Cryptography and Network Security Digital Signatures DS Message












- Slides: 29

Cryptography and Network Security

Digital Signatures (DS) Ø Message authentication does not address issues of lack of trust Ø digital signatures provide the ability to: l l l verify author, date & time of signature authenticate message contents be verified by third parties to resolve disputes Ø DS includes message authentication function with additional capabilities

Digital Signature Properties must depend on the message signed Ø must use information unique to sender Ø l to prevent both forgery and denial must be relatively easy to produce Ø must be relatively easy to recognize & verify Ø be computationally infeasible to forge Ø l l Ø with new message for existing digital signature with fraudulent digital signature for given message be practical to save digital signature in storage

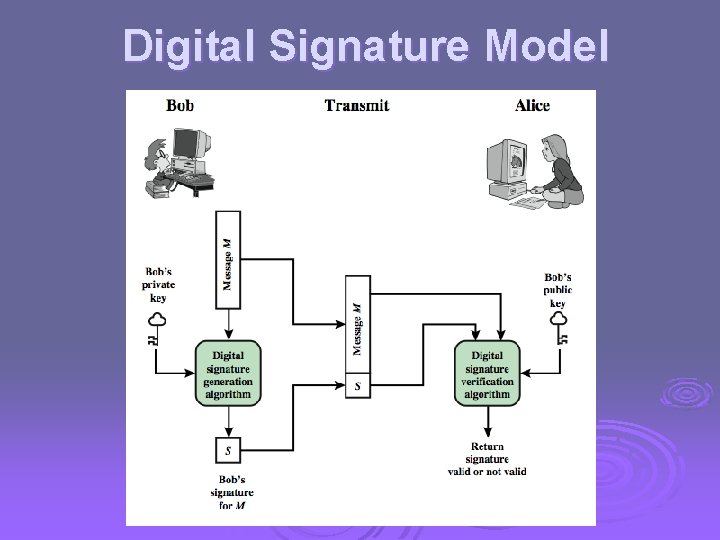
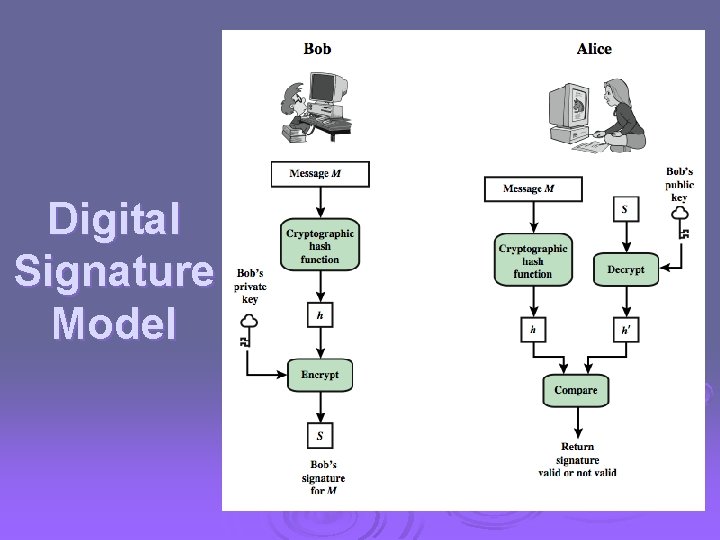
Direct Digital Signatures Ø involve only sender & receiver Ø assumed receiver has sender’s public-key Ø digital signature made by sender signing entire message or hash with private-key Ø can encrypt using receivers public-key Ø important that sign first then encrypt message & signature Ø security depends on sender’s private-key

Digital Signature Model

Digital Signature Model

Arbitrated Digital Signatures Ø involves use of an arbiter who l l validates any signed message then dated and sent to recipient Ø requires suitable level of trust in arbiter Ø can be implemented with either private or public-key algorithms Ø arbiter may or may not see message

Authentication Protocols Ø used to convince parties of each others identity and to exchange session keys Ø may be one-way or mutual Ø key issues are l l confidentiality – to protect session keys timeliness – to prevent replay attacks Ø published protocols are often found to have flaws and need to be modified

