PostQuantum Cryptography Andreas Hlsing TU Eindhoven Quantum kills










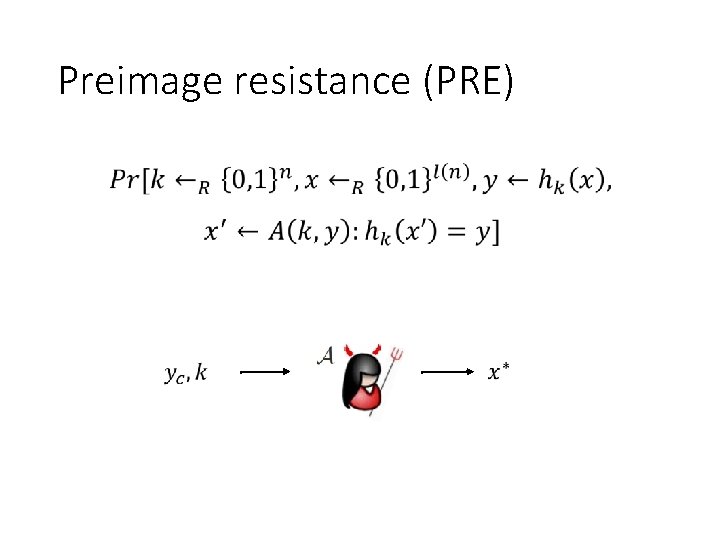
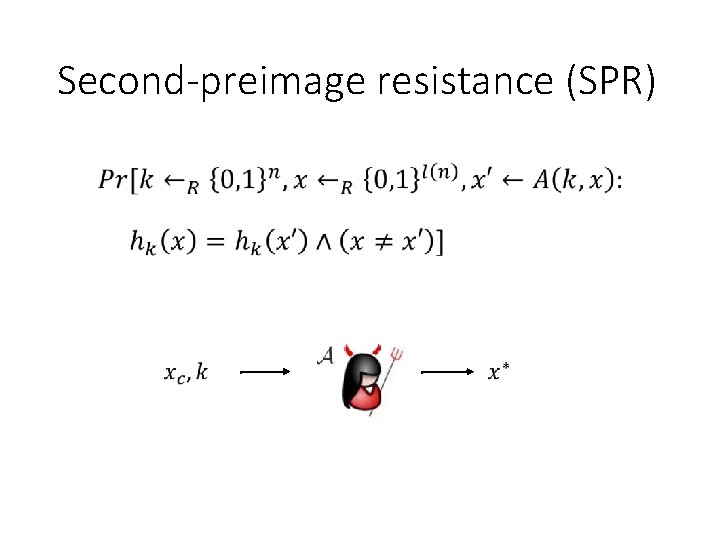








- Slides: 48

Post-Quantum Cryptography Andreas Hülsing TU Eindhoven

Quantum kills the Internet 10/21/2021 Andreas Hülsing https: //huelsing. net 2

Background: Cryptography 10/21/2021 Andreas Hülsing https: //huelsing. net 3

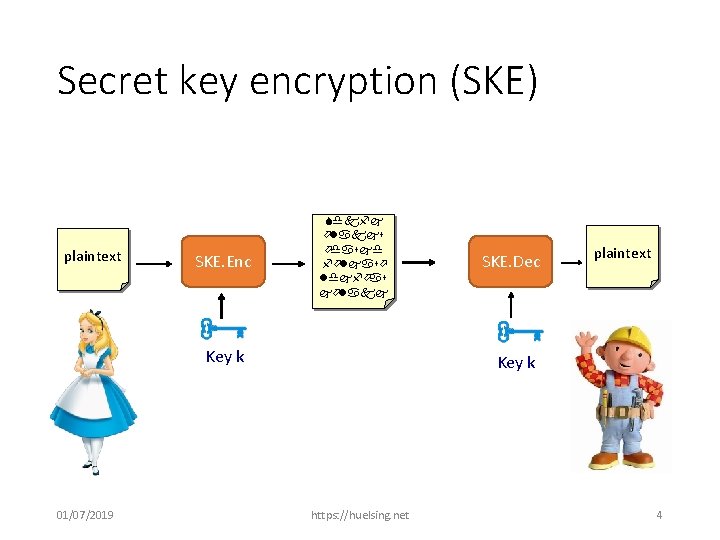
Secret key encryption (SKE) plaintext SKE. Enc Sdkfj ölakjs ödasjd följasö ldjföas jölakj Key k 01/07/2019 SKE. Dec plaintext Key k https: //huelsing. net 4

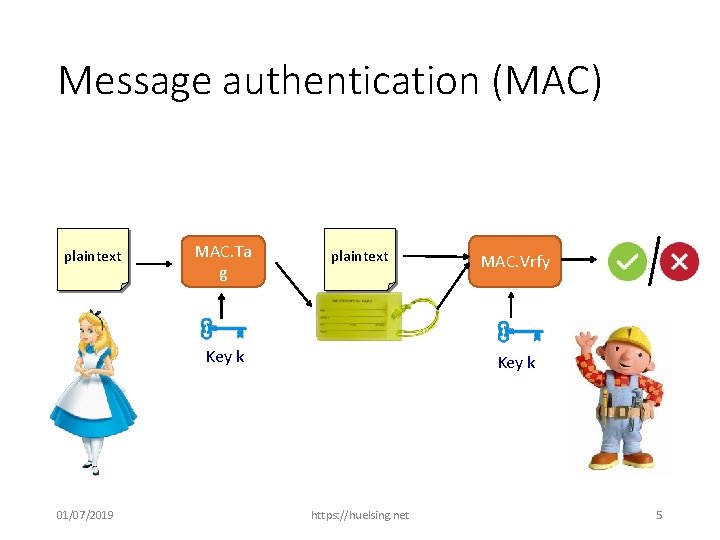
Message authentication (MAC) plaintext MAC. Ta g plaintext Key k 01/07/2019 MAC. Vrfy Key k https: //huelsing. net 5

