Review for Final MIS 2101 May 7 2014
































- Slides: 79

Review for Final – MIS 2101 May 7, 2014 Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -1

Question • Applications that integrate business activities across departmental boundaries are often referred to as ____ systems. – A) computer-integrated manufacturing – B) capacity requirement planning – C) enterprise resource planning – D) manufacturing resource planning – E) materials requirement planning

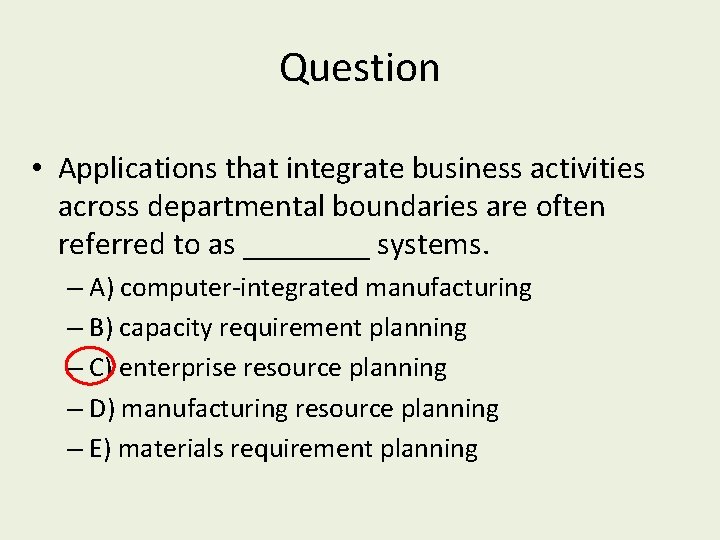
Enterprise System Approach • • An integrated suite of business applications for virtually every department, process, and industry, allowing companies to integrate information across operations on a company-wide basis using one large database. Helps to improve accuracy and timeliness of shipments, anticipate shortages, minimize costs, increase customer satisfaction and company profitability

Question • ____ occur(s) when data are isolated and replicated in separated information systems. – A) Metadata publishing – B) Encapsulation – C) Information silos – D) Automation 8/22/2011 Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -4

What Problem Does an ERP System Solve? • Information Silo Problem – Data isolated in separate information systems – Leads to inconsistent, stale and incomplete data – Difficult to make decisions rapidly • Solutions – Enterprise Application Integration (EAI) – Enterprise Resource Planning (ERP) Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -5

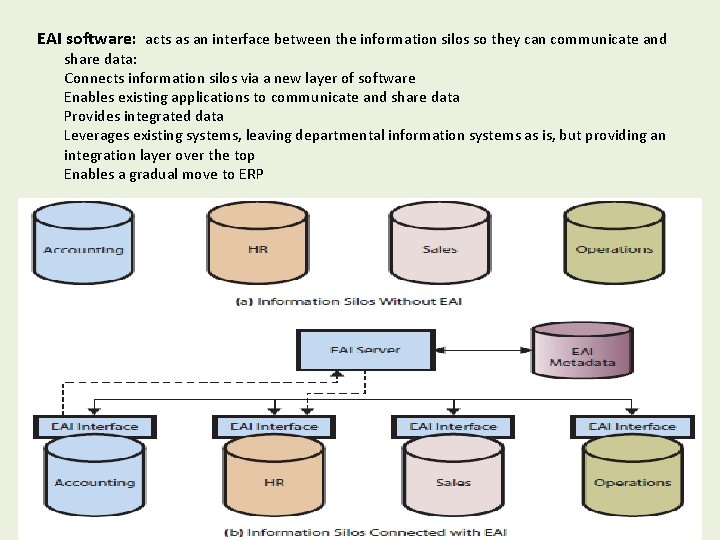
EAI software: acts as an interface between the information silos so they can communicate and share data: Connects information silos via a new layer of software Enables existing applications to communicate and share data Provides integrated data Leverages existing systems, leaving departmental information systems as is, but providing an integration layer over the top Enables a gradual move to ERP 6 -6

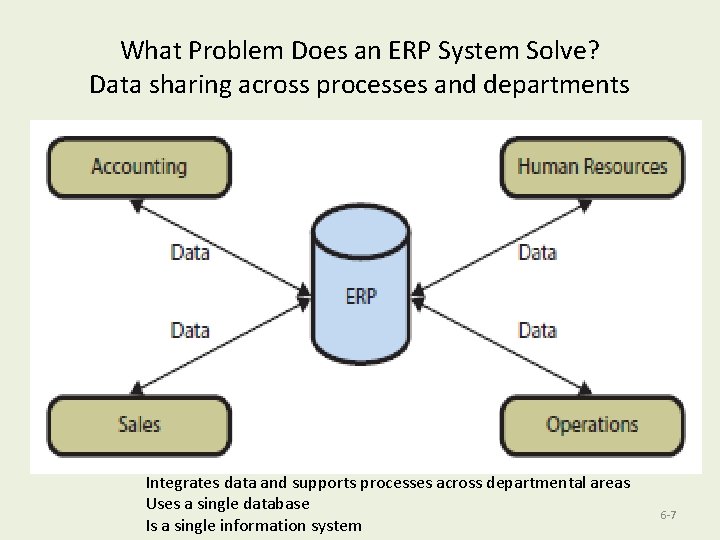
What Problem Does an ERP System Solve? Data sharing across processes and departments Integrates data and supports processes across departmental areas Uses a single database Is a single information system 6 -7

What Problem Does an ERP System Solve? • The left hand knows what the right hand is doing • ERP Systems standardize processes and bring the data from the company’s processes into one place into one single information system • By consolidating data about customers, suppliers, products, machinery, facilities, production schedules, finances, managers: – – – 8/22/2011 Make decisions with real time data Make accurate sales forecasts Save time because information is at their disposal Speed up production Address problems as they arise Save money Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 8

Question • The customization of ERP software to meet different customer requirements without changing the program code is called ____. – A) automation – B) configuration – C) modularity – D) process blueprinting 8/22/2011 Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -9

ERP System includes applications that integrate: – Supply Chain Management –inventory management, supplier management – Manufacturing – scheduling, capacity planning, quality control, Bill of Materials – CRM – sales prospecting, customer management, marketing, customer support, call center support – Human Resources – payroll, time and attendance, HR management, commission calculations, benefits admin – Accounting – GL, AR, AP, cash management, fixed-asset accounting Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -10

What Are the Elements of an ERP System? • Five Components of an ERP System: – IS Components • Software • Hardware • Data – Procedures – People • To create an ERP product, software and databases are installed on hardware; people are trained on ERP procedures Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -11

What Are the Elements of an ERP System? • Hardware – ERP Hardware Dilemma: • Use of smartphones for business activity • Should private smartphones be used to interact with ERP applications and data? • People – Users: directly interact with the system – Business or Systems Analysts: analyze to maintain and adapt the system post implementation – Consultants: multiple roles from training, to PM to configuration Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -12

What Are the Elements of an ERP System? Inherent Business Processes in ERP known as process blueprints: – System specified business processes – These are pre-defined – Organizations are often forced to adapt existing processes to these inherent business processes. – Organizations that prefer not to do this are forced to customize the ERP system to meet their requirements Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -13

