CSC 482582 Computer Security Classical Cryptography CSC 482582



























- Slides: 86

CSC 482/582: Computer Security Classical Cryptography CSC 482/582: Computer Security

Topics 1. 2. 3. 4. 5. 6. 7. 8. 9. Modular Arithmetic Review What is Cryptography? Substitution Ciphers Cryptanalysis: frequency analysis Stream Ciphers Block Ciphers DES Block Cipher Modes AES CSC 482/582: Computer Security

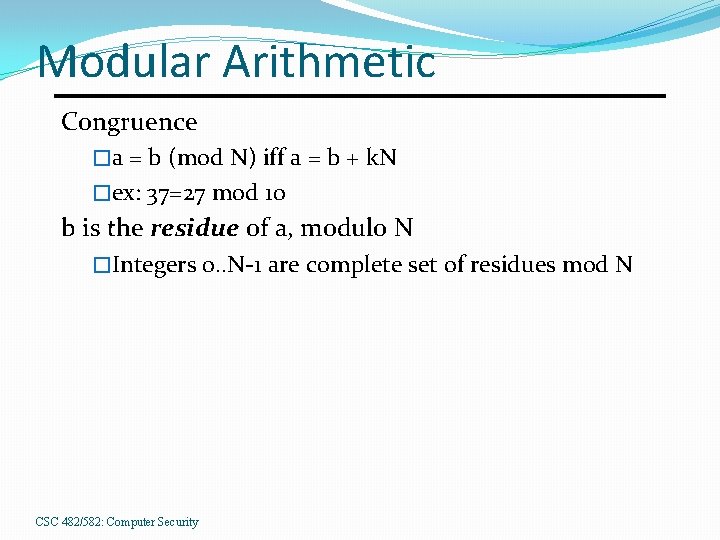
Modular Arithmetic Congruence �a = b (mod N) iff a = b + k. N �ex: 37=27 mod 10 b is the residue of a, modulo N �Integers 0. . N-1 are complete set of residues mod N CSC 482/582: Computer Security

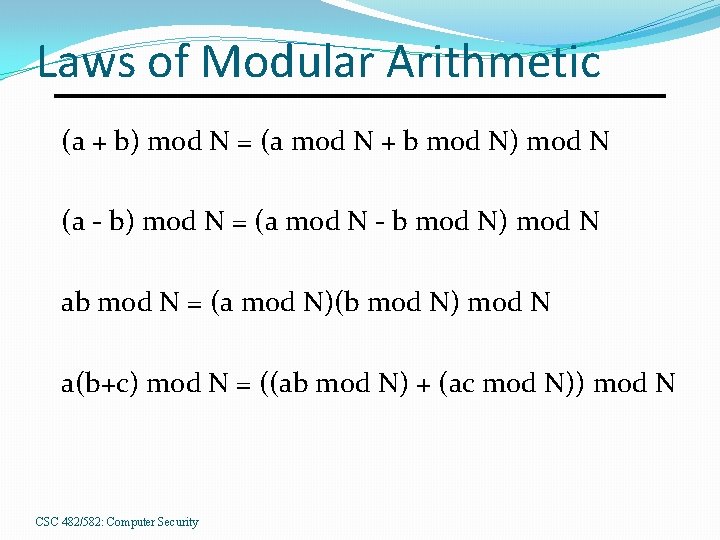
Laws of Modular Arithmetic (a + b) mod N = (a mod N + b mod N) mod N (a - b) mod N = (a mod N - b mod N) mod N ab mod N = (a mod N)(b mod N) mod N a(b+c) mod N = ((ab mod N) + (ac mod N)) mod N CSC 482/582: Computer Security

What is Cryptography? Cryptography: The art and science of keeping messages secure. Cryptanalysis: the art and science of decrypting messages. Cryptology: cryptography + cryptanalysis CSC 482/582: Computer Security

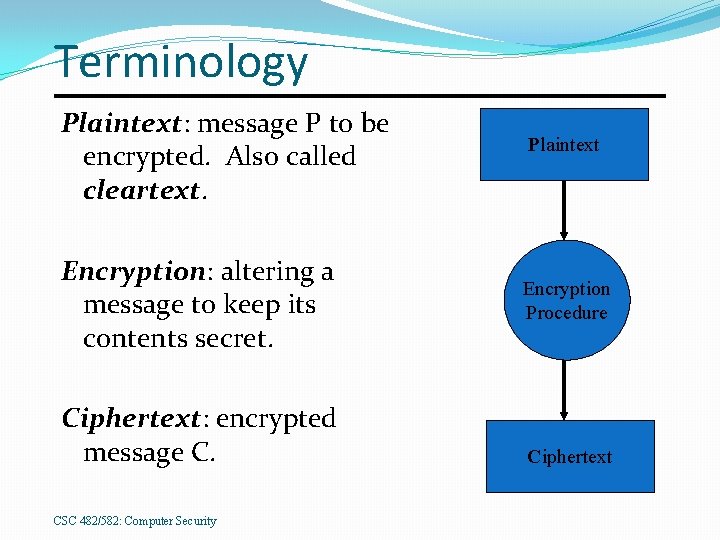
Terminology Plaintext: message P to be encrypted. Also called cleartext. Encryption: altering a message to keep its contents secret. Ciphertext: encrypted message C. CSC 482/582: Computer Security Plaintext Encryption Procedure Ciphertext

Early Cryptography Egyptian hieroglyphics ~ 2000 B. C. E. �Cryptic tomb inscriptions for regality. Spartan skytale cipher ~ 500 B. C. E. �Wrapped thin sheet of papyrus around staff. �Messages written down length of staff. �Decrypted by wrapped around = diameter staff. Cæsar cipher ~ 50 B. C. E. �Simple alphabetic substitution cipher. al-Kindi ~ 850 C. E. �Cryptanalysis using letter frequencies. 7

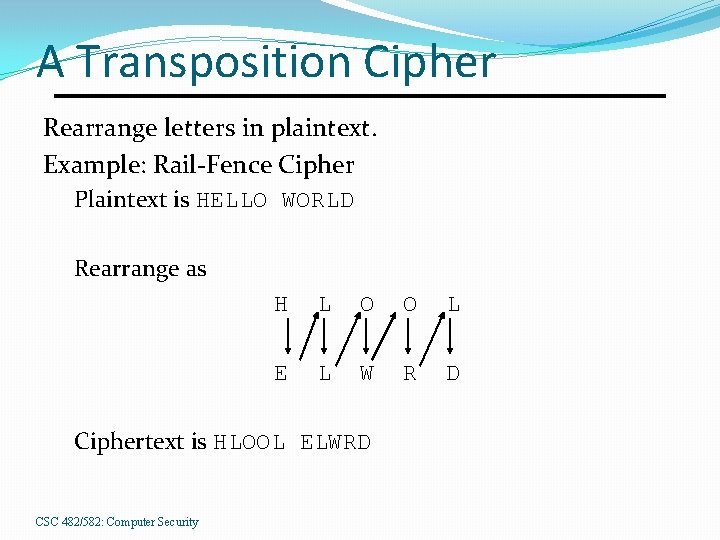
A Transposition Cipher Rearrange letters in plaintext. Example: Rail-Fence Cipher Plaintext is HELLO WORLD Rearrange as H L O O L E L W R D Ciphertext is HLOOL ELWRD CSC 482/582: Computer Security

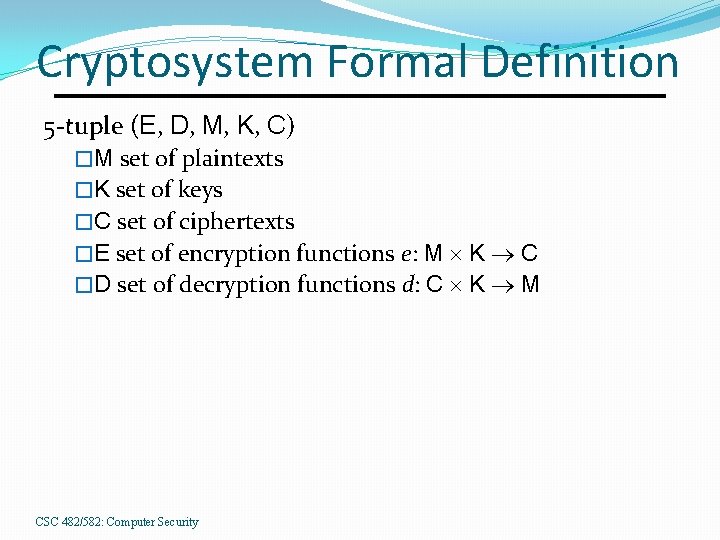
Cryptosystem Formal Definition 5 -tuple (E, D, M, K, C) �M set of plaintexts �K set of keys �C set of ciphertexts �E set of encryption functions e: M K C �D set of decryption functions d: C K M CSC 482/582: Computer Security

Cæsar cipher Letter shifting cipher (A=>D, B=>E, C=>F, … 5 -tuple M = { all sequences of letters } K = { i | i is an integer and 0 ≤ i ≤ 25 } E = { Ek | k K and for all letters m, Ek(m) = (m + k) mod 26 } D = { Dk | k K and for all letters c, Dk(c) = (26 + c – k) mod 26 } C=M History: Cæsar’s key was 3. CSC 482/582: Computer Security

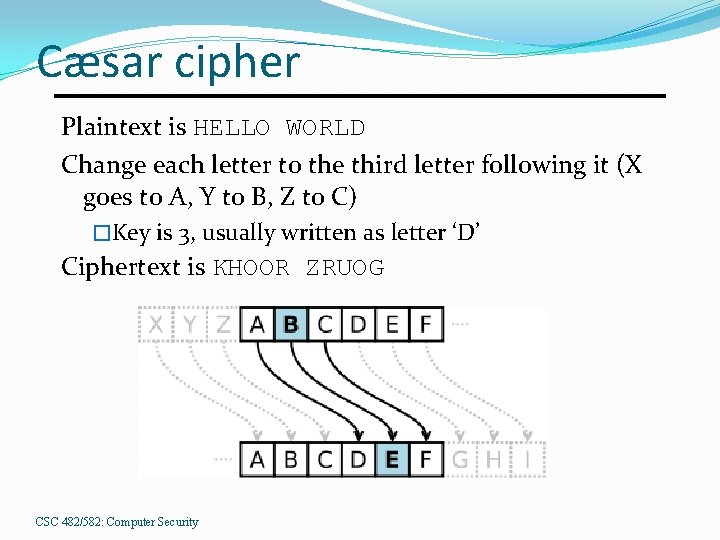
Cæsar cipher Plaintext is HELLO WORLD Change each letter to the third letter following it (X goes to A, Y to B, Z to C) �Key is 3, usually written as letter ‘D’ Ciphertext is KHOOR ZRUOG CSC 482/582: Computer Security

