CSC 482582 Computer Security HTTP Security CSC 482582






- Slides: 36

CSC 482/582: Computer Security HTTP Security CSC 482/582: Computer Security Slide #1

Topics 1. 2. 3. 4. 5. 6. 7. 8. How HTTP works HTTP methods, headers, and responses URIs, URLs, and URNs Statelessness Cookies More HTTP methods and headers Proxying and Caching HTTP Vulnerabilities CSC 482/582: Computer Security Slide #2

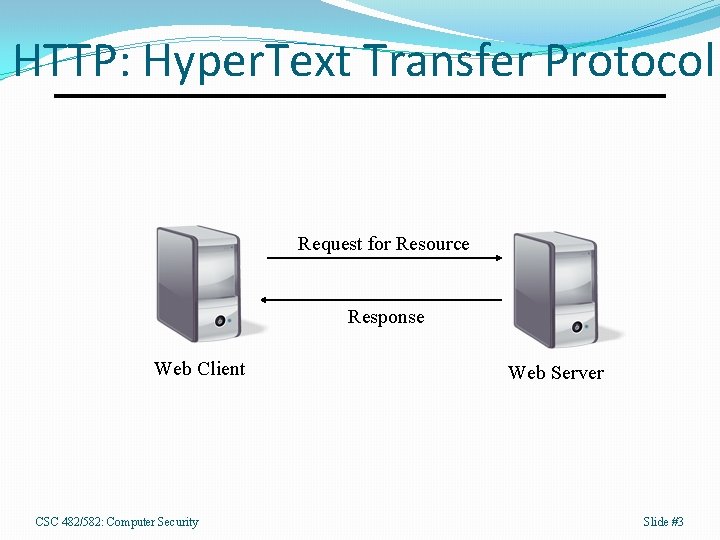
HTTP: Hyper. Text Transfer Protocol Request for Resource Response Web Client CSC 482/582: Computer Security Web Server Slide #3

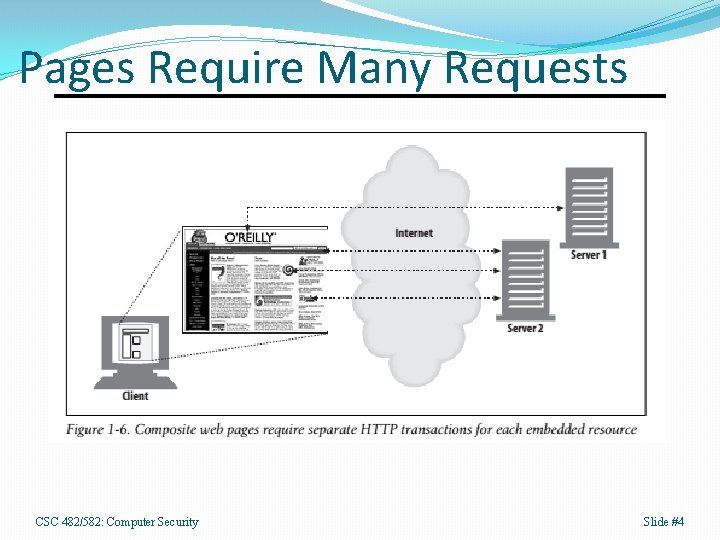
Pages Require Many Requests CSC 482/582: Computer Security Slide #4

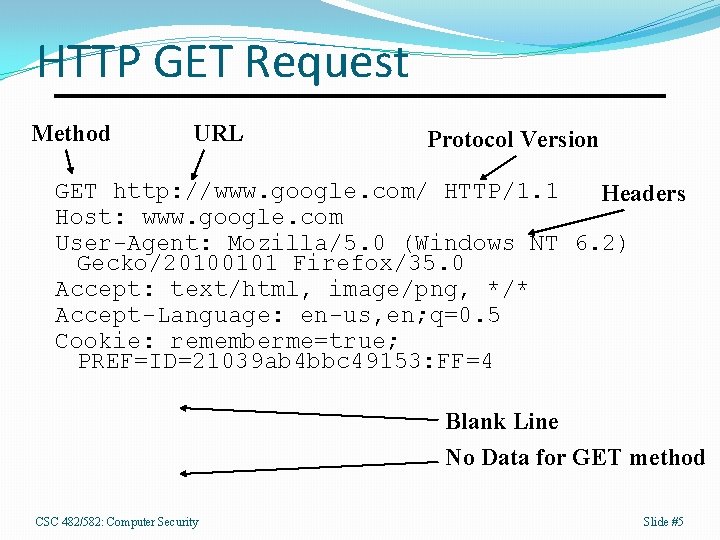
HTTP GET Request Method URL Protocol Version GET http: //www. google. com/ HTTP/1. 1 Headers Host: www. google. com User-Agent: Mozilla/5. 0 (Windows NT 6. 2) Gecko/20100101 Firefox/35. 0 Accept: text/html, image/png, */* Accept-Language: en-us, en; q=0. 5 Cookie: rememberme=true; PREF=ID=21039 ab 4 bbc 49153: FF=4 Blank Line No Data for GET method CSC 482/582: Computer Security Slide #5