How to build secret key crypto? • Spoiler: Killed by quantum? Not that we know. (but weakened)* Engineering* * Disclaimer: Massive simplification 10/21/2021 Andreas Hülsing https: //huelsing. net 6

How does Bob learn shared key k? 10/21/2021 Andreas Hülsing https: //huelsing. net 7

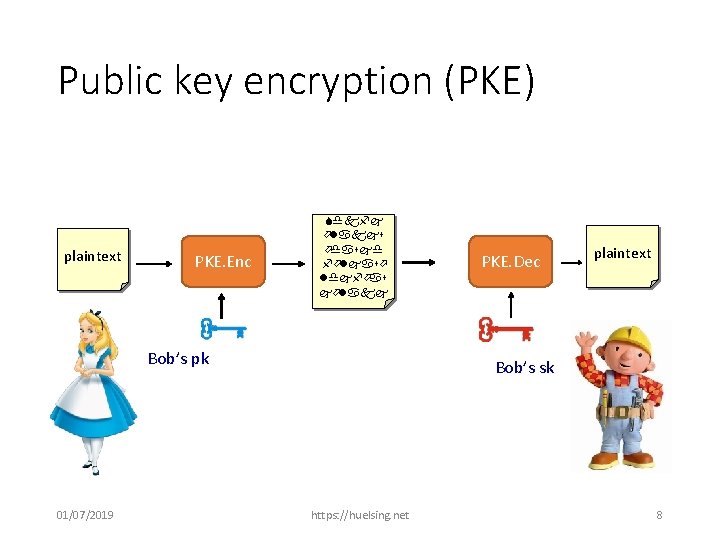
Public key encryption (PKE) plaintext PKE. Enc Sdkfj ölakjs ödasjd följasö ldjföas jölakj Bob’s pk 01/07/2019 PKE. Dec plaintext Bob’s sk https: //huelsing. net 8

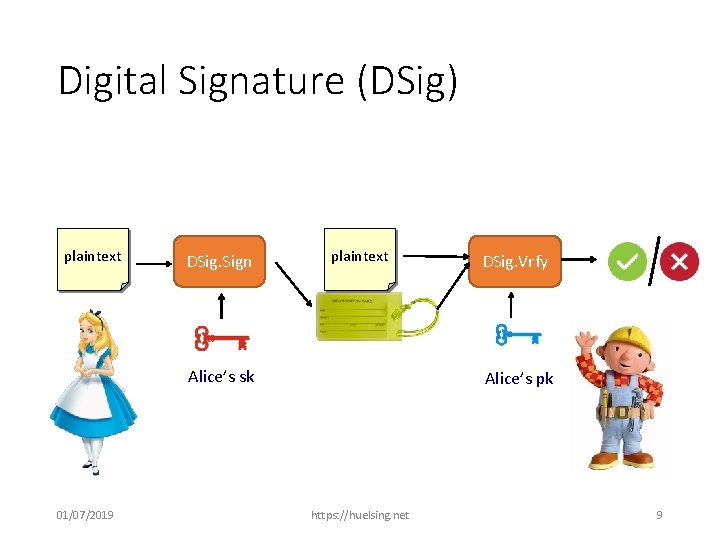
Digital Signature (DSig) plaintext DSig. Sign plaintext Alice’s sk 01/07/2019 DSig. Vrfy Alice’s pk https: //huelsing. net 9

Applications • Code signing (DSIG) • Software updates • Software distribution • Mobile code • Communication security (DSIG, PKE / KEX /KEM) • TLS, SSH, IPSec, . . . • e. Commerce, online banking, e. Government, . . . • Private online communication 10/21/2021 Andreas Hülsing https: //huelsing. net 11

