CSC 482582 Computer Security Passwords CSC 482582 Computer






























- Slides: 45

CSC 482/582: Computer Security Passwords CSC 482/582: Computer Security

Topics 1. 2. 3. 4. 5. Password Systems Password Attacks Mitigating Attacks Graphical passwords One-time passwords CSC 482/582: Computer Security

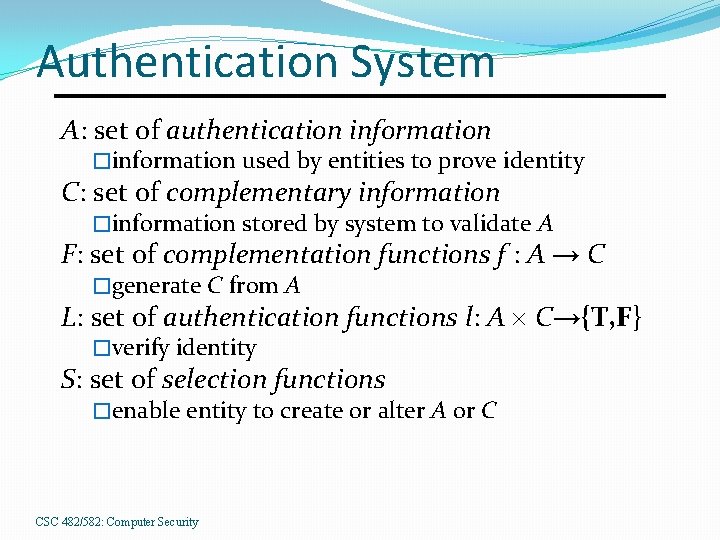
Authentication System A: set of authentication information �information used by entities to prove identity C: set of complementary information �information stored by system to validate A F: set of complementation functions f : A → C �generate C from A L: set of authentication functions l: A C→{T, F} �verify identity S: set of selection functions �enable entity to create or alter A or C CSC 482/582: Computer Security

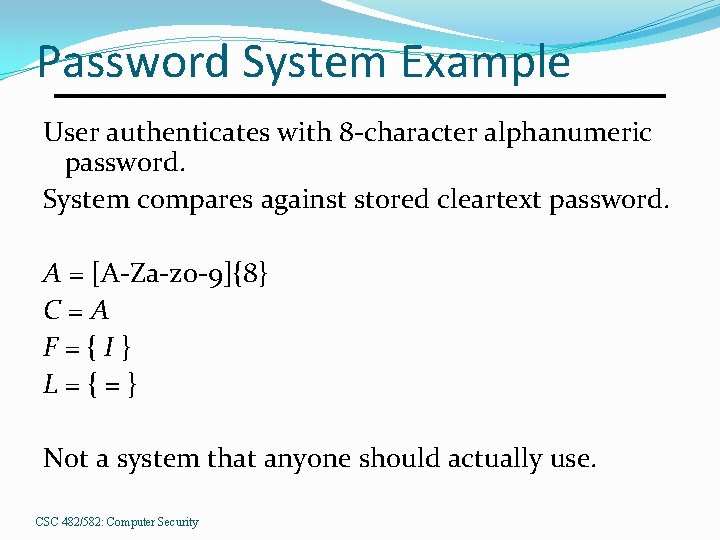
Password System Example User authenticates with 8 -character alphanumeric password. System compares against stored cleartext password. A = [A-Za-z 0 -9]{8} C=A F={I} L={=} Not a system that anyone should actually use. CSC 482/582: Computer Security

Passwords What you know Sequence of characters Complementation Function �Identity: requires access control to protect C �One-way Hash � easy to compute c = f(a) � difficult to compute a = f-1(c) CSC 482/582: Computer Security

