Postquantum cryptography Andreas Hlsing 19 12 2017 Todays



















![Hash-based Signature Schemes [Mer 89] Post quantum Only secure hash function Security well understood Hash-based Signature Schemes [Mer 89] Post quantum Only secure hash function Security well understood](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-38.jpg)
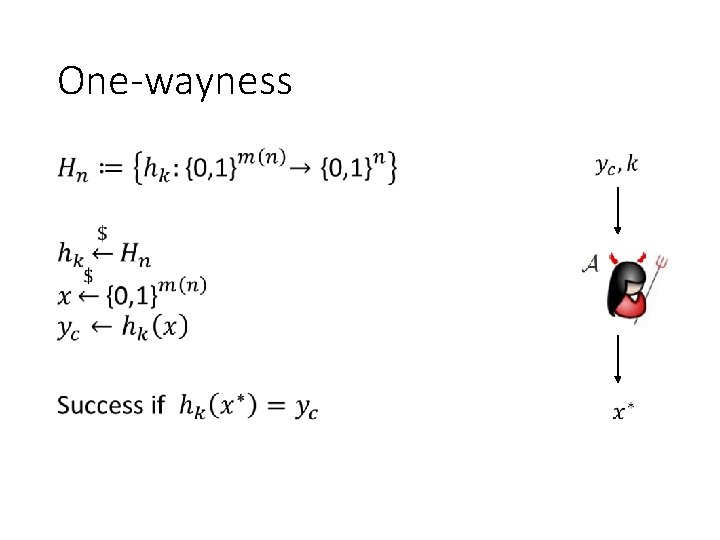
![Lamport-Diffie OTS [Lam 79] Message M = b 1, …, bm, OWF H SK Lamport-Diffie OTS [Lam 79] Message M = b 1, …, bm, OWF H SK](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-49.jpg)





![Recap LD-OTS [Lam 79] Message M = b 1, …, bm, OWF H SK Recap LD-OTS [Lam 79] Message M = b 1, …, bm, OWF H SK](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-61.jpg)







![HORS [RR 02] * Message M, OWF H, CRHF H’ = n bit Parameters HORS [RR 02] * Message M, OWF H, CRHF H’ = n bit Parameters](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-80.jpg)



- Slides: 87

Post-quantum cryptography Andreas Hülsing 19. 12. 2017

Today‘s Crypto-Eco-System Public key cryptography: • Deployed schemes are based on RSA- and discrete logarithm problem (incl. ECC, DH. . . ). Secret key / Symmetric cryptography: • Wide range of different schemes. • Not based on „hard problems“, rather on „design principles“

Today‘s Crypto-Eco-System • We need public key cryptography for almost all applications of cryptography • Remember key exchange problem • Advanced applications mostly rely on hardness of same problems

What happens if the TWO problems are solved? • No (practical) secure communication • No online payment • No e-Commerce • No Internet privacy • No private online communication • with insurance company, public institutions, etc. • With private contacts (this includes Skype, whatsapp, etc. (although these are already questionable today. . )) • Everyone in same Wi. Fi network can listen to your connection

Quantum computers • 1980 Theoretical concept • 1994 Shor‘s algorithm • 1995 First quantum gate experimentally realized • 1996 Grover‘s algorithm • 2014 Largest number factored: 56153

(Big) Players in quantum game


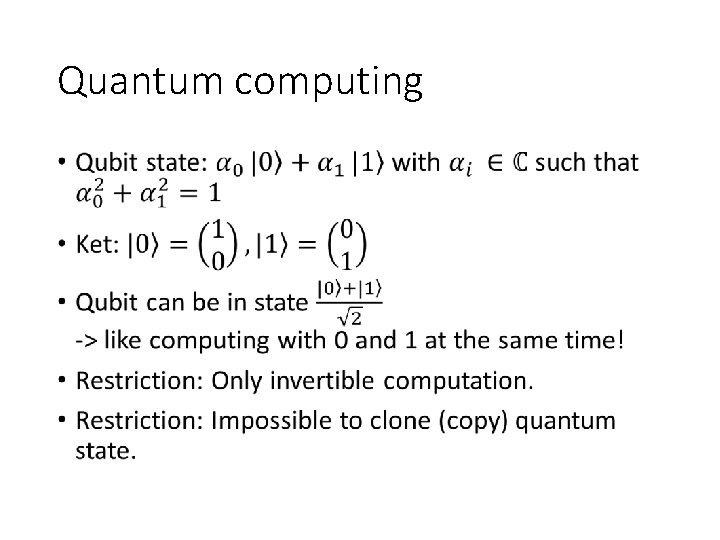
Quantum computing •

Quantum computing II • Restriction: To learn outcome one has to measure. • Colapses qubit to basis state • 1 qubit leads 1 classical bit of information • Randomized process • Goal: Amplify amplitude of solution vector. • Many fancy things like quantum teleportation • Not important for us

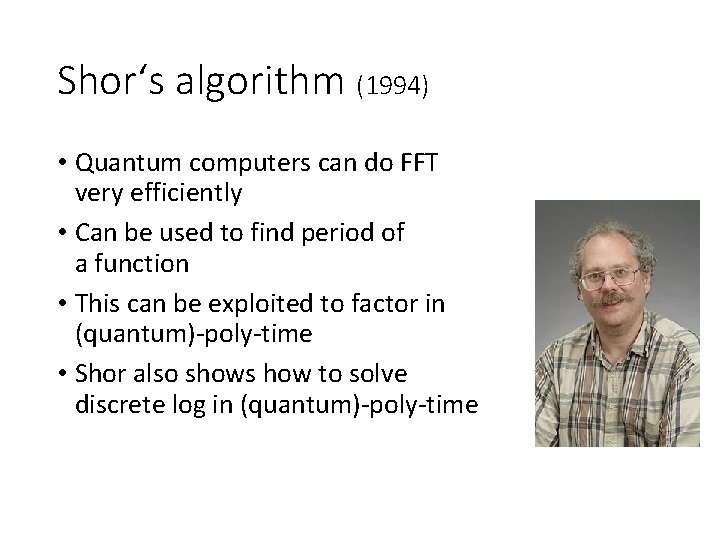
Shor‘s algorithm (1994) • Quantum computers can do FFT very efficiently • Can be used to find period of a function • This can be exploited to factor in (quantum)-poly-time • Shor also shows how to solve discrete log in (quantum)-poly-time

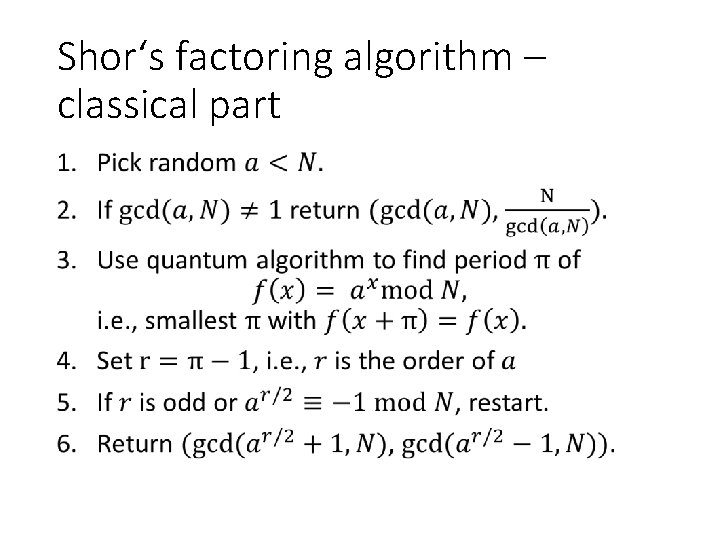
Shor‘s factoring algorithm – classical part •

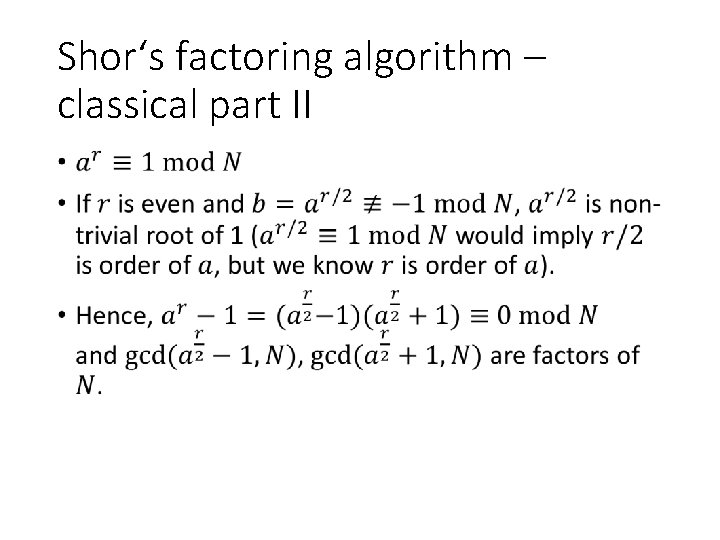
Shor‘s factoring algorithm – classical part II •