Using Symmetric Encryption Ø Can use a two-level hierarchy of keys Ø usually with a trusted Key Distribution Center (KDC) l l l each party shares own master key with KDC generates session keys used for connections between parties master keys used to distribute these to them

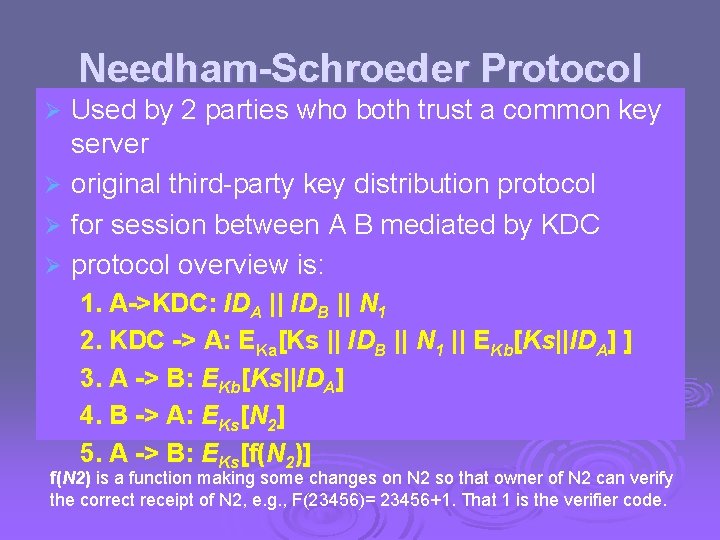
Needham-Schroeder Protocol Used by 2 parties who both trust a common key server Ø original third-party key distribution protocol Ø for session between A B mediated by KDC Ø protocol overview is: Ø 1. A->KDC: IDA || IDB || N 1 2. KDC -> A: EKa[Ks || IDB || N 1 || EKb[Ks||IDA] ] 3. A -> B: EKb[Ks||IDA] 4. B -> A: EKs[N 2] 5. A -> B: EKs[f(N 2)] f(N 2) is a function making some changes on N 2 so that owner of N 2 can verify the correct receipt of N 2, e. g. , F(23456)= 23456+1. That 1 is the verifier code.

Needham-Schroeder Protocol Ø used to securely distribute a new session key for communications between A & B Ø but is vulnerable to a replay attack if an old session key has been compromised l then message 3 can be resent convincing B that is communicating with A Ø modifications to address this require: l l timestamps using an extra nonce

Using Public-Key Encryption Ø have a range of approaches based on the use of public-key encryption Ø need to ensure have correct public keys for other parties Ø using a central Authentication Server (AS) Ø various protocols exist using timestamps or nonces

Denning Authentication Server Protocol Ø Denning presented the following: 1. A -> AS: IDA || IDB 2. AS -> A: EPRas[IDA||PUa||T] || EPRas[IDB||PUb||T] 3. A -> B: EPRas[IDA||PUa||T] || EPRas[IDB||PUb||T] || EPUb[EPRa[Ks||T]] Note that to avoid the risk of exposure by the AS session key is chosen by A, hence AS need not be trusted to protect it Ø timestamps prevent replay attacks but require synchronized clocks Ø

One-Way Authentication The recipient wants some assurance that the message is from the alleged sender. One-Way Authentication addresses these requirements. Ø Required when sender & receiver communicate in connectionless mode (eg. email) Ø Have header in clear text so can be delivered by email systems Ø May want contents of body protected & sender authenticated Ø

One-Way Authentication Using Symmetric Encryption Ø can refine use of KDC but can’t have final exchange of nonces: 1. A->KDC: IDA || IDB || N 1 2. KDC -> A: EKa[Ks || IDB || N 1 || EKb[Ks||IDA] ] 3. A -> B: EKb[Ks||IDA] || EKs[M] Ø does not protect against replays l could rely on timestamp in message, though email delays make this problematic

One-Way Authentication Using Public-Key Approaches Ø have seen some public-key approaches Ø if confidentiality is major concern, can use: A->B: EPUb[Ks] || EKs[M] l has encrypted session key, encrypted message Ø if authentication needed use a digital signature with a digital certificate: A->B: M || EPRa[H(M)] || EPRa[T||IDA||PUa] l with message, signature, certificate

