CSC 482582 Computer Security Protocols CSC 482582 Computer






























- Slides: 73

CSC 482/582: Computer Security Protocols CSC 482/582: Computer Security

Topics 1. 2. 3. 4. 5. 6. Basic Concepts of Cryptography Security Protocols Authentication Protocols Key Exchange Protocols Kerberos Public Key Infrastructure CSC 482/582: Computer Security

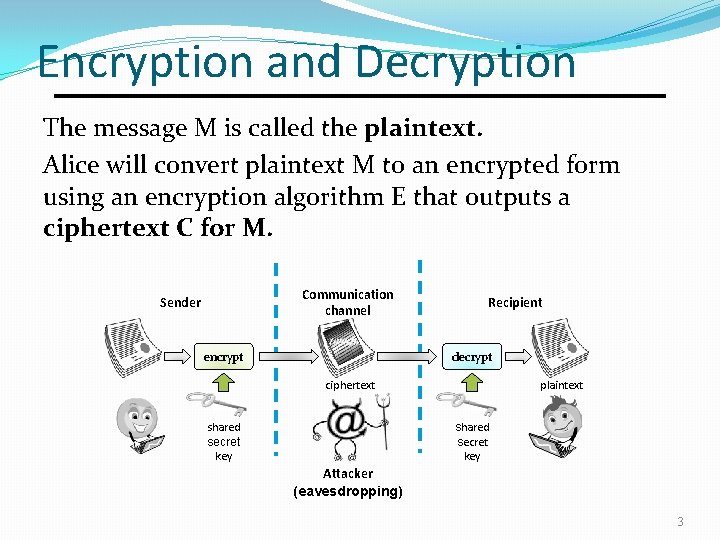
Encryption and Decryption The message M is called the plaintext. Alice will convert plaintext M to an encrypted form using an encryption algorithm E that outputs a ciphertext C for M. Communication channel Sender encrypt Recipient decrypt ciphertext plaintext shared secret key Attacker (eavesdropping) 3

Encryption and Decryption As equations: C = E(M, K) M = D(C, K) The encryption and decryption algorithms are chosen so that it is infeasible for someone other than Alice and Bob to determine plaintext M from ciphertext C without knowing the key K. Thus, ciphertext C can be transmitted over an insecure channel that can be eavesdropped by an adversary. 4

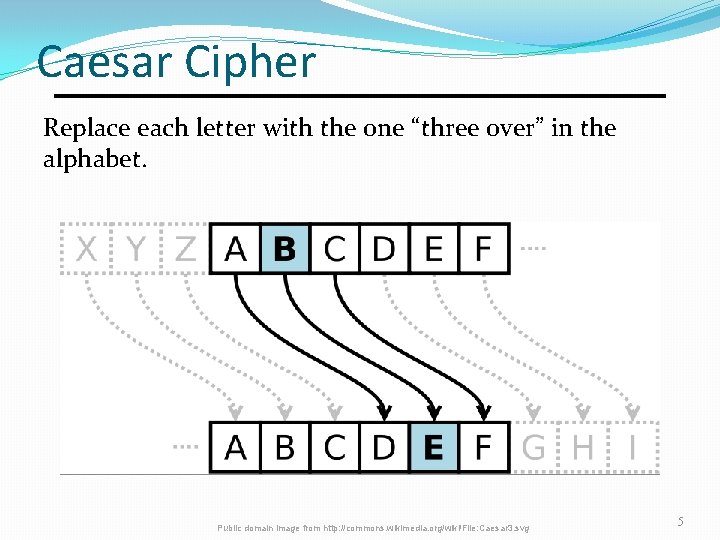
Caesar Cipher Replace each letter with the one “three over” in the alphabet. Public domain image from http: //commons. wikimedia. org/wiki/File: Caesar 3. svg 5

Kerckhoff’s Principle Security of cryptosystem should only depend on 1. Quality of shared encryption algorithm E 2. Secrecy of key K Security through obscurity tends to fail ex: DVD Content Scrambling System 6

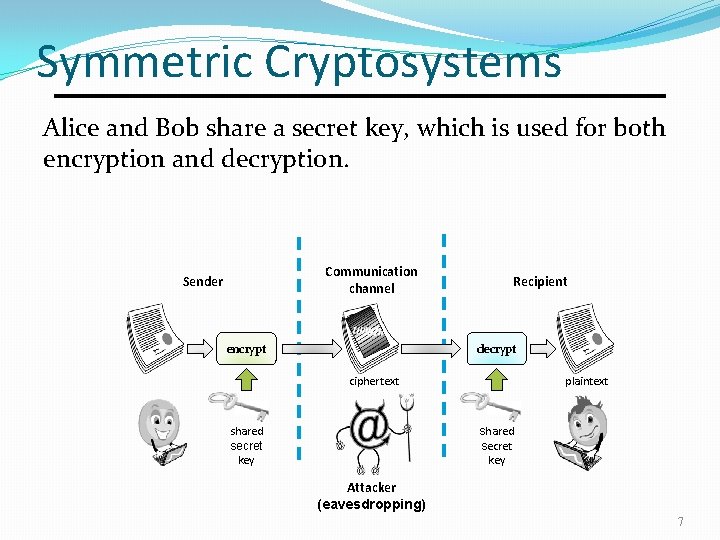
Symmetric Cryptosystems Alice and Bob share a secret key, which is used for both encryption and decryption. Communication channel Sender encrypt Recipient decrypt ciphertext plaintext shared secret key Attacker (eavesdropping) 7

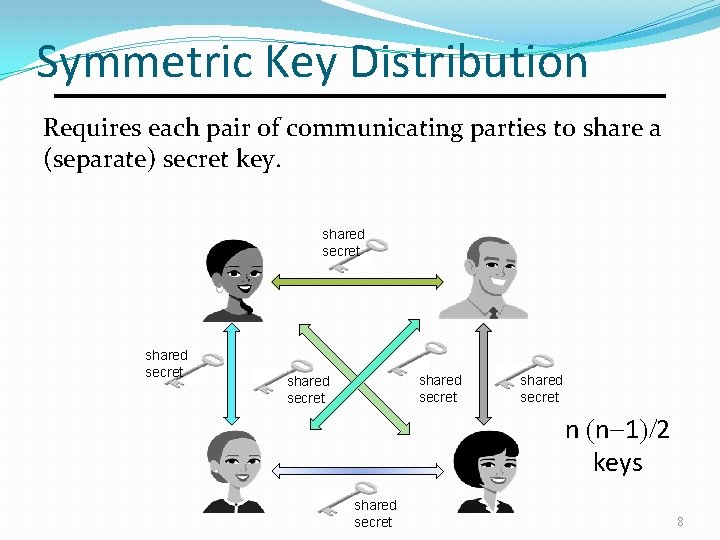
Symmetric Key Distribution Requires each pair of communicating parties to share a (separate) secret key. shared secret shared secret n (n-1)/2 keys shared secret 8

Public-Key Cryptography Bob has two keys: a private key, SB, which Bob keeps secret, and a public key, PB, which Bob broadcasts widely. �In order for Alice to send an encrypted message to Bob, she need only obtain his public key, PB, use that to encrypt her message, M, and send the result, C = EPB (M), to Bob then uses his secret key to decrypt the message as M = DSB (C). 9

