CSC 482582 Computer Security Policies CSC 482582 Computer





















- Slides: 48

CSC 482/582: Computer Security Policies CSC 482/582: Computer Security

Topics 1. 2. 3. 4. What is a security policy? Types of Policies Trust Types of Access Control Discretionary (DAC) 2. Mandatory (MAC) 3. Originator-based (ORBAC) 1. 5. Policy Expression Languages CSC 482/582: Computer Security

Security Policy Security policy partitions system states into: �Authorized (secure) � These are states the system is allowed to enter. �Unauthorized (nonsecure) � If the system enters any of these states, it’s a security violation. Secure system �Starts in authorized state. �Never enters unauthorized state. CSC 482/582: Computer Security

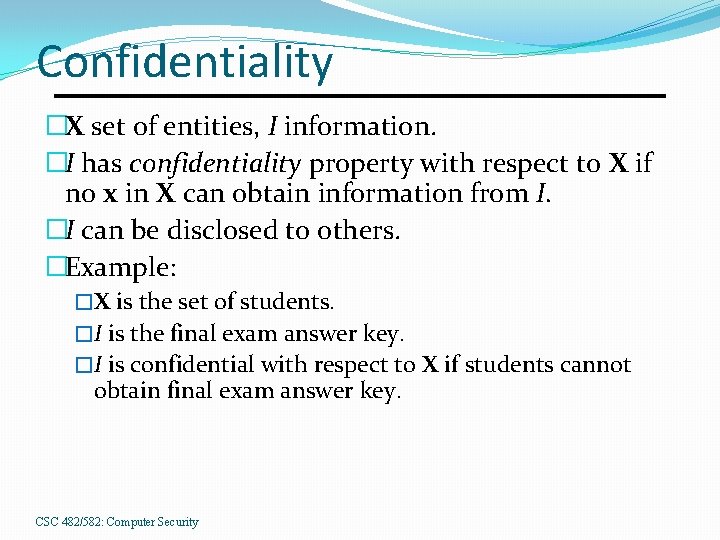
Confidentiality �X set of entities, I information. �I has confidentiality property with respect to X if no x in X can obtain information from I. �I can be disclosed to others. �Example: �X is the set of students. �I is the final exam answer key. �I is confidential with respect to X if students cannot obtain final exam answer key. CSC 482/582: Computer Security

Integrity �X set of entities, I information. �I has integrity property with respect to X if all x in X trust information in I. �Types of integrity: �trust I, its conveyance and protection (data integrity) �I information about origin of something or an identity (origin integrity, authentication) �I resource: means resource functions as it should (assurance) CSC 482/582: Computer Security

Availability �X set of entities, I resource. �I has availability property with respect to X if all x in X can access I. �Types of availability: �traditional: x gets access or not �quality of service: promise specific level of access (e. g. , a specific level of bandwidth) CSC 482/582: Computer Security

Discussion Question �Academic policy disallows cheating. �Includes copying homework, with or without permission. �CS students work on networked systems. �Anne forgets to read-protect her files. �Bill copies Anne’s homework file. �Who cheated? �Anne, Bill, or both? CSC 482/582: Computer Security

NKU AUP Discussion What are the integrity aspects of the policy regarding user data? What are the availability aspects? 2. Which of the following is a violation? Support your answer with quotes from the policy. 1. 2. 3. 4. 5. One student copies another student’s homework. One student shares his password with another student who forgot his own; no homework or other data is available on the shared account. A student uses the campus network to sell items over e-bay. A staff member copies a file of student grades onto an unencrypted USB drive and takes it home. A system CSC administrator reads student e-mail messages. 482/582: Computer Security

Policy vs. Mechanism Security Policy �Statement that divides system into authorized and unauthorized states. Mechanism �Entity or procedure that enforces some part of a security policy. CSC 482/582: Computer Security

Dirty Politics Republican Senate staffers gained access to Democrat computer files 2002 -2003. � Both parties share computer server. � 2001 misconfiguration allowed access w/o pw. � Defence: "The bottom line here is that the technology staff of the Democrats was negligent. They put these memos in a shared hard drive. It was like putting the memos on our desk. ” – Manuel Miranda CSC 482/582: Computer Security

Trust Administrator installs patch: 1. Trusts patch came from vendor, not tampered with in transit. 2. Trusts vendor tested patch thoroughly. 3. Trusts vendor’s test environment corresponds to local environment. 4. Trusts patch is installed correctly. CSC 482/582: Computer Security

How much do you trust? Ken Thompson’s compiler hack from “Reflections on Trusting Trust. ” �Modified C compiler does two things: � If compiling a compiler, inserts the self-replicating code into the executable of the new compiler. � If compiling login, inserts code to allow a backdoor password. �After recompiling and installing old C compiler: � Source code for Trojan horse does not appear anywhere in login or C compiler. � Only method of finding Trojan is analyzing binary. CSC 482/582: Computer Security Slide #12

Trust in Formal Verification �Gives formal mathematical proof that given input i, program P produces output o as specified. �Suppose a security-related program S formally verified to work with operating system O. �What are the assumptions? CSC 482/582: Computer Security

