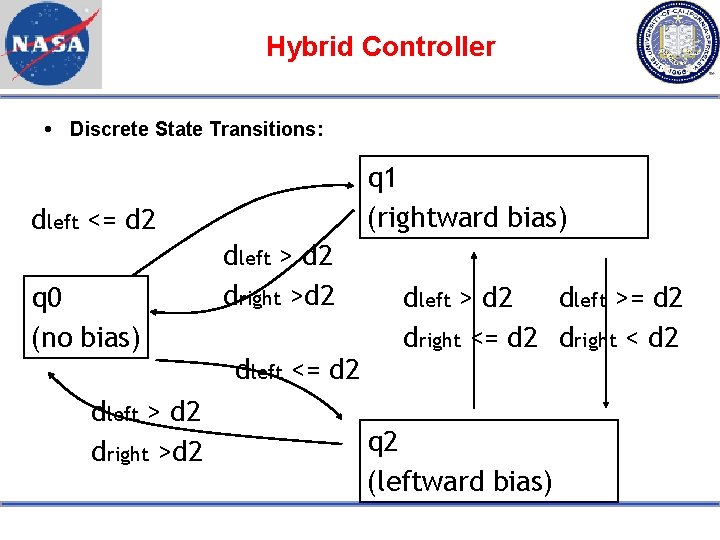
Hybrid Controller Discrete State Transitions: q 1 (rightward bias) dleft <= d 2 q 0 (no bias) dleft > d 2 dright >d 2 dleft <= d 2 dleft >= d 2 dright < d 2 q 2 (leftward bias)

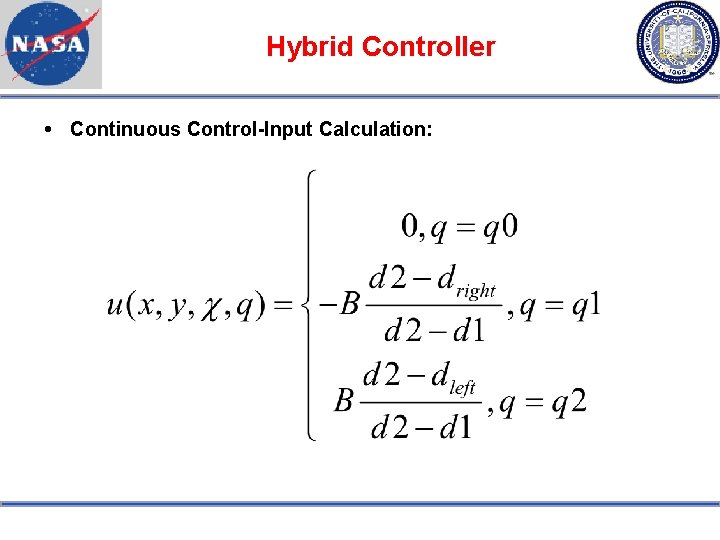
Hybrid Controller Continuous Control-Input Calculation:

Hybrid Controller Thereom: Given N, if dleft(t 0) > d 2, and dright(t 0) > d 2, then using this hybrid controller, (x, y) N t > t 0 That is, this hybrid controller gaurantees the aircraft never enters the no-fly zone

Controller Impracticallity Because this controller may capture the aircraft (if dleft(t) = d 1 or dright(t) = d 1), this algorithm is impractical. However, it may work without capturing the aircraft, as long as the control bias never saturates.