CSC 482582 Computer Security Applying Cryptography CSC 482582








- Slides: 37

CSC 482/582: Computer Security Applying Cryptography CSC 482/582: Computer Security

Topics 1. 2. 3. 4. 5. 6. 7. Applications of Randomness Defining and Evaluating Randomness Pseudo-Random Number Generators (PRNGs) Cryptographically Secure PRNGs (CSPRNGs) Attacks on PRNGs Entropy Gathering Storing Secrets CSC 482/582: Computer Security

Key Generation Goal: generate difficult to guess keys Given set of K potential keys, choose one randomly. �Equivalent to selecting a random number between 0 and K– 1 inclusive. Difficulty: generating random numbers �Software generated numbers are pseudo-random, that is, generated by an algorithm. �If you start with the same random seed, then software random number generators will produce the same sequence of numbers each time. CSC 482/582: Computer Security

Cryptographic Use of Randomness 1. Generation of session keys. 2. Seeds for routines that generate large prime numbers for public key ciphers like RSA. 3. Salts for password hashing. 4. Initialization vectors for block cipher chaining modes. 5. Nonces for cryptographic protocols. CSC 482/582: Computer Security

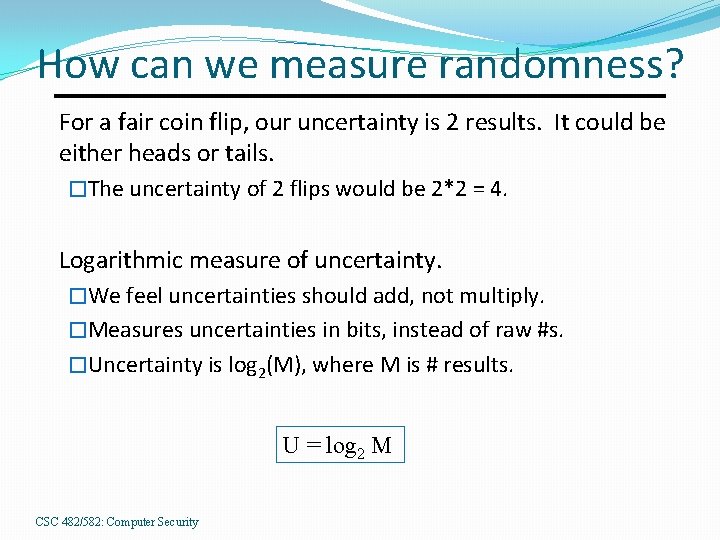
How can we measure randomness? For a fair coin flip, our uncertainty is 2 results. It could be either heads or tails. �The uncertainty of 2 flips would be 2*2 = 4. Logarithmic measure of uncertainty. �We feel uncertainties should add, not multiply. �Measures uncertainties in bits, instead of raw #s. �Uncertainty is log 2(M), where M is # results. U = log 2 M CSC 482/582: Computer Security

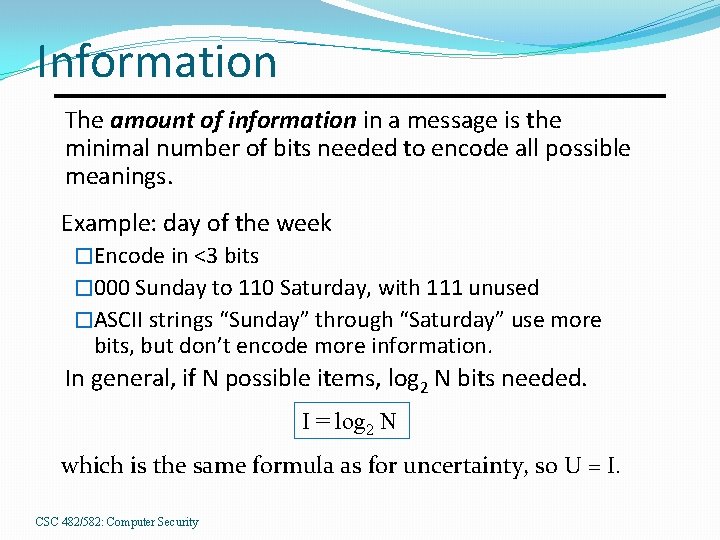
Information The amount of information in a message is the minimal number of bits needed to encode all possible meanings. Example: day of the week (7 possibilities) �Encode in 3 bits � 000 Sunday to 110 Saturday, with 111 unused �ASCII strings “Sunday” through “Saturday” use more bits, but don’t encode more information. CSC 482/582: Computer Security

Information The amount of information in a message is the minimal number of bits needed to encode all possible meanings. Example: day of the week �Encode in <3 bits � 000 Sunday to 110 Saturday, with 111 unused �ASCII strings “Sunday” through “Saturday” use more bits, but don’t encode more information. In general, if N possible items, log 2 N bits needed. I = log 2 N which is the same formula as for uncertainty, so U = I. CSC 482/582: Computer Security

