Physical Personnel Security Physical Security Personnel Security Acknowledgments

























- Slides: 47

Physical & Personnel Security Physical Security Personnel Security

Acknowledgments Material is from: n CISA® Review Manual 2009, © 2008, ISACA. All rights reserved. Used by permission. n CISM® Review Manual 2009, © 2008, ISACA. All rights reserved. Used by permission. Author: Susan J Lincke, Ph. D Univ. of Wisconsin-Parkside Reviewers: Funded by National Science Foundation (NSF) Course, Curriculum and Laboratory Improvement (CCLI) grant 0837574: Information Security: Audit, Case Study, and Service Learning. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and/or source(s) and do not necessarily reflect the views of the National Science Foundation. CISA Review Manual 2009

Remember Data Criticality Classification? Critical $$$$: Cannot be performed manually. Tolerance to interruption is very low Vital $$: Can be performed manually for very short time Sensitive $: Can be performed manually for a period of time, but may cost more in staff Nonsensitive ¢: Can be performed manually for an extended period of time with little additional cost and minimal recovery effort CISA Review Manual 2009

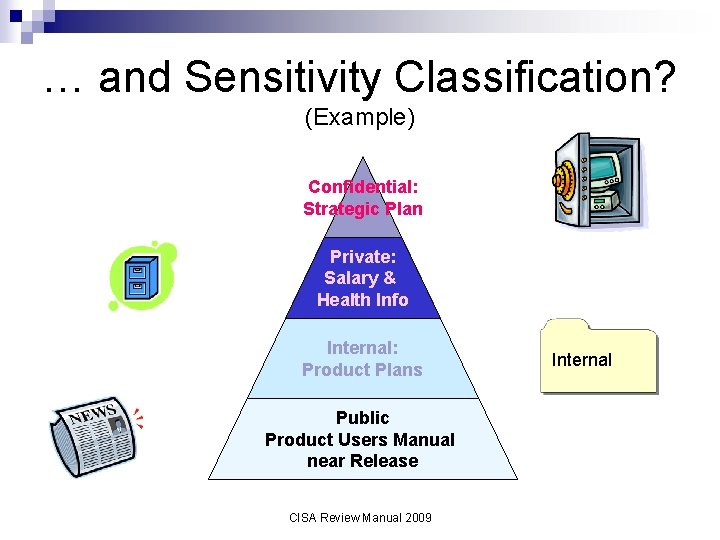
… and Sensitivity Classification? (Example) Confidential: Strategic Plan Private: Salary & Health Info Internal: Product Plans Public Product Users Manual near Release CISA Review Manual 2009 Internal

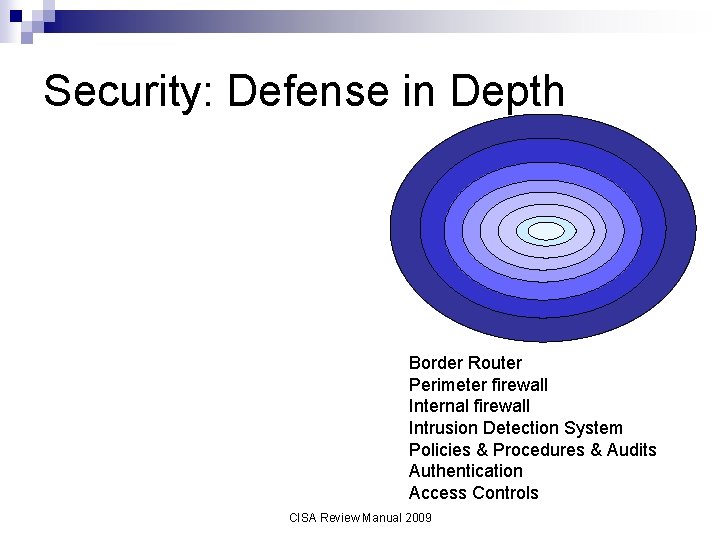
Security: Defense in Depth Border Router Perimeter firewall Internal firewall Intrusion Detection System Policies & Procedures & Audits Authentication Access Controls CISA Review Manual 2009

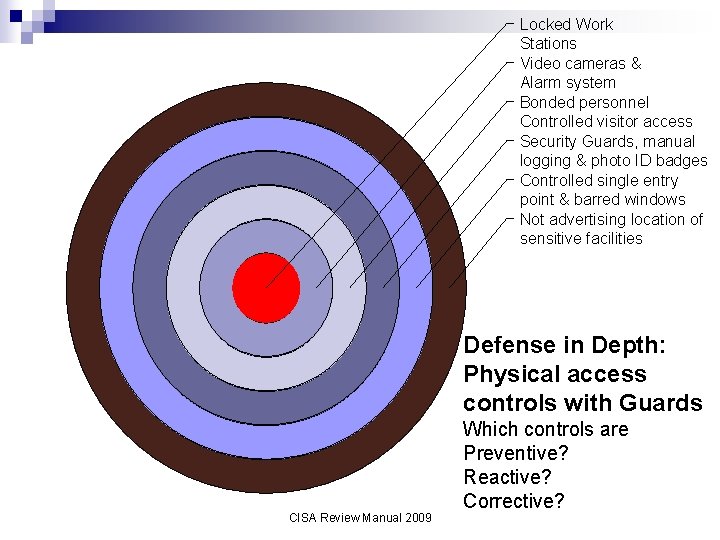
Locked Work Stations Video cameras & Alarm system Bonded personnel Controlled visitor access Security Guards, manual logging & photo ID badges Controlled single entry point & barred windows Not advertising location of sensitive facilities Defense in Depth: Physical access controls with Guards CISA Review Manual 2009 Which controls are Preventive? Reactive? Corrective?