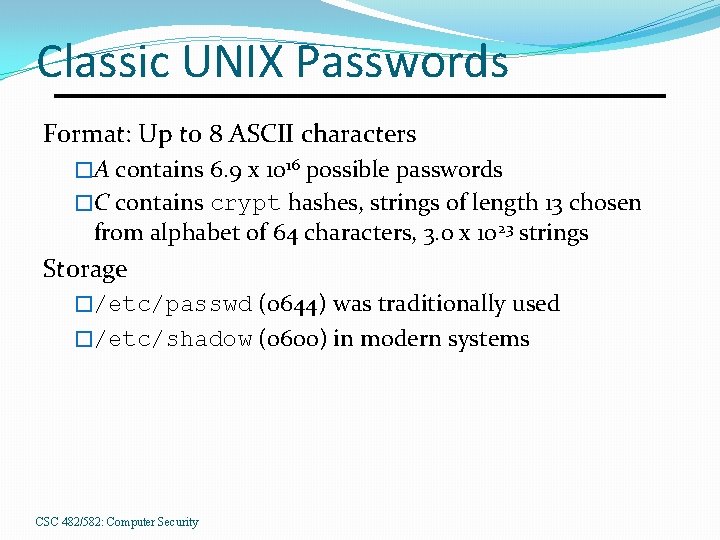
Classic UNIX Passwords Format: Up to 8 ASCII characters �A contains 6. 9 x 1016 possible passwords �C contains crypt hashes, strings of length 13 chosen from alphabet of 64 characters, 3. 0 x 1023 strings Storage �/etc/passwd (0644) was traditionally used �/etc/shadow (0600) in modern systems CSC 482/582: Computer Security

Attacks on Password Systems 1. 2. 3. 4. Offline password cracking Online dictionary attacks Observe passwords Attacking password infrastructure CSC 482/582: Computer Security

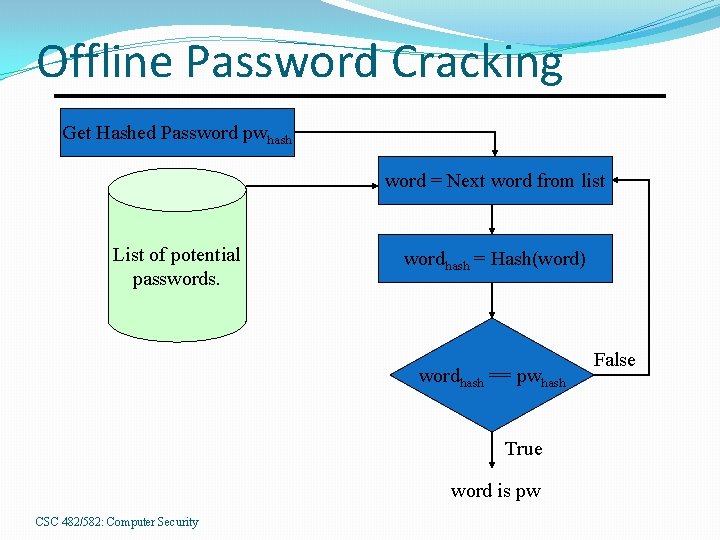
Offline Password Cracking Get Hashed Password pwhash word = Next word from list List of potential passwords. wordhash = Hash(word) wordhash == pwhash True word is pw CSC 482/582: Computer Security False

Cracking Methods 1. 2. 3. List of common passwords List of English/foreign words Permutation rules Substitute numbers/symbols for letters � Change case, pluralize, reverse words, character shifts, digit/symbol prefix/postfix, joining words � 4. Brute force � All possible passwords CSC 482/582: Computer Security

Online Password Guessing Use application’s login interface Much slower than offline attack, but Always possible to do. Two types of attack Guess passwords for a specific known user account � Know that it’s a valid account � Use information about user (name, bday) to guess Guess usernames and guess passwords for all accounts � Don’t know if account is valid � Failures may be due to invalid username or password � Someone probably has an easy to guess password CSC 482/582: Computer Security

Observe Passwords Sniff passwords off network �Must be able to access a network node in path between source and destination of communication �Impossible if connection is encrypted Find passwords in a file or database �Identify files/databases that likely to contain passwords �May or may not be encrypted Shoulder surf �Watch for someone to type a password Desk search �Passwords may be written down near workspace CSC 482/582: Computer Security

Attacking Password Infrastructure Web sites will e-mail you password if you answer a simple “secret” question: 1. 2. 3. What is your favorite color? What is your pet’s name? What is your mother’s maiden name? Violation of fail-safe defaults Failover to less secure protocol. How many favorite colors are there? CSC 482/582: Computer Security