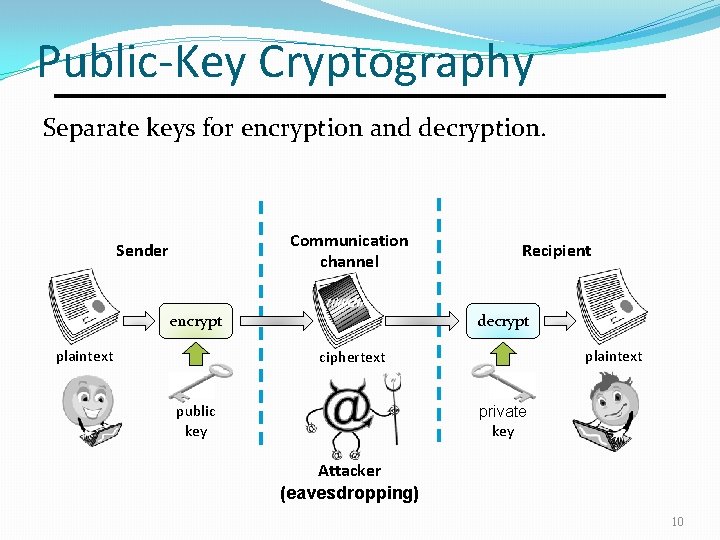
Public-Key Cryptography Separate keys for encryption and decryption. Communication channel Sender encrypt plaintext Recipient decrypt plaintext ciphertext plaintext public key private key Attacker (eavesdropping) 10

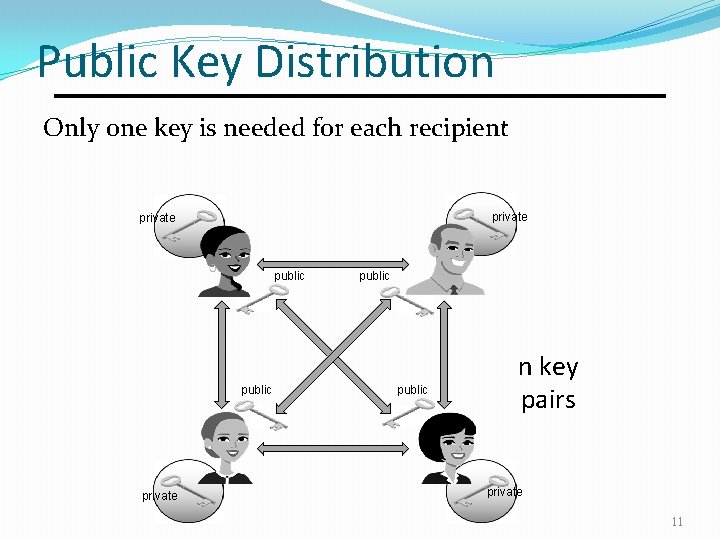
Public Key Distribution Only one key is needed for each recipient private public n key pairs private 11

Digital Signatures Public-key encryption provides a method for doing digital signatures, which serve the same authentication purpose as script signatures. To sign a message, M, Alice just encrypts it with her private key, SA, creating C = ESA(M). 2. Anyone can decrypt this message using Alice’s public key, as M’ = DPA(C). 3. If M=M’, then signature is valid. 1. 12

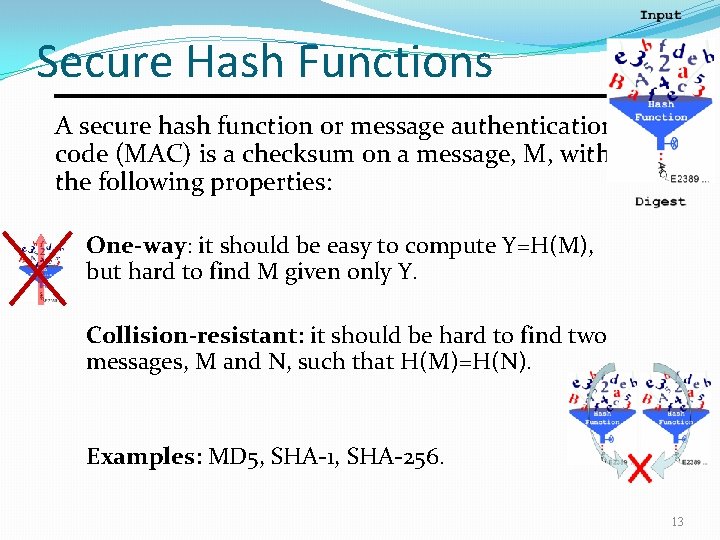
Secure Hash Functions A secure hash function or message authentication code (MAC) is a checksum on a message, M, with the following properties: One-way: it should be easy to compute Y=H(M), but hard to find M given only Y. Collision-resistant: it should be hard to find two messages, M and N, such that H(M)=H(N). Examples: MD 5, SHA-1, SHA-256. 13

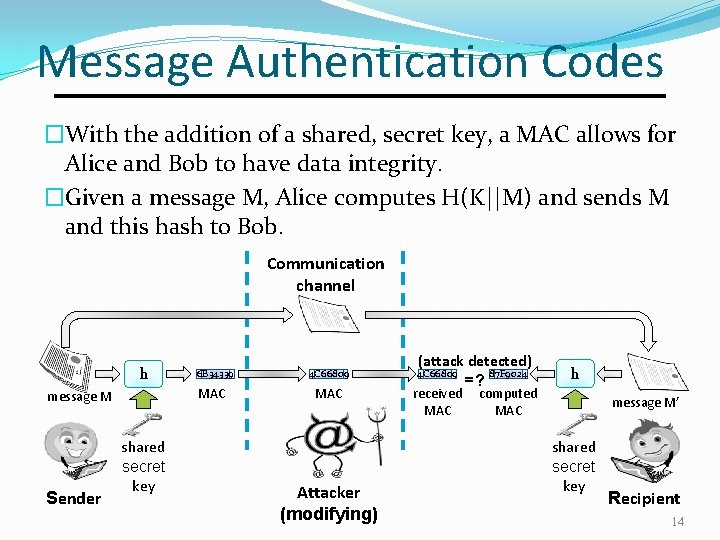
Message Authentication Codes �With the addition of a shared, secret key, a MAC allows for Alice and Bob to have data integrity. �Given a message M, Alice computes H(K||M) and sends M and this hash to Bob. Communication channel h MAC message M Sender 6 B 34339 shared secret key (attack detected) 87 F 9024 =? 4 C 66809 MAC received MAC Attacker (modifying) h computed MAC message M’ shared secret key Recipient 14

What is a Protocol? Human protocols: rules and procedures followed in human interactions, such as social situations. �Example: Ordering, eating, and paying in a restaurant. Network protocols: rules followed in networked communication systems. �Examples: TCP/IP, HTTP, FTP, etc. Security protocols: communication rules followed in a security application. �Examples: SSL/TLS, IPSec, Kerberos, etc. CSC 482/582: Computer Security

ATM Machine Protocol 1. 2. 3. Insert ATM card. Enter PIN. Correct PIN? (3 tries allowed) Yes? Conduct your transaction No? Machine eats card

Dramatis Personae Cathy, the Computer, trusted 3 rd party. Alice, 1 st participant Bob, 2 nd participant Eve, the Eavesdropper CSC 482/582: Computer Security

Notation X sends Y a message Z encrypted with key k. X Y : {Z} k Concatenation of bit sequences A and B A || B Key subscripts indicate ownership k. A is the key belonging to user A(lice) k. A, B is a key shared by A(lice) and B(ob) Nonces (nonrepeating random numbers) r 1, r 2 CSC 482/582: Computer Security

Car unlocking protocols Principals are the engine controller E and the car key transponder T. T E: KT How does protocol address the threat of car theft? �Threat can replay KT to gain access to car later. �Can thief guess the transponder key, KT?

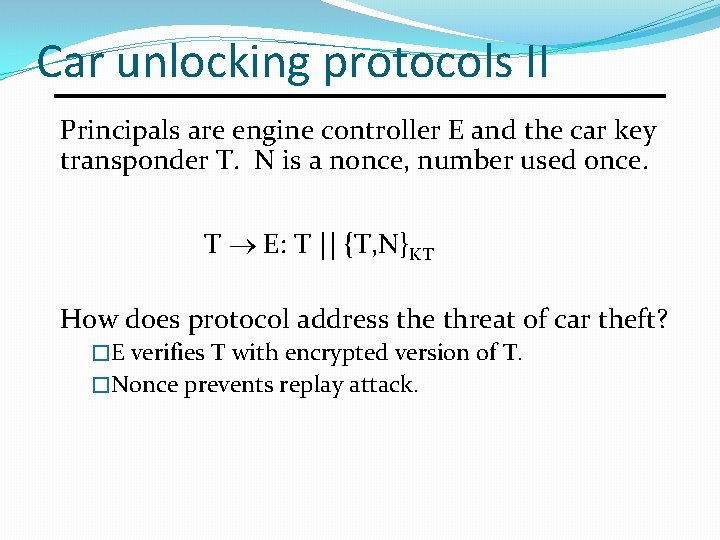
Car unlocking protocols II Principals are engine controller E and the car key transponder T. N is a nonce, number used once. T E: T || {T, N}KT How does protocol address the threat of car theft? �E verifies T with encrypted version of T. �Nonce prevents replay attack.