Physical Issues and Controls Mobile Computing Power Protection Fire Suppression Door Locks & Security IPF Environment CISA Review Manual 2009

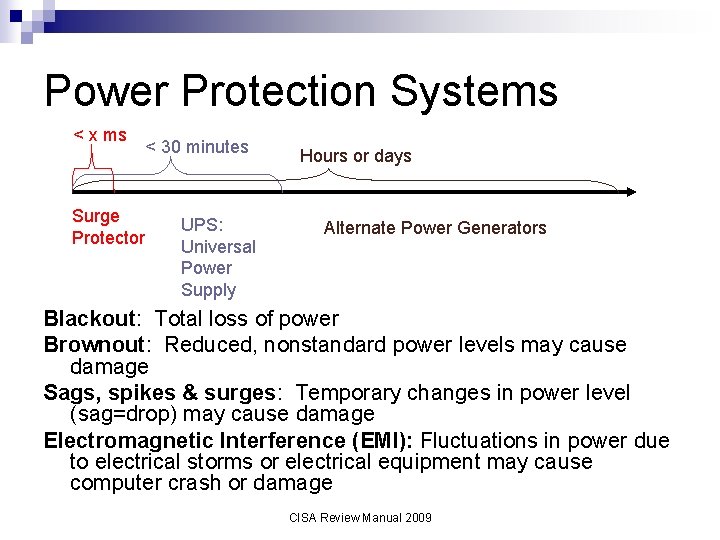
Power Protection Systems < x ms Surge Protector < 30 minutes UPS: Universal Power Supply Hours or days Alternate Power Generators Blackout: Total loss of power Brownout: Reduced, nonstandard power levels may cause damage Sags, spikes & surges: Temporary changes in power level (sag=drop) may cause damage Electromagnetic Interference (EMI): Fluctuations in power due to electrical storms or electrical equipment may cause computer crash or damage CISA Review Manual 2009

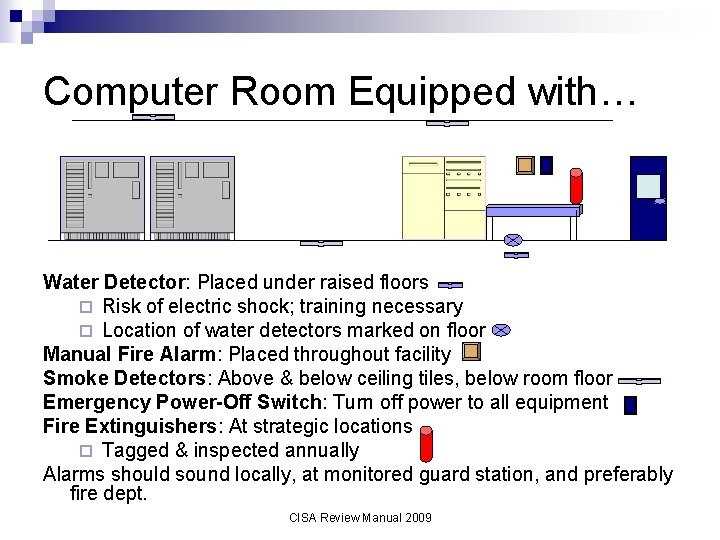
Computer Room Equipped with… Water Detector: Placed under raised floors ¨ Risk of electric shock; training necessary ¨ Location of water detectors marked on floor Manual Fire Alarm: Placed throughout facility Smoke Detectors: Above & below ceiling tiles, below room floor Emergency Power-Off Switch: Turn off power to all equipment Fire Extinguishers: At strategic locations ¨ Tagged & inspected annually Alarms should sound locally, at monitored guard station, and preferably fire dept. CISA Review Manual 2009

IPF Environment n n n Computer room on middle floor Fire department inspects room annually Fire-resistant walls, floor, ceiling, furniture, electrical panel & conduit ¨ Two-hour fire resistance rating for walls Emergency Power-off switch: Panel in and outside room n Redundant power lines reduce risk of environmental hazards n Surge protectors & UPS n No smoking, food or water in IPF Audit: Observe some, request documentation, may test batteries, handheld fire extinguishers, ensure fire suppression system is to code n CISA Review Manual 2009