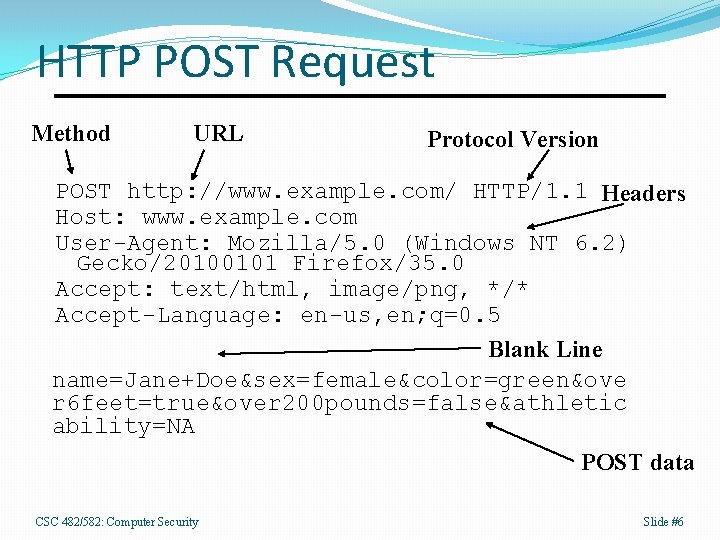
HTTP POST Request Method URL Protocol Version POST http: //www. example. com/ HTTP/1. 1 Headers Host: www. example. com User-Agent: Mozilla/5. 0 (Windows NT 6. 2) Gecko/20100101 Firefox/35. 0 Accept: text/html, image/png, */* Accept-Language: en-us, en; q=0. 5 Blank Line name=Jane+Doe&sex=female&color=green&ove r 6 feet=true&over 200 pounds=false&athletic ability=NA POST data CSC 482/582: Computer Security Slide #6

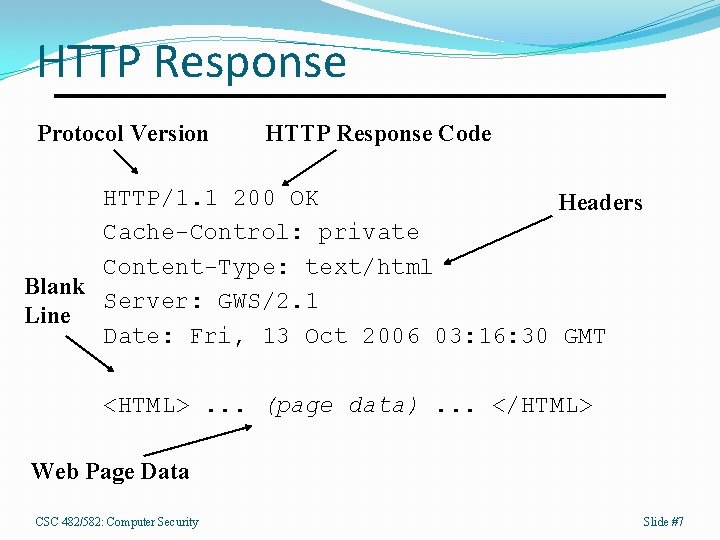
HTTP Response Protocol Version HTTP Response Code HTTP/1. 1 200 OK Headers Cache-Control: private Content-Type: text/html Blank Server: GWS/2. 1 Line Date: Fri, 13 Oct 2006 03: 16: 30 GMT <HTML>. . . (page data). . . </HTML> Web Page Data CSC 482/582: Computer Security Slide #7

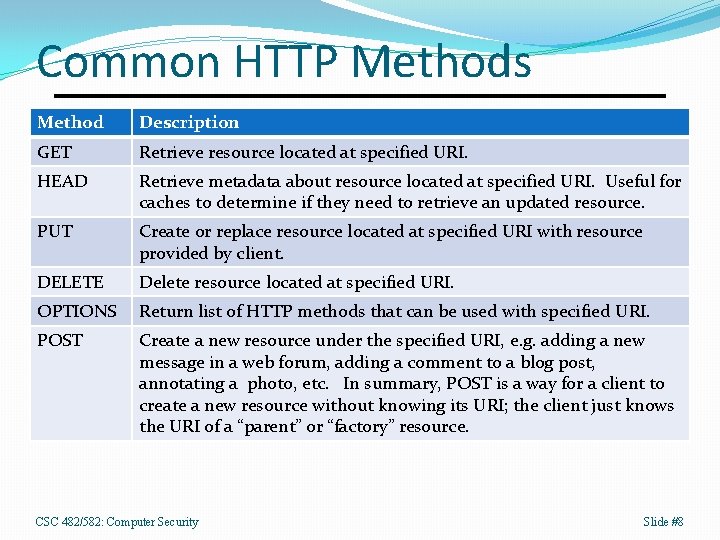
Common HTTP Methods Method Description GET Retrieve resource located at specified URI. HEAD Retrieve metadata about resource located at specified URI. Useful for caches to determine if they need to retrieve an updated resource. PUT Create or replace resource located at specified URI with resource provided by client. DELETE Delete resource located at specified URI. OPTIONS Return list of HTTP methods that can be used with specified URI. POST Create a new resource under the specified URI, e. g. adding a new message in a web forum, adding a comment to a blog post, annotating a photo, etc. In summary, POST is a way for a client to create a new resource without knowing its URI; the client just knows the URI of a “parent” or “factory” resource. CSC 482/582: Computer Security Slide #8

Idempotence and Safety An operation is safe if making the request will not change any state on the server. • GET, HEAD, and OPTIONS are safe. An operation is idempotent if making one request has the same effect as making a series of identical requests. • PUT and DELETE are idempotent. POST is neither safe nor idempotent. It is possible for servers to misuse requests like GET. • Example: GET https: //api. deli. icio. us/posts/delete • If misused, testing tools, spiders, caches can destroy data. CSC 482/582: Computer Security Slide #9