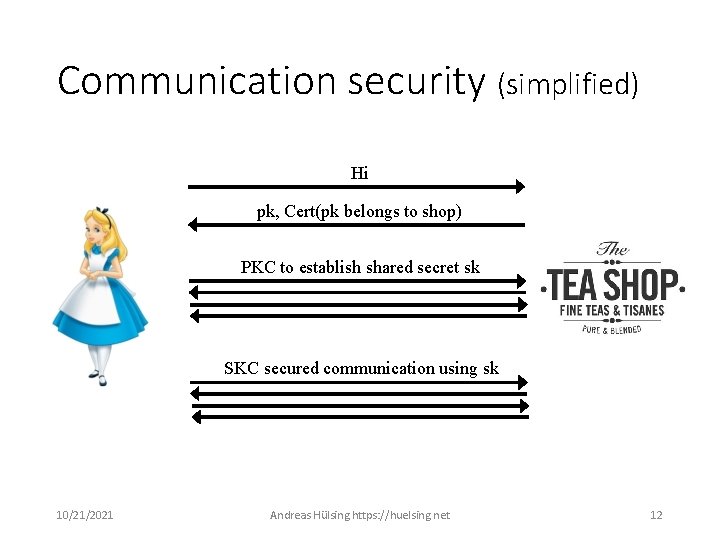
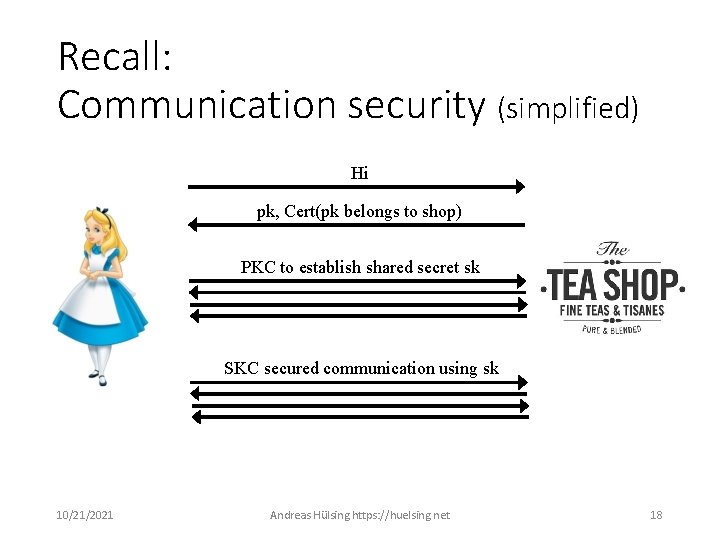
Communication security (simplified) Hi pk, Cert(pk belongs to shop) PKC to establish shared secret sk SKC secured communication using sk 10/21/2021 Andreas Hülsing https: //huelsing. net 12

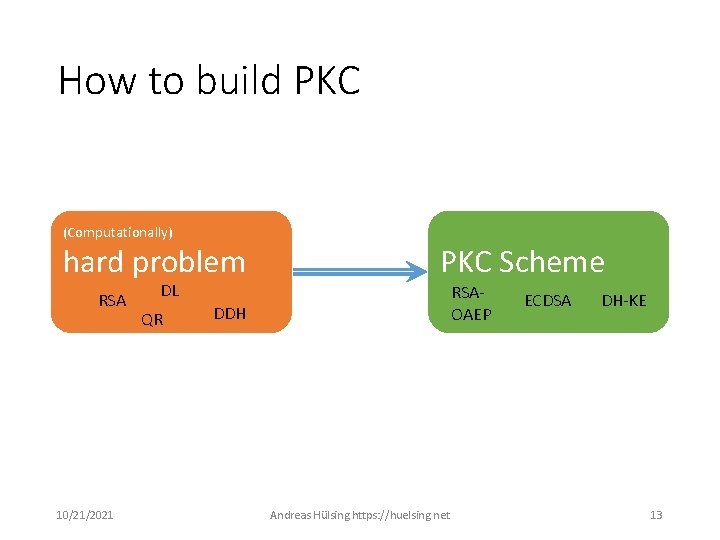
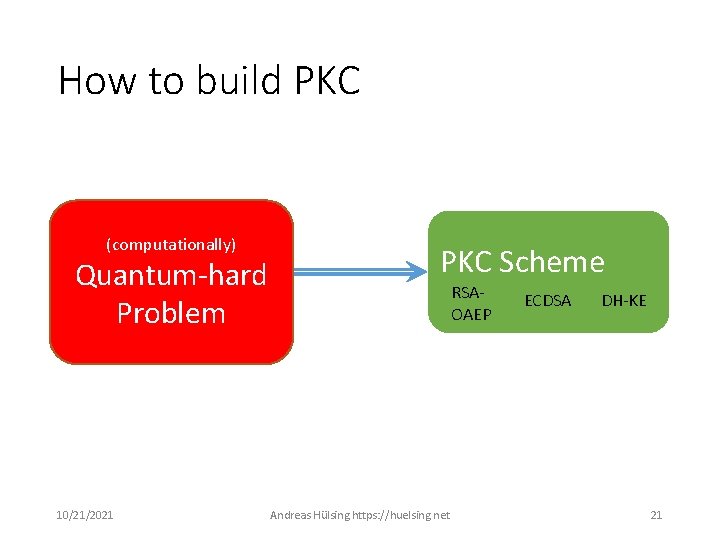
How to build PKC (Computationally) hard problem RSA 10/21/2021 DL QR PKC Scheme RSAOAEP DDH Andreas Hülsing https: //huelsing. net ECDSA DH-KE 13