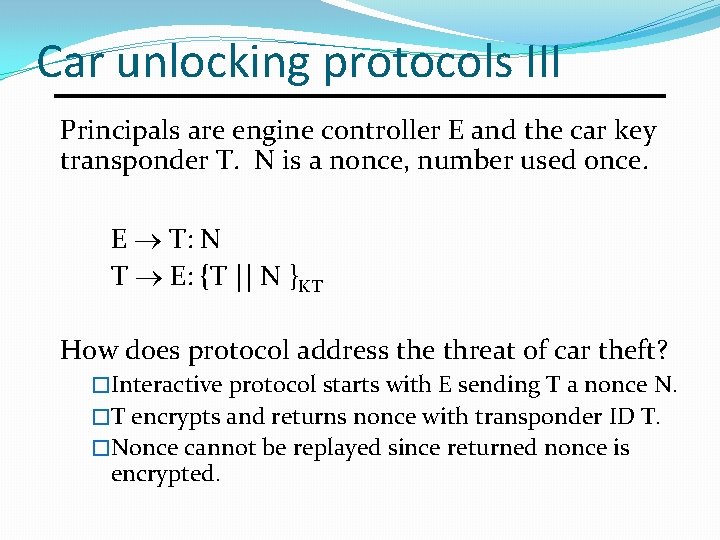
Car unlocking protocols III Principals are engine controller E and the car key transponder T. N is a nonce, number used once. E T: N T E: {T || N }KT How does protocol address the threat of car theft? �Interactive protocol starts with E sending T a nonce N. �T encrypts and returns nonce with transponder ID T. �Nonce cannot be replayed since returned nonce is encrypted.

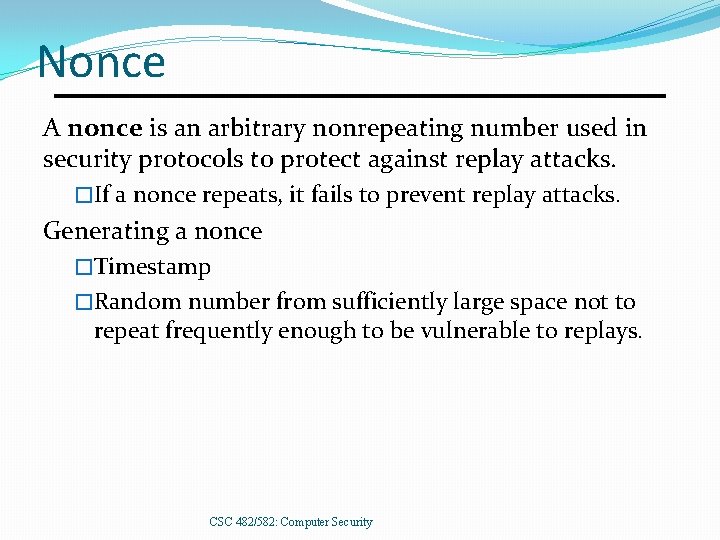
Nonce A nonce is an arbitrary nonrepeating number used in security protocols to protect against replay attacks. �If a nonce repeats, it fails to prevent replay attacks. Generating a nonce �Timestamp �Random number from sufficiently large space not to repeat frequently enough to be vulnerable to replays. CSC 482/582: Computer Security

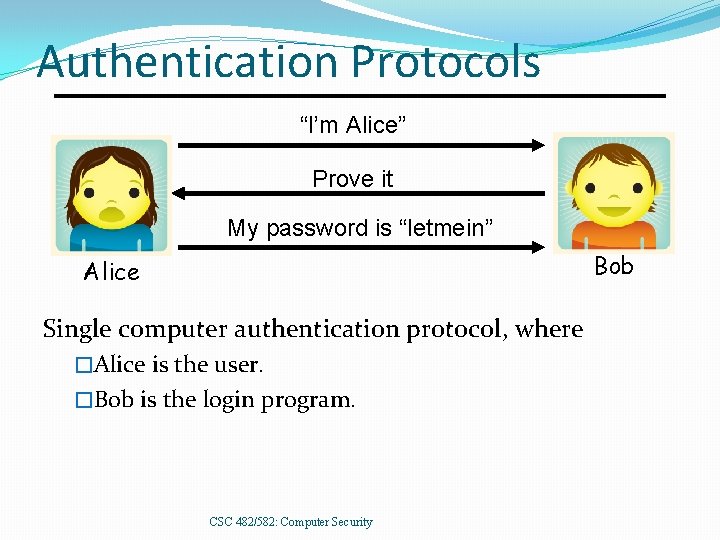
Authentication Protocols “I’m Alice” Prove it My password is “letmein” Bob Alice Single computer authentication protocol, where �Alice is the user. �Bob is the login program. CSC 482/582: Computer Security

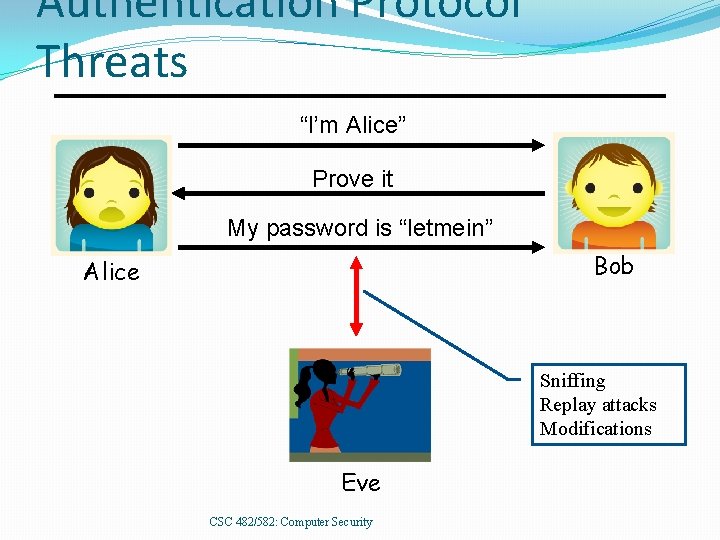
Authentication Protocol Threats “I’m Alice” Prove it My password is “letmein” Bob Alice Sniffing Replay attacks Modifications Eve CSC 482/582: Computer Security

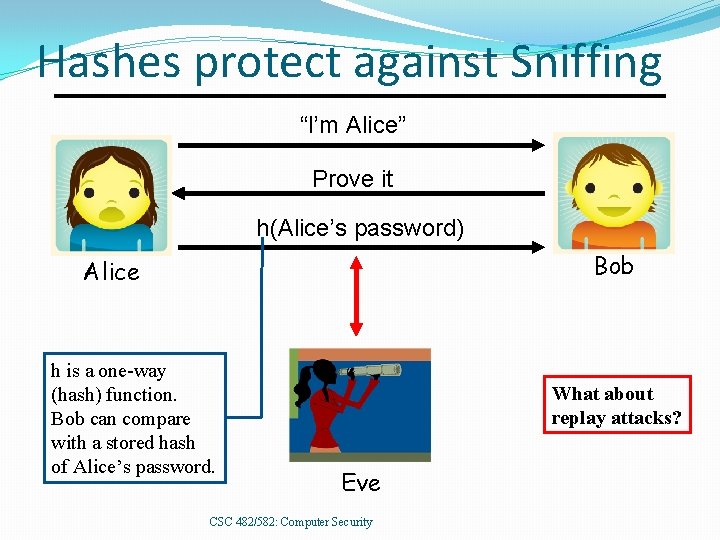
Hashes protect against Sniffing “I’m Alice” Prove it h(Alice’s password) Bob Alice h is a one-way (hash) function. Bob can compare with a stored hash of Alice’s password. What about replay attacks? Eve CSC 482/582: Computer Security

