Introduction to Networking and the Internet Copyright University



- Slides: 37

Introduction to Networking and the Internet Copyright © University of Illinois CS 241 Staff 1

Announcements n Brighten’s office hours cancelled for today ¡ n extra hours next week Wade Fagen lecturing on Friday Copyright © University of Illinois CS 241 Staff 2

Where are we? n Function calls, system calls, threads and processes Copyright © University of Illinois CS 241 Staff 3

What’s next? n Networked communication and distributed applications Copyright © University of Illinois CS 241 Staff 4

Introduction n n What is the Internet? Network edge What is a protocol? Protocol layers, service models Copyright © University of Illinois CS 241 Staff 5

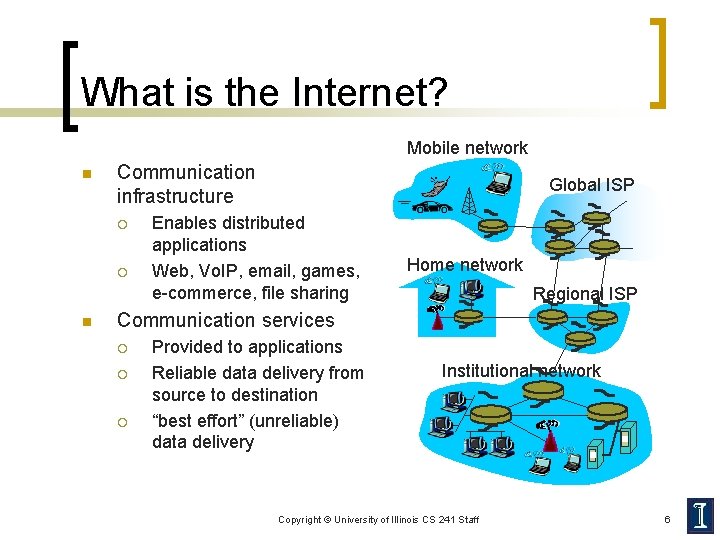
What is the Internet? Mobile network n Communication infrastructure ¡ ¡ n Global ISP Enables distributed applications Web, Vo. IP, email, games, e-commerce, file sharing Home network Regional ISP Communication services ¡ ¡ ¡ Provided to applications Reliable data delivery from source to destination “best effort” (unreliable) data delivery Institutional network Copyright © University of Illinois CS 241 Staff 6

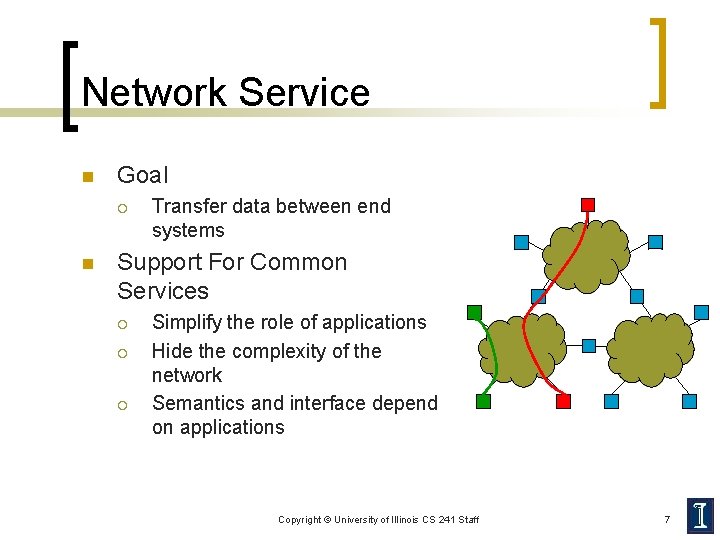
Network Service n Goal ¡ n Transfer data between end systems Support For Common Services ¡ ¡ ¡ Simplify the role of applications Hide the complexity of the network Semantics and interface depend on applications Copyright © University of Illinois CS 241 Staff 7

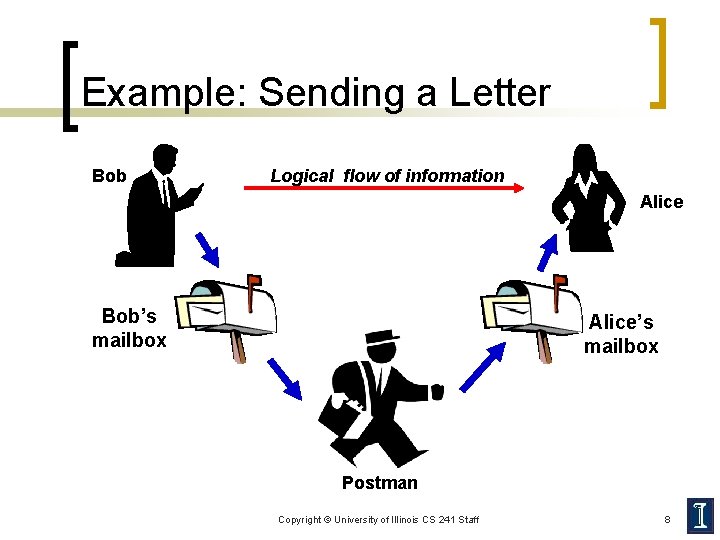
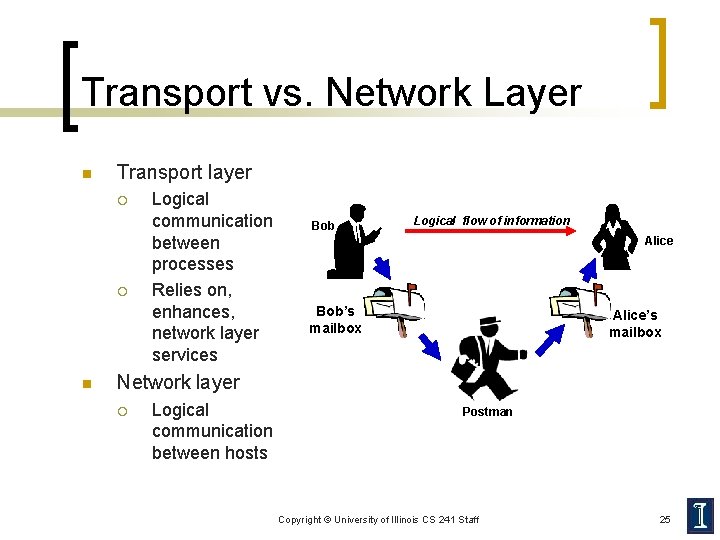
Example: Sending a Letter Bob Logical flow of information Alice Bob’s mailbox Alice’s mailbox Postman Copyright © University of Illinois CS 241 Staff 8

