THE POWER OF PAIRINGS TOWARDS STANDARD MODEL SECURITY















- Slides: 37

THE POWER OF PAIRINGS TOWARDS STANDARD MODEL SECURITY Pairings, IBE, IND-CCA-secure encryption, authentication

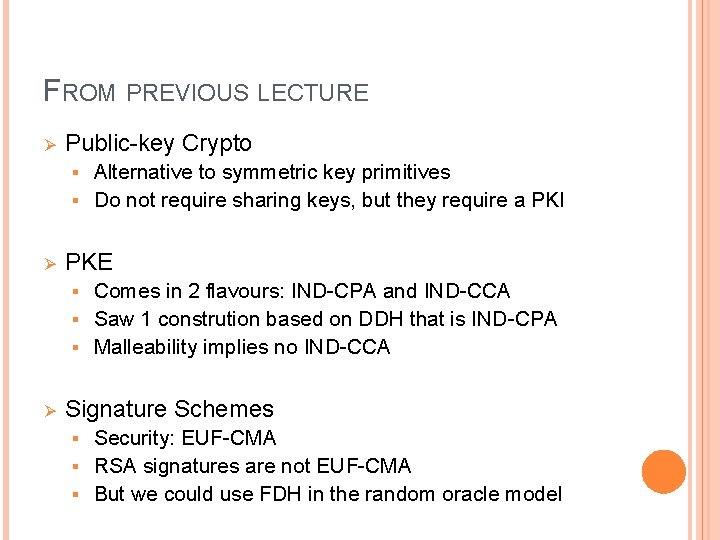
FROM PREVIOUS LECTURE Ø Public-key Crypto Alternative to symmetric key primitives § Do not require sharing keys, but they require a PKI § Ø PKE Comes in 2 flavours: IND-CPA and IND-CCA § Saw 1 constrution based on DDH that is IND-CPA § Malleability implies no IND-CCA § Ø Signature Schemes Security: EUF-CMA § RSA signatures are not EUF-CMA § But we could use FDH in the random oracle model §

PART I PAIRINGS

PAIRINGS IN GENERAL Ø

PAIRINGS IN CRYPTOGRAPHY Ø Ø Ø Usually computed on elliptic curves There are different types, depending on how the pairing is constructed Security depends on type and on something called “embedding degree” Mostly defined with elements from additive subgroups (rather than multiplicative ones), but we will keep the multiplicative notation We will not cover specifics in this course If you’re interested, you could read: Lawrence C. Washington: ‘Elliptic curves: Number theory and cryptography’ §