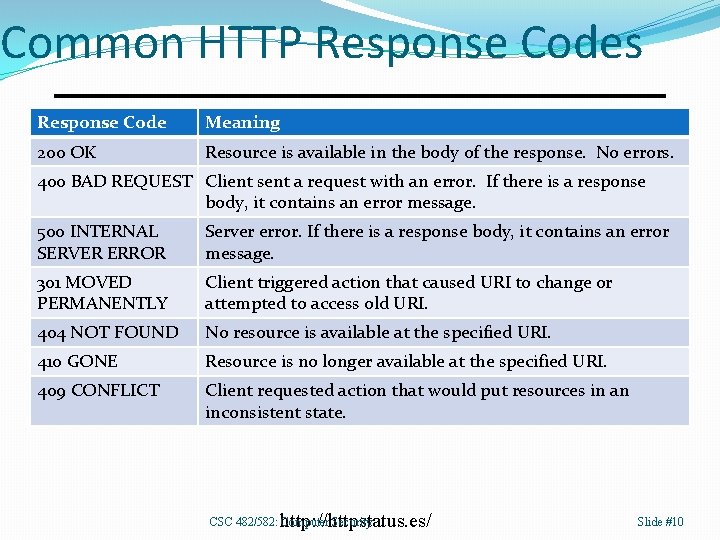
Common HTTP Response Codes Response Code Meaning 200 OK Resource is available in the body of the response. No errors. 400 BAD REQUEST Client sent a request with an error. If there is a response body, it contains an error message. 500 INTERNAL SERVER ERROR Server error. If there is a response body, it contains an error message. 301 MOVED PERMANENTLY Client triggered action that caused URI to change or attempted to access old URI. 404 NOT FOUND No resource is available at the specified URI. 410 GONE Resource is no longer available at the specified URI. 409 CONFLICT Client requested action that would put resources in an inconsistent state. http: //httpstatus. es/ CSC 482/582: Computer Security Slide #10

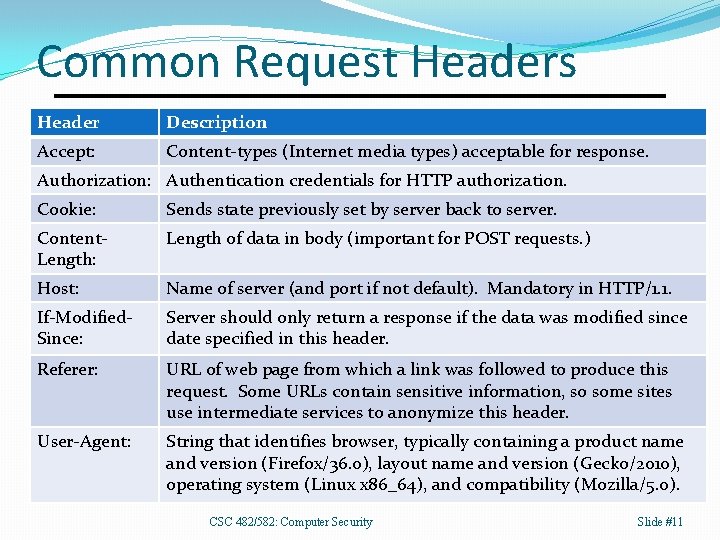
Common Request Headers Header Description Accept: Content-types (Internet media types) acceptable for response. Authorization: Authentication credentials for HTTP authorization. Cookie: Sends state previously set by server back to server. Content. Length: Length of data in body (important for POST requests. ) Host: Name of server (and port if not default). Mandatory in HTTP/1. 1. If-Modified. Since: Server should only return a response if the data was modified since date specified in this header. Referer: URL of web page from which a link was followed to produce this request. Some URLs contain sensitive information, so some sites use intermediate services to anonymize this header. User-Agent: String that identifies browser, typically containing a product name and version (Firefox/36. 0), layout name and version (Gecko/2010), operating system (Linux x 86_64), and compatibility (Mozilla/5. 0). CSC 482/582: Computer Security Slide #11

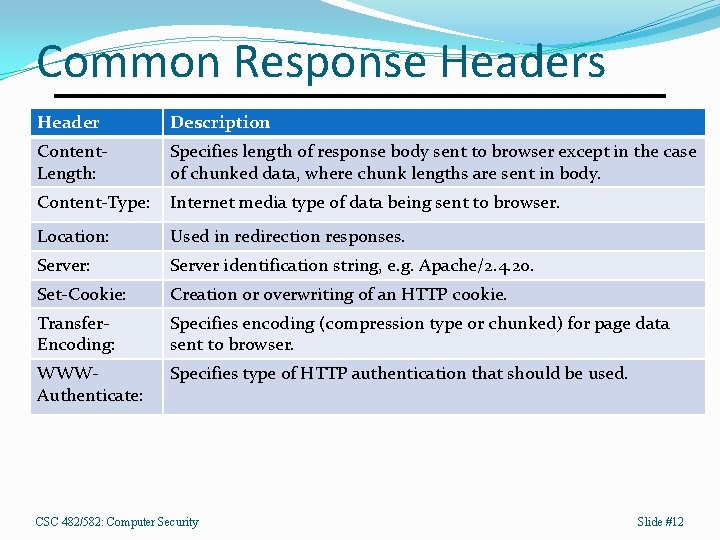
Common Response Headers Header Description Content. Length: Specifies length of response body sent to browser except in the case of chunked data, where chunk lengths are sent in body. Content-Type: Internet media type of data being sent to browser. Location: Used in redirection responses. Server: Server identification string, e. g. Apache/2. 4. 20. Set-Cookie: Creation or overwriting of an HTTP cookie. Transfer. Encoding: Specifies encoding (compression type or chunked) for page data sent to browser. WWWAuthenticate: Specifies type of HTTP authentication that should be used. CSC 482/582: Computer Security Slide #12