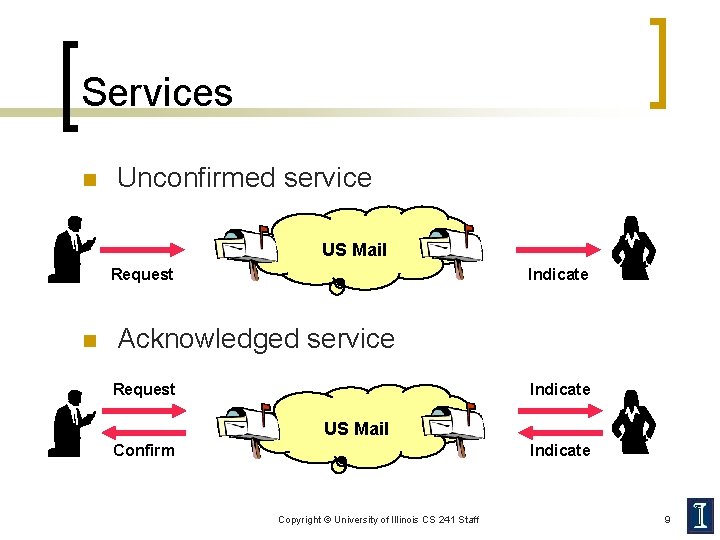
Services n Unconfirmed service US Mail Request n Indicate Acknowledged service Request Indicate US Mail Confirm Indicate Copyright © University of Illinois CS 241 Staff 9

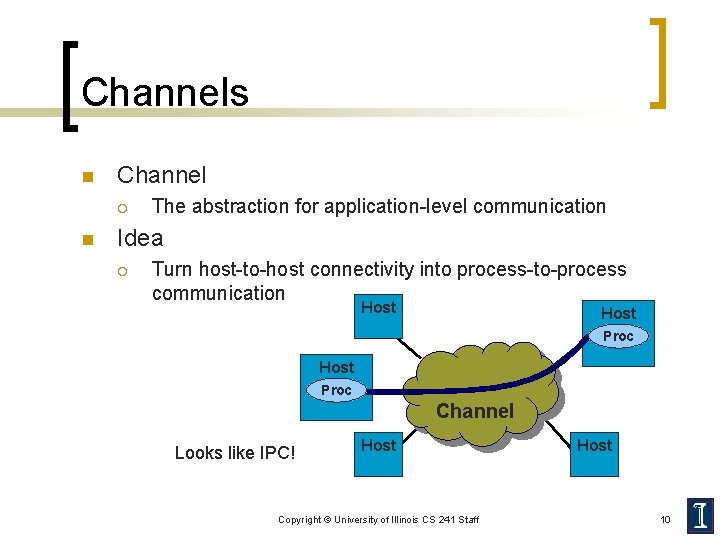
Channels n Channel ¡ n The abstraction for application-level communication Idea ¡ Turn host-to-host connectivity into process-to-process communication Host Proc Channel Looks like IPC! Host Copyright © University of Illinois CS 241 Staff Host 10

Networked Communication Challenges n n Networked communication IPC Problems typically masked by communication channel abstractions ¡ ¡ ¡ n Bit errors (electrical interference) Packet errors (congestion) Link/node failures Message delays Out-of-order delivery Eavesdropping Goal ¡ Fill the gap between what applications expect and what the underlying technology provides Copyright © University of Illinois CS 241 Staff 11

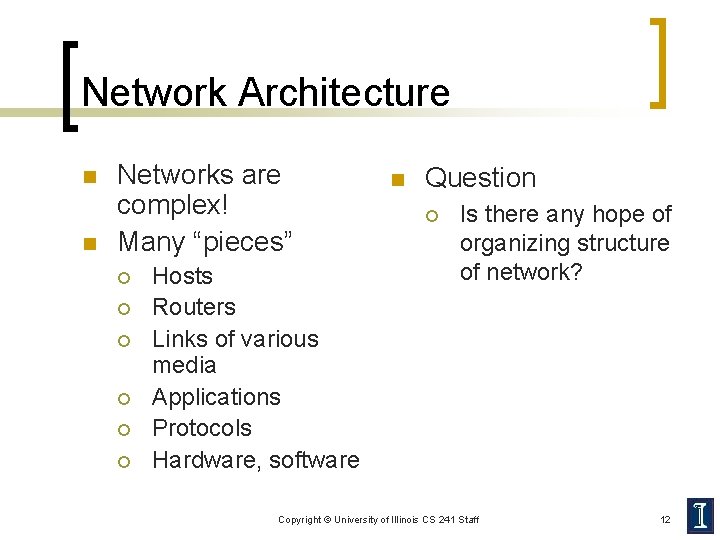
Network Architecture n n Networks are complex! Many “pieces” ¡ ¡ ¡ Hosts Routers Links of various media Applications Protocols Hardware, software n Question ¡ Is there any hope of organizing structure of network? Copyright © University of Illinois CS 241 Staff 12