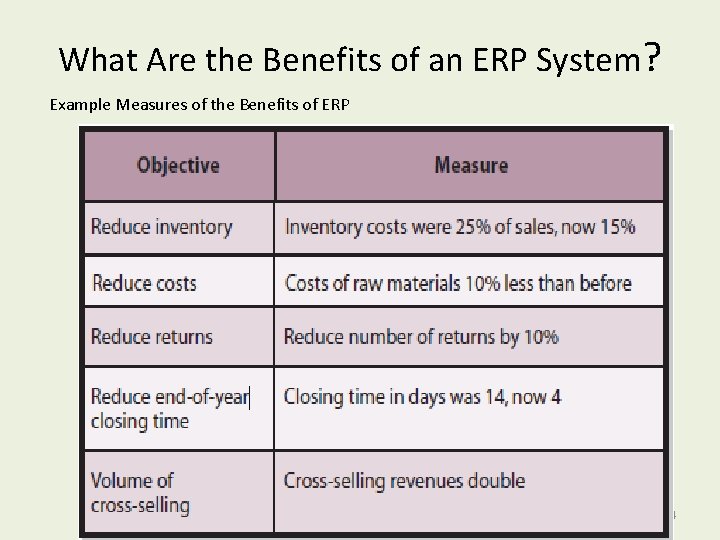
What Are the Benefits of an ERP System? Example Measures of the Benefits of ERP Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -14

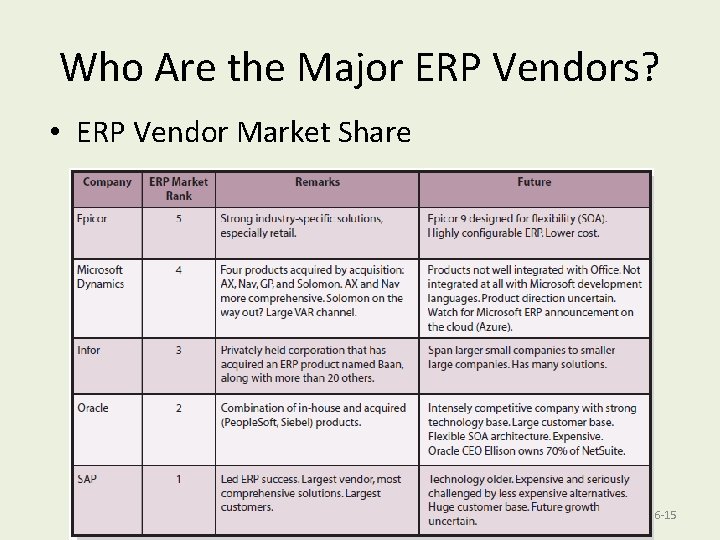
Who Are the Major ERP Vendors? • ERP Vendor Market Share Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -15

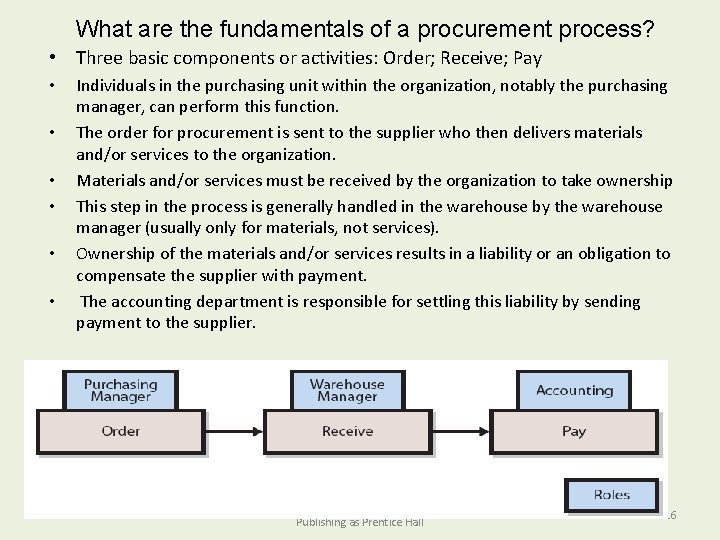
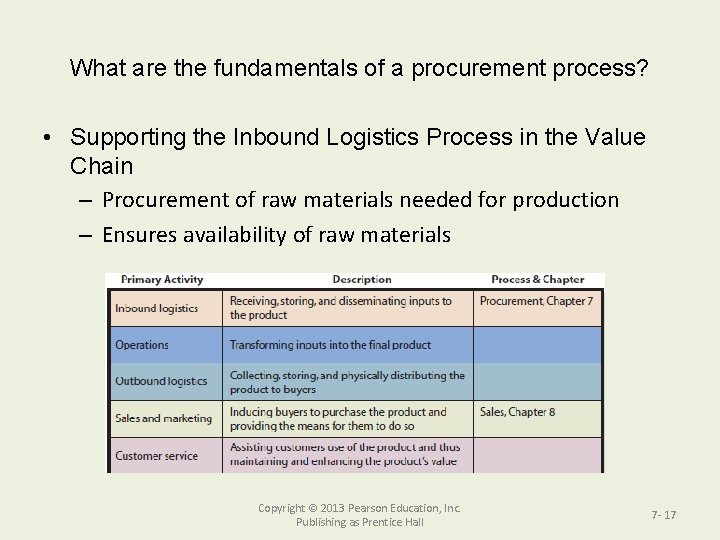
What are the fundamentals of a procurement process? • Three basic components or activities: Order; Receive; Pay • • • Individuals in the purchasing unit within the organization, notably the purchasing manager, can perform this function. The order for procurement is sent to the supplier who then delivers materials and/or services to the organization. Materials and/or services must be received by the organization to take ownership This step in the process is generally handled in the warehouse by the warehouse manager (usually only for materials, not services). Ownership of the materials and/or services results in a liability or an obligation to compensate the supplier with payment. The accounting department is responsible for settling this liability by sending payment to the supplier. Figure 7 -1 Main Procurement Process Activities and Roles Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 7 - 16

What are the fundamentals of a procurement process? • Supporting the Inbound Logistics Process in the Value Chain – Procurement of raw materials needed for production – Ensures availability of raw materials Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 7 - 17

How does the Procurement process work at CBI after SAP? • Maintained same three major activities – Order; Receive; and Pay • Benefits of SAP for CBI’s procurement process – Single database – Shared information in real time – Reduction of errors – Improved financial controls – Increased responsiveness Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 7 - 18

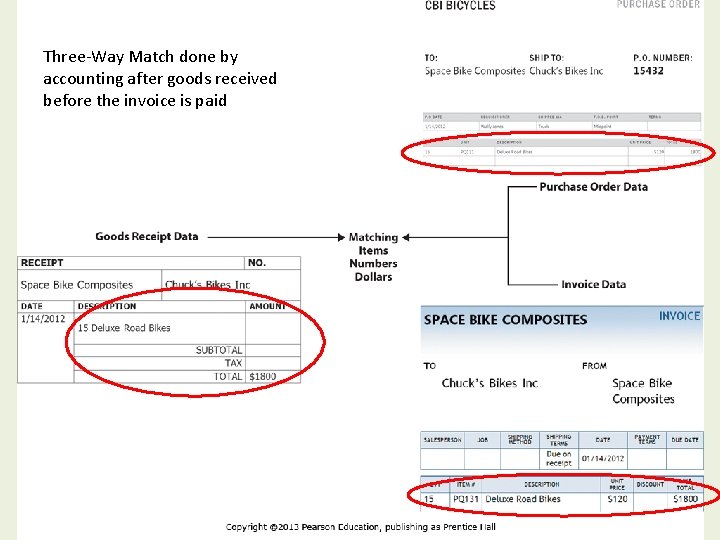
Three-Way Match done by accounting after goods received before the invoice is paid 8/22/2011 Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 7 - 19

