CSC 482582 Computer Security Election Security CSC 482582



























- Slides: 50

CSC 482/582: Computer Security Election Security CSC 482/582: Computer Security

Topics 1. 2. 3. 4. 5. Voting rights History of voting Election systems Electronic voting Campaign security CSC 482/582: Computer Security

Voting Rights Poll Do we have a right to vote? CSC 482/582: Computer Security

No Constitutional Right to Vote • Constitution does not describe a right to vote or indicate who can vote. • Bush v. Gore: SCOTUS majority concluded: "the individual citizen has no federal constitutional right to vote for electors for the President of the United States. " (Bush v. Gore, 531 U. S. 98, 104 (200 • States are responsible for determining who can vote. • States have had widely varying standards. • In most states, prisoners cannot vote, and in former confederate states, many states prevent some or all former felons from voting. CSC 482/582: Computer Security

U. S. Voting Rights • 1789: U. S. Constitution allow states to determine who could vote. Financial requirements, such as property ownership limited franchise to 6% of the population. • 1800: States begin to require voters to be citizens, not inhabitants. • 1807: New Jersey removes property requirement and bans women and free blacks from voting, including those who voted before. • 1840: Illinois allows non-citizen immigrants to vote, starting a wave of western states doing so to attract settlers. • 1856: North Carolina is last state to abolish property ownership requirement. Five states still have tax paying requirements. • 1870: 15 th Amendment prevent states from limiting voting rights based on "race, color, or previous condition of servitude". CSC 482/582: Computer Security

U. S. Voting Rights • 1877: Reconstruction ends. Jim Crow laws disenfranchise African Americans with poll taxes, literacy requirements, and grandfather clauses. • 1898: MA employers threaten striking workers with disenfranchisement, as they are unemployed paupers. • 1920: 19 th Amendment grants women the right to vote. • 1948: Native Americans in all states eligible to vote. • 1961: 23 rd Amendment grants D. C. residents the right to vote for President. • 1964: 24 th Amendments prevents poll taxes from being used to prohibit voting in federal elections. • 1965: 26 th Amendment grants voting rights to citizens aged 18 -21 years. Voting Rights Act ends Jim Crow rules. CSC 482/582: Computer Security

Factors affecting Right to Vote Factors towards reduction of voting rights • Racism • Sexism • Classism (Property requirements from 40 acres to a freehold) • Religion (Catholics and Jews couldn't vote in some states) • Citizenship status (immigrants, US territories) Factors towards expansion of voting rights • War (soldiers think they should be able to vote) • Growth of cities • Increased education CSC 482/582: Computer Security

How to win: control who votes • Limit who can vote (voting rights above) • By law (age, race, sex, citizenship, wealth) • Poll taxes, tests, voter ID • Limit who goes to the polls • Increase/decrease voter registration • Reduce voting times • Close polling places • Limit who votes at the polls • Difficult to reach locations and long lines, but also • Voter intimidation: RNC hired off-duty police officers in NJ 1981 election as members of "National Ballot Security Task Force" • Consent decree requiring pre-approval of such operations was allowed to expire in 1981. CSC 482/582: Computer Security

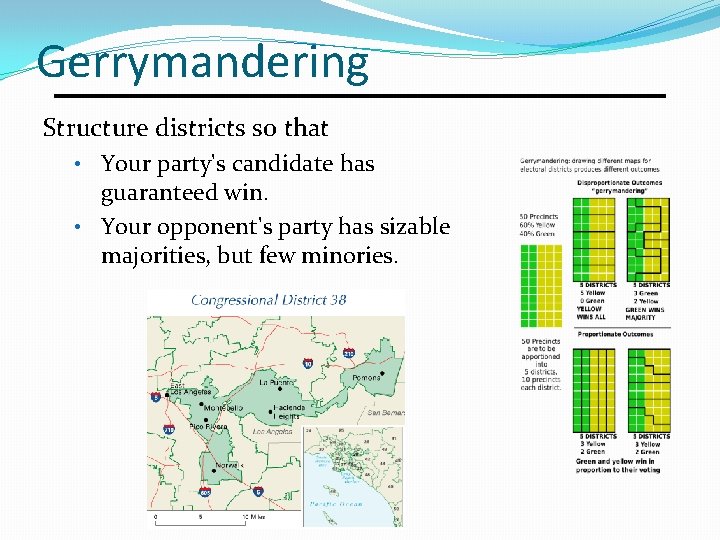
Gerrymandering Structure districts so that • Your party's candidate has guaranteed win. • Your opponent's party has sizable majorities, but few minories. CSC 482/582: Computer Security