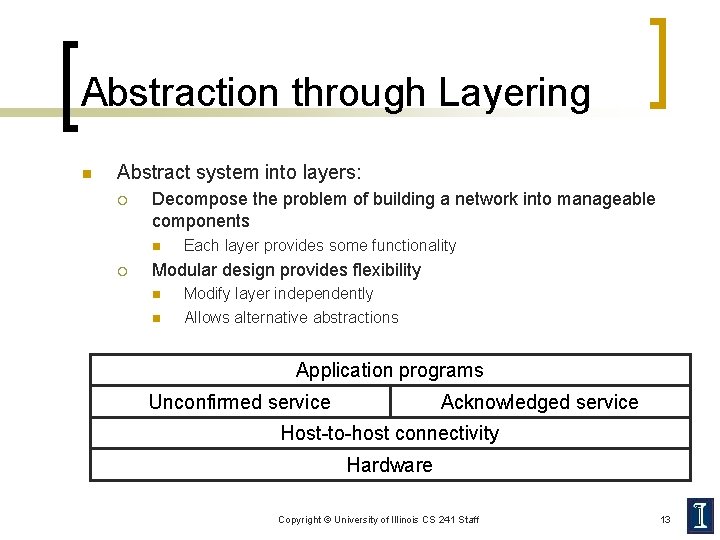
Abstraction through Layering n Abstract system into layers: ¡ Decompose the problem of building a network into manageable components n ¡ Each layer provides some functionality Modular design provides flexibility n n Modify layer independently Allows alternative abstractions Application programs Unconfirmed service Acknowledged service Host-to-host connectivity Hardware Copyright © University of Illinois CS 241 Staff 13

Layering Example: Air Travel n Layers ¡ ¡ ¡ Each layer implements a service Via its own internal-layer actions Relying on services provided by layer below Copyright © University of Illinois CS 241 Staff 14

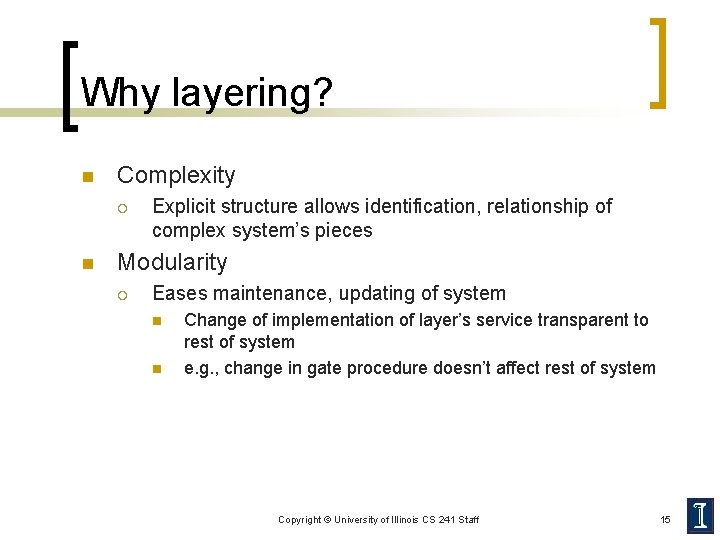
Why layering? n Complexity ¡ n Explicit structure allows identification, relationship of complex system’s pieces Modularity ¡ Eases maintenance, updating of system n n Change of implementation of layer’s service transparent to rest of system e. g. , change in gate procedure doesn’t affect rest of system Copyright © University of Illinois CS 241 Staff 15

Protocol: Language of communication across hosts n n Defines structure of n Protocols define communication ¡ Format between two instances ¡ Order of msgs sent of a layer (on two and received hosts) among network Protocols are defined entities by ¡ Actions taken on ¡ Specific msgs sent msg transmission, ¡ Specific actions receipt taken when msgs received, or other events Copyright © University of Illinois CS 241 Staff 16

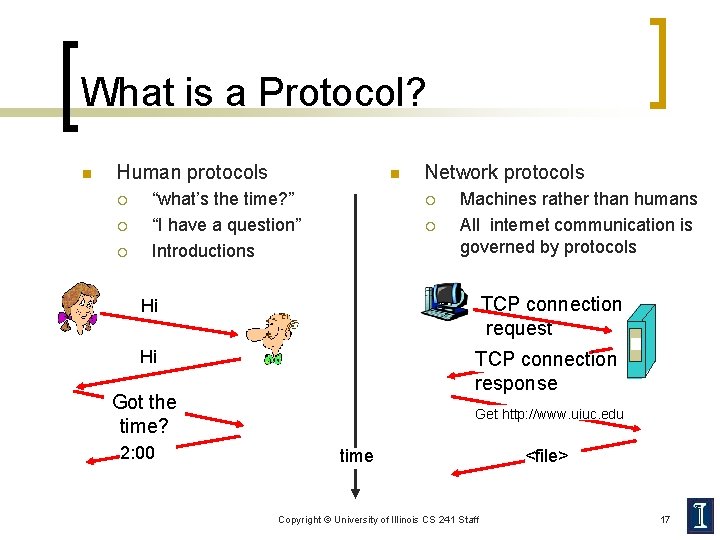
What is a Protocol? n Human protocols ¡ ¡ ¡ n “what’s the time? ” “I have a question” Introductions Network protocols ¡ ¡ Machines rather than humans All internet communication is governed by protocols Hi TCP connection request Hi TCP connection response Got the time? 2: 00 Get http: //www. uiuc. edu time Copyright © University of Illinois CS 241 Staff <file> 17