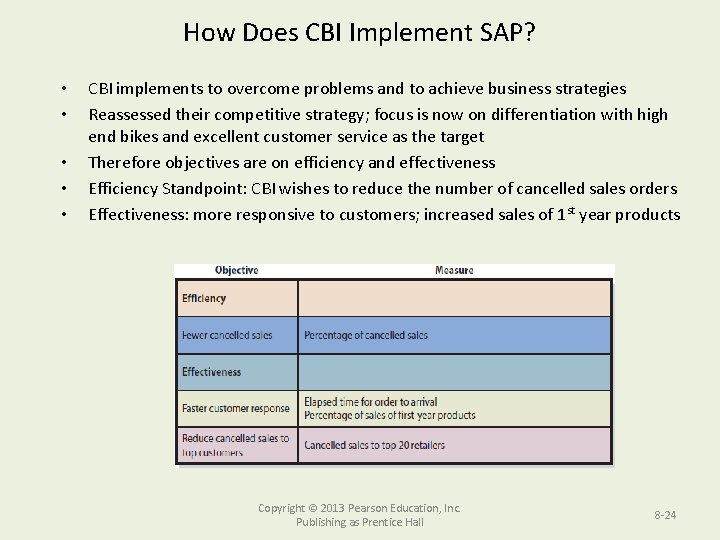
How does CBI implement SAP? • To address their problems, CBI had to reexamine and refocus their strategy • Involved three activities – Determine industry structure – Commit to a specific competitive strategy – Develop objectives and measures for processes • To help determine the industry structure, CBI turned to Porter’s Five Forces Model. – Using this model, CBI discovered the wholesale bike industry has strong rivalry with low switching costs. – For CBI, this means a retailer could easily switch from one bike maker to another. Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 7 - 20

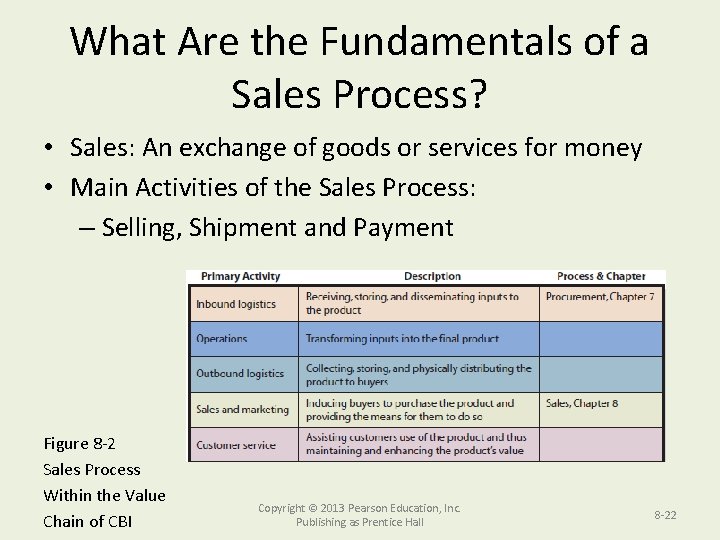
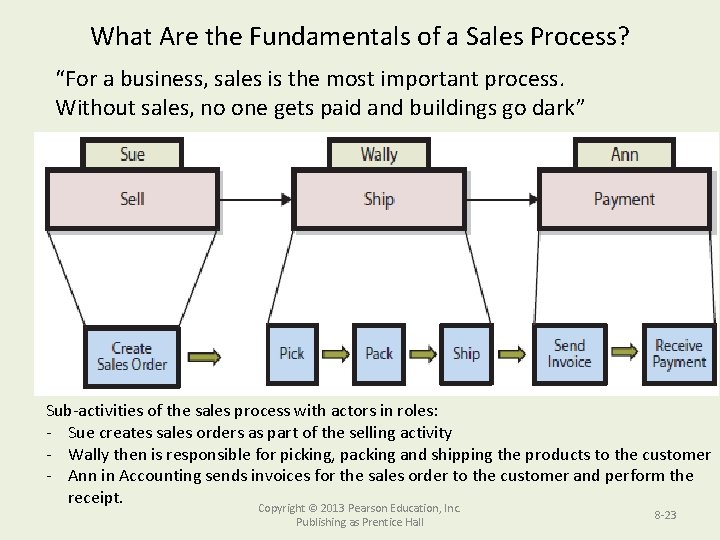
What Are the Fundamentals of a Sales Process? • Sales: An exchange of goods or services for money • Main Activities of the Sales Process: – Selling, Shipment and Payment Figure 8 -2 Sales Process Within the Value Chain of CBI Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 8 -22

What Are the Fundamentals of a Sales Process? “For a business, sales is the most important process. Without sales, no one gets paid and buildings go dark” Sub-activities of the sales process with actors in roles: - Sue creates sales orders as part of the selling activity - Wally then is responsible for picking, packing and shipping the products to the customer - Ann in Accounting sends invoices for the sales order to the customer and perform the receipt. Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 8 -23

How Does CBI Implement SAP? • • • CBI implements to overcome problems and to achieve business strategies Reassessed their competitive strategy; focus is now on differentiation with high end bikes and excellent customer service as the target Therefore objectives are on efficiency and effectiveness Efficiency Standpoint: CBI wishes to reduce the number of cancelled sales orders Effectiveness: more responsive to customers; increased sales of 1 st year products Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 8 -24

What Is a Supply Chain? • A supply chain is a collection of companies and processes moving a product: – suppliers of raw materials – suppliers of intermediate components – final production – to the customer • Upstream—flow from sources of raw materials and components • Downstream—flow to customers • Suppliers have their own supply chain • A more accurate name: supply network

Benefits and Problems with Supply Chains • Potential benefits (the well oiled machine!) – Process innovations – Just-In-time Production (JIT) – Vendor-Managed Inventory (VMI) • Potential problems (with primitive supply chains) – – Distorted information Excessive inventories Inaccurate manufacturing capacity plans Missed product schedules

Just-in-Time Production (JIT) • Keeping inventory is costly (storage, capital, missed production schedules). • JIT optimizes ordering quantities. – Parts and raw materials arrive when needed for production. – As orders arrive in smaller quantities, but at higher frequency, investment in storage space and inventory is minimized. • The approach was pioneered by Toyota. • It is used extensively by computer manufacturers to avoid component obsolescence (Moore’s law). – Example: Dell keeps only two hours of inventory in stock • JIT requires tight cooperation between all partners in the supply network.

