PHYSICAL SECURITY PROFESSIONAL PSP Certification Examination Review 3













































































































- Slides: 124

PHYSICAL SECURITY PROFESSIONAL (PSP) Certification Examination Review 3 DOMAIN IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) October 2017 Dennis Shepp, CPP

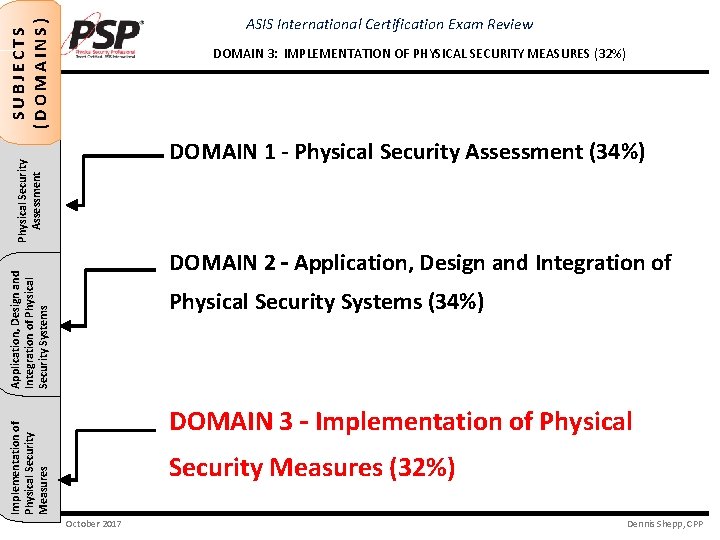
SUBJECTS (DOMAINS) ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) ACCESS CONTROL Application, Design and Physical Security SYSTEMS Integration of Physical Assessment Security Systems DOMAIN 1 - Physical Security Assessment (34%) DOMAIN 2 – Application, Design and Integration of Physical Security Systems (34%) Implementation of Physical Security Measures DOMAIN 3 – Implementation of Physical Security Measures (32%) October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) Task 1: Outline criteria for pre-bid meeting to ensure comprehensiveness and appropriateness of implementation Task 2: Procure system to address risks identified Task 3: Conduct final acceptance testing and implement/provide procedures for ongoing monitoring and evaluation of the measures Task 4: Implement procedures for ongoing monitoring and evaluation throughout the system life cycle Task 5: Develop requirements for personnel involved in support of the security program October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) Task 1: Outline criteria for pre-bid meeting to ensure comprehensiveness and appropriateness of implementation October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) Task 1: Outline criteria for pre-bid meeting to ensure comprehensiveness and appropriateness of implementation. Knowledge of: 1. 2. 3. 4. Bid package components Criteria for evaluation of bids Technical compliance criteria Ethics in contracting October 2017 Dennis Shepp, CPP

3. 1. 1: “The bid package components for pre-bid meeting to ensure comprehensiveness and appropriateness of implementation” CHAPTER 13 PRINCIPLES OF PROJECT MANAGEMENT, Knoke Physical Security Principles (Kindle Locations 1054610548) • Combining the design package into a bid package (including manufacturer’s contract information, drawings, specifications, hardware schedules, bidder instructions and requirements, licenses, experience, and qualifications; terms and conditions; and securitysensitive information requirements)

CHAPTER 6 PROCUREMENT Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1726 -1729) • Invitation for bids (IFB) - used when the customer has completed its own security system design, including the selection of hardware and software. • The invitation for bids asks vendors to state the cost of materials and installation. • Usually, the qualified bidder with the lowest price is awarded the contract. This type of procurement is also referred to as a request of quotation (RFQ). • Bid package or construction documents consists of bidders’ instructions, specifications, drawings and schedules, and hardware schedules.

3. 1. 2 and 3. 1. 4: “Outline the criteria for the evaluation of bids and explain the ethics in contracting relating to the pre-bid meeting to ensure comprehensiveness and appropriateness of implementation. ” CHAPTER 6 PROCUREMENT “Evaluation Criteria”, • Forms a basis for ethical guidelines and metrics for the procurement and selection process. • No direct reference to ethics in the pre-bid, bid or entire procurement process. • Recommend follow standards and best practice as outlined in the Procurement Process (14. 8 Knoke) and Patterson – be guided accordingly by the processes discussed.


3. 1. 3: “Outline the technical compliance criteria for pre-bid meeting to ensure comprehensiveness and appropriateness of implementation” CHAPTER 5: Patterson, page 80: • Bid bond - guarantees that the bidder on a contract will enter into the contract and furnish the required payment and performance bonds. • Common business practice for the tender to be supported by a bid bond (also known as a tender bond). • An indication of the contractor’s ability to carry out the work requested. • Form of insurance should the successful bidder fail to proceed with the contract for any reason.

• Performance bond - Most large projects put out to bid require the successful bidder to provide a performance bond after being awarded the contract. • Indicates that the company has the necessary skills and capabilities to carry out the required work and comply with the agreed terms and conditions of the contract. 14. 3. 5 SPECIFICATIONS Knoke page 458 • PPS specification includes: • instructions to bidders with a list of all documents included in the contract documents • list of project references

• functional description of the complete system design, its intended functional operation in a concept of operations, maintenance and warranty requirements, quality assurance provisions, and installation schedule • list of design drawings • list and description of products and services to be included in the contract • list of required products and services included in other contracts (such as electrical door hardware, which is provided and installed under the door hardware contract but must be connected to the PPS by the security contractor)

• list of applicable codes and standards • support services, such as drawing, sample and documentation submittals, commissioning, testing, training, warranty, maintenance, and spare parts • technical descriptions of all major subsystems and their components, including capacity, capability, expandability, performance and operational parameters, environmental operating parameters, installation and integration details, appearance and finish, and acceptable makes and models • general site conditions, installation standards, exact statement of particulars, materials, dimensions, and quality control standards