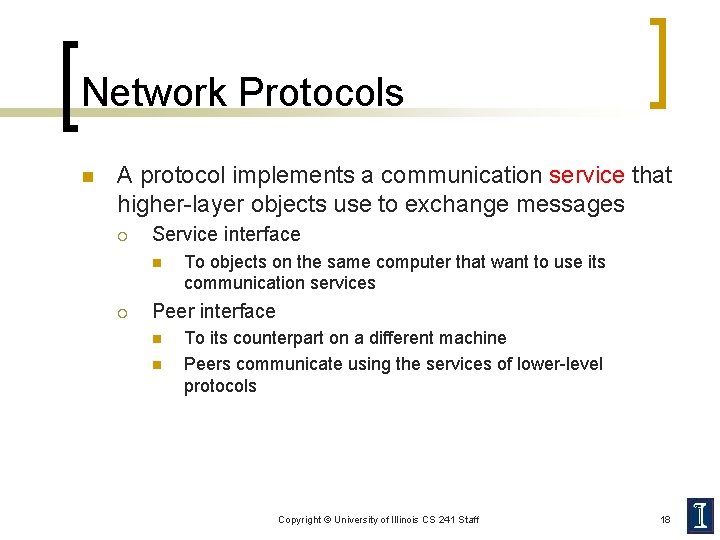
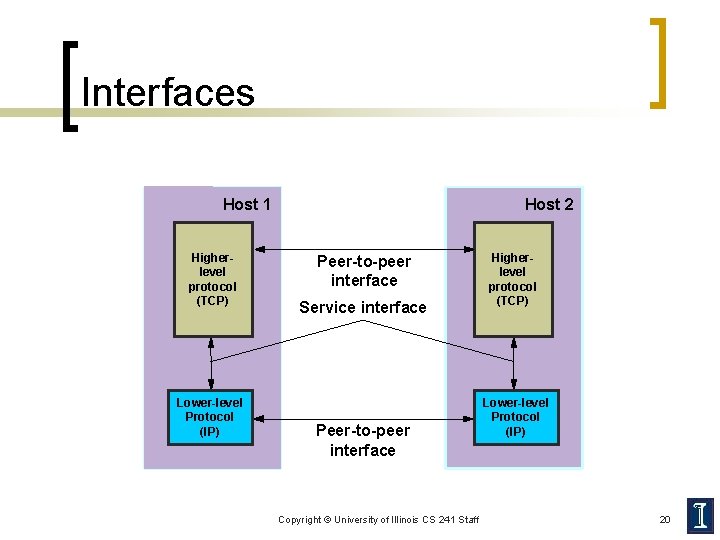
Network Protocols n A protocol implements a communication service that higher-layer objects use to exchange messages ¡ Service interface n ¡ To objects on the same computer that want to use its communication services Peer interface n n To its counterpart on a different machine Peers communicate using the services of lower-level protocols Copyright © University of Illinois CS 241 Staff 18

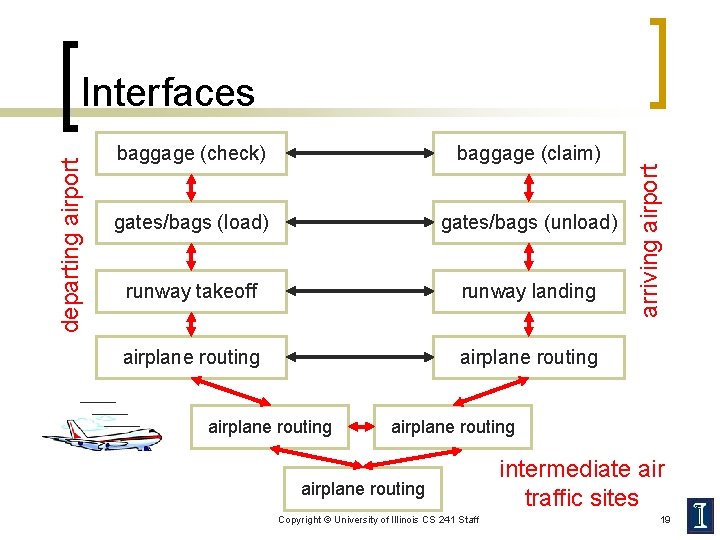
baggage (check) baggage (claim) gates/bags (load) gates/bags (unload) runway takeoff runway landing airplane routing arriving airport departing airport Interfaces airplane routing Copyright © University of Illinois CS 241 Staff intermediate air traffic sites 19

Interfaces Host 1 Higherlevel protocol (TCP) Lower-level Protocol (IP) Host 2 Peer-to-peer interface Service interface Peer-to-peer interface Copyright © University of Illinois CS 241 Staff Higherlevel protocol (TCP) Lower-level Protocol (IP) 20

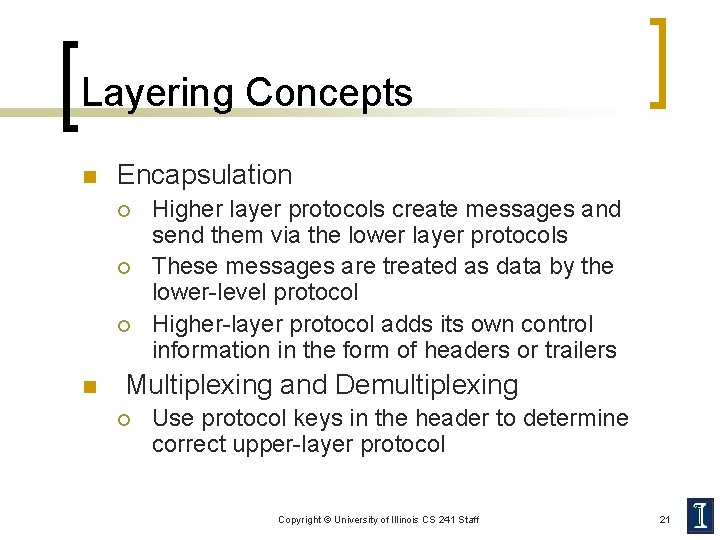
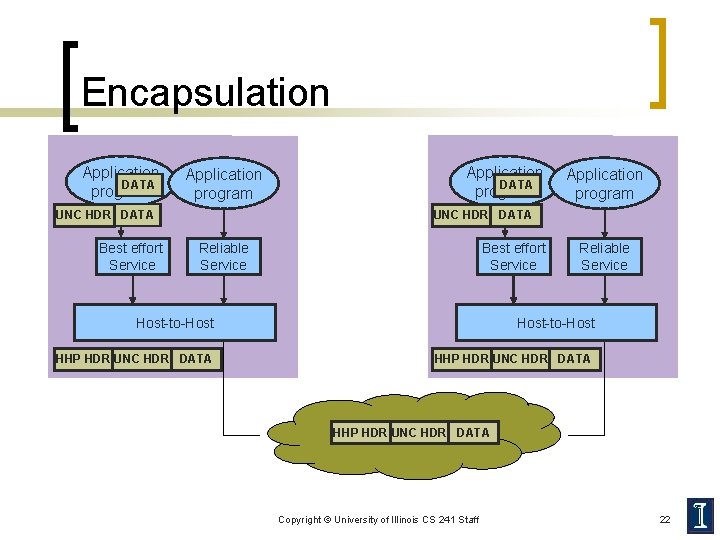
Layering Concepts n Encapsulation ¡ ¡ ¡ n Higher layer protocols create messages and send them via the lower layer protocols These messages are treated as data by the lower-level protocol Higher-layer protocol adds its own control information in the form of headers or trailers Multiplexing and Demultiplexing ¡ Use protocol keys in the header to determine correct upper-layer protocol Copyright © University of Illinois CS 241 Staff 21