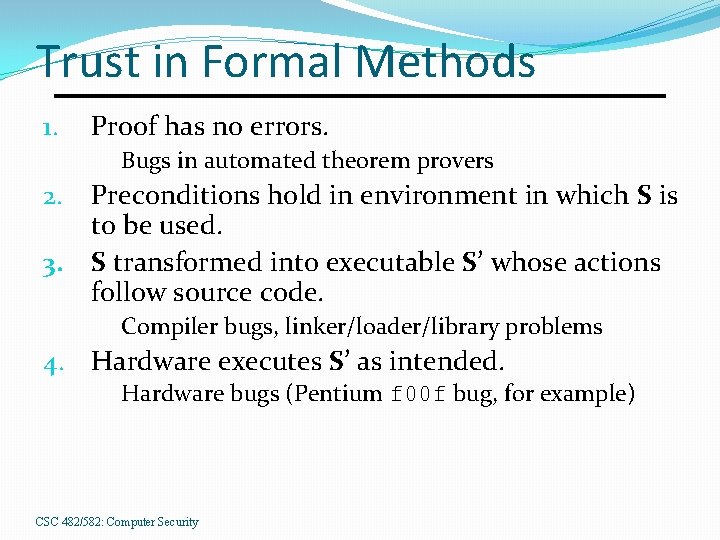
Trust in Formal Methods 1. Proof has no errors. Bugs in automated theorem provers Preconditions hold in environment in which S is to be used. 3. S transformed into executable S’ whose actions follow source code. 2. Compiler bugs, linker/loader/library problems 4. Hardware executes S’ as intended. Hardware bugs (Pentium f 00 f bug, for example) CSC 482/582: Computer Security

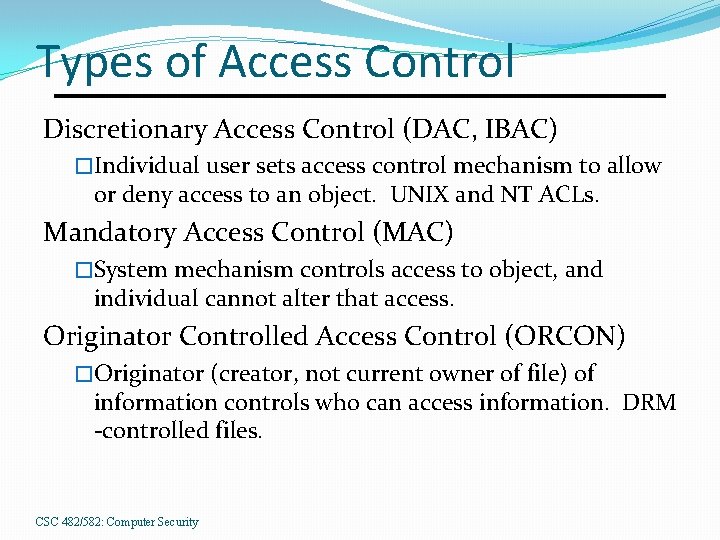
Types of Access Control Discretionary Access Control (DAC, IBAC) �Individual user sets access control mechanism to allow or deny access to an object. UNIX and NT ACLs. Mandatory Access Control (MAC) �System mechanism controls access to object, and individual cannot alter that access. Originator Controlled Access Control (ORCON) �Originator (creator, not current owner of file) of information controls who can access information. DRM -controlled files. CSC 482/582: Computer Security

SELinux: MAC for Linux What is SELinux? �Linux kernel modifications to provide MAC. What’s the problem with DAC? �TCB large: Security depends on kernel, all privileged aplications, and their configurations. �Coarse-grained: Applications run with all user privileges, even for root user. Security of MAC depends on: �kernel �SElinux security policy configuration CSC 482/582: Computer Security

SELinux Advantages and Issues Advantages �Fine-grained control by program, not by user. �Protects system from flawed or malicious code. Security policy configuration is complex. �Policy language resembles DTEL. �Fine-grained: can control program accesses to individual files, signals, etc. Difficult to find security policies that work for all. �Fedora Core 2’s strict policy caused many problems. �Fedora Core 3 applies policies to known server and system process, lets other programs run w/o restriction. CSC 482/582: Computer Security

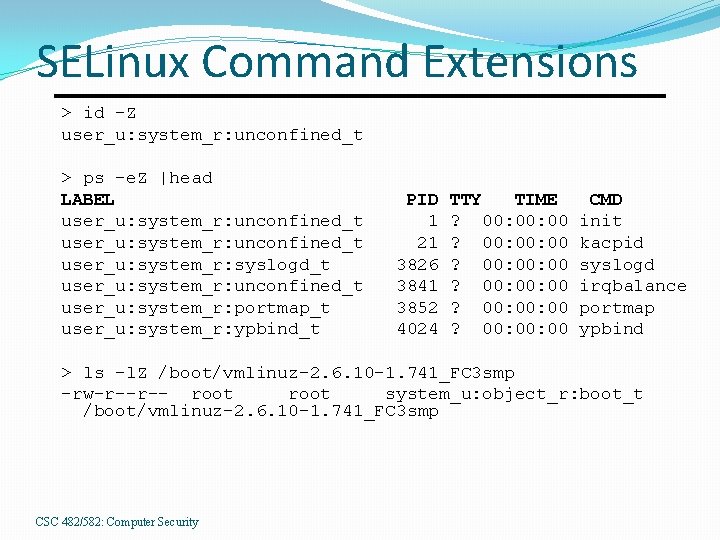
SELinux Command Extensions > id -Z user_u: system_r: unconfined_t > ps -e. Z |head LABEL user_u: system_r: unconfined_t user_u: system_r: syslogd_t user_u: system_r: unconfined_t user_u: system_r: portmap_t user_u: system_r: ypbind_t PID 1 21 3826 3841 3852 4024 TTY TIME ? 00: 00: 00 ? 00: 00: 00 CMD init kacpid syslogd irqbalance portmap ypbind > ls -l. Z /boot/vmlinuz-2. 6. 10 -1. 741_FC 3 smp -rw-r--r-- root system_u: object_r: boot_t /boot/vmlinuz-2. 6. 10 -1. 741_FC 3 smp CSC 482/582: Computer Security

Policy Languages Express security policies in a precise way. High-level languages �Policy constraints expressed abstractly. Low-level languages �Policy constraints expressed in terms of program options, input, or specific characteristics of entities on system. CSC 482/582: Computer Security