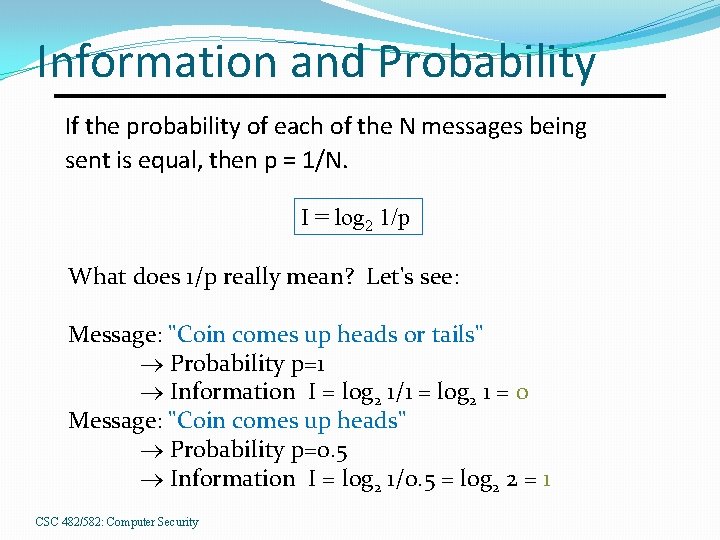
Information and Probability If the probability of each of the N messages being sent is equal, then p = 1/N. I = log 2 1/p What does 1/p really mean? Let's see: Message: "Coin comes up heads or tails" Probability p=1 Information I = log 2 1/1 = log 2 1 = 0 Message: "Coin comes up heads" Probability p=0. 5 Information I = log 2 1/0. 5 = log 2 2 = 1 CSC 482/582: Computer Security

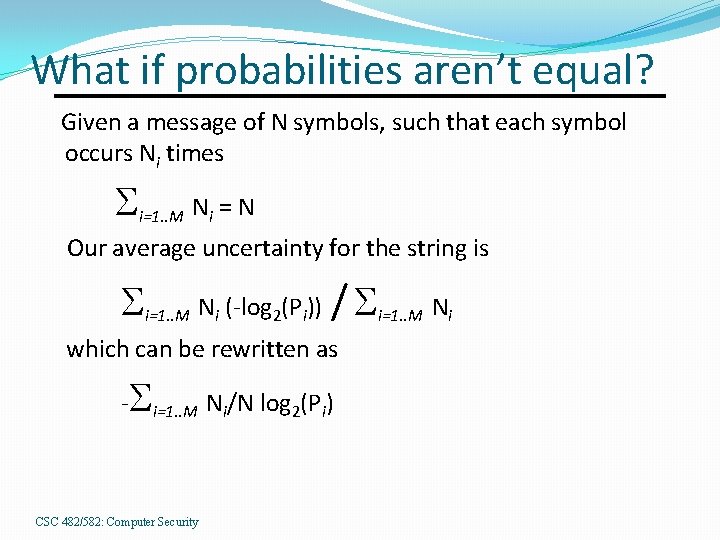
What if probabilities aren’t equal? Given a message of N symbols, such that each symbol occurs Ni times i=1. . M Ni = N Our average uncertainty for the string is / i=1. . M Ni (-log 2(Pi)) i=1. . M Ni which can be rewritten as - i=1. . M Ni/N log 2(Pi) CSC 482/582: Computer Security

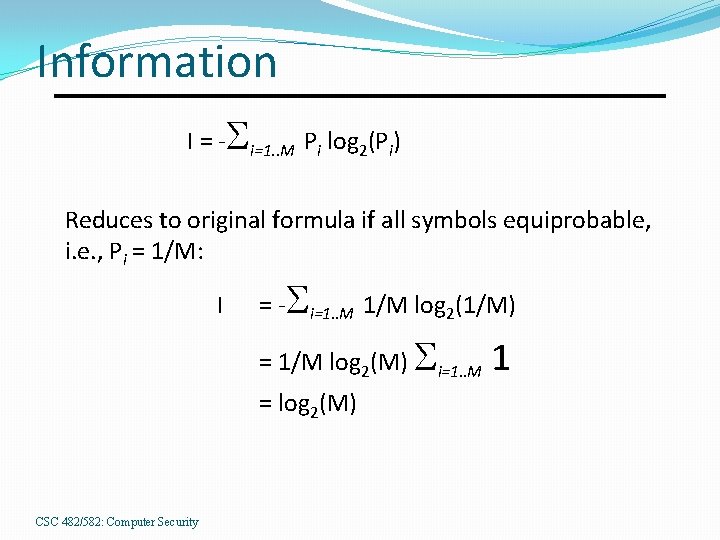
Information I = - i=1. . M Pi log 2(Pi) Reduces to original formula if all symbols equiprobable, i. e. , Pi = 1/M: I = - i=1. . M 1/M log 2(1/M) = 1/M log 2(M) i=1. . M 1 = log 2(M) CSC 482/582: Computer Security