Encapsulation Application DATA program Application program UNC HDR DATA Best effort Service Reliable Service Host-to-Host HHP HDR UNC HDR DATA Copyright © University of Illinois CS 241 Staff 22

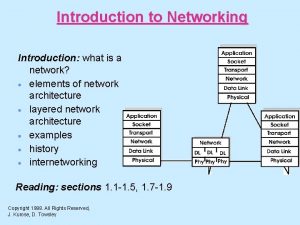
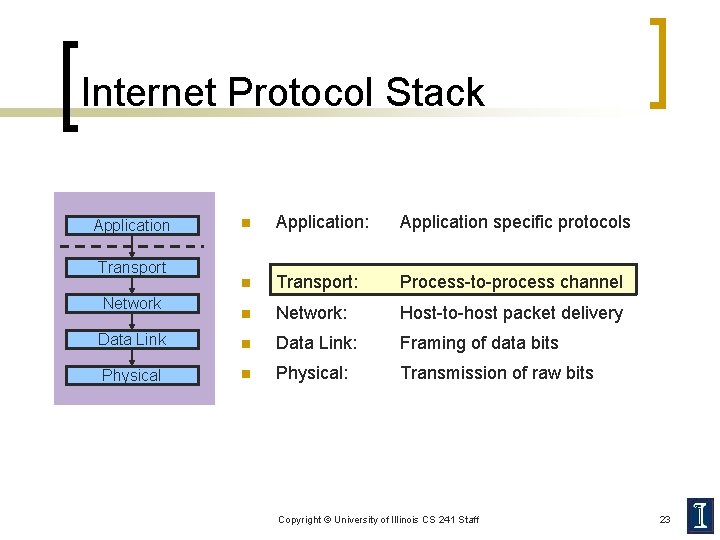
Internet Protocol Stack n Application: Application specific protocols n Transport: Process-to-process channel n Network: Host-to-host packet delivery Data Link n Data Link: Framing of data bits Physical n Physical: Transmission of raw bits Application Transport Network Copyright © University of Illinois CS 241 Staff 23

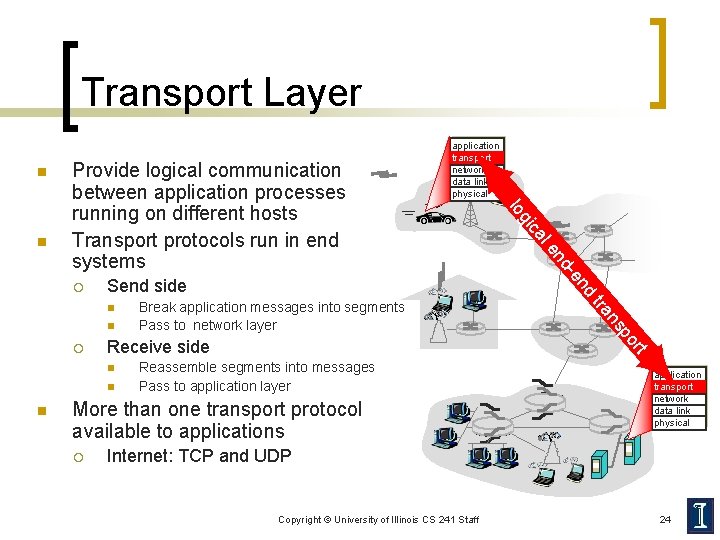
Transport Layer n n n Reassemble segments into messages Pass to application layer More than one transport protocol available to applications ¡ rt po n ns Receive side tra ¡ nd -e nd n Break application messages into segments Pass to network layer l e n ca Send side gi ¡ lo n Provide logical communication between application processes running on different hosts Transport protocols run in end systems application transport network data link physical Internet: TCP and UDP Copyright © University of Illinois CS 241 Staff 24

Transport vs. Network Layer n Transport layer ¡ ¡ n Logical communication between processes Relies on, enhances, network layer services Bob Logical flow of information Alice Bob’s mailbox Alice’s mailbox Network layer ¡ Logical communication between hosts Postman Copyright © University of Illinois CS 241 Staff 25

