UDP Improving UDP Hole Punching Technique For Io

















- Slides: 39

改良UDP洞穿技術設計物聯網通訊: 以遠端門鈴監控系統為例 Improving UDP Hole Punching Technique For Io. T Communications: A Remote Door-bell Monitoring System 楊凱勝 指導教授:柯開維 博士 2017/7/14

Outline ü ü Background ü Experiment n Network Address Translation (NAT) n Experiment Steps n NAT Traversal n Result and Analysis n UDP Hole Punching Technique n Visual Bell Application Proposed Method ü Conclusion n Register Phase n Conclusion n Port Prediction Phase n Future works n Punching Phase n Peer-to-peer Phase n Retry Procedures 1

Background n Network Address Translation (NAT) n NAT Traversal n UDP Hole Punching 2

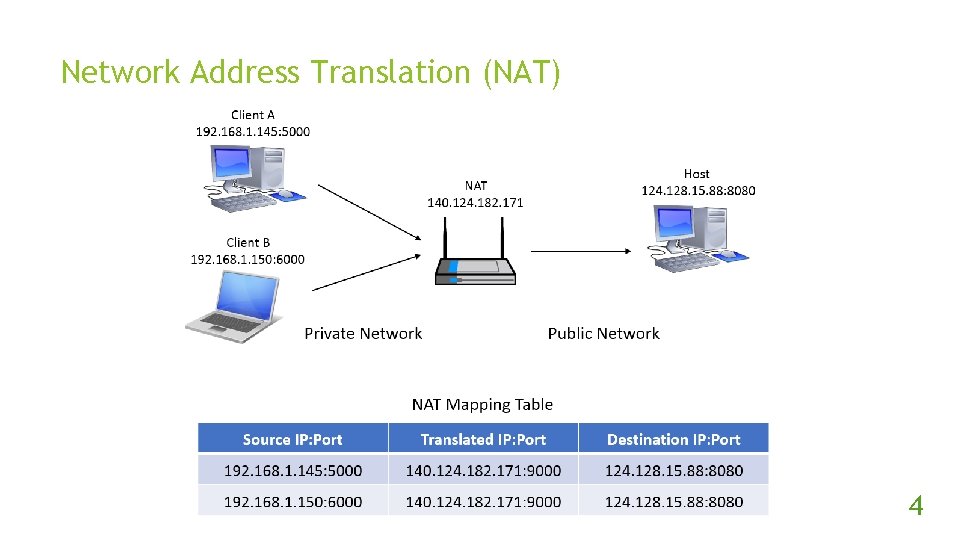
Network Address Translation (NAT) The IPv 4 address is not enough and IPv 6 is still not widespread. Let many hosts share a global IPv 4 address. 3