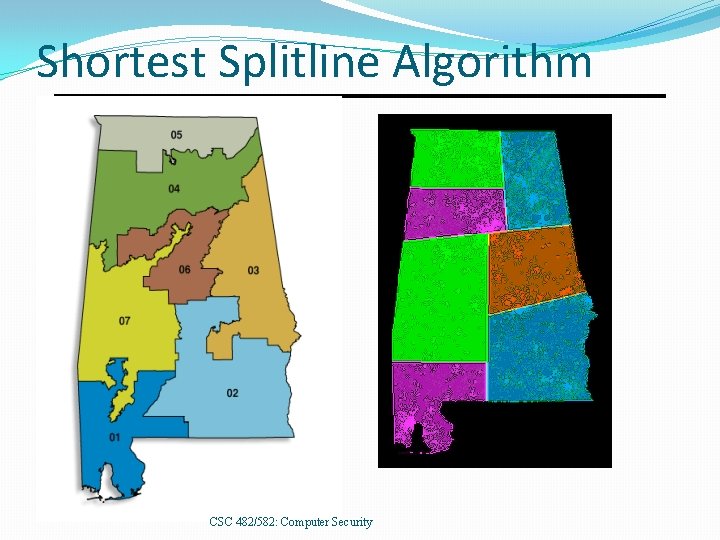
Shortest Splitline Algorithm CSC 482/582: Computer Security

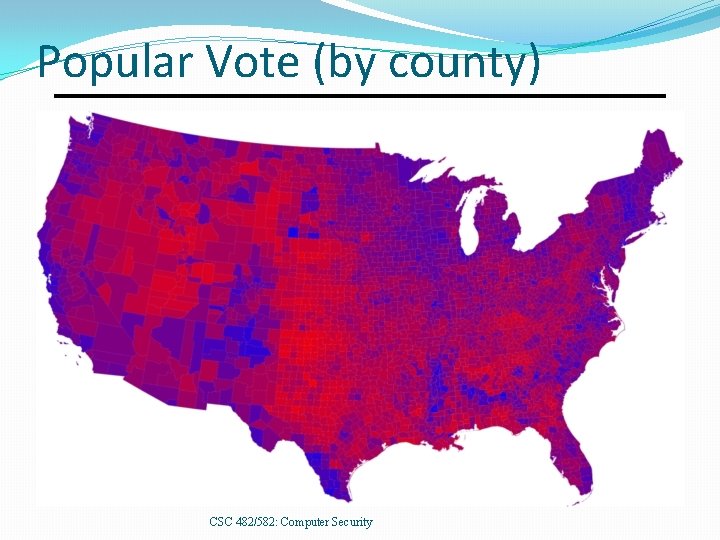
Popular Vote (by county) CSC 482/582: Computer Security

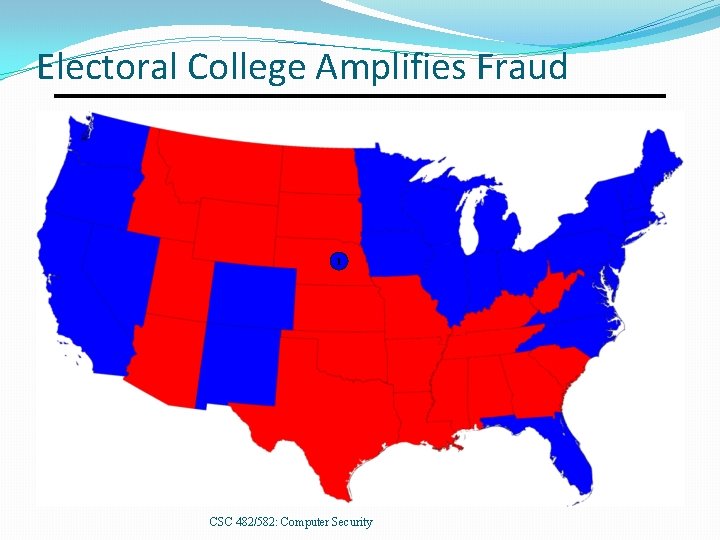
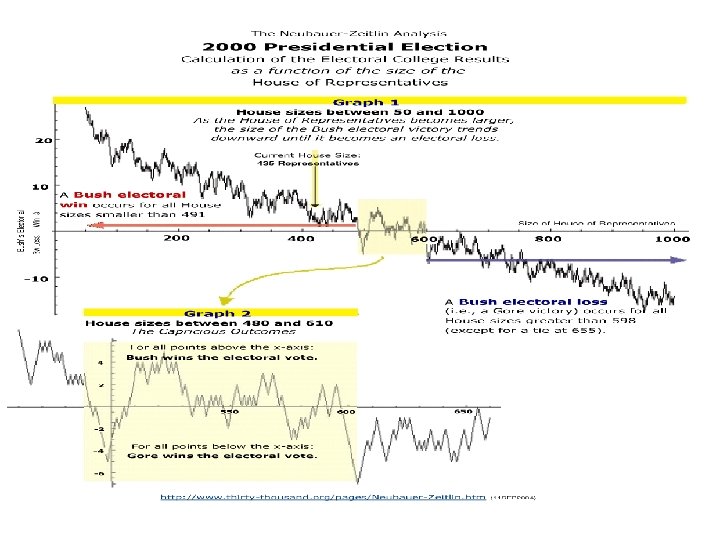
Electoral College Amplifies Fraud 1 CSC 482/582: Computer Security