Mitigating Password Attacks 1. 2. 3. 4. 5. 6. 7. 8. Enable system to use long passwords with a large alphabet of possible characters Hash passwords to protect against file attacks Salt passwords to protect against offline cracking Select hard to guess passwords Mitigating online attacks with backoff and lockout Protect password management functions Password aging One-time passwords CSC 482/582: Computer Security

Countering Password Guessing Choose A, C, and F to select suitably low probability P(T) of guessing in time T. P(T) >= TG / N G is number of guess per time unit T � T is number of time units in attack � N is number of possible passwords � CSC 482/582: Computer Security

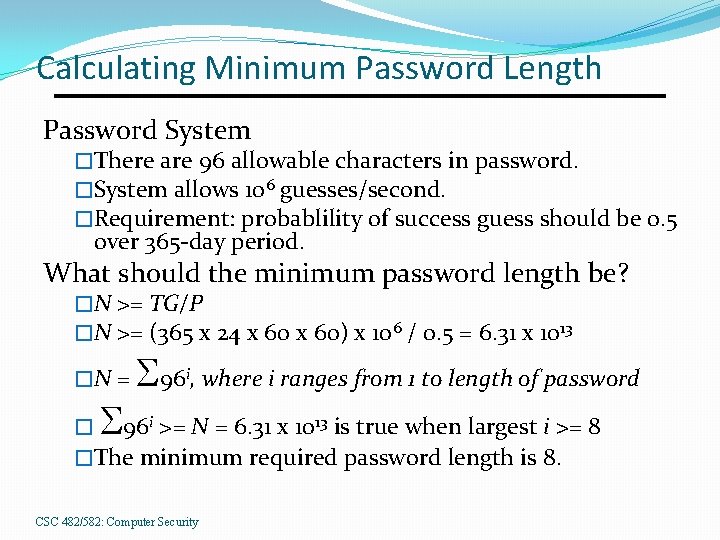
Calculating Minimum Password Length Password System �There are 96 allowable characters in password. �System allows 106 guesses/second. �Requirement: probablility of success guess should be 0. 5 over 365 -day period. What should the minimum password length be? �N >= TG/P �N >= (365 x 24 x 60) x 106 / 0. 5 = 6. 31 x 1013 �N = S S 96 , where i ranges from 1 to length of password i � 96 i >= N = 6. 31 x 1013 is true when largest i >= 8 �The minimum required password length is 8. CSC 482/582: Computer Security

UNIX Password Hashing crypt() function used for hashing �DES encrypts 64 -bit block of 0 s (25 rounds) using your password for the key. � Modified tools. DES incompatible with DES hardware cracking �Limited to 8 characters or less. �If limited to 95 printable characters, only 253 possible passwords. �How to resist dictionary attacks? Salting CSC 482/582: Computer Security

Salting Adds a 2 -character (12 -bit) random, public data to password to create key. Any word may be encrypted in 4096 possible ways (i. e. , there are 4096 f F). �Your password always uses same salt. �Someone else with same password (a) probably has different salt, and thus different c = f(a). Number of possible keys increased to 266 �Too small for today; modern UNIX doesn’t use crypt. CSC 482/582: Computer Security

Salting (cont. ) Prevents pre-calculated dictionary attack � 266 passwords requires millions of terabytes crypt() 218 passwords/second �Brute force would require 8000 machines for 48 days. CSC 482/582: Computer Security