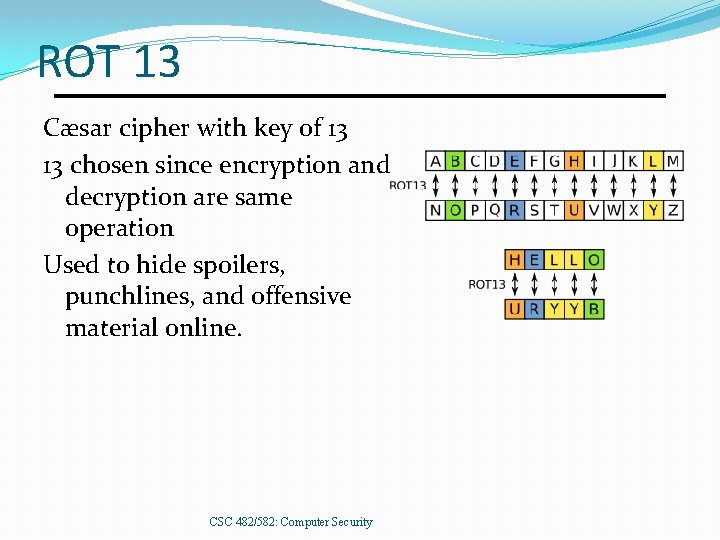
ROT 13 Cæsar cipher with key of 13 13 chosen since encryption and decryption are same operation Used to hide spoilers, punchlines, and offensive material online. CSC 482/582: Computer Security

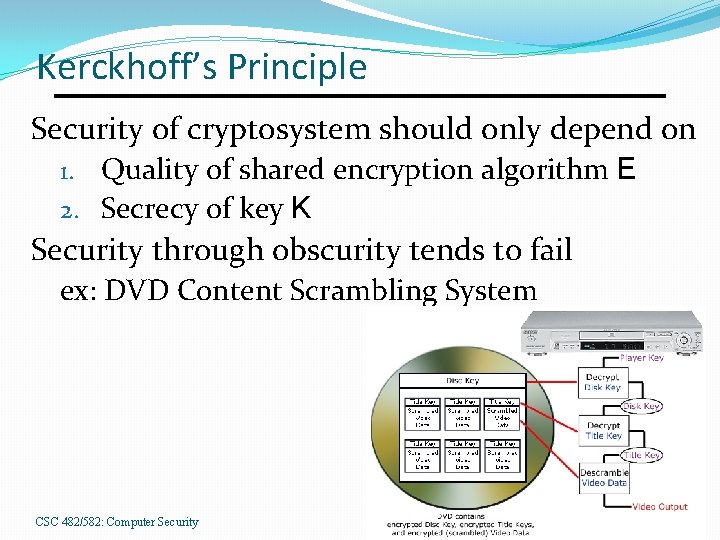
Kerckhoff’s Principle Security of cryptosystem should only depend on 1. Quality of shared encryption algorithm E 2. Secrecy of key K Security through obscurity tends to fail ex: DVD Content Scrambling System CSC 482/582: Computer Security

Cryptanalysis Goals 1. Decrypt a given message. 2. Recover encryption key. Threat models vary based on 1. Type of information available to adversary 2. Interaction with cryptosystem. CSC 482/582: Computer Security

Cryptanalysis Threat Models ciphertext only: adversary has only ciphertext; goal is to find plaintext, possibly key. known plaintext: adversary has ciphertext, corresponding plaintext; goal is to find key. chosen plaintext: adversary may supply plaintexts and obtain corresponding ciphertext; goal is to find key. CSC 482/582: Computer Security

Brute Force Attack Exhaustive search of keyspace by decrypting ciphertext C with all possible keys K. �Must determine if DK(C) is a likely plaintext �Requires some knowledge of format (language, doc type) For N possible keys, �Worst case is N decryptions. �Mean case is N/2 decryptions. Example: DES has 56 -bit keys �Average time to find key is 255 decryptions. CSC 482/582: Computer Security

Is 128 bits enough? 128 -bit keyspace permits 2128 keys � 340, 282, 366, 920, 938, 463, 374, 607, 431, 768, 211, 456 or � 3. 4 x 1038 keys Cracking 1 trillion (1012) keys per second requires � 3. 4 x 1026 seconds or � 1. 08 x 1019 years Cracking 1 trillion keys per second on 1 billion CPUs �requires 1. 08 x 1010 years = 10. 8 billion years CSC 482/582: Computer Security

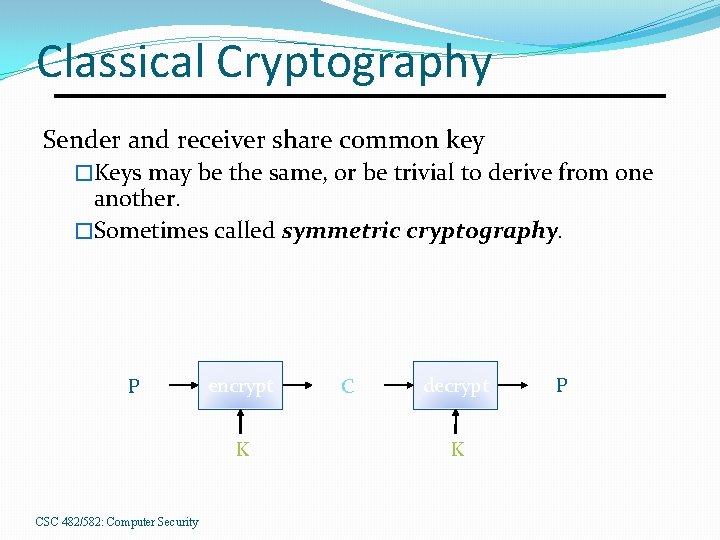
Classical Cryptography Sender and receiver share common key �Keys may be the same, or be trivial to derive from one another. �Sometimes called symmetric cryptography. P encrypt K CSC 482/582: Computer Security C decrypt K P

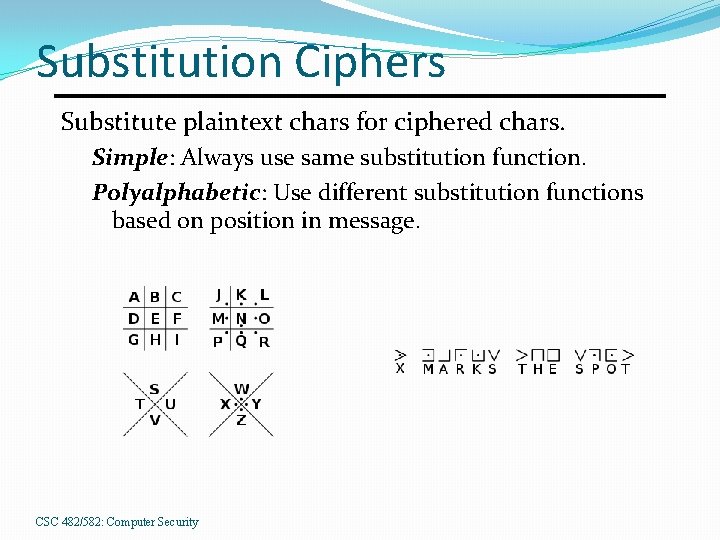
Substitution Ciphers Substitute plaintext chars for ciphered chars. Simple: Always use same substitution function. Polyalphabetic: Use different substitution functions based on position in message. CSC 482/582: Computer Security

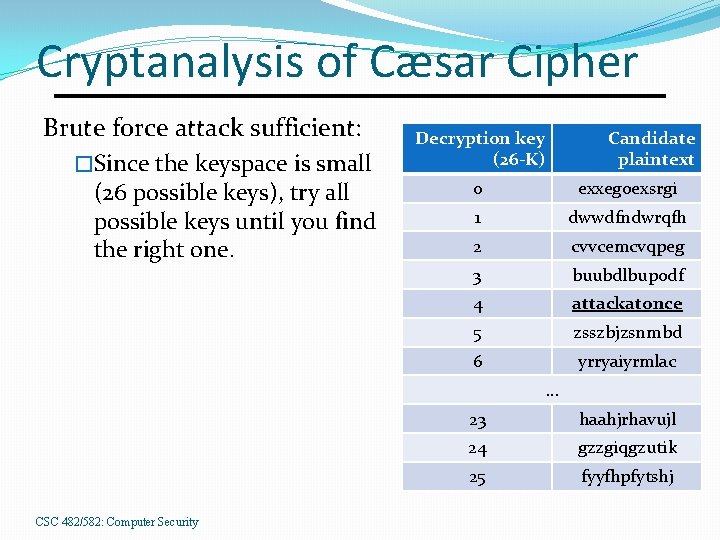
Cryptanalysis of Cæsar Cipher Brute force attack sufficient: �Since the keyspace is small (26 possible keys), try all possible keys until you find the right one. Decryption key (26 -K) Candidate plaintext 0 exxegoexsrgi 1 dwwdfndwrqfh 2 cvvcemcvqpeg 3 buubdlbupodf 4 attackatonce 5 zsszbjzsnmbd 6 yrryaiyrmlac. . . CSC 482/582: Computer Security 23 haahjrhavujl 24 gzzgiqgzutik 25 fyyfhpfytshj

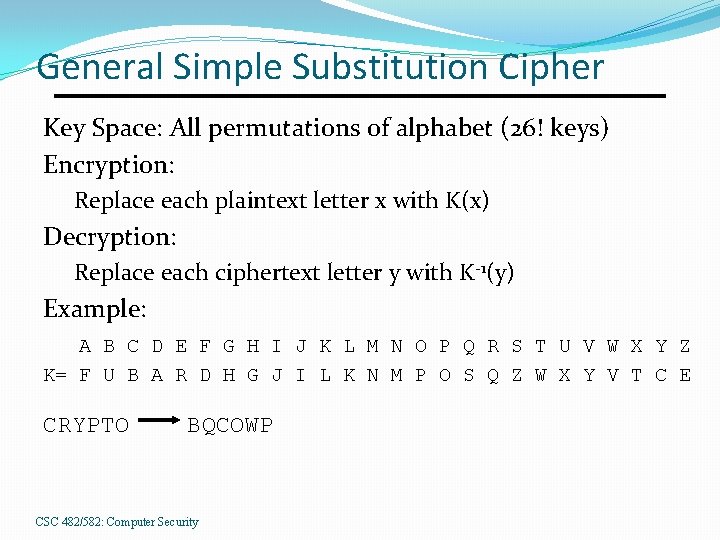
General Simple Substitution Cipher Key Space: All permutations of alphabet (26! keys) Encryption: Replace each plaintext letter x with K(x) Decryption: Replace each ciphertext letter y with K-1(y) Example: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z K= F U B A R D H G J I L K N M P O S Q Z W X Y V T C E CRYPTO BQCOWP CSC 482/582: Computer Security