The Quantum Threat

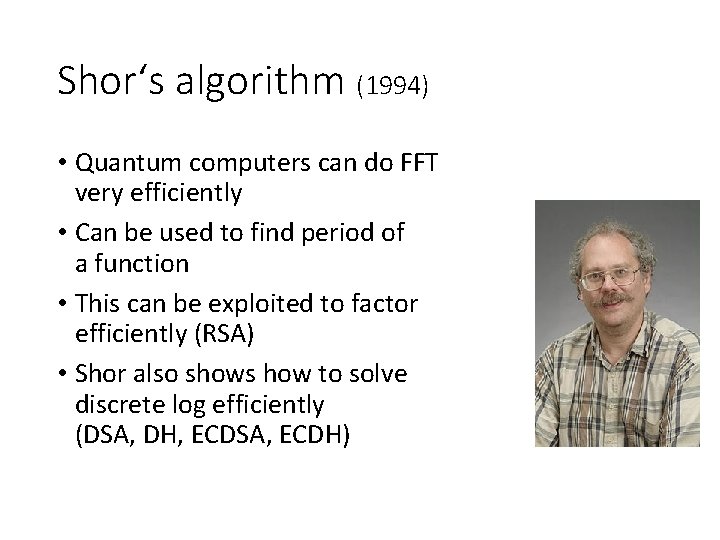
Shor‘s algorithm (1994) • Quantum computers can do FFT very efficiently • Can be used to find period of a function • This can be exploited to factor efficiently (RSA) • Shor also shows how to solve discrete log efficiently (DSA, DH, ECDSA, ECDH)

Grover‘s algorithm (1996) •

What is the problem that QKD solves? 10/21/2021 Andreas Hülsing https: //huelsing. net 17

Recall: Communication security (simplified) Hi pk, Cert(pk belongs to shop) PKC to establish shared secret sk SKC secured communication using sk 10/21/2021 Andreas Hülsing https: //huelsing. net 18

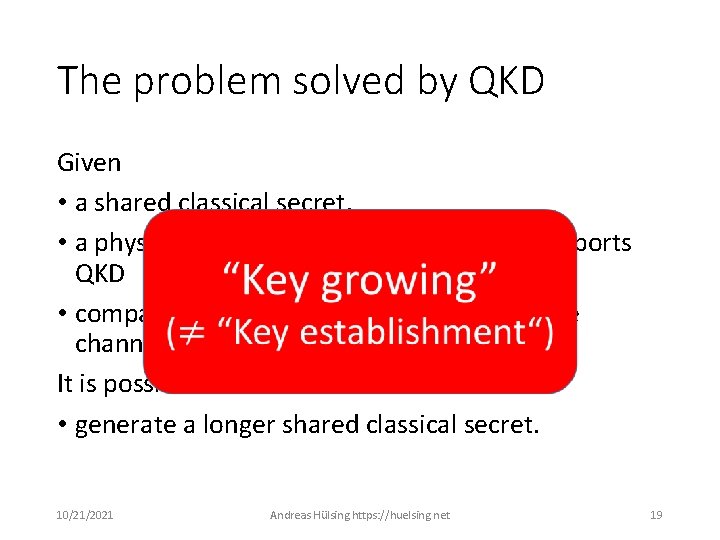
The problem solved by QKD Given • a shared classical secret, • a physical channel between parties that supports QKD • compatible QKD devices on both ends of the channel It is possible to • generate a longer shared classical secret. 10/21/2021 Andreas Hülsing https: //huelsing. net 19

Solution to the problem caused by Shor? Post-quantum cryptography 10/21/2021 Andreas Hülsing https: //huelsing. net 20

How to build PKC (Computationally) (computationally) hard problem Quantum-hard DL RSA DDH Problem QR 10/21/2021 PKC Scheme RSAOAEP Andreas Hülsing https: //huelsing. net ECDSA DH-KE 21

Early post-quantum crypto „Cryptography based on problems that are conjectured to be hard even for quantum computers. “ Lattice-based: SVP / CVP Hash-based: CR / SPR /. . . Code-based: SD Multivariate: MQ 10/21/2021 Andreas Hülsing https: //huelsing. net 22

Conjectured quantum-hard problems • Solving multivariate quadratic equations (MQ-problem) -> Multivariate Crypto • Syndrom decoding problem (SD) -> Code-based crypto • Short(est) and close(st) vector problem (SVP, CVP) -> Lattice-based crypto • Breaking security of symmetric primitives (SHAx-, AES-, Keccak-, . . . problem) -> Hash-based signatures / symmetric crypto • (Finding isogenies between supersingular elliptic curves -> SIDH / CSIDH) 10/21/2021 Andreas Hülsing https: //huelsing. net 23

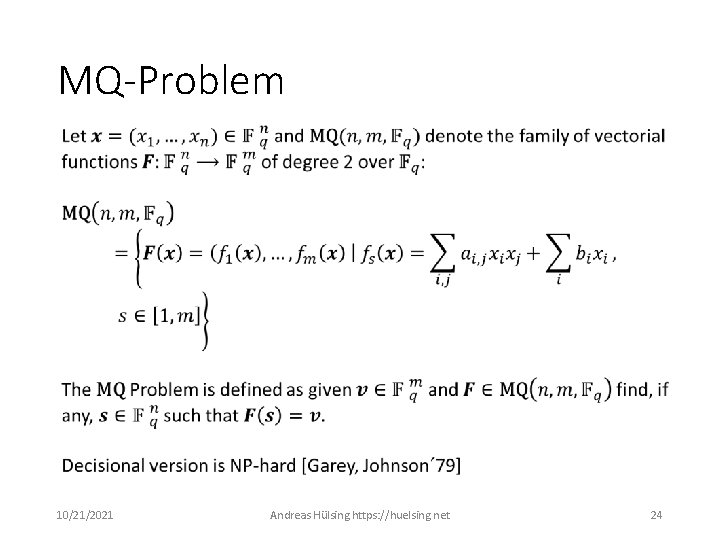
MQ-Problem 10/21/2021 Andreas Hülsing https: //huelsing. net 24