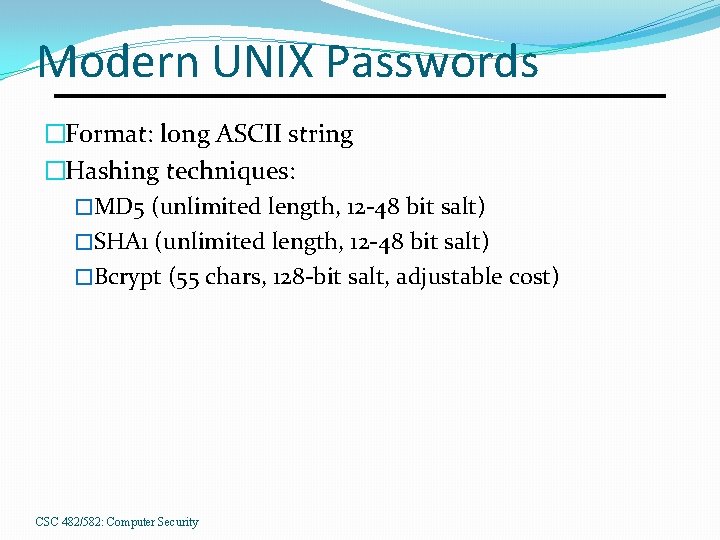
Modern UNIX Passwords �Format: long ASCII string �Hashing techniques: �MD 5 (unlimited length, 12 -48 bit salt) �SHA 1 (unlimited length, 12 -48 bit salt) �Bcrypt (55 chars, 128 -bit salt, adjustable cost) CSC 482/582: Computer Security

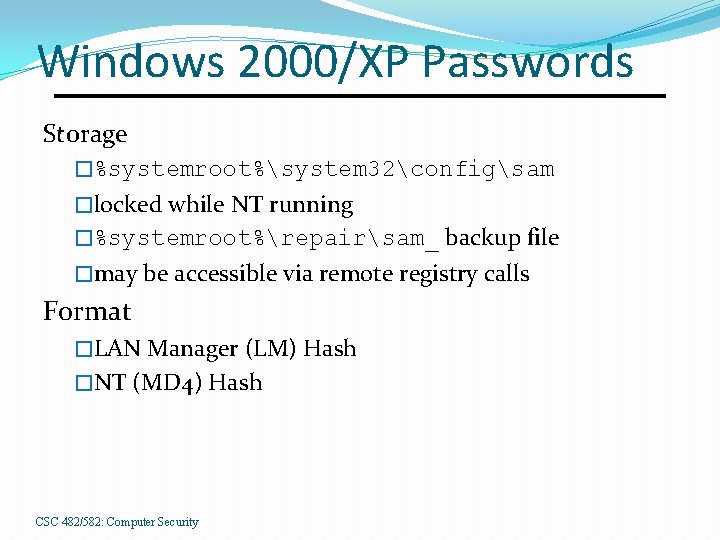
Windows 2000/XP Passwords Storage �%systemroot%system 32configsam �locked while NT running �%systemroot%repairsam_ backup file �may be accessible via remote registry calls Format �LAN Manager (LM) Hash �NT (MD 4) Hash CSC 482/582: Computer Security

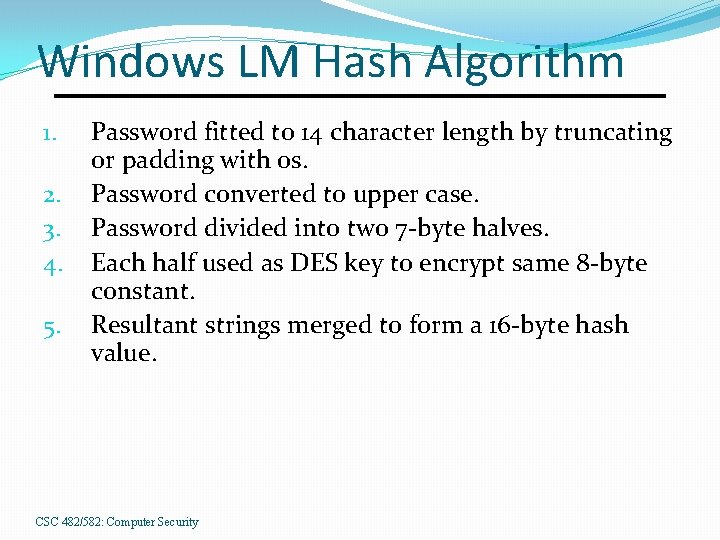
Windows LM Hash Algorithm 1. 2. 3. 4. 5. Password fitted to 14 character length by truncating or padding with 0 s. Password converted to upper case. Password divided into two 7 -byte halves. Each half used as DES key to encrypt same 8 -byte constant. Resultant strings merged to form a 16 -byte hash value. CSC 482/582: Computer Security