High-Level Policy Languages �Constraints expressed independent of enforcement mechanism. �Constraints restrict entities, actions. �Constraints expressed unambiguously �Requires a precise language, usually a mathematical, logical, or programming-like language. CSC 482/582: Computer Security

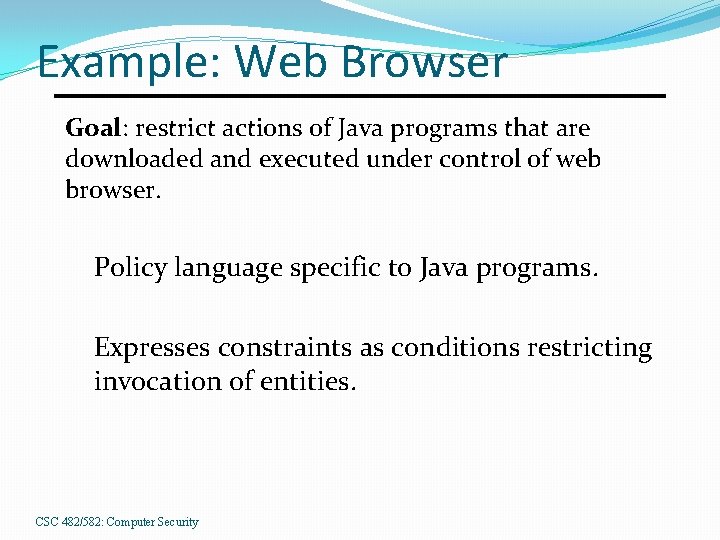
Example: Web Browser Goal: restrict actions of Java programs that are downloaded and executed under control of web browser. Policy language specific to Java programs. Expresses constraints as conditions restricting invocation of entities. CSC 482/582: Computer Security

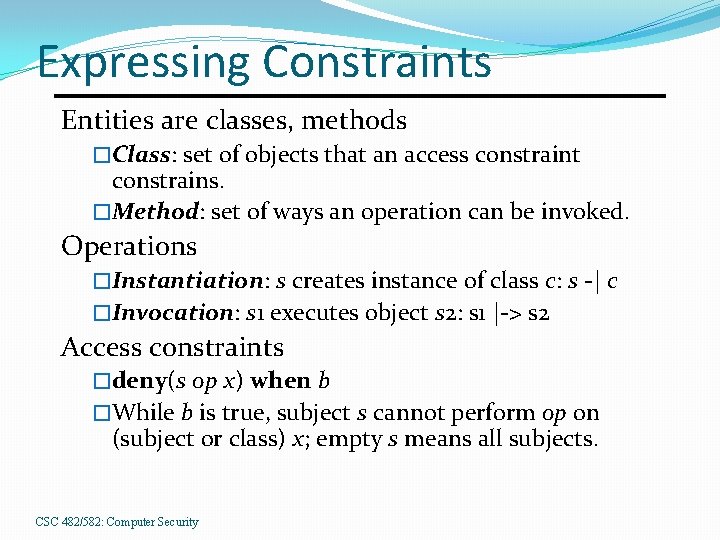
Expressing Constraints Entities are classes, methods �Class: set of objects that an access constraint constrains. �Method: set of ways an operation can be invoked. Operations �Instantiation: s creates instance of class c: s -| c �Invocation: s 1 executes object s 2: s 1 |-> s 2 Access constraints �deny(s op x) when b �While b is true, subject s cannot perform op on (subject or class) x; empty s means all subjects. CSC 482/582: Computer Security

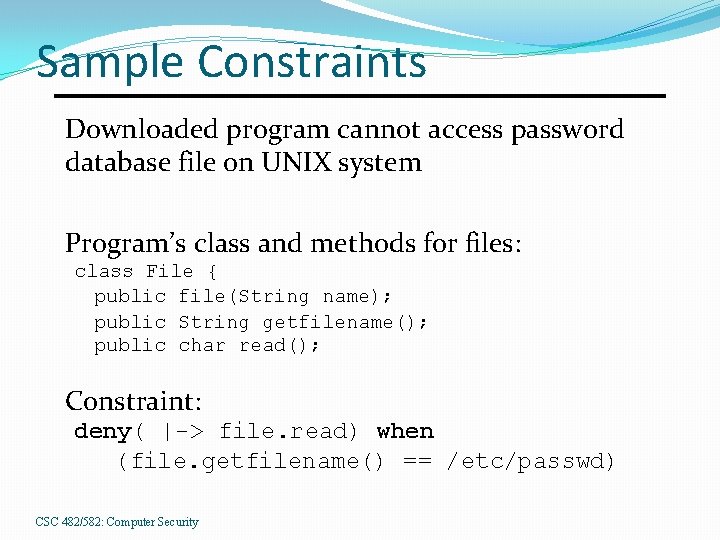
Sample Constraints Downloaded program cannot access password database file on UNIX system Program’s class and methods for files: class File { public file(String name); public String getfilename(); public char read(); Constraint: deny( |-> file. read) when (file. getfilename() == /etc/passwd) CSC 482/582: Computer Security

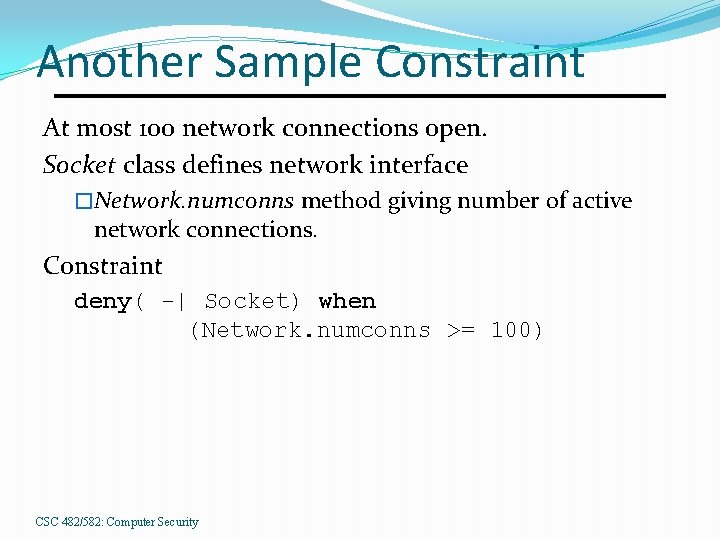
Another Sample Constraint At most 100 network connections open. Socket class defines network interface �Network. numconns method giving number of active network connections. Constraint deny( -| Socket) when (Network. numconns >= 100) CSC 482/582: Computer Security