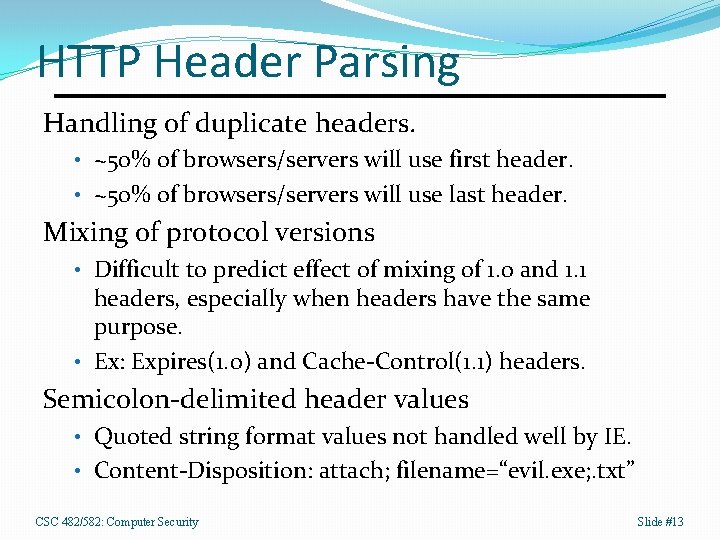
HTTP Header Parsing Handling of duplicate headers. • ~50% of browsers/servers will use first header. • ~50% of browsers/servers will use last header. Mixing of protocol versions • Difficult to predict effect of mixing of 1. 0 and 1. 1 headers, especially when headers have the same purpose. • Ex: Expires(1. 0) and Cache-Control(1. 1) headers. Semicolon-delimited header values • Quoted string format values not handled well by IE. • Content-Disposition: attach; filename=“evil. exe; . txt” CSC 482/582: Computer Security Slide #13

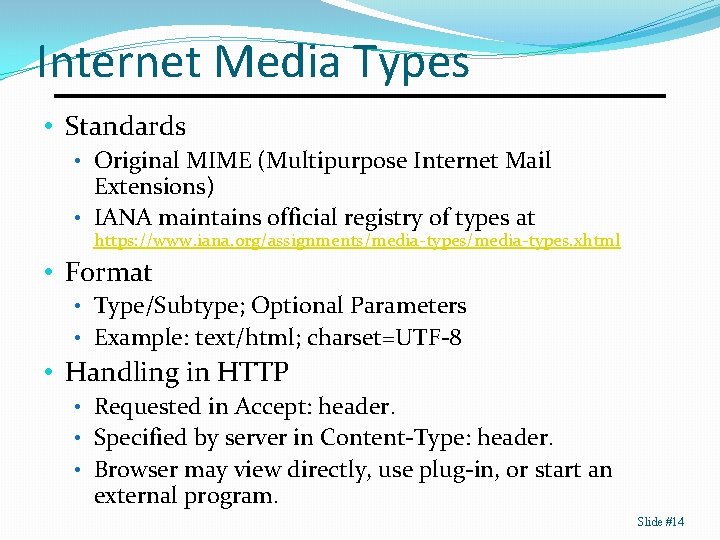
Internet Media Types • Standards • Original MIME (Multipurpose Internet Mail Extensions) • IANA maintains official registry of types at https: //www. iana. org/assignments/media-types. xhtml • Format • Type/Subtype; Optional Parameters • Example: text/html; charset=UTF-8 • Handling in HTTP • Requested in Accept: header. • Specified by server in Content-Type: header. • Browser may view directly, use plug-in, or start an external program. Slide #14

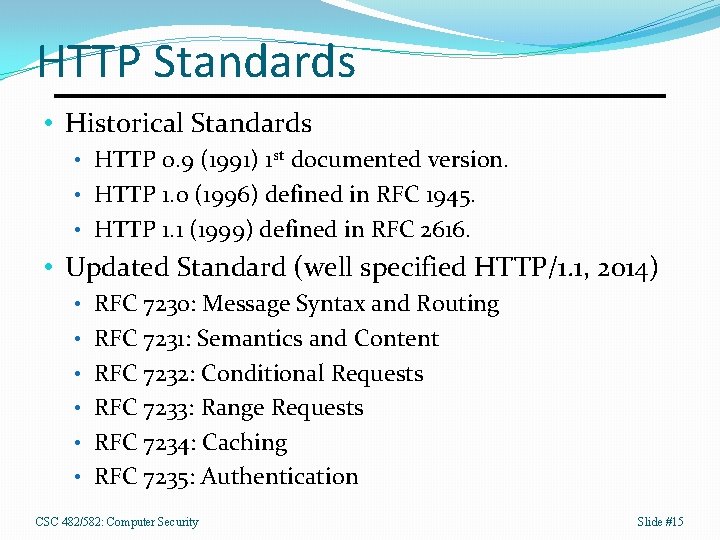
HTTP Standards • Historical Standards • HTTP 0. 9 (1991) 1 st documented version. • HTTP 1. 0 (1996) defined in RFC 1945. • HTTP 1. 1 (1999) defined in RFC 2616. • Updated Standard (well specified HTTP/1. 1, 2014) • RFC 7230: Message Syntax and Routing • RFC 7231: Semantics and Content • RFC 7232: Conditional Requests • RFC 7233: Range Requests • RFC 7234: Caching • RFC 7235: Authentication CSC 482/582: Computer Security Slide #15

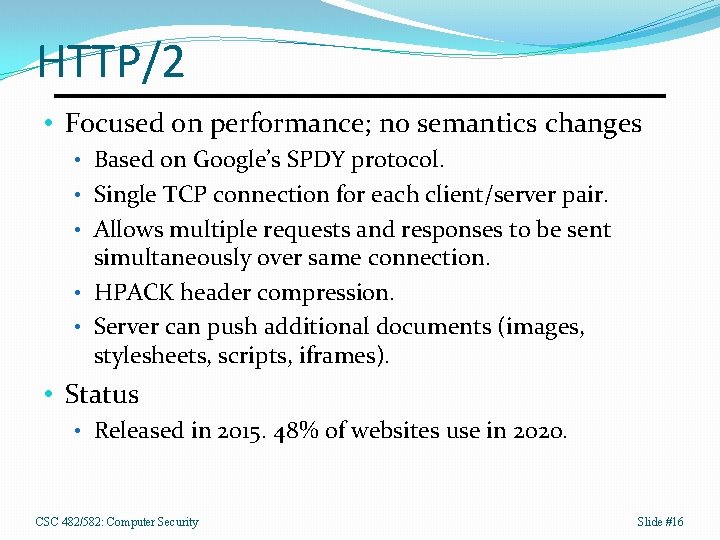
HTTP/2 • Focused on performance; no semantics changes • Based on Google’s SPDY protocol. • Single TCP connection for each client/server pair. • Allows multiple requests and responses to be sent simultaneously over same connection. • HPACK header compression. • Server can push additional documents (images, stylesheets, scripts, iframes). • Status • Released in 2015. 48% of websites use in 2020. CSC 482/582: Computer Security Slide #16