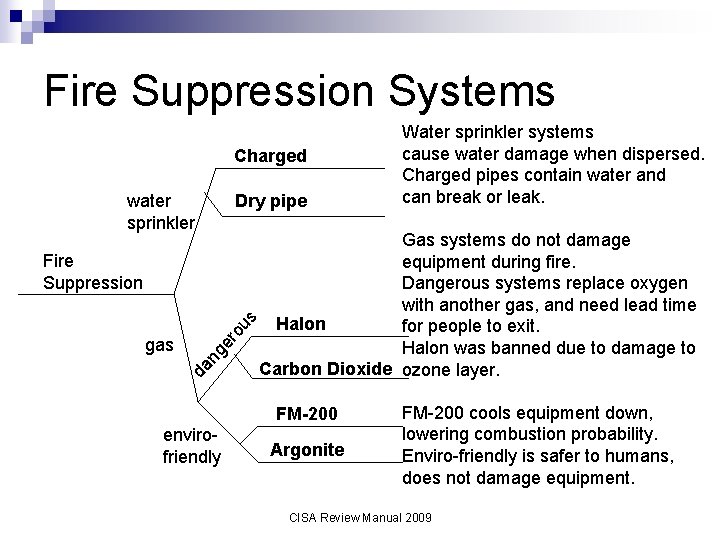
Fire Suppression Systems Charged water sprinkler Dry pipe er ng da gas ou s Fire Suppression Gas systems do not damage equipment during fire. Dangerous systems replace oxygen with another gas, and need lead time Halon for people to exit. Halon was banned due to damage to Carbon Dioxide ozone layer. FM-200 envirofriendly Water sprinkler systems cause water damage when dispersed. Charged pipes contain water and can break or leak. Argonite FM-200 cools equipment down, lowering combustion probability. Enviro-friendly is safer to humans, does not damage equipment. CISA Review Manual 2009

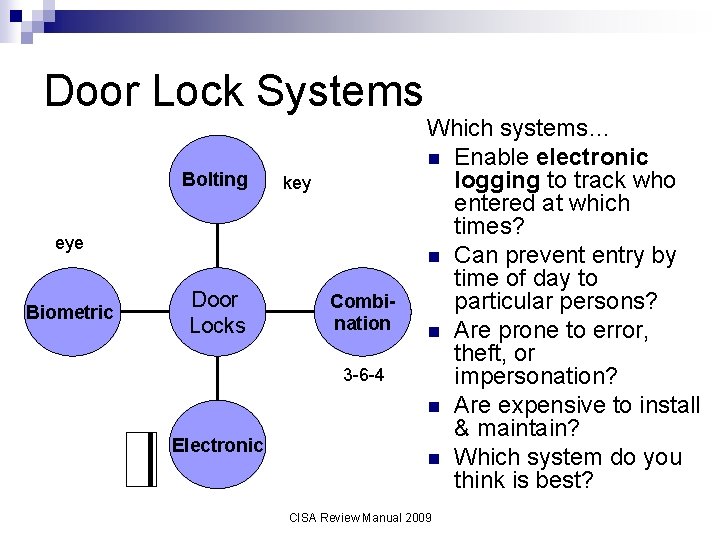
Door Lock Systems Bolting key eye Biometric Door Locks Combination 3 -6 -4 Electronic Which systems… n Enable electronic logging to track who entered at which times? n Can prevent entry by time of day to particular persons? n Are prone to error, theft, or impersonation? n Are expensive to install & maintain? n Which system do you think is best? CISA Review Manual 2009

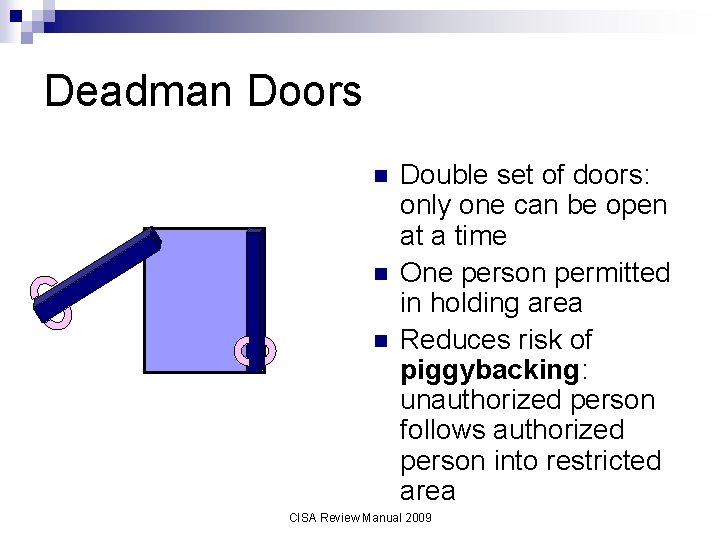
Deadman Doors n n n Double set of doors: only one can be open at a time One person permitted in holding area Reduces risk of piggybacking: unauthorized person follows authorized person into restricted area CISA Review Manual 2009

Computers in Public Places Logical Protections n Imaged computers ¨ n Antivirus / antispyware ¨ n Avoid pornography, violence, adult content Login/passwords ¨ n Protects users from each other Web filters ¨ n No client storage for programs and/or data If privileged clientele allowed Firewall protection from rest of organization Physical Locks

Mobile Computing n n n Engrave a serial number and company name/logo on laptop using engraver or tamper-resistant tags Back up critical/sensitive data Use cable locking system Encrypt sensitive files Allocate passwords to individual files ¨ n Consider if password forgotten or person leaves company…? Establish a theft response team for when a laptop is stolen. Report loss of laptop to police ¨ Determine effect of lost or compromised data on company, clients, third parties ¨ CISA Review Manual 2009