Network Address Translation (NAT) 4

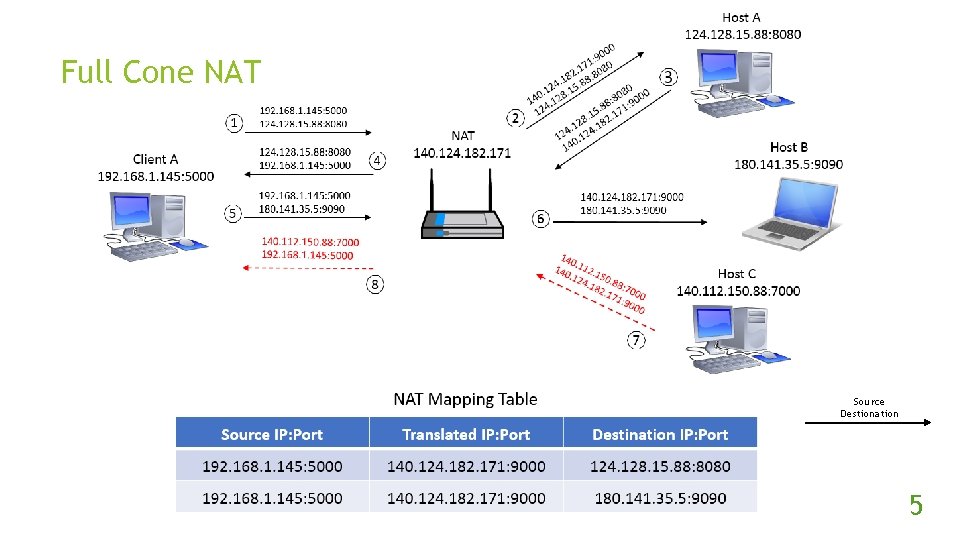
Full Cone NAT Source Destionation 5

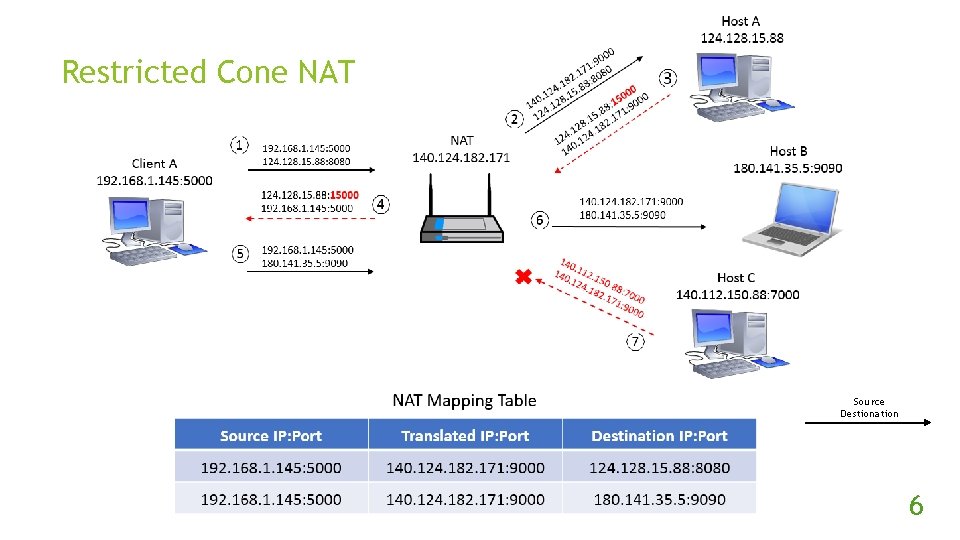
Restricted Cone NAT Source Destionation 6

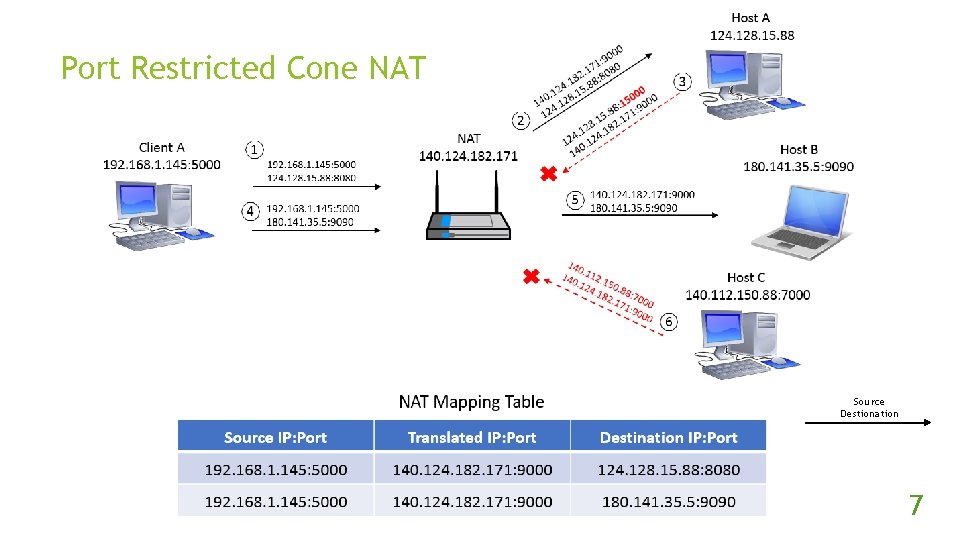
Port Restricted Cone NAT Source Destionation 7