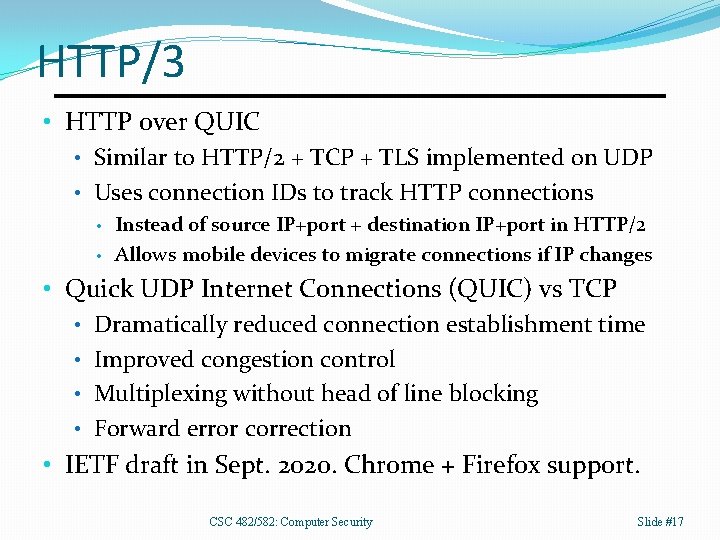
HTTP/3 • HTTP over QUIC • Similar to HTTP/2 + TCP + TLS implemented on UDP • Uses connection IDs to track HTTP connections • • Instead of source IP+port + destination IP+port in HTTP/2 Allows mobile devices to migrate connections if IP changes • Quick UDP Internet Connections (QUIC) vs TCP • Dramatically reduced connection establishment time • Improved congestion control • Multiplexing without head of line blocking • Forward error correction • IETF draft in Sept. 2020. Chrome + Firefox support. CSC 482/582: Computer Security Slide #17

Think, Pair, Share: HTTP Headers 1. On your own 1. Login to your SEED VM and start Firefox 2. Right click on the page and select Inspect Element 3. Load the SEED labs page or another page of your choice 4. Go to Network tab to view all HTTP requests 5. Search the headers to find answers to: 1. 2. Find one request/response pair using headers named starting with "x-". What is the purpose of these headers? Find the cookies being used. Pick one cookie to research: identify which organization it came from and what its purpose is. Pair 1. Explain the HTTP x-header that you found to your partner. 2. Explain what you learned about your chosen cookie to your partner. CSC 482/582: Computer Security Slide #18

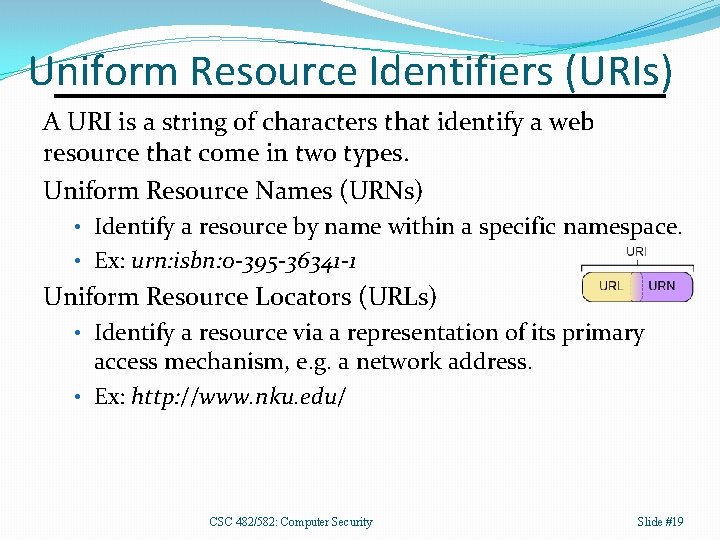
Uniform Resource Identifiers (URIs) A URI is a string of characters that identify a web resource that come in two types. Uniform Resource Names (URNs) • Identify a resource by name within a specific namespace. • Ex: urn: isbn: 0 -395 -36341 -1 Uniform Resource Locators (URLs) • Identify a resource via a representation of its primary access mechanism, e. g. a network address. • Ex: http: //www. nku. edu/ CSC 482/582: Computer Security Slide #19