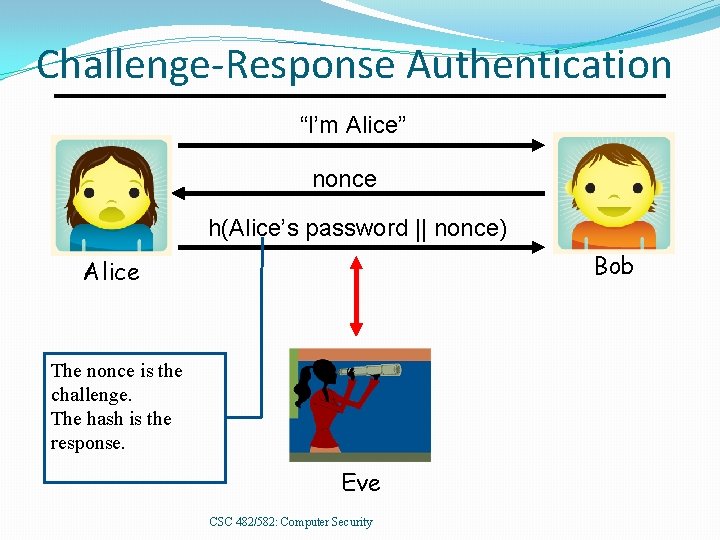
Challenge-Response Authentication “I’m Alice” nonce h(Alice’s password || nonce) Bob Alice The nonce is the challenge. The hash is the response. Eve CSC 482/582: Computer Security

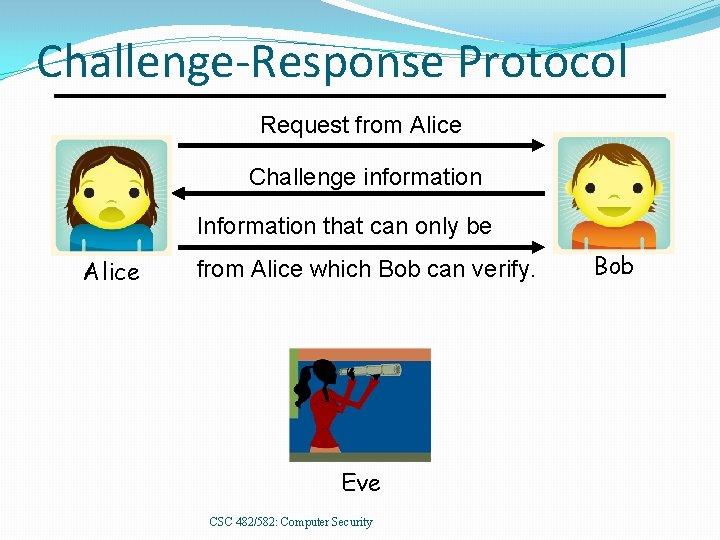
Challenge-Response Protocol Request from Alice Challenge information Information that can only be Alice from Alice which Bob can verify. Eve CSC 482/582: Computer Security Bob

Symmetric Key Problems 1. 2. 3. Keys must be distributed in secret. If key is compromised, Eve can decrypt all message traffic encrypted with key. If each pair of users needs a key, number of keys n(n-1) increases rapidly with size of network. CSC 482/582: Computer Security

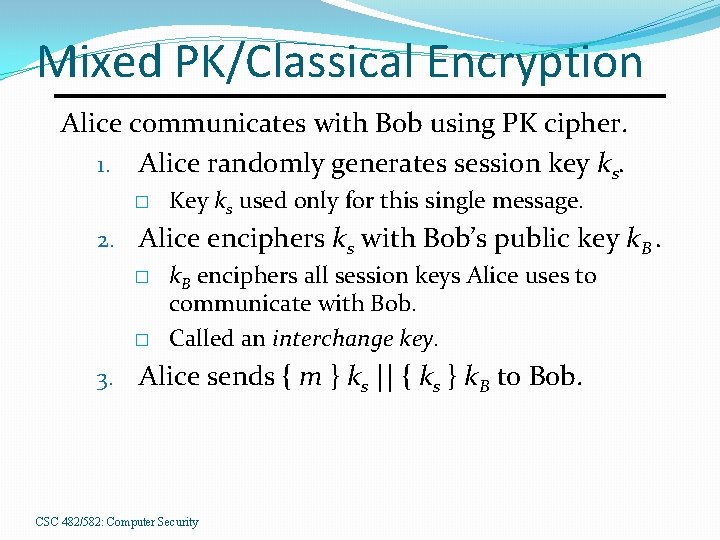
Mixed PK/Classical Encryption Alice communicates with Bob using PK cipher. 1. Alice randomly generates session key ks. � Key ks used only for this single message. 2. Alice enciphers ks with Bob’s public key k. B. � k. B enciphers all session keys Alice uses to communicate with Bob. � Called an interchange key. 3. Alice sends { m } ks || { ks } k. B to Bob. CSC 482/582: Computer Security

Session Key A key used to encrypt a single session. Advantages �Reduces data ciphered with a single key. �Protection against replay attacks. �Prevents forward search (dictionary) attack. Forward search example �Alice client of Bob’s brokerage. �Communicates with BUY and SELL messages. �Eve enciphers both messages with Bob’s key. �Compares intercepted traffic with ciphertext. CSC 482/582: Computer Security

Key Exchange Algorithms Goal: Alice, Bob obtain shared secret key. Requirements: �Key cannot be sent in clear: � Attacker can intercept key. � Key can be sent enciphered, or derived from exchanged data plus data not known to an eavesdropper. �Alice, Bob may trust third party (Cathy. ) �All cryptosystems, protocols publicly known � Only secret data is keys or data used to derive keys. � Anything transmitted is assumed known to attacker. CSC 482/582: Computer Security

Classical Key Exchange Bootstrap problem: how do Alice, Bob begin? �Alice can’t send it to Bob in the clear! Assume trusted third party, Cathy �Alice and Cathy share secret key k. A. �Bob and Cathy share secret key k. B. Let Cathy generate shared key ks. �Cathy can send it securely to either A or B. CSC 482/582: Computer Security

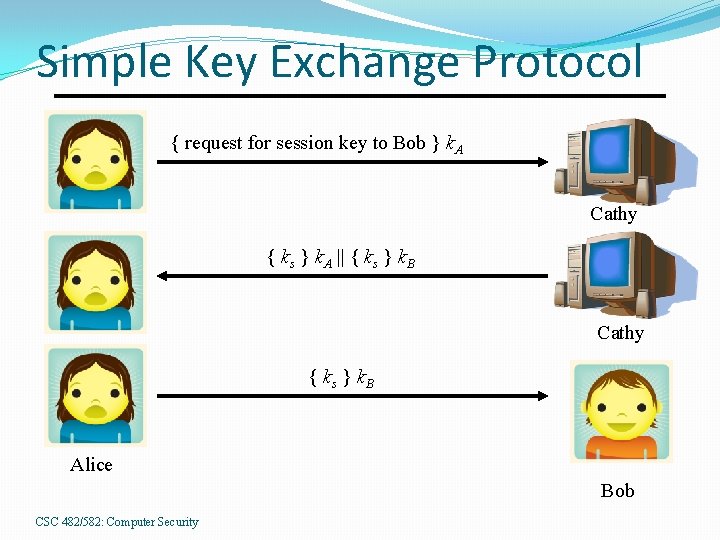
Simple Key Exchange Protocol { request for session key to Bob } k. A Cathy { ks } k. A || { ks } k. B Cathy { ks } k. B Alice Bob CSC 482/582: Computer Security