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) Task 2: Procure system to address risks identified October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) Task 2: Procure system to address risks identified. Knowledge of: 1. Project management functions and processes throughout the system life cycle. 2. Vendor pre-qualification (interviews and due diligence). 3. Procurement process. 7. End user training requirements October 2017 Dennis Shepp, CPP

“Procuring systems to address risks identified and describe project management functions and processes throughout the system life cycle. ” CHAPTER 2 OVERVIEW OF LIFE CYCLE PHASES, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 449) Stage 1: Project Feasibility. Stage 2: Project Development Stage 3: Project Execution Stage 4: Project Closeout



“Describe Installation and inspection techniques regarding integrations. ” CHAPTER 6 SELECTING CONTRACTORS, Patterson • Bidder Qualifications (examples provided) CHAPTER 8: COMMISSIONING AND WARRANTY, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 2757 -2760). • Commissioning is the process of ensuring that all systems and components are designed, installed, tested, and operated according to the operational requirements of the owner. • An all-inclusive process for all the planning, design, assembly, delivery, installation, and verification of a PPS.

• Commissioning should formalize the review and integration of all project expectations, during all the PPS phases, through inspection, functional performance testing, oversight of operator training, and detailed documentation. • Goals of commissioning are as follows: o Define and document requirements clearly at the outset of each phase and update through the process. o Verify and document compliance at the completion of each phase. o Establish and document commissioning tasks for subsequent-phase team members.

o Deliver PPSs that meet the customer’s needs at the time of completion. o Verify that alarm assessment and response procedures are completed. o Verify that operation and maintenance personnel are properly trained. o Verify PPS performance across its life cycle. • Key activities are as follows: o Establish goals for quality, efficiency, and functionality. o Establish a commissioning approach and scope. o Establish a commissioning budget. o Establish commissioning plans. o Establish commissioning schedules. o Develop commissioning specifications.

o Determine special testing needs. o Establish re-commissioning plans. o Document compliance and acceptance. • The commissioning plan sets out how the organization wants the new system to be installed and commissioned.

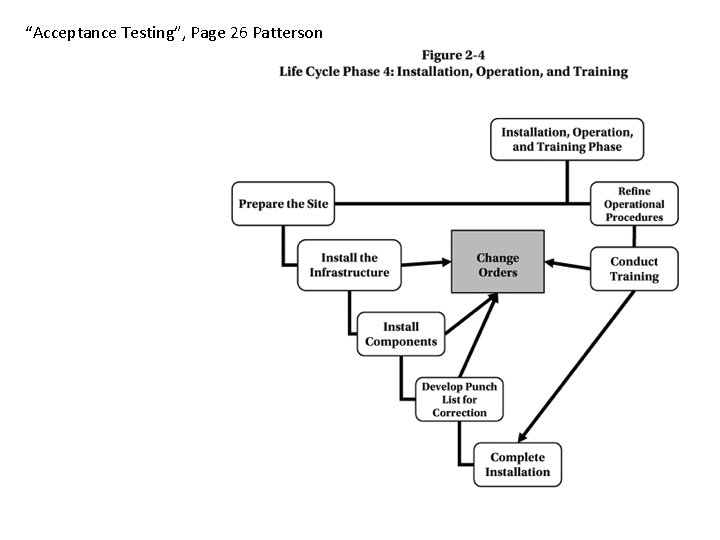
“Describe methods and process for commissioning and installation problem resolution (punchlists). ” CHAPTER 2: PPS Life Cycle Phase 4: Installation, Operation, and Training, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition • Punch list is a contract document used in the architecture and building trades to organize the completion of a construction project. • Commissioning is the process of ensuring that all systems and components of a system are designed, installed, tested, operated, and maintained according to the operational requirements of the owner. .

• PPS Life Cycle Phase 5: Commissioning and Warranty The tests performed by the implementation team may involve equipment, personnel, procedures, or any combination. Tests should simulate realistic conditions and provide conclusive evidence about the effectiveness of the security system. While a system is still under warranty, usually for one year, the installation contractor is expected to maintain the system free of charge. Figure 2 -5 shows key steps in the commissioning and warranty phase.

“Describe the systems configuration management and final acceptance testing criteria. ” 15. 4. 2 SITE ACCEPTANCE TESTING, Knoke. Physical Security Principles (Kindle Locations 11995 -11996) PAGE 507 For the security system acceptance tests, the following should be done: • verification that the data and video transmission system and any signal or control cabling have been installed, tested, and approved as specified • when the system includes remote control/ monitoring stations or remote switch panels, verification that the remote devices are functional, communicate with the security monitoring center, and perform all functions as specified

• verification that the video switcher is fully functional and that the switcher software has been programmed as needed for the site configuration • verification that all system software functions work correctly • operation of all electrical and mechanical controls and verification that the controls perform the designed functions • verification that all video sources and video outputs provide a full-bandwidth signal • verification that all input signals are terminated properly • verification that all cameras are aimed and focused properly

• verification that cameras facing the rising or setting sun are aimed sufficiently below the horizon that they do not view the sun directly • if vehicles are used near the assessment areas, verification of night assessment capabilities (including whether headlights cause blooming [loss of detail due to excessive bright spot] or picture degradation) • verification that all cameras are synchronized and that the picture does not roll when cameras are switched • verification that the alarm interface to the intrusion detection subsystem is functional and that automatic camera call-up is functional for all designated alarm points and cameras

• when pan/ tilt mounts are used in the system, verification that the limit stops have been set correctly, that all controls for pan/ tilt or zoom mechanisms are operative, and that the controls perform the desired function • if pre-position controls are used, verification that all home positions have been set correctly and have been tested for auto home function and correct home position