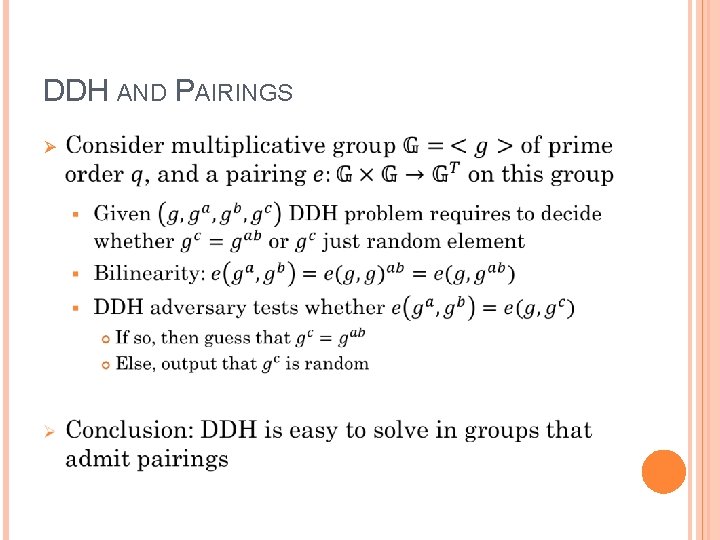
DDH AND PAIRINGS Ø

HARD PROBLEMS WITH PAIRINGS Ø

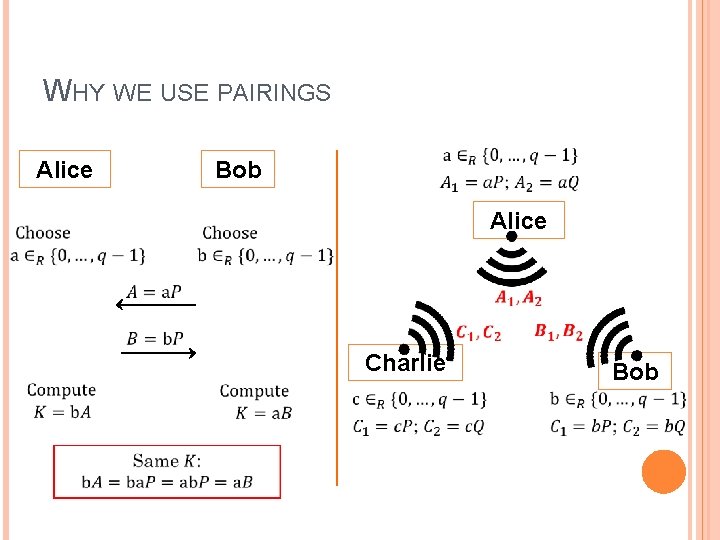
WHY WE USE PAIRINGS Alice Bob Alice Charlie Bob

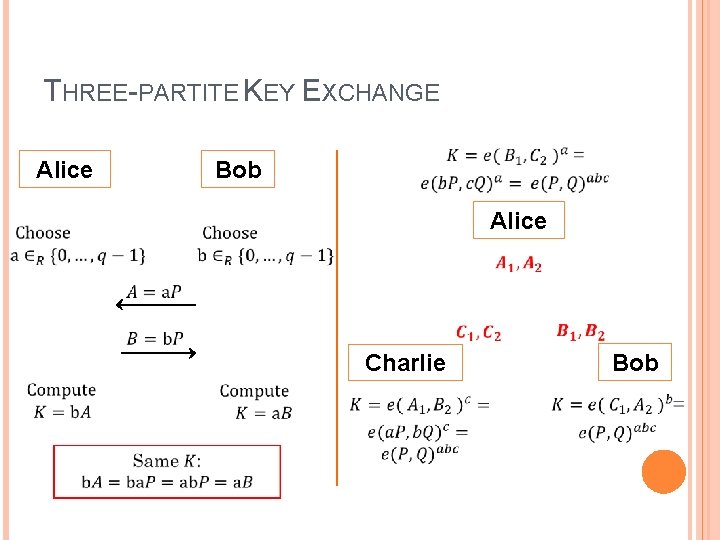
THREE-PARTITE KEY EXCHANGE Alice Bob Alice Bob Charlie

PART II IDENTITY-BASED ENCRYPTION

PKE AND IBE Ø PKE: Alice has a private key for decryption § Bob (and everyone else) has a public key for encryption to Alice § Problem of certification: whose key is that? § Ø IBE: Bob has (a function of) Alice’s identity (name, email address, social security number) as a PK § Alice can derive a secret key from that § Bob encrypts with Alice’s identity, so only she can decrypt §

IBE SYNTAX Ø

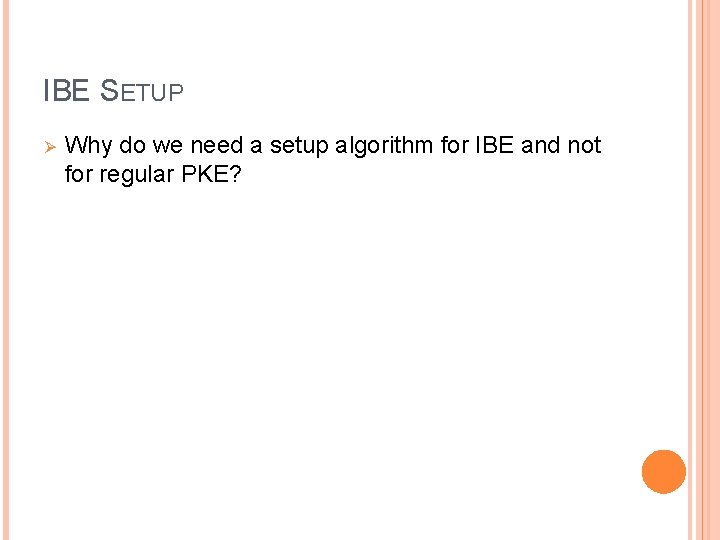
IBE SETUP Ø Why do we need a setup algorithm for IBE and not for regular PKE?