Simple Key Exchange Vulnerabilities How does Bob know he is talking to Alice? Replay attack: Eve records message from Alice to Bob, later replays it; Bob may think he’s talking to Alice, but he isn’t. Session key reuse: Eve replays key exchange message from Alice to Bob, so Bob re-uses session key. Protocols must provide authentication and defense against replay. CSC 482/582: Computer Security

Needham-Schroeder Alice || Bob || r 1 Alice { Alice || Bob || r 1 || ks || { Alice || ks } k. B } k. A Alice CSC 482/582: Computer Security { Alice || ks } k. B { r 2 } k s { r 2 – 1 } k s Cathy Bob Bob

Is Alice really talking to Bob? Second message �Cathy encrypted it, since only A, C know key k. A. �It must be a response to first message as contains r 1. Third message �Alice knows only Bob can read it since encrypted w/ k B. �Any messages enciphered with k. S are from Bob, since only Alice, Bob, and Cathy have k. S. CSC 482/582: Computer Security

Is Bob really talking to Alice? Third message �Cathy encrypted it, since only B, C know key k. B. �Cathy provides session key, says Alice is other party. Fourth message �Uses session key to determine if 3 rd was replay. � If not, Alice will respond correctly in fifth message. � If 3 rd message was replay attack, Eve can’t decipher r 2 and so can’t respond, or responds incorrectly. CSC 482/582: Computer Security

Needham-Schroeder Assumptions A trusted 3 rd party exists, Cathy. �Many transactions require 3 rd parties. Session keys are always secure. �What if Eve can obtain old keys? CSC 482/582: Computer Security

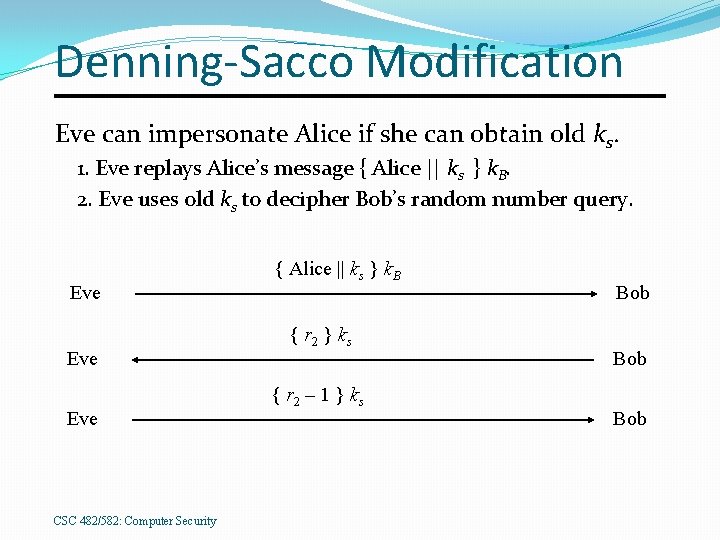
Denning-Sacco Modification Eve can impersonate Alice if she can obtain old ks. 1. Eve replays Alice’s message { Alice || ks } k. B. 2. Eve uses old ks to decipher Bob’s random number query. Eve Eve CSC 482/582: Computer Security { Alice || ks } k. B { r 2 } k s { r 2 – 1 } k s Bob Bob

Solution How can we avoid replay in step 3 of N-S? �Use time stamp T to detect replay. Weakness: if clocks not synchronized, may either reject valid messages or accept replays. �Parties with slow/fast clocks vulnerable to replay. �Resetting clock does not eliminate vulnerability. CSC 482/582: Computer Security

Needham-Schroeder + Denning-Sacco Mod Bob will reject message if timestamp T is too old. Alice || Bob || r 1 Alice { Alice || Bob || r 1 || ks || { Alice || T || ks } k. B } k. A Alice CSC 482/582: Computer Security { Alice || T || ks } k. B { r 2 } k s { r 2 – 1 } k s Cathy Bob Bob

Otway-Rees Protocol Corrects replay attack w/o timestamps. �Not vulnerable to clock skew problems of Denning- Sacco modification. Uses integer n to associate all messages with a particular exchange. CSC 482/582: Computer Security

Otway-Rees Protocol Alice Cathy n || Alice || Bob || { r 1 || n || Alice || Bob } k. A || { r 2 || n || Alice || Bob } k. B Cathy Alice CSC 482/582: Computer Security n || { r 1 || ks } k. A || { r 2 || ks } k. B n || { r 1 || ks } k. A Bob Bob

Argument: Alice talking to Bob Fourth message �If n matches first message, Alice knows it is part of this protocol exchange. �Cathy generated ks because only she & Alice know k. A. �Enciphered part belongs to exchange as r 1 matches r 1 in encrypted part of first message. CSC 482/582: Computer Security

Argument: Bob talking to Alice Third message �If n matches second message, Bob knows it is part of this protocol exchange. �Cathy generated ks because only she & Bob know k. B. �Enciphered part belongs to exchange as r 2 matches r 2 in encrypted part of second message. CSC 482/582: Computer Security

Defeating Replay Attacks Eve acquires old ks, message in third step: �n || { r 1 || ks } k. A || { r 2 || ks } k. B Eve forwards appropriate part to Alice: �Alice has no ongoing key exchange with Bob: n matches nothing, so is rejected. �Alice has ongoing key exchange with Bob: n does not match, so is again rejected. �If replay is for the current key exchange, and Eve sent the relevant part before Bob did, Eve could simply listen to traffic; no replay needed. CSC 482/582: Computer Security

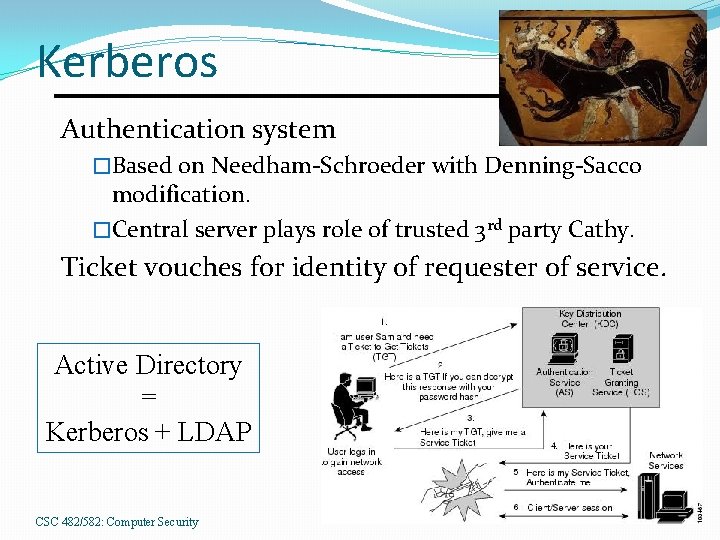
Kerberos Authentication system �Based on Needham-Schroeder with Denning-Sacco modification. �Central server plays role of trusted 3 rd party Cathy. Ticket vouches for identity of requester of service. Active Directory = Kerberos + LDAP CSC 482/582: Computer Security

Ticket Granting Service Requirement: Users only enter password once. �User u authenticates to Kerberos server. �Gets ticket Tu, TGS for ticket granting service (TGS) Requirement: Users don’t send password over net. CSC 482/582: Computer Security

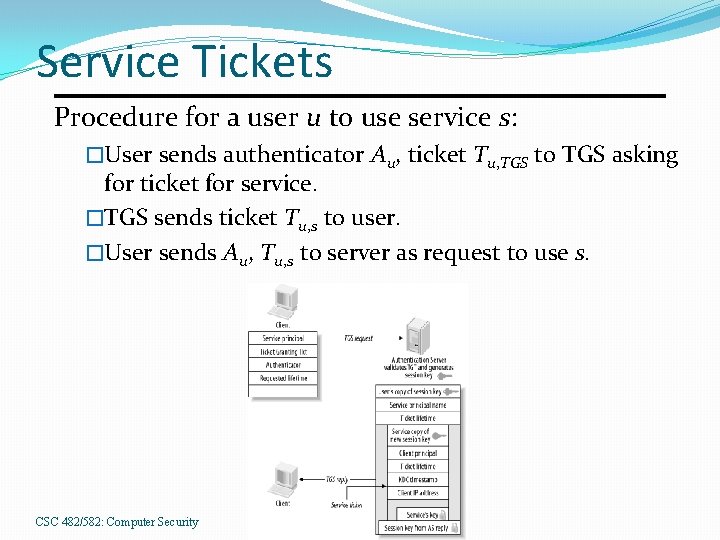
Service Tickets Procedure for a user u to use service s: �User sends authenticator Au, ticket Tu, TGS to TGS asking for ticket for service. �TGS sends ticket Tu, s to user. �User sends Au, Tu, s to server as request to use s. CSC 482/582: Computer Security