ASIS International Certificationrisks Exam Review “Procuring systems to address identified and DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) describe vendor pre-qualification (interviews and due diligence). CHAPTER 6 PROCUREMENT - SELECTING CONTRACTORS , Patterson, Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 1833 -1835). • Requires the same amount of effort as hiring a new employee. • Qualifications must be reviewed, references checked, and interviews held with the people who will perform the work. • Ensure that the personnel identified in proposals are the ones who will actually perform the work. October 2017 Dennis Shepp, CPP

• Ask for written employee guarantees from the contractor. • Once three or four qualified contractors have been identified, the proposal can be sent to them alone. • Be prepared to defend its selection of qualified contractors by using written selection criteria and documenting the results. • Reduce selection down to two or three vendors. • The project team interviews these contractors and asks about their experiences on other projects and how they plan to approach this project. • Interviews provide valuable insight into contractors’ understanding of the project and objectives, compatibility with company culture and personnel, and ability to complete the project successfully.

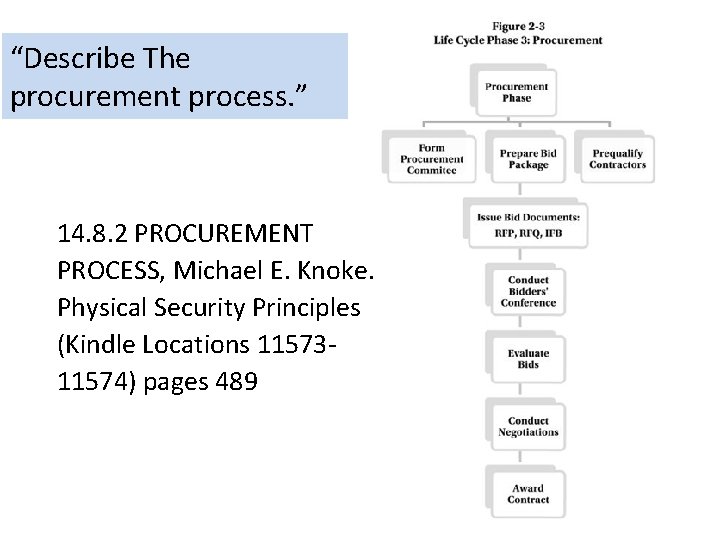
“Describe The procurement process. ” 14. 8. 2 PROCUREMENT PROCESS, Michael E. Knoke. Physical Security Principles (Kindle Locations 1157311574) pages 489

“Facilities Physical Security Guidelines” for information describing implementation of physical security measures and end user training requirements. 3. 6. 6 Maintenance – “Camera maintenance must be considered before system implementation. ” 3. 2. 1. 3. 2 Turnstiles – “In deploying circular turnstiles, it is important to remember that turnstiles added to a fence, it may provide a means for an intruder to climb over and enter the area. ” 3. 7. 2. 1 Organization – “Proprietary security offers more control over hiring, supervision and training. ” 3. 7. 2. 4 Training – “Security officers should be trained and tested on the following:

Officers who handle weapons require extensive and ongoing training.

“Implementing Physical Security Systems”, (Patterson) for information describing implementation of physical security measures and end user training requirements. CHAPTER 1: PHYSICAL PROTECTION SYSTEMS, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 187 -190) • Physical protection systems are systems that combine equipment, people, and procedures to protect assets against theft, destruction, sabotage, and other malevolent human acts. • A PPS may consist of a guard force, obstacles (like fences and locked doors), and electronic components (such as access control systems, intrusion detection systems, and closed-circuit television (CCTV) systems).

“Physical Security Principles” (ASIS International) for information describing implementation of physical security measures and end user training requirements. 15. 5 TRAINING, 15. 5. 1 GENERAL TRAINING REQUIREMENTS, Knoke. Physical Security Principles (Kindle Locations 12102 -12105) pages 511 -512 • Well-conceived, well-executed security training programs, personnel can be better prepared to prevent incidents from happening, respond properly to incidents that do arise, and contribute to recovery efforts more effectively. • Without appropriate training, personnel are more likely to contribute to security risks accidentally.

15. 5. 2 TRAINING TOPICS • System administration • System monitoring • Alarm system & dispatch • Incident response • System maintenance & troubleshooting • IT function • System overview

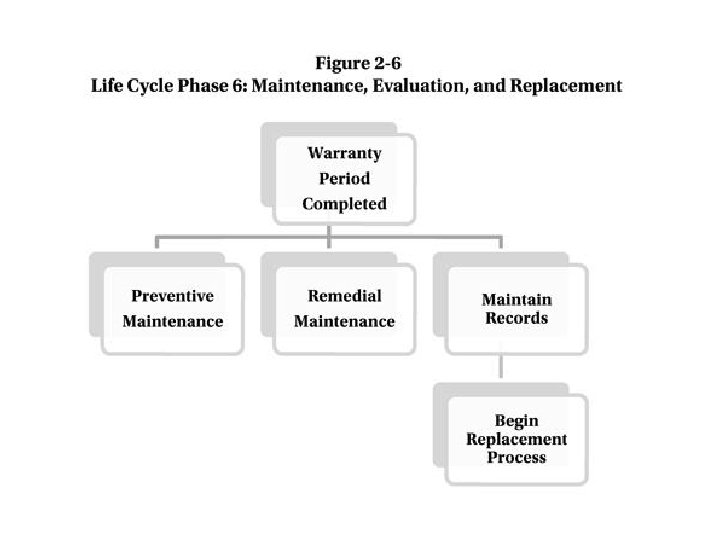
Task 4. 1. Implement procedures for ongoing monitoring and evaluation throughout the system life cycle describing maintenance inspection techniques. CHAPTER 16. 1 MAINTENANCE, PAGES 516 -523, Knoke. Physical Security Principles (Kindle Locations 1220912210) Pages 516 - 523 • Remedial Maintenance - This corrects faults and returns the system to operation in the event that a hardware or software component fails. • Preventive Maintenance - This consists of scheduled maintenance to keep the hardware and software in good operating condition.