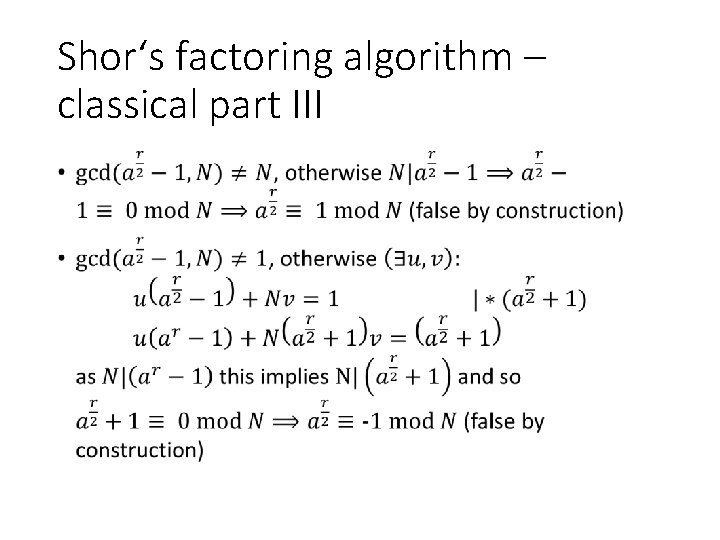
Shor‘s factoring algorithm – classical part III •

Example •

Grover‘s algorithm •

A comment on D-Waves quantum annealing computer This is no quantum computer that breaks crypto!


Interim conclusion • Quantum computers are powerful but not almighty • Can be used to break some crypto but not all crypto: Asymmetric falls, symmetric survives • Unclear when large scale QC‘s ready • If we want to preserve privacy for more than a short time: We have to react now!

Quantum Cryptography

Why not beat ‘em with their own weapons? • QKD: Quantum Key distribution. • Based on some nice quantum properties: entanglement & collapsing measurments • Information theoretic security -> Great! • For sale today! • So why don‘t we use this? • Only short distance, point-to-point connections! • Internet? No way! • Longer distances require „trusted-repeaters“ • We all know where this leads. . . • More issues with actual implementations. . .

Post-Quantum Cryptography

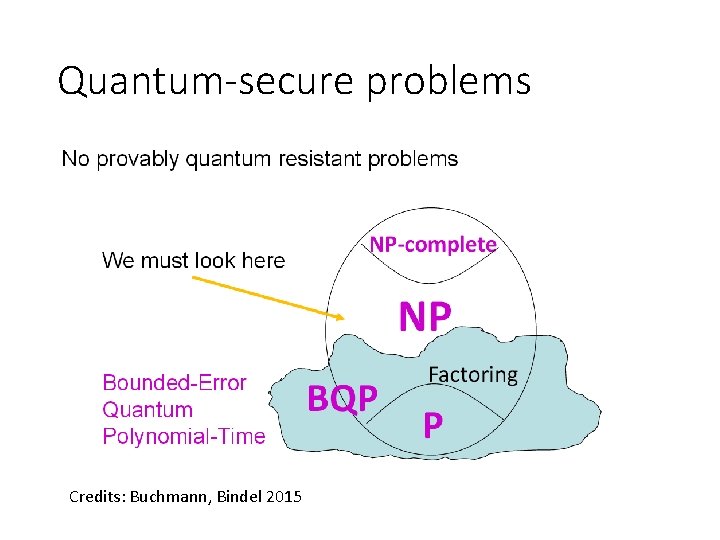
Quantum-secure problems Credits: Buchmann, Bindel 2015

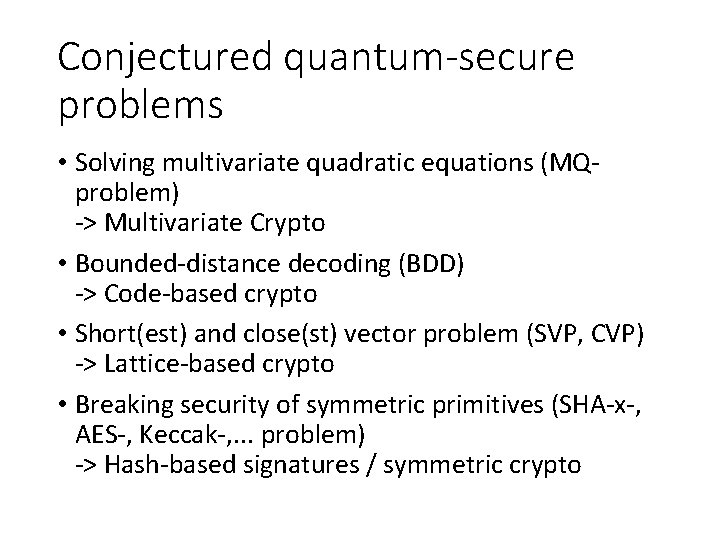
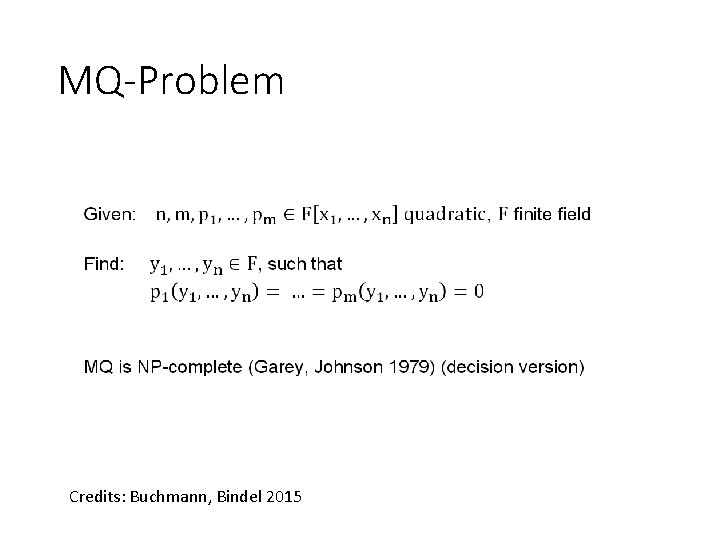
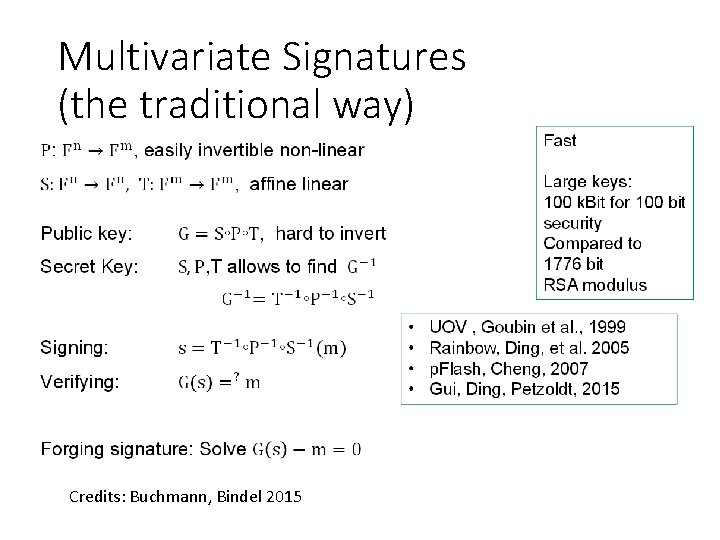
Conjectured quantum-secure problems • Solving multivariate quadratic equations (MQproblem) -> Multivariate Crypto • Bounded-distance decoding (BDD) -> Code-based crypto • Short(est) and close(st) vector problem (SVP, CVP) -> Lattice-based crypto • Breaking security of symmetric primitives (SHA-x-, AES-, Keccak-, . . . problem) -> Hash-based signatures / symmetric crypto

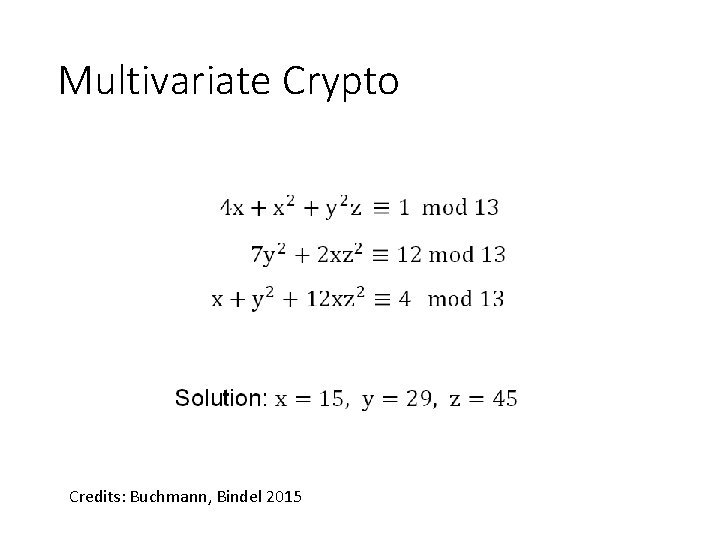
Multivariate Crypto Credits: Buchmann, Bindel 2015