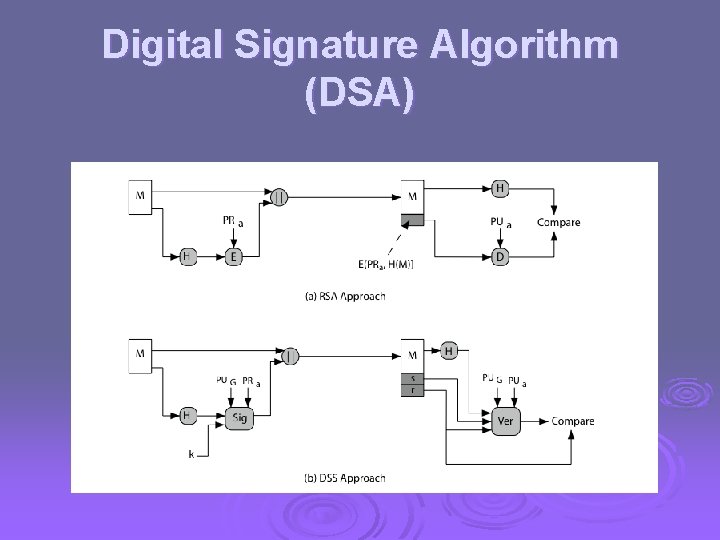
Digital Signature Standard (DSS) US Govt approved signature scheme Ø designed by NIST & NSA in early 90's Ø published as FIPS-186 in 1991 Ø revised in 1993, 1996 & then 2000 Ø uses the SHA hash algorithm Ø DSS is the standard, DSA is the algorithm Ø FIPS 186 -2 (2000) includes alternative RSA & elliptic curve signature variants Ø

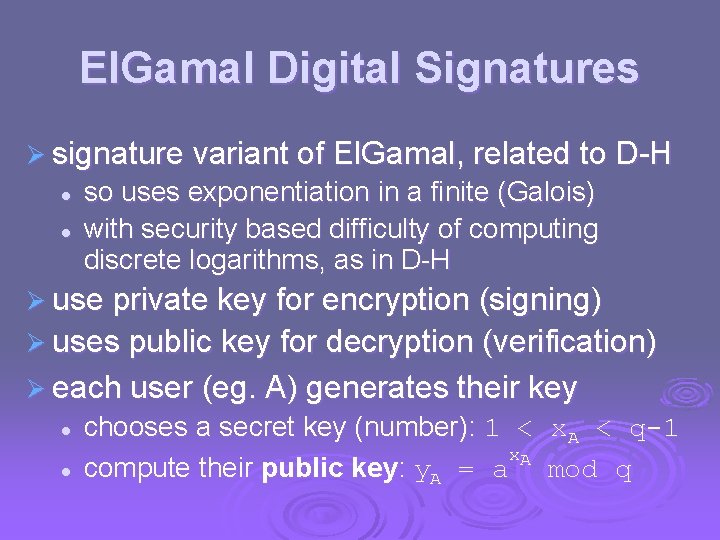
El. Gamal Digital Signatures Ø signature variant of El. Gamal, related to D-H l l so uses exponentiation in a finite (Galois) with security based difficulty of computing discrete logarithms, as in D-H Ø use private key for encryption (signing) Ø uses public key for decryption (verification) Ø each user (eg. A) generates their key l l chooses a secret key (number): 1 < x. A < q-1 x. A compute their public key: y. A = a mod q

