CSC 482582 Computer Security Introduction CSC 482582 Computer






















- Slides: 31

CSC 482/582: Computer Security Introduction CSC 482/582: Computer Security Slide #1

Topics 1. What is computer security? 2. Who's trying to get into your systems? 1. Threat Models 3. What do they want? 1. Money 2. Cyberwar 4. How do they get into your systems? 1. Attacks 2. Vulnerabilities and Exploits 3. Patches 5. How do we stop them from getting into our systems? CSC 482/582: Computer Security Slide #2

What is Computer Security? Computer Security is the prevention of certain types of intentional actions from occurring in a system. • The people who might attack a system are called • • threats, attackers, or adversaries. Threats carry out attacks to compromise a system. Attacks work by exploiting vulnerabilities in a system. The goal of attacks is to obtain assets from a system, which may be informational or physical in nature. Security controls reduce the ability of threats to obtain assets from a system by exploiting vulnerabilities.

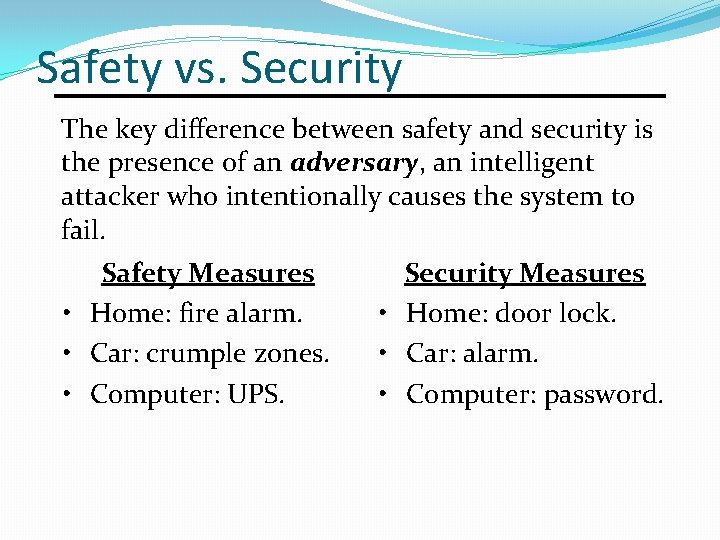
Safety vs. Security The key difference between safety and security is the presence of an adversary, an intelligent attacker who intentionally causes the system to fail. Safety Measures • Home: fire alarm. • Car: crumple zones. • Computer: UPS. Security Measures • Home: door lock. • Car: alarm. • Computer: password.

Who's trying to get into your systems? CSC 482/582: Computer Security Slide #5

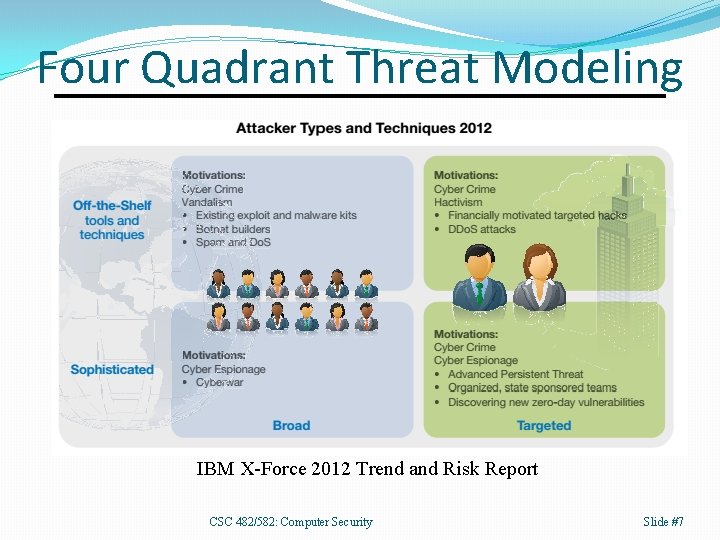
Threat Model A threat model describes which threats exist to a system, their capabilities, resources, motivations, and risk tolerance. Also known as an adversary model. • Four quadrant model: skill and targeting. • Resources and capabilities. • Do you keep enough data about historical incidents to know capabilities and motivations? CSC 482/582: Computer Security Slide #6

Four Quadrant Threat Modeling IBM X-Force 2012 Trend and Risk Report CSC 482/582: Computer Security Slide #7