MQ-Problem Credits: Buchmann, Bindel 2015

Multivariate Signatures (the traditional way) Credits: Buchmann, Bindel 2015

Multivariate Cryptography (the traditional way) •

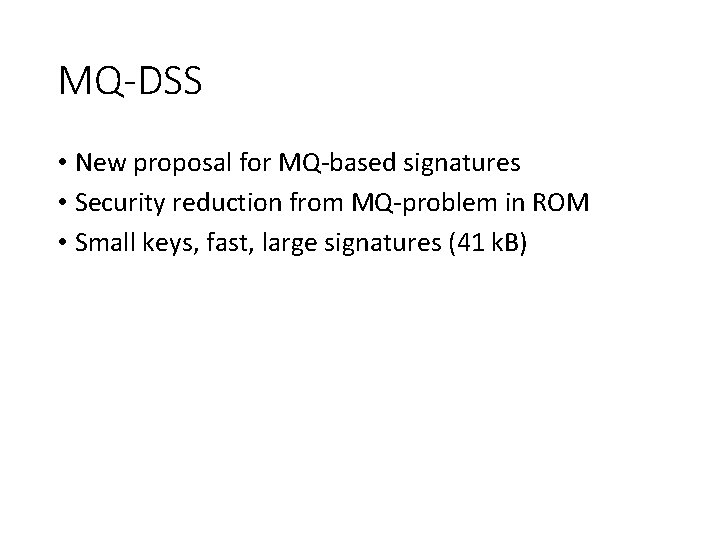
MQ-DSS • New proposal for MQ-based signatures • Security reduction from MQ-problem in ROM • Small keys, fast, large signatures (41 k. B)

Coding-based cryptography - BDD Credits: Buchmann, Bindel 2015

Mc. Eliece PKE (1978) Credits: Buchmann, Bindel 2015

Code-based cryptography •

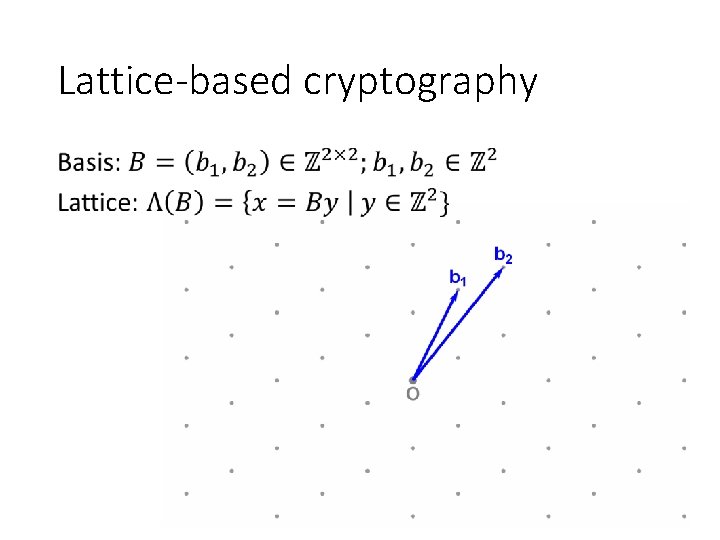
Lattice-based cryptography •

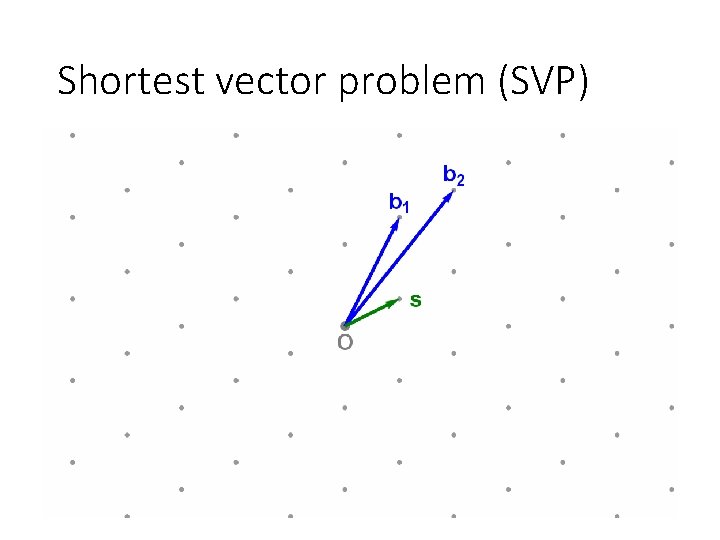
Shortest vector problem (SVP)

(Worst-case) Lattice Problems •

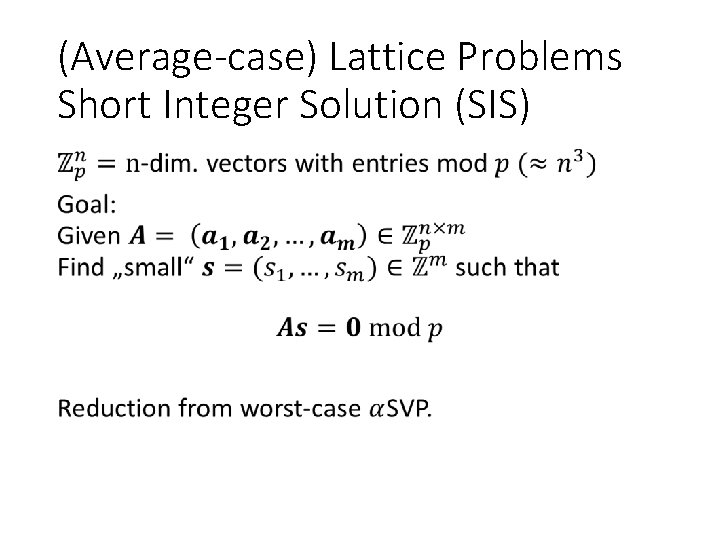
(Average-case) Lattice Problems Short Integer Solution (SIS) •

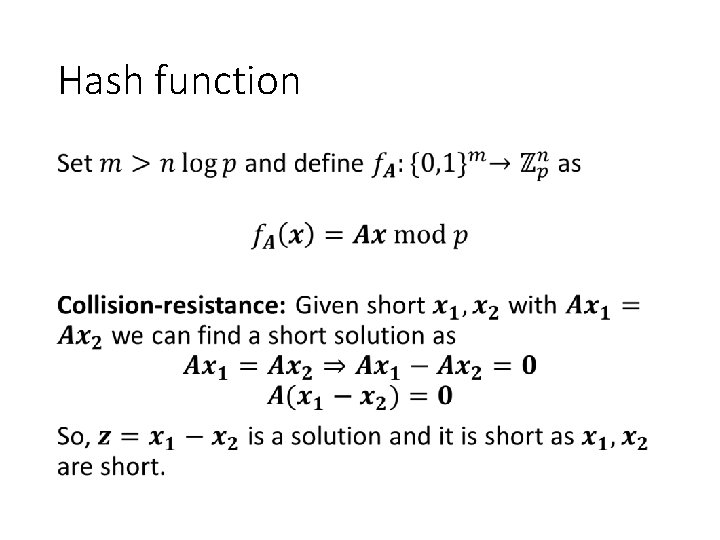
Hash function •

Lattice-based crypto • SIS: Allows to construct signature schemes, hash functions, . . . , basically minicrypt. • For more advanced applications: Learning with errors (LWE) • Allows to build PKE, IBE, FHE, . . . • Performance: Sizes can almost reach those of RSA (just small const. factor), really fast. • BUT: Exact security not well accessed, yet. Especially, no good estimate for quantum computer aided attacks.
![Hashbased Signature Schemes Mer 89 Post quantum Only secure hash function Security well understood Hash-based Signature Schemes [Mer 89] Post quantum Only secure hash function Security well understood](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-38.jpg)
Hash-based Signature Schemes [Mer 89] Post quantum Only secure hash function Security well understood Fast 7 -6 -2021 PAGE 38