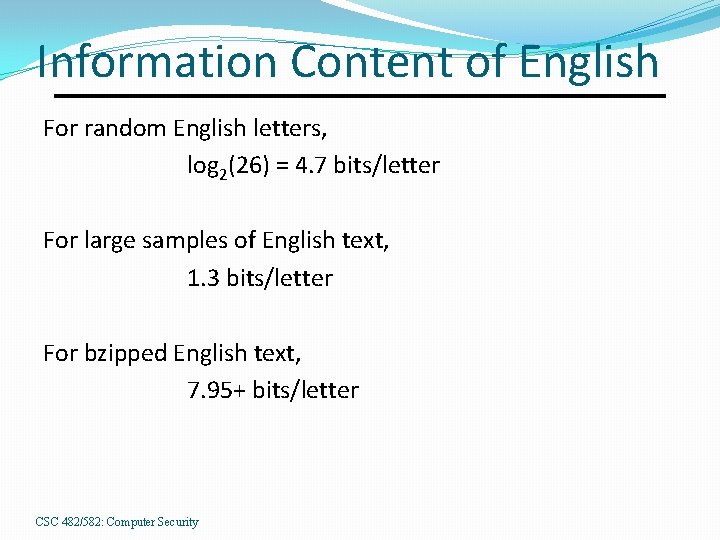
Information Content of English For random English letters, log 2(26) = 4. 7 bits/letter For large samples of English text, 1. 3 bits/letter For bzipped English text, 7. 95+ bits/letter CSC 482/582: Computer Security

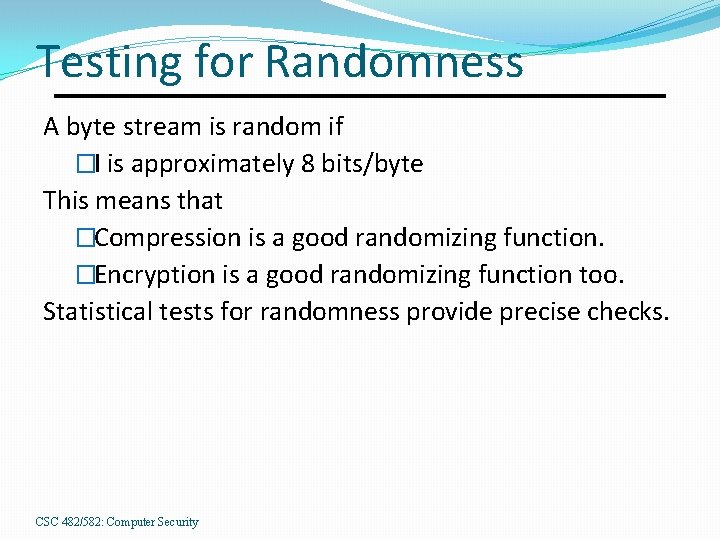
Testing for Randomness A byte stream is random if �I is approximately 8 bits/byte This means that �Compression is a good randomizing function. �Encryption is a good randomizing function too. Statistical tests for randomness provide precise checks. CSC 482/582: Computer Security

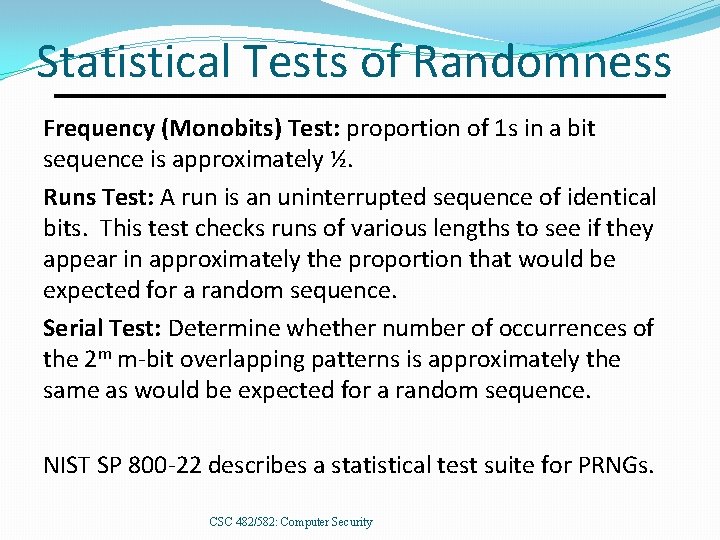
Statistical Tests of Randomness Frequency (Monobits) Test: proportion of 1 s in a bit sequence is approximately ½. Runs Test: A run is an uninterrupted sequence of identical bits. This test checks runs of various lengths to see if they appear in approximately the proportion that would be expected for a random sequence. Serial Test: Determine whether number of occurrences of the 2 m m-bit overlapping patterns is approximately the same as would be expected for a random sequence. NIST SP 800 -22 describes a statistical test suite for PRNGs. CSC 482/582: Computer Security