Windows LM Hash Problems Last 8 bytes of c known if password < 7 chars. Dividing password into halves reducing problem of breaking 14 -character password to breaking two 7 character passwords. Conversion to upper case reduces character set. Dictionary of password hashes can be prebuilt �Number of possible passwords much smaller than DES space. �No salt is used. CSC 482/582: Computer Security

Windows NT Hash Converts to Unicode, MD 4 hashes result Caveat: Often used in conjunction with LM hash, which is required for backwards compatibility. No salt: identical passwords generate identical hashes. CSC 482/582: Computer Security

Password Selection 1. 2. 3. Random Selection Pronounceable Passwords User Selection CSC 482/582: Computer Security

Random Selection Yields equal distribution of passwords for maximum difficulty in cracking �What about short passwords? Random passwords aren’t easy to remember �Short term memory holds 7 +/- 2 items �People have multiple passwords �Principle of Psychological Acceptability Requires a good PRNG CSC 482/582: Computer Security

Random Selection (Bad)Example PDP-11 password generator � 16 -bit machine � 8 upper-case letters and digits �|P| = 368 = 2. 8 x 1012 �At 0. 00156 sec/encryption, 140 years to brute force PRNG had period of 216 – 1 �Only 65, 535 possible passwords �Requires 102 seconds to try all passwords CSC 482/582: Computer Security

Pronounceable Passwords Generate passwords from random phonemes instead of random characters. �People can remember password as sequence of audible phonemes instead of characters, allowing easy recall of longer passwords. �Fewer pronounceable passwords exist than random passwords. CSC 482/582: Computer Security

User Selection Allow users to choose passwords. Reject insecure passwords based on ruleset: 1. 2. 3. 4. 5. 6. 7. 8. Based on account, user, or host names Dictionary words Permuted dictionary words Patterns from keyboard Shorter than 6 characters Digits, lowercase, or uppercase only passwords License plates or acronyms Based on previously used passwords CSC 482/582: Computer Security

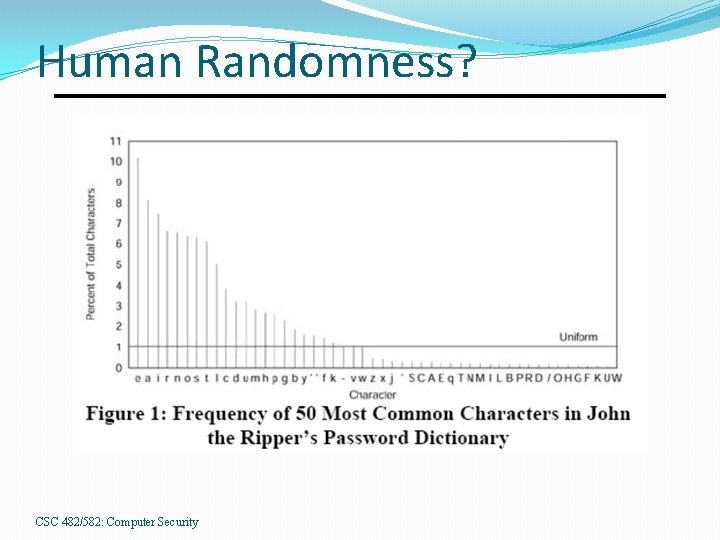
Human Randomness? CSC 482/582: Computer Security

Most Common Passwords CSC 482/582: Computer Security

How to Select Good Passwords Long passwords, consisting of multiple words. . 1. Use nth letter of each word if phrase too long. Themes: 2. 1. 2. 3. 4. 5. 6. 7. Word combinations: 3 blind katz E-mail or URL: yoda@strong-this-password-is. net Phone number: (888) 888 -eight Bracketing: Starfleet -> *!-Starfleet-!* Add a word: shopping -> Goin’ shopping Repetition: Pirate--Pirate. Ship Letter swapping: Sour Grape -> Gour Srape CSC 482/582: Computer Security

Mitigating Online Attacks If complements not accessible, attacker cannot use offline attacks and must use authentication functions. Cannot be prevented. Increase difficulty of auth function attack: Backoff: increasing wait before reprompting. Disconnection: disconnect after n failures. Disabling: disable account after n failures. Jailing: permit access to limited system, so admins can observe attacker. CSC 482/582: Computer Security