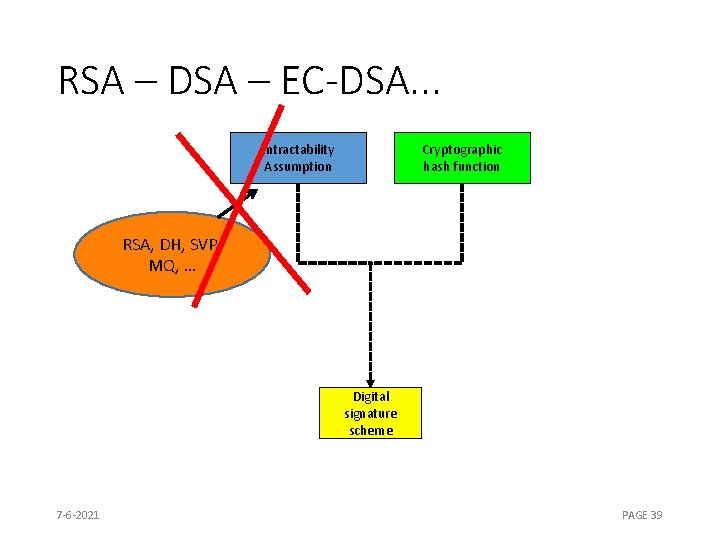
RSA – DSA – EC-DSA. . . Intractability Assumption Cryptographic hash function RSA, DH, SVP, MQ, … Digital signature scheme 7 -6 -2021 PAGE 39

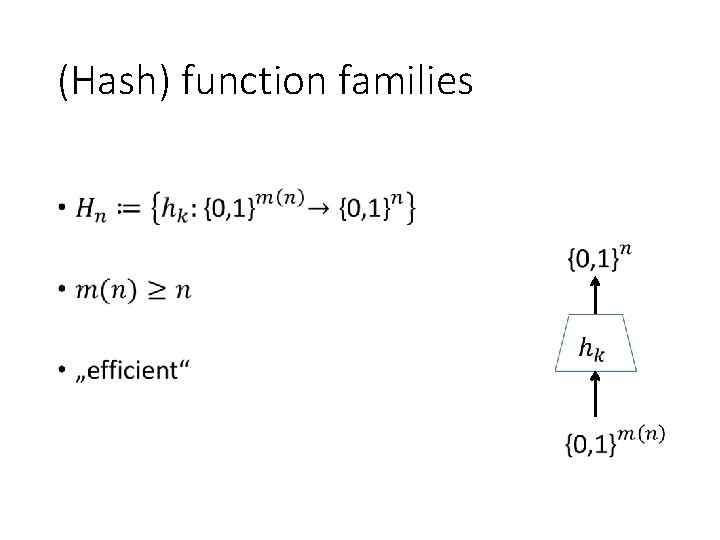
(Hash) function families •
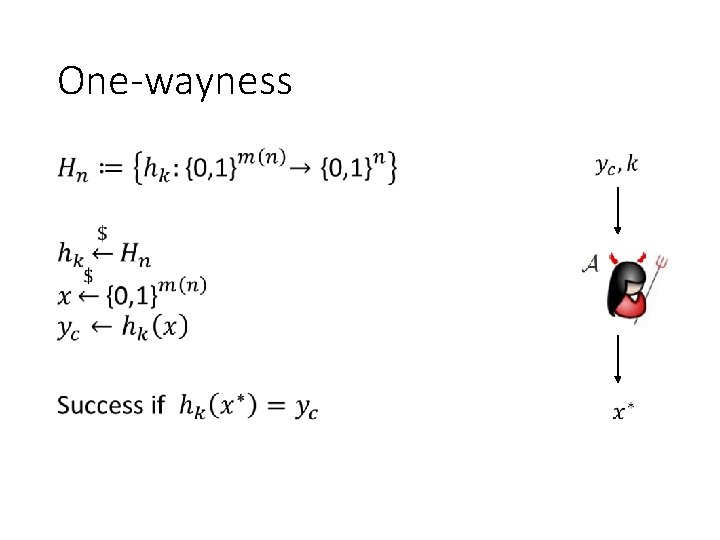
One-wayness •

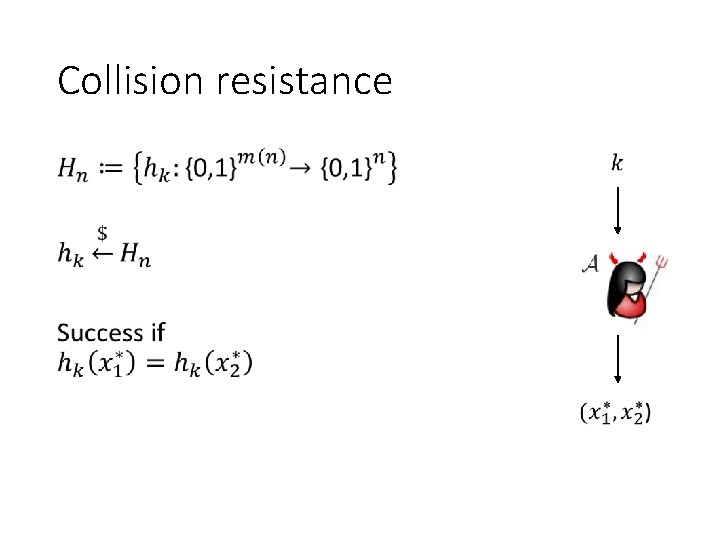
Collision resistance

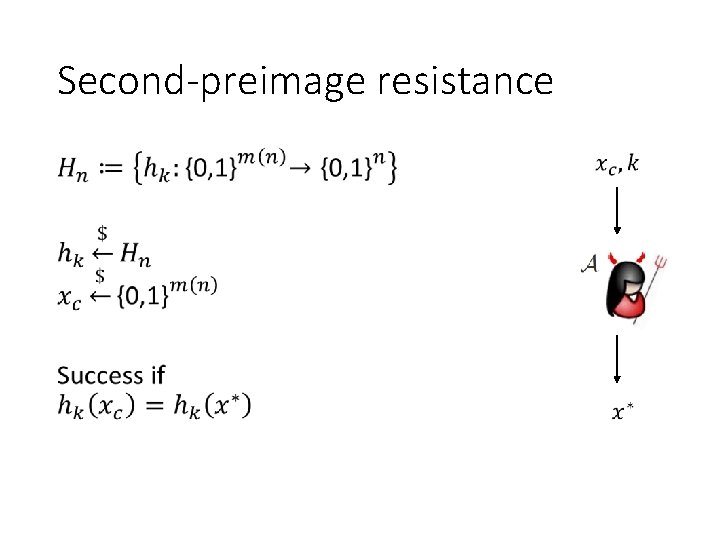
Second-preimage resistance •

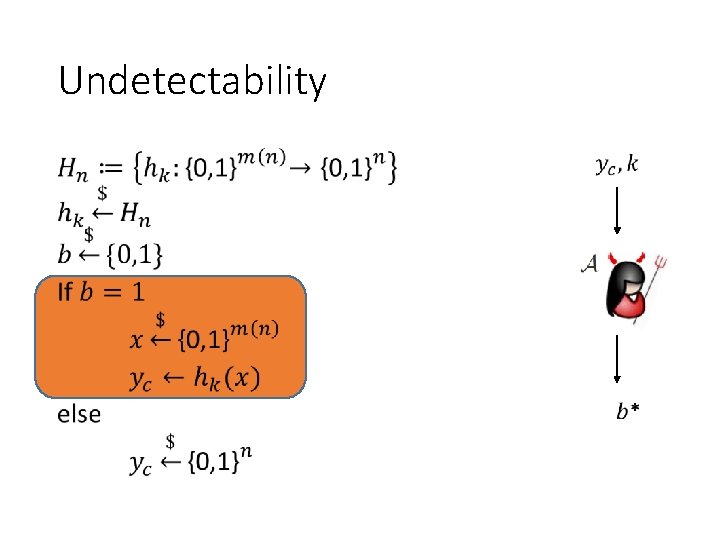
Undetectability •

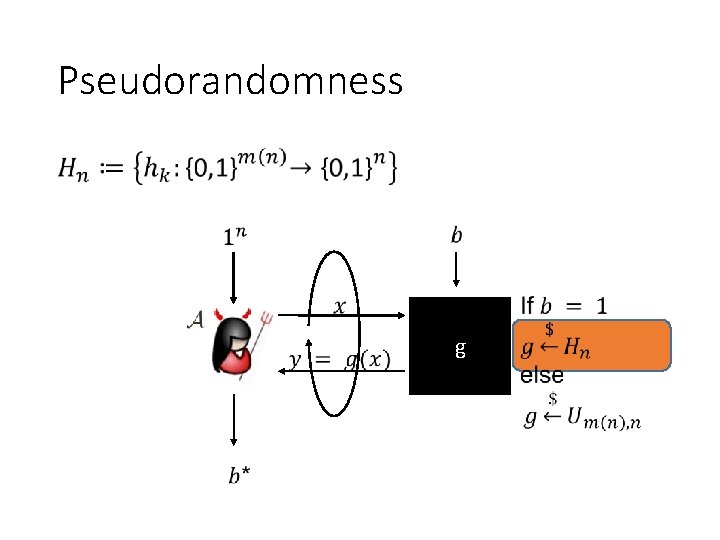
Pseudorandomness • g

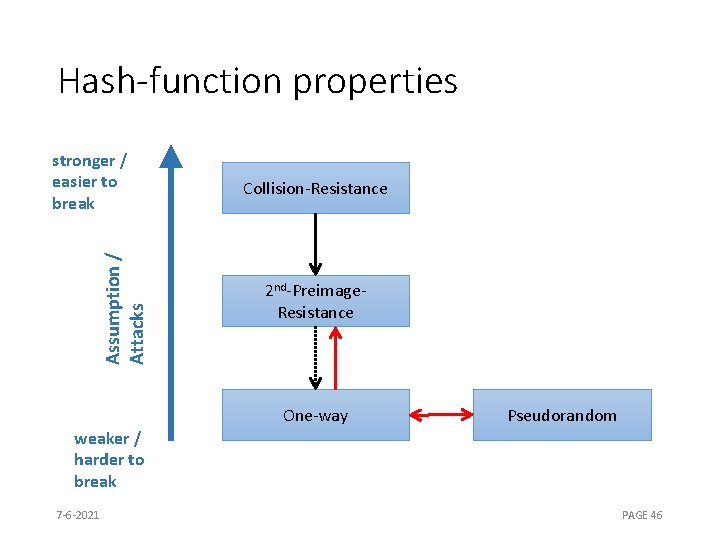
Hash-function properties Assumption / Attacks stronger / easier to break Collision-Resistance 2 nd-Preimage. Resistance One-way Pseudorandom weaker / harder to break 7 -6 -2021 PAGE 46