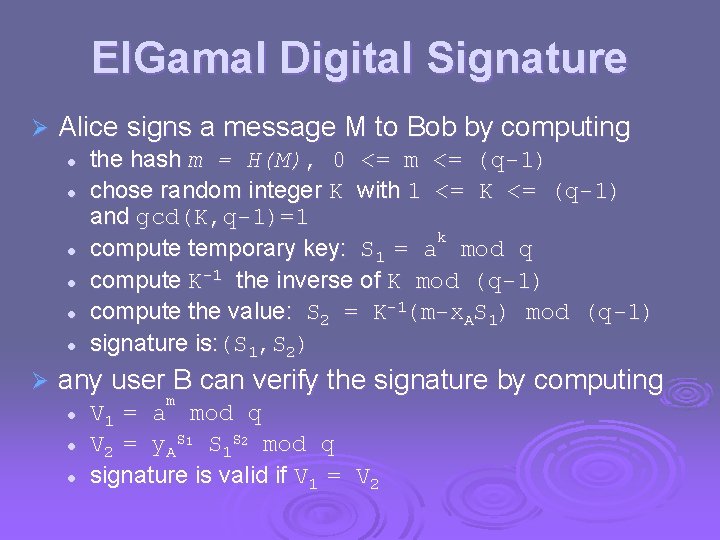
El. Gamal Digital Signature Ø Alice signs a message M to Bob by computing l l l Ø the hash m = H(M), 0 <= m <= (q-1) chose random integer K with 1 <= K <= (q-1) and gcd(K, q-1)=1 k compute temporary key: S 1 = a mod q compute K-1 the inverse of K mod (q-1) compute the value: S 2 = K-1(m-x. AS 1) mod (q-1) signature is: (S 1, S 2) any user B can verify the signature by computing l l l m V 1 = a mod q V 2 = y. AS 1 S 1 S 2 mod q signature is valid if V 1 = V 2

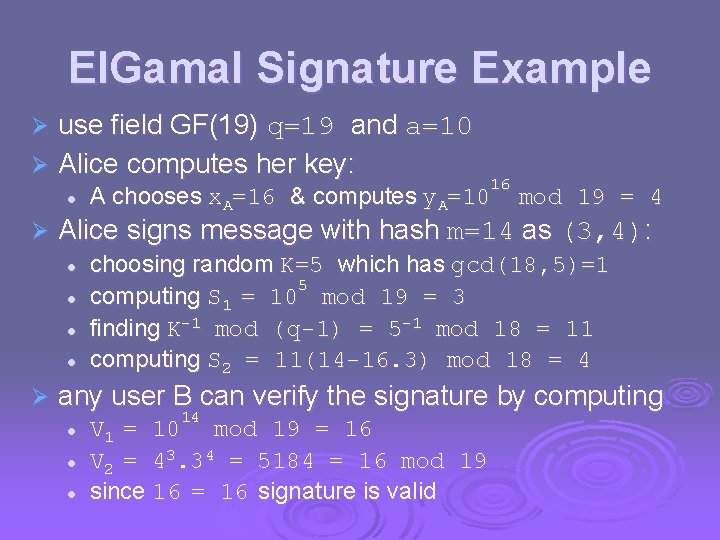
El. Gamal Signature Example use field GF(19) q=19 and a=10 Ø Alice computes her key: Ø l Ø mod 19 = 4 Alice signs message with hash m=14 as (3, 4): l l Ø 16 A chooses x. A=16 & computes y. A=10 choosing random K=5 which has gcd(18, 5)=1 5 computing S 1 = 10 mod 19 = 3 finding K-1 mod (q-1) = 5 -1 mod 18 = 11 computing S 2 = 11(14 -16. 3) mod 18 = 4 any user B can verify the signature by computing l l l 14 V 1 = 10 mod 19 = 16 V 2 = 43. 34 = 5184 = 16 mod 19 since 16 = 16 signature is valid

Schnorr Digital Signatures Ø also uses exponentiation in a finite (Galois) l security based on discrete logarithms, as in D-H Ø minimizes message dependent computation l multiplying a 2 n-bit integer with an n-bit integer Ø main work can be done in idle time prime modulus p l l using a p– 1 has a prime factor q of appropriate size typically p 1024 -bit and q 160 -bit numbers