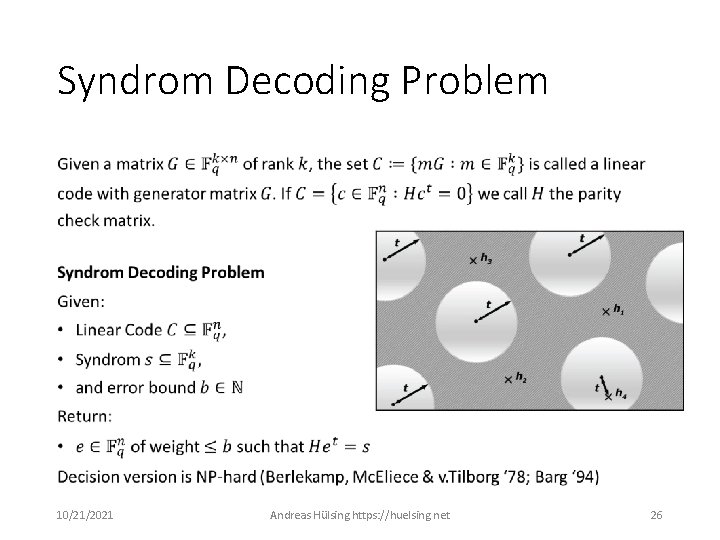
Syndrom Decoding Problem • 10/21/2021 Andreas Hülsing https: //huelsing. net 26

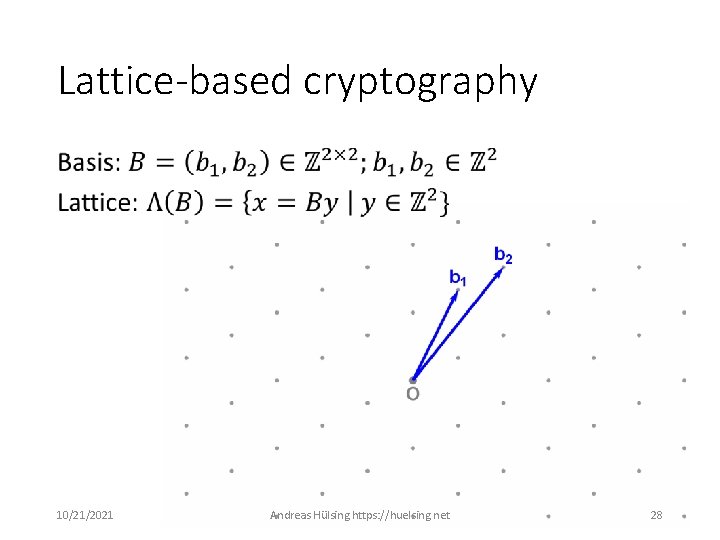
Lattice-based cryptography • 10/21/2021 Andreas Hülsing https: //huelsing. net 28

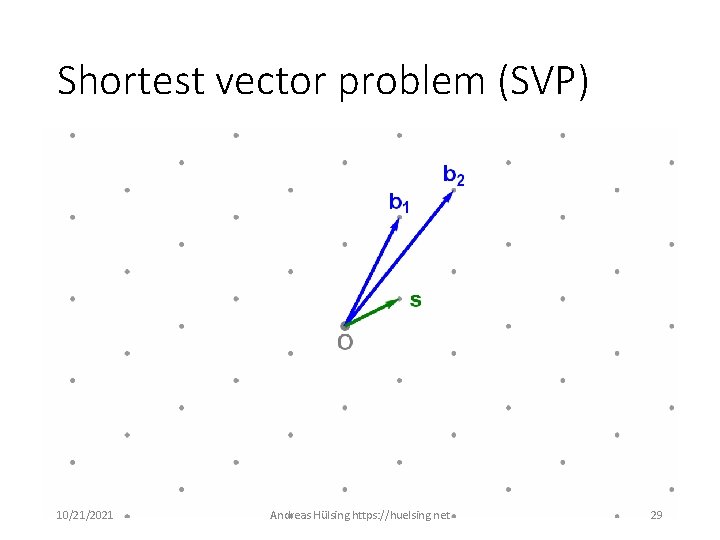
Shortest vector problem (SVP) 10/21/2021 Andreas Hülsing https: //huelsing. net 29

(Worst-case) Lattice Problems • 10/21/2021 Andreas Hülsing https: //huelsing. net 30

MQ, lattice & codes • Average-case versions of NP-hard problems • Best known quantum attacks: ”Quantizations” of classical attacks • Need “structured versions” for efficiency • More structure -> often easier break • Still only quantum attacks on “overstretched parameters“ • Theoretically, signatures & PKE/KEM possible 10/21/2021 Andreas Hülsing https: //huelsing. net 32