Vendor-Managed Inventory (VMI) • VMI is a business model in which suppliers manage the manufacturer’s (or retailer’s) inventory levels based on preestablished service levels. • Supplier monitors stock levels and sales data. • VMI requires manufacturer (retailer) to share real-time data. • Benefits – – – Cost savings Minimized stock-out situations Accurate forecasts Reduced errors Prioritized goods shipments

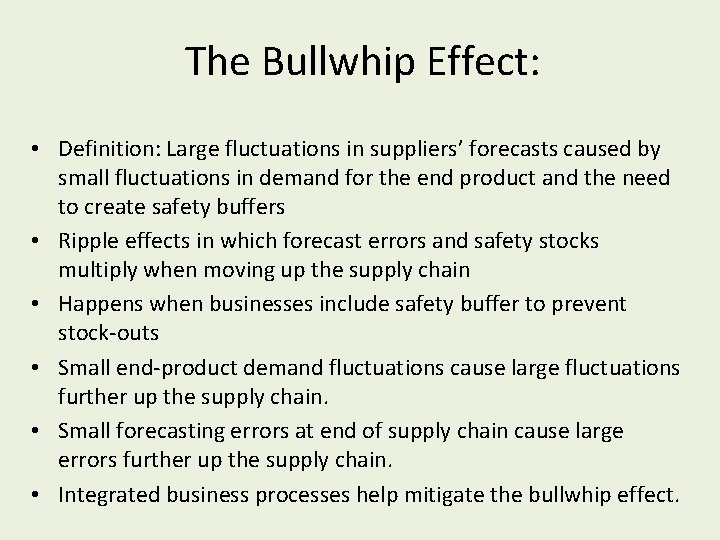
The Bullwhip Effect: • Definition: Large fluctuations in suppliers’ forecasts caused by small fluctuations in demand for the end product and the need to create safety buffers • Ripple effects in which forecast errors and safety stocks multiply when moving up the supply chain • Happens when businesses include safety buffer to prevent stock-outs • Small end-product demand fluctuations cause large fluctuations further up the supply chain. • Small forecasting errors at end of supply chain cause large errors further up the supply chain. • Integrated business processes help mitigate the bullwhip effect.

Integrating SCM with ERP and CRM • ERP systems are primarily used to optimize business processes within the organization. • SCM is used to improve business processes that span organizational boundaries. • Tight ERP/CRM/SCM integration reaps great benefits. • SCM uses data about customer orders (from CRM) and payments (from ERP).

Question • System efficiency is the extent to which a system ____. – A) allows firms to reach their operational targets – B) allows employees to reduce the risks associated with tasks – C) enables people to accomplish goals or tasks well – D) enables people to do things faster or at lower cost – E) allows people to plan tasks that are achievable

The Productivity Paradox • Measurement Problems – Effectiveness vs. efficiency – Too often the measure is based on efficiency.

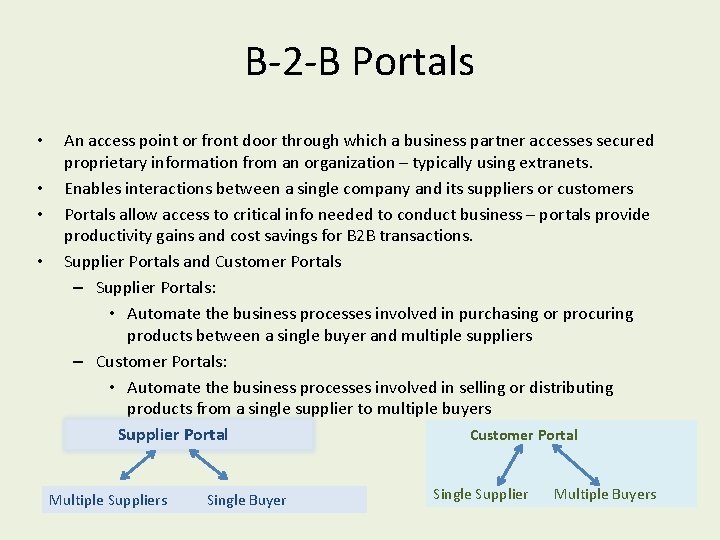
B-2 -B Portals • • An access point or front door through which a business partner accesses secured proprietary information from an organization – typically using extranets. Enables interactions between a single company and its suppliers or customers Portals allow access to critical info needed to conduct business – portals provide productivity gains and cost savings for B 2 B transactions. Supplier Portals and Customer Portals – Supplier Portals: • Automate the business processes involved in purchasing or procuring products between a single buyer and multiple suppliers – Customer Portals: • Automate the business processes involved in selling or distributing products from a single supplier to multiple buyers Supplier Portal Customer Portal Multiple Suppliers Single Buyer Single Supplier Multiple Buyers

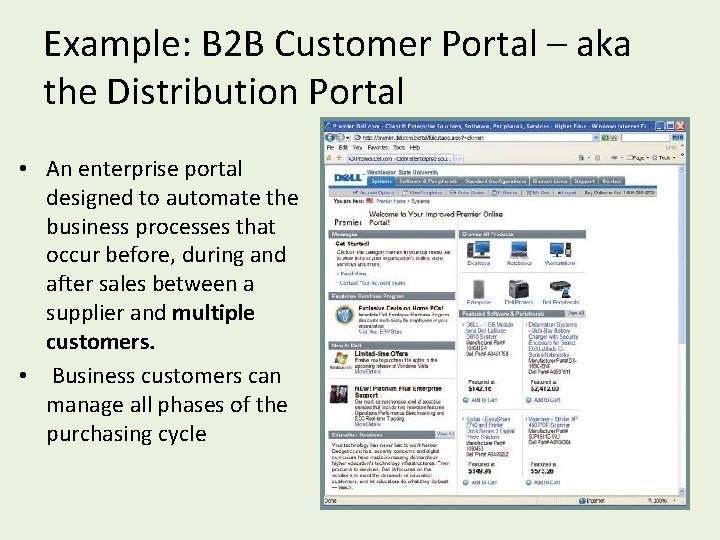
Example: B 2 B Customer Portal – aka the Distribution Portal • An enterprise portal designed to automate the business processes that occur before, during and after sales between a supplier and multiple customers. • Business customers can manage all phases of the purchasing cycle

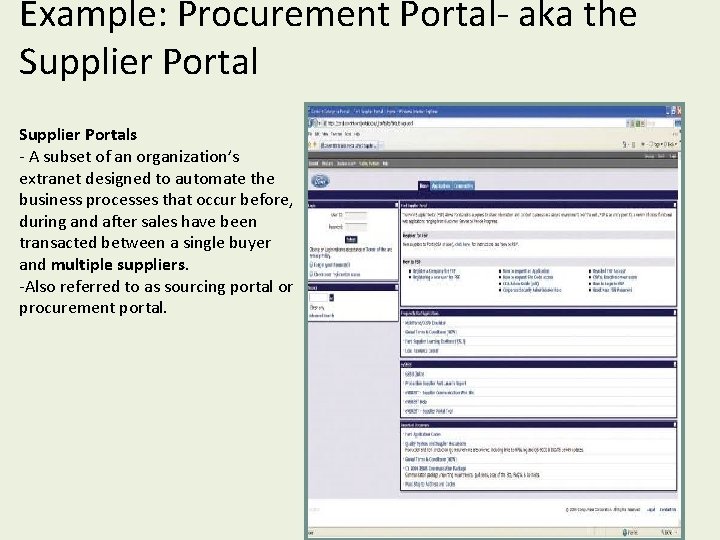
Example: Procurement Portal- aka the Supplier Portals - A subset of an organization’s extranet designed to automate the business processes that occur before, during and after sales have been transacted between a single buyer and multiple suppliers. -Also referred to as sourcing portal or procurement portal.

Customer Relationship Management (CRM) • Organizations must work harder than ever to attract and retain customers where comparison shopping is the norm and competitors are just a click away. • Customers have the power. • Economic transformation is taking place; i. e. , from transactions to relationships. • Keeping customers satisfied is key.

Customer Relationship Management (CRM) Involves managing all aspects of a customer’s relationship to increase customer loyalty and retention and profitability CRM Applications focusing on downstream information flows which have 3 objectives: • Attract potential customers • Create customer loyalty • Portray a positive corporate image Managers need to be able to monitor and analyze factors driving customer satisfaction.