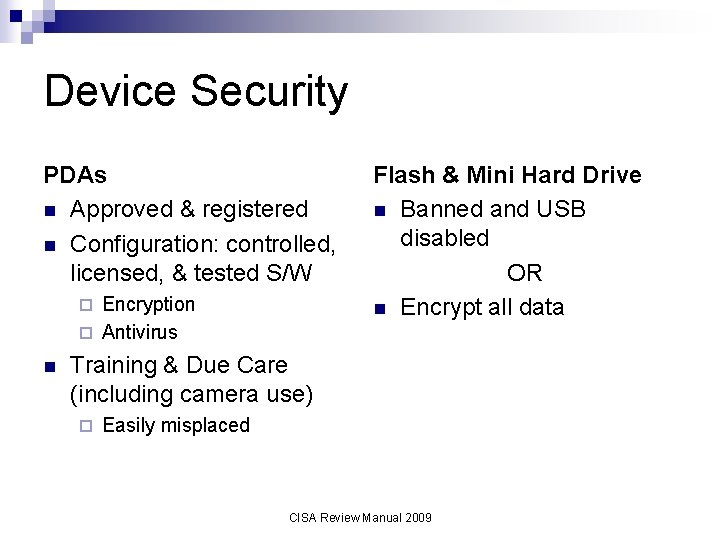
Device Security PDAs n Approved & registered n Configuration: controlled, licensed, & tested S/W Encryption ¨ Antivirus ¨ n Flash & Mini Hard Drive n Banned and USB disabled OR n Encrypt all data Training & Due Care (including camera use) ¨ Easily misplaced CISA Review Manual 2009

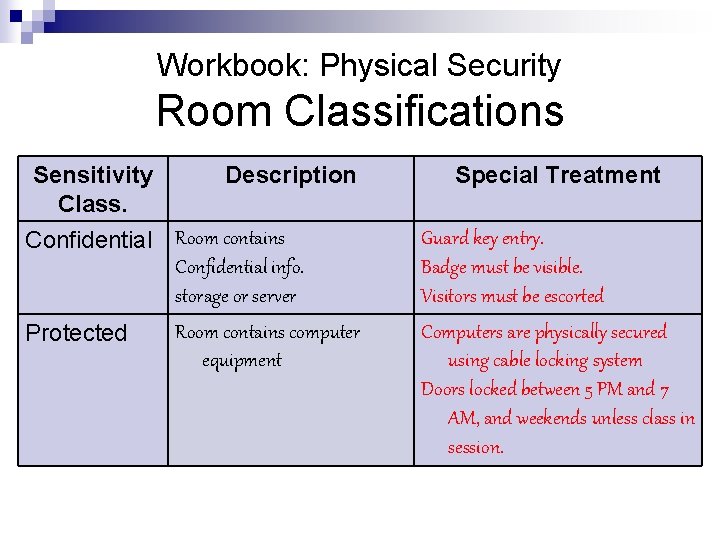
Workbook: Physical Security Room Classifications Sensitivity Class. Description Confidential Room contains Confidential info. storage or server Room contains computer Protected equipment Special Treatment Guard key entry. Badge must be visible. Visitors must be escorted Computers are physically secured using cable locking system Doors locked between 5 PM and 7 AM, and weekends unless class in session.

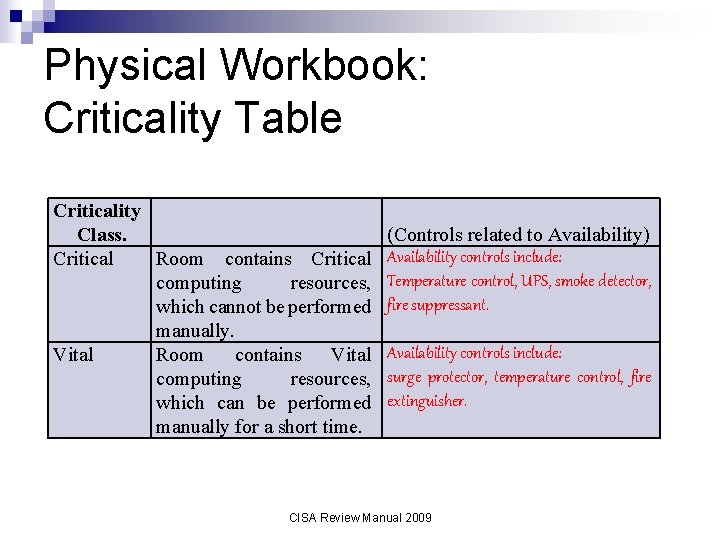
Physical Workbook: Criticality Table Criticality Class. Critical Room contains Critical computing resources, which cannot be performed manually. Vital Room contains Vital computing resources, which can be performed manually for a short time. (Controls related to Availability) Availability controls include: Temperature control, UPS, smoke detector, fire suppressant. Availability controls include: surge protector, temperature control, fire extinguisher. CISA Review Manual 2009