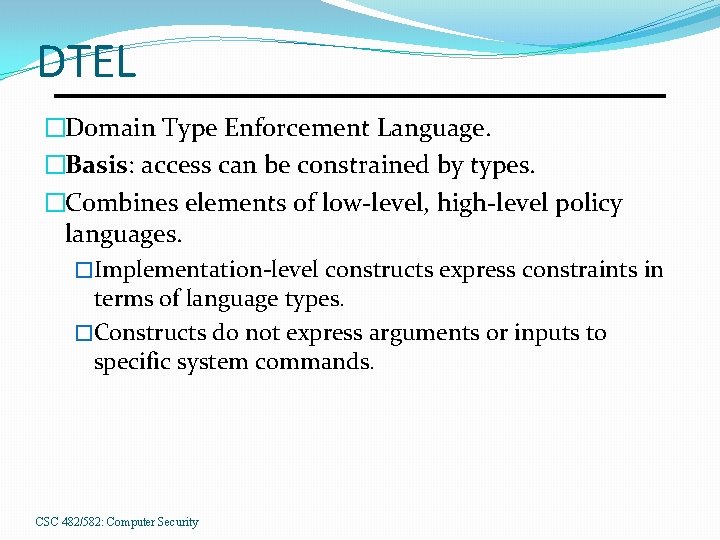
DTEL �Domain Type Enforcement Language. �Basis: access can be constrained by types. �Combines elements of low-level, high-level policy languages. �Implementation-level constructs express constraints in terms of language types. �Constructs do not express arguments or inputs to specific system commands. CSC 482/582: Computer Security

Example Goal: users cannot write to system binaries. Subjects in administrative domain can User must authenticate to enter that domain. Subjects belong to domains: d_user ordinary users d_administrative users d_login for login d_daemon system daemons CSC 482/582: Computer Security

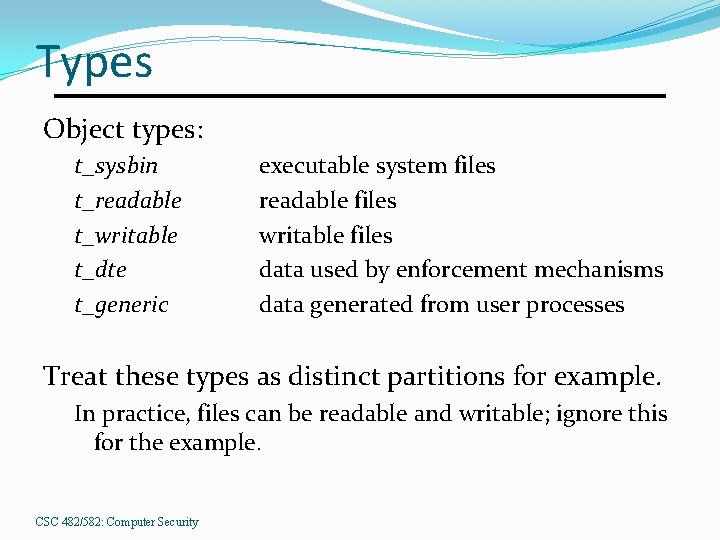
Types Object types: t_sysbin t_readable t_writable t_dte t_generic executable system files readable files writable files data used by enforcement mechanisms data generated from user processes Treat these types as distinct partitions for example. In practice, files can be readable and writable; ignore this for the example. CSC 482/582: Computer Security

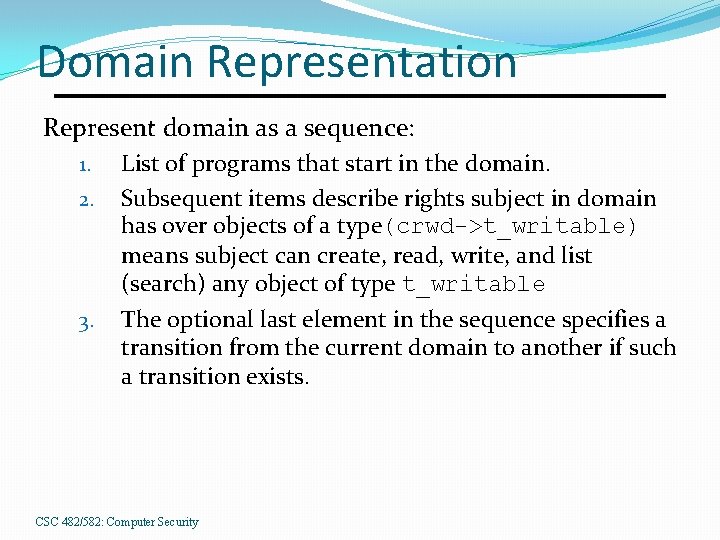
Domain Representation Represent domain as a sequence: 1. 2. 3. List of programs that start in the domain. Subsequent items describe rights subject in domain has over objects of a type(crwd->t_writable) means subject can create, read, write, and list (search) any object of type t_writable The optional last element in the sequence specifies a transition from the current domain to another if such a transition exists. CSC 482/582: Computer Security