Customer Relationship Management (CRM) CRM is not just technology, but a strategy, that an organization must embrace on an enterprisewide level. CRM can enable an organization to: • Identify types of customers • Design individual customer marketing campaigns • Treat each customer as an individual • Understand customer buying behaviors

Customer Relationship Management (CRM) A successful CRM implementation takes into consideration: • Data collection analysis and sharing • Policies and business processes • Documentation • Employee Training

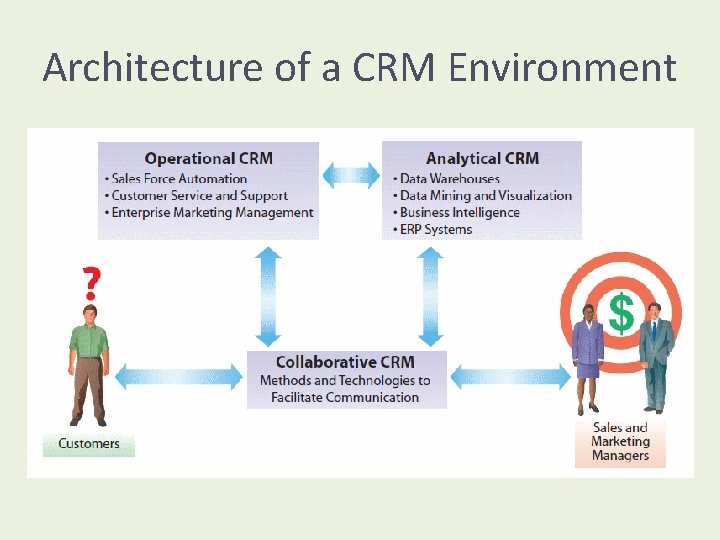
Architecture of a CRM Environment

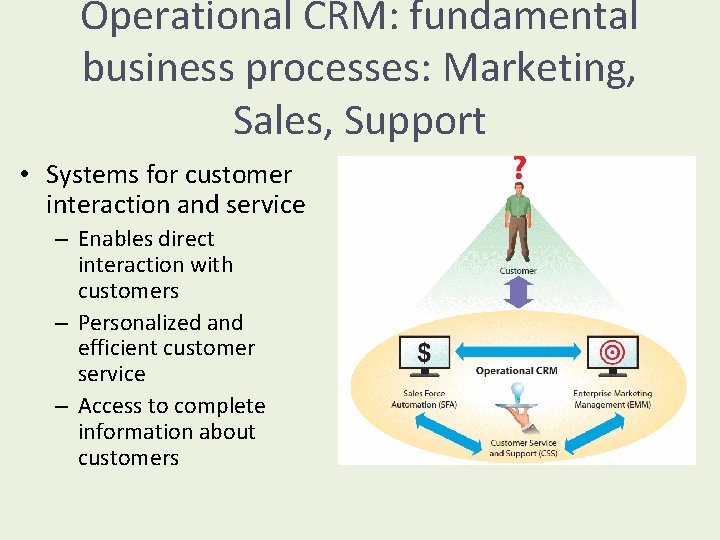
Operational CRM: fundamental business processes: Marketing, Sales, Support • Systems for customer interaction and service – Enables direct interaction with customers – Personalized and efficient customer service – Access to complete information about customers

Sales Force Automation - SFA • Component of operational CRM • Supports day-to-day sales activities: Order processing and tracking Account and contact management Opportunity management Sales management Territory management Customer history preferences, (product and communication) management – Sales forecasting and performance analysis – – –

Examples of Sales Measures Tracked by SFA • • Sales pipeline for each salesperson, including rating and probability • • Margins by product category, customer segment, or customer • Number of lost customers period or cost of customer acquisition • Percentage of goods returned, number of customer complaints, or number of overdue accounts Revenue per sales person, per territory, or as a percentage of sales quota Number of calls per day, time spent per contract, revenue per call, cost per call, ratio of orders to calls

Enterprise Marketing Management (EMM) • Third component of an operational CRM is Enterprise Marketing Management (EMM) • Improve management of promotional campaigns – Make sure right messages are sent to the right people through the right channels • Customer lists need to be managed carefully • Individualized attention to each potential customer – Extensive analytical capabilities that can help to analyze effectiveness of campaigns

Analytical CRM – one goal: a 360 degree view of the customer to maximize the outcomes of sales and marketing campaigns and to find the most profitable customers • Analysis of customer behavior and perceptions • Customized marketing – Up-selling, cross-selling more profitable products and more profitable bundles of products or services tailored to specific customers – Zip code, state, and regional analysis – Customers’ preferred communication channels – Retaining customers • Key technologies used to create predictive models for acquisition and retention: – Data mining – Takes into account: customer demand, product usage as well as competitors: price, quality, and satisfaction • Continuous data collection and analysis is necessary

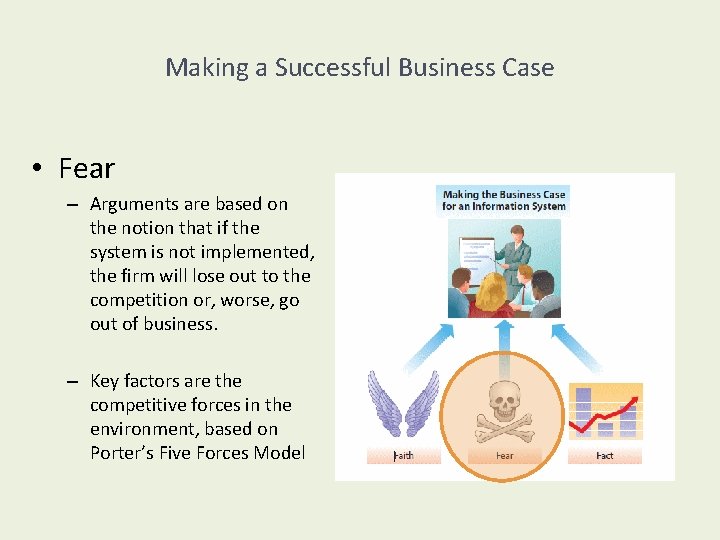
Making a Successful Business Case • Three common types of arguments in a business case for an IS: – Faith – Fear – Fact

Making a Successful Business Case • Faith – Arguments are based on beliefs about organizational strategy, competitive advantage, industry forces, customer perceptions, market share, and so on – Firm’s mission and objectives, strategy for achieving them, and types of IS needed should be clearly described.

Making a Successful Business Case • Fear – Arguments are based on the notion that if the system is not implemented, the firm will lose out to the competition or, worse, go out of business. – Key factors are the competitive forces in the environment, based on Porter’s Five Forces Model

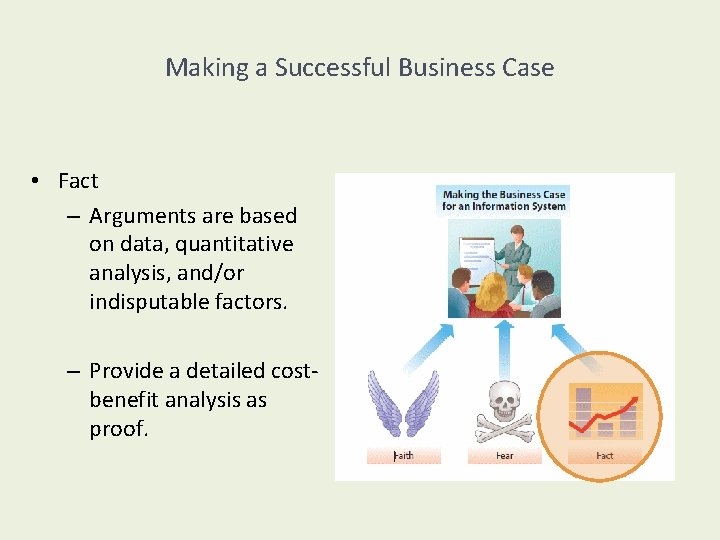
Making a Successful Business Case • Fact – Arguments are based on data, quantitative analysis, and/or indisputable factors. – Provide a detailed costbenefit analysis as proof.