PRNGs 1. 2. 3. 4. 5. 6. Seeding the PRNG Linear Congruential CSPNRGs Blum-Shub Tiny Attacks on PNRGs CSC 482/582: Computer Security

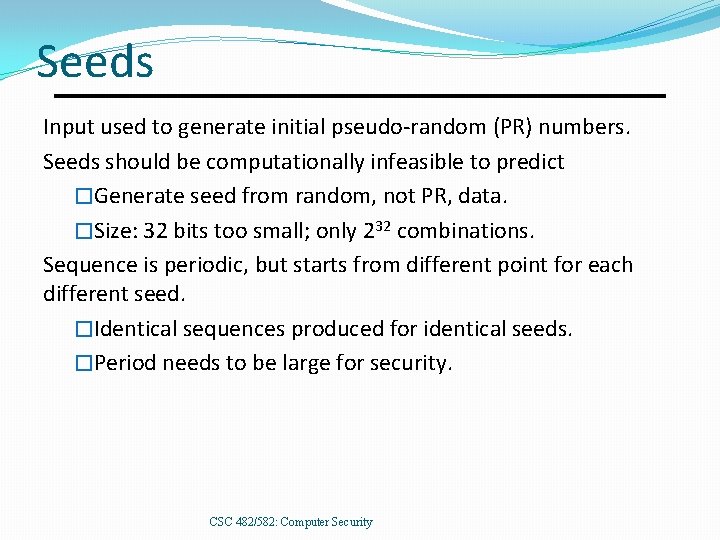
Seeds Input used to generate initial pseudo-random (PR) numbers. Seeds should be computationally infeasible to predict �Generate seed from random, not PR, data. �Size: 32 bits too small; only 232 combinations. Sequence is periodic, but starts from different point for each different seed. �Identical sequences produced for identical seeds. �Period needs to be large for security. CSC 482/582: Computer Security

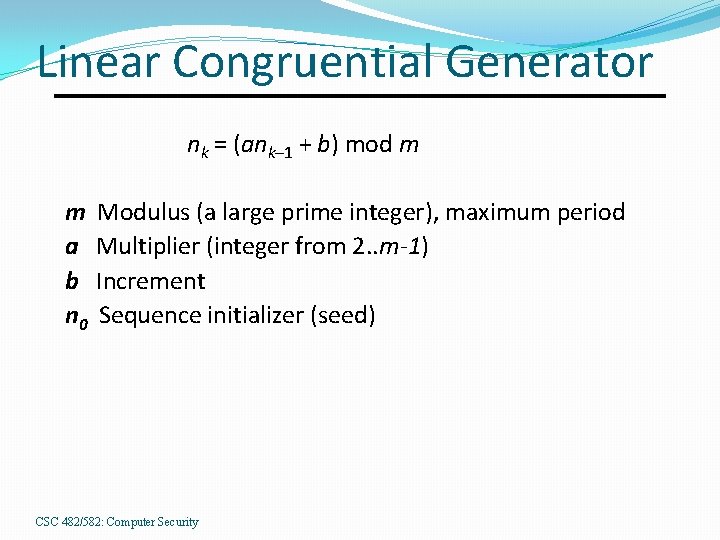
Linear Congruential Generator nk = (ank– 1 + b) mod m m Modulus (a large prime integer), maximum period a Multiplier (integer from 2. . m-1) b Increment n 0 Sequence initializer (seed) CSC 482/582: Computer Security

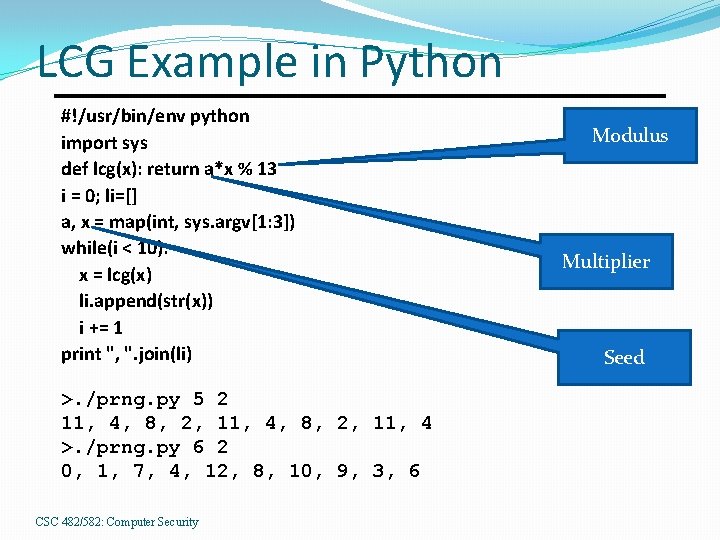
LCG Example in Python #!/usr/bin/env python import sys def lcg(x): return a*x % 13 i = 0; li=[] a, x = map(int, sys. argv[1: 3]) while(i < 10): x = lcg(x) li. append(str(x)) i += 1 print ", ". join(li) >. /prng. py 5 2 11, 4, 8, 2, 11, 4 >. /prng. py 6 2 0, 1, 7, 4, 12, 8, 10, 9, 3, 6 CSC 482/582: Computer Security Modulus Multiplier Seed