Electoral College Size

EC Constitutional Questions Is President of Senate or the two Houses of Congress the final judge of the validity of votes? 2. Is the power to count merely the power to enumerate votes given by electors declared by state authority to have been appointed, or is there power to determine the correctness of the state authority's declaration and to examine the validity of the acts of the electors? 3. How is the evidence necessary to a decision to be presented, and by what means is the decision to be made? 1. https: //en. wikipedia. org/wiki/Electoral_Count_Act

Election Crisis of 1876 • Disputes about electoral vote count • Rutherford B. Hayes (R) had 165 electoral votes (EVs) • Samuel Tilden (D) won popular vote and 184 EVs • 4 states sent rival slates of electors (20 EVs total) • Danger • Worries of a second civil war. • President Grant threatened martial law to ensure Hayes was sworn in as President. • Compromise of 1877 • Two days before inauguration day, Democrats conceded election to Hayes in exchange for ending Reconstruction. CSC 482/582: Computer Security

Electoral Count Act of 1887 • Provisions • Electors chosen no more than 41 days after election day • Governor submits a certificate of ascertainment identifying electors that have been appointed by state. • "if there shall have been any final determination in a State in the manner provided for by [state] law of a controversy or contest, " governor sends a certificate of final determination. • Hawaii sent 2 sets of EVs in 1960 election • Nixon was ahead initially, but Kennedy won recount. • Nixon, as Vice President, presided over joint session of Congress to certify the presidential vote and counted the second set of EVs, which were for Kennedy. • John F. Kennedy had won electoral vote with or without Hawaii EVs. https: //en. wikipedia. org/wiki/Electoral_Count_Act

Election Requirements 1. 2. 3. 4. 5. Privacy—voters have the right to keep their ballots secret. Incoercibility—voters cannot prove contents of their ballots. Accuracy—final tally is sum of all ballots. Availability—voters should be able to vote when they reach the polling place. Verifiability—voters can prove to themselves that their ballots were cast as intended and counted and that everyone can prove final tally is accurate.

History of Voting Voice Voting • Observers can record votes. • So can others, leading to bribery and coercion. Ballots • Clay or stone tokens to represent vote. • Black balls used for negative, white for positive. Paper Ballots • Used in Rome as early as 139 BCE. • Originally supplied by voters, later by parties. • Difficult to ensure privacy while avoiding fraud. CSC 482/582: Computer Security

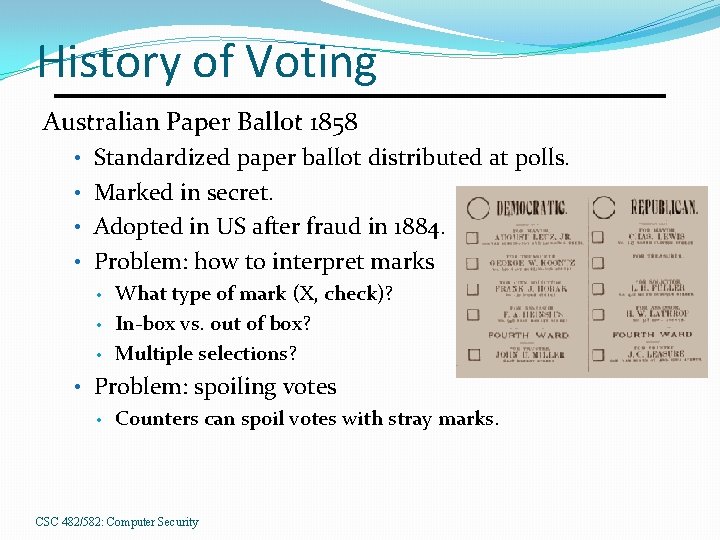
History of Voting Australian Paper Ballot 1858 • Standardized paper ballot distributed at polls. • Marked in secret. • Adopted in US after fraud in 1884. • Problem: how to interpret marks • What type of mark (X, check)? • In-box vs. out of box? • Multiple selections? • Problem: spoiling votes • Counters can spoil votes with stray marks. CSC 482/582: Computer Security

Punched Card Systems 1964 Flaws • Hanging Chads • Dimpled Chads • Chad Jams HAVA 2002 • Reaction to 2000 Florida. • $3. 8 B to replace punch card + lever machines. • Accessibility requirements. • No security requirements.

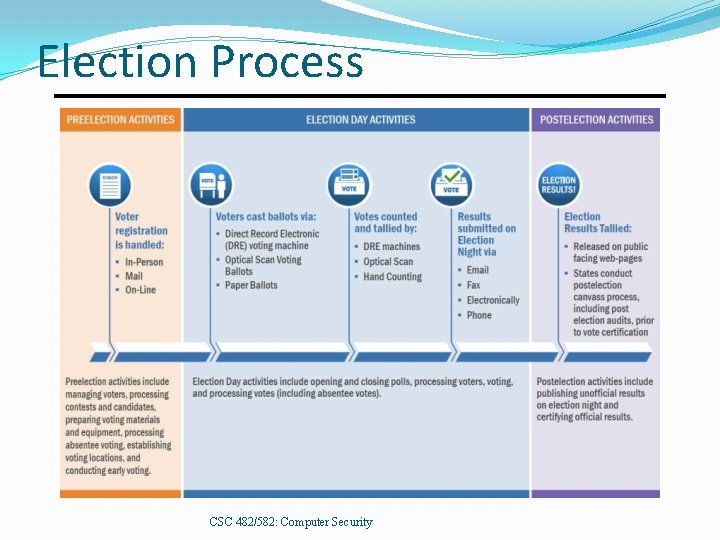
Election Process CSC 482/582: Computer Security