Presenting the Business Case • Know the audience. – People from different areas of the firm typically hold very different perspectives. • Convert benefits to monetary terms. – Example: Convert time savings into dollar figures. • Devise proxy variables. – Alternative measures of outcomes – Example: Reduction in administrative tasks, more customer contact • Measure what is important to management. – Concentrate on the issues senior business managers care about. – Hot-button issues: Cycle time, regulatory and compliance issues, customer feedback, employee morale

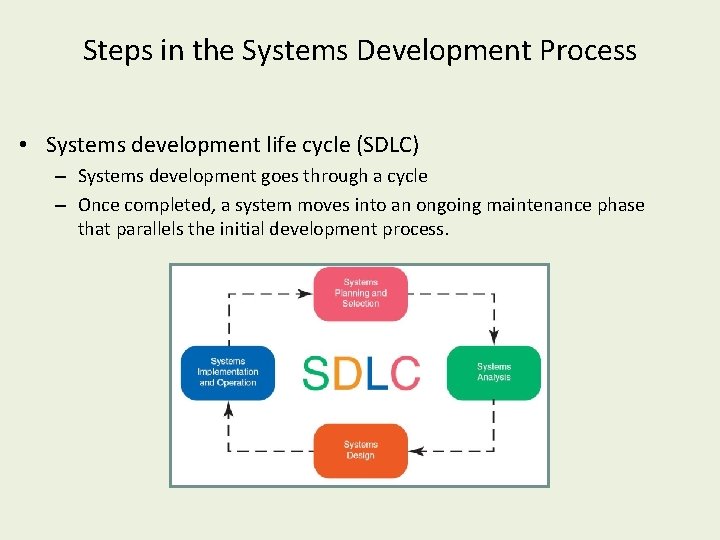
Steps in the Systems Development Process • Systems development life cycle (SDLC) – Systems development goes through a cycle – Once completed, a system moves into an ongoing maintenance phase that parallels the initial development process.

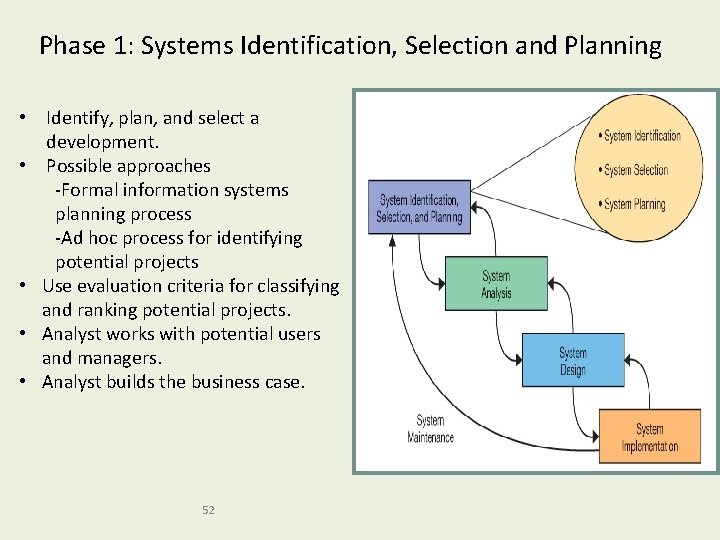
Phase 1: Systems Identification, Selection and Planning • Identify, plan, and select a development. • Possible approaches -Formal information systems planning process -Ad hoc process for identifying potential projects • Use evaluation criteria for classifying and ranking potential projects. • Analyst works with potential users and managers. • Analyst builds the business case. 52

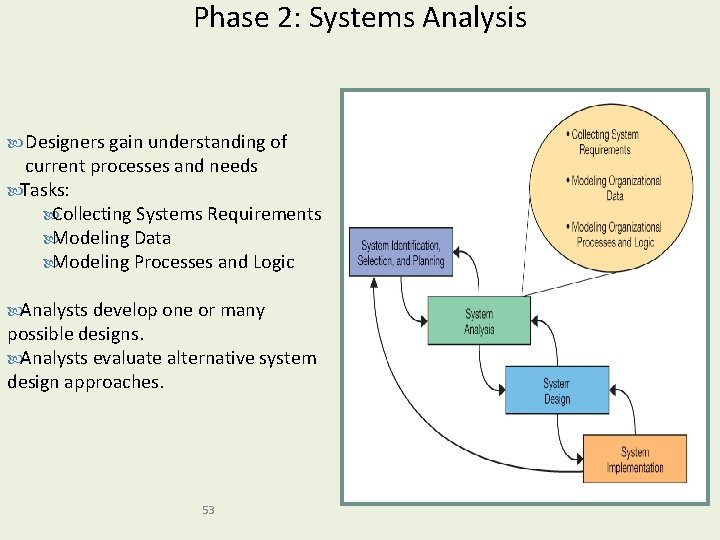
Phase 2: Systems Analysis Designers gain understanding of current processes and needs Tasks: Collecting Systems Requirements Modeling Data Modeling Processes and Logic Analysts develop one or many possible designs. Analysts evaluate alternative system design approaches. 53