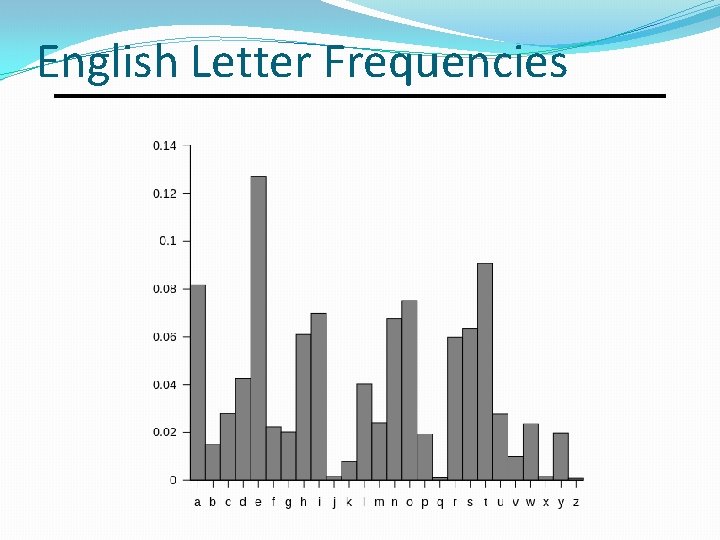
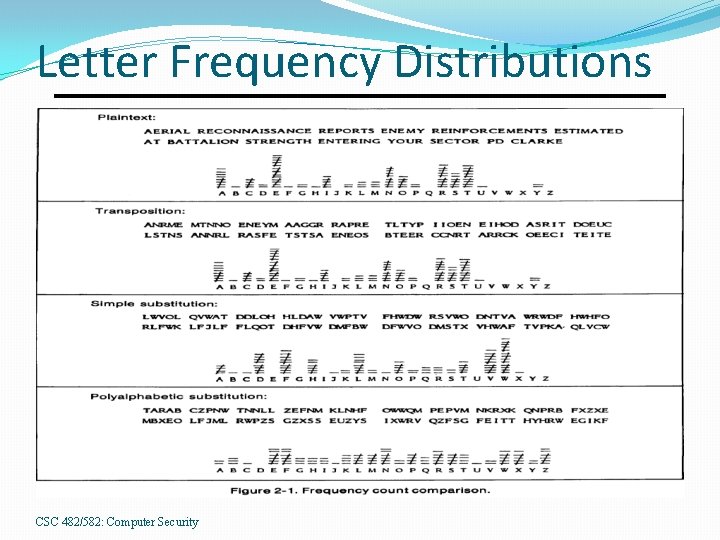
General Simple Substitution Cryptanalysis Exhaustive search impossible �Key space size is 26! =~ 4 x 1026 �Historically thought to be unbreakable. However, languages have different frequencies of �letters �digraphs (groups of 2 letters) �trigraphs (groups of 3 letters) �etc. Simple substitution ciphers preserve letter frequencies. CSC 482/582: Computer Security

English Letter Frequencies

Additional Frequency Features Digraph frequencies �Common digraphs: EN, RE, ER, NT Trigraph frequencies �Common trigraphs: THE, AND, ING �Digraph and trigraph tables can be found at http: //www. sttmedia. com/syllablefrequencyenglish The letter Q is followed only by U.

Countering Frequency Analysis Nulls �Insert additional symbols (numbers) which have no meaning in random places. Idiosyncratic spellings �n 0 r. M 4 L s 34 r. Ch �Hacker speak: www. google. com/webhp? hl=xx-hacker Homophonic substitution �Each letter has multiple substitutions. Techniques increase difficulty but don’t make impossible. CSC 482/582: Computer Security

Countering Frequency Analysis Primary weakness of simple substitution: �Each ciphertext letter corresponds to only one letter of plaintext. Solution: polyalphabetic substitution �Use multiple cipher alphabets. �Switch between cipher alphabets from character to character in the plaintext. CSC 482/582: Computer Security

Letter Frequency Distributions CSC 482/582: Computer Security

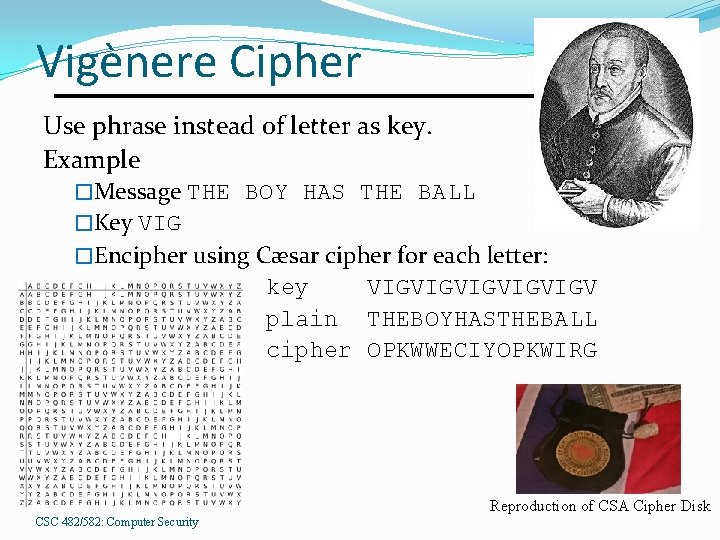
Vigènere Cipher Use phrase instead of letter as key. Example �Message THE BOY HAS THE BALL �Key VIG �Encipher using Cæsar cipher for each letter: key VIGVIGVIGV plain THEBOYHASTHEBALL cipher OPKWWECIYOPKWIRG Reproduction of CSA Cipher Disk CSC 482/582: Computer Security

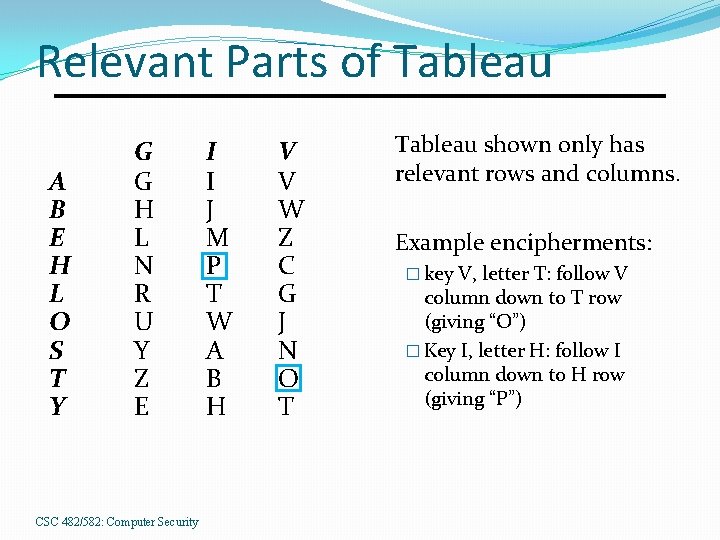
Relevant Parts of Tableau A B E H L O S T Y G G H L N R U Y Z E CSC 482/582: Computer Security I I J M P T W A B H V V W Z C G J N O T Tableau shown only has relevant rows and columns. Example encipherments: � key V, letter T: follow V column down to T row (giving “O”) � Key I, letter H: follow I column down to H row (giving “P”)

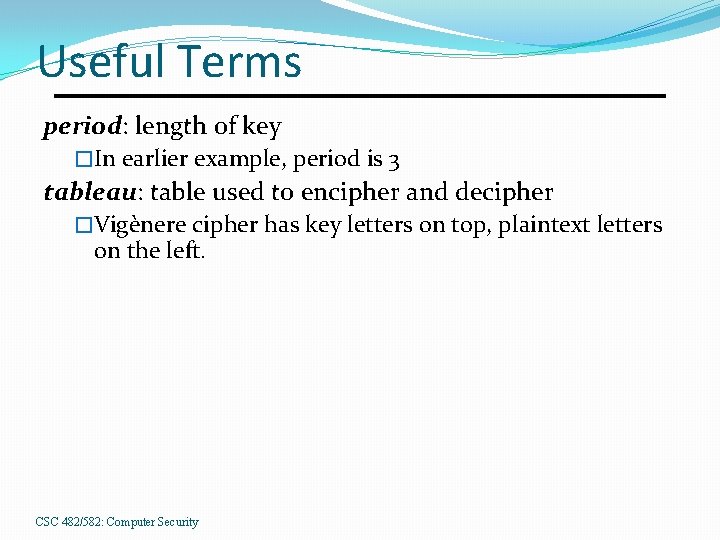
Useful Terms period: length of key �In earlier example, period is 3 tableau: table used to encipher and decipher �Vigènere cipher has key letters on top, plaintext letters on the left. CSC 482/582: Computer Security

Vigènere Cryptanalysis 1. 2. 3. Find key length (period), which we will call n. Break message into n parts, each part being enciphered using the same key letter. Use frequency analysis to solve resulting n simple substitution ciphers. key VIGVIGVIGV plain THEBOYHASTHEBALL cipher OPKWWECIYOPKWIRG CSC 482/582: Computer Security

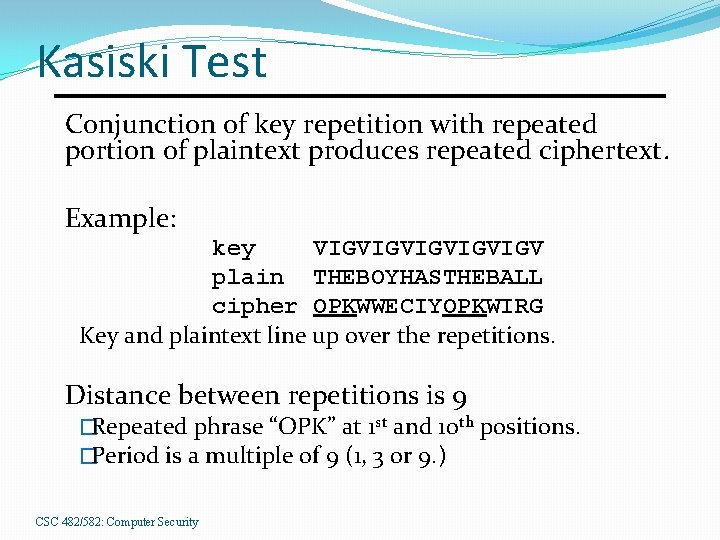
Kasiski Test Conjunction of key repetition with repeated portion of plaintext produces repeated ciphertext. Example: key VIGVIGVIGV plain THEBOYHASTHEBALL cipher OPKWWECIYOPKWIRG Key and plaintext line up over the repetitions. Distance between repetitions is 9 �Repeated phrase “OPK” at 1 st and 10 th positions. �Period is a multiple of 9 (1, 3 or 9. ) CSC 482/582: Computer Security