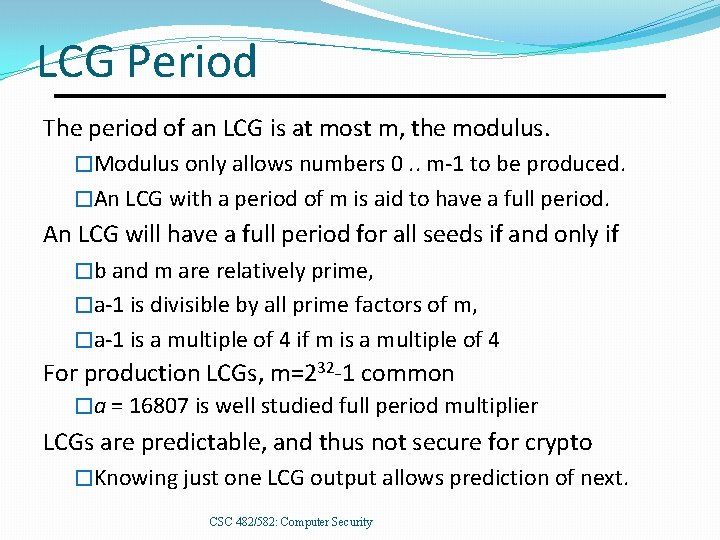
LCG Period The period of an LCG is at most m, the modulus. �Modulus only allows numbers 0. . m-1 to be produced. �An LCG with a period of m is aid to have a full period. An LCG will have a full period for all seeds if and only if �b and m are relatively prime, �a-1 is divisible by all prime factors of m, �a-1 is a multiple of 4 if m is a multiple of 4 For production LCGs, m=232 -1 common �a = 16807 is well studied full period multiplier LCGs are predictable, and thus not secure for crypto �Knowing just one LCG output allows prediction of next. CSC 482/582: Computer Security

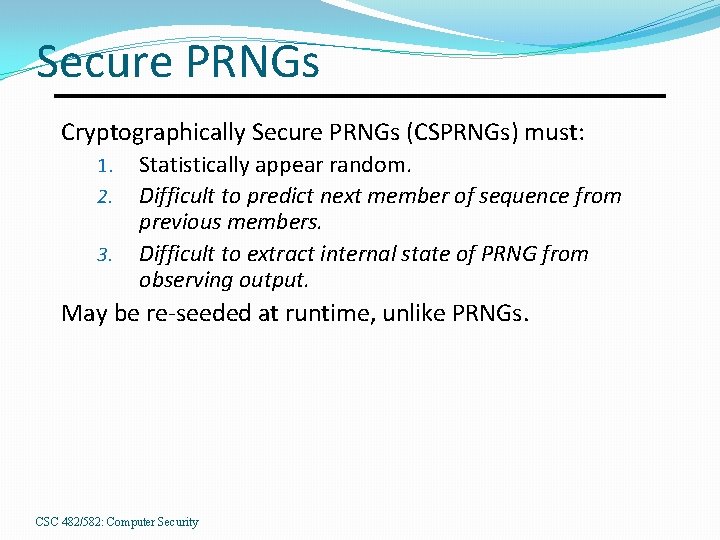
Secure PRNGs Cryptographically Secure PRNGs (CSPRNGs) must: 1. 2. 3. Statistically appear random. Difficult to predict next member of sequence from previous members. Difficult to extract internal state of PRNG from observing output. May be re-seeded at runtime, unlike PRNGs. CSC 482/582: Computer Security

Classes of CSPRNGs 1. Designs based on cryptographic primitives � Based on block cipher in counter mode or � Use a secure hash of a counter. 2. Number theoretic designs � Based on hard mathematical problems. � Example: Blum Shub 3. Special purpose designs � May introduce extra entropy when available. � Example: Yarrow (Free. BSD, Mac OS X) CSC 482/582: Computer Security