Protecting Password Management Always send password to a predetermined location �Do not let user change email/phone when requesting a password reset or change. Always notify the user of a password change �User can be alerted in case an attacker has changed the password. Let user create questions and answers �Don’t provide a list of pre-determined questions. CSC 482/582: Computer Security

Password Aging Requirement that password be changed after a period of time or after an event has occurred If expected time to guess is 180 days, should change password more frequently than 180 days 1. 2. 3. 4. If change time too short, users have difficulty recalling passwords. Cannot allow users to change password to current one. Also prevent users from changing passwords too soon. Give notice of impending password change requirement. CSC 482/582: Computer Security

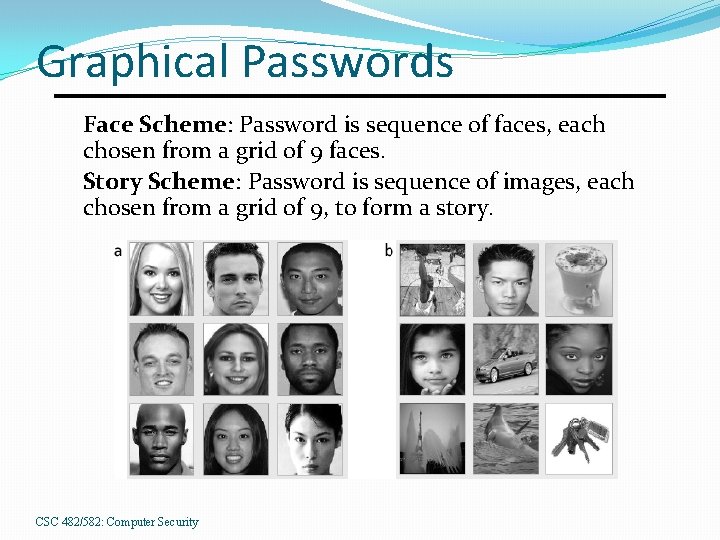
Graphical Passwords Face Scheme: Password is sequence of faces, each chosen from a grid of 9 faces. Story Scheme: Password is sequence of images, each chosen from a grid of 9, to form a story. CSC 482/582: Computer Security

Password Reuse http: //xkcd. com/792/ CSC 482/582: Computer Security

Challenge-Response Problem: passwords are reusable, and thus subject to replay attacks. Solution: authenticate in such a way that the transmitted password changes each time. CSC 482/582: Computer Security

One-Time Passwords A password that’s invalidated once used. Challenge: number of auth attempt Response: one-time password Problems Generation of one-time passwords � Use hash or crytographic function Synchronization of the user and the system � Number or timestamp passwords CSC 482/582: Computer Security

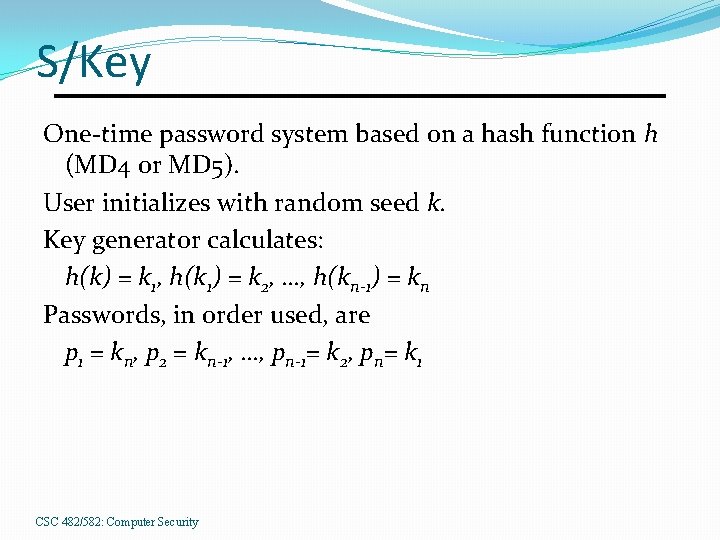
S/Key One-time password system based on a hash function h (MD 4 or MD 5). User initializes with random seed k. Key generator calculates: h(k) = k 1, h(k 1) = k 2, …, h(kn-1) = kn Passwords, in order used, are p 1 = kn, p 2 = kn-1, …, pn-1= k 2, pn= k 1 CSC 482/582: Computer Security