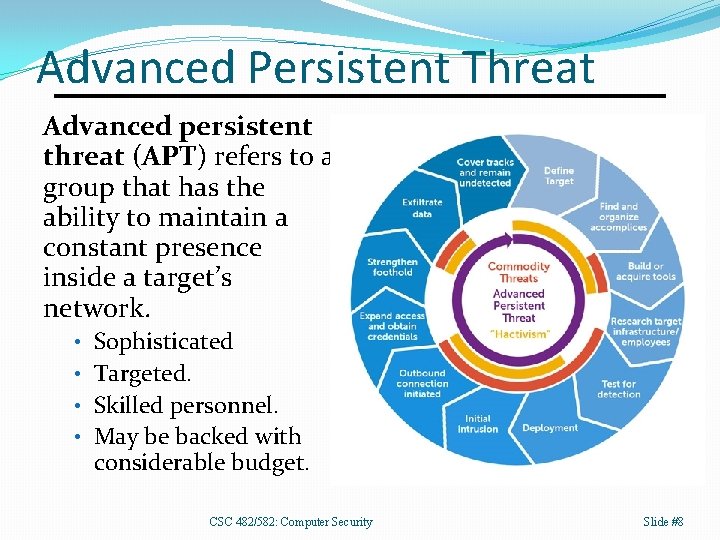
Advanced Persistent Threat Advanced persistent threat (APT) refers to a group that has the ability to maintain a constant presence inside a target’s network. • Sophisticated • Targeted. • Skilled personnel. • May be backed with considerable budget. CSC 482/582: Computer Security Slide #8

What do they want? CSC 482/582: Computer Security Slide #9

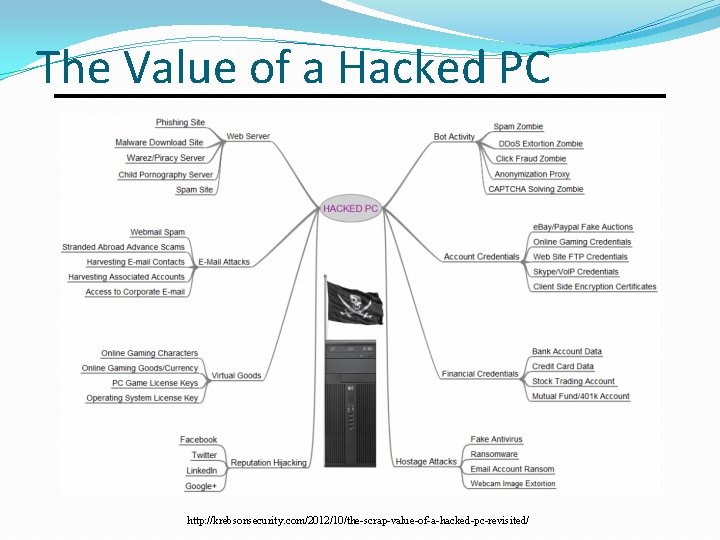
The Value of a Hacked PC http: //krebsonsecurity. com/2012/10/the-scrap-value-of-a-hacked-pc-revisited/

Cyberwar affects physical world CSC 482/582: Computer Security Slide #11

How do they get in? Attacks and Vulnerabilities CSC 482/582: Computer Security Slide #12

Attacks An attack is an action taken by an adversary to gain unauthorized access to information or resources or to make unauthorized modifications to information or computing systems. • Spoofing (pretending to be another entity) • Packet sniffing (intercepting network traffic) • Man in the middle (active interception of traffic) • Injection Attacks (buffer overflows, sql injection, etc. ) • Denial of Service (resource depletion) • Account Compromises (passwords, session hijacking) • Social Engineering, etc. CSC 482/582: Computer Security Slide #13

Spoofing A spoofing attack is when a threat masquerades as another entity on a telecommunications network. Examples of spoofing include: • E-mail spoofing • MAC address spoofing • ARP spoofing (MAC to IP address map spoofing) • IP address spoofing • Caller ID spoofing • GPS spoofing CSC 482/582: Computer Security Slide #14

Sniffing Packet sniffing is when a program records wired or wireless network packets destined for other hosts. • Wireless traffic is available to everyone nearby. • Antennas can extend range to miles. • Wired traffic is accessible depending on network location. • If network location unsatisfactory, ARP spoofing can redirect traffic to sniffing machine. Sniffing used to • Obtain passwords (ftp, imap, etc. ) • Obtain other confidential information CSC 482/582: Computer Security Slide #15