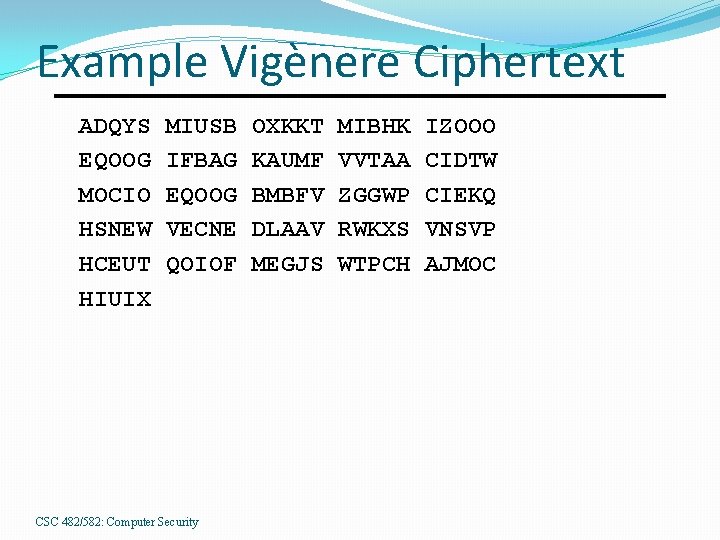
Example Vigènere Ciphertext ADQYS EQOOG MOCIO HSNEW HCEUT HIUIX MIUSB IFBAG EQOOG VECNE QOIOF CSC 482/582: Computer Security OXKKT KAUMF BMBFV DLAAV MEGJS MIBHK VVTAA ZGGWP RWKXS WTPCH IZOOO CIDTW CIEKQ VNSVP AJMOC

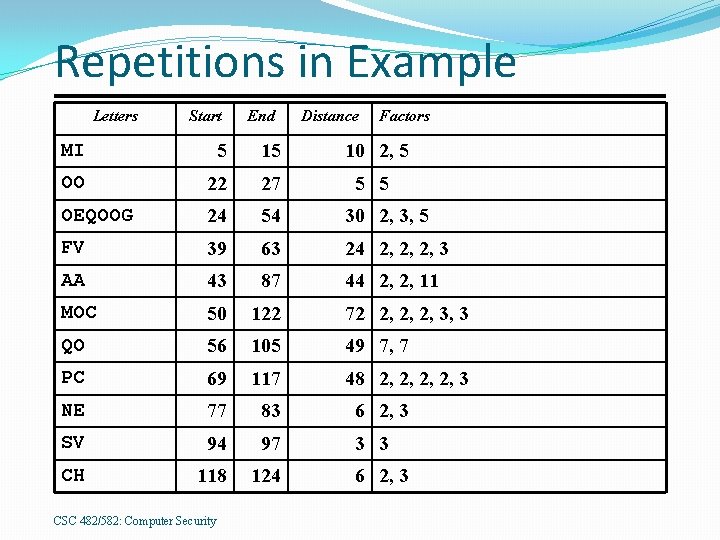
Repetitions in Example Letters Start End Distance Factors MI 5 15 10 2, 5 OO 22 27 5 5 OEQOOG 24 54 30 2, 3, 5 FV 39 63 24 2, 2, 2, 3 AA 43 87 44 2, 2, 11 MOC 50 122 72 2, 2, 2, 3, 3 QO 56 105 49 7, 7 PC 69 117 48 2, 2, 3 NE 77 83 6 2, 3 SV 94 97 3 3 CH 118 124 CSC 482/582: Computer Security 6 2, 3

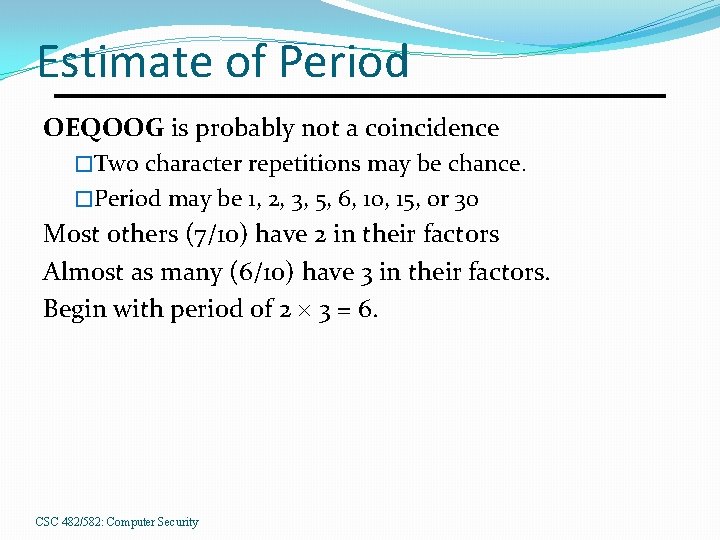
Estimate of Period OEQOOG is probably not a coincidence �Two character repetitions may be chance. �Period may be 1, 2, 3, 5, 6, 10, 15, or 30 Most others (7/10) have 2 in their factors Almost as many (6/10) have 3 in their factors. Begin with period of 2 3 = 6. CSC 482/582: Computer Security

Letter Coincidence: Picking two letters at random from a message that are identical. Procedure �Place one text above other. �Count coincidences. Coincidence probabilities for two letters: �Random English letters: 1/26 @ 0. 0385 �English plaintext: 0. 0667 CSC 482/582: Computer Security

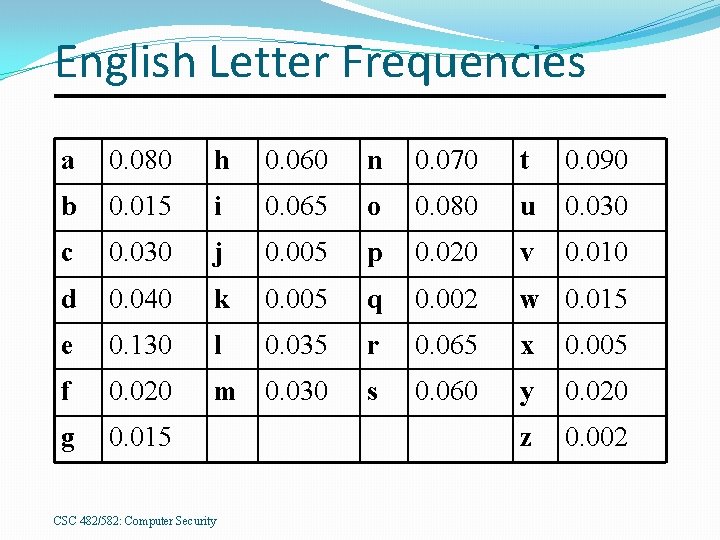
English Letter Frequencies a 0. 080 h 0. 060 n 0. 070 t 0. 090 b 0. 015 i 0. 065 o 0. 080 u 0. 030 c 0. 030 j 0. 005 p 0. 020 v 0. 010 d 0. 040 k 0. 005 q 0. 002 w 0. 015 e 0. 130 l 0. 035 r 0. 065 x 0. 005 f 0. 020 m 0. 030 s 0. 060 y 0. 020 g 0. 015 z 0. 002 CSC 482/582: Computer Security

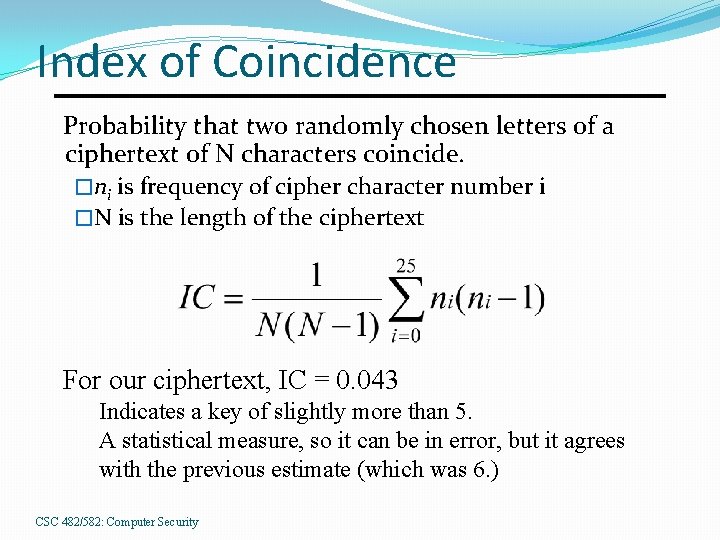
Index of Coincidence Probability that two randomly chosen letters of a ciphertext of N characters coincide. �ni is frequency of cipher character number i �N is the length of the ciphertext For our ciphertext, IC = 0. 043 Indicates a key of slightly more than 5. A statistical measure, so it can be in error, but it agrees with the previous estimate (which was 6. ) CSC 482/582: Computer Security

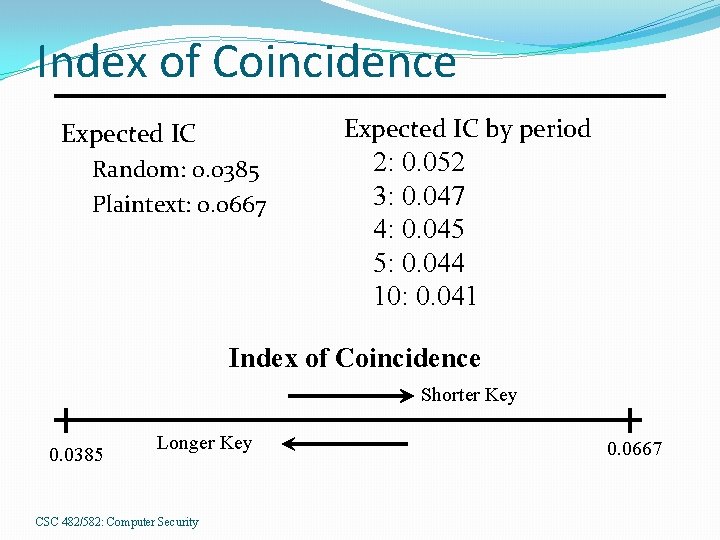
Index of Coincidence Expected IC by period Expected IC Random: 0. 0385 Plaintext: 0. 0667 2: 0. 052 3: 0. 047 4: 0. 045 5: 0. 044 10: 0. 041 Index of Coincidence Shorter Key 0. 0385 Longer Key CSC 482/582: Computer Security 0. 0667

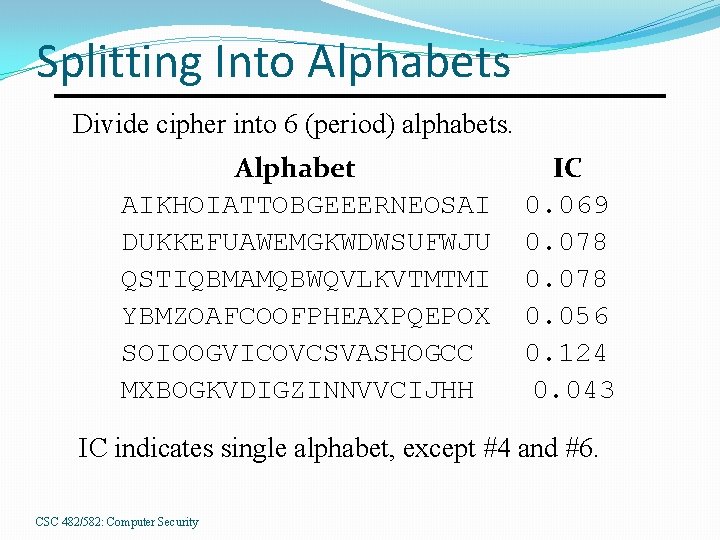
Splitting Into Alphabets Divide cipher into 6 (period) alphabets. Alphabet AIKHOIATTOBGEEERNEOSAI DUKKEFUAWEMGKWDWSUFWJU QSTIQBMAMQBWQVLKVTMTMI YBMZOAFCOOFPHEAXPQEPOX SOIOOGVICOVCSVASHOGCC MXBOGKVDIGZINNVVCIJHH IC 0. 069 0. 078 0. 056 0. 124 0. 043 IC indicates single alphabet, except #4 and #6. CSC 482/582: Computer Security