Election Systems There are multiple systems involved in elections • Voter registration systems • Voting machines • Vote-counting machines • Poll books Real world entities may use combinations like • Internet-based voter registration • Touch screen voting machines that print paper ballots • Optical scan tabulation machines to count votes • Three-ring binder paper-based poll books CSC 482/582: Computer Security

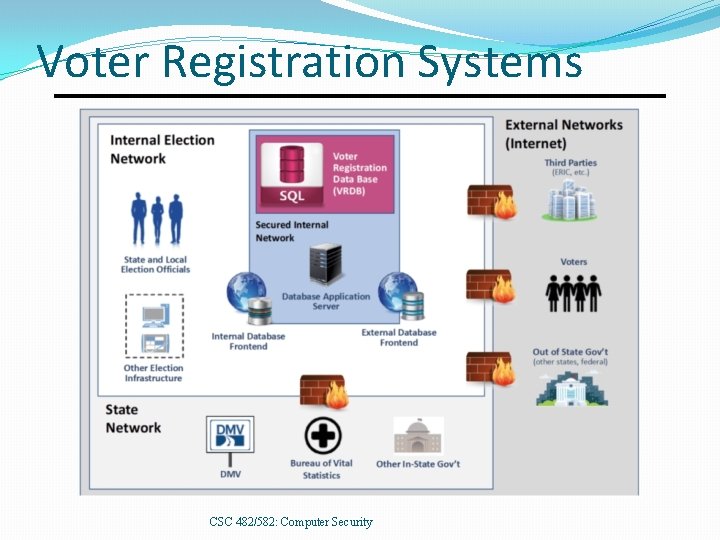
Voter Registration Systems CSC 482/582: Computer Security

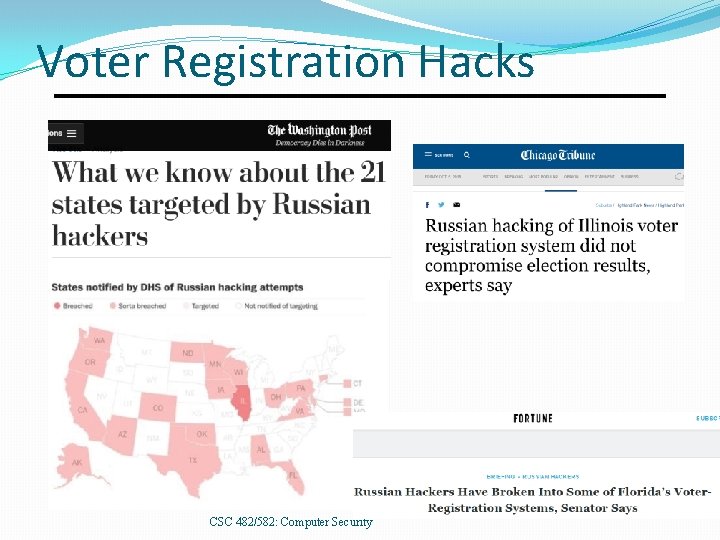
Voter Registration Hacks CSC 482/582: Computer Security

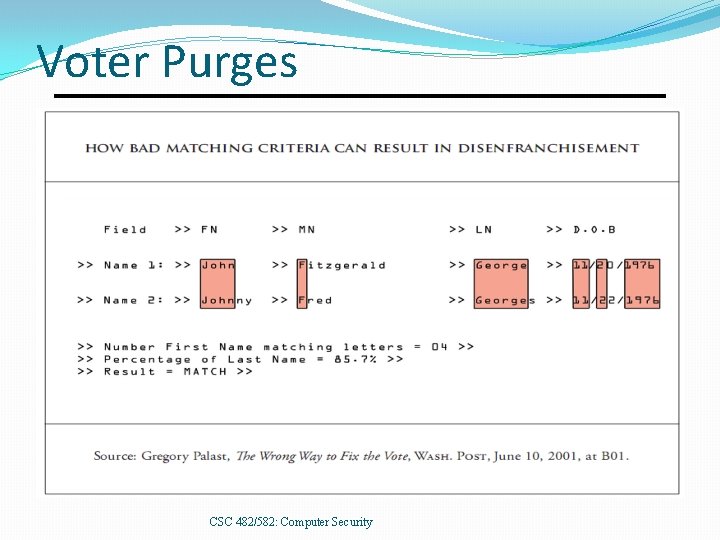
Voter Purges Bad Matching Criteria. • 2000, Florida, 60, 000 purged based on 80% of surname + DOB. ~5000 appeals afterwards. Software errors? • Ohio purged 194, 000 supposedly inactive voters in 2019, but some had voted in 2018. OH So. S blamed software errors. State gets list of voters to purge from 88 counties, which can use different software. Voting Rights Act • SCOTUS 2013 Shelby County decision removed preclearance requirements. • In 2016 -2018, purge rates in former preclearance counties were 40% higher than in other counties. If rates were same, 1. 1 million fewer voters would've been purged in 2016 -2018. CSC 482/582: Computer Security