S/Key Attacker cannot derive pi+1 from pi since pi = kn-i+1, pi+1 = kn-i, and h(kn-i) = kn-i+1 which would require inverting h. Once user has used all passwords, S/Key must be reinitialized with a new seed. CSC 482/582: Computer Security

S/Key Login User supplies account name to server Server replies with number i stored in skeykeys file 3. User supplies corresponding password pi 4. Server computes h(pi) = h(kn-i+1) = kn-i+2 = pi-1 and compares result with stored password. If match, user is authenticated and S/Key updates number in skeykeys file to i-1 and stores pi 1. 2. CSC 482/582: Computer Security

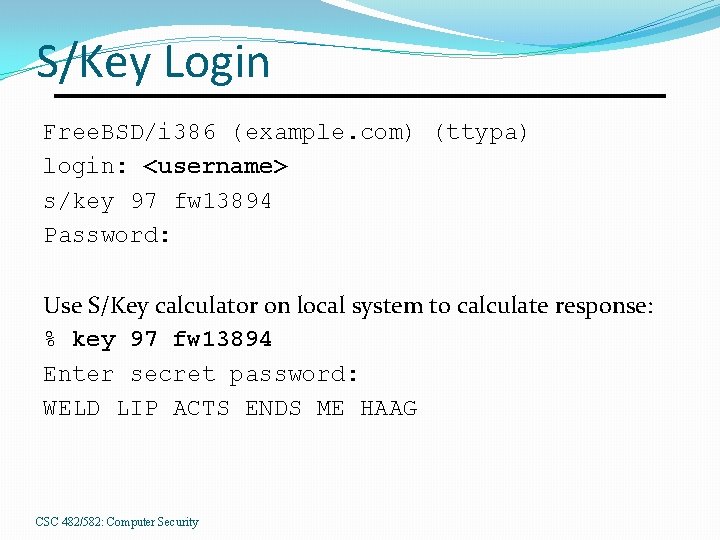
S/Key Login Free. BSD/i 386 (example. com) (ttypa) login: <username> s/key 97 fw 13894 Password: Use S/Key calculator on local system to calculate response: % key 97 fw 13894 Enter secret password: WELD LIP ACTS ENDS ME HAAG CSC 482/582: Computer Security

Other One Time Password Systems Software: OPIE �Backwards compatible with S/Key (if same hash used). Hardware: RSA Secur. ID card �Displayed password changes every 60 sec. �Password = constant password + Secur. ID CSC 482/582: Computer Security

Key Points Passwords can be attacked by �Offline cracking �Online guessing �Observation �Attacking password management functions Stored passwords are secured via �Hashing (crypt, MD 5, SHA 1, bcrypt) �Salting Good passwords need to be �Complex �Unique �Secret �Changed on a regular basis One-time passwords offer greater security. CSC 482/582: Computer Security

References 1. 2. 3. 4. 5. 6. 7. 8. 9. Ross Anderson, Security Engineering, Wiley, 2001. Matt Bishop, Introduction to Computer Security, Addison. Wesley, 2005. Mark Burnett and Dave Kleiman, Perfect Passwords, Syngress, 2006. Lorie Faith Cranor and Simson Garfinkel, Security and Usability, O’Reilly, 2005. Daswani, Foundations of Security, APress, 2007. Cynthia Kuo et. al. , “Human Selection of Mnemonic Phrasebased Passwords, ” SOUPS 2006, http: //cups. cmu. edu/soups/2006/proceedings/p 67_kuo. pdf, 2006. Neils Provos and David Mazieres, “A Future-Adaptable Password Scheme, ” http: //www. openbsd. org/papers/bcrypt-paper. pdf, 2006. Ed Skoudis, Counter Hack Reloaded, Prentice Hall, 2006. Simson Garfinkel, Gene Spafford, and Alan Schwartz, Practical UNIX and Internet Security, 3/e O’Reilly, 2003. CSC 482/582: Computer Security