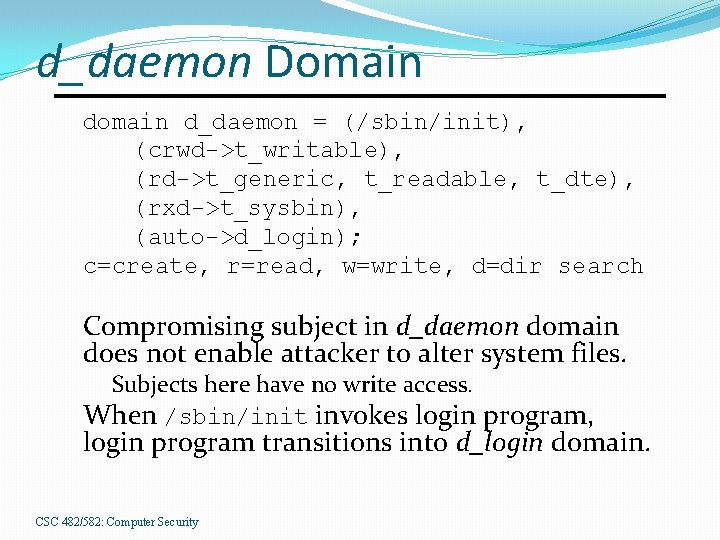
d_daemon Domain d_daemon = (/sbin/init), (crwd->t_writable), (rd->t_generic, t_readable, t_dte), (rxd->t_sysbin), (auto->d_login); c=create, r=read, w=write, d=dir search Compromising subject in d_daemon domain does not enable attacker to alter system files. Subjects here have no write access. When /sbin/init invokes login program, login program transitions into d_login domain. CSC 482/582: Computer Security

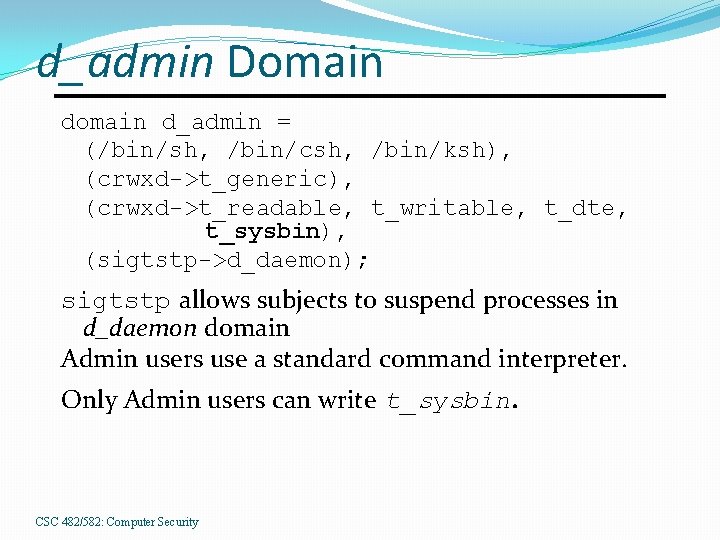
d_admin Domain d_admin = (/bin/sh, /bin/csh, /bin/ksh), (crwxd->t_generic), (crwxd->t_readable, t_writable, t_dte, t_sysbin), (sigtstp->d_daemon); sigtstp allows subjects to suspend processes in d_daemon domain Admin users use a standard command interpreter. Only Admin users can write t_sysbin. CSC 482/582: Computer Security

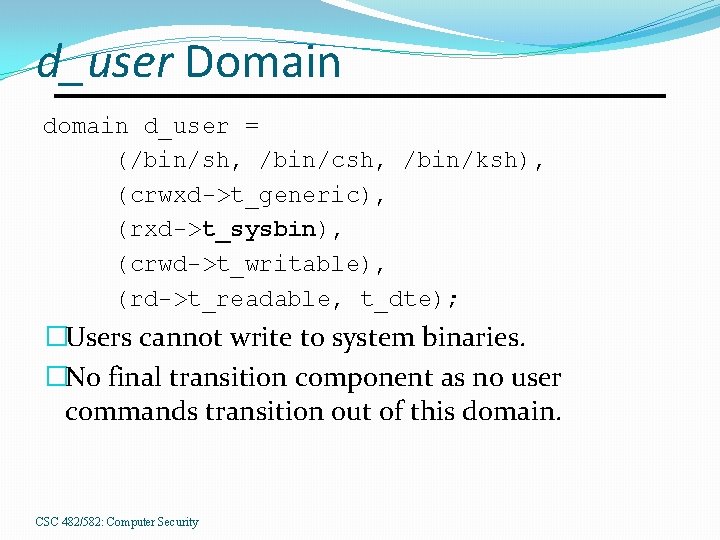
d_user Domain d_user = (/bin/sh, /bin/csh, /bin/ksh), (crwxd->t_generic), (rxd->t_sysbin), (crwd->t_writable), (rd->t_readable, t_dte); �Users cannot write to system binaries. �No final transition component as no user commands transition out of this domain. CSC 482/582: Computer Security

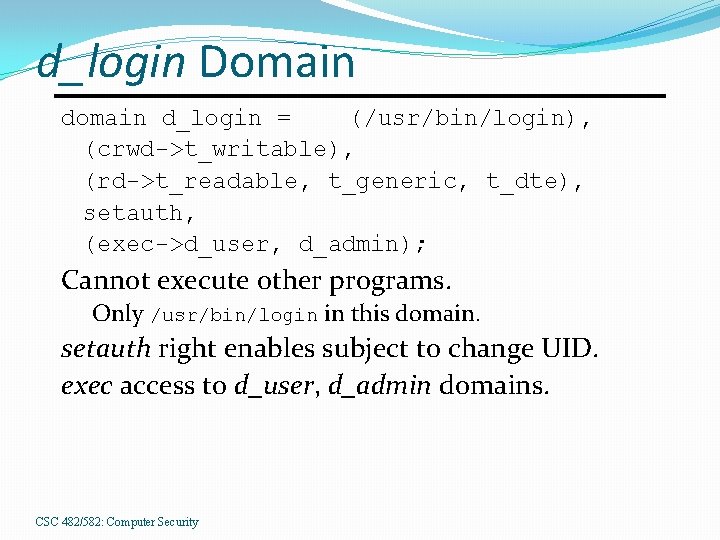
d_login Domain d_login = (/usr/bin/login), (crwd->t_writable), (rd->t_readable, t_generic, t_dte), setauth, (exec->d_user, d_admin); Cannot execute other programs. Only /usr/bin/login in this domain. setauth right enables subject to change UID. exec access to d_user, d_admin domains. CSC 482/582: Computer Security