CHAPTER 9: MAINTENANCE, EVALUATION & REPLACEMENT, Pages 178, 180, 191 Patterson, • Remedial Maintenance • Preventive Maintenance

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) TASK 4: Implement procedures for ongoing monitoring and evaluation throughout the system life cycle. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) TASK 4: Implement procedures for ongoing monitoring and evaluation throughout the system life cycle. Knowledge of: 1. 2. 3. 4. Maintenance inspection techniques Test and acceptance criteria Warranty types Ongoing maintenance, inspections, and upgrades 5. Ongoing training requirements 6. Systems disposal and replacement processes October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) TASK 5: Develop requirements for personnel involved in the support of the security program. October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) TASK 5: Develop requirements for personnel involved in the support of the security program. Knowledge of: 1. Roles, responsibilities and limitations of security personnel (including proprietary (in-house) and contract security staff) 2. Human resource management 3. Security personnel training, development and certification 4. General, post and special orders 5. Security personnel uniforms and equipment 6. Personnel performance review and improvement processes 7. Methods to provide security awareness training and education for non-security personnel October 2017 Dennis Shepp, CPP

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) • ALL groups have 30 – minutes to complete the research and complete the report. • Report in Power. Point or using flipcharts • All presentations must identify the name of the resource, chapter number and page location of the information EXAMPLE: (ASIS Int’l Facilities Physical Security Measures Guideline, Chap. 3. 4. 1 Security Lighting Applications, Page 23 – 25) October 2017 Dennis Shepp, CPP

Task 4. 2 & 4. 3. Implement procedures for ongoing monitoring and evaluation throughout the system life cycle describing test and acceptance criteria as well as the warranty types. CHAPTER 8: PPS TESTING, Patterson, Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 2809 -2810), page 164 • Ideal testing stresses the established limits sitespecific threats. • Simulate actual threat conditions and provide conclusive evidence that the security system will counter each threat scenario.

CHAPTER 2: OUTPUTS OR DELIVERABLES, “Commissioning and Warranty Phase”, Patterson, Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 590 -597), page 170 • Factory acceptance test plan • Site acceptance test plan • Pre-delivery or factory acceptance test data • Site acceptance test data • Factory acceptance tests punch list • Site acceptance tests punch list • Reliability or availability test data and punch list • After-acceptance test data • Warranty plan • Warranty reports

CHAPTER 2: OUTPUTS OR DELIVERABLES, “Commissioning and Warranty Phase”, Patterson, Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 590 -597), page 170 • Warranty records • Upgrades


Task 4. 4 & 4. 5. Implement procedures for ongoing monitoring and evaluation throughout the system life cycle describing ongoing maintenance, inspections, upgrades and training requirements. CHAPTER 2: OVERVIEW OF LIFE CYCLE PHASES, Patterson, page 25 -28 • A physical protection system (PPS) has a life cycle that includes six phases: 1. Planning 2. Design and estimation 3. Procurement 4. Installation, operation, and training 5. Testing and warranty 6. Maintenance, evaluation, and replacement

Task 4. 6: Implement procedures for ongoing monitoring and evaluation throughout the system life cycle describing systems disposal and replacement processes. “CHAPTER 2: PPS Life Cycle Phase 6: Maintenance, Evaluation, and Replacement ”, page 191 Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 547 -551). • Warranty completed organization must assume maintenance of the PPS. • Sometimes an organization will train its own personnel to maintain the PPS. • Other times, the organization will have the supplying contractor continue to perform maintenance. • Option is to solicit bids for the maintenance work.

• When system completes its useful life the process of replacement will begin. • To justify the replacement cost, factors such as the cost of maintenance, lack of spare parts, obsoleteness of hardware and software, operating costs, unreliability, and other negative aspects should be considered. • Replacement may also be justified by new technologies and features that provide improved security, the ability to reduce manpower, or other benefits.

“Acceptance Testing”, Page 26 Patterson


Task 5. 1. Develop requirements for personnel involved in the support of the security program describing the roles, responsibilities and limitations of security personnel (including proprietary (in-house) and contract security staff). 12. 5 SECURITY OFFICER FUNCTIONS, Knoke, • Access control and movement of pedestrian and vehicular traffic • Patrol of buildings and perimeters • Inspection of security and fire exposures • Monitoring of assets from a central control facility • Emergency response • Traffic control • Dealing with disturbed persons • Escort materials or persons • Special assignments

• Because the vast majority of private security officers are not law enforcement officers, observing and reporting are key responsibilities of most patrol officers. • Security officers are often the first responders to an emergency scene and must be capable of directing, coordinating, and carrying out the responses established by security management. • Administer first aid, evacuation, rescue, searches, dangerous weapons. • Often fill vital roles in support of an organization or client. • Include public relations or management representative, intelligence agent, enforcement or compliance agent, legal consultant, and physical security or crime prevention specialist.