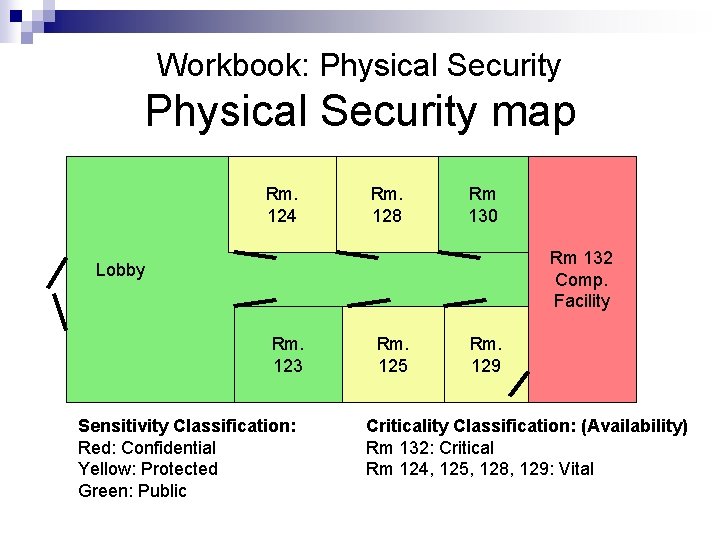
Workbook: Physical Security map Rm. 124 Rm. 128 Rm 130 Rm 132 Comp. Facility Lobby Rm. 123 Sensitivity Classification: Red: Confidential Yellow: Protected Green: Public Rm. 125 Rm. 129 Criticality Classification: (Availability) Rm 132: Critical Rm 124, 125, 128, 129: Vital

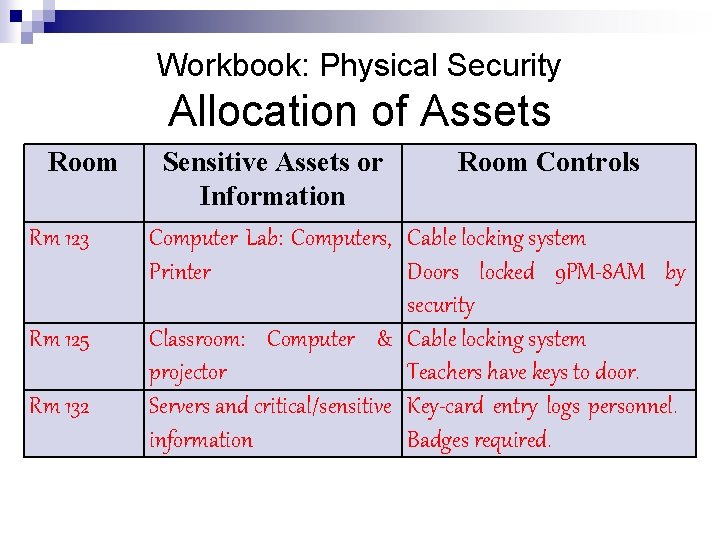
Workbook: Physical Security Allocation of Assets Room Rm 123 Rm 125 Rm 132 Sensitive Assets or Room Controls Information Computer Lab: Computers, Cable locking system Printer Doors locked 9 PM-8 AM by security Classroom: Computer & Cable locking system projector Teachers have keys to door. Servers and critical/sensitive Key-card entry logs personnel. information Badges required.

Summary of Physical Controls Physical Access Control n Walls, Doors, Locks n Badges, smart cards n Biometrics n Security cameras & guards n Fences, lighting, sensors n Cable locking system n Computer screen hoods Environmental Controls n Backup power n Air conditioning n Fire suppressant Secure procedures n Engraved serial numbers n Locked files, desks n Clean desk n Paper shredders n Locking screensaver n Secure procedures: locked doors at night

Question 1. 2. 3. 4. A Fire Suppression system that is environmentally friendly, is not lethal, and does not damage equipment is: Dry Pipe Halon Charged FM-200

Question 1. 2. 3. 4. The best way to prevent piggybacking into secured areas is: Deadman door Bolting door Guard Camera

Question A surge protector is the best protection against 1. Electromagnetic interference 2. Loss of power for 10 -30 minutes 3. A blackout 4. Sags and spikes

Question 1. 2. 3. 4. To eliminate problems with incomplete transactions during a sudden power failure, Joe has decided that some form of temporary power supply is necessary to ensure a graceful shut down. The best option for Joe is: UPS Surge protector Alternate power generator Battery supply

Personnel Security Auditors check for both Physical and Personnel Security too… CISA Review Manual 2009

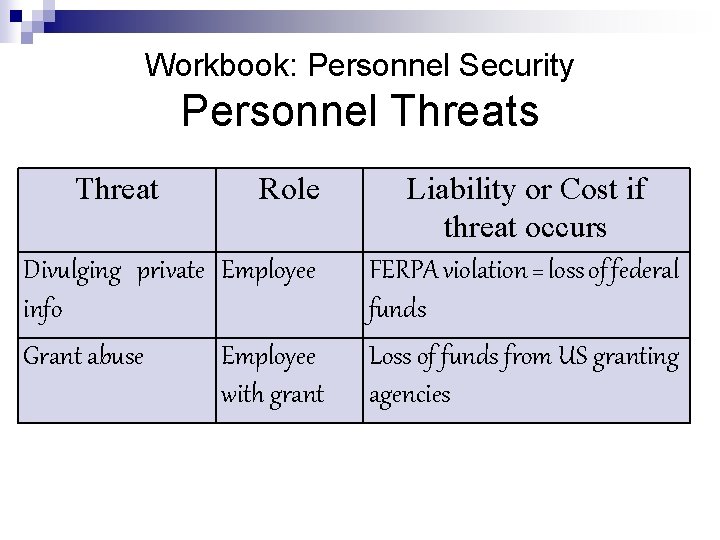
Workbook: Personnel Security Personnel Threats Threat Role Divulging private Employee info Grant abuse Employee with grant Liability or Cost if threat occurs FERPA violation = loss of federal funds Loss of funds from US granting agencies