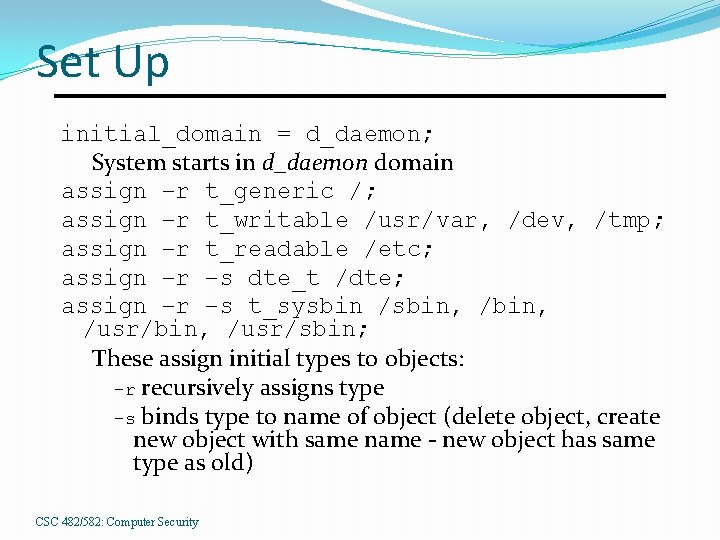
Set Up initial_domain = d_daemon; System starts in d_daemon domain assign –r t_generic /; assign –r t_writable /usr/var, /dev, /tmp; assign –r t_readable /etc; assign –r –s dte_t /dte; assign –r –s t_sysbin /sbin, /usr/bin, /usr/sbin; These assign initial types to objects: –r recursively assigns type –s binds type to name of object (delete object, create new object with same name - new object has same type as old) CSC 482/582: Computer Security

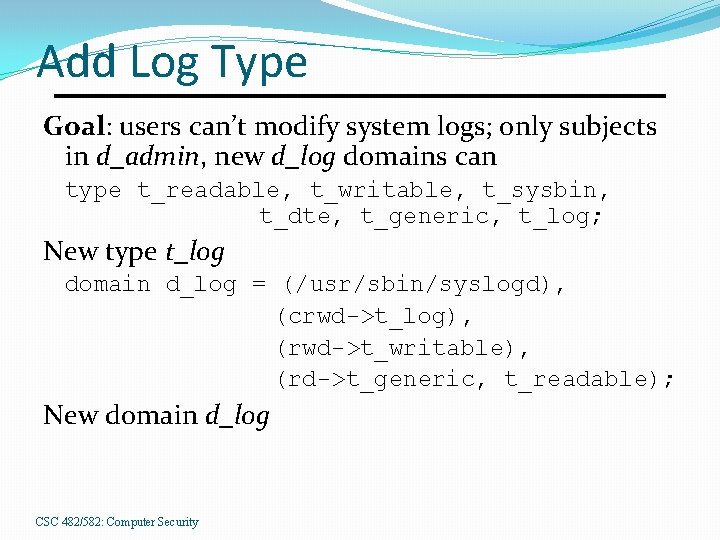
Add Log Type Goal: users can’t modify system logs; only subjects in d_admin, new d_log domains can type t_readable, t_writable, t_sysbin, t_dte, t_generic, t_log; New type t_log domain d_log = (/usr/sbin/syslogd), (crwd->t_log), (rwd->t_writable), (rd->t_generic, t_readable); New domain d_log CSC 482/582: Computer Security

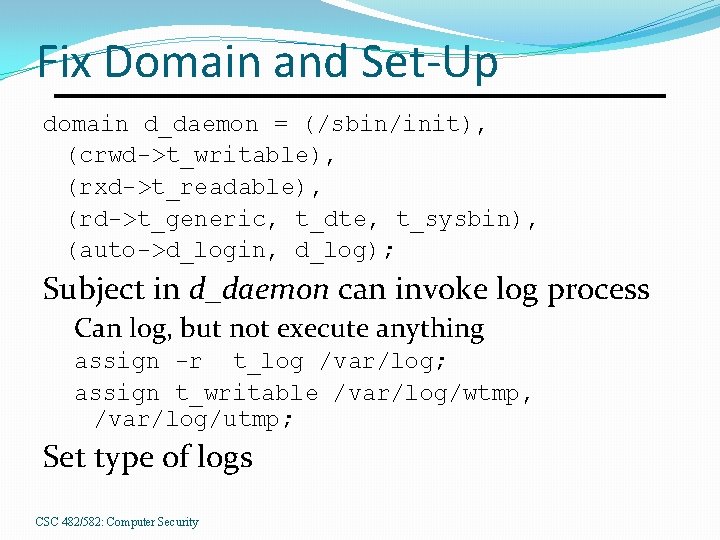
Fix Domain and Set-Up domain d_daemon = (/sbin/init), (crwd->t_writable), (rxd->t_readable), (rd->t_generic, t_dte, t_sysbin), (auto->d_login, d_log); Subject in d_daemon can invoke log process Can log, but not execute anything assign -r t_log /var/log; assign t_writable /var/log/wtmp, /var/log/utmp; Set type of logs CSC 482/582: Computer Security