• Security officer is most times first person visitor meets at organization – first impressions of organization. • Help form and maintain good relationships with other functional areas within the organizations. • Arming security officers - must consider regulations, increased liability, and the increased costs associated with training, insurance, and regulatory compliance. • Organizations that employ or provide security officers on a contract basis should maintain a use-of-force policy and incorporate the policy into the security officer training program. • Essential for minimizing injuries to officers and others, as well as mitigating liability. REVIEW THE SECTIONS RELATING TO ARMED SECURITY

Task 5. 2. Develop requirements for personnel involved in the support of the security program and describe the human resource management components. 12. 8 SECURITY OFFICER SELECTION Knoke. Physical Security Principles (Kindle Location 9638). Pages 421 -429 • Essential to establish minimum standards for hiring and training. • NOTE: Figure 12 -2 Page 399 Employment Screening 12. 8. 1 ASIS GUIDELINE PSO-2010 Private Security Officer Selection & Training Guideline. • Security officers regulated in most jurisdictions. • Essential personal attributes (good character • good customer service skills • neat appearance • knowledge of the job • education • ethics)

• Benefits of training (improved job performance – ease of supervision – reduced turnover – legal protection) • Identifying training requirements is provided by – regulations – guidelines – job requirements - best practises 12. 10 MANAGING THE SECURITY OFFICER FORCE, Knoke. Physical Security Principles (Kindle Location 10123). 12. 10. 4 Supervision • The number and layers of supervision at a facility is influenced by numerous factors, including facility size, hours, and geographic location of posts • Supervisors - special training in management, leadership, human relations, interpersonal communication skills, labor and criminal laws, emergency response, and other issues.

Task 5. 3. Develop requirements for personnel involved in the support of the security program and describe the security personnel training requirements, development and certification. 12. 9 SECURITY OFFICER TRAINING Knoke. Physical Security Principles (Kindle Location 9716). Pages 402 -420 • Key concepts (Learning – cognitive learning (amount of material that is learned and theory relating to the material) – affective learning (Training of this type includes understanding various cultures, dealing with disabled persons, practicing safety compliance, and exploring the methods used by adversaries to acquire information) – psychomotor learning (The physical or hands-on aspect of learning falls under the psychomotor domain)

• Retention, or the amount of learning that remains with the learner over a period of time, requires reiteration. • Socialization includes the process by which an employee learns and adopts workplace values. • Training is a major part of formal socialization - occupational or professional socialization. • Supervision is another key aspect – send single coherent messages to employees. • Education + Training + Guided Experience = Development • Difference between training – education!

• Benefits of training (inproved job performance – ease of supervision – reduced turnover – legal protection) • Identifying training requirements is provided by – regulations – guidelines – job requirements - best practises 12. 9. 7 TRAINING STRATEGIES Michael E. Knoke. Physical Security Principles (Kindle Locations 10040 -10041). • Online – off duty – recognition programs • CPO - CSSM (IFPO) – CPP – PSP – PCI (ASIS)

Task 5. 4 & 5. 5. Develop requirements for personnel involved in the support of the security program and describe the general, post and special orders as well as uniforms and equipment for security personnel. 12. 10. 1 PERSONNEL REQUIREMENTS, Knoke. Physical Security Principles (Kindle Locations 10131 -10132), page 386 • Post orders are based on standard operating procedures (SOPs), which should be site-specific. • SOPs are compendiums of procedures for the security group to follow in day-to-day operations. • They may also include emergency response procedures. • A security officer post is any location or combination of activities for which a trained human being is necessary.

• Post orders are the single most important instructions for the security force. • Post orders • express the policies of the protected enterprise, • summarize required officer duties, • avoid the problems of word-of-mouth instructions, and • provide a basis for site-specific training. • Developing post orders – Each order deals with single subject – Brief – Simply written – Indexed – Available (each post) – Team effort to develop – May address special events

12. 7 Uniforms and Equipment, Knoke. Physical Security Principles (Kindle Location 9567). Page 349 • Many government agencies that regulate the private security industry also have specific requirements for uniforms and equipment. • Uniforms & equipment: o Uniforms, communication devices, safety equipment, ID badges, keys, weapons & restraints, vehicles

Task 5. 6 & 5. 7. Develop requirements for personnel involved in the support of the security program and describe the personnel performance review and improvement processes and methods to provide security awareness training and education for non-security personnel. Chapter 2, Functions of Physical Security, Michael E. Knoke. Physical Security Principles • A truly comprehensive asset protection strategy should include security awareness training that extends to personnel in all departments, regardless of whether an organization has proprietary, contract, or hybrid security operations, or none at all.

11. 6 Trends and Issues, Michael E. Knoke. Physical Security Principles (Kindle Locations 9166 -9168). ASIS International. Kindle Edition. • E-learning training tools - training software in a state of continued improvement. • Tools for users of legacy & new control systems. • This is accomplished using case-specific training. • Ability to author, publish, and manage enterprise-wide, repeatable training and site-specific security awareness programs. • Reduces costs associated with operator & administration training. • Enhances compliance training for regulated industries.

12. 6. 1 Security Officers as Public Relations Agents, Michael E. Knoke. Physical Security Principles (Kindle Locations 10369 -10370), page 392 • Protection officers act as agents of management when they assume a public relations role in dealing with visitors, customers, tenants, and vendors. • Security personnel must be well versed in corporate expectations and culture. • Equipped with this knowledge, protection officers can become adjunct members of the management team. • Security officers are often the first contact a visitor, customer, vendor, or employee has with an organization.

• The way they deal with people has a marked effect on the initial impression made by the organization. • Security officers can also help form and maintain good relationships between the security department (in-house or contract) and others in the organization. • By being involved in a security awareness program, officers can have a positive impact in encouraging employees to report or decrease security risks. • Well-trained officers who are courteous, act with restraint, and use good judgment can often overcome any people who may be antagonistic. • Cost-effective & practical ideas to increase organizationwide security awareness include incorporating training into new-hire orientations, special luncheons, or regular business meetings.

• Organizations should also explore the many excellent and free online security awareness training options, such as the Nationwide SAR (Suspicious Activity Reporting) Initiative training programs and the many courses offered by government.