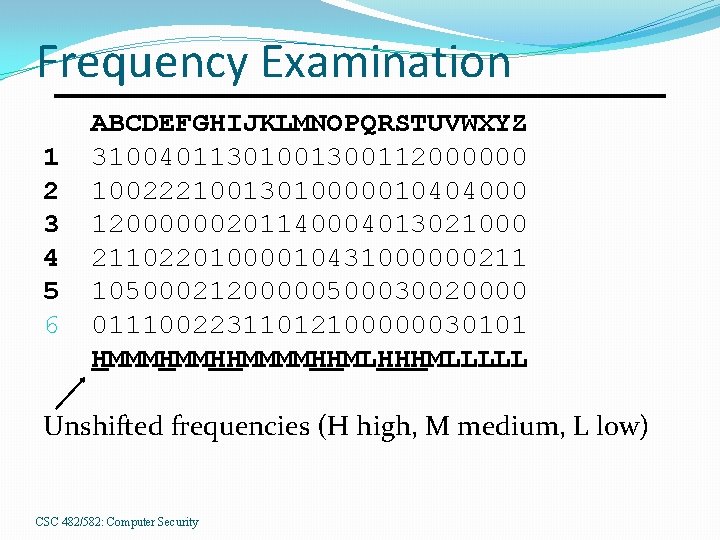
Frequency Examination 1 2 3 4 5 6 ABCDEFGHIJKLMNOPQRSTUVWXYZ 31004011301001300112000000 10022210013010000010404000 12000000201140004013021000 21102201000010431000000211 10500021200000500030020000 01110022311012100000030101 HMMMHMMHHMMMMHHMLHHHMLLLLL Unshifted frequencies (H high, M medium, L low) CSC 482/582: Computer Security

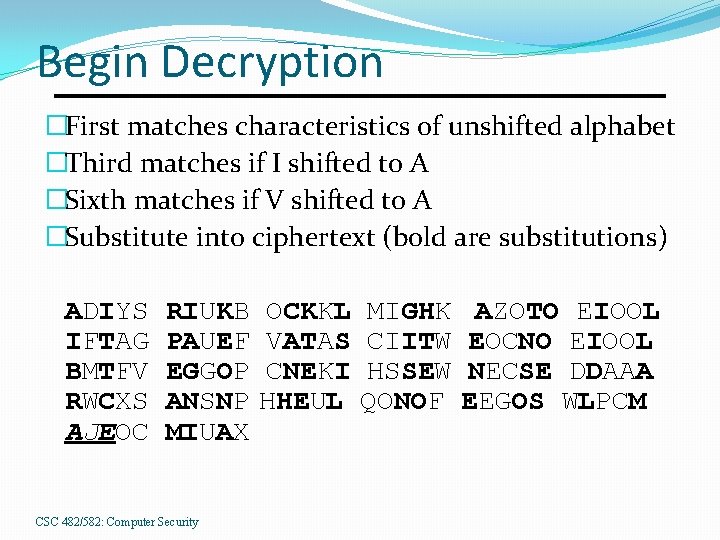
Begin Decryption �First matches characteristics of unshifted alphabet �Third matches if I shifted to A �Sixth matches if V shifted to A �Substitute into ciphertext (bold are substitutions) ADIYS IFTAG BMTFV RWCXS AJEOC RIUKB PAUEF EGGOP ANSNP MIUAX CSC 482/582: Computer Security OCKKL VATAS CNEKI HHEUL MIGHK CIITW HSSEW QONOF AZOTO EIOOL EOCNO EIOOL NECSE DDAAA EEGOS WLPCM

Look For Clues AJE in last line suggests “are”, meaning second alphabet maps A into S: ALIYS MIOOL EOCNO HSSEE HHECL MICAX RICKB INTAG MIOOL NECSE QONON CSC 482/582: Computer Security OCKSL PACEF BUTFV LDAAA EEGOS MIGHS VATIS EGOOP RECXS ELPCM AZOTO CIITE CNESI ANANP AREOC

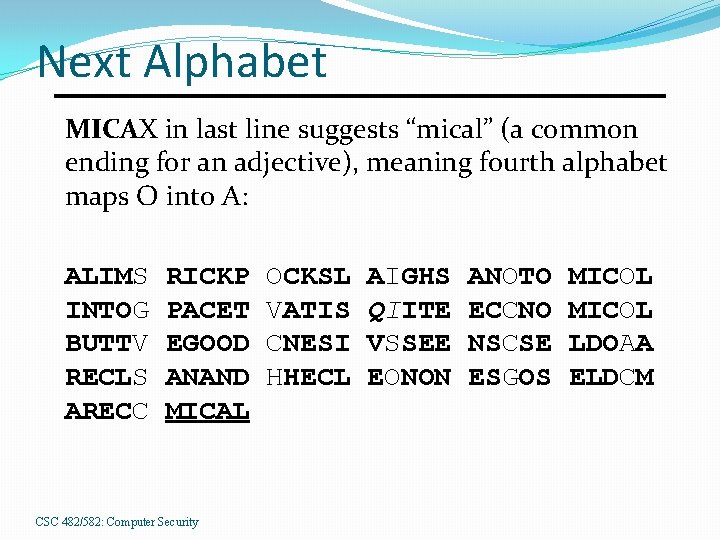
Next Alphabet MICAX in last line suggests “mical” (a common ending for an adjective), meaning fourth alphabet maps O into A: ALIMS INTOG BUTTV RECLS ARECC RICKP PACET EGOOD ANAND MICAL CSC 482/582: Computer Security OCKSL VATIS CNESI HHECL AIGHS QIITE VSSEE EONON ANOTO ECCNO NSCSE ESGOS MICOL LDOAA ELDCM

Got It! QI means that U maps into I, as Q is always followed by U: ALIME INTOS BUTTH RECLE ARECO RICKP PACET EGOOD ANAND MICAL CSC 482/582: Computer Security ACKSL HATIS ONESI THECL AUGHS QUITE VESEE EANON ANATO ECONO NSOSE ESSOS MICAL LDOMA ELDOM

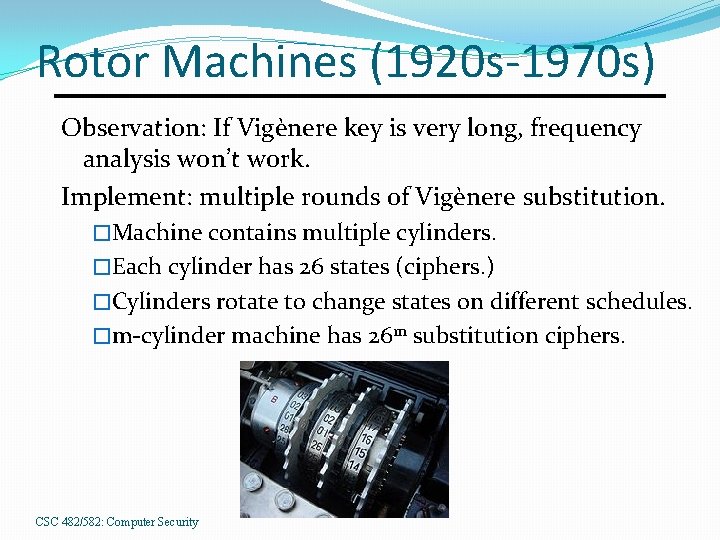
Rotor Machines (1920 s-1970 s) Observation: If Vigènere key is very long, frequency analysis won’t work. Implement: multiple rounds of Vigènere substitution. �Machine contains multiple cylinders. �Each cylinder has 26 states (ciphers. ) �Cylinders rotate to change states on different schedules. �m-cylinder machine has 26 m substitution ciphers. CSC 482/582: Computer Security

Enigma Machine 3 rotors: 17576 substitutions. 3 rotors can be used in any order: 6 combinations. Some machines had up to 8 rotors Plug board: 6 pairs of letters can be swapped. Total keys ~ 1016 CSC 482/582: Computer Security

The World Wars Decryption of Zimmerman telegram 1917 �Leads US into World War I Japanese Purple Machine cracked 1937 �US breaks rotor machine for highest secrets. German Enigma machine cracked 1933 -45 �Initially broken by Polish mathematician �Variants broken at Bletchley Park in UK �Colossus, world’s 1 st electronic computer. 48

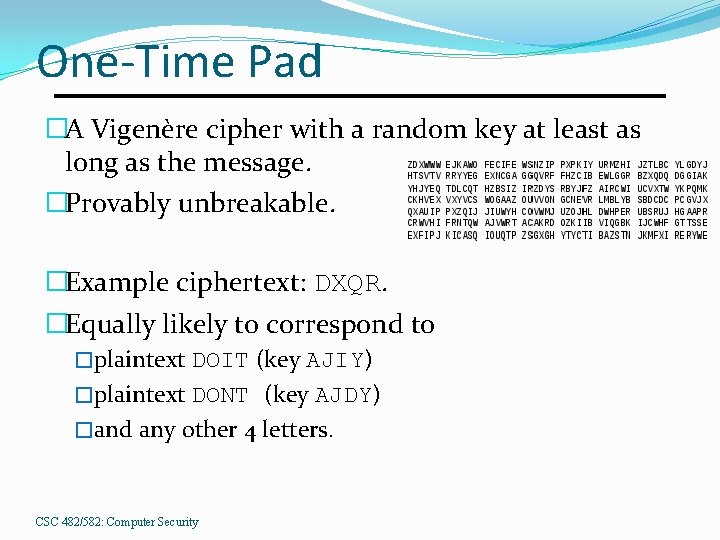
One-Time Pad �A Vigenère cipher with a random key at least as long as the message. �Provably unbreakable. �Example ciphertext: DXQR. �Equally likely to correspond to �plaintext DOIT (key AJIY) �plaintext DONT (key AJDY) �and any other 4 letters. CSC 482/582: Computer Security

Binary One Time Pad Encrypt a message M with pad P to produce ciphertext C=M⊕P where ⊕ is the exclusive OR operator. Decrypt a ciphertext C with the same pad P M=C⊕P We can prove this as follows: C ⊕ P = (M ⊕ P) ⊕ P = M ⊕ (P ⊕ P) associativity =M⊕ 0 =M CSC 482/582: Computer Security

One Time Pad Problems 1. The one-time pad must be random. Software pseudo-random number generators are not random. Pad needs hardware randomness. 2. Transmission of long pads is difficult. The pad is just as long as all the messages you’ll ever send with it, so you’ve just moved the problem of transmitting secret messages to transmitting a secret pad. 3. Pad must always be kept secret. If pad is ever discovered, then attacker can decrypt old messages. Pads must be securely destroyed at end of use. CSC 482/582: Computer Security