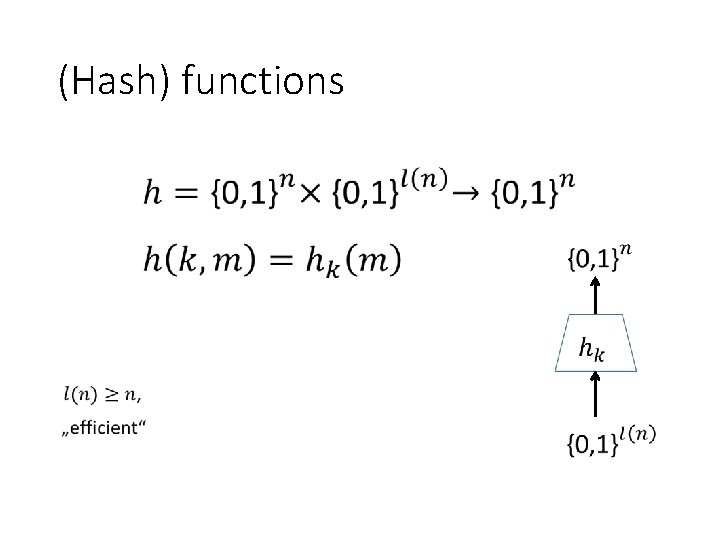
(Hash) functions •
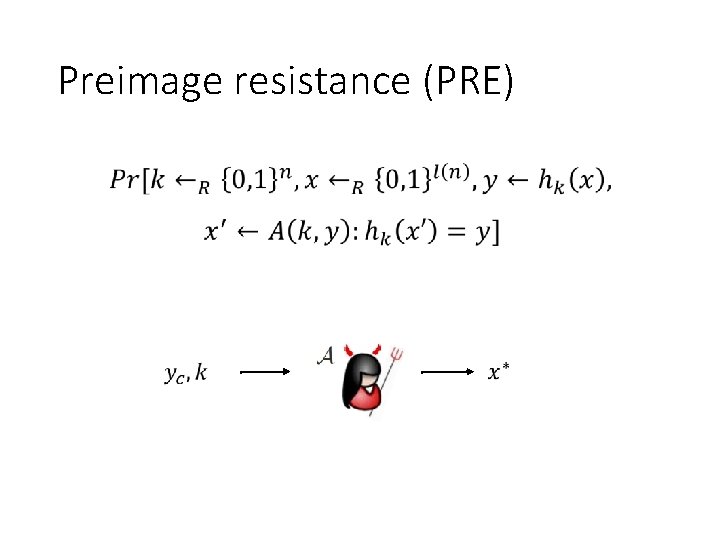
Preimage resistance (PRE) •

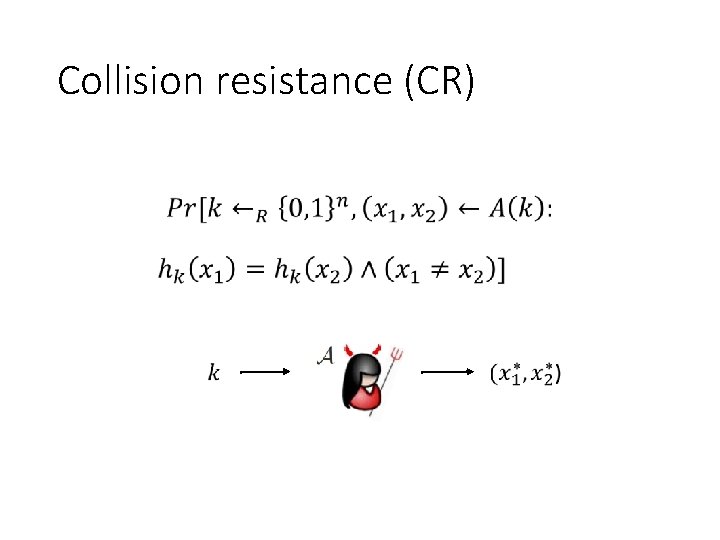
Collision resistance (CR)
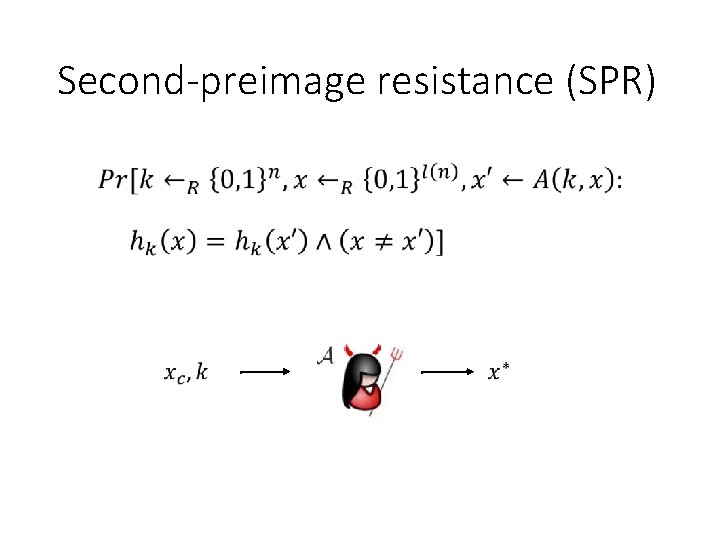
Second-preimage resistance (SPR) •