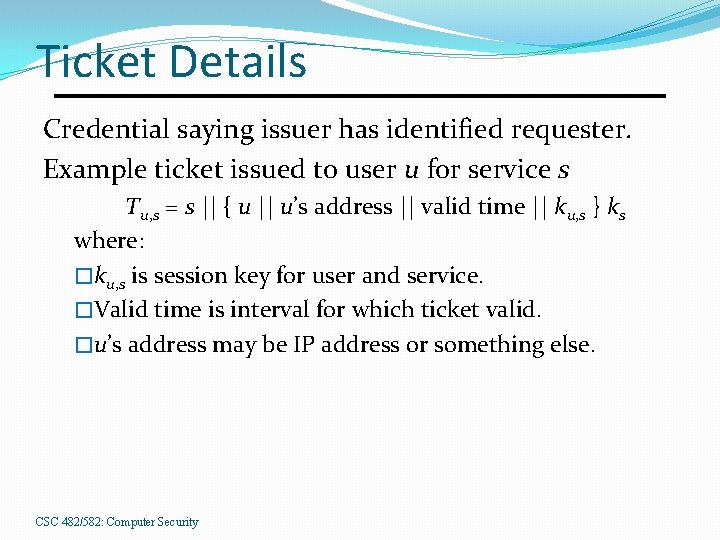
Ticket Details Credential saying issuer has identified requester. Example ticket issued to user u for service s Tu, s = s || { u || u’s address || valid time || ku, s } ks where: �ku, s is session key for user and service. �Valid time is interval for which ticket valid. �u’s address may be IP address or something else. CSC 482/582: Computer Security

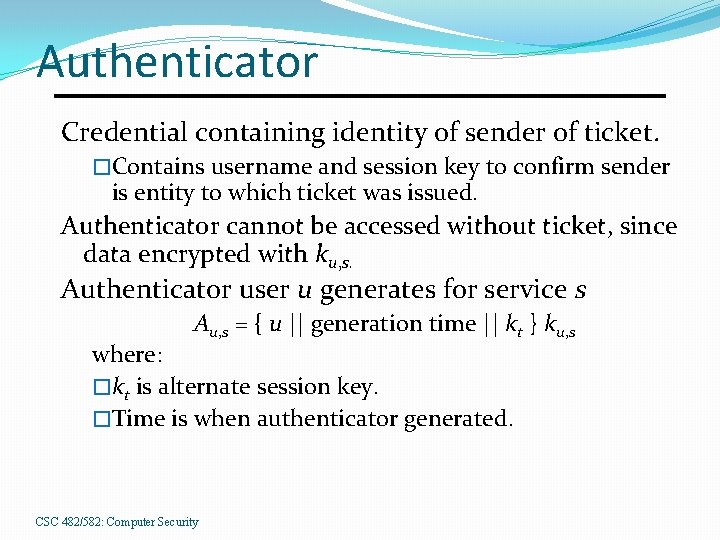
Authenticator Credential containing identity of sender of ticket. �Contains username and session key to confirm sender is entity to which ticket was issued. Authenticator cannot be accessed without ticket, since data encrypted with ku, s. Authenticator user u generates for service s Au, s = { u || generation time || kt } ku, s where: �kt is alternate session key. �Time is when authenticator generated. CSC 482/582: Computer Security

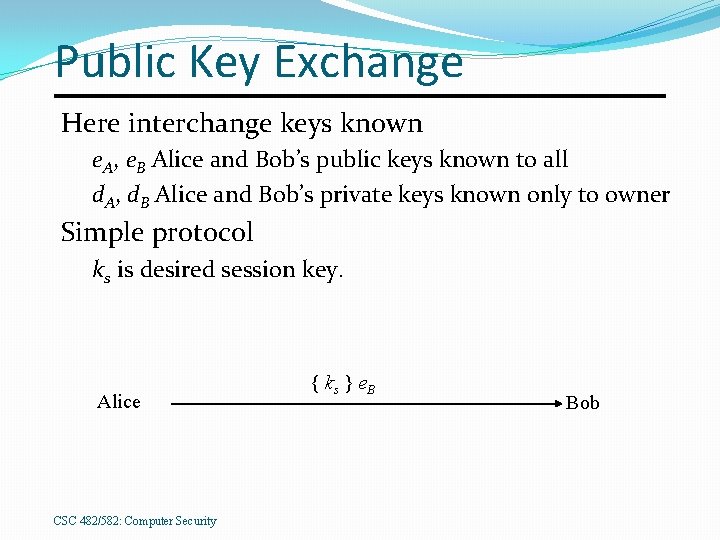
Public Key Exchange Here interchange keys known e. A, e. B Alice and Bob’s public keys known to all d. A, d. B Alice and Bob’s private keys known only to owner Simple protocol ks is desired session key. Alice CSC 482/582: Computer Security { ks } e. B Bob

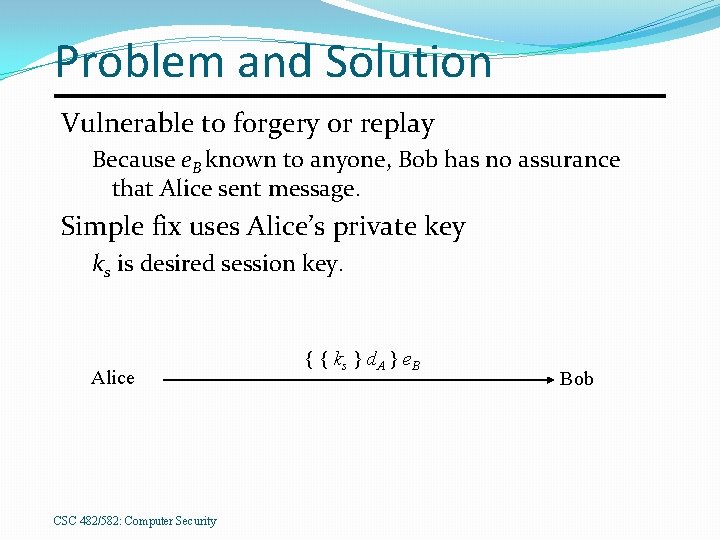
Problem and Solution Vulnerable to forgery or replay Because e. B known to anyone, Bob has no assurance that Alice sent message. Simple fix uses Alice’s private key ks is desired session key. Alice CSC 482/582: Computer Security { { ks } d. A } e. B Bob

Notes Can include message enciphered with ks Assumes Bob has Alice’s public key, and vice versa �If not, each must get it from public server. �If keys not bound to identity of owner, attacker Eve can launch a man-in-the-middle attack (next slide; Cathy is public server providing public keys. ) �Solution: Public key infrastructure (PKI) CSC 482/582: Computer Security