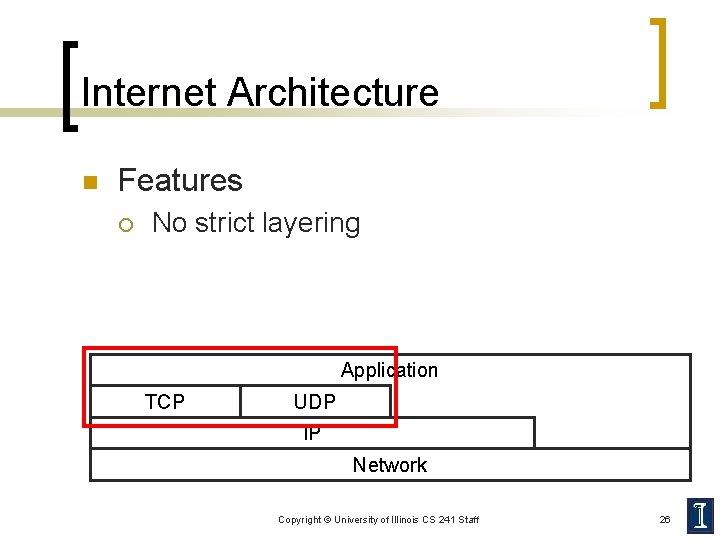
Internet Architecture n Features ¡ No strict layering Application TCP UDP IP Network Copyright © University of Illinois CS 241 Staff 26

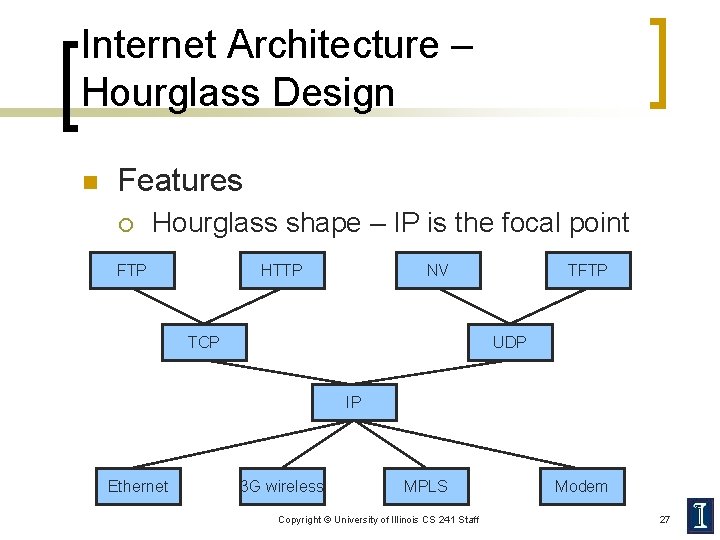
Internet Architecture – Hourglass Design n Features ¡ Hourglass shape – IP is the focal point FTP HTTP NV TCP TFTP UDP IP Ethernet 3 G wireless MPLS Copyright © University of Illinois CS 241 Staff Modem 27

Network Applications Copyright © University of Illinois CS 241 Staff 28

Creating a Network Application n Write programs that ¡ ¡ Run on (different) end systems Communicate over network n n e. g. , web server software communicates with browser software No need to write software for network-core devices ¡ Network-core devices do not run user applications Copyright © University of Illinois CS 241 Staff 29

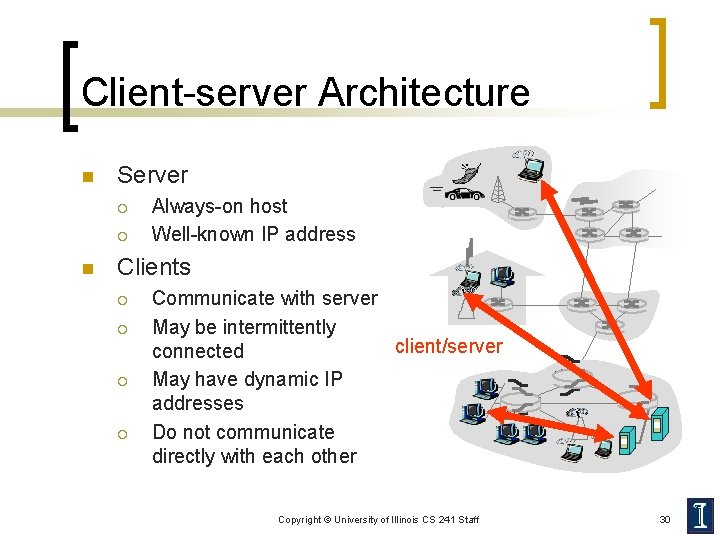
Client-server Architecture n Server ¡ ¡ n Always-on host Well-known IP address Clients ¡ ¡ Communicate with server May be intermittently client/server connected May have dynamic IP addresses Do not communicate directly with each other Copyright © University of Illinois CS 241 Staff 30

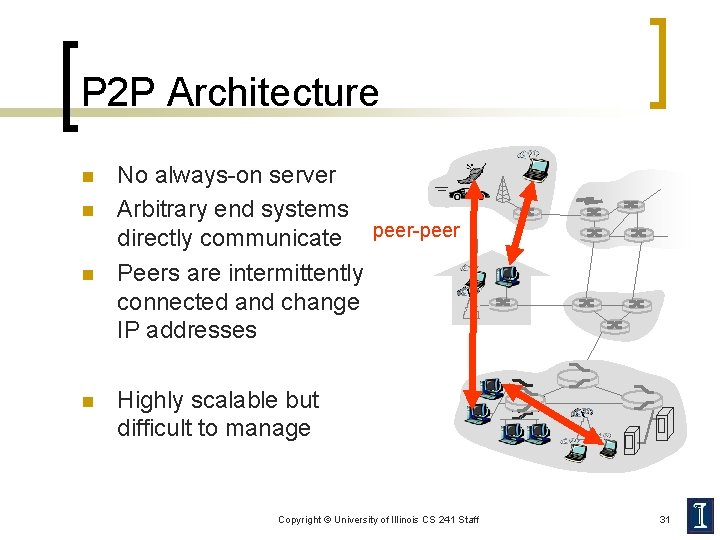
P 2 P Architecture n n No always-on server Arbitrary end systems directly communicate peer-peer Peers are intermittently connected and change IP addresses Highly scalable but difficult to manage Copyright © University of Illinois CS 241 Staff 31