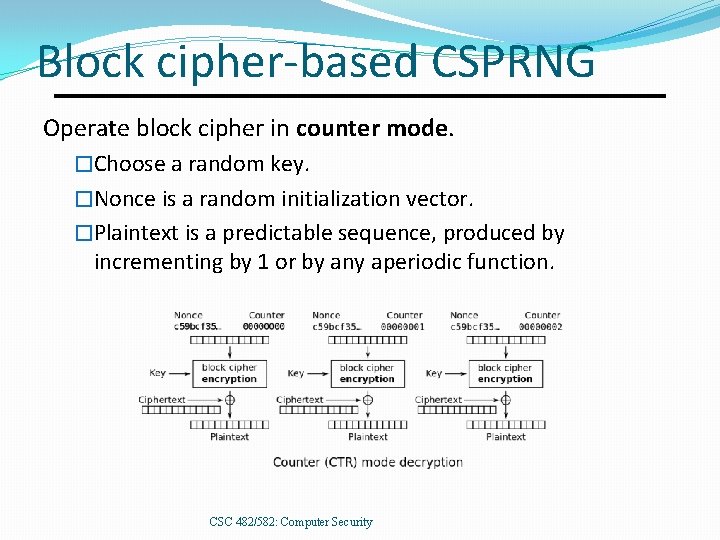
Block cipher-based CSPRNG Operate block cipher in counter mode. �Choose a random key. �Nonce is a random initialization vector. �Plaintext is a predictable sequence, produced by incrementing by 1 or by any aperiodic function. CSC 482/582: Computer Security

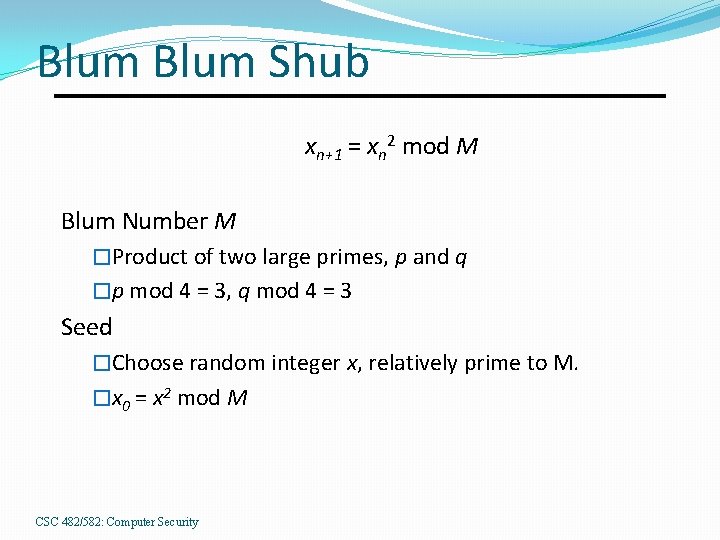
Blum Shub xn+1 = xn 2 mod M Blum Number M �Product of two large primes, p and q �p mod 4 = 3, q mod 4 = 3 Seed �Choose random integer x, relatively prime to M. �x 0 = x 2 mod M CSC 482/582: Computer Security

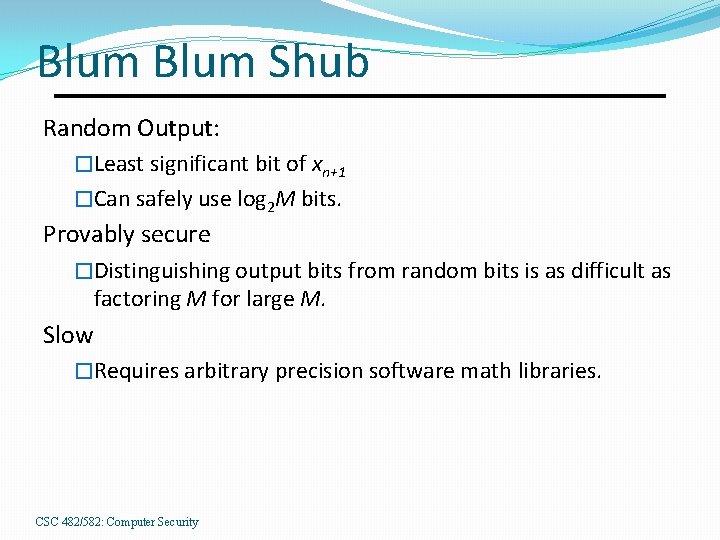
Blum Shub Random Output: �Least significant bit of xn+1 �Can safely use log 2 M bits. Provably secure �Distinguishing output bits from random bits is as difficult as factoring M for large M. Slow �Requires arbitrary precision software math libraries. CSC 482/582: Computer Security

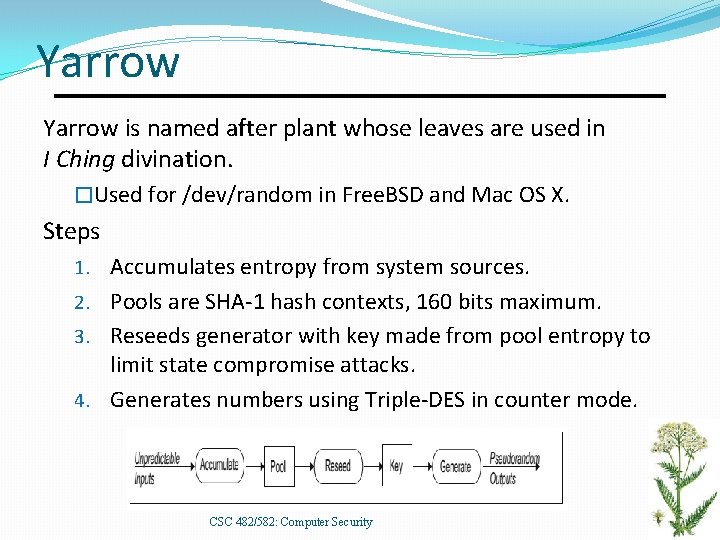
Yarrow is named after plant whose leaves are used in I Ching divination. �Used for /dev/random in Free. BSD and Mac OS X. Steps 1. Accumulates entropy from system sources. 2. Pools are SHA-1 hash contexts, 160 bits maximum. 3. Reseeds generator with key made from pool entropy to limit state compromise attacks. 4. Generates numbers using Triple-DES in counter mode. CSC 482/582: Computer Security