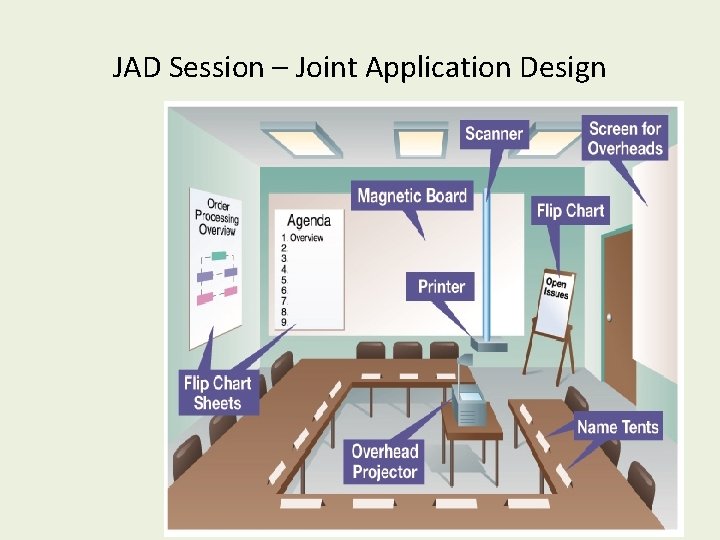
JAD Session – Joint Application Design

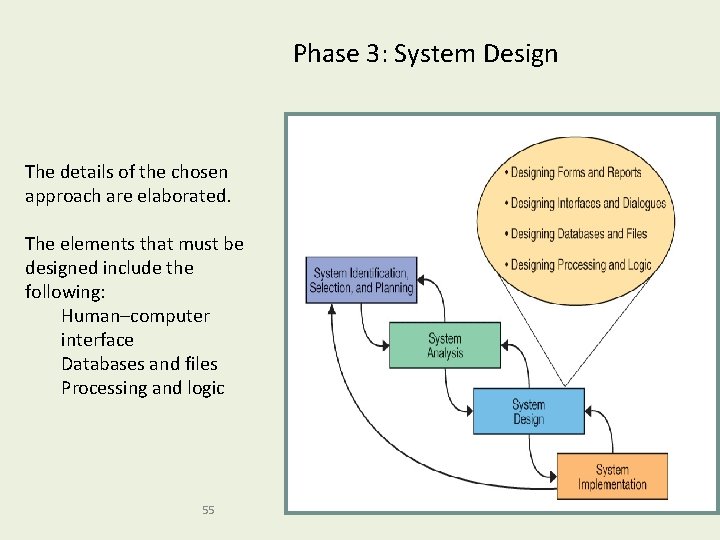
Phase 3: System Design The details of the chosen approach are elaborated. The elements that must be designed include the following: Human–computer interface Databases and files Processing and logic 55

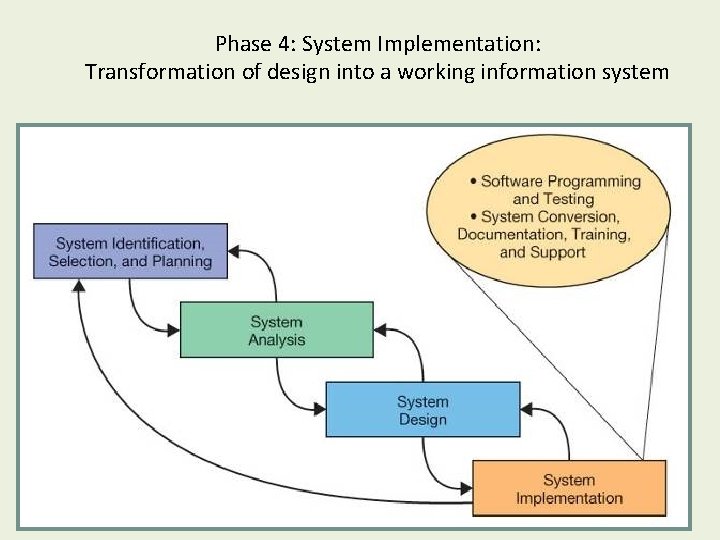
Phase 4: System Implementation: Transformation of design into a working information system

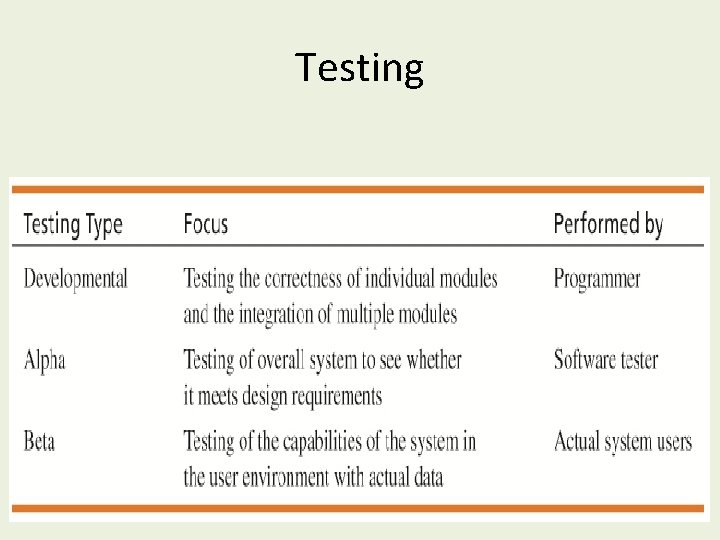
Testing

Improving Business Processes Through Enterprise Systems • Packaged software aka Off the Shelf Software – Written by third-party vendors – Used by many different organizations – Useful for standardized, repetitive tasks – Cost effective – Example: Microsoft Office, Intuit Payroll & Quick. Books • Custom software – Developed exclusively for a specific organization – Designed for particular business needs – Higher development costs – Example: used in hospitals, schools, billing, construction

Customized Vs. Off-the-Shelf Software • General purpose systems typically are purchased offthe-shelf. • Specific needs often cannot be met by off-the shelf software. • Companies capitalizing on a first-mover advantage often cannot purchase existing systems. – Examples: online retailing (Amazon. com) and Budget air travel (Southwest Airlines)

Off-the-Shelf Software • Packaged software • Supports common business processes that do not require any specific tailoring • Advantages – Less costly – Easy to procure – Require no specific tailoring

Customized Software • Developed in-house or contracted/outsourced to a specialized vendor • Advantages of customized software – Customizability • Fit with business operations, culture, and so on – Problem specificity • Company only pays for features actually needed.

Vanilla Versus Customized Software • Vanilla version – This version contains features and modules that an enterprise system comes with out of the box. – Certain processes might not be supported. • Customization – This version contains additional software or changes to vanilla version. – It always needs to be updated with new versions of vanilla.

Licenses • Shrink Wrap Licenses: – Primarily used on consumer products – Contract is activated when the shrink wrap on the package is removed • Click Wrap Licenses: – Primarily used for downloaded software – Computer user must accept the license terms by clicking a button before installing the software • Enterprise Licenses: AKA Volume Licenses – Usually negotiated between the vendor and the purchasing company – Contracts include permissions and rights – Liability and warranty disclaimers included to protect the software vendor from being sued • Freeware or Shareware – Freely available – Copyright owners usually retain their rights – Vendors usually do not provide access to the source code 8/22/2011 Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -63

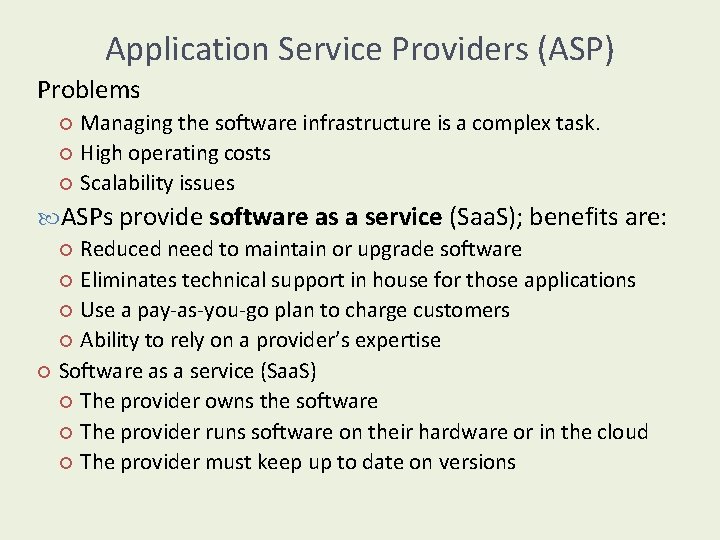
Application Service Providers (ASP) Problems Managing the software infrastructure is a complex task. High operating costs Scalability issues ASPs provide software as a service (Saa. S); benefits are: Reduced need to maintain or upgrade software Eliminates technical support in house for those applications Use a pay-as-you-go plan to charge customers Ability to rely on a provider’s expertise Software as a service (Saa. S) The provider owns the software The provider runs software on their hardware or in the cloud The provider must keep up to date on versions

Steps in External Acquisition • Competitive bid process—find the best system for lowest possible price. 1. Systems planning and selection 2. Systems analysis 3. Development of a request for proposal 4. Proposal evaluation 5. Vendor selection • The first two steps are similar to SDLC.