Security Awareness & Training n Training covers what is expected of employees ¨ Why is policy in place? ¨ How is policy enforced? n Training may be implemented as: ¨ New employee orientation ¨ Company newsletters ¨ Determine effectiveness by interviewing employees CISA Review Manual 2009

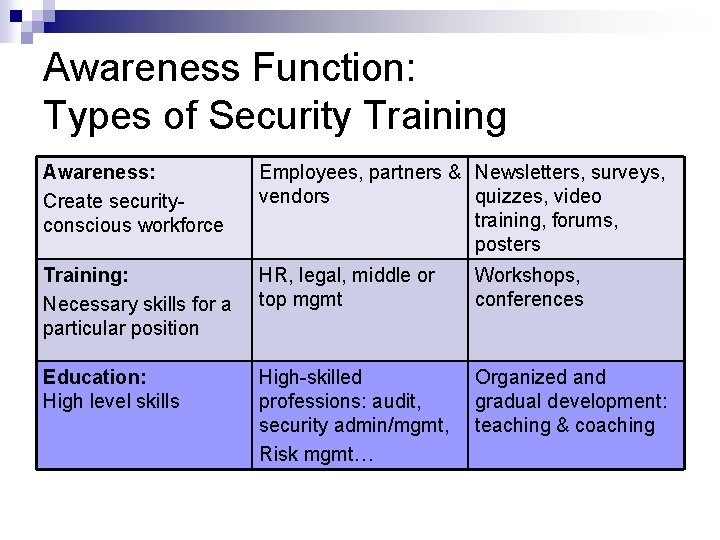
Awareness Function: Types of Security Training Awareness: Create securityconscious workforce Employees, partners & Newsletters, surveys, vendors quizzes, video training, forums, posters Training: Necessary skills for a particular position HR, legal, middle or top mgmt Workshops, conferences Education: High level skills High-skilled professions: audit, security admin/mgmt, Risk mgmt… Organized and gradual development: teaching & coaching

Awareness Training n n n Signed employment agreements, video, memos, emails, posters, seminars and training classes A combination of parallel approaches Knowledge areas: ¨ ¨ ¨ ¨ n Back-up work-related files Choosing passwords and avoiding exposure Avoiding email and web viruses Recognizing social engineers Recognizing & reporting security incidents Securing electronic & paper media against theft & exposure Spotting malware that could lead to identity theft & desktop spying Metrics should be established to determine effectiveness of change in behavior and workforce attitude

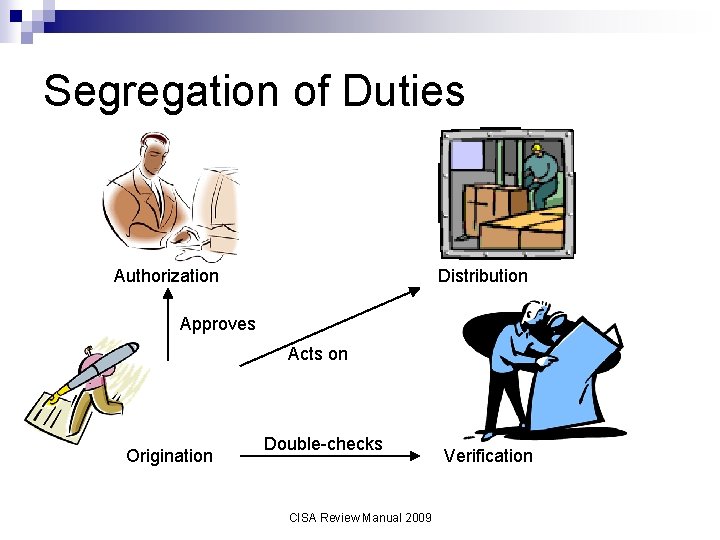
Segregation of Duties Authorization Distribution Approves Acts on Origination Double-checks CISA Review Manual 2009 Verification

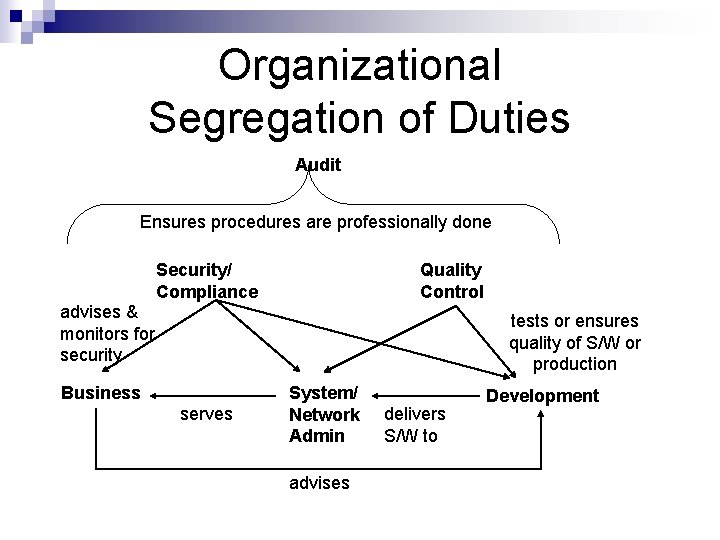
Organizational Segregation of Duties Audit Ensures procedures are professionally done Security/ Compliance Quality Control advises & monitors for security tests or ensures quality of S/W or production Business serves System/ Network Admin advises delivers S/W to Development