IBE SETUP Ø

IBE SETUP Ø

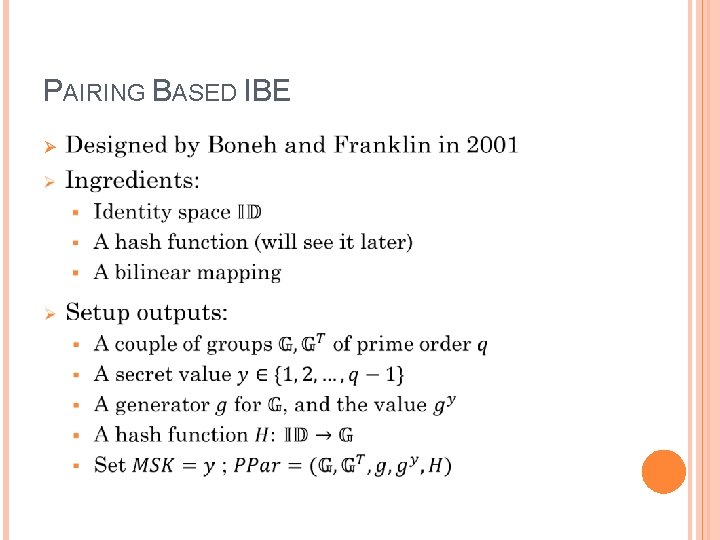
PAIRING BASED IBE Ø

BONEH-FRANKLIN IBE Ø

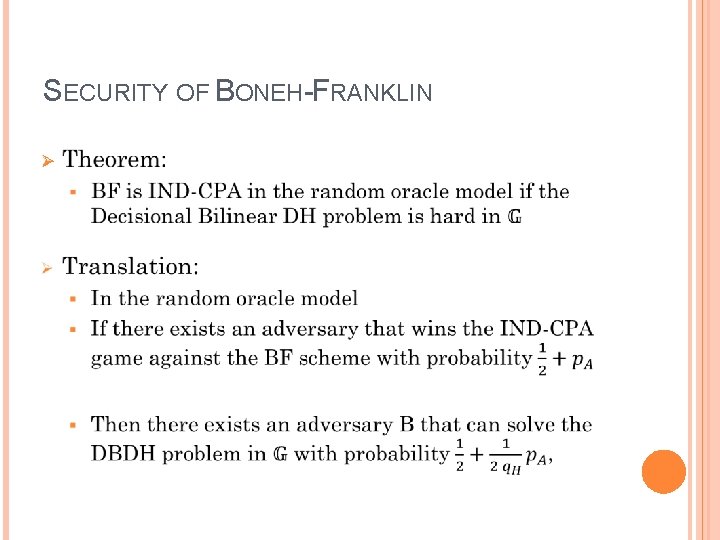
SECURITY OF BONEH-FRANKLIN Ø

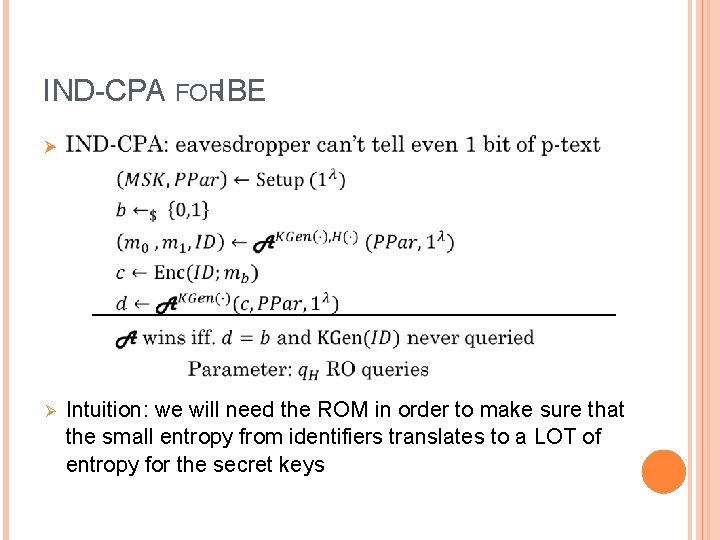
IND-CPA FORIBE Ø Ø Intuition: we will need the ROM in order to make sure that the small entropy from identifiers translates to a LOT of entropy for the secret keys