Voter Purges CSC 482/582: Computer Security

Poll Books Voting jurisdictions have poll books with lists of eligible voters from the voter registration database. • 36 states used e-poll books in 1+ jurisdictions in 2018. To vote, your name + signature is checked against poll book. • To prevent double voting, your name is crossed off. The list of people who voted is checked vs. absentee ballots. • You cannot vote in other jurisdictions, as your name is not in their poll book. What if you impersonate someone to vote twice? • It's a felony if you get caught, and it's just one vote. • You could impact more votes by requesting absentee ballots for people who you don't want to vote, complete them, and prevent them from voting, but • Registration and tabulation attacks can affect far more votes. CSC 482/582: Computer Security

Voter ID Partially effective solution to a tiny problem. • Non-citizens and felons can obtain and often have valid IDs like driver's licenses that are used in voter ID laws. • 2018: Kansas study of past 20 years found 38 ineligible people had registered to vote, and 5 had voted. • Iowa study: loosest definitions of fraud give incidences < 10 -4 Voter ID laws designed to suppress voting by Democrats • Within 24 hours of VRA preclearance ending, 5 of 9 VRA states started legislative process on voter ID laws. • Laws exclude student IDs and tribal IDs, held by groups that mostly vote Democrat, but allow gun permits. • States make. CSCit 482/582: harder to get voter IDs after laws passed. Computer Security

Voter Registration and Covid • DMV offices closed in many states • Reduce ability of people to obtain voter ID • Example: Texas voter suppression • No online voter registration. • Those over 65 can request absentee ballot without question, but Covid not a reason to obtain one. • Governor limited counties to 1 drop off box for ballots. County populations range from Loving county (169 people) to Harris county (4. 7 M). CSC 482/582: Computer Security

Tabulation “As long as I count the votes, what are you going to do about it? ” -- William Marcy “Boss” Tweed, 1871

Tabulation Attacks • Manual counting • Spoil ballots by making stray marks with a piece of pencil lead under the fingernail. • Reject absentee ballots by being very picky about ballot signature match with voter registration signature. • Scale of problem • Florida rejected mail-in 32, 000 ballots in 2018 election. • WI rejected mail-in 23, 000 ballots in 2020 primary. • Covid-19 increases worried about tabulation • Tremendous increase in mail-in ballots. • Slowed down postal service. • Population that expects immediate election results. CSC 482/582: Computer Security

Vote-Counting Software • Case Study: Bernalillo County, NM 2000 • in-person voters used DRE machines • absentee ballots used optical mark cards • In past, absentee ballots were mostly Republican, but in this election, Democratic candidate was strongly ahead. • Problem: the counting program didn’t handle the “straight ticket” option properly • Elections supervisor explanation: the software was buggy • Vendor explanation: he programmed it incorrectly 32

Electronic Voting Security https: //xkcd. com/2030/

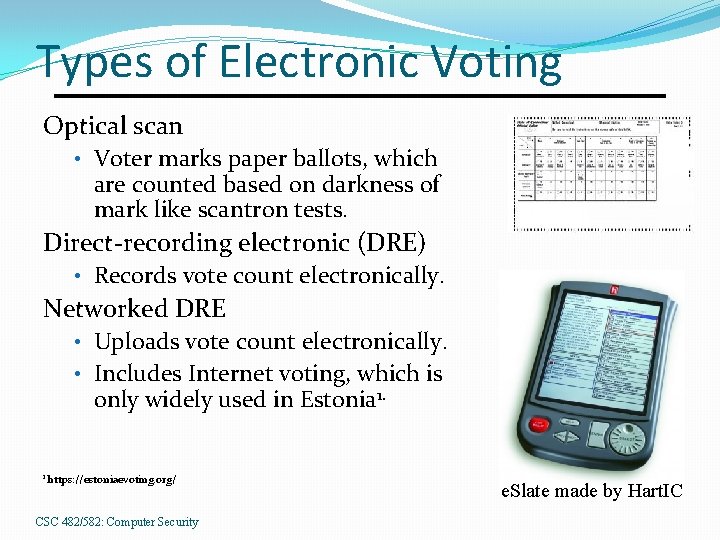
Types of Electronic Voting Optical scan • Voter marks paper ballots, which are counted based on darkness of mark like scantron tests. Direct-recording electronic (DRE) • Records vote count electronically. Networked DRE • Uploads vote count electronically. • Includes Internet voting, which is only widely used in Estonia 1. 1 https: //estoniaevoting. org/ CSC 482/582: Computer Security e. Slate made by Hart. IC