Attacks on PNRGs Direct Cryptanalytic �Distinguish between PRNG output and random output with better than 50% accuracy. Input-Based �Use knowledge of PRNG input to predict output, or �Insert input into PRNG to control output. State Compromise Extension �Extend previously successful attack that has recovered internal state to recover either or both: � past unknown PRNG outputs � future PRNG outputs after additional inputs given to PRNG CSC 482/582: Computer Security

ASF On-line Gambling Re-seeded PRNG before each shuffle �always start with ordered deck. Shuffling �Fair: 52! @ 2226 combinations � 32 -bit seed: 232 combinations �ms seed: 86, 400, 000 combinations �synchronize time: 200, 000 combinations Predict deck based on 5 known cards. CSC 482/582: Computer Security

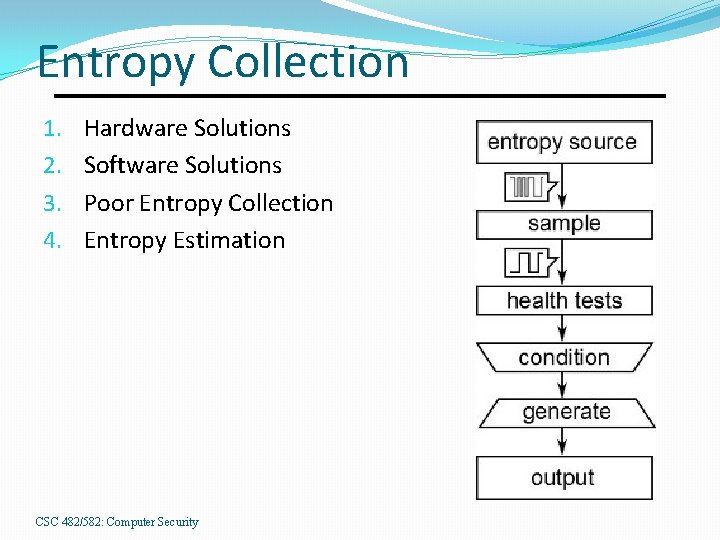
Entropy Collection 1. 2. 3. 4. Hardware Solutions Software Solutions Poor Entropy Collection Entropy Estimation CSC 482/582: Computer Security

Hardware Sources Radioactive Decay �Hotbits: 256 bits/s �http: //www. fourmilab. ch/hotbits/ Thermal or Electrical Noise �Comscire QNG Model J 1000 KU, 1 Mbit/s �Digital RNG (DRNG) on Ivy Bridge and later Intel CPUs Lava. Rnd �SGI used Lava. Lite; Lava. Rnd uses lenscapped digicam �http: //www. lavarnd. org/ �up to 200 kbits/s CSC 482/582: Computer Security

Software Sources Less Secure, More Convenient �Software systems can be sufficiently complex to be almost impossible to predict. �Example: time between user keystrokes or mouse events. User Input: Push, don’t Pull �Record time stamp when keystroke or mouse event occurs. �Don’t poll most recent user input every. 1 s � Far fewer possible timestamps. UNIX systems provide via /dev/random �User inputs, network inputs, disk seeks, etc. with an algorithm like Yarrow to aggregate entropy and reseed. CSC 482/582: Computer Security

Linux Sources: /dev/random �each bit is truly random. �blocks unless enough random bits are available. /dev/urandom �supplies requested number of bits immediately. �reuses current state of pool—lower quality randomness. CSC 482/582: Computer Security

Poor Entropy: Netscape 1. 1 SSL encryption �generates random 40 - or 128 -bit session key �Netscape 1. 1 seeded PRNG with � time of day � PID and PPID �All visible to attacker on same machine. Remote attack broke keys in 30 seconds �guessed limited randomness in PID/PPID. �packet sniffing can determine time of day. CSC 482/582: Computer Security

Random Number APIs Windows �rand() – insecure PRNG, uses LCG �Crypt. Gen. Random() – CSRNG �Crypt. Gen. Key() – to securely generate keys Java �java. util. Random – insecure PRNG �java. security. Secure. Random – CSRNG �Relies on OS, so Secure. Random can fall back to insecure Random if OS does not provide /dev/random or similar CSC 482/582: Computer Security