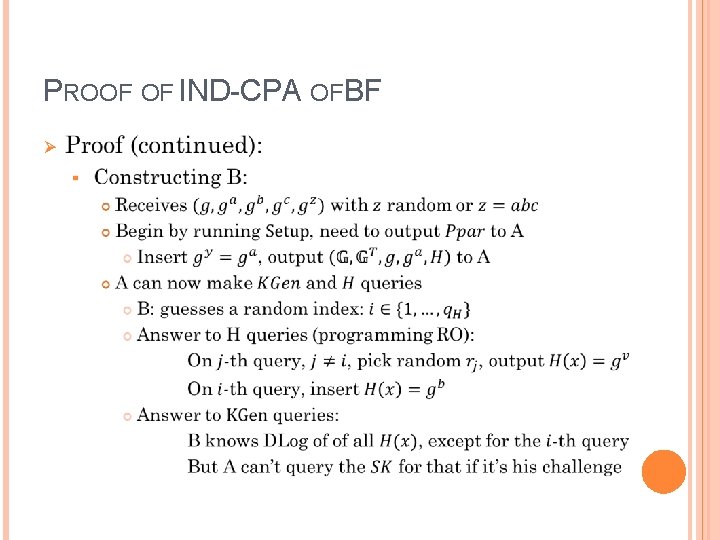
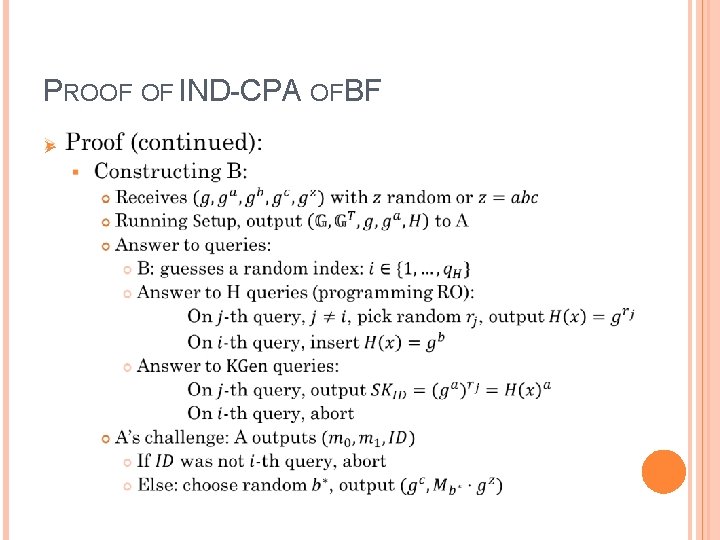
PROOF OF IND-CPA OF BF Ø