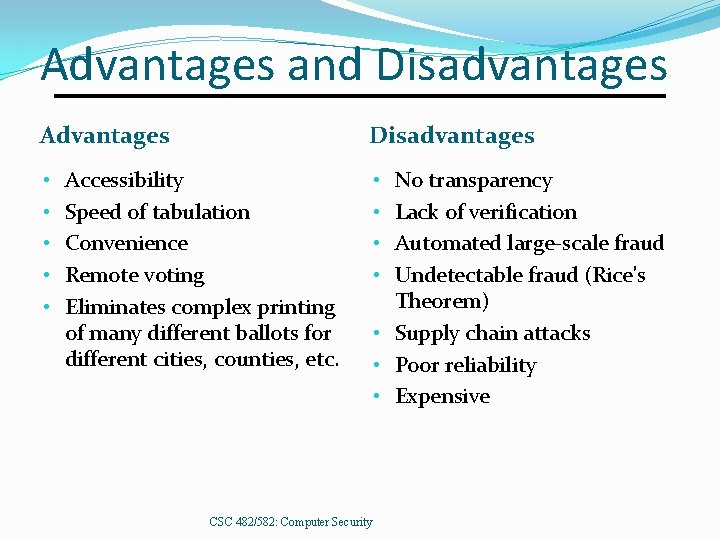
Advantages and Disadvantages Advantages • • • Accessibility Speed of tabulation Convenience Remote voting Eliminates complex printing of many different ballots for different cities, counties, etc. CSC 482/582: Computer Security No transparency Lack of verification Automated large-scale fraud Undetectable fraud (Rice's Theorem) • Supply chain attacks • Poor reliability • Expensive • •

Reliability Issues Kenton County, KY: 108 e. Slate machines taken out of service 9 am Tuesday. Punch machines available as backups. Franklin County, OH: One Columbus precinct has 1, 066 registered voters but posted 1, 138 votes. In suburban Worthington, a precinct has 534 registered voters but counted 633 votes, and another has 951 registered voters but reported 1, 095 votes. 35, 000 forced to use provisional ballots due to a database ‘glitch. ’ Wellington, FL: two losing candidates were declared winners by the Dominion’s win. EDS software, which incorrectly swapped totals among candidates. CSC 482/582: Computer Security

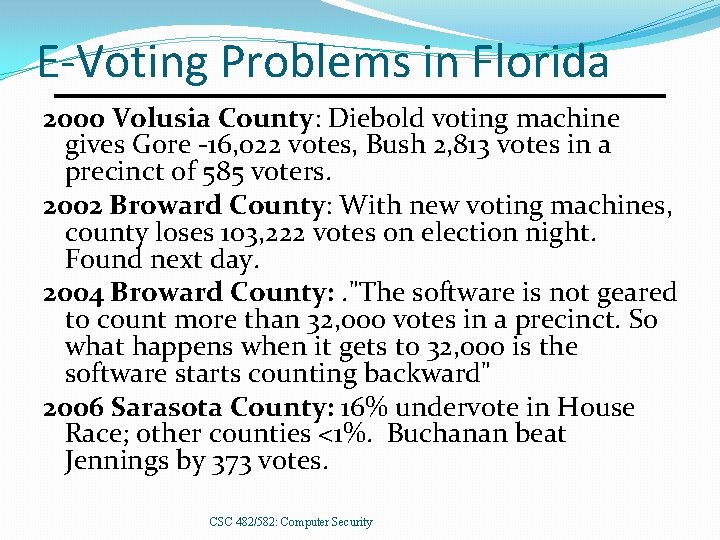
E-Voting Problems in Florida 2000 Volusia County: Diebold voting machine gives Gore -16, 022 votes, Bush 2, 813 votes in a precinct of 585 voters. 2002 Broward County: With new voting machines, county loses 103, 222 votes on election night. Found next day. 2004 Broward County: . "The software is not geared to count more than 32, 000 votes in a precinct. So what happens when it gets to 32, 000 is the software starts counting backward" 2006 Sarasota County: 16% undervote in House Race; other counties <1%. Buchanan beat Jennings by 373 votes. CSC 482/582: Computer Security

Electronic Voting (DRE) Reliability • History of inaccuracy. • Hardware failures (10% fail each election). Security • Designed like a PC. • Most use Windows CE. • Impossible to audit without paper trail. Usability e. Slate made by Hart. IC • Support for disabilities, multiple ballots, languages. • Touch screen problems. • Hart double-selection ‘bug’ CSC 482/582: Computer Security

Voting Equipment by County CSC 482/582: Computer Security

Diebold Ballot. Station 1. Setup D/L ballot setup 2. Pre-Election L&A testing 3. Election Voting 4. Post-Election Print result tape Transfer votes CSC 482/582: Computer Security