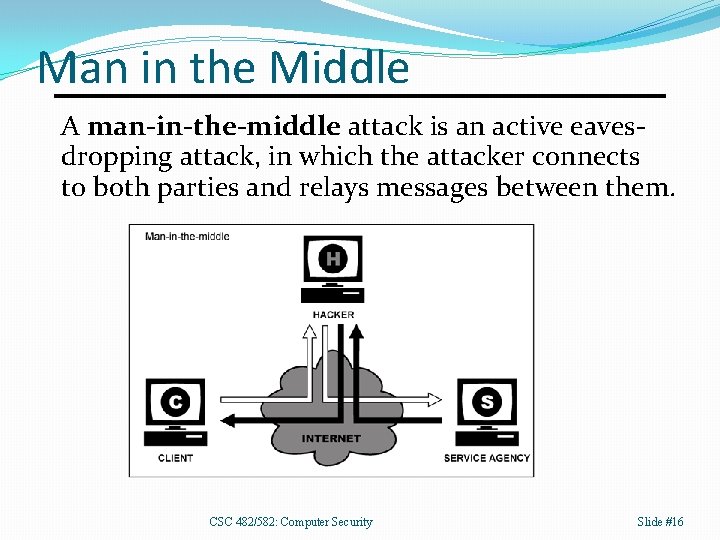
Man in the Middle A man-in-the-middle attack is an active eavesdropping attack, in which the attacker connects to both parties and relays messages between them. CSC 482/582: Computer Security Slide #16

Injection Attacks Injection attacks send code to a program instead of the data it was expected, then exploit a vulnerability in the software to execute the code. • Buffer overflows inject machine code into a process. • Cross-site scripting injects Java. Script code into a web page seen by another user. • SQL injection injects SQL code into a database query run by an application. CSC 482/582: Computer Security Slide #17

Denial of Service A denial of service (Do. S) attack attempts to make computer or network resources unavailable to its intended users. A distributed Do. S (DDo. S) attack is a Do. S attack coming from multiple sources. Slide #18

Account Compromise Attackers can take over a user’s account and use that account’s permissions to obtain or modify data. Account compromise often requires just a password obtained by: • Guessing attacks with automated software. • Reuse of passwords exposed in a data breach. • Phishing. • Keylogging. • Password resets. Attackers can temporarily compromise an attack by hijacking a user session via a MITM attack. CSC 482/582: Computer Security Slide #19

Social Engineering Social engineering is the psychological manipulation of people to reveal confidential information or perform actions to violate security policy. CSC 482/582: Computer Security Slide #20

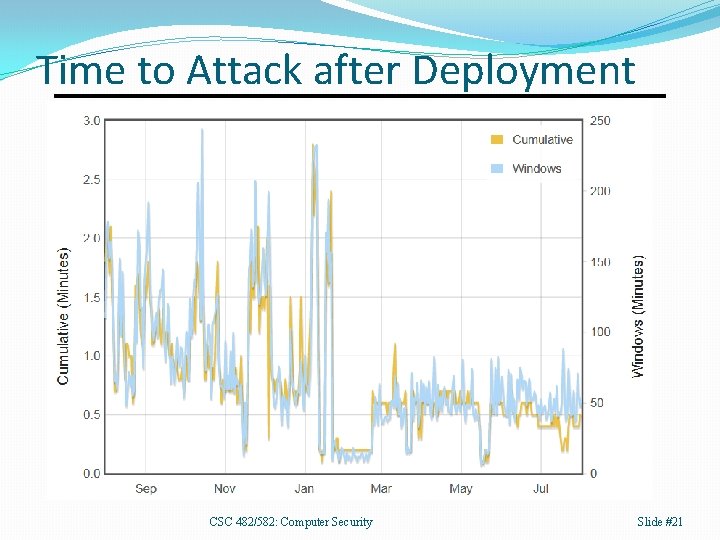
Time to Attack after Deployment CSC 482/582: Computer Security Slide #21

Vulnerabilities and Exploits • A vulnerability is a flaw or weakness in a system's design, implementation, configuration, or management that could be exploited to violate security policy. • An exploit is a technique or tool that takes advantage of a vulnerability to carry out an attack. They can be categorized by 1. The type of vulnerability they exploit. 2. Local (runs on vulnerable host) or remote. 3. Result of exploit (elevation of privilege, Do. S, spoofing, remote access, etc. ) CSC 482/582: Computer Security Slide #22

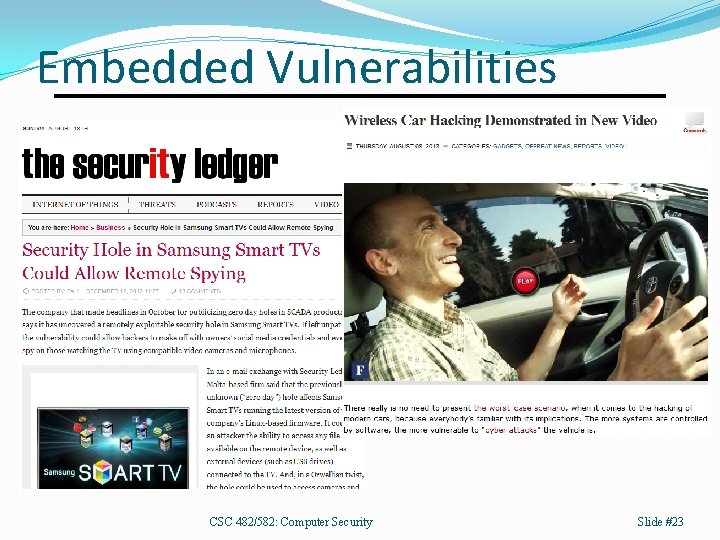
Embedded Vulnerabilities CSC 482/582: Computer Security Slide #23