Stream Ciphers �Stream ciphers approximate one time pad by �Generating pseudorandom bits, the keystream. �XOR keystream with stream of plaintext bits �i. e. Ci = Pi ⊕ Ki where Ki generated from small key k �Stream ciphers default for most mobile hardware �Simple (good when chip size and power limited) �Fast (mobile devices are slow) �Also widely used in software in the form of RC 4. �Important: reuse of keystream for multiple messages is insecure for a stream cipher. CSC 482/582: Computer Security

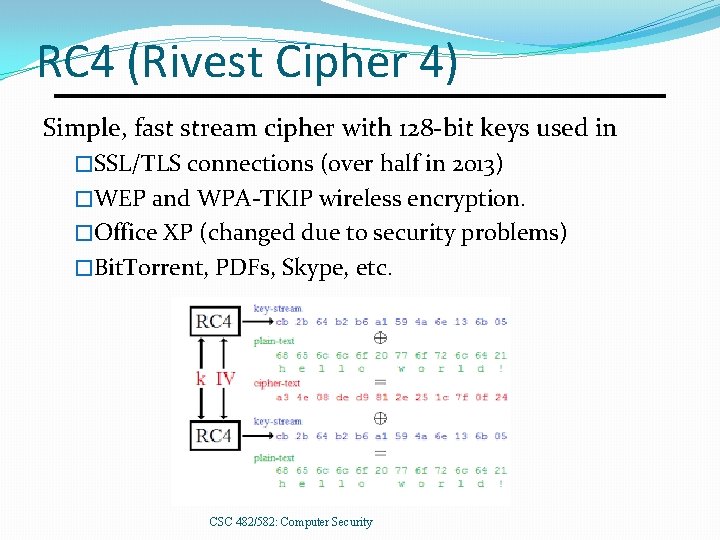
RC 4 (Rivest Cipher 4) Simple, fast stream cipher with 128 -bit keys used in �SSL/TLS connections (over half in 2013) �WEP and WPA-TKIP wireless encryption. �Office XP (changed due to security problems) �Bit. Torrent, PDFs, Skype, etc. CSC 482/582: Computer Security

RC 4 Security Problems Misuse �Office XP encrypted different versions of same document with same key, reusing keystream. �Solution: XOR key with nonce, changing nonce for each document version. Weaknesses �If you flip a bit in the ciphertext, it flips the corresponding bit in the plaintext. Solution: MACs. �First part of keystream has many biases (predictable patterns) that have been used to attack RC 4. CSC 482/582: Computer Security

RC 4 Security Attacks Attacking RC 4 in Wireless (FMS Attack) � Knowing first 3 bytes of key, biases in keystreams can let an attacker with a few hundred keystreams extract the key. � Seems unlikely, but many RC 4 users (such as WEP) create key by prepending a predictable Initialization Vector (IV) to a strong key. Attacking RC 4 in TLS (http: //www. isg. rhul. ac. uk/tls/) � Known plaintext attack based on knowledge of HTTP protocol. � Attacker inserts Java. Script that makes page reload in background. � RC 4 biases allow cookie extraction based on millions of encryptions of same known plaintext (headers like Cookie and Content-Type). � RC 4 -drop. N variants proposed where RC 4 drops first 768 or more bytes to eliminate biased output. Browsers will stop using RC 4 in TLS in early 2016. CSC 482/582: Computer Security

Block Ciphers Encrypt groups (blocks) of chars at once. �Combine substitution and transposition. Improvement over single char substitution �Cryptanalysis must use digraph frequencies for two- char blocks, trigraph for three-char blocks, etc. �Longer blocks are more difficult to analyze. Example: Playfair Cipher, 1854 CSC 482/582: Computer Security

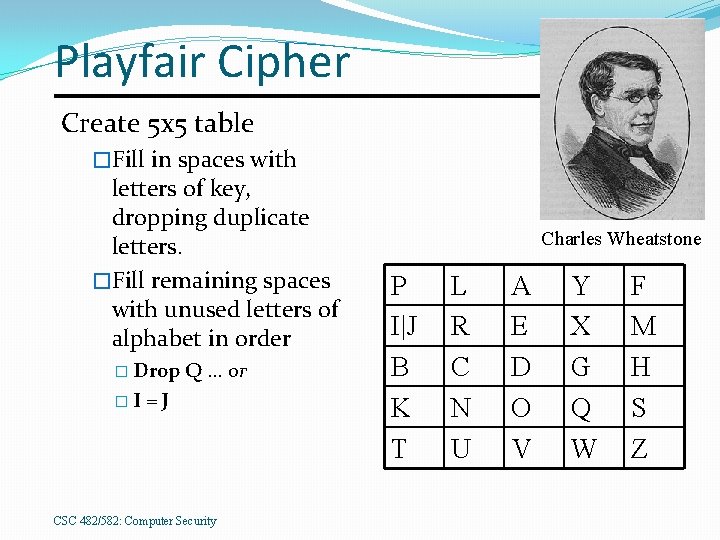
Playfair Cipher Create 5 x 5 table �Fill in spaces with letters of key, dropping duplicate letters. �Fill remaining spaces with unused letters of alphabet in order � Drop �I Q … or =J CSC 482/582: Computer Security Charles Wheatstone P I|J B K T L R C N U A E D O V Y X G Q W F M H S Z

Playfair Cipher Encryption Algorithm 1. 2. 3. If letters of pair are identical (or only one letter remains), add an “X” after first letter. If two letters are in same row or column, replace them with the succeeding letters. Otherwise, two letters form a rectangle, and we replace them with letters on the same row respectively at the other pair of corners. CSC 482/582: Computer Security

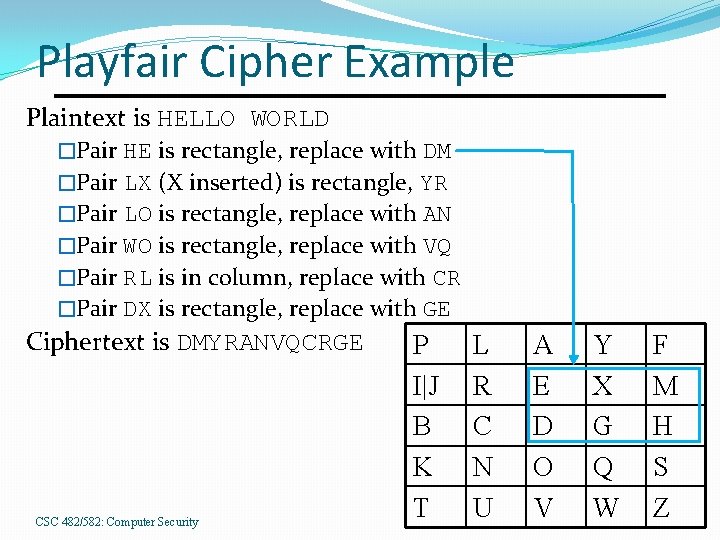
Playfair Cipher Example Plaintext is HELLO WORLD �Pair HE is rectangle, replace with DM �Pair LX (X inserted) is rectangle, YR �Pair LO is rectangle, replace with AN �Pair WO is rectangle, replace with VQ �Pair RL is in column, replace with CR �Pair DX is rectangle, replace with GE Ciphertext is DMYRANVQCRGE CSC 482/582: Computer Security P I|J B K T L R C N U A E D O V Y X G Q W F M H S Z

Modern Block Ciphers �Long blocks � 64 -bit in 20 th century � 128 -bit in early 21 st century �Round structure �Create simple block cipher (S-box). �Repeat cipher multiple times, each time with diff key. �Key scheduling algorithm generates round keys. CSC 482/582: Computer Security

SP-Networks Combine Substitution+Permutation (transposition) �Confusion: adding unknown key values will confuse attacker about value of plaintext symbol. �Diffusion: Spread plaintext data throughout ciphertext. Designing for Security �Block Size �Number of Rounds � Each input bit is XOR of several output bits from previous round. �Choice of S-boxes CSC 482/582: Computer Security

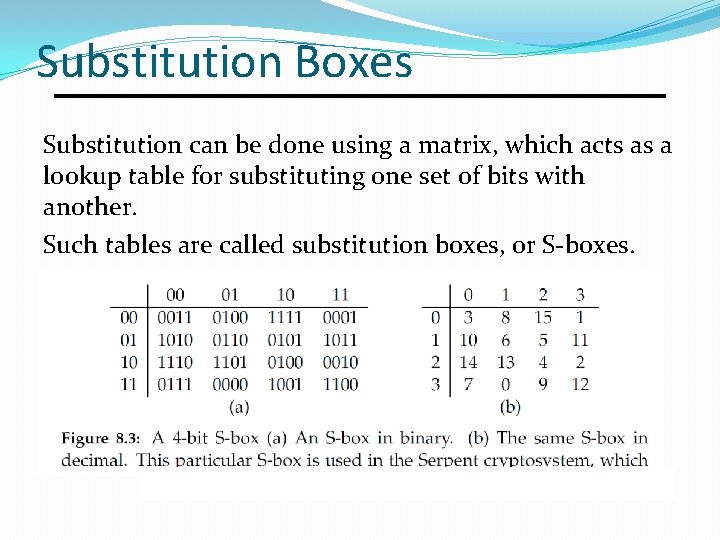
Substitution Boxes Substitution can be done using a matrix, which acts as a lookup table for substituting one set of bits with another. Such tables are called substitution boxes, or S-boxes.