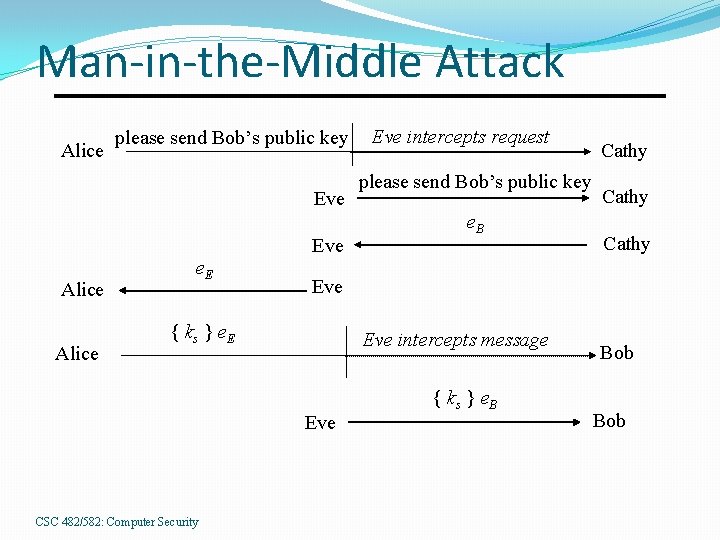
Man-in-the-Middle Attack Alice please send Bob’s public key Eve Alice e. E please send Bob’s public key e. B Cathy Eve { ks } e. E Eve intercepts message Eve CSC 482/582: Computer Security Eve intercepts request { ks } e. B Bob

Cryptographic Key Infrastructure Solution: bind identity to key Classical: not possible as all keys are shared �Use protocols to agree on a shared key (see earlier. ) Public key: bind identity to public key �Crucial as people will use key to communicate with principal whose identity is bound to key. �Erroneous binding means no secrecy between principals. �Assume principal identified by an acceptable name. CSC 482/582: Computer Security

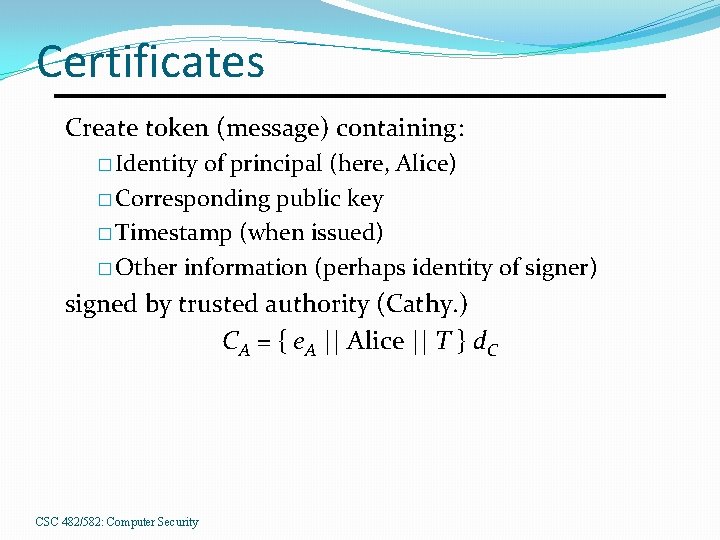
Certificates Create token (message) containing: � Identity of principal (here, Alice) � Corresponding public key � Timestamp (when issued) � Other information (perhaps identity of signer) signed by trusted authority (Cathy. ) CA = { e. A || Alice || T } d. C CSC 482/582: Computer Security

Use Bob downloads Alice’s certificate �If he knows Cathy’s public key, he can decipher the certificate � When was certificate issued? � Is the principal Alice? �Now Bob has Alice’s public key. Problem: Bob needs Cathy’s PK to validate cert. �Problem pushed up a level. �Solution: signature chains. CSC 482/582: Computer Security

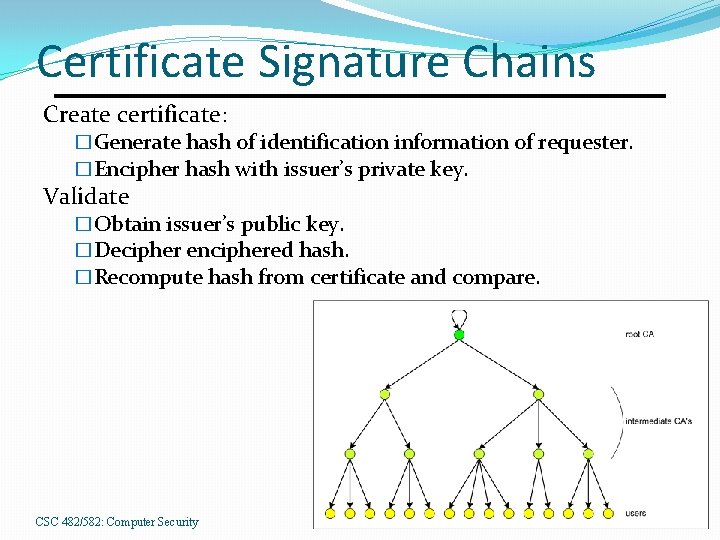
Certificate Signature Chains Create certificate: �Generate hash of identification information of requester. �Encipher hash with issuer’s private key. Validate �Obtain issuer’s public key. �Decipher enciphered hash. �Recompute hash from certificate and compare. CSC 482/582: Computer Security

X. 509 (SSL) Certificates Some certificate components in X. 509 v 3: �Version �Serial number �Signature algorithm identifier: hash algorithm �Issuer’s name; uniquely identifies issuer �Interval of validity �Subject’s name; uniquely identifies subject �Subject’s public key �Signature: enciphered hash CSC 482/582: Computer Security

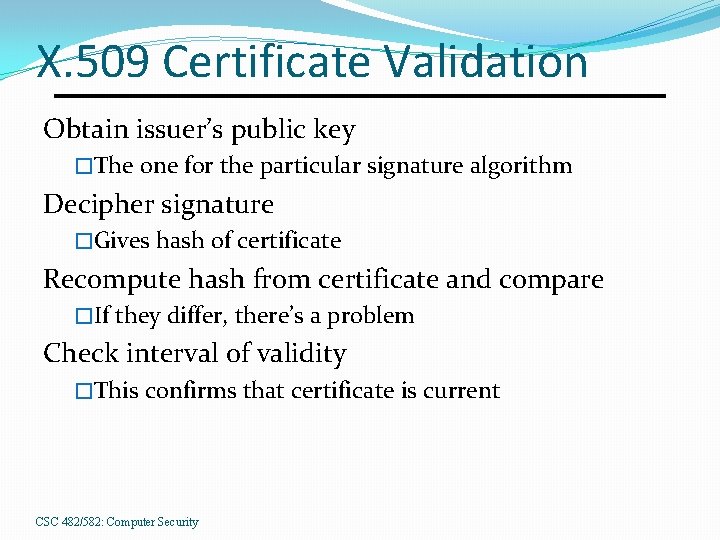
X. 509 Certificate Validation Obtain issuer’s public key �The one for the particular signature algorithm Decipher signature �Gives hash of certificate Recompute hash from certificate and compare �If they differ, there’s a problem Check interval of validity �This confirms that certificate is current CSC 482/582: Computer Security

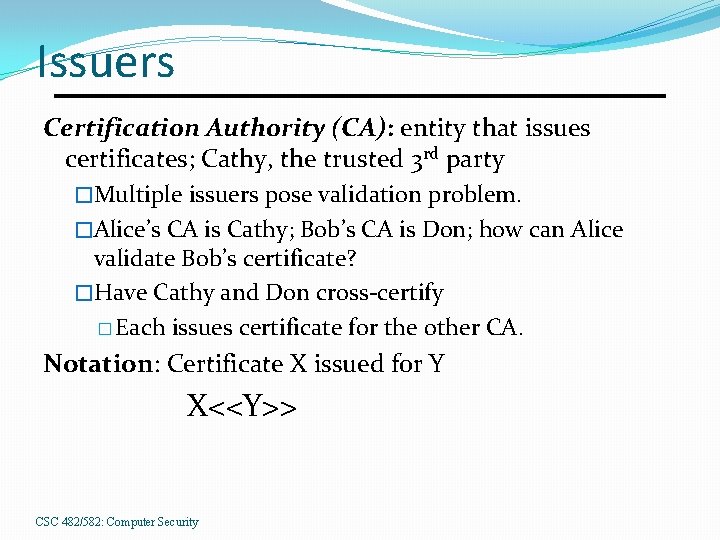
Issuers Certification Authority (CA): entity that issues certificates; Cathy, the trusted 3 rd party �Multiple issuers pose validation problem. �Alice’s CA is Cathy; Bob’s CA is Don; how can Alice validate Bob’s certificate? �Have Cathy and Don cross-certify � Each issues certificate for the other CA. Notation: Certificate X issued for Y X<<Y>> CSC 482/582: Computer Security