Key Storage Source Code � Can use strings command to extract from binary. File on Disk � Attacker can search disk for files with high entropy, which are likely to contain keys. � Encryption of file adds another layer of difficulty, but there must be a key someplace. Many languages provide APIs for storing keys or certificates in encrypted files. Registry � Attacker can access with regedit. External Device, e. g. smartcards, smartphones, remote server, … � Attacker can obtain PINs or use power analysis attackers to extract keys from device. � Remote servers can be compromised too. Store parts of key in different places � Break up key, then store part in source, part in file, part in db, etc. CSC 482/582: Computer Security

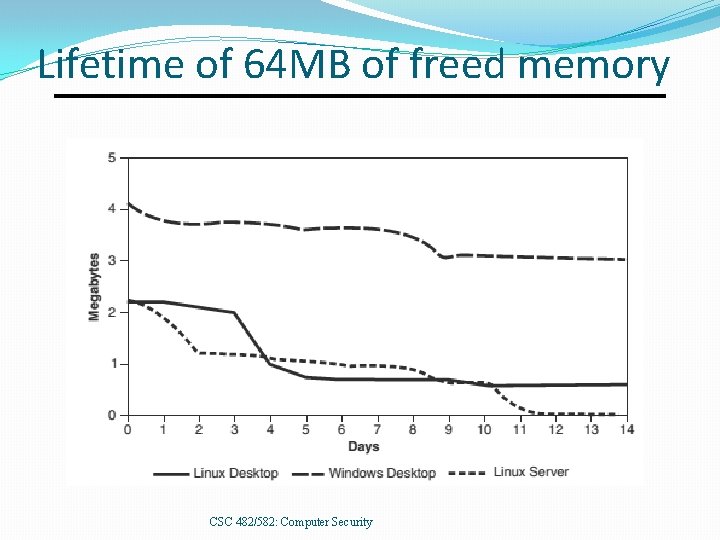
Lifetime of 64 MB of freed memory CSC 482/582: Computer Security

Key Storage in Memory 1. Minimize time spent holding secrets. �Load only when needed. �Erase when not needed any longer. �Prevent pages with secrets from being written to disk. � mlock() and munlock() in UNIX � Virtual. Lock() and Virtual. Un. Lock() in MS Windows 2. Erase secrets securely. �Use memset() to overwrite secret with zeros. 3. Prevent unnecessary duplication. �Avoid realloc() in C. If your threat model includes attacks on secrets in memory, then you cannot use a garbage-collected language like Java or Python. CSC 482/582: Computer Security

Key Points 1. 2. 3. 4. 5. 1. 2. Measuring randomness Measure information (entropy) content. Statistical tests: frequency of 1 s, bit sequences, etc. CSPRNGs must have the following qualities: 1. 2. 3. Statistically appear random. Difficult to predict next member of sequence from previous members. Difficult to extract internal state of PRNG from observing output. 1. 2. Linear congruential generators are insecure. CSPRNG types: cipher-based, algorithmic, special designs. 1. 2. Hardware RNGs: thermal noise, radioactive decay. Software RNGs: disk seeks, interrupts, time btw keystrokes. 1. 2. Permanent: disk, db, registry, hardware device. In memory: minimize time holding secrets, erase securely. Algorithmic PRNG techniques: Computer sources of randomness: Securely storing keys: CSC 482/582: Computer Security

References 1. 2. 3. 4. 5. 6. 7. 8. 9. Brian Chess and Jacob West. Secure programming with static analysis. Pearson Education, 2007. D. Eastlake, “Randomness Recommendations for Security, ” RFC 1750, http: //www. ietf. org/rfc 1750. txt, 1994. Ian Goldberg and David Wagner, “Randomness and the Netscape Browser, ” Doctor Dobbs’ Journal, 1996. http: //www. cs. berkeley. edu/~daw/papers/ddjnetscape. html John Kelsey, Bruce Schneier, and Niels Ferguson. "Yarrow-160: Notes on the design and analysis of the yarrow cryptographic pseudorandom number generator. " Selected Areas in Cryptography. Springer Berlin Heidelberg, 2000. Alfred J. Menezes, Paul C. van Oorschot and Scott A. Vanstone, Handbook of Applied Cryptography, http: //www. cacr. math. uwaterloo. ca/hac/, CRC Press, 1996. S. K. Park, K. W. Miller, “Random number generators: good ones are hard to find, ” Communications of the ACM, Volume 31 Issue 10 , October 1988. John R. Pierce, An Introduction to Information Theory, Dover Press, 1980. Tom Schneider, “Information Theory Primer, ” http: //www. lecb. ncifcrf. gov/~toms/paper/primer/, 2000. Bruce Schneier, Applied Cryptography, 2 nd edition, Wiley, 1996. CSC 482/582: Computer Security