Discussion Question The 4 th Amendment to the US Constitution “The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized. ” ILLINOIS v. CABALLES Decision 1/24/2005 �Roy Caballes pulled over by IL Police for speeding. �While one officer was writing him a ticket, another officer in another patrol car came by with a drug sniffing dog. �Dog “sniff” considered probable cause to search trunk. CSC 482/582: Computer Security

Discussion Question � ILLINOIS v. CABALLES Decision � SCOTUS ruled search constitutional. � Search did not “compromise any legitimate interest in privacy” because search could only reveal contraband, the concealment of which “compromises no legitimate privacy interest. ” � Questions: 1. Does this argument that a search cannot violate privacy if it can only reveal crime make sense? 2. What are the implications of this ruling for computerized law enforcement surveillance? CSC 482/582: Computer Security

Low-Level Policy Languages Set of inputs or arguments to commands. Check or set constraints on system. Low level of abstraction. Need details of system, commands. CSC 482/582: Computer Security

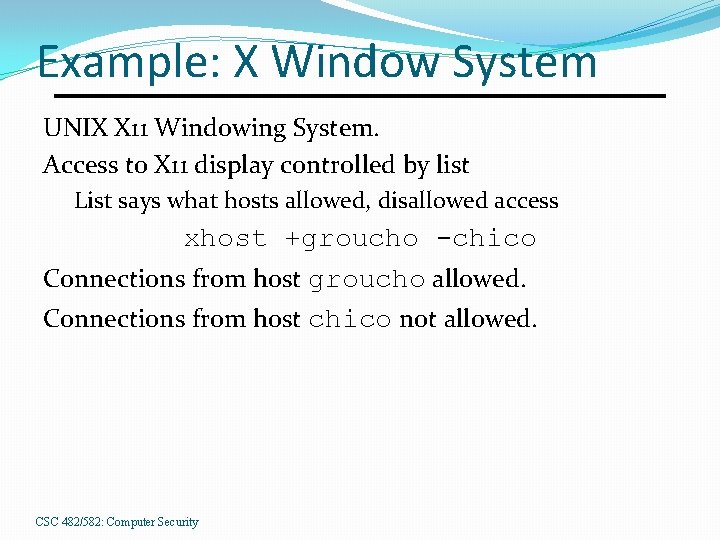
Example: X Window System UNIX X 11 Windowing System. Access to X 11 display controlled by list List says what hosts allowed, disallowed access xhost +groucho -chico Connections from host groucho allowed. Connections from host chico not allowed. CSC 482/582: Computer Security

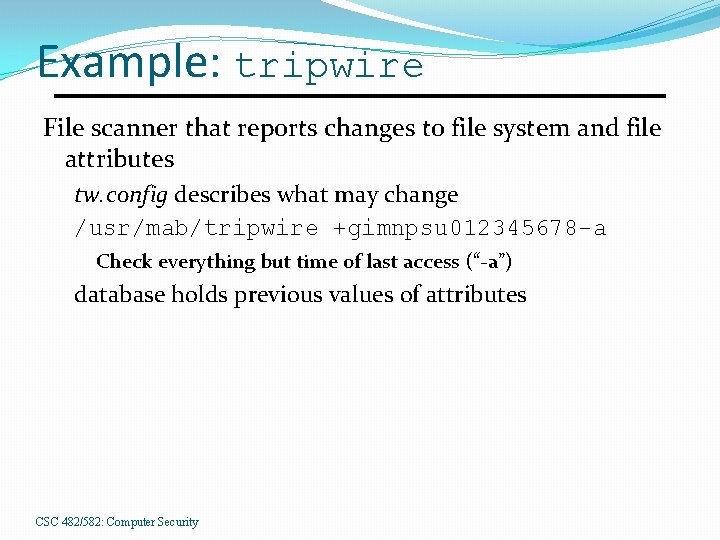
Example: tripwire File scanner that reports changes to file system and file attributes tw. config describes what may change /usr/mab/tripwire +gimnpsu 012345678 -a Check everything but time of last access (“-a”) database holds previous values of attributes CSC 482/582: Computer Security

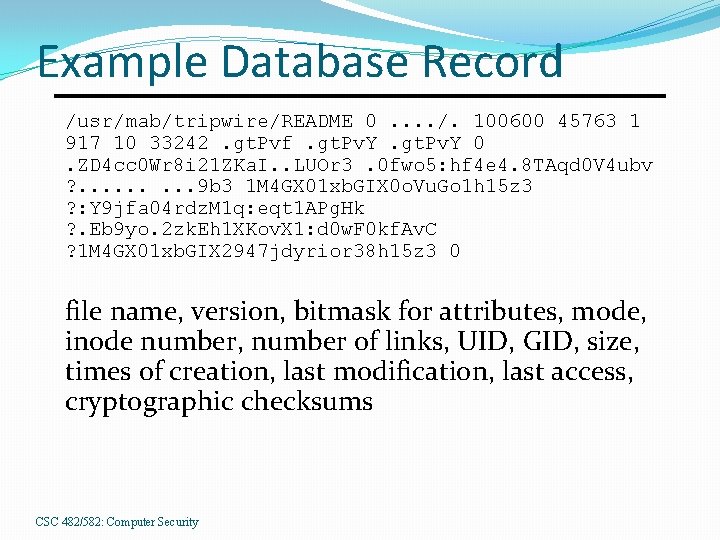
Example Database Record /usr/mab/tripwire/README 0. . /. 100600 45763 1 917 10 33242. gt. Pvf. gt. Pv. Y 0. ZD 4 cc 0 Wr 8 i 21 ZKa. I. . LUOr 3. 0 fwo 5: hf 4 e 4. 8 TAqd 0 V 4 ubv ? . . 9 b 3 1 M 4 GX 01 xb. GIX 0 o. Vu. Go 1 h 15 z 3 ? : Y 9 jfa 04 rdz. M 1 q: eqt 1 APg. Hk ? . Eb 9 yo. 2 zk. Eh 1 XKov. X 1: d 0 w. F 0 kf. Av. C ? 1 M 4 GX 01 xb. GIX 2947 jdyrior 38 h 15 z 3 0 file name, version, bitmask for attributes, mode, inode number, number of links, UID, GID, size, times of creation, last modification, last access, cryptographic checksums CSC 482/582: Computer Security