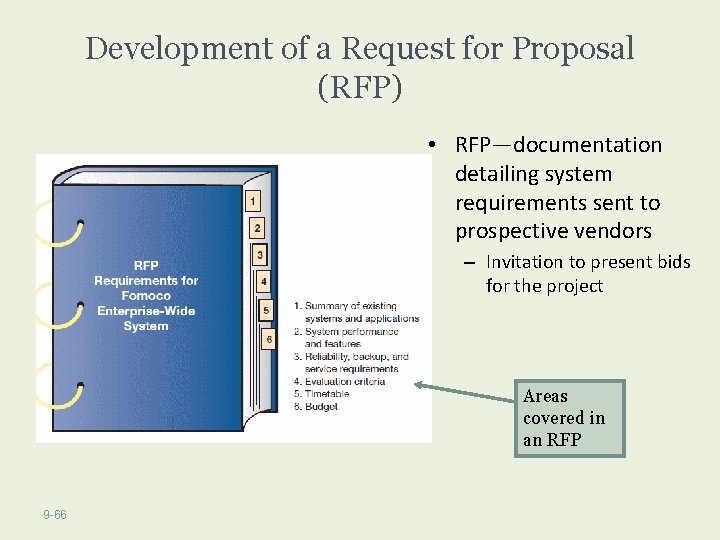
Development of a Request for Proposal (RFP) • RFP—documentation detailing system requirements sent to prospective vendors – Invitation to present bids for the project Areas covered in an RFP 9 -66

Proposal Evaluation • Proposal evaluation—An assessment of proposals received from vendors. – May include system demonstrations – System benchmarking – evaluation method • Standardized tests to compare different proposed systems • Common system benchmarks – – – Response time given a specified number of users Time to sort records Time to retrieve a set of records Time to produce a given record Time to read in a set of data

Vendor Selection • Usually more than one system will meet the criteria. • Determine the best fit • Need to prioritize/rank the proposed systems – Best ranking system is chosen. – Formal approach—devise a scoring system for the criteria; multi-layer criteria with weighting – Less formal approaches: • Checklists • Subjective processes

Computer Crime • Computer crime—The act of using a computer to commit an illegal act. – Targeting a computer while committing an offense. – Using a computer to commit an offense. – Using computers to support a criminal activity. • Overall trend for computer crime has been declining over the past several years (CSI, 2011). • IS Risk Management, gaining an understanding of the interplay between: – Threats: undesirable event that can cause harm – Vulnerabilities: weakness in an organization’s systems or security policies – Impact: Severity of the consequences if a threat causes damage by exploiting a vulnerability

Hacking and Cracking • Which one is the “bad guy”? – Hackers: • Someone who is knowledgeable enough to gain access to computer systems without authorization • Done out of curiosity and not with the desire to harm – Crackers • Those who break into computer systems with the intention of doing damage or committing a crime – Hacktivists • Those who attempt to break into systems or deface Web sites to promote political or ideological goals (free speech, human rights, and antiwar campaigns)

Cybersquatting • The practice of registering a domain name and later reselling it for $$$ • Some of the victims include: – – Eminem Panasonic Hertz Avon • Anti-Cybersquatting Consumer Protection Act in 1999 – Fines as high as $100, 000 – Some companies pay the cybersquatters to speed up the process of getting the domain – Regardless, dealing with cybersquatting takes up valuable time and money

Cyber Harassment and Stalking • Cyber harassment— – Crime that broadly refers to the use of a computer to communicate obscene, vulgar, or threatening content. – Against a group or person to express hatred or seek revenge • Cyber stalking – Making false accusations that damage reputation of another – Gaining information on a victim by monitoring online activities – Using the Internet to encourage others to harass a victim – Attacking data and equipment of a victim by sending e-mail viruses or other destructive code – Using the Internet to place false orders for goods or services

Cyberwar • Cyberwar—Military’s attempt to disrupt or destroy another country’s information and communication systems – Goal is to diminish opponent’s communication capabilities. – It is used in concert with traditional methods.

Cyberterrorism • Governments are not involved. • Attacks can be launched from anywhere in the world. • Goal is to cause fear, panic, and destruction. • Cyberterrorism will likely become weapon of choice.

Information Systems Security • All systems connected to a network are at risk. – Internal threats – External threats • Information systems security – Precautions to keep IS safe from unauthorized access and use • Explicit need for good computer security with global use of the Internet

Biometrics • Form of authentication – Fingerprints – Retinal patterns – Facial features and so on • Fast authentication • High security

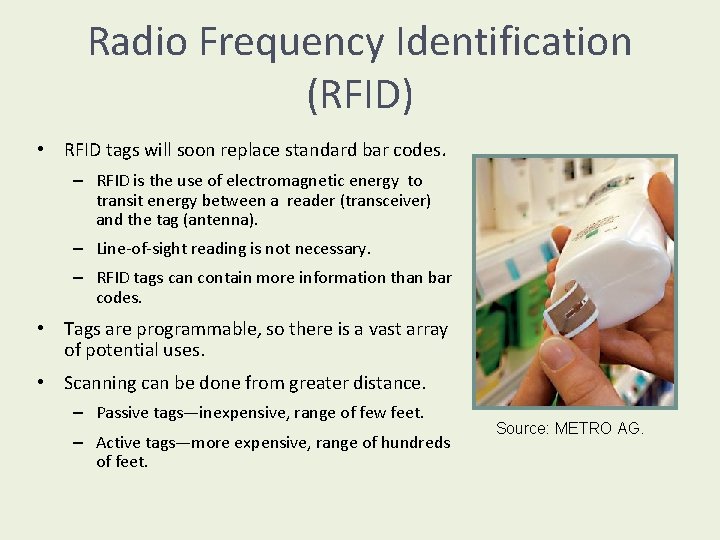
Radio Frequency Identification (RFID) • RFID tags will soon replace standard bar codes. – RFID is the use of electromagnetic energy to transit energy between a reader (transceiver) and the tag (antenna). – Line-of-sight reading is not necessary. – RFID tags can contain more information than bar codes. • Tags are programmable, so there is a vast array of potential uses. • Scanning can be done from greater distance. – Passive tags—inexpensive, range of few feet. – Active tags—more expensive, range of hundreds of feet. Source: METRO AG.

Disaster Planning • Disasters can’t be completely avoided. Need to be prepared. • Business continuity plan – describes how a business resumes operation after a disaster • Disaster recovery plan – Subset of business continuity plan – Procedures for recovering from systems-related disasters – Two types of objectives • Recovery time objectives (Maximum time allowed to recover) • Recovery point objectives (How current should the backup material be? ) – Mission critical data should have complete redundancy, e. g. transactions – Data mining could wait longer without disrupting primary business processes

Audits • Organizations periodically have an external entity review the controls so as to uncover any potential problems in the controls. This process is called an information systems audit 8/22/2011 Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -79

Other Areas to focus on • • Supply Chain Sequence Steps in the procurement process Procurement Terms and sequencing The value of Information Systems 8/22/2011 Copyright © 2013 Pearson Education, Inc. Publishing as Prentice Hall 6 -80