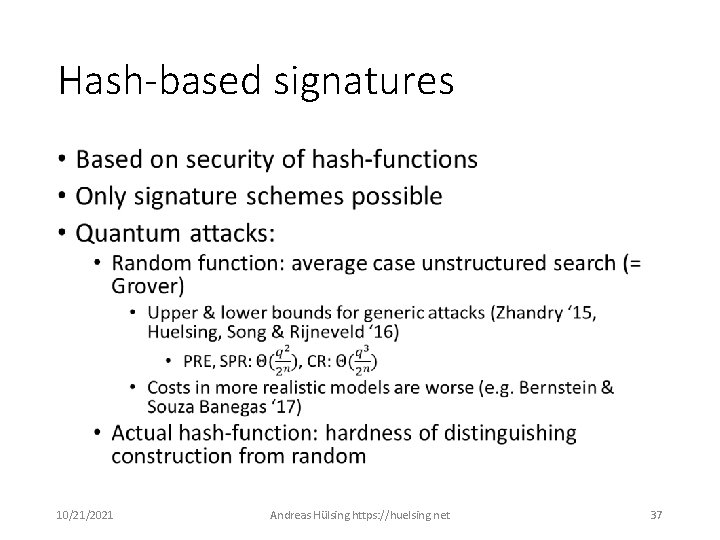
Hash-based signatures • 10/21/2021 Andreas Hülsing https: //huelsing. net 37

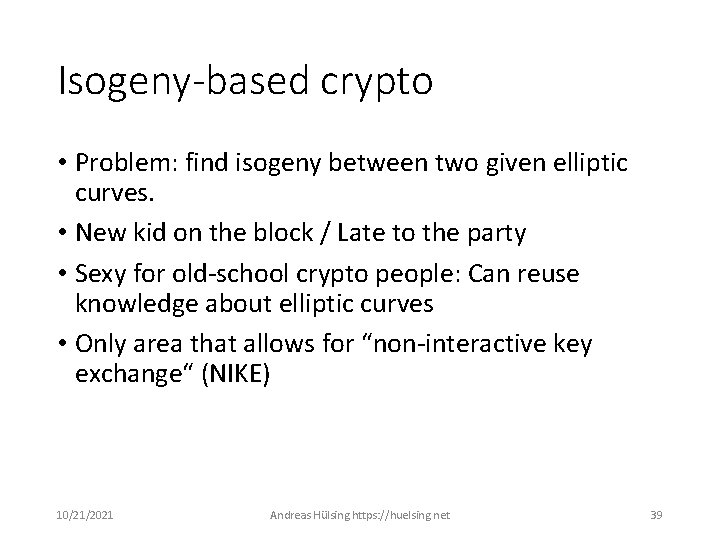
Isogeny-based crypto • Problem: find isogeny between two given elliptic curves. • New kid on the block / Late to the party • Sexy for old-school crypto people: Can reuse knowledge about elliptic curves • Only area that allows for “non-interactive key exchange“ (NIKE) 10/21/2021 Andreas Hülsing https: //huelsing. net 39

10/21/2021 Andreas Hülsing https: //huelsing. net 40

CSIDH (Castryck, Lange, Martindale, Renes, Panny) • Classical world: Diffie-Hellman key exchange operation very special • Only real post-quantum replacement for DH • Subexponential time quantum attacks (Kuperberg‘s algorithm) • Not my speciality -> ask the experts in the room 10/21/2021 Andreas Hülsing https: //huelsing. net 41

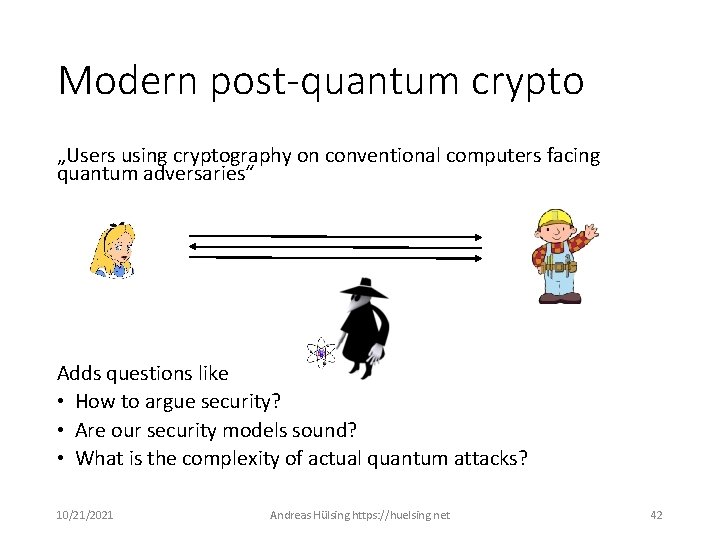
Modern post-quantum crypto „Users using cryptography on conventional computers facing quantum adversaries“ Adds questions like • How to argue security? • Are our security models sound? • What is the complexity of actual quantum attacks? 10/21/2021 Andreas Hülsing https: //huelsing. net 42