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) PRACTICE QUESTIONS October 2017 Dennis Shepp, CPP

Which of the following statements is TRUE concerning managing the bid process? a. Finding qualified bidders through the use of a questionnaire to find credible and competent vendors. b. Finding qualified bidders is NOT recommended through using questionnaires. c. Every bid should be awarded to the lowest priced proposal because saving money is the most important consideration. d. Security professionals should ONLY rely on potential vendors that are referred by colleagues.

Which of the following statements is TRUE concerning managing the bid process? a. Finding qualified bidders through the use of a questionnaire to find credible and competent vendors. b. Finding qualified bidders is NOT recommended through using questionnaires. c. Every bid should be awarded to the lowest priced proposal because saving money is the most important consideration. d. Security professionals should ONLY rely on potential vendors that are referred by colleagues. Michael E. Knoke. Physical Security Principles (Kindle Location 10549). ASIS International. Kindle Edition.

The complete set of procurement (bid) documents consist of three (3) sections, they are: a. Contractual details, bid package and construction specifications. b. Contractual details, construction specifications and construction drawings. c. Proposal details, bid package and construction specifications. d. Proposal details, bid details and construction drawings

The complete set of procurement (bid) documents consist of three (3) sections, they are: a. Contractual details, bid package and construction specifications. b. Contractual details, construction specifications and construction drawings. c. Proposal details, bid package and construction specifications. d. Proposal details, bid details and construction drawings Michael E. Knoke. Physical Security Principles (Kindle Location 10817). ASIS International. Kindle Edition.

This type of procurement is the most common method and based on a detailed design and construction documents and specifications. Certain vendors may be invited or it may be open to a list of prequalified vendors. The selection is not based on lowest bid and technical proposals are sought. This is referred to as: a. Sole source procurement b. Invitation for bid c. Request for proposal d. Open proposal bid

This type of procurement is the most common method and based on a detailed design and construction documents and specifications. Certain vendors may be invited or it may be open to a list of prequalified vendors. The selection is not based on lowest bid and technical proposals are sought. This is referred to as: a. Sole source procurement b. Invitation for bid c. Request for proposal d. Open proposal bid Michael E. Knoke. Physical Security Principles (Kindle Location 11567). ASIS International. Kindle Edition.

The performance measurement of a project’s progress to specific point-in-time or the sum of the cumulative budgeted cost of a project compared to the actual cost of all work completed at a specific point in the schedule, is referred to as: a. Project management b. Work breakdown structure c. Task and resource performance metric d. Earned value

The performance measurement of a project’s progress to specific point-in-time or the sum of the cumulative budgeted cost of a project compared to the actual cost of all work completed at a specific point in the schedule, is referred to as: a. Project management b. Work breakdown structure c. Task and resource performance metric d. Earned value Michael E. Knoke. Physical Security Principles (Kindle Location 2067). ASIS International. Kindle Edition.

Project management involves: a. Planning, organizing and supervising resources on a project b. Planning, organizing and controlling resources on a project c. Managing, organizing and controlling resources on a project d. Managing, organizing and supervising resources on a project

Project management involves: a. Planning, organizing and supervising resources on a project b. Planning, organizing and controlling resources on a project c. Managing, organizing and controlling resources on a project d. Managing, organizing and supervising resources on a project Michael E. Knoke. Physical Security Principles (Kindle Locations 10439 -10440). ASIS International. Kindle Edition.

Which of the following is the BEST definition for “scope creep”? a. Approved documented changes in a project plan that change the original project plan. b. Adjustments made to a RFP and IFP to change the specifications in the design. c. Undocumented changes in a project that can impact resources, tasks, timelines and budgets. d. Changes made to personnel training requirements without advising security management.

Which of the following is the BEST definition for “scope creep”? a. Approved documented changes in a project plan that change the original project plan. b. Adjustments made to a RFP and IFP to change the specifications in the design. c. Undocumented changes in a project that can impact resources, tasks, timelines and budgets. d. Changes made to personnel training requirements without advising security management. Michael E. Knoke. Physical Security Principles (Kindle Location 1363). ASIS International. Kindle Edition.

A contract document used in the architecture and building trades to organize the completion of a construction project, is called a: a. Commissioning Checklist b. Punch List c. Project Plan d. Completion Checklist

A contract document used in the architecture and building trades to organize the completion of a construction project, is called a: a. Commissioning Checklist b. Punch List c. Project Plan d. Completion Checklist Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 533 -534). ASIS International. Kindle Edition.

Which of the following is part of the Installation, Operation and Training Phase of a systems installation? a. Develop system specifications b. Acceptance test results c. Determine procurement method d. Contract evaluation criteria

Which of the following is part of the Installation, Operation and Training Phase of a systems installation? a. Develop system specifications b. Acceptance test results c. Determine procurement method d. Contract evaluation criteria Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 585). ASIS International. Kindle Edition.

Pre-delivery or factory acceptance test data is collected in which phase of the system implementation? a. Design and estimation b. Procurement c. Installation, operation and training d. Commissioning and warranty

Pre-delivery or factory acceptance test data is collected in which phase of the system implementation? a. Design and estimation b. Procurement c. Installation, operation and training d. Commissioning and warranty Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 592). ASIS International. Kindle Edition.

In a PPS implementation phase, the system objectives, functional requirements, operational improvements and economic justification are part of which phase? a. Planning b. Design and estimation c. Procurement d. Installation, operation and training

In a PPS implementation phase, the system objectives, functional requirements, operational improvements and economic justification are part of which phase? a. Planning b. Design and estimation c. Procurement d. Installation, operation and training Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 604). ASIS International. Kindle Edition.