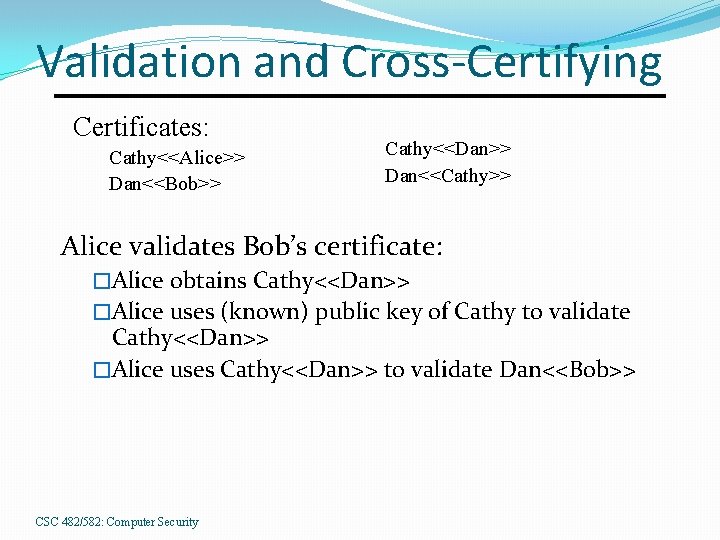
Validation and Cross-Certifying Certificates: Cathy<<Alice>> Dan<<Bob>> Cathy<<Dan>> Dan<<Cathy>> Alice validates Bob’s certificate: �Alice obtains Cathy<<Dan>> �Alice uses (known) public key of Cathy to validate Cathy<<Dan>> �Alice uses Cathy<<Dan>> to validate Dan<<Bob>> CSC 482/582: Computer Security

PGP Chains Open. PGP certificates verified via “web of trust” �No hierarchy of CAs to follow like SSL certificates �Certificates can be signed by multiple parties Open. PGP certificates structured into packets: �One public key packet. �Zero or more signature packets. CSC 482/582: Computer Security

Signing Single certificate may have multiple signatures. Notion of “trust” embedded in each signature �Range from “untrusted” to “ultimate trust. ” �Signer defines meaning of trust level (no standards!) All version 4 keys signed by subject �Called “self-signing. ” CSC 482/582: Computer Security

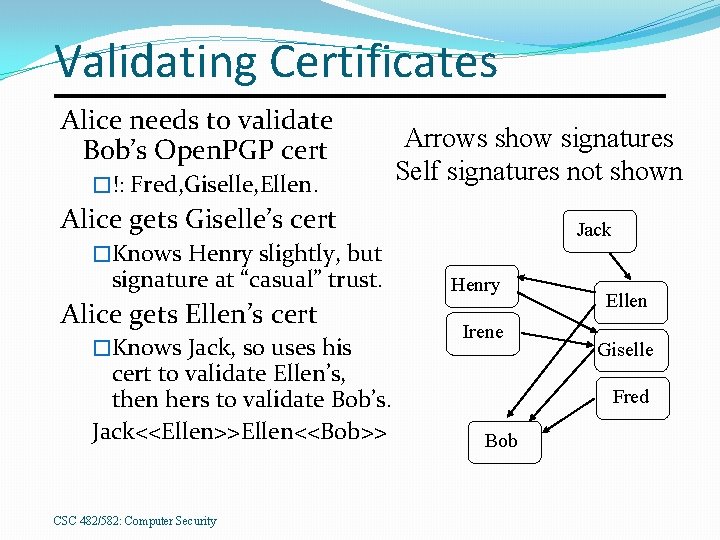
Validating Certificates Alice needs to validate Bob’s Open. PGP cert �!: Fred, Giselle, Ellen. Arrows show signatures Self signatures not shown Alice gets Giselle’s cert Jack �Knows Henry slightly, but signature at “casual” trust. Alice gets Ellen’s cert �Knows Jack, so uses his cert to validate Ellen’s, then hers to validate Bob’s. Jack<<Ellen>>Ellen<<Bob>> CSC 482/582: Computer Security Henry Irene Ellen Giselle Fred Bob

Storing Keys Multi-user or networked systems: attackers may defeat access control mechanisms. 1. Encipher file containing key. � � 2. Attacker can monitor keystrokes to decipher files Key will be resident in memory. Use physical devices like “smart card. ” � � Smart card performs encryption. Computer transfers plaintext to card. Card transfers ciphertext to computer. Card can be stolen, split key between two devices. CSC 482/582: Computer Security

Key Revocation Certificates invalidated before expiration �Usually due to compromised key. �May be due to change in circumstance (e. g. , someone leaving company. ) Problems �Is entity revoking certificate authorized to do so? �Can revocation information circulates to everyone quickly enough to avoid a compromise? CSC 482/582: Computer Security

CRLs A Certificate revocation lists certificates that are revoked, with their IDs and revocation dates. X. 509: only issuer can revoke certificate. PGP: signers can revoke signatures; owners can revoke certificates, or allow others to do so. �Revocation message placed in PGP packet and signed. �Flag marks it as revocation message. CSC 482/582: Computer Security

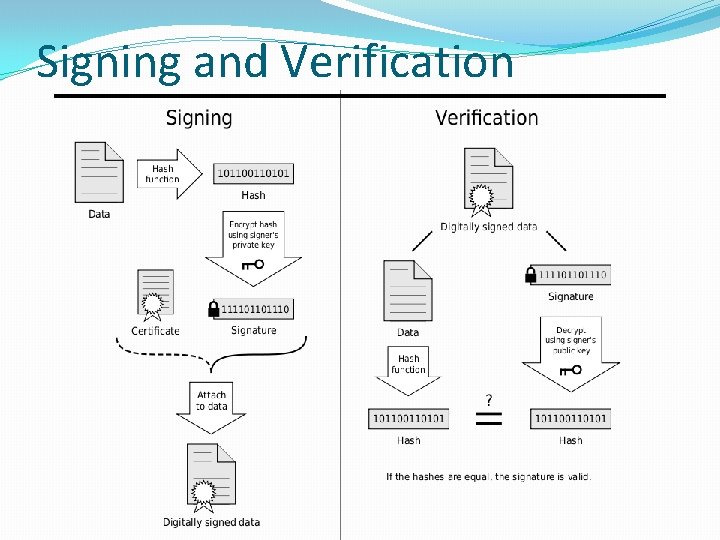
Digital Signature Construct that authenticates origin & contents of message in a manner provable to a disinterested third party (“judge. ”) Nonrepudiatable �Sender cannot deny having sent message. �Proves that sender’s key was used to sign message. �What if you claim key was stolen/compromised? � Court would have to decide. CSC 482/582: Computer Security

Signing and Verification

Key Points 1. Security protocols 1. 2. Definition and notation Authentication protocols 2. Key protocols critical to effective use of cryptosystems. 1. 2. Different levels of keys (session vs. interchange. ) Nonces, sequence numbers, timestamps to avoid replay attacks. 3. Keys require an infrastructure to identify holders and allow revocation. 1. 2. SSL certificates verified with hierarchy of CAs. PGP certificates verified via web of trust. 4. Digital signatures: integrity of origin and content. 1. Signature is hash of signed document that is encrypted with signer’s private key. CSC 482/582: Computer Security

References Matt Bishop, Introduction to Computer Security, Addison-Wesley, 2005. 2. Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone, Handbook of Applied Cryptography, http: //www. cacr. math. uwaterloo. ca/hac/, CRC Press, 1996. 3. Bruce Schneier, Applied Cryptography, 2 nd edition, Wiley, 1996. 4. John Viega and Gary Mc. Graw, Building Secure Software, Addison-Wesley, 2002. 1. CSC 482/582: Computer Security