QS 0: Classical security 01/07/2019 https: //huelsing. net 43

QS 1: Post-quantum security 01/07/2019 https: //huelsing. net 44

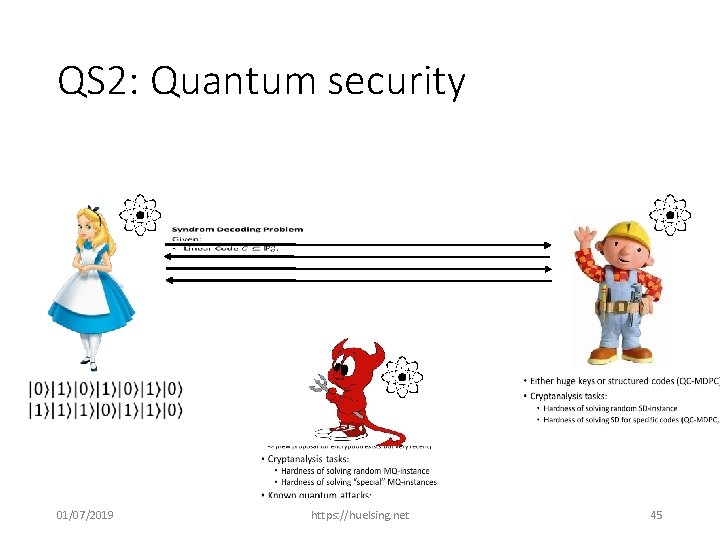
QS 2: Quantum security 01/07/2019 https: //huelsing. net 45

For practical applications we care about QS 1 01/07/2019 https: //huelsing. net 46

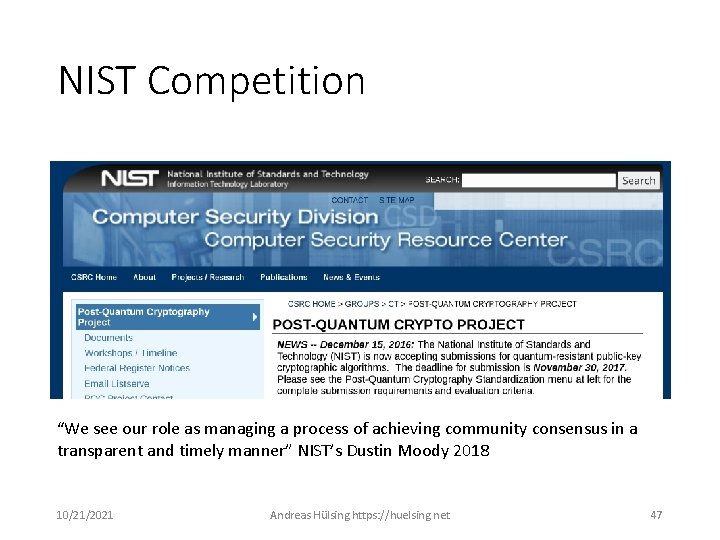
NIST Competition “We see our role as managing a process of achieving community consensus in a transparent and timely manner” NIST’s Dustin Moody 2018 10/21/2021 Andreas Hülsing https: //huelsing. net 47

Status of the competition • Nov 2017: 82 submissions collected • Dec 2017: 69 “complete & proper” proposals published • -> Starts round 1 (of 2 or 3 rounds) • 6 proposals with involvement from Eindhoven • Jan 2019: 26 proposals selected for 2 nd round. • 17 KEM, 9 Signature • TU/e: 4 KEM, 2 Signature in 2 nd round! • 2022 – 2024 Draft standards exist 10/21/2021 Andreas Hülsing https: //huelsing. net 48

Implementation security 10/21/2021 Andreas Hülsing https: //huelsing. net 49

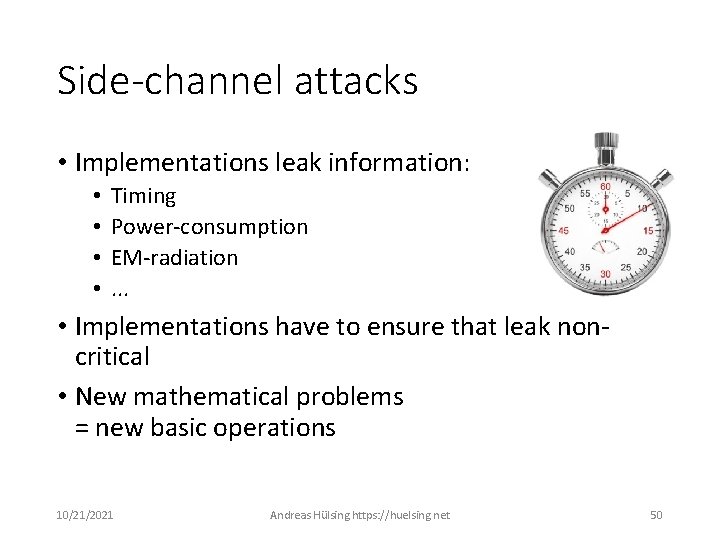
Side-channel attacks • Implementations leak information: • • Timing Power-consumption EM-radiation. . . • Implementations have to ensure that leak noncritical • New mathematical problems = new basic operations 10/21/2021 Andreas Hülsing https: //huelsing. net 50

Gaussian sampling 10/21/2021 Andreas Hülsing https: //huelsing. net 51

Resources • PQ Summer School: http: //www. pqcschool. org/ • NIST PQC Standardization Project: https: //csrc. nist. gov/Projects/Post-Quantum. Cryptography 10/21/2021 Andreas Hülsing https: //huelsing. net 52

Thank you! Questions? 10/21/2021 Andreas Hülsing https: //huelsing. net 53