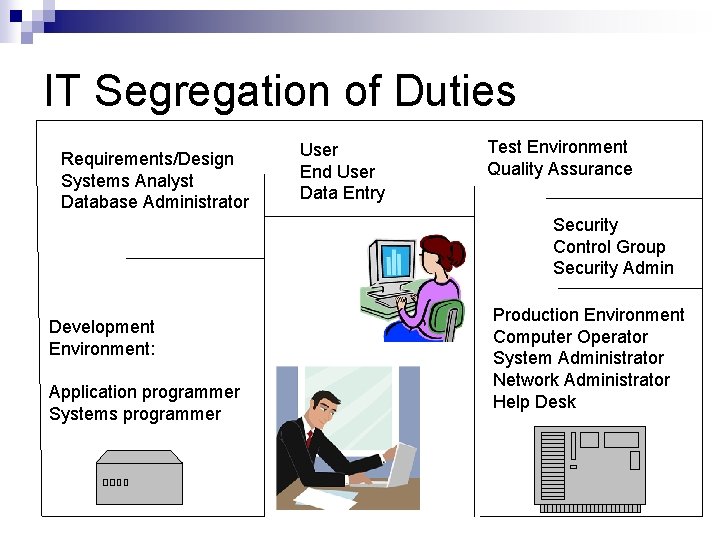
IT Segregation of Duties Requirements/Design Systems Analyst Database Administrator User End User Data Entry Test Environment Quality Assurance Security Control Group Security Admin Development Environment: Application programmer Systems programmer Production Environment Computer Operator System Administrator Network Administrator Help Desk

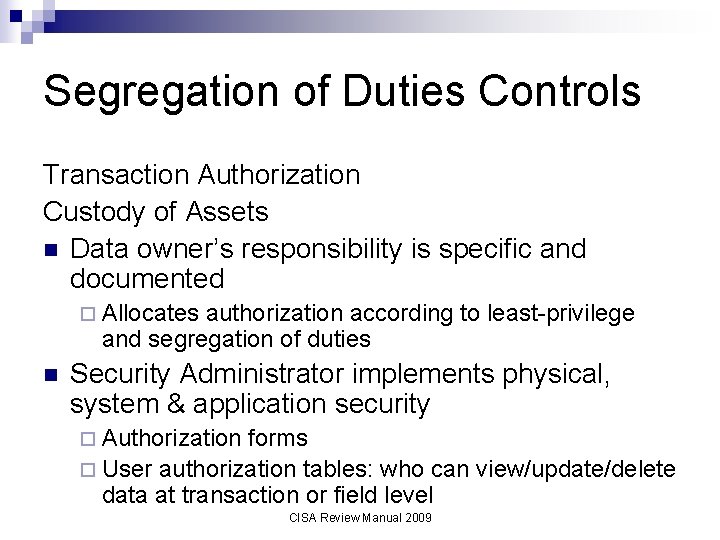
Segregation of Duties Controls Transaction Authorization Custody of Assets n Data owner’s responsibility is specific and documented ¨ Allocates authorization according to least-privilege and segregation of duties n Security Administrator implements physical, system & application security ¨ Authorization forms ¨ User authorization tables: who can view/update/delete data at transaction or field level CISA Review Manual 2009

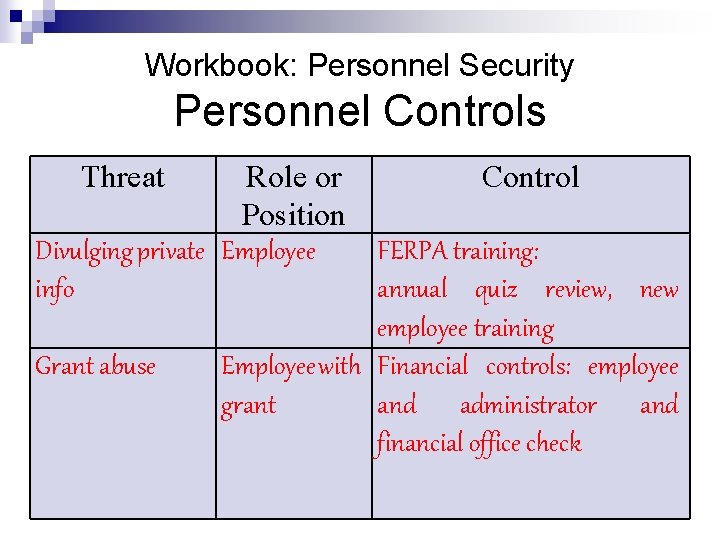
Workbook: Personnel Security Personnel Controls Threat Role or Control Position Divulging private Employee FERPA training: info annual quiz review, new employee training Grant abuse Employee with Financial controls: employee grant and administrator and financial office check