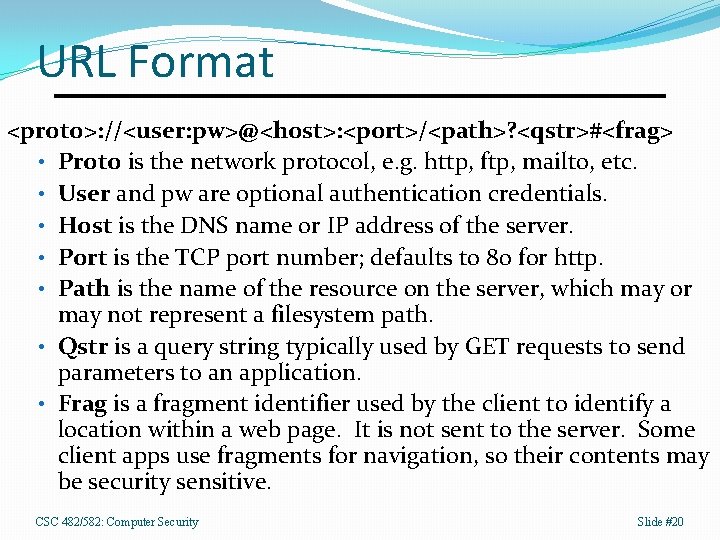
URL Format <proto>: //<user: pw>@<host>: <port>/<path>? <qstr>#<frag> • Proto is the network protocol, e. g. http, ftp, mailto, etc. • User and pw are optional authentication credentials. • Host is the DNS name or IP address of the server. • Port is the TCP port number; defaults to 80 for http. • Path is the name of the resource on the server, which may or may not represent a filesystem path. • Qstr is a query string typically used by GET requests to send parameters to an application. • Frag is a fragment identifier used by the client to identify a location within a web page. It is not sent to the server. Some client apps use fragments for navigation, so their contents may be security sensitive. CSC 482/582: Computer Security Slide #20

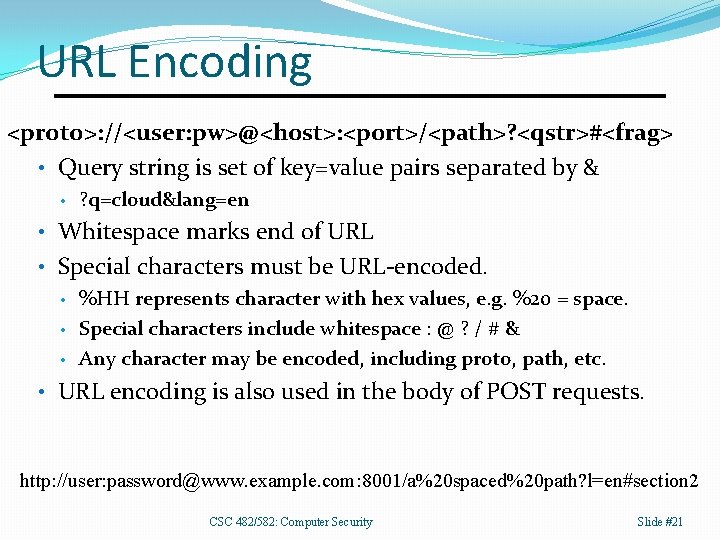
URL Encoding <proto>: //<user: pw>@<host>: <port>/<path>? <qstr>#<frag> • Query string is set of key=value pairs separated by & • ? q=cloud&lang=en • Whitespace marks end of URL • Special characters must be URL-encoded. • %HH represents character with hex values, e. g. %20 = space. • Special characters include whitespace : @ ? / # & • Any character may be encoded, including proto, path, etc. • URL encoding is also used in the body of POST requests. http: //user: password@www. example. com: 8001/a%20 spaced%20 path? l=en#section 2 CSC 482/582: Computer Security Slide #21

HTTP is a stateless protocol A stateful protocol allows requests to move the server into a different state, in which a request may produce a different result. • Example protocols: FTP, SMTP, TCP • FTP command “get rest. txt” will return a different file when cwd is /public rather than /private. A stateless protocol treats each request as an independent transaction that is unrelated to any previous request so that communication consists of independent pairs of requests and responses. • Examples: HTTP, IP CSC 482/582: Computer Security Slide #22

Handling Statelessness • Store state information directly in the address (URI) • To access second page in google search for “http”: • https: //encrypted. google. com/webhp? q=http&safe=off&start=10 • Works best for web services. • Store state indirectly in an HTTP header (cookies) • Most common type of state storage. • HTML 5 provides additional browser storage features. CSC 482/582: Computer Security Slide #23

Cookies • Maintain state via HTTP headers • State specified is set of name=value pairs. • Set-Cookie header sent from server. • Cookie header sent from browser. • No RFC specification used til RFC 6265 in 2011. • Examples • Set-Cookie: foo=bar; path=/; expires Fri, 20 -Feb-2015 23: 59: 00 GMT • Cookie: foo=bar • Encoding • Encode cookies with base 64 to avoid metacharacter interpretation (colons, commas, slashes, quotes, etc. ) CSC 482/582: Computer Security Slide #24

Cookie Fields Expires: if specified, cookie may be saved to disk and persist across sessions. If not, then cookie persists for duration of browser session. Max-age: similar to Expires, but not supported by IE. Domain: scoping mechanism to allow cookie to be scoped to domain broader than host that sent Set-Cookie header. Path: scopes cookie to a specified path prefix. Secure: prevents cookie from being sent over non-encrypted connections. Http. Only: removes ability to read cookie via document. cookie API in Java. Script to protect against XSS. CSC 482/582: Computer Security Slide #25

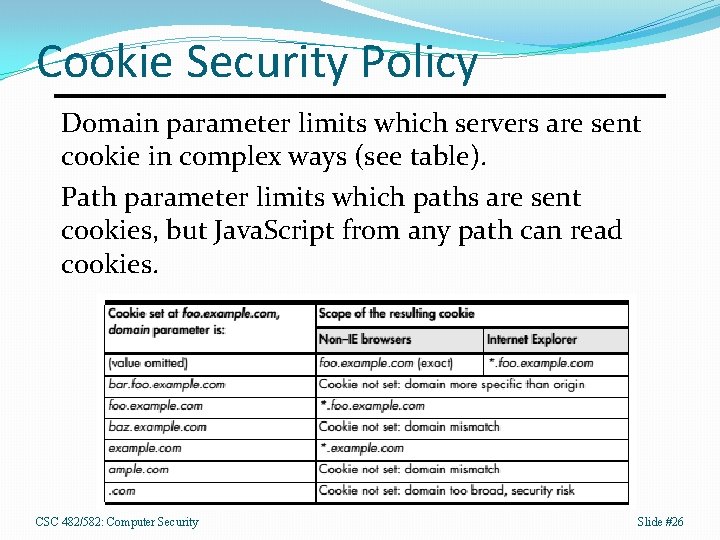
Cookie Security Policy Domain parameter limits which servers are sent cookie in complex ways (see table). Path parameter limits which paths are sent cookies, but Java. Script from any path can read cookies. CSC 482/582: Computer Security Slide #26