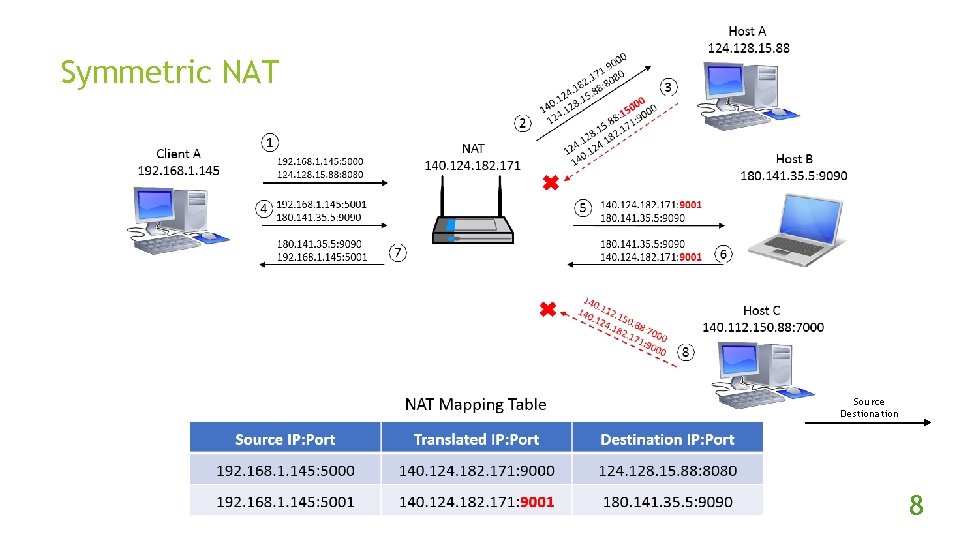
Symmetric NAT Source Destionation 8

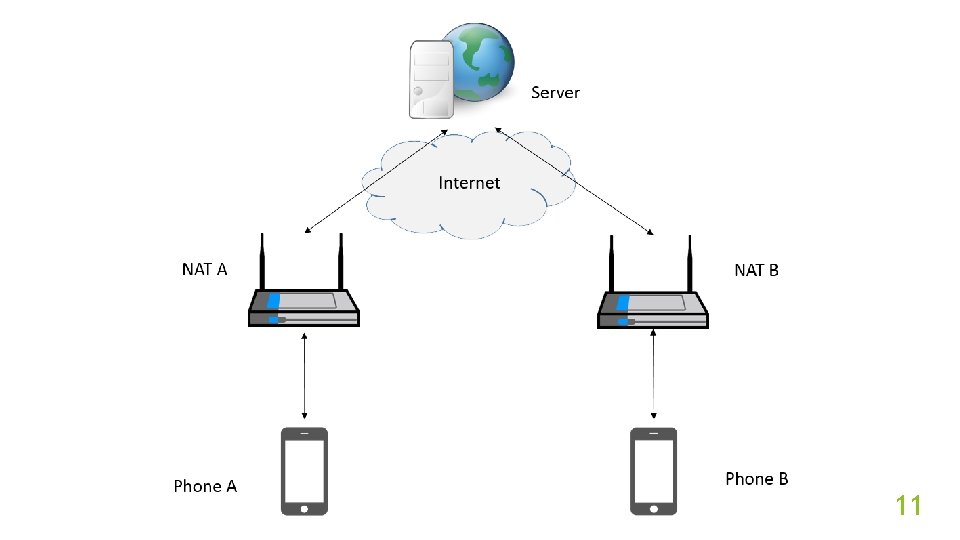
NAT Traversal NAT makes peer-to-peer connection more difficult. NAT traversal technique can make hosts connect to each other directly. Peer-to-peer applications and the nodes of Io. T especially need NAT traversal technique. 9

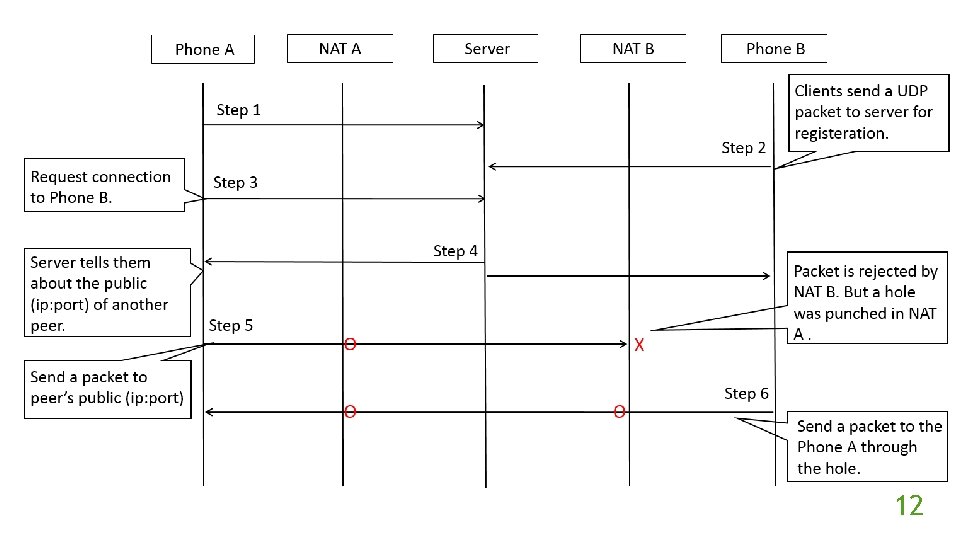
UDP Hole Punching Technique Create mapping in NAT so that hosts can pass through it. The mapping looks like a “hole”. 10

11

12

UDP Hole Punching Technique (con’t) The UDP hole punching has many limits. Improve the UDP hole punching techinique. Make an smart home Io. T application to verify the usability of the proposed method. 13

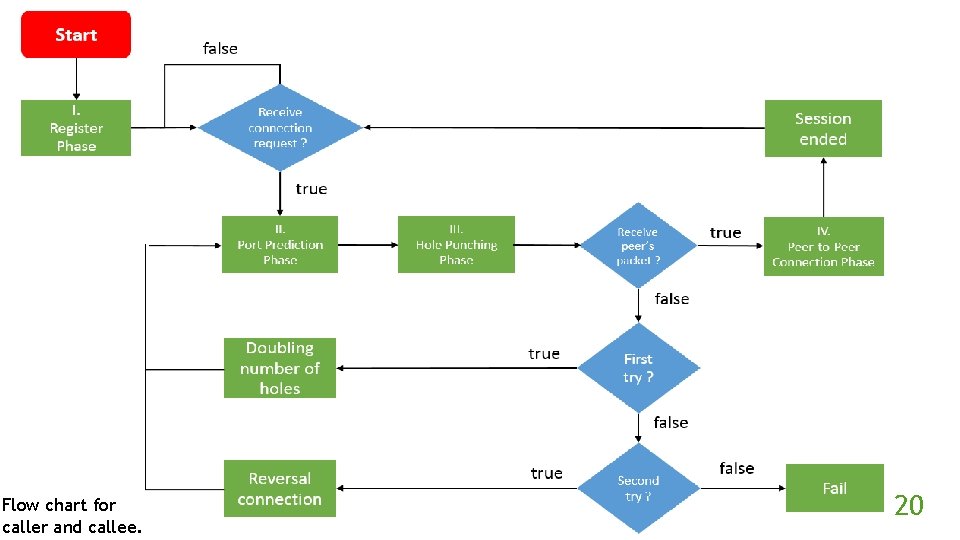
Proposed Method n Register Phase n Port Prediction Phase n Hole Punching Phase n Peer-to-peer Phase n Retry Procedures 14

