Ing Ondej eveek GOPAS a s MCM Directory























- Slides: 90

Ing. Ondřej Ševeček | GOPAS a. s. | MCM: Directory Services | MVP: Enterprise Security | ondrej@sevecek. com | www. sevecek. com | CLIENT INTERACTIONS

Active Directory Client Interactions INTRO

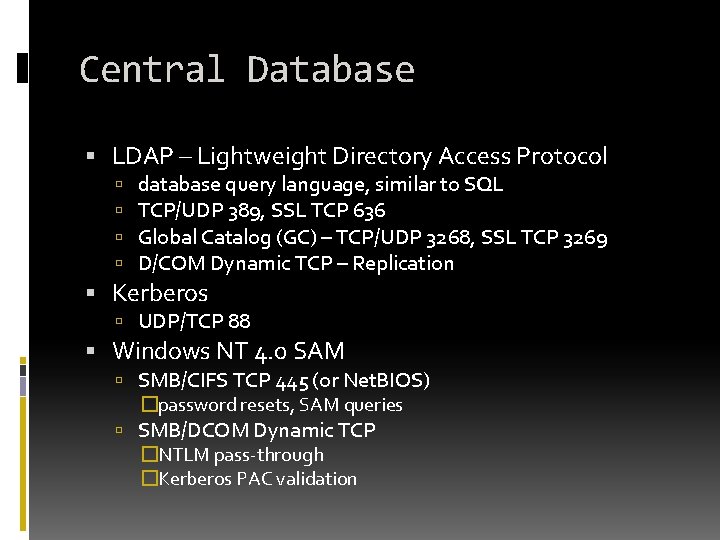
Central Database LDAP – Lightweight Directory Access Protocol database query language, similar to SQL TCP/UDP 389, SSL TCP 636 Global Catalog (GC) – TCP/UDP 3268, SSL TCP 3269 D/COM Dynamic TCP – Replication Kerberos UDP/TCP 88 Windows NT 4. 0 SAM SMB/CIFS TCP 445 (or Net. BIOS) �password resets, SAM queries SMB/DCOM Dynamic TCP �NTLM pass-through �Kerberos PAC validation

Design Considerations Distributed system DCs disconnected for very long times several months Multimaster replication with some FSMO roles

Design Considerations Example: Caribean cruises, DC/IS/Exchange on board with tens of workstations and users, some staff hired during journey. No or bad satelite connectivity only. DCs synced after ship is berthed at main office. Challenge: Must work independently for long time periods. Different independent cruiseliners/DCs can accomodate changes to user accounts, email addresses, Exchange settings. Cannot afford lost of any one.

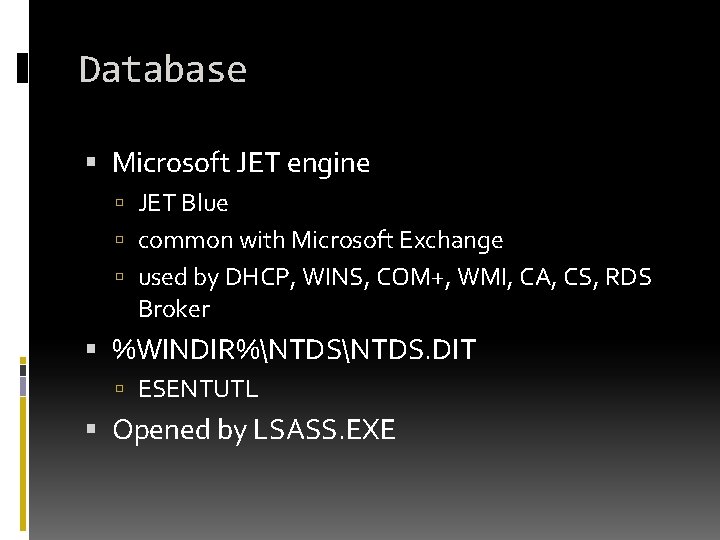
Database Microsoft JET engine JET Blue common with Microsoft Exchange used by DHCP, WINS, COM+, WMI, CA, CS, RDS Broker %WINDIR%NTDS. DIT ESENTUTL Opened by LSASS. EXE