Comments System administrators not expected to edit database to set attributes properly. Checking for changes with tripwire is easy. Just run once to create the database, run again to check. Checking for conformance to policy is harder. Need to either edit database file, or (better) set system up to conform to policy, then run tripwire to construct database. CSC 482/582: Computer Security

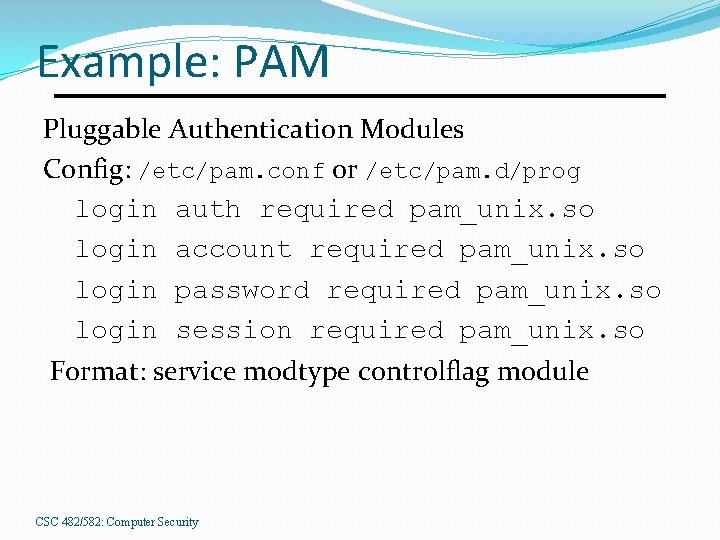
Example: PAM Pluggable Authentication Modules Config: /etc/pam. conf or /etc/pam. d/prog login auth required pam_unix. so login account required pam_unix. so login password required pam_unix. so login session required pam_unix. so Format: service modtype controlflag module CSC 482/582: Computer Security

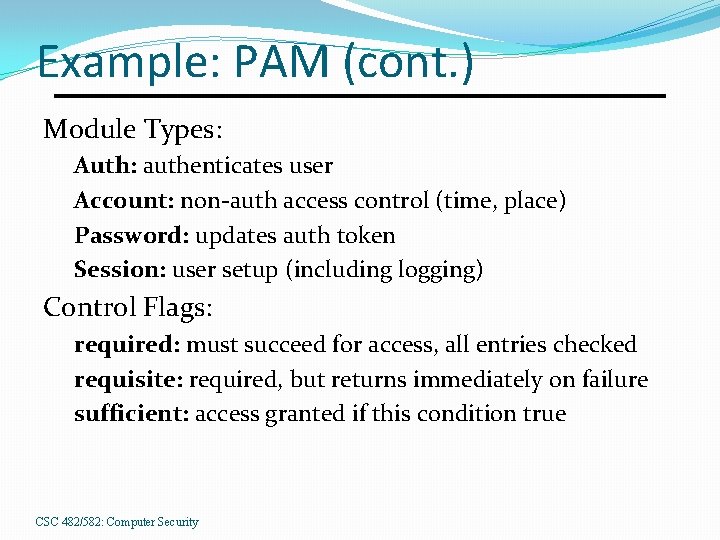
Example: PAM (cont. ) Module Types: Auth: authenticates user Account: non-auth access control (time, place) Password: updates auth token Session: user setup (including logging) Control Flags: required: must succeed for access, all entries checked requisite: required, but returns immediately on failure sufficient: access granted if this condition true CSC 482/582: Computer Security

Policy Models Abstract description of a policy or class of policies. Focus on points of interest in policies: Security levels in multilevel security models. Unclassified, Confidential, Secret, Top Secret Separation of duty in Clark-Wilson model. Conflict of interest in Chinese Wall model. CSC 482/582: Computer Security

Types of Security Policies Military (governmental) security policy �Policy primarily protecting confidentiality. Commercial security policy �Policy primarily protecting integrity. Confidentiality policy �Policy protecting only confidentiality. Integrity policy �Policy protecting only integrity. CSC 482/582: Computer Security

Key Points 1. Policies describe what is allowed. Policy languages like PAM, SELinux, describe policies. 2. Mechanisms control how policies are enforced. 3. Types of Access Control 1. Discretionary (DAC) 2. Mandatory (MAC) 3. Originator Based (ORBAC) 4. Trust underlies everything. CSC 482/582: Computer Security

References 1. Anderson, Ross, Security Engineering, Wiley, 2001. 2. David E. Bell and Leonard J. La. Padula, Secure Computer System: Unified Exposition and MULTICS Interpretation, MTR 2997 Rev. 1, The MITRE Corporation, Bedford, MA 01730 (Mar. 1976) http: //csrc. nist. gov/publications/history/bell 76. pdf 3. Bishop, Matt, Introduction to Computer Security, Addison. Wesley, 2005. 4. Department of Defense, Trusted Computer System Evaluation Criteria, Do. D 5200. 28 -STD (“Orange Book”), National Computer Security Center, Ft. Meade, MD 20755 (Dec. 1985) http: //csrc. nist. gov/publications/history/dod 85. pdf 5. Peter Loscocco and Stephen Smalley, “Integrating Flexible Support for Security Policies into the Linux Operating System, ” Proceedings of the FREENIX Track of the 2001 USENIX Annual Technical Conference, 2001. CSC 482/582: Computer Security