When working with metrics, the acronym SMART is used. SMART stands for: a. Specific; Measureable; Accountable; Relevant; Time-dependent b. Specific; Measurable; Attainable; Repeatable; Time-dependent c. Specific; Measurable; Attainable; Relevant; Time-dependent d. Specific; Measurable; Accountable; Repeatable; Time-dependent

When working with metrics, the acronym SMART is used. SMART stands for: a. Specific; Measureable; Accountable; Relevant; Time-dependent b. Specific; Measurable; Attainable; Repeatable; Time-dependent c. Specific; Measurable; Attainable; Relevant; Time-dependent d. Specific; Measurable; Accountable; Repeatable; Time-dependent Michael E. Knoke. Physical Security Principles (Kindle Location 1799). ASIS International. Kindle Edition.

Organizations use three (3) common types of procurement actions: request for proposals, invitation for bids and which of the following? a. Multi source b. Sole source c. Single bid d. Open source

Organizations use three (3) common types of procurement actions: request for proposals, invitation for bids and which of the following? a. Multi source b. Sole source c. Single bid d. Open source Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 526 -527).

In the life cycle phase concerning maintenance, evaluation and replacement of PPS components or systems, which of the following is a key step in the phase? a. Design specification b. Manufacturer's specification c. Preventive maintenance d. Customer specification

In the life cycle phase concerning maintenance, evaluation and replacement of PPS components or systems, which of the following is a key step in the phase? a. Design specification b. Manufacturer's specification c. Preventive maintenance d. Customer specification Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 552 -554).

When comparing the project stage correlation to the Life Cycle Phase, which of the following, BEST correlates to the Life Cycle Phase 3 – “Procurement” Phase? a. Feasibility Stage b. Development Stage c. Execution Stage d. Closeout Stage

When comparing the project stage correlation to the Life Cycle Phase, which of the following, BEST correlates to the Life Cycle Phase 3 – “Procurement” Phase? a. Feasibility Stage b. Development Stage c. Execution Stage d. Closeout Stage Figure 3 -1, Project Stage/Life Cycle Phase Correlation, Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition

Which of the following definitions BEST describes “Work Breakdown Structure”? a. It determines the schedule or timeline showing the milestones and tasks to be completed. b. It calculates the earned value of completed tasks as compared to the timeline. c. It determines the activities to be executed for the entire project to be completed. d. It measures the progress of the project and costs assigned to each task.

Which of the following definitions BEST describes “Work Breakdown Structure”? a. It determines the schedule or timeline showing the milestones and tasks to be completed. b. It calculates the earned value of completed tasks as compared to the timeline. c. It determines the activities to be executed for the entire project to be completed. d. It measures the progress of the project and costs assigned to each task. Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Location 734)

“A detailed examination including risk assessment, vulnerability evaluation, cost-benefit analysis, and risk management alternatives, all performed to understand the nature of unwanted consequences. ” This BEST defines which of the following? a. Risk assessment b. Security survey c. Risk analysis d. Risk Management

“A detailed examination including risk assessment, vulnerability evaluation, cost-benefit analysis, and risk management alternatives, all performed to understand the nature of unwanted consequences. ” This BEST defines which of the following? a. Risk assessment b. Security survey c. Risk analysis d. Risk Management Patterson, David G. . Implementing Physical Protection Systems: A Practical Guide, 2 nd Edition (Kindle Locations 967 -968)

“A particularly relevant form of risk assessment is the physical security assessment. It focuses on two things: the risks to the physical assets and property of an organization, and the protection measures (against any risk) that comprise the realm of physical security. ” This is also called: a. Threat assessment b. Security survey c. Loss event profile d. Threat risk analysis

“A particularly relevant form of risk assessment is the physical security assessment. It focuses on two things: the risks to the physical assets and property of an organization, and the protection measures (against any risk) that comprise the realm of physical security. ” This is also called: a. Threat assessment b. Security survey c. Loss event profile d. Threat risk analysis Michael E. Knoke. Physical Security Principles

Security surveys are usually concerned with measuring at least three basic factors, which of the following BEST describes those factors? a. Quality, reliability and cost b. Threats, assets and people c. Quality, prevention and cost d. Threats, risks and property

Security surveys are usually concerned with measuring at least three basic factors, which of the following BEST describes those factors? a. Quality, reliability and cost b. Threats, assets and people c. Quality, prevention and cost d. Threats, risks and property Michael E. Knoke. Physical Security Principles (Kindle Locations 13751376).

The most common and reliable tool for determining adequacy and foreseeability is which of the following? a. The risk assessment b. The risk analysis c. The security survey d. The threat assessment

The most common and reliable tool for determining adequacy and foreseeability is which of the following? a. The risk assessment b. The risk analysis c. The security survey d. The threat assessment Michael E. Knoke. Physical Security Principles (Kindle Locations 13831384)

A comprehensive risk assessment focuses equally on assets, threats, vulnerabilities, and consequences, a security survey places more emphasis on which of the following? a. Vulnerabilities b. Threats c. Assets d. People

A comprehensive risk assessment focuses equally on assets, threats, vulnerabilities, and consequences, a security survey places more emphasis on which of the following? a. Vulnerabilities b. Threats c. Assets d. People Michael E. Knoke. Physical Security Principles (Kindle Locations 1403 -1404)

The Security Metrics Evaluation Tool (MET) helps security professionals evaluate any metric according to a criteria, which includes Operational (Security) Criteria. Which of the following is part of that criteria? a. Reliability, validity, generalizability b. Cost, timeliness, manipulation c. Return on investment, organizational relevance, communication d. Effectiveness, efficiency, strategic improvement

The Security Metrics Evaluation Tool (MET) helps security professionals evaluate any metric according to a criteria, which includes Operational (Security) Criteria. Which of the following is part of that criteria? a. Reliability, validity, generalizability b. Cost, timeliness, manipulation c. Return on investment, organizational relevance, communication d. Effectiveness, efficiency, strategic improvement Michael E. Knoke. Physical Security Principles (Kindle Location 1757).