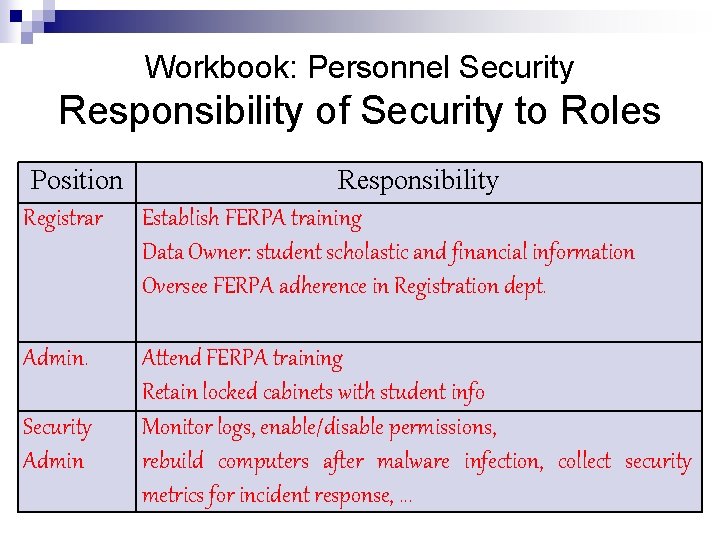
Workbook: Personnel Security Responsibility of Security to Roles Position Responsibility Registrar Establish FERPA training Data Owner: student scholastic and financial information Oversee FERPA adherence in Registration dept. Admin. Security Admin Attend FERPA training Retain locked cabinets with student info Monitor logs, enable/disable permissions, rebuild computers after malware infection, collect security metrics for incident response, . . .

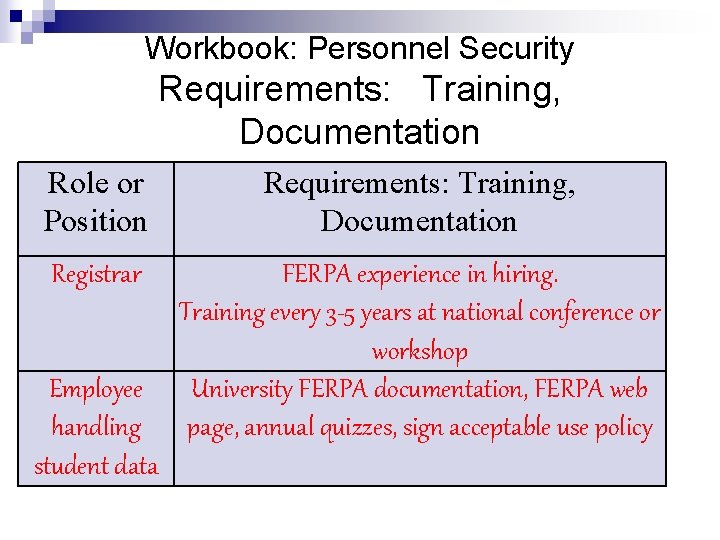
Workbook: Personnel Security Requirements: Training, Documentation Role or Position Requirements: Training, Documentation Registrar FERPA experience in hiring. Training every 3 -5 years at national conference or workshop University FERPA documentation, FERPA web page, annual quizzes, sign acceptable use policy Employee handling student data

Personnel Issues n Background checks can reduce fraud ¨ More secure position=more checking required ¨ A standard or procedure may be useful n n Training & signed contracts Track and document theft ¨ Minor incidents could add up to a major pattern problem n Email can be monitored for potential problem employees ¨ Assuming policy is in place and employees are aware

Employee Hiring Document security responsibilities n Screen candidates for sensitive positions n Have signed agreements regarding n ¨ Job responsibilities, conditions of employment ¨ Security responsibilities (incl. copyright) ¨ Confidentiality agreement n Indicate corrective actions taken if security requirements not followed CISA Review Manual 2009

New Employee Orientation New employee signs document: n Has read and agreed to follow security policies n Promise to not divulge logon IDs and passwords n Create quality passwords n Lock terminal when not present n Report suspected violations of security n Maintain good physical security (locked doors, private keys) n Conform to laws and regulations n Use IT resources only for authorized business purposes CISA Review Manual 2009

Employee Termination Unless continued relationship expected: n Return equipment n Revoke access CISA Review Manual 2009

Third Party Agreements n n n Define information security policy Define procedures to implement policy Deploy controls to protect against malicious software Publish restrictions on copying/distributing information Implement procedures to determine whether assets were compromised Ensure return or destruction of data at end of job CISA Review Manual 2009

Summary of Personnel Controls n n n Segregation of Duties Mandatory vacations or job rotation Training and written policies and procedures Background checks Need to Know/Least Privilege Fraud reporting mechanism

Question 1. 2. 3. 4. Which of the following duties can be performed by one person in a well-controlled IS environment? Software Developer and System Administration Database administration and Data Entry System Administrator and Quality Assurance and Software Developer

Question Which is MOST important for a successful security awareness program? 1. Technical training for security administrators 2. Aligning the training to organization requirements 3. Training management for security awareness 4. Using metrics to ensure that training is effective

Question To detect fraud, the BEST type of audit trail to log would be: 1. User session logs 2. Firewall incidents 3. Operating system incidents 4. Application transactions

Vocabulary n n n Blackout, brownout, sag, spike, surge, electromagnetic interference Surge protector, UPS, alternate power generator Fire suppression: charged, dry pipe, FM 200, Argonite Deadman door, piggybacking Security awareness, security training, security education Segregation of duties CISA Review Manual 2009