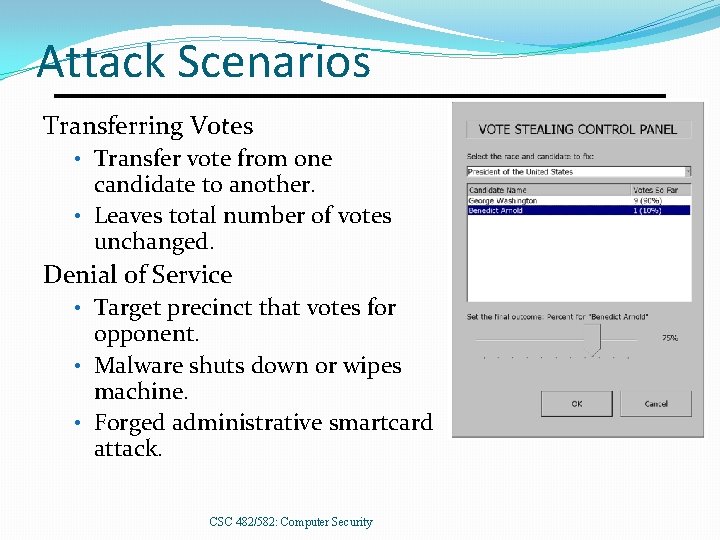
Attack Scenarios Transferring Votes • Transfer vote from one candidate to another. • Leaves total number of votes unchanged. Denial of Service • Target precinct that votes for opponent. • Malware shuts down or wipes machine. • Forged administrative smartcard attack. CSC 482/582: Computer Security

Injecting Attack Code • Direct installation • Reboot using smartcard with fboot. nbo. • Reboot using smartcard with explorer. glb. • Replace EPROM. • Voting machines use standard minibar keys. • Virus • Infects memory cards. • Memory cards infect machines on boot. • Upgrades delivered via memory cards. CSC 482/582: Computer Security

Concealing Voting Malware • Timing • Software only active in Election mode. • Software only active on certain dates / times. • Knock • Activates only after secret “knock” given. • Hiding processes and files • Rootkit techniques • Virtualization CSC 482/582: Computer Security

Has e-voting improved? • DMCA 2015 exception granted research security of voting machines. • DEF-CON Hacking Village 2017 -2019 • Collection of voting, tabulation, and poll book devices. • All devices were hacked every year. • Default passwords common. • Vulnerable to old known vulnerabilities. AVS Win. Vote hacked in 2017 with vulnerability published in 2003. • Accessible OS. AVS Win. Vote had USB ports, allowing voter to plugin keyboard and run Windows programs. CSC 482/582: Computer Security

Defending Voting Machines Paper ballots (Voter verified paper audit trail) • Lets voters verify their votes. • Allow secure recounts. • Some DREs just save number of votes and their recount function just prints the same number. Risk Limiting Audits (RLAs) • Statistically rigorous technique that tabulates a random sample of paper ballots to determine if machine-tabulated results are consistent with what a full hand count of ballots would reveal. • A 5% risk limit means that if the election outcome is wrong, the chance that the audit will mistakenly confirm it is 5% or less. • Sample size depends on margin of victory and desired risk limit. • Four states require RLAs in 2020. Many states cannot perform or do not allow post-election audits of any type. CSC 482/582: Computer Security

Obama, Mc. Cain Campaigns Hacked Obama, Mc. Cain Campaign Computers Hacked Tech experts at the Obama headquarters initially believed that the computer systems had been invaded by a computer virus. By Antone Gonsalves, Information. Week Nov. 5, 2008 URL: http: //www. informationweek. com/story/show. Article. jhtml? article. ID=212000820 Computer systems used by the Obama and Mc. Cain campaigns were reportedly hacked over the summer by an unknown "foreign entity, " according to an account of the attacks published Wednesday. The sophisticated cyberattacks has prompted a federal investigation, Newsweek reported Wednesday. Attacks on both campaigns were similar in that investigators believed a foreign entity or organization sought to steal information on policy positions. Such information could be used in negotiations with the future administration. Tech experts at the Obama headquarters initially believed that the computer systems had been invaded by a computer virus. The next day, however, they were told by the FBI and Secret Service that the problem was far more serious, the magazine reported. "You have a problem way bigger than what you understand, " an agent told Obama's team, according to Newsweek. "You have been compromised, and a serious amount of files have been loaded off your system. " Federal agents told Obama's aides that the Mc. Cain campaign had suffered a similar attack, which a top Mc. Cain official later confirmed to Newsweek. CSC 482/582: Computer Security

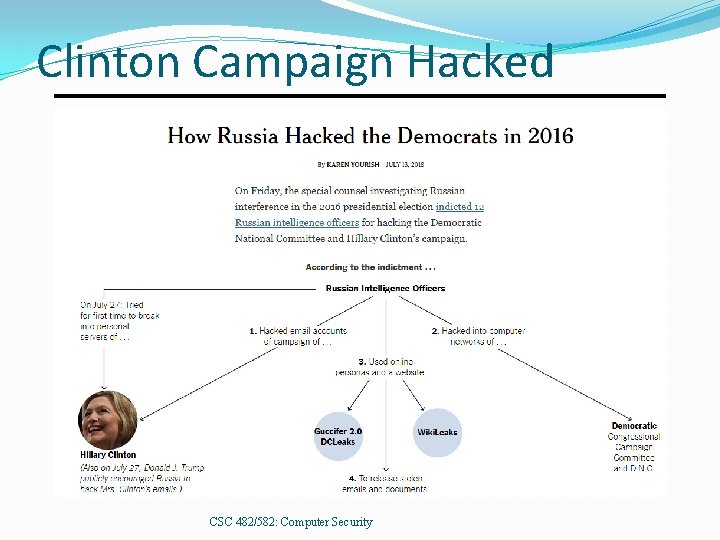
Clinton Campaign Hacked CSC 482/582: Computer Security