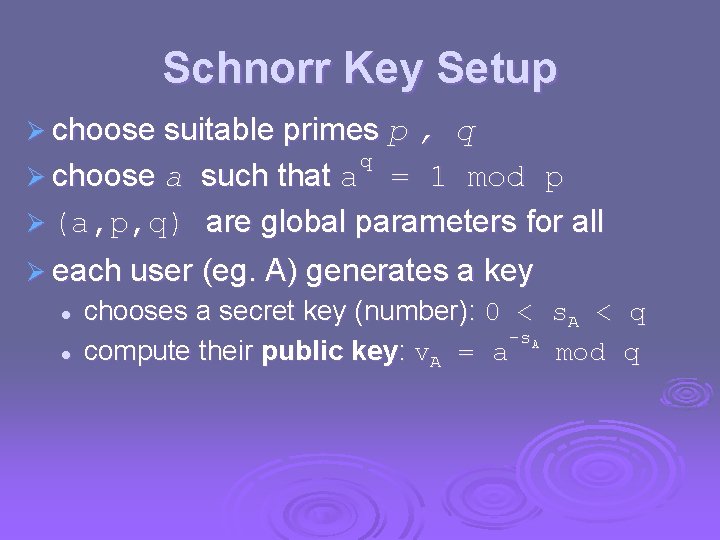
Schnorr Key Setup Ø choose suitable primes p , q q Ø choose a such that a = 1 mod p Ø (a, p, q) are global parameters for all Ø each user (eg. A) generates a key l l chooses a secret key (number): 0 < -s. A compute their public key: v. A = a s. A < mod q q

Schnorr Signature Ø user signs message by choosing random r with 0<r<q and computing x = ar mod p l concatenate message with x and hash result to computing: e = H(M || x) l computing: y = (r + se) mod q l signature is pair (e, y) Ø any other user can verify the signature as follows: y e mod p l computing: x' = a v l verifying that: e = H(M || x’) l

Digital Signature Algorithm (DSA) Ø creates a 320 bit signature Ø with 512 -1024 bit security Ø smaller and faster than RSA Ø a digital signature scheme only Ø security depends on difficulty of computing discrete logarithms Ø variant of El. Gamal & Schnorr schemes

Digital Signature Algorithm (DSA)

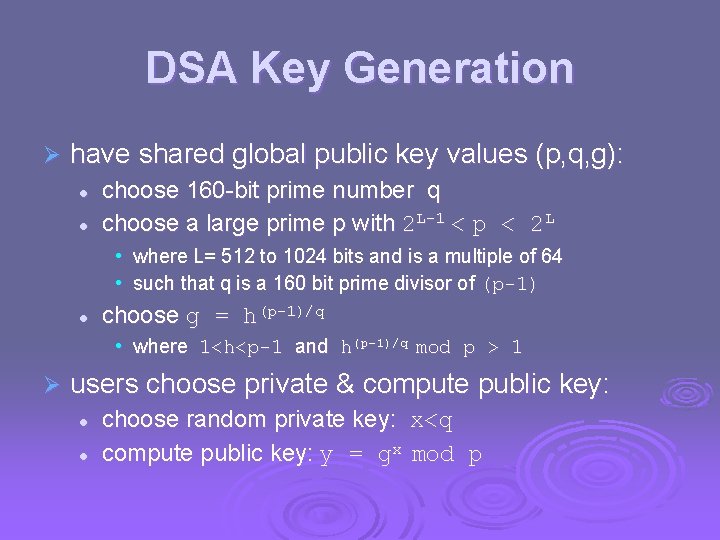
DSA Key Generation Ø have shared global public key values (p, q, g): l l choose 160 -bit prime number q choose a large prime p with 2 L-1 < p < 2 L • where L= 512 to 1024 bits and is a multiple of 64 • such that q is a 160 bit prime divisor of (p-1) l choose g = h(p-1)/q • where 1<h<p-1 and h(p-1)/q mod p > 1 Ø users choose private & compute public key: l l choose random private key: x<q compute public key: y = gx mod p