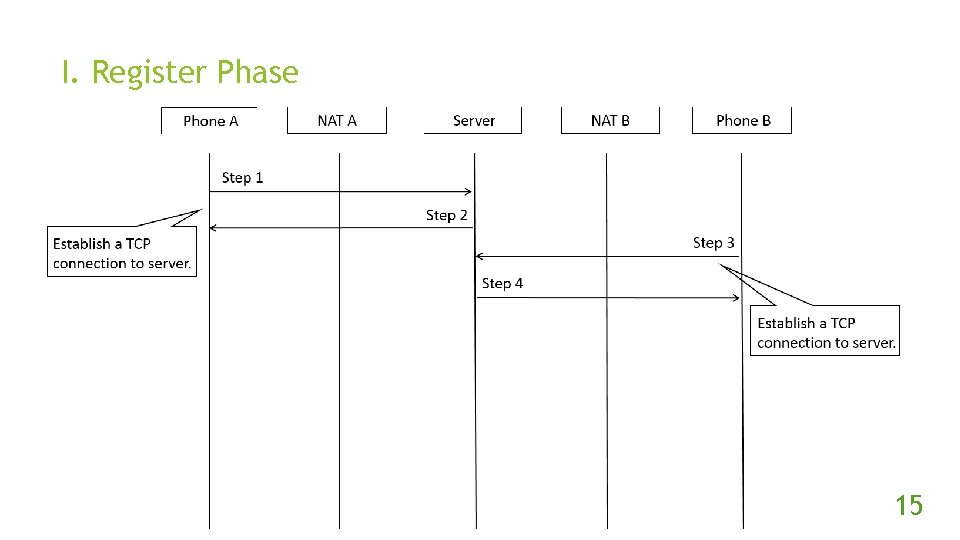
I. Register Phase 15

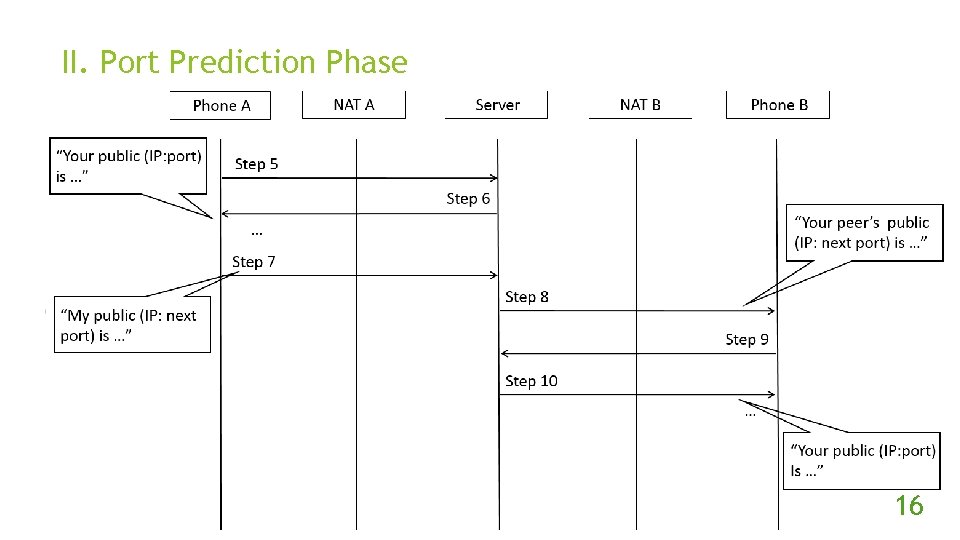
II. Port Prediction Phase 16

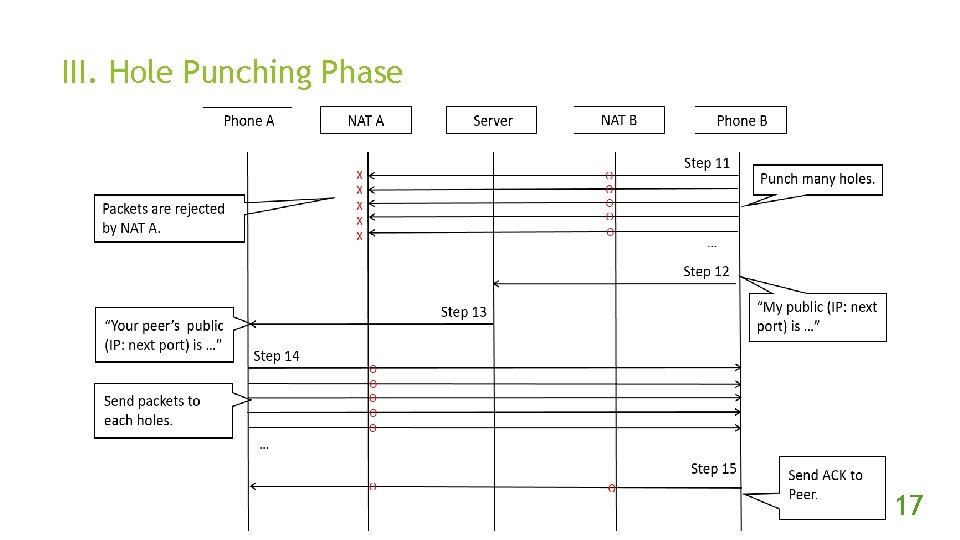
III. Hole Punching Phase 17

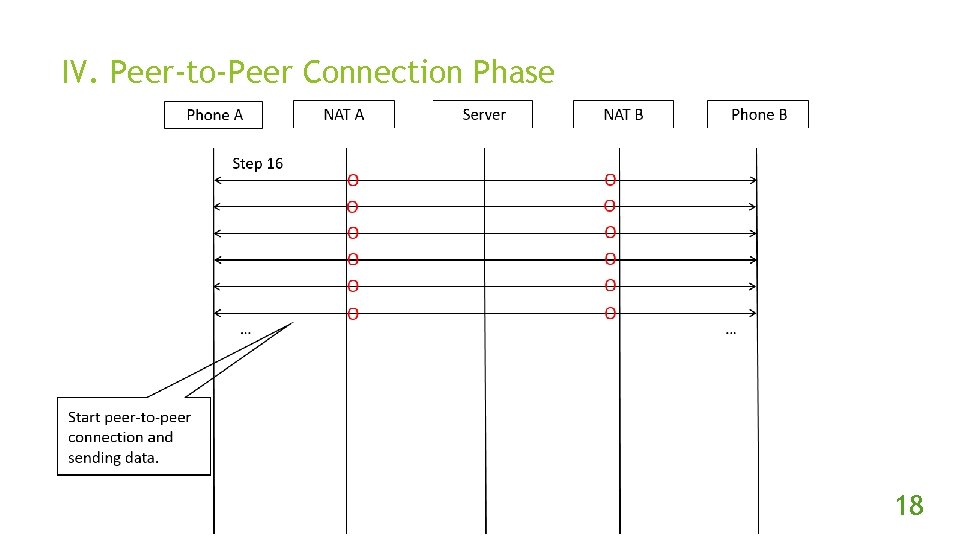
IV. Peer-to-Peer Connection Phase 18