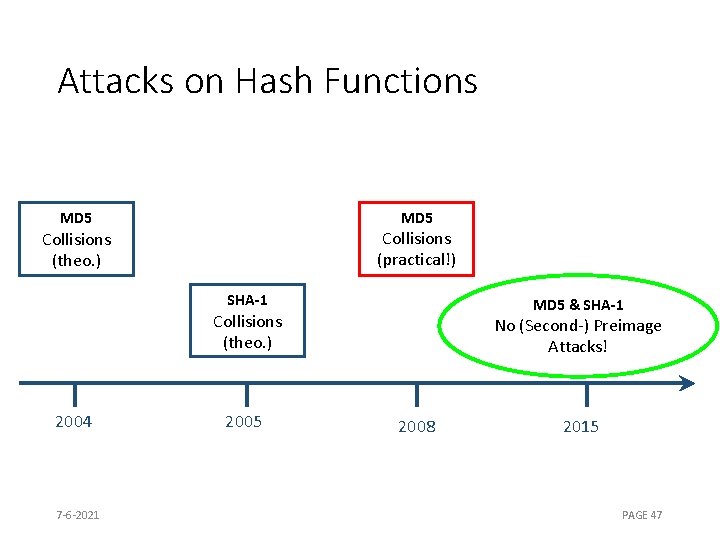
Attacks on Hash Functions MD 5 Collisions (practical!) Collisions (theo. ) SHA-1 MD 5 & SHA-1 Collisions (theo. ) 2004 7 -6 -2021 2005 No (Second-) Preimage Attacks! 2008 2015 PAGE 47

Basic Construction 7 -6 -2021 PAGE 48
![LamportDiffie OTS Lam 79 Message M b 1 bm OWF H SK Lamport-Diffie OTS [Lam 79] Message M = b 1, …, bm, OWF H SK](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-49.jpg)
Lamport-Diffie OTS [Lam 79] Message M = b 1, …, bm, OWF H SK sk 1, 0 sk 1, 1 H PK Sig 7 -6 -2021 skm, 0 H pk 1, 0 b 1 = n bit * H H pk 1, 1 Mux sk 1, b 1 skm, 1 H H pkm, 0 b 2 Mux bm pkm, 1 Mux skm, bm PAGE 49

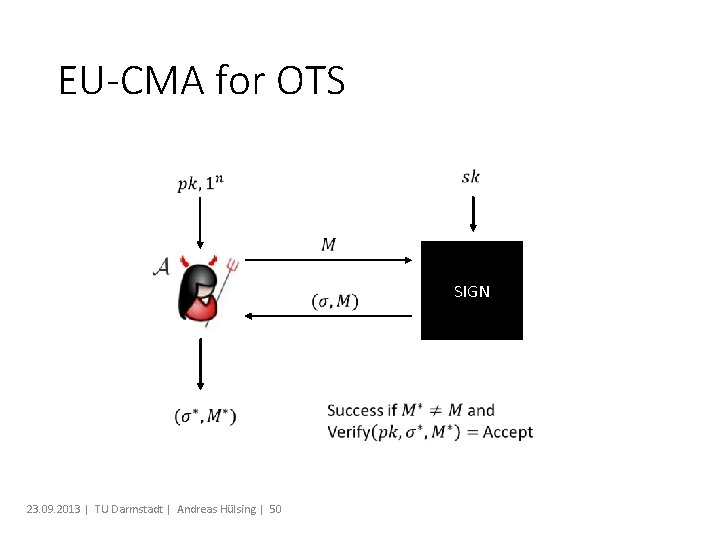
EU-CMA for OTS SIGN 23. 09. 2013 | TU Darmstadt | Andreas Hülsing | 50

Security Theorem: If H is one-way then LD-OTS is one-time eu-cmasecure.

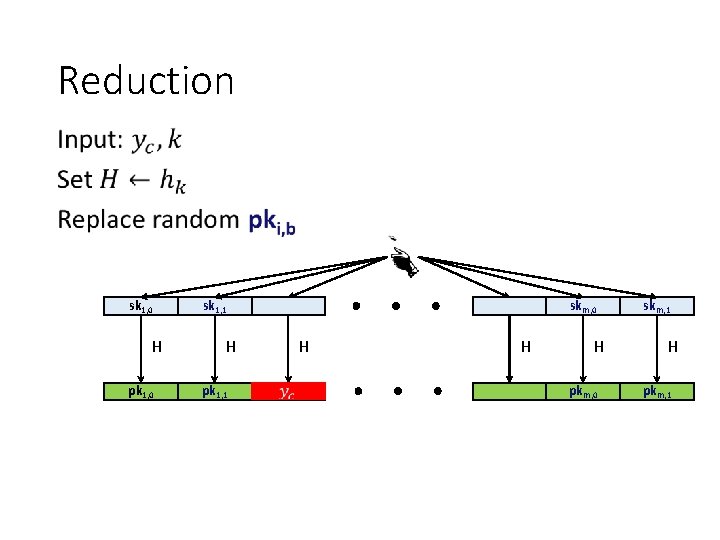
Reduction • sk 1, 0 H pk 1, 0 sk 1, 1 H pk 1, 1 skm, 0 H H H pkm, 0 skm, 1 H pkm, 1

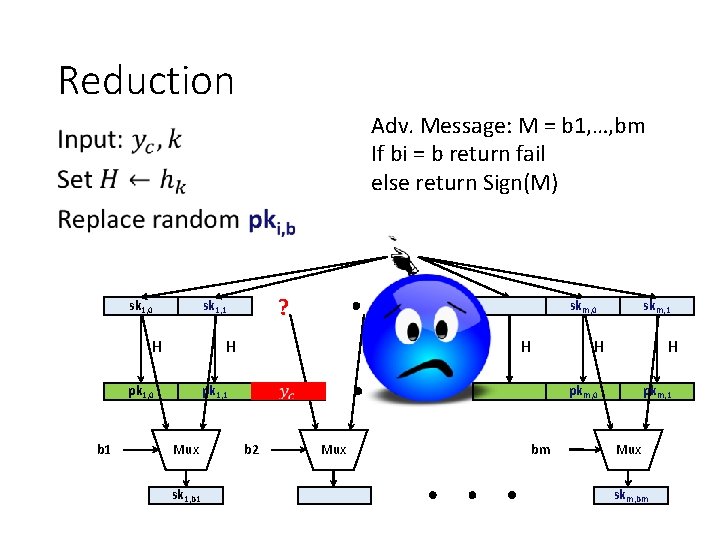
Reduction Adv. Message: M = b 1, …, bm If bi = b return fail else return Sign(M) • sk 1, 0 H skm, 0 H pk 1, 0 b 1 ? sk 1, 1 H H pk 1, 1 Mux sk 1, b 1 skm, 1 H pkm, 0 b 2 Mux bm pkm, 1 Mux skm, bm

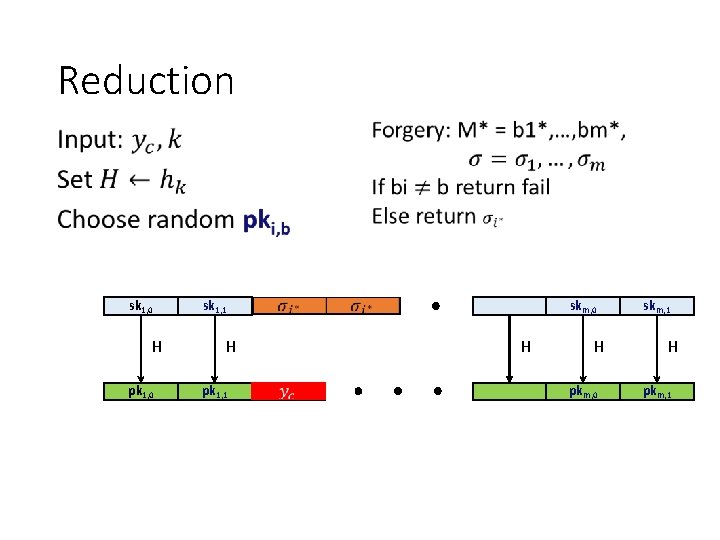
Reduction • sk 1, 0 H pk 1, 0 sk 1, 1 H pk 1, 1 ? skm, 0 H H pkm, 0 skm, 1 H pkm, 1