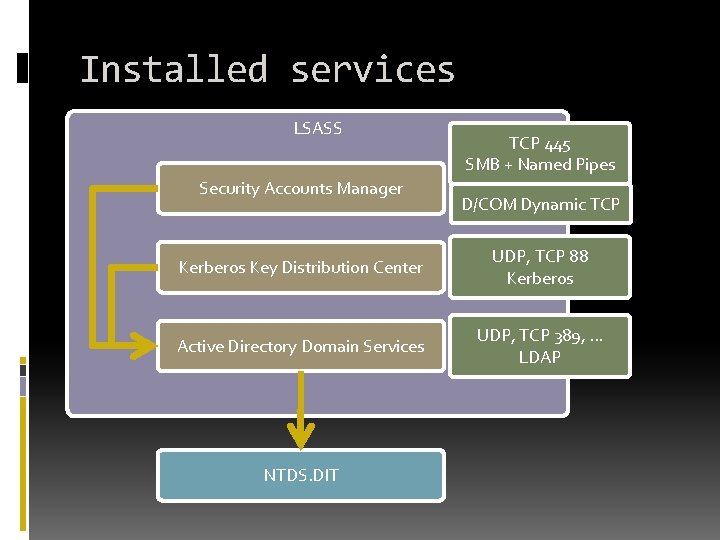
Installed services LSASS Security Accounts Manager TCP 445 SMB + Named Pipes D/COM Dynamic TCP Kerberos Key Distribution Center UDP, TCP 88 Kerberos Active Directory Domain Services UDP, TCP 389, . . . LDAP NTDS. DIT

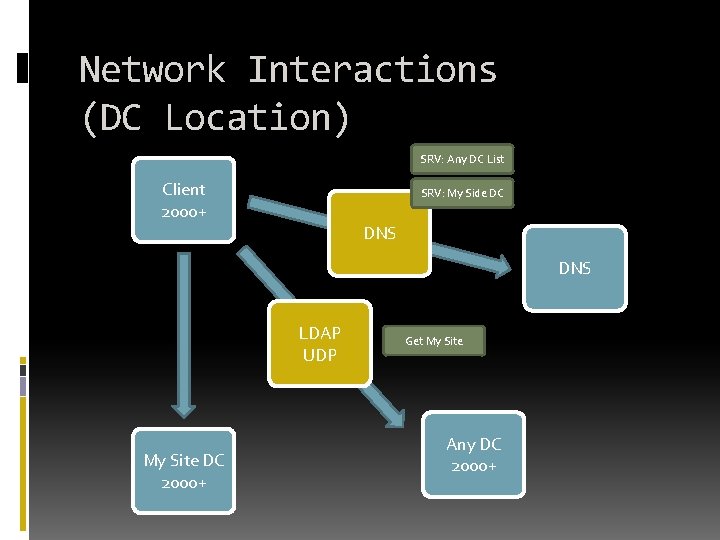
Network Interactions (DC Location) SRV: Any DC List Client 2000+ SRV: My Side DC DNS LDAP UDP My Site DC 2000+ Get My Site Any DC 2000+

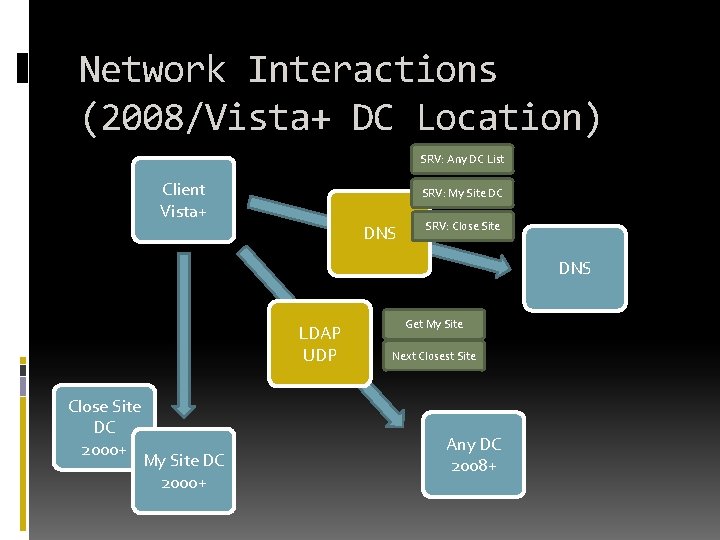
Network Interactions (2008/Vista+ DC Location) SRV: Any DC List Client Vista+ SRV: My Site DC DNS SRV: Close Site DNS LDAP UDP Close Site DC 2000+ My Site DC 2000+ Get My Site Next Closest Site Any DC 2008+