HTTP Proxies forward GET requests from browser • Request appears to come from proxy, not browser host. • May add X-Forwarded-for: header revealing host IP. • Uses CONNECT requests to tunnel HTTPS protocol. Reverse proxies accept HTTP requests for servers • Used for load balancing: 1 proxy, many web servers • Used as endpoint for TLS connections to • Reduce CPU load on web servers. • Enable network security monitoring of TLS sessions. CSC 482/582: Computer Security Slide #27

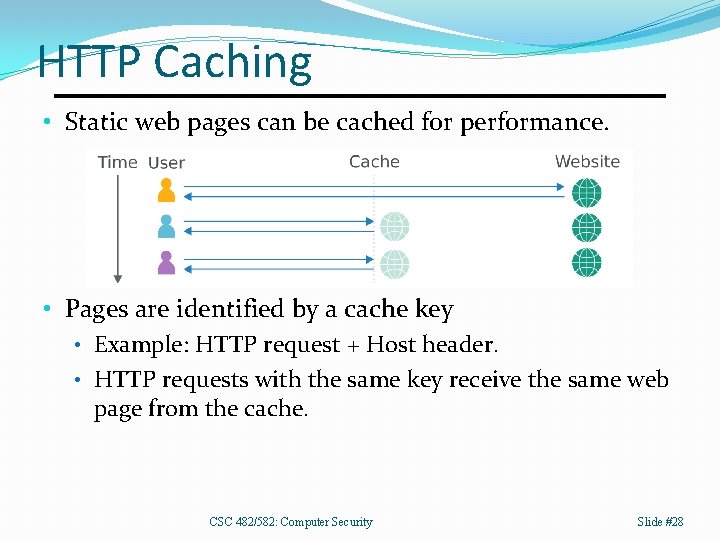
HTTP Caching • Static web pages can be cached for performance. • Pages are identified by a cache key • Example: HTTP request + Host header. • HTTP requests with the same key receive the same web page from the cache. CSC 482/582: Computer Security Slide #28

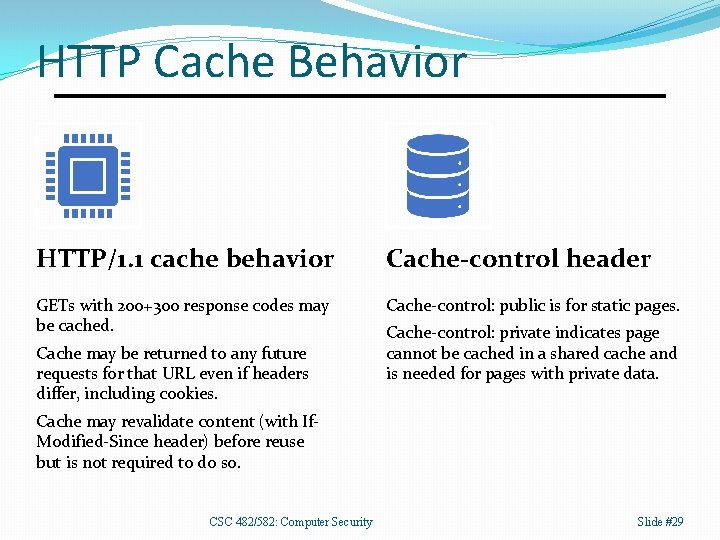
HTTP Cache Behavior HTTP/1. 1 cache behavior Cache-control header GETs with 200+300 response codes may be cached. Cache-control: public is for static pages. Cache may be returned to any future requests for that URL even if headers differ, including cookies. Cache-control: private indicates page cannot be cached in a shared cache and is needed for pages with private data. Cache may revalidate content (with If. Modified-Since header) before reuse but is not required to do so. CSC 482/582: Computer Security Slide #29

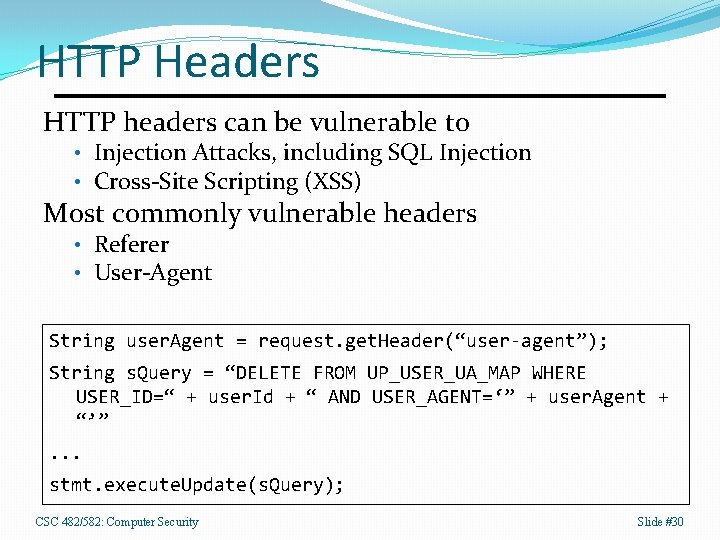
HTTP Headers HTTP headers can be vulnerable to • Injection Attacks, including SQL Injection • Cross-Site Scripting (XSS) Most commonly vulnerable headers • Referer • User-Agent String user. Agent = request. get. Header(“user-agent”); String s. Query = “DELETE FROM UP_USER_UA_MAP WHERE USER_ID=“ + user. Id + “ AND USER_AGENT=‘” + user. Agent + “’”. . . stmt. execute. Update(s. Query); CSC 482/582: Computer Security Slide #30