Retry Procedures Doubling the number of holes. Reversal connection. 19

Flow chart for caller and callee. 20

Experiment n Experiment Steps n Result and Analysis n Visual Bell Application 21

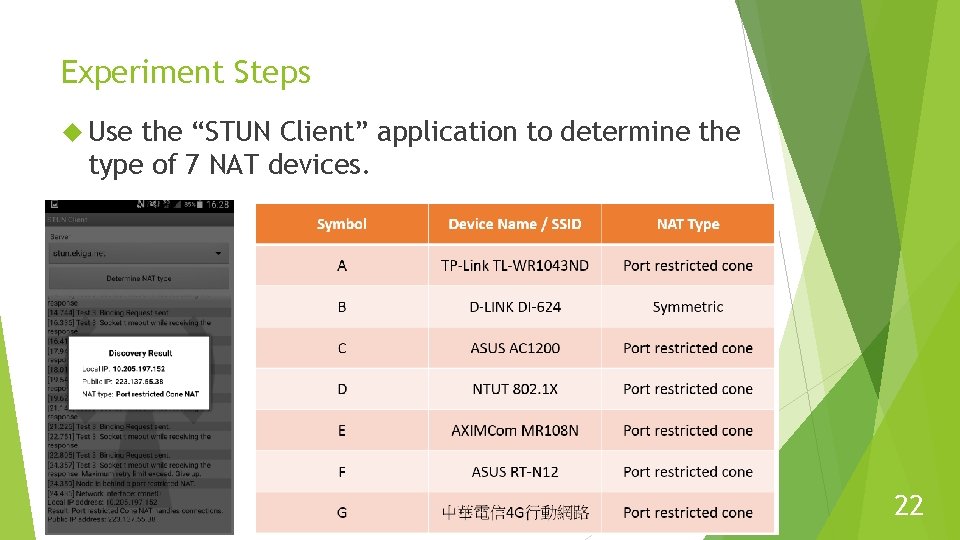
Experiment Steps Use the “STUN Client” application to determine the type of 7 NAT devices. 22