Generally, a high-rise structure is considered to be one that extends higher than the maximum reach of available firefighting equipment. What is considered the effective height? a. Between 20 ft. (6 m) and 30 ft. (9 m) or 3 - 5 floors. b. Between 50 ft. (15 m) and 70 ft. (20 m) or 4 – 5 floors. c. Between 50 ft. (15 m) and 100 ft. (30 m) or 5 – 8 floors. d. Between 75 ft. (23 m) and 100 ft. (30 m) or 7 – 10 floors.

Generally, a high-rise structure is considered to be one that extends higher than the maximum reach of available firefighting equipment. What is considered the effective height? a. Between 20 ft. (6 m) and 30 ft. (9 m) or 3 - 5 floors. b. Between 50 ft. (15 m) and 70 ft. (20 m) or 4 – 5 floors. c. Between 50 ft. (15 m) and 100 ft. (30 m) or 5 – 8 floors. d. Between 75 ft. (23 m) and 100 ft. (30 m) or 7 – 10 floors. Michael E. Knoke. Physical Security Principles (Kindle Locations 12539 -12541)

Which one of the following lamps has the BEST color rendition index? a. High Pressure Sodium b. LED c. Metal Halide d. Halogen

Which one of the following lamps has the BEST color rendition index? a. High Pressure Sodium b. LED c. Metal Halide d. Halogen Figure 9 -24 Chapter 9. 4. 3 Characteristics of Lights and Lighting; Michael E. Knoke. Physical Security Principles (Kindle Location 4492).

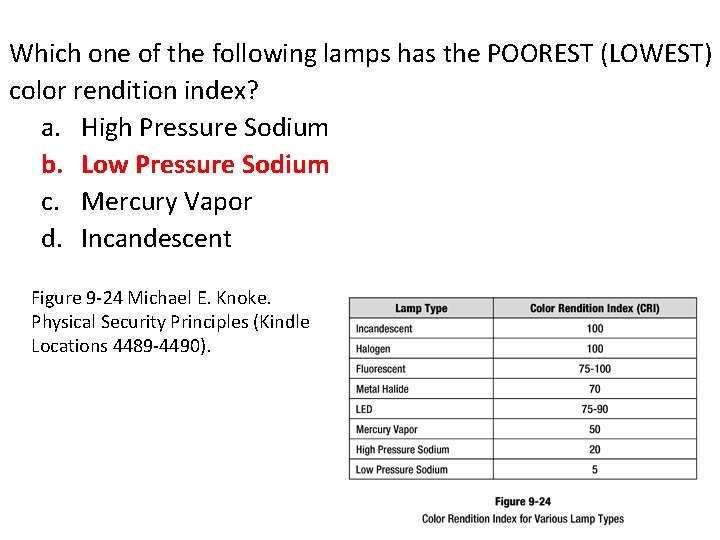
Which one of the following lamps has the POOREST (LOWEST) color rendition index? a. High Pressure Sodium b. Low Pressure Sodium c. Mercury Vapor d. Incandescent

Which one of the following lamps has the POOREST (LOWEST) color rendition index? a. High Pressure Sodium b. Low Pressure Sodium c. Mercury Vapor d. Incandescent Figure 9 -24 Michael E. Knoke. Physical Security Principles (Kindle Locations 4489 -4490).

The ability of a lamp to discriminate, grade, and faithfully reproduce the colors seen in an object is known as color rendition and is measured as a color rendition index (CRI) on a scale. What CRI is considered “Good”? a. A CRI of 30 to 40. b. A CRI of 50 to 60. c. A CRI of 70 to 80. d. A CRI of 80 or 100.

The ability of a lamp to discriminate, grade, and faithfully reproduce the colors seen in an object is known as color rendition and is measured as a color rendition index (CRI) on a scale. What CRI is considered “Good”? a. A CRI of 30 to 40. b. A CRI of 50 to 60. c. A CRI of 70 to 80. d. A CRI of 80 or 100. Michael E. Knoke. Physical Security Principles (Kindle Locations 44894490).

In a mechanical cylinder lock mechanism, instead of grooves at the bottom of the plug, a side bar is moved into a cutout housing in the shell or withdrawn into grooves in the pins. The keys are specially cut at specific angles, making routine duplication of keys quite difficult, except on special equipment used by the manufacturer. This mechanism is BEST described as a: a. Conventional security cylinder b. Medeco high-security cylinder c. Warded lock mechanism d. Lever lock mechanism

In a mechanical cylinder lock mechanism, instead of grooves at the bottom of the plug, a side bar is moved into a cutout housing in the shell or withdrawn into grooves in the pins. The keys are specially cut at specific angles, making routine duplication of keys quite difficult, except on special equipment used by the manufacturer. This mechanism is BEST described as a: a. Conventional security cylinder b. Medeco high-security cylinder c. Warded lock mechanism d. Lever lock mechanism Michael E. Knoke. Physical Security Principles (Kindle Locations 4077 -4079).

A locking mechanism that will unlock under any failure condition, such as loss of power, failure of the mechanism itself and any connected control device is referred to as which of the following types of locks? a. Fail safe b. Fail secure c. Emergency d. System safe

A locking mechanism that will unlock under any failure condition, such as loss of power, failure of the mechanism itself and any connected control device is referred to as which of the following types of locks? a. Fail safe b. Fail secure c. Emergency d. System safe Michael E. Knoke. Physical Security Principles (Kindle Locations 4152 -4153).

ASIS International Certification Exam Review DOMAIN 3: IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) 3 DOMAIN October 2017 IMPLEMENTATION OF PHYSICAL SECURITY MEASURES (32%) October 2017 Dennis Shepp, CPP