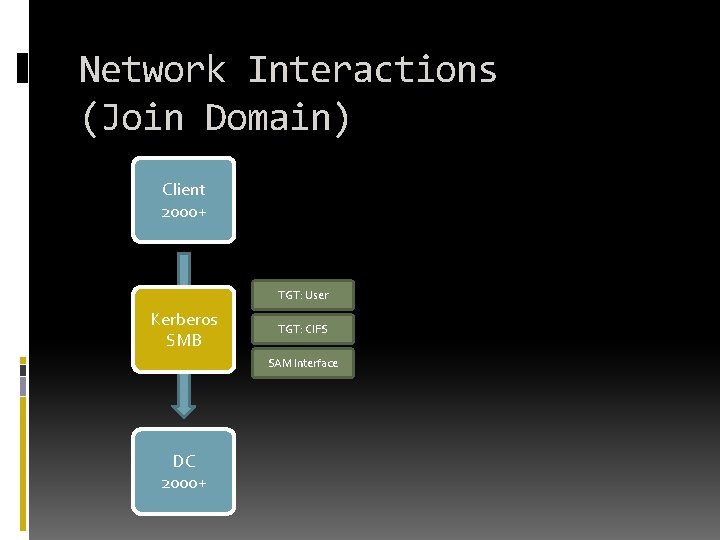
Network Interactions (Join Domain) Client 2000+ TGT: User Kerberos SMB TGT: CIFS SAM Interface DC 2000+

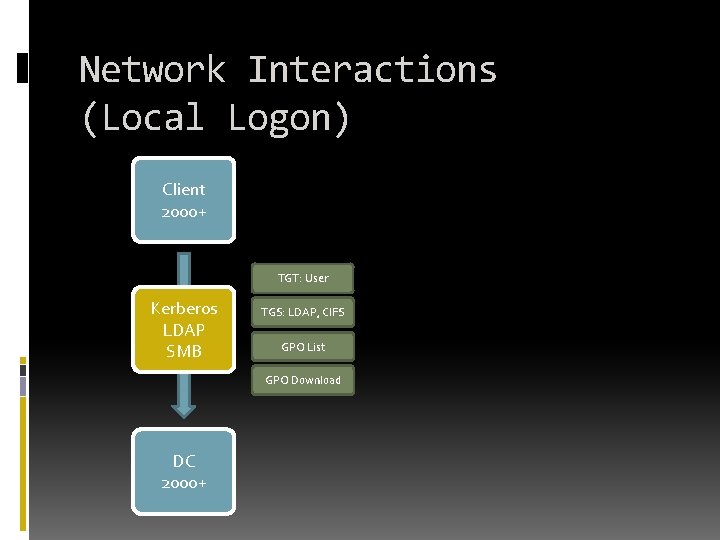
Network Interactions (Local Logon) Client 2000+ TGT: User Kerberos LDAP SMB TGS: LDAP, CIFS GPO List GPO Download DC 2000+

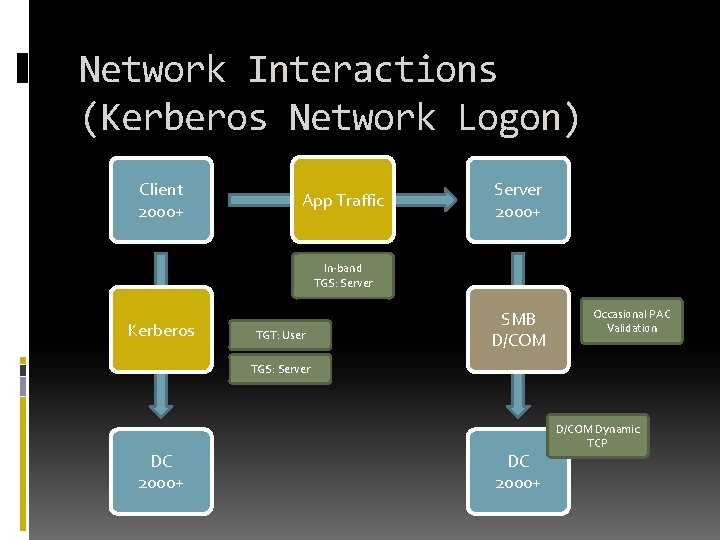
Network Interactions (Kerberos Network Logon) Client 2000+ App Traffic Server 2000+ In-band TGS: Server Kerberos TGT: User SMB D/COM Occasional PAC Validation TGS: Server DC 2000+ D/COM Dynamic TCP