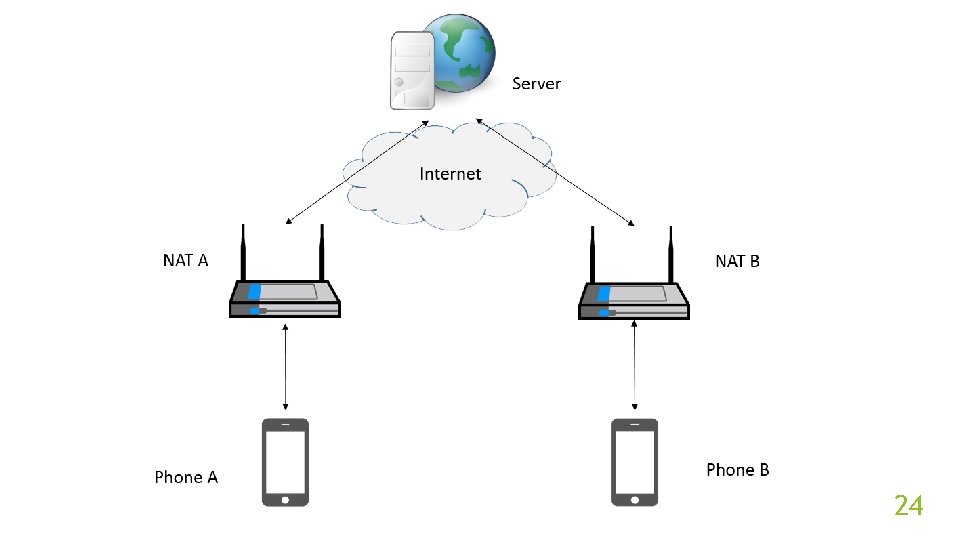
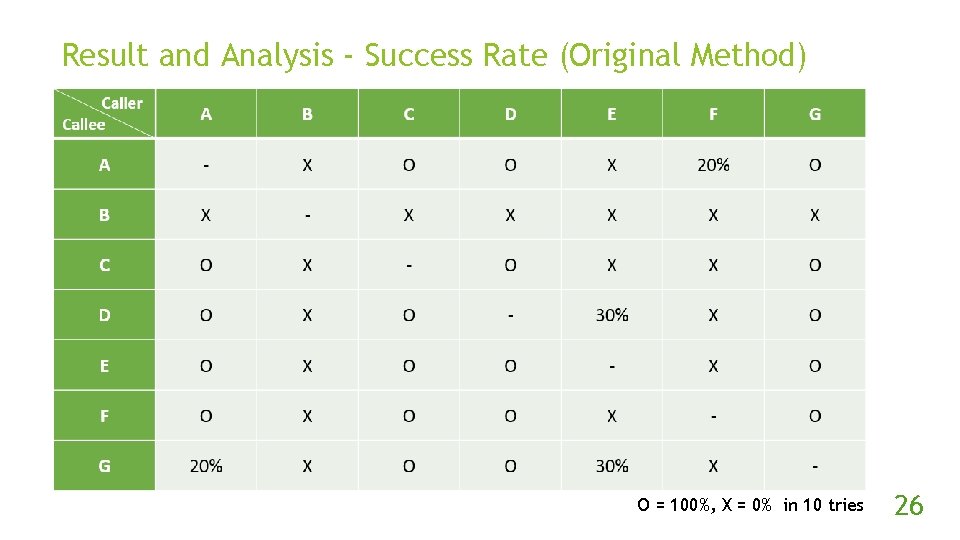
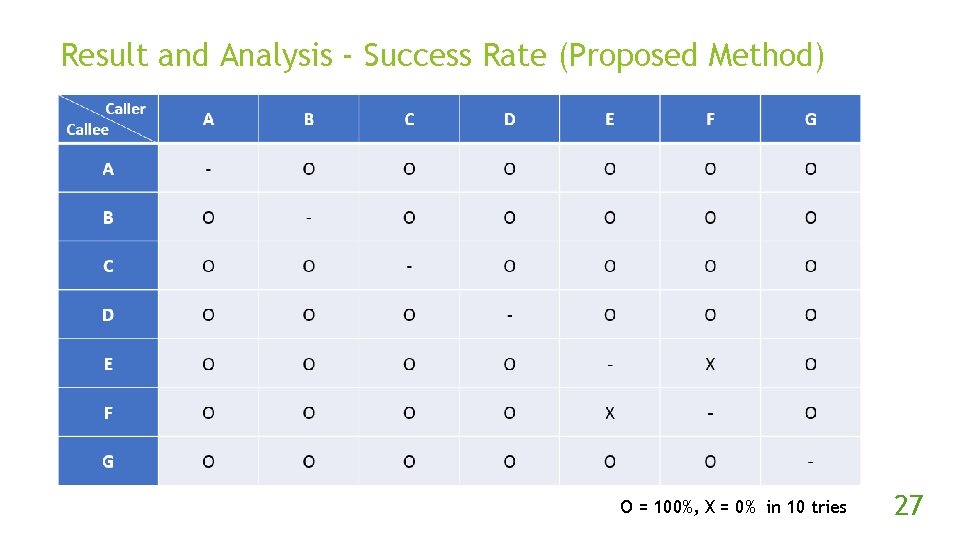
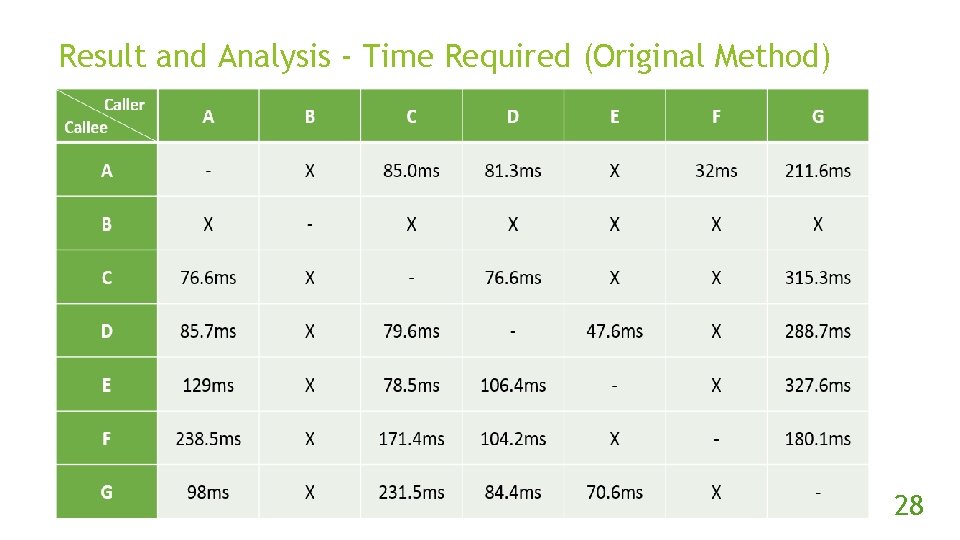
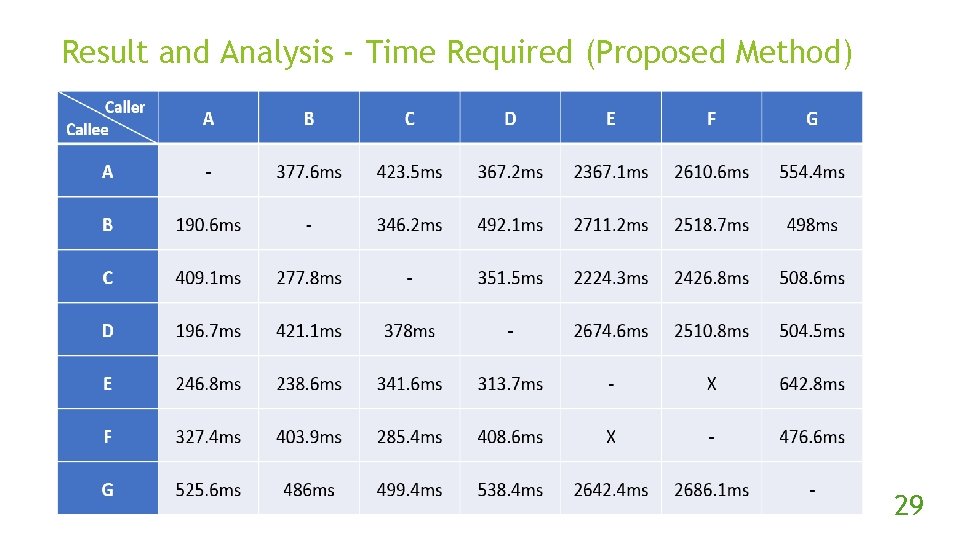
Experiment Steps (con’t) Implement the original and proposed method. Use the methods 10 times per combinations of NAT devices to traverse the NAT. In each try, if two peers got packet from another, then success, otherwise fail. 23