PROOF OF IND-CPA OF BF Ø

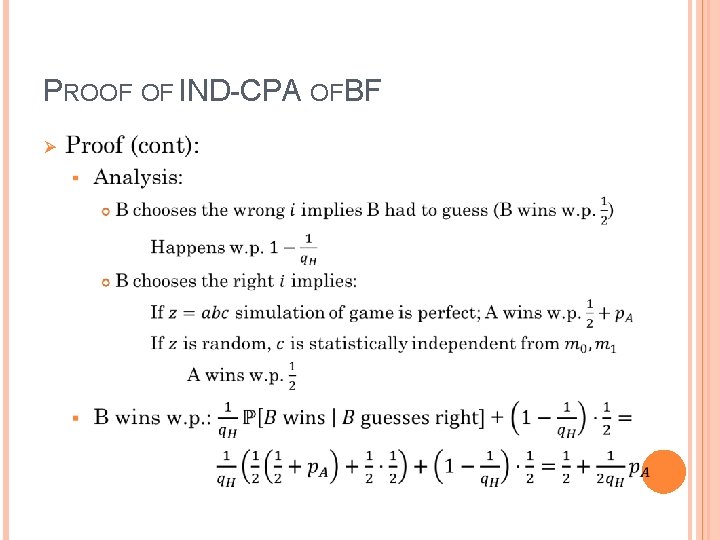
PROOF OF IND-CPA OF BF Ø

PROOF OF IND-CPA OF BF Ø

PROOF OF IND-CPA OF BF Ø

PART II THE USES OF IBE

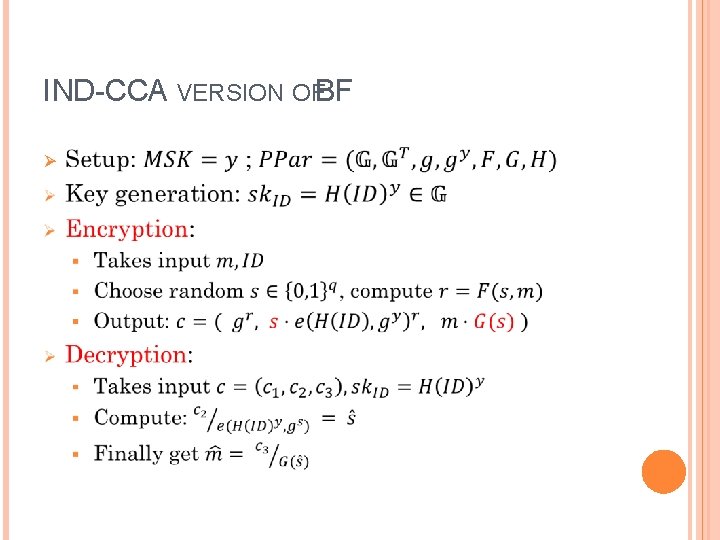
FUJISAKI-OKAMOTO Ø Designed a “compiler”: Input: a PKE scheme that’s IND-CPA secure § Output: a PKE scheme that’s IND-CCA secure § Ø Boneh and Franklin used it on their IND-CPA scheme, and obtained an IND-CCA one Ø We won’t look at the generic compiler, but let’s see the IND-CCA version of BF! Ø For interested readers, see: Fujisaki, Okamoto “Secure integration of asymmetric and symmetric encryption schemes”, Crypto 99

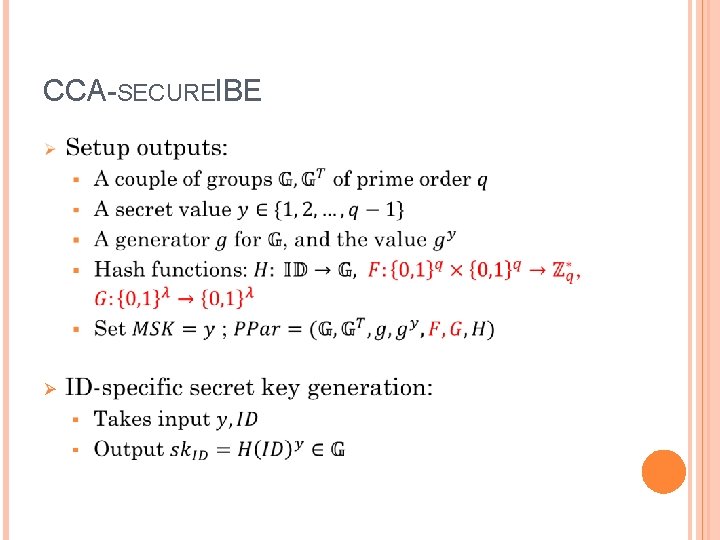
CCA-SECUREI BE Ø

IND-CCA VERSION OFBF Ø

SECURITY STATEMENT Ø

SIGNATURES IN THE STANDARD MODEL Ø So far we’ve seen: IND-CPA-secure encryption in the standard model (no ROs required) – El. Gamal § IND-CPA-secure IBE in the ROM – Boneh-Franklin § IND-CCA-secure IBE in the ROM – BF + FO § § Ø EUF-CMA signatures in the ROM using Full-domain hashing (FDH) Let’s see now: § (strongly) EUF-CMA signatures without random oracles, using pairings