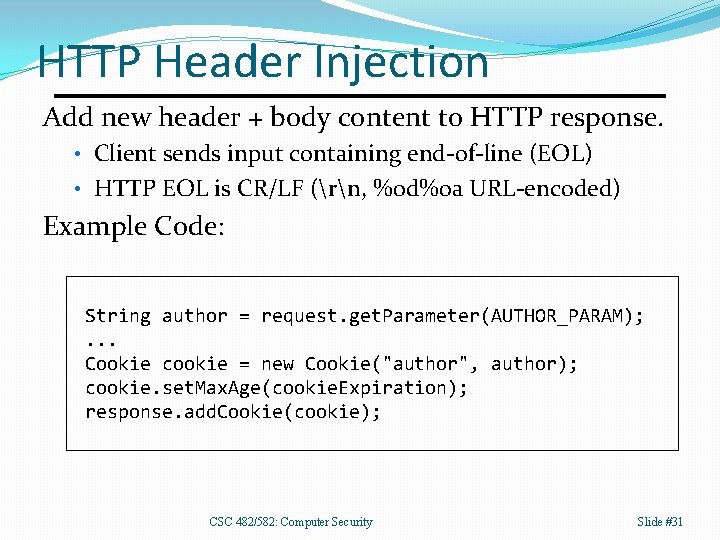
HTTP Header Injection Add new header + body content to HTTP response. • Client sends input containing end-of-line (EOL) • HTTP EOL is CR/LF (rn, %0 d%0 a URL-encoded) Example Code: String author = request. get. Parameter(AUTHOR_PARAM); . . . Cookie cookie = new Cookie("author", author); cookie. set. Max. Age(cookie. Expiration); response. add. Cookie(cookie); CSC 482/582: Computer Security Slide #31

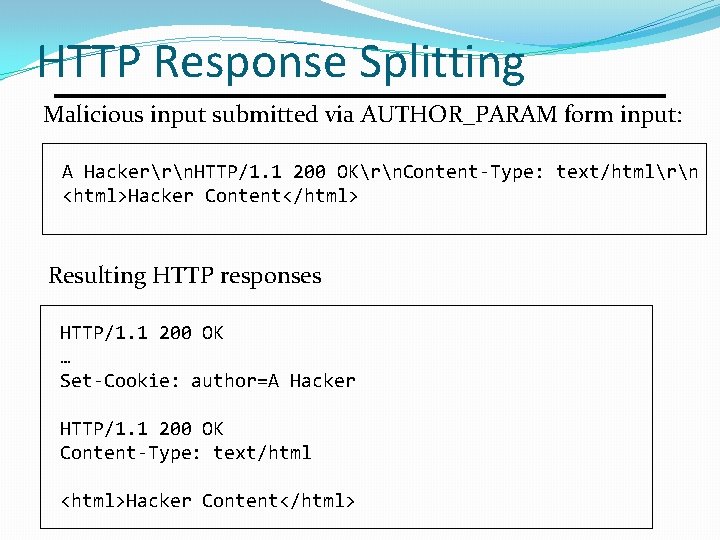
HTTP Response Splitting Malicious input submitted via AUTHOR_PARAM form input: A Hackerrn. HTTP/1. 1 200 OKrn. Content-Type: text/htmlrn <html>Hacker Content</html> Resulting HTTP responses HTTP/1. 1 200 OK … Set-Cookie: author=A Hacker HTTP/1. 1 200 OK Content-Type: text/html <html>Hacker Content</html>

Response Splitting Impact • Server generates 2 HTTP responses to one request. • First response doesn't matter for attack. • Attacker completely controls second response. • Attacker-controlled 2 nd response can be used to • Change apparent contents of web page (defacement) • Redirect user with 3 xx response to malicious web site. • Add a new Set-Cookie header to perform session fixation attacks. • Defeat header-based security features like CORS. • Run Java. Script code with access to cookies and other data of legitimate site. CSC 482/582: Computer Security Slide #33

Web Cache Poisoning 1. Attacker sends two requests • Request 1 is an HTTP response splitting attack. • Request 2 is for the page to be cached. 2. Cache sees 2 responses from request 1. • Attacker crafted second response generated by request 1 to have the same cache key as request 2. • Cache caches second response for that cache key. 3. When users request that page from the cache • They receive response 2 from the HTTP response splitting attack. • Attackers can manipulate caching headers in response 2 to ensure response 2 is cached as long as possible. CSC 482/582: Computer Security Slide #34

Key Points 1. Requests Idempotence 2. Safety 1. 2. 3. 4. 5. Stateless architecture Cookies HTTP response splitting Cache poisoning CSC 482/582: Computer Security Slide #35

References 1. David Gourley et. Al. , HTTP: The Definitive Guide, O’Reilly, 2002. Krishnamurthy et. Al. , Key Differences Between HTTP/1. 0 and HTTP/1. 1, http: //www 8. org/w 8 -papers/5 c-protocols/key. html. 3. Mark Nottingham, RFC 2616 is Dead, https: //www. mnot. net/blog/2014/06/07/rfc 2616_is_dead, 2014. Dafydd Stuttart and Marcus Pinto, The Web Application Hacker’s Handbook, 2 nd Edition, Wiley, 2011. 5. HTTP/2 Home Page, https: //http 2. github. io/. 6. Sanctum, “HTTP Response Splitting Whitepaper, ” http: //www. packetstormsecurity. org/papers/general/whitepaper_h ttpresponse. pdf, 2004. 7. Michael Zalewski, The Tangled Web: A Guide to Securing Modern Web Applications, No Starch Press, 2011. CSC 482/582: Computer Security Slide #36