24

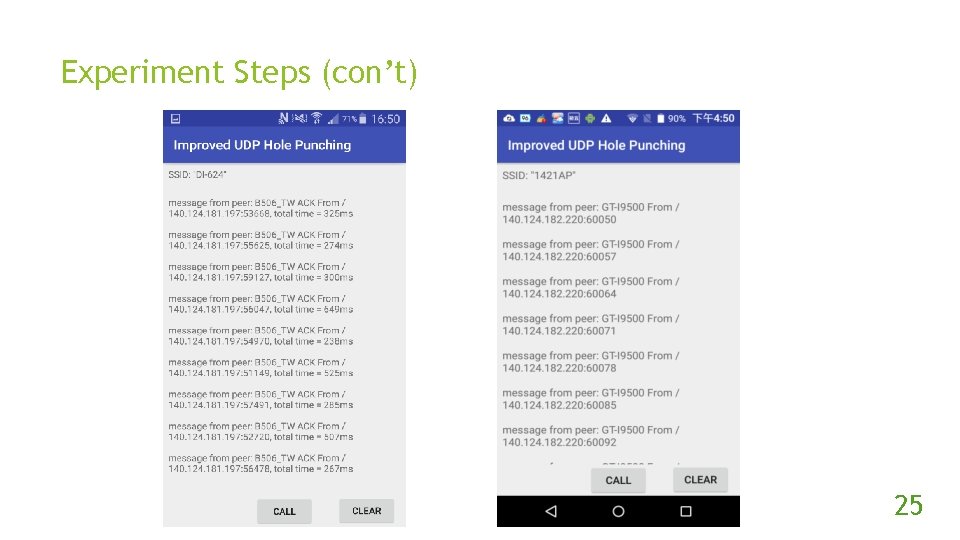
Experiment Steps (con’t) 25

Result and Analysis - Success Rate (Original Method) O = 100%, X = 0% in 10 tries 26