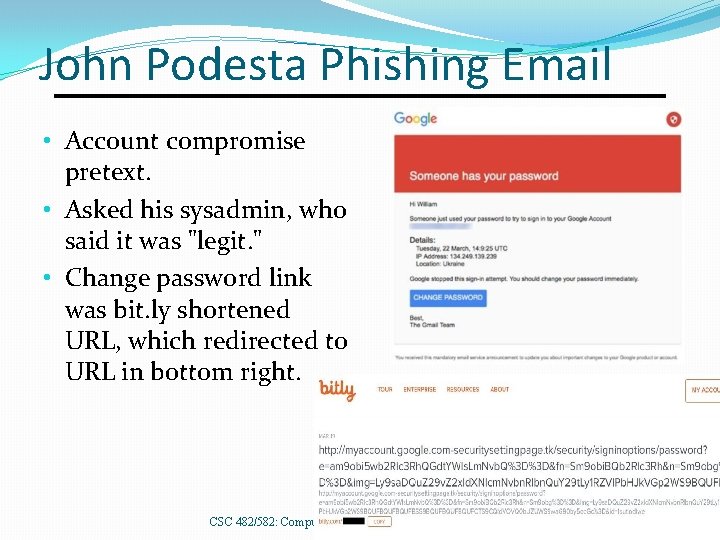
John Podesta Phishing Email • Account compromise pretext. • Asked his sysadmin, who said it was "legit. " • Change password link was bit. ly shortened URL, which redirected to URL in bottom right. CSC 482/582: Computer Security

Key Points Election Requirements 1. 1. 2. 3. 4. 5. Privacy Incoercibility Accuracy Availability Verifiability Direct Electronic Voting (DRE) 2. 1. 2. Lack of reliability, verifiability, and security. Possibility of undetectable wholesale fraud. Alternatives 3. 1. 2. Use e-voting to mark ballots only. Use simple pre-rendered systems with appropriate software and physical security. CSC 482/582: Computer Security

References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. 19. Matt Blaze et. Al. DEFCON-25 Voting Machine Hacking Village Report. http: //cs. brown. edu/people/jsavage/Voting. Project/2017_09_DEF_CON_25_Voting_Village_Report. pdf. 2017. Matt Blaze et. Al. DEFCON-27 Voting Machine Hacking Village Report. https: //media. defcon. org/DEF%20 CON%2027/voting-village-report-defcon 27. pdf. 2019. DHS. Election Security. https: //www. dhs. gov/topic/election-security “More e-voting problems, ” http: //www. evoting-experts. com/, December 12, 2004. Ariel J. Feldman, J. Alex Halderman, Edward W. Felten, “Security Analysis of the Diebold Accu. Vote-TS Voting Machine, ” http: //itpolicy. princeton. edu/voting, Sep 13, 2006. Susan Hennessey. Cybersecurity of Voting Machines [Congressional Testimony]. https: //www. brookings. edu/testimonies/cybersecurity-of-voting-machines/. 2017. Douglas Jones, “Illustrated Voting Machine History, ” http: //www. cs. uiowa. edu/~jones/voting/pictures/, 2003. Douglas Jones, "The 2016 Election: Was it Hacked? ", https: //homepage. divms. uiowa. edu/~jones/voting/ICFRC 17. html, 2017. Douglas Jones, “Four ways to defend democracy and protect every voter's ballot”, https: //phys. org/news/2018 -09 -ways-defend-democracy-voter-ballot. html, 2018. Alexander Keyssar. The Right to Vote: The Contested History of Democracy in the United States. Basic Books. 2009. Tadayoshi Kohno, Adam Stubblefield, Aviel D. Rubin, Dan S. Wallach, “Analysis of an Electronic Voting System, ” IEEE Symposium on Security and Privacy, Oakland, CA, May, 2004. Lorrain C. Minnite. The Myth of Voter Fraud. Cornell University Press. 2011. MITRE. Recommended Security Controls for Voter Registration. https: //www. mitre. org/publications/technical-papers/recommended-security-controls-forvoter-registration-systems. 2019. National Academies of Science, Engineering, and Medicine. Securing the Vote. https: //www. nap. edu/catalog/25120/securing-the-vote-protecting-american-democracy. 2018. Mark Newman, “Election Result Maps, ” http: //www-personal. umich. edu/~mejn/election/, 2016. Avi Rubin, Brave New Ballot, Morgan Road Books, 2006. Verified Voting, Key Facts 2012, https: //www. verifiedvoting. org/key-facts-2012/. Verified Voting. What is a Risk Limiting Audit. https: //verifiedvoting. org/publication/what-is-a-risklimiting-audit/. 2020. Kim Zetter, “House Dems seek Election Inquiry, ” http: //www. wired. com/news/evote/0, 2645, 65623, 00. html, Nov 5, 2004. CSC 482/582: Computer Security