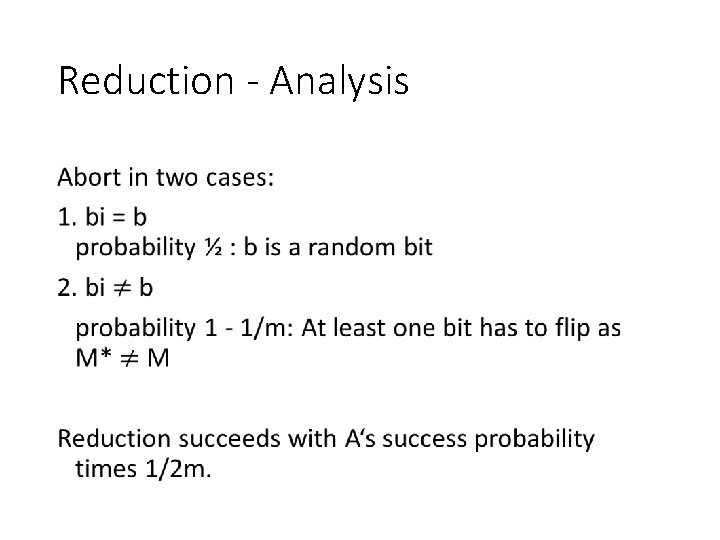
Reduction - Analysis •

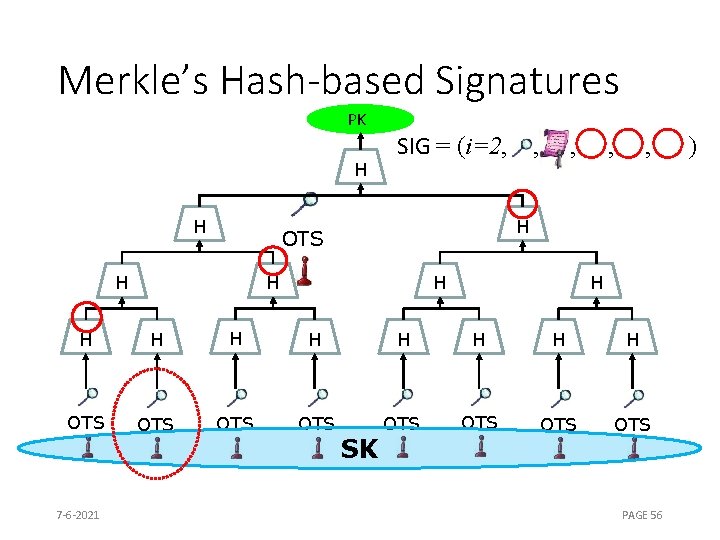
Merkle’s Hash-based Signatures PK H H SIG = (i=2, , H OTS H , H H H OTS OTS 7 -6 -2021 SK PAGE 56 )

Security Theorem: MSS is eu-cma-secure if OTS is a one-time eu-cma secure signature scheme and H is a random element from a family of collision resistant hash functions.

Reduction •

Reduction (Step 4, Extraction) •

Winternitz-OTS
![Recap LDOTS Lam 79 Message M b 1 bm OWF H SK Recap LD-OTS [Lam 79] Message M = b 1, …, bm, OWF H SK](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-61.jpg)
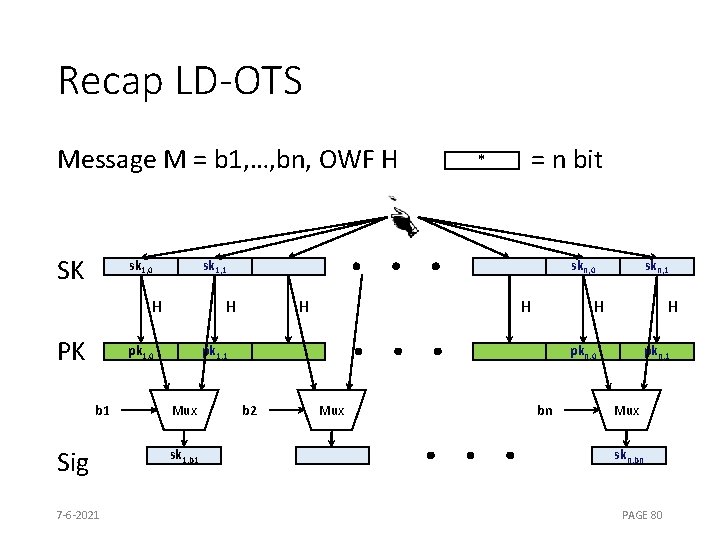
Recap LD-OTS [Lam 79] Message M = b 1, …, bm, OWF H SK sk 1, 0 Sig skm, 0 H pk 1, 0 b 1 = n bit sk 1, 1 H PK * H H H pk 1, 1 Mux sk 1, b 1 skm, 1 H pkm, 0 b 2 Mux bn pkm, 1 Mux skm, bm

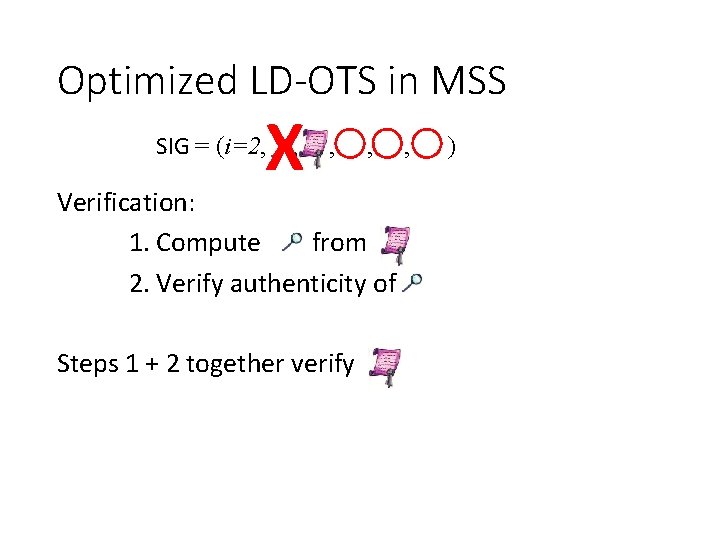
LD-OTS in MSS SIG = (i=2, , , ) Verification: 1. Verify 2. Verify authenticity of We can do better!

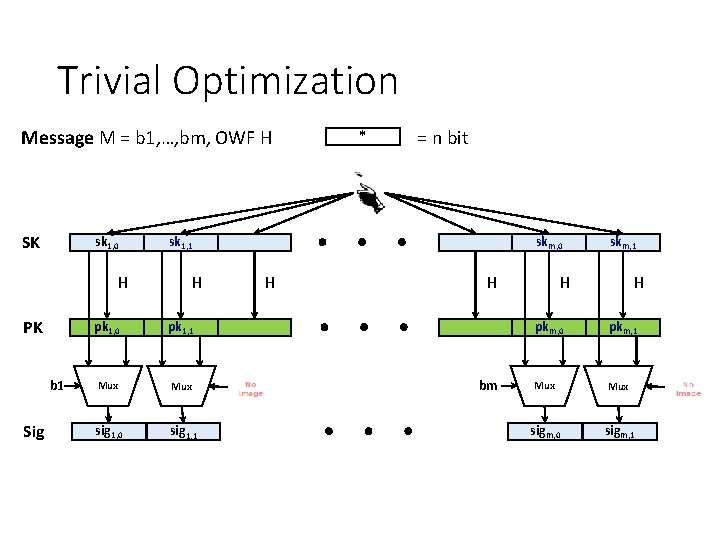
Trivial Optimization Message M = b 1, …, bm, OWF H SK sk 1, 0 H PK b 1 Sig * = n bit sk 1, 1 H pk 1, 0 pk 1, 1 Mux sig 1, 0 sig 1, 1 skm, 0 H H bm skm, 1 H H pkm, 0 pkm, 1 Mux sigm, 0 sigm, 1

Optimized LD-OTS in MSS X SIG = (i=2, , , , Verification: 1. Compute from 2. Verify authenticity of Steps 1 + 2 together verify , )

Germans love their „Ordnung“! Checksum with bad performance!