Result and Analysis - Success Rate (Proposed Method) O = 100%, X = 0% in 10 tries 27

Result and Analysis - Time Required (Original Method) 28

Result and Analysis - Time Required (Proposed Method) 29

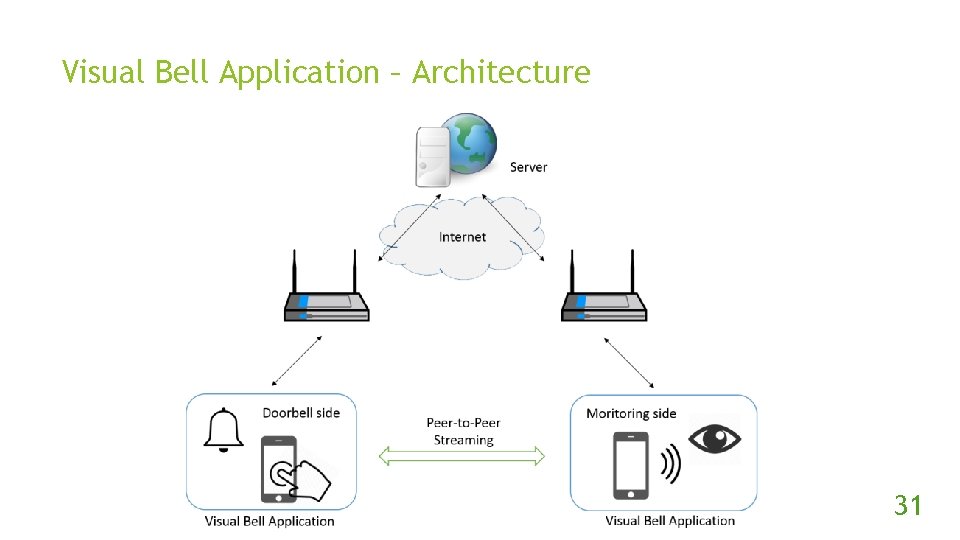
Visual Bell Application A smart-home Io. T application to verify the usability of the proposed method – A remote doorbell monitoring system, named “Visual Bell”. Two android phones, one acts doorbell, the other one acts monitor. 30

Visual Bell Application – Architecture 31

Visual Bell Application – Use case 32

Conclusion n Future Works 33

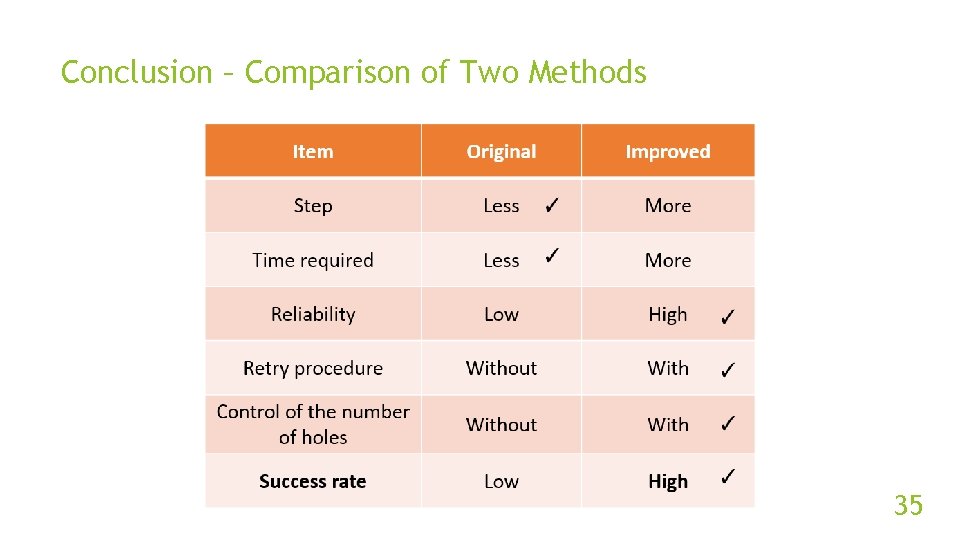
Conclusion This thesis improves the oringial UDP Hole Punching technique by following methods: Establish TCP connection to server to make sure clients can receive control messages from server. Predict the next port number used by Symmetric NAT. Create a number of mappings (holes) in NAT to increase success rate. Add two retry procedures. 34

Conclusion – Comparison of Two Methods 35

Conclusion Overall, the proposed method is better than the original one. The proposed can be applied to Android phone application and to smart home Io. T environment. 36

Future Works Speed up the proposed method. Improve Add UI. authentications. Multicasting. 37

Thanks. 38