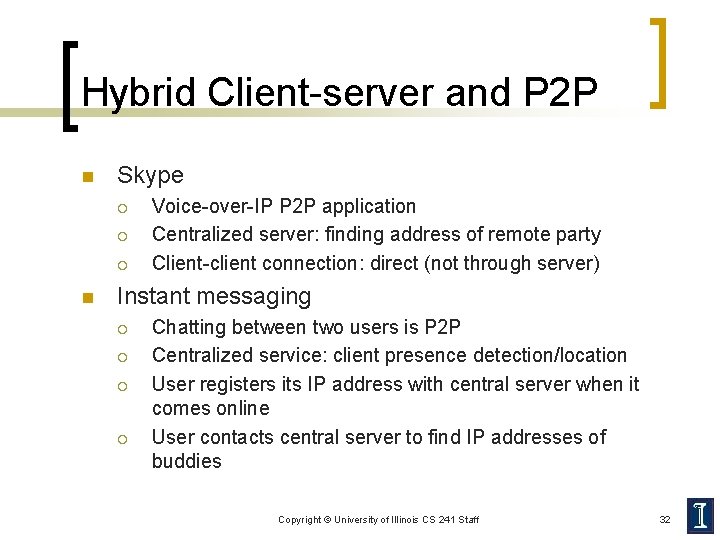
Hybrid Client-server and P 2 P n Skype ¡ ¡ ¡ n Voice-over-IP P 2 P application Centralized server: finding address of remote party Client-client connection: direct (not through server) Instant messaging ¡ ¡ Chatting between two users is P 2 P Centralized service: client presence detection/location User registers its IP address with central server when it comes online User contacts central server to find IP addresses of buddies Copyright © University of Illinois CS 241 Staff 32

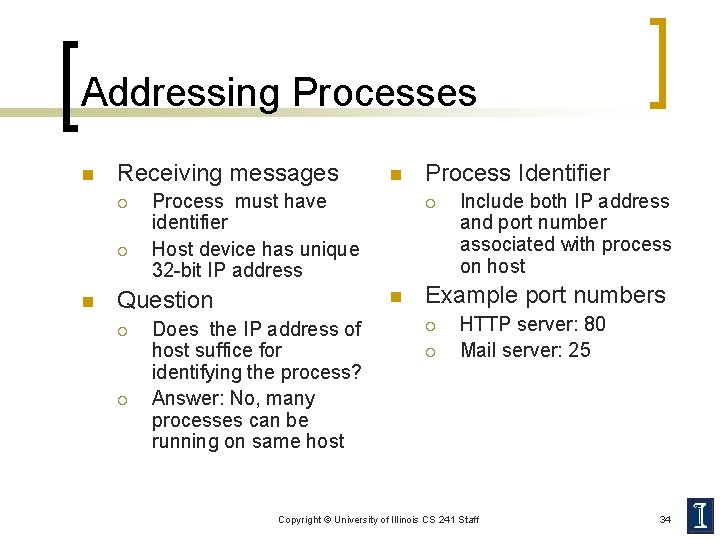
Addressing Processes n Receiving messages ¡ ¡ n Process must have identifier Host device has unique 32 -bit IP address Question ¡ ¡ n Does the IP address of host suffice for identifying the process? Answer: No, many processes can be running on same host Process Identifier Include both IP address and port number associated with process on host Example port numbers ¡ ¡ HTTP server: 80 Mail server: 25 Copyright © University of Illinois CS 241 Staff 34

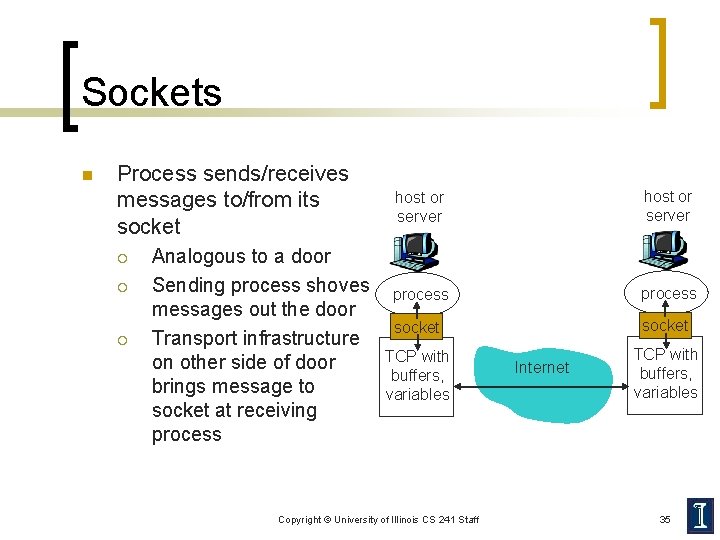
Sockets n Process sends/receives messages to/from its socket ¡ ¡ ¡ Analogous to a door Sending process shoves messages out the door Transport infrastructure on other side of door brings message to socket at receiving process host or server process socket TCP with buffers, variables Copyright © University of Illinois CS 241 Staff Internet TCP with buffers, variables 35