Optimized LD-OTS

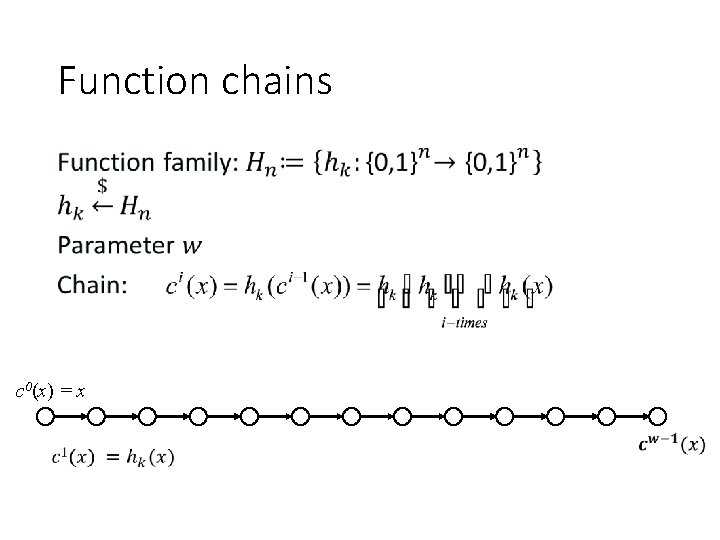
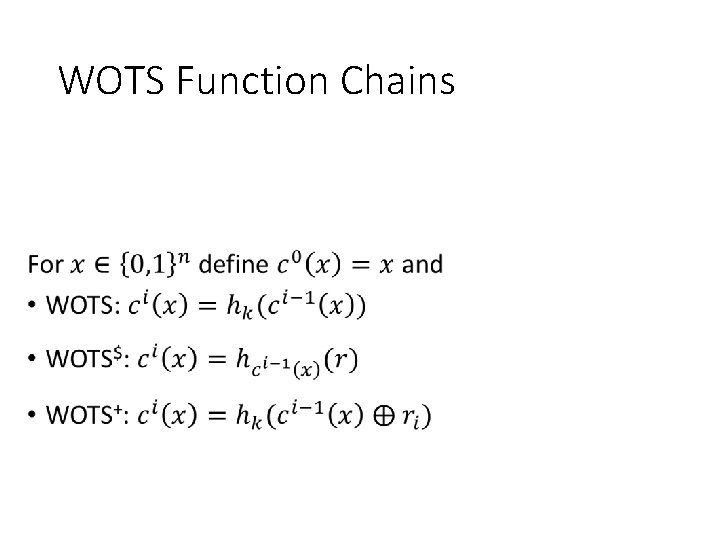
Function chains • c 0(x) = x

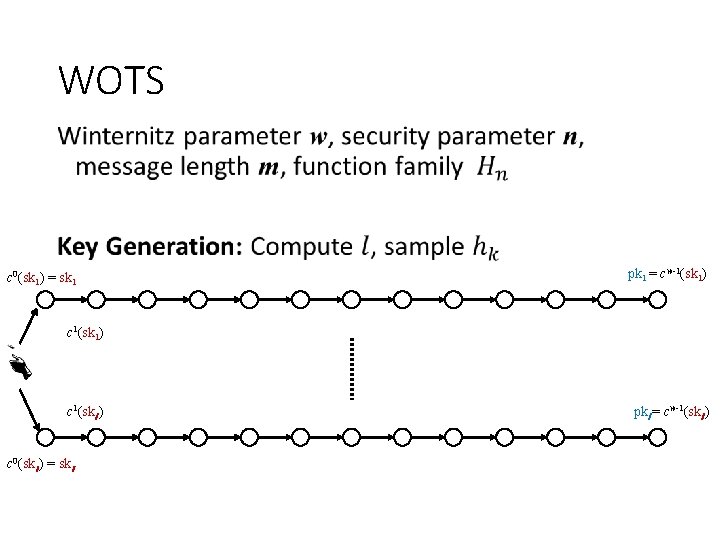
WOTS • c 0(sk 1) = sk 1 pk 1 = cw-1(sk 1) c 1(skl ) c 0(skl ) = skl pkl = cw-1(skl )

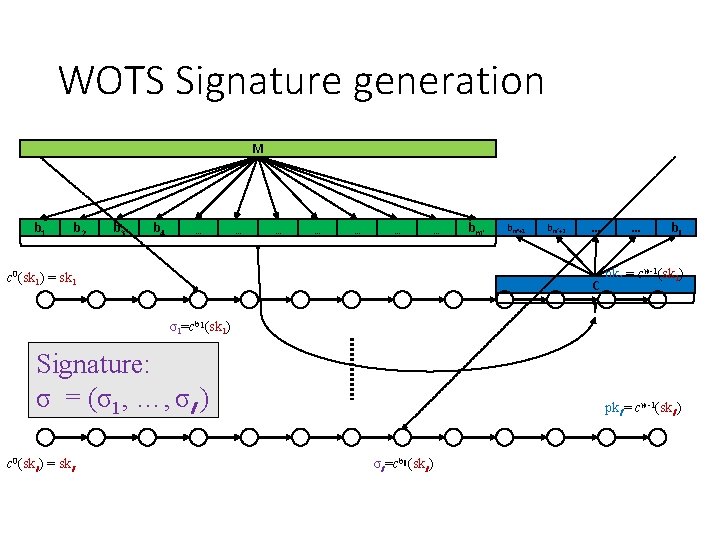
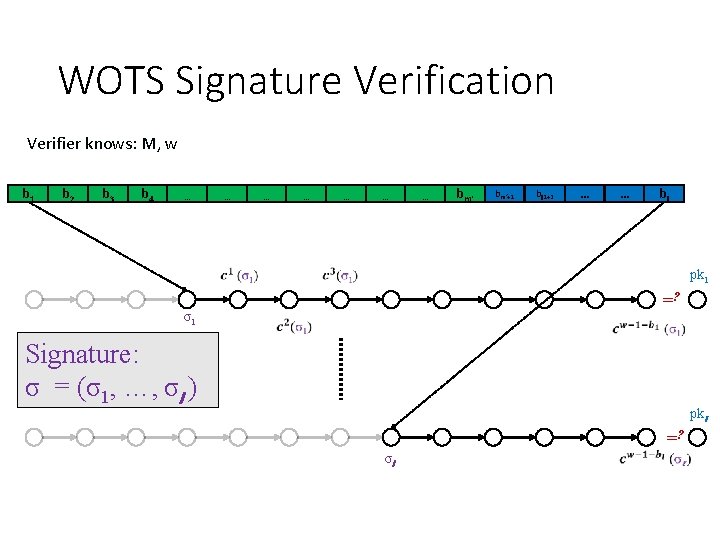
WOTS Signature generation M b 1 b 2 b 3 b 4 … … … … c 0(sk 1) = sk 1 bm‘+1 bm‘+2 … C … bl pk 1 = cw-1(sk 1) σ1=cb 1(sk 1) Signature: σ = (σ1, …, σl ) c 0(skl ) = skl pkl = cw-1(skl ) σl =cbl (skl )

WOTS Signature Verification Verifier knows: M, w b 1 b 2 b 3 b 4 … … … … bm‘+1 bl 1+2 … … bl pk 1 =? σ1 Signature: σ = (σ1, …, σl ) pkl =? σl

WOTS Function Chains •

WOTS Security •

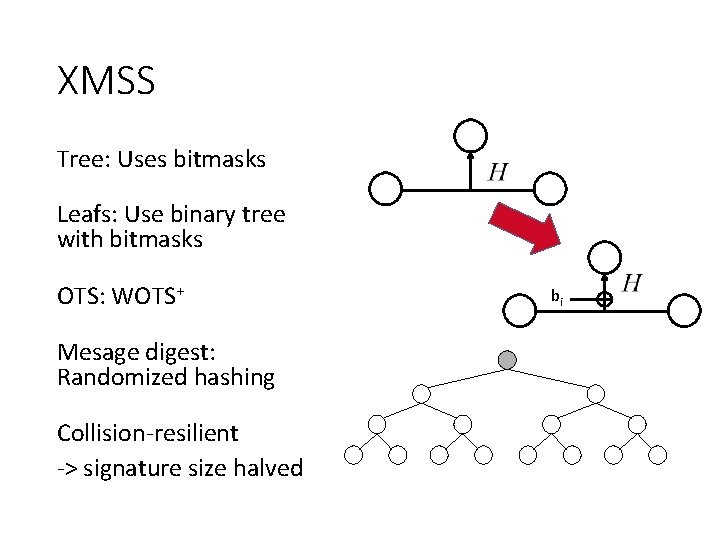
XMSS

XMSS Tree: Uses bitmasks Leafs: Use binary tree with bitmasks OTS: WOTS+ Mesage digest: Randomized hashing Collision-resilient -> signature size halved bi