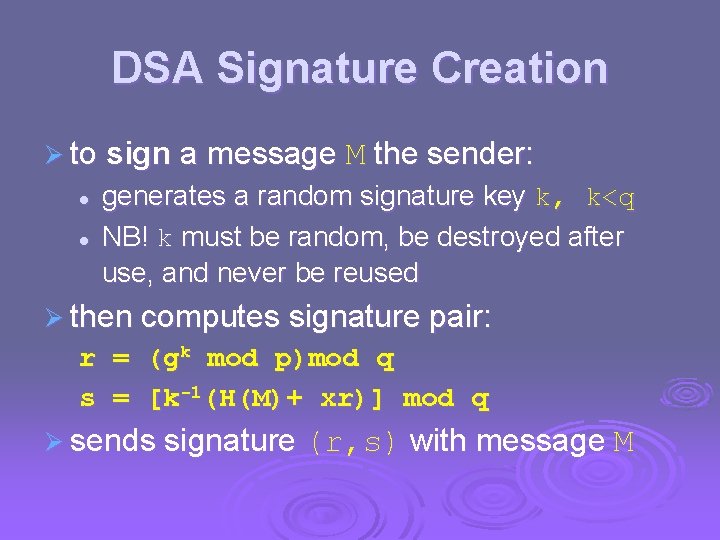
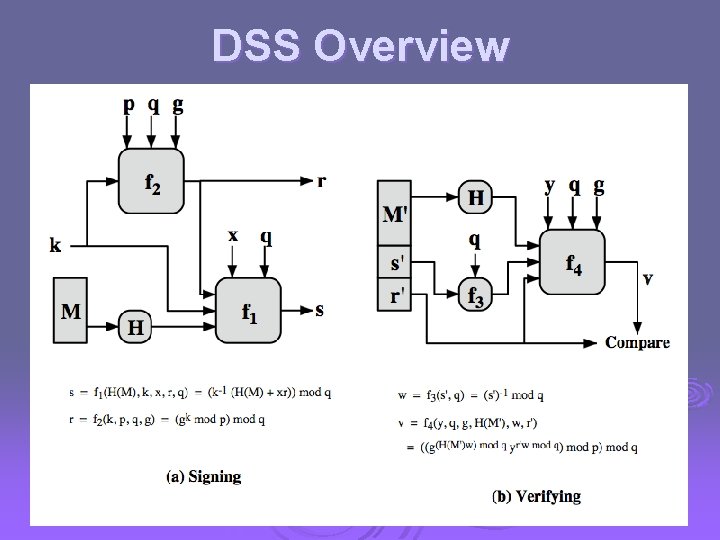
DSA Signature Creation Ø to sign a message M the sender: l l generates a random signature key k, k<q NB! k must be random, be destroyed after use, and never be reused Ø then computes signature pair: r = (gk mod p)mod q s = [k-1(H(M)+ xr)] mod q Ø sends signature (r, s) with message M

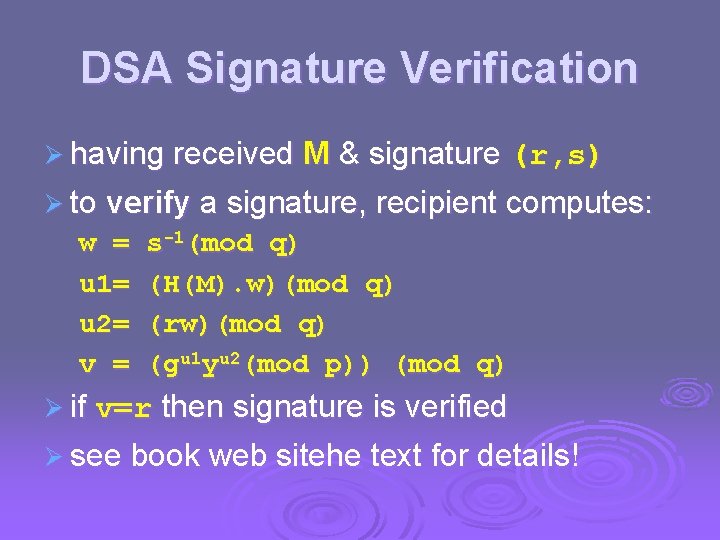
DSA Signature Verification Ø having received M & signature (r, s) Ø to verify a signature, recipient computes: w = u 1= u 2= v = s-1(mod q) (H(M). w)(mod q) (rw)(mod q) (gu 1 yu 2(mod p)) (mod q) Ø if v=r then signature is verified Ø see book web sitehe text for details!

DSS Overview