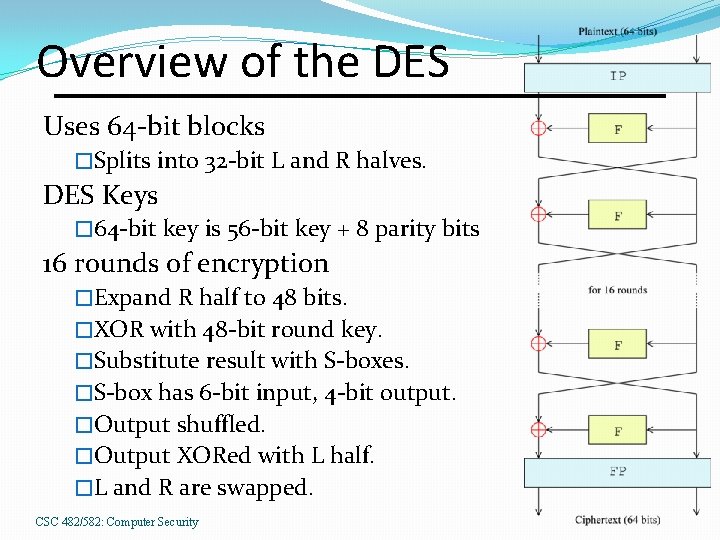
Overview of the DES Uses 64 -bit blocks �Splits into 32 -bit L and R halves. DES Keys � 64 -bit key is 56 -bit key + 8 parity bits 16 rounds of encryption �Expand R half to 48 bits. �XOR with 48 -bit round key. �Substitute result with S-boxes. �S-box has 6 -bit input, 4 -bit output. �Output shuffled. �Output XORed with L half. �L and R are swapped. CSC 482/582: Computer Security

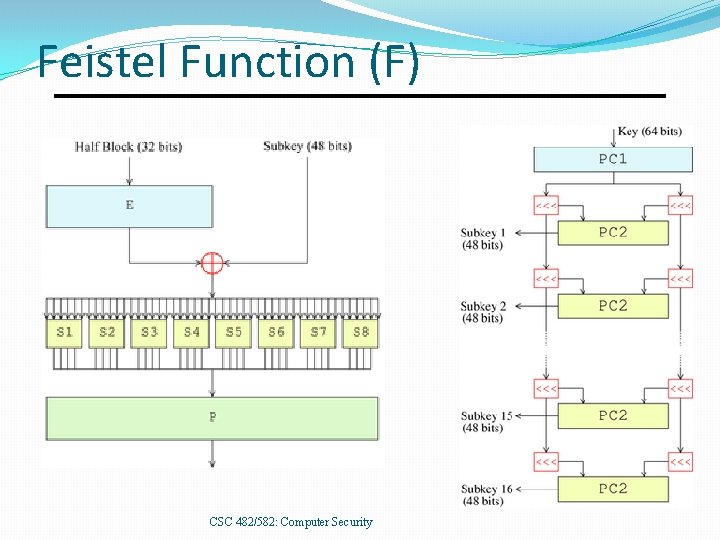
Feistel Function (F) CSC 482/582: Computer Security

DES Weaknesses Keys are too short �NSA reduced key length from 128 -bits to 56 -bits. �EFF “Deep Crack” brute forced DES in 48 -hours in 1998. Weak keys exist �If key is 0, all round keys are 0 too. �Other keys also produce identical round keys. Design decision worries �Did NSA leave backdoor in S-box? CSC 482/582: Computer Security

Differential Cryptanalysis A chosen ciphertext attack �Biham and Shamir rediscovered in late 1980 s �Examines pairs of plaintext with particular differences. �Requires 247 plaintext, ciphertext pairs. �Only 214 pairs required with 8 round DES. Revealed several properties �S-box designed to resist differential cryptanalysis. �IBM revealed knowledge of technique at design time. Linear cryptanalysis improves result �Linear approximation of DES. �Requires 243 plaintext, ciphertext pairs. �DES not designed to resist this technique. CSC 482/582: Computer Security

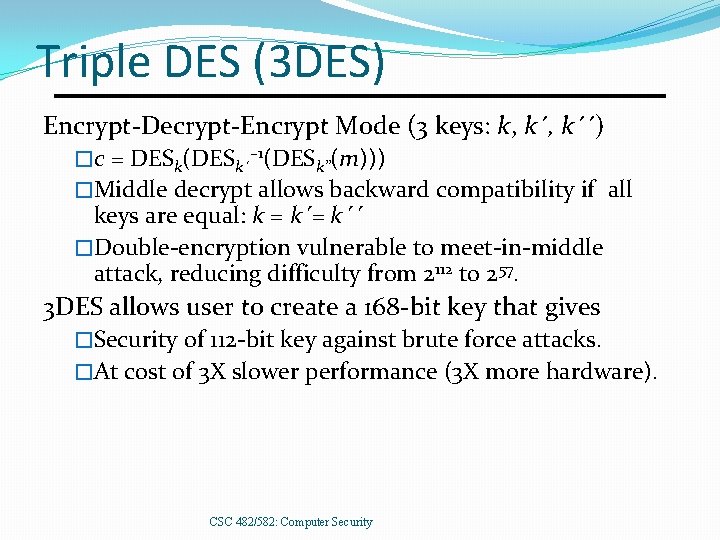
Triple DES (3 DES) Encrypt-Decrypt-Encrypt Mode (3 keys: k, k´´) �c = DESk(DESk´– 1(DESk’’(m))) �Middle decrypt allows backward compatibility if all keys are equal: k = k´´ �Double-encryption vulnerable to meet-in-middle attack, reducing difficulty from 2112 to 257. 3 DES allows user to create a 168 -bit key that gives �Security of 112 -bit key against brute force attacks. �At cost of 3 X slower performance (3 X more hardware). CSC 482/582: Computer Security

DES is Insecure Brute force attacks can now be completed in <1 day �Distributed computing attacks. �RIVYERA FPGA-based parallel computer breaks DES in <1 day for a hardware cost of <$10, 000. Linear cryptanalysis faster than brute force �Need 241 known plaintexts CSC 482/582: Computer Security

Block Cipher Modes CSC 482/582: Computer Security

Padding �We want to encrypt data of any length. �But block ciphers encrypt fixed sized blocks. �Therefore we need padding. �Obvious but wrong �Just add zero bytes until last block is filled. �When decrypting, which zeros are plaintext or padding? �Common padding algorithms �Append 128 followed by as many zeros as needed to fill final block. �Compute number of padding bytes required. Pad plaintext by appending n bytes, each with value n. CSC 482/582: Computer Security

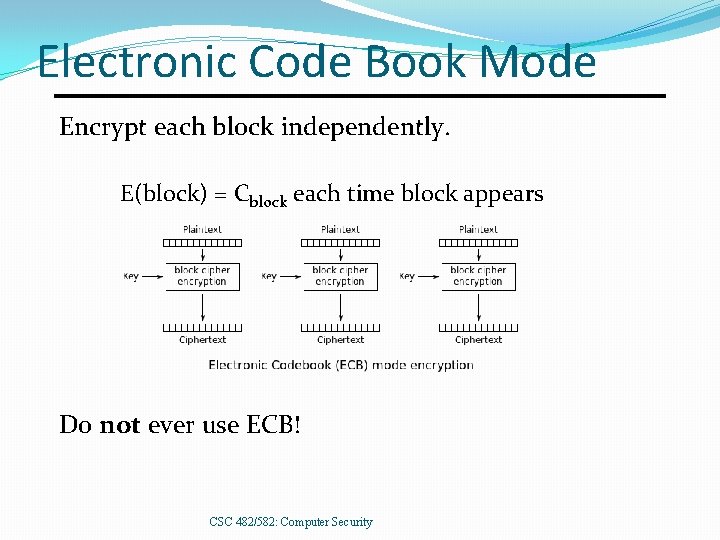
Electronic Code Book Mode Encrypt each block independently. E(block) = Cblock each time block appears Do not ever use ECB! CSC 482/582: Computer Security

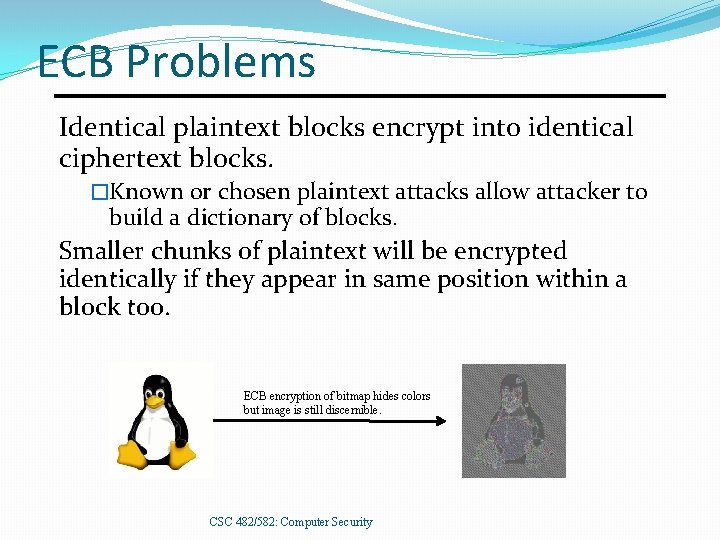
ECB Problems Identical plaintext blocks encrypt into identical ciphertext blocks. �Known or chosen plaintext attacks allow attacker to build a dictionary of blocks. Smaller chunks of plaintext will be encrypted identically if they appear in same position within a block too. ECB encryption of bitmap hides colors but image is still discernible. CSC 482/582: Computer Security

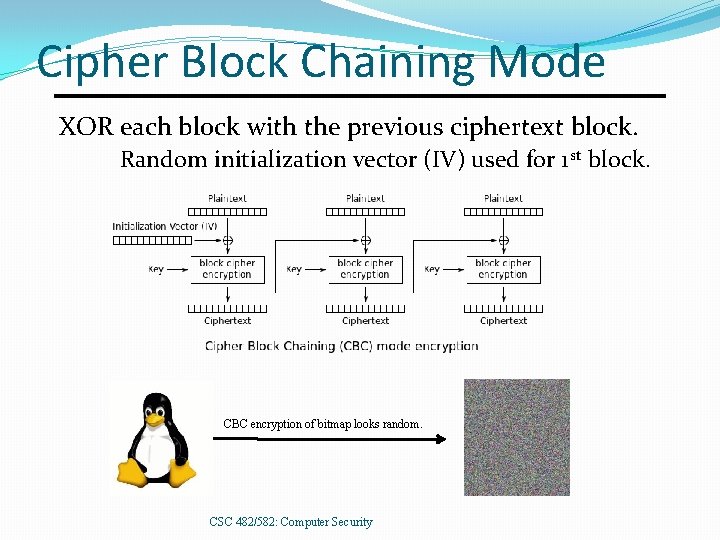
Cipher Block Chaining Mode XOR each block with the previous ciphertext block. Random initialization vector (IV) used for 1 st block. CBC encryption of bitmap looks random. CSC 482/582: Computer Security

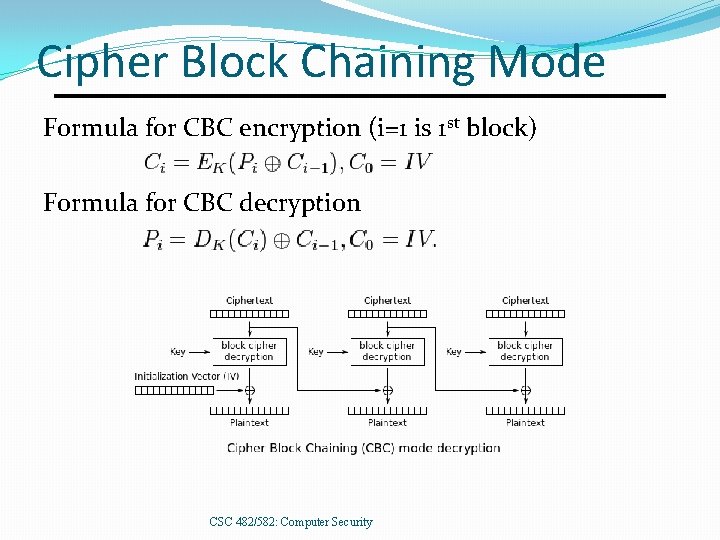
Cipher Block Chaining Mode Formula for CBC encryption (i=1 is 1 st block) Formula for CBC decryption CSC 482/582: Computer Security