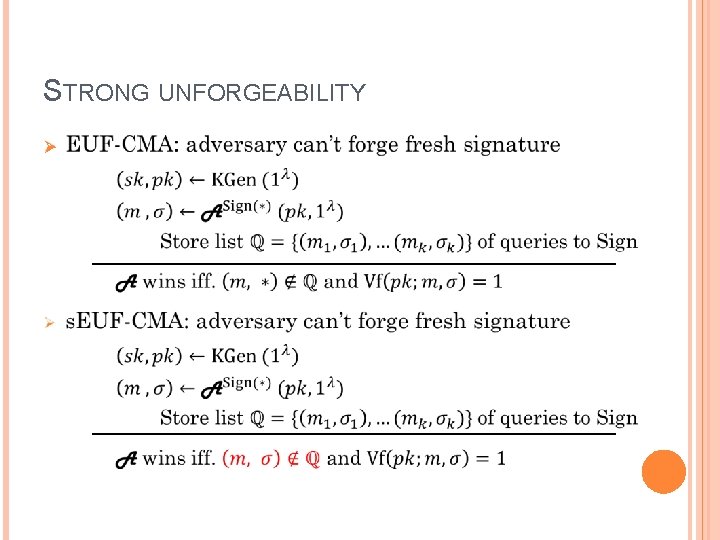
STRONG UNFORGEABILITY Ø

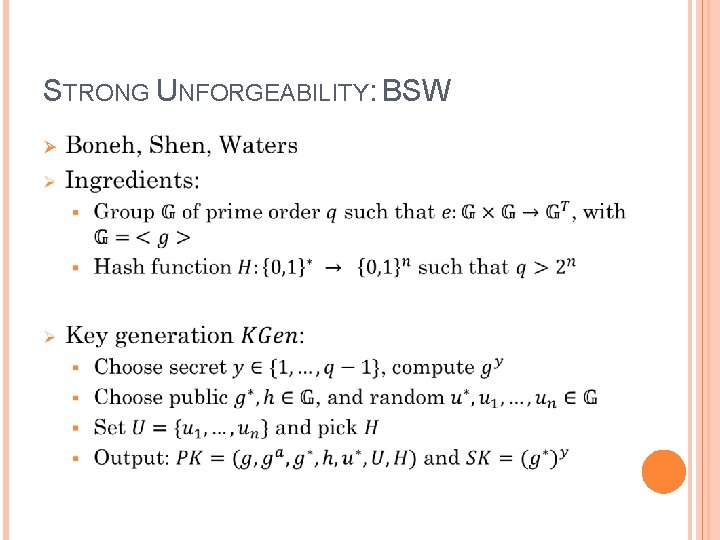
STRONG UNFORGEABILITY: BSW Ø

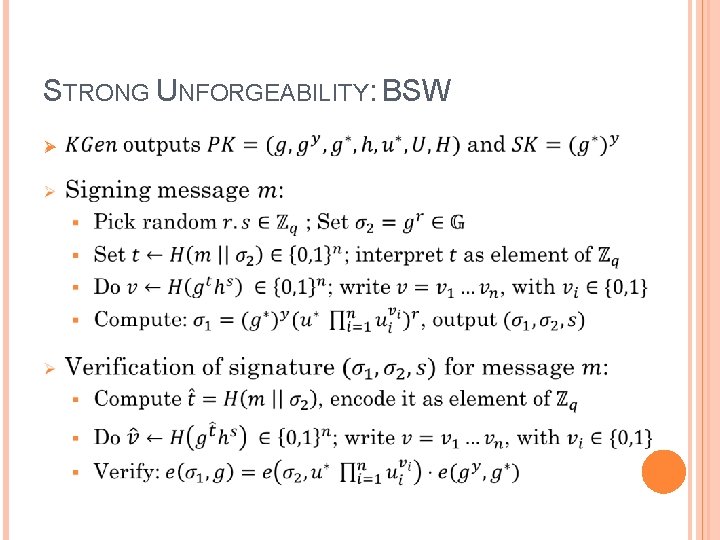
STRONG UNFORGEABILITY: BSW Ø

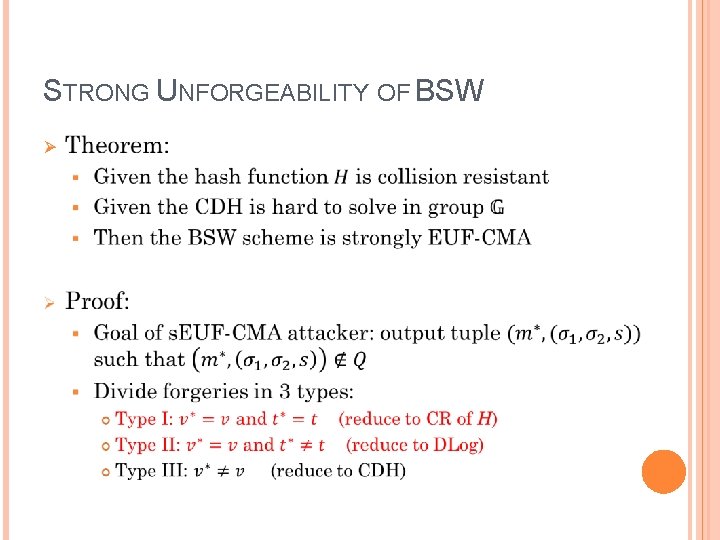
STRONG UNFORGEABILITY OF BSW Ø

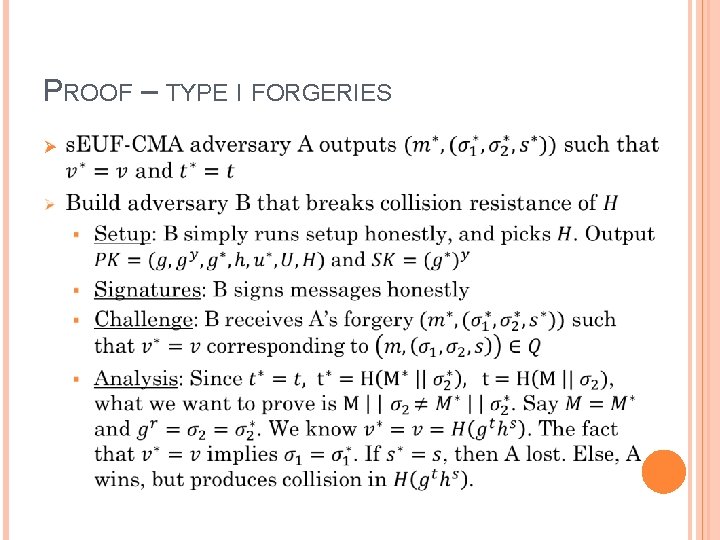
PROOF – TYPE I FORGERIES Ø

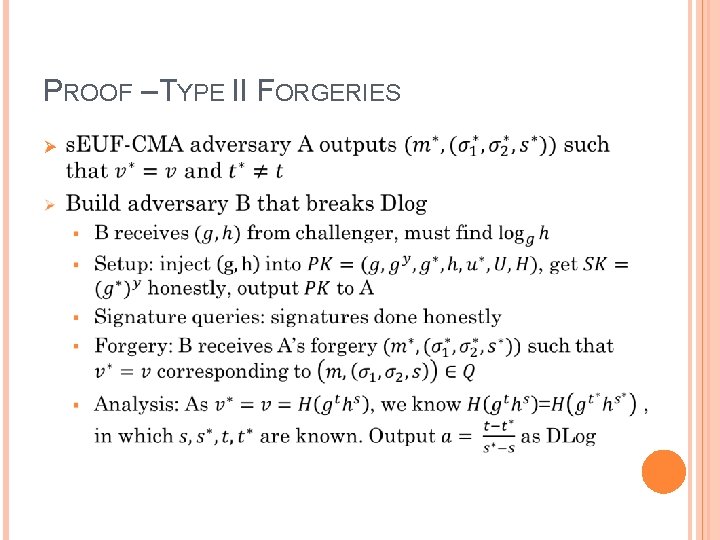
PROOF – TYPE II FORGERIES Ø

PROOF – TYPE III FORGERIES Ø Ø We will not cover them here. Proof is more complicated, and relies on a transformation of EUF-CMA to s. EUF-CMA
 Song and poem pairings
Song and poem pairings Private secuirty
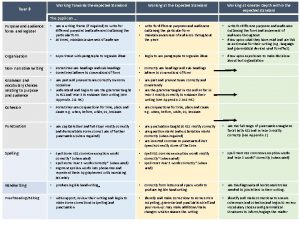
Private secuirty Working towards the expected standard meaning
Working towards the expected standard meaning Triangle of power
Triangle of power Visa international security model
Visa international security model Information security
Information security Power model vs exponential model
Power model vs exponential model Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Glasgow thang điểm
Glasgow thang điểm Chúa sống lại
Chúa sống lại Các môn thể thao bắt đầu bằng từ đua
Các môn thể thao bắt đầu bằng từ đua Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Cong thức tính động năng
Cong thức tính động năng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư tọa độ 5x5
Mật thư tọa độ 5x5 101012 bằng
101012 bằng độ dài liên kết
độ dài liên kết Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thơ thất ngôn tứ tuyệt đường luật
Thơ thất ngôn tứ tuyệt đường luật Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng nó xinh thế chỉ nói điều hay thôi
Cái miệng nó xinh thế chỉ nói điều hay thôi Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Thế nào là sự mỏi cơ
Thế nào là sự mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Thứ tự các dấu thăng giáng ở hóa biểu
Thứ tự các dấu thăng giáng ở hóa biểu Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Phối cảnh
Phối cảnh Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là