Security Patches A security patch is a software modification designed to prevent or limit a vulnerability. A patch is a type of mitigation. • Administrator may have to apply manually. • Some vendors specify certain days to patch, such as “Patch Tuesday, ” the 2 nd Tuesday of the month when MS releases updates. • Increasingly software auto updates itself with current patches. CSC 482/582: Computer Security Slide #24

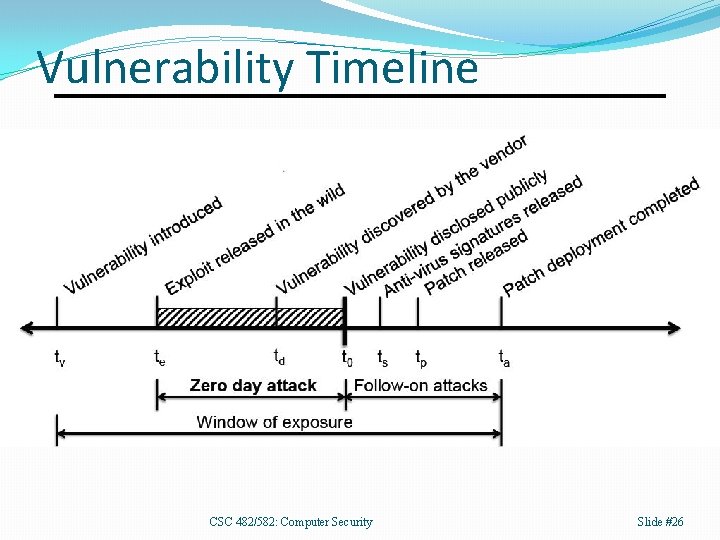
Zero Day A zero day vulnerability, attack, or exploit is a newly discovered one for which no patch currently exists. • Once a patch is released, the vulnerability, attack, or exploit is no longer a zero day. CSC 482/582: Computer Security Slide #25

Vulnerability Timeline CSC 482/582: Computer Security Slide #26

Vulnerability Markets CSC 482/582: Computer Security Slide #27

Vulnerability Databases CSC 482/582: Computer Security

Key Points Definitions: computer security, security control, threat model, attack, asset, vulnerability. 2. Who's trying to get into your systems? 1. Four Quadrant Threat Model 3. What do they want? 1. Money, Cyberwar 4. How do they get into your systems? 1. Attacks 2. Vulnerabilities and their lifecycle 3. Exploits 4. Patches CSC 482/582: Computer Security Slide #29

References 1. Arbaugh, William A. , William L. Fithen, and John Mc. Hugh. "Windows of vulnerability: A case study analysis. " Computer 33. 12 (2000): 52 -59. 2. Will Gragido and John Pirc. Cybercrime and Espionage: An Analysis of Subversive Multi-Vector Threats. Syngress. 2011. 3. Honeynet Project. Know Your Enemy, 2 nd edition, Addison-Wesley, 2004. 4. IBM X-Force Threat Intelligence Index 2018. 5. Stuart Mc. Clure, Joel Scambray, and George Kurtz. Hacking Exposed, 7 th edition, Mc. Graw-Hill, 2012. 6. Verizon. 2018 Data Breach Investigation Report. 2018. 7. Michael E. Whitman and Herbert J. Mattord. Principles of Information Security, 6 th Edition. Course Technology. 2017. CSC 482/582: Computer Security Slide #30

Released under CC BY-SA 3. 0 § This presentation is released under the Creative Commons Attribution-Share. Alike 3. 0 Unported (CC BYSA 3. 0) license § You are free: § to Share — to copy and redistribute the material in any medium § to Adapt— to remix, build, and transform upon the material § to use part or all of this presentation in your own classes § Under the following conditions: § Attribution — You must attribute the work to James Walden, but cannot do so in a way that suggests that he endorses you or your use of these materials. § Share Alike — If you remix, transform, or build upon this material, you must distribute the resulting work under this or a similar open license. § Details and full text of the license can be found at https: //creativecommons. org/licenses/by-nc-sa/3. 0/ CSC 482/582: Computer Security Slide #31