CBC Self-Healing Property Plaintext “heals” after 2 blocks. i. e. , if ciphertext altered, error propagated 2 blocks. Initial message 3231343336353837 Received as (underlined 4 c should be 4 b) ef 7 c 4 cb 2 b 4 ce 6 f 3 b f 6266 e 3 a 97 af 0 e 2 c 746 ab 9 a 6308 f 4256 33 e 60 b 451 b 09603 d Which decrypts to efca 61 e 19 f 4836 f 1 3231333336353837 3231343336353837 CSC 482/582: Computer Security

Initialization Vectors �Reuse of a key/IV combination will result in identical encryption to previous use of combination. �IV Algorithms �Counter IV: Use 0 for 1 st message, 1 for 2 nd, etc. �Random IV: Randomly generate IV for each message and send IV in cleartext with message. �Nonce-generated IV: 1) 2) 3) 4) 5) 6) Assign a number to each message (can use counter). Use message number to generate unique nonce. Nonce should be as large as a single block. Encrypt nonce with block cipher to generate IV. Encrypt message in CBC mode using IV. Add message number in front of ciphertext. Only use message numbers once. CSC 482/582: Computer Security

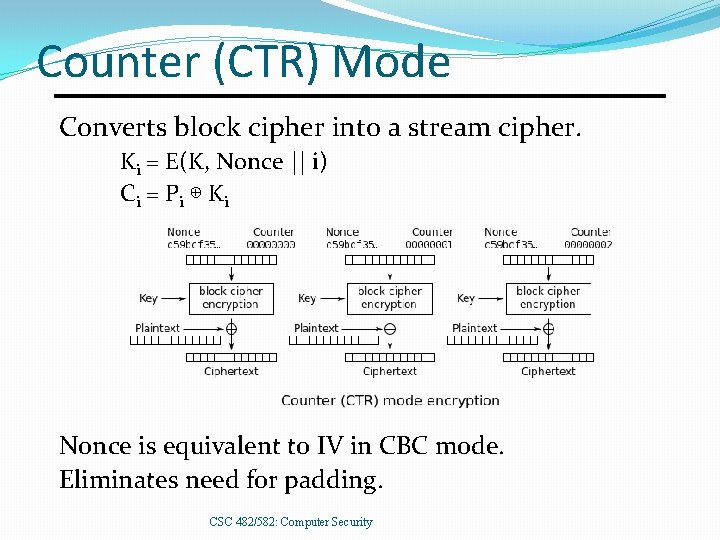
Counter (CTR) Mode Converts block cipher into a stream cipher. Ki = E(K, Nonce || i) C i = Pi ⊕ K i Nonce is equivalent to IV in CBC mode. Eliminates need for padding. CSC 482/582: Computer Security

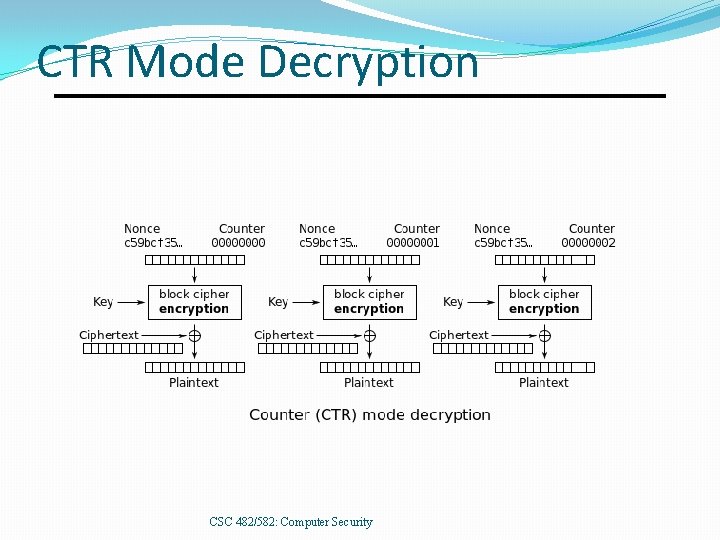
CTR Mode Decryption CSC 482/582: Computer Security

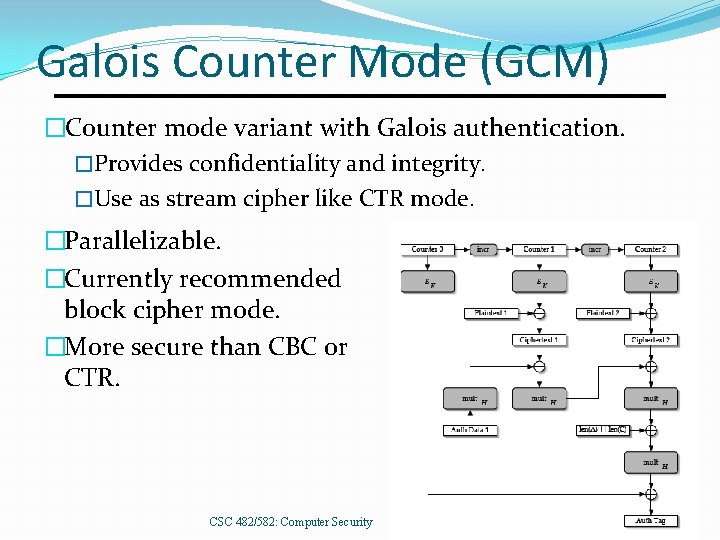
Galois Counter Mode (GCM) �Counter mode variant with Galois authentication. �Provides confidentiality and integrity. �Use as stream cipher like CTR mode. �Parallelizable. �Currently recommended block cipher mode. �More secure than CBC or CTR. CSC 482/582: Computer Security

Advanced Encryption Standard (AES) Winner of open NIST competition (1997 -2000) �Rijndael, designed by Joan Daemen and Vincent Rijmen. �Published as FIPS 197 in November 2001. 128 -bit block cipher � 128 -, 192 -, or 256 -bit keys. � 10, 12, or 14 rounds, depending on key size. Replacement for DES �DES vulnerable to brute force attacks due to 56 -bit keys. �AES is about 2 X faster than DES, 6 X faster than 3 DES. 9/6/2021 Cryptography 80

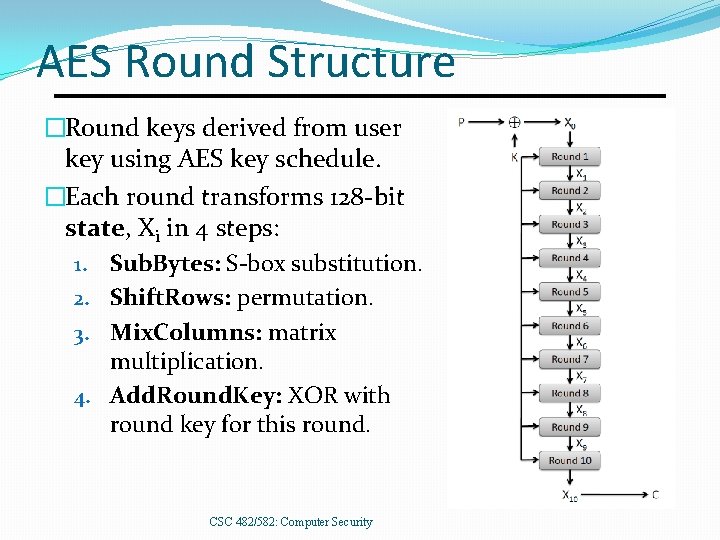
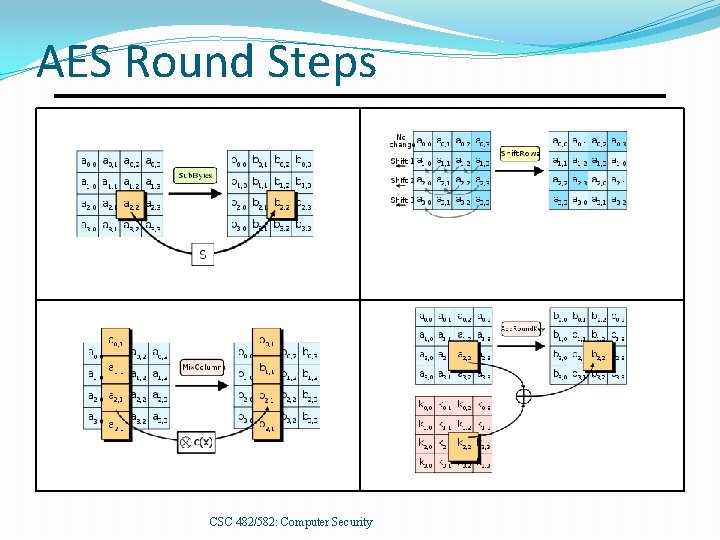
AES Round Structure �Round keys derived from user key using AES key schedule. �Each round transforms 128 -bit state, Xi in 4 steps: 1. Sub. Bytes: S-box substitution. 2. Shift. Rows: permutation. 3. Mix. Columns: matrix multiplication. 4. Add. Round. Key: XOR with round key for this round. CSC 482/582: Computer Security

AES Round Steps CSC 482/582: Computer Security

AES Cryptanalysis Biclique attack (2011) �Faster than brute force by a factor of 4 �So can break AES-128 with 2126. 1 operations. Related key attacks (2009) �Requires 299. 5 operations to break AES-256 �Requires 2176 operations to break AES-192 �Due to weak key scheduling algorithm for AES-256 �This means AES-128 is more secure than AES-256! CSC 482/582: Computer Security

AES Alternatives Caveat �Alternatives have seen much less analysis than AES, so we know less about their security. �But what if AES was broken? AES Contest Runner Ups �Serpent and Two. Fish �Ranked higher in security, lower in performance. Recent Ciphers �Three. Fish �Salsa 20 (a stream cipher) CSC 482/582: Computer Security

Key Points Types of ciphers �Substitution (monoalphabetic and polyalphabetic) �Transposition (permutation) �Product (Substitution + Permutation) Cryptanalysis �Kerchoff’s principle �Brute force attack �One-time pad is provably secure �Frequency analysis: Kasiski test, Index of Coincidence. Block ciphers �ECB mode insecure; need to use CBC for block ciphers. �DES obsolete due to small 56 -bit keys. 3 DES=112 bit key. �AES current standard, best symmetric cipher is AES-128. CSC 482/582: Computer Security

References 1. 2. 3. 4. 5. 6. 7. 8. Ross Anderson, Security Engineering, 2 nd edition, Wiley, 2008. Matt Bishop, Introduction to Computer Security, Addison-Wesley, 2005. Neil Daswani et. al. , Foundations of Security, Apress, 2007. Ferguson and Schneier, Practical Cryptography, Wiley, 2003. David Kahn, The Codebreakers, Mac. Millan, 1967. Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone, Handbook of Applied Cryptography, http: //www. cacr. math. uwaterloo. ca/hac/, CRC Press, 1996. NIST, FIPS Publication 46 -3: Data Encryption Standard (DES), 1999, http: //csrc. nist. gov/publications/fips 46 -3/fips 46 -3. pdf US Government Dept of the Army, FM 34 -40 -2 FIELD MANUAL, 1990, http: //www. umich. edu/~umich/fm-34 -40 -2/ CSC 482/582: Computer Security