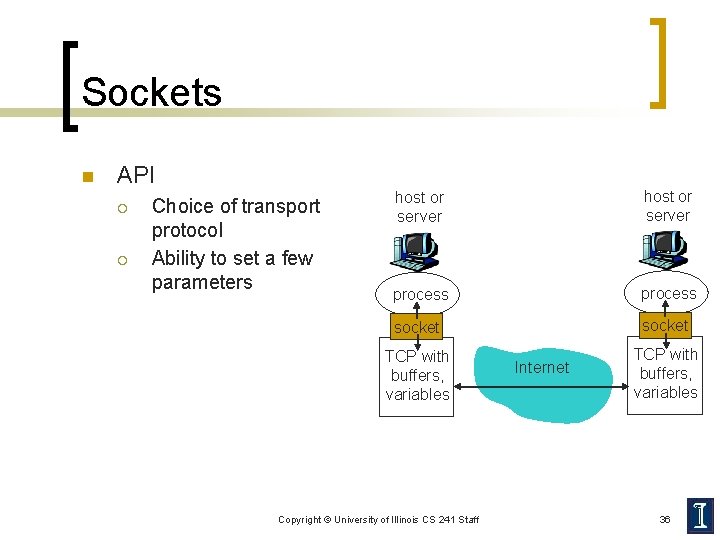
Sockets n API ¡ ¡ Choice of transport protocol Ability to set a few parameters host or server process socket TCP with buffers, variables Copyright © University of Illinois CS 241 Staff Internet TCP with buffers, variables 36

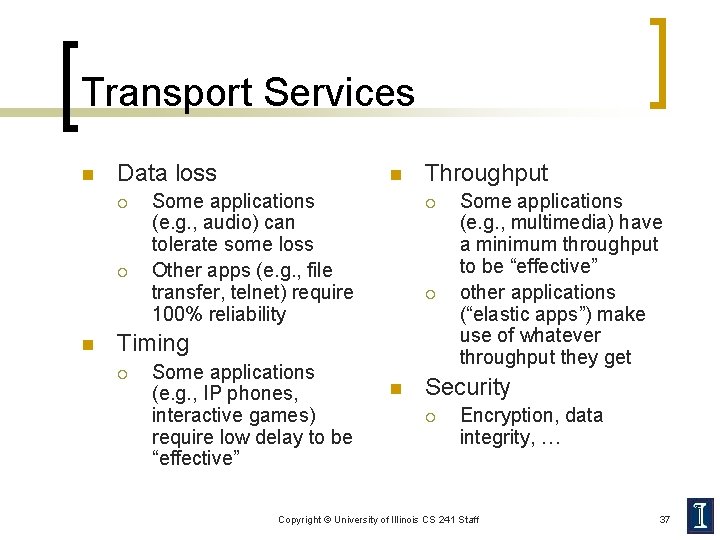
Transport Services n Data loss ¡ ¡ n n Some applications (e. g. , audio) can tolerate some loss Other apps (e. g. , file transfer, telnet) require 100% reliability Throughput ¡ ¡ Timing ¡ Some applications (e. g. , IP phones, interactive games) require low delay to be “effective” n Some applications (e. g. , multimedia) have a minimum throughput to be “effective” other applications (“elastic apps”) make use of whatever throughput they get Security ¡ Encryption, data integrity, … Copyright © University of Illinois CS 241 Staff 37

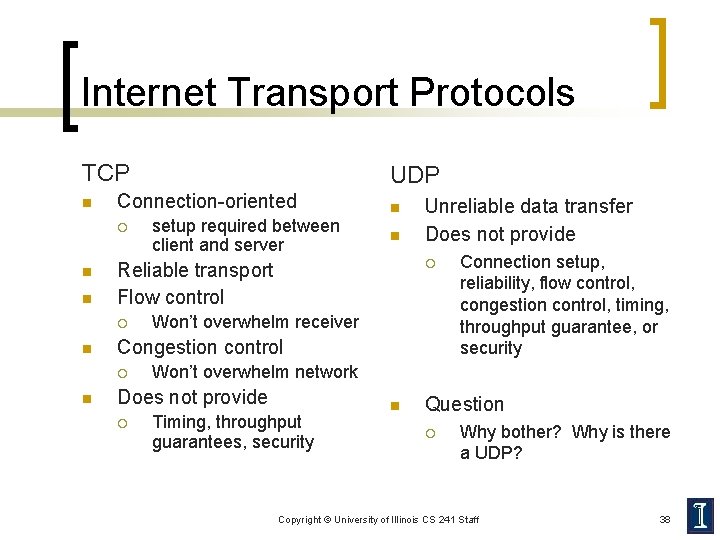
Internet Transport Protocols TCP n Connection-oriented ¡ n n n Unreliable data transfer Does not provide ¡ Won’t overwhelm receiver Congestion control ¡ n setup required between client and server n Reliable transport Flow control ¡ n UDP Won’t overwhelm network Does not provide ¡ Connection setup, reliability, flow control, congestion control, timing, throughput guarantee, or security Timing, throughput guarantees, security n Question ¡ Why bother? Why is there a UDP? Copyright © University of Illinois CS 241 Staff 38
 Sdn vs traditional networking
Sdn vs traditional networking Internet way of networking
Internet way of networking Introduction to data communications and networking
Introduction to data communications and networking Introduction of networking
Introduction of networking Internet or internet
Internet or internet Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Lp html
Lp html Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Voi kéo gỗ như thế nào
Voi kéo gỗ như thế nào Glasgow thang điểm
Glasgow thang điểm Chúa yêu trần thế alleluia
Chúa yêu trần thế alleluia Môn thể thao bắt đầu bằng từ đua
Môn thể thao bắt đầu bằng từ đua Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tính độ biến thiên đông lượng
Công thức tính độ biến thiên đông lượng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư anh em như thể tay chân
Mật thư anh em như thể tay chân Làm thế nào để 102-1=99
Làm thế nào để 102-1=99 độ dài liên kết
độ dài liên kết Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thơ thất ngôn tứ tuyệt đường luật
Thơ thất ngôn tứ tuyệt đường luật Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng nó xinh thế
Cái miệng nó xinh thế Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Biện pháp chống mỏi cơ
Biện pháp chống mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Thế nào là giọng cùng tên
Thế nào là giọng cùng tên Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Tia chieu sa te
Tia chieu sa te Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là Dot
Dot Bảng số nguyên tố lớn hơn 1000
Bảng số nguyên tố lớn hơn 1000