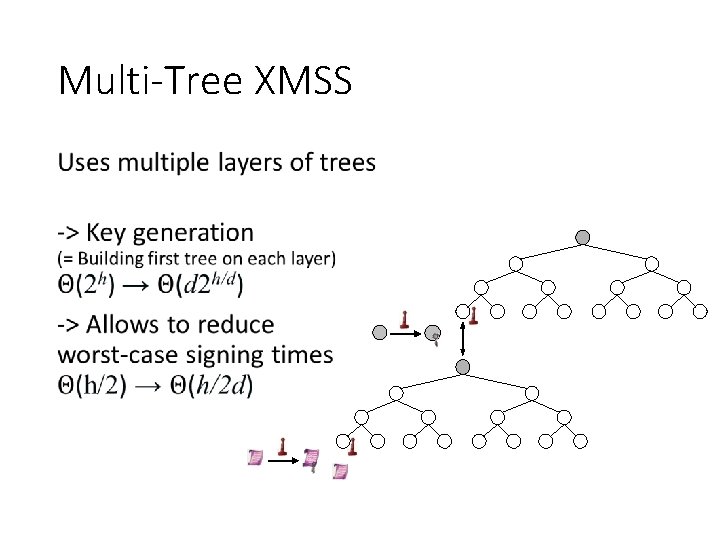
Multi-Tree XMSS •

How to Eliminate the State

Protest? PAGE 78 7 -6 -2021

Few-Time Signature Schemes 7 -6 -2021 PAGE 79

Recap LD-OTS Message M = b 1, …, bn, OWF H SK sk 1, 0 sk 1, 1 H PK Sig 7 -6 -2021 skn, 0 H pk 1, 0 b 1 = n bit * H H H pk 1, 1 Mux sk 1, b 1 skn, 1 H pkn, 0 b 2 Mux bn pkn, 1 Mux skn, bn PAGE 80
![HORS RR 02 Message M OWF H CRHF H n bit Parameters HORS [RR 02] * Message M, OWF H, CRHF H’ = n bit Parameters](https://slidetodoc.com/presentation_image_h2/5f4df18f8375ca3f5786b335c7f4c2ea/image-80.jpg)
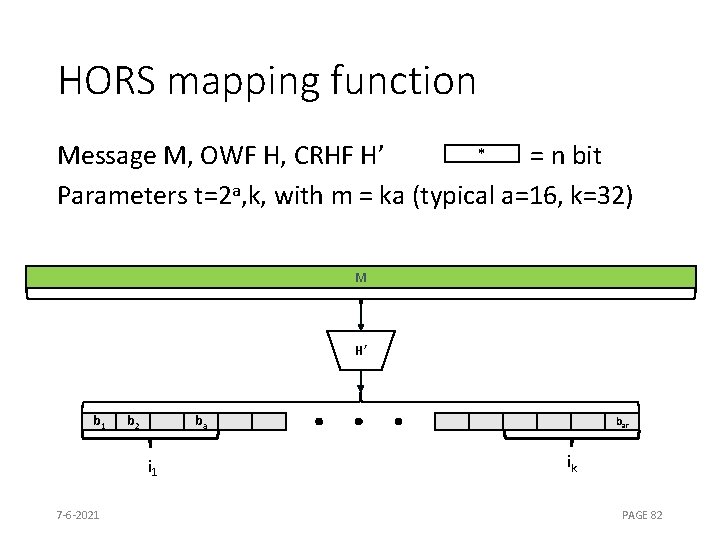
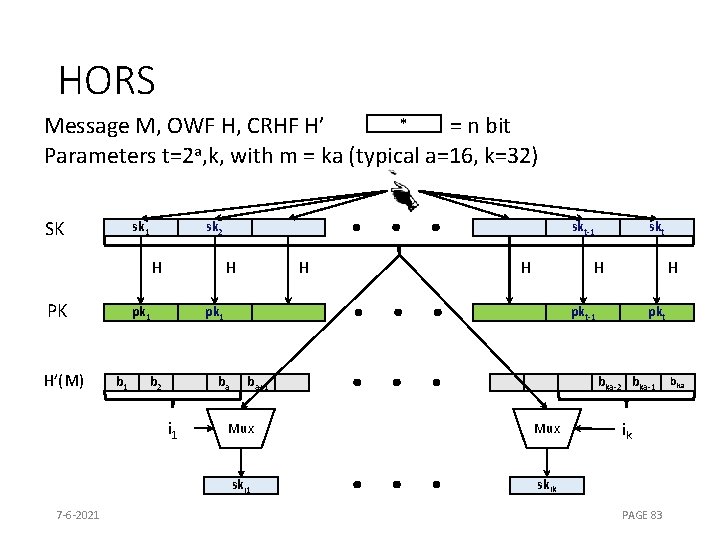
HORS [RR 02] * Message M, OWF H, CRHF H’ = n bit Parameters t=2 a, k, with m = ka (typical a=16, k=32) SK sk 1 sk 2 H PK 7 -6 -2021 pk 1 skt-1 H pk 1 H H skt H pkt-1 H pkt PAGE 81

HORS mapping function * Message M, OWF H, CRHF H’ = n bit Parameters t=2 a, k, with m = ka (typical a=16, k=32) M H’ b 1 b 2 ba i 1 7 -6 -2021 bar ik PAGE 82

HORS * Message M, OWF H, CRHF H’ = n bit Parameters t=2 a, k, with m = ka (typical a=16, k=32) SK sk 1 sk 2 H PK H’(M) H pk 1 b 1 H H b 2 skt H pk 1 H pkt-1 ba i 1 7 -6 -2021 skt-1 ba+1 pkt bka-2 bka-1 Mux ski 1 skik ik PAGE 83 bka

HORS Security • 7 -6 -2021 PAGE 84

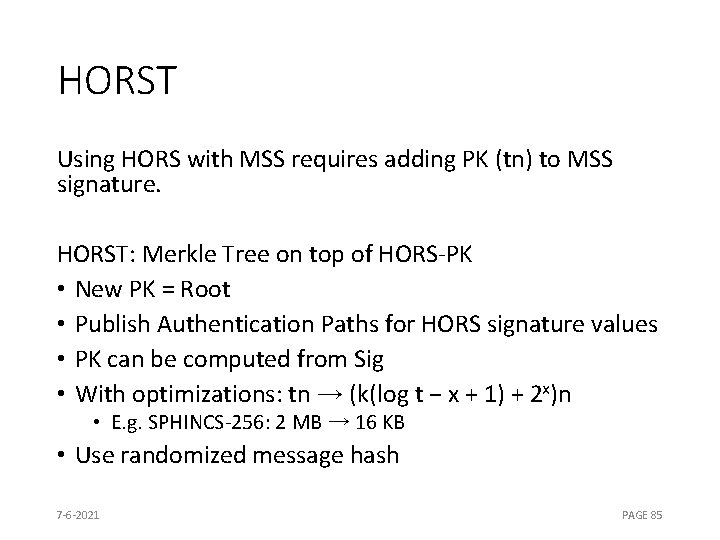
HORST Using HORS with MSS requires adding PK (tn) to MSS signature. HORST: Merkle Tree on top of HORS-PK • New PK = Root • Publish Authentication Paths for HORS signature values • PK can be computed from Sig • With optimizations: tn → (k(log t − x + 1) + 2 x)n • E. g. SPHINCS-256: 2 MB → 16 KB • Use randomized message hash 7 -6 -2021 PAGE 85

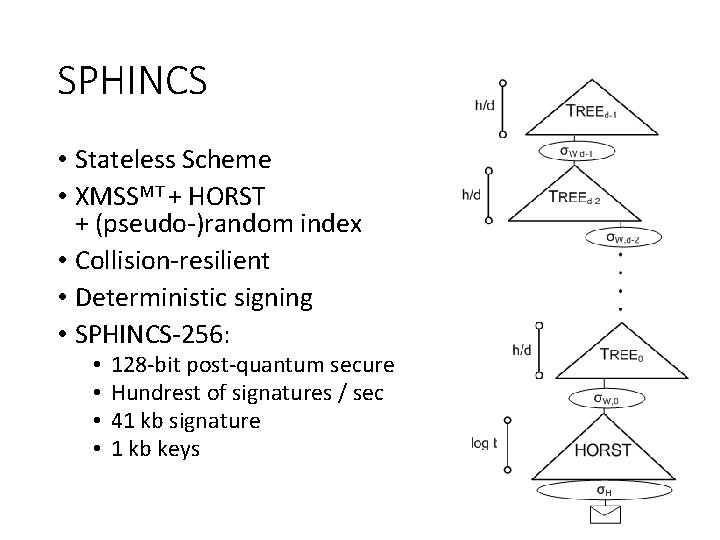
SPHINCS • Stateless Scheme • XMSSMT + HORST + (pseudo-)random index • Collision-resilient • Deterministic signing • SPHINCS-256: • • 128 -bit post-quantum secure Hundrest of signatures / sec 41 kb signature 1 kb keys

PQ-Crypto is currently a hot topic

Thank you! Questions? For references & further literature see https: //huelsing. wordpress. com/hash-based-signature-schemes/literature/ 7 -6 -2021 PAGE 88