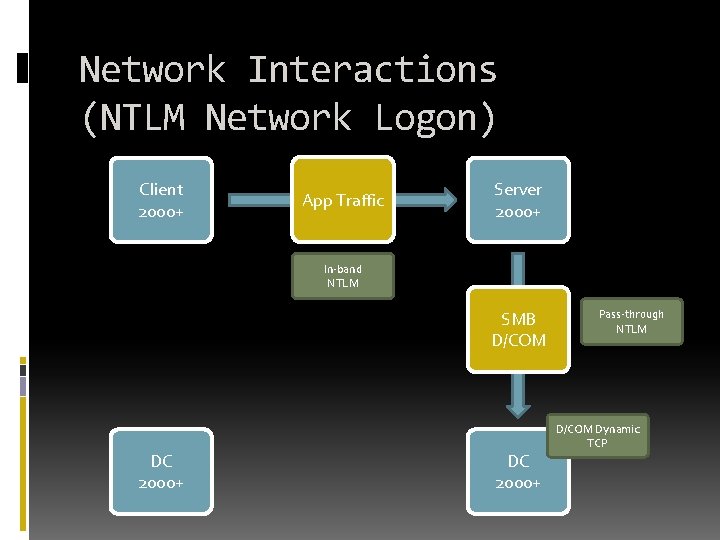
Network Interactions (NTLM Network Logon) Client 2000+ App Traffic Server 2000+ In-band NTLM SMB D/COM DC 2000+ Pass-through NTLM D/COM Dynamic TCP

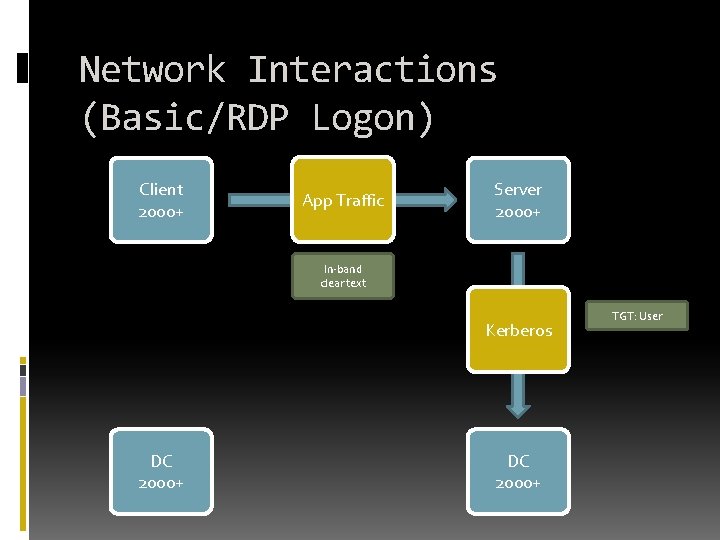
Network Interactions (Basic/RDP Logon) Client 2000+ App Traffic Server 2000+ In-band clear text Kerberos DC 2000+ TGT: User

Active Directory Replication ATTRIBUTE NOTES

Attribute Types string, integer, datetime, boolean, binary DN reference multivalue up to 5000 items linked multivalue unlimited, requires 2003 Forest Level backlink member. Of computed primary. Group. Token, token. Groups, last. Logon. Timestamp write/only attributes unicode. Pwd

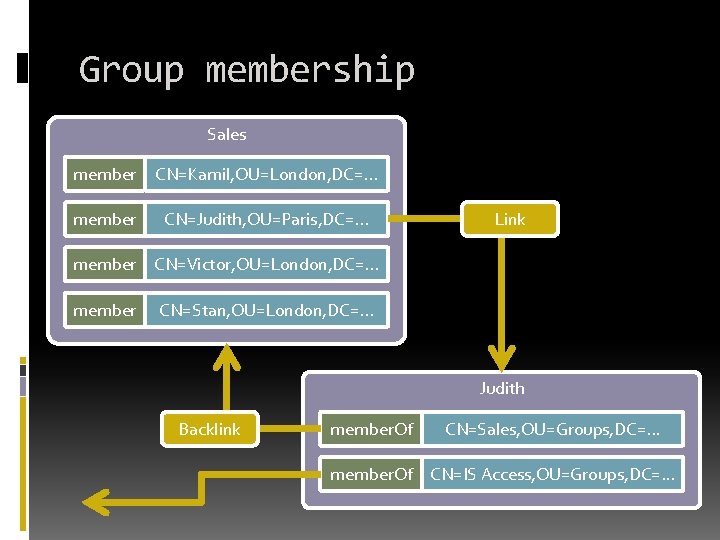
Group membership Sales member CN=Kamil, OU=London, DC=. . . member CN=Judith, OU=Paris, DC=. . . Link member CN=Victor, OU=London, DC=. . . member CN=Stan, OU=London, DC=. . . Judith Backlink member. Of CN=Sales, OU=Groups, DC=. . . member. Of CN=IS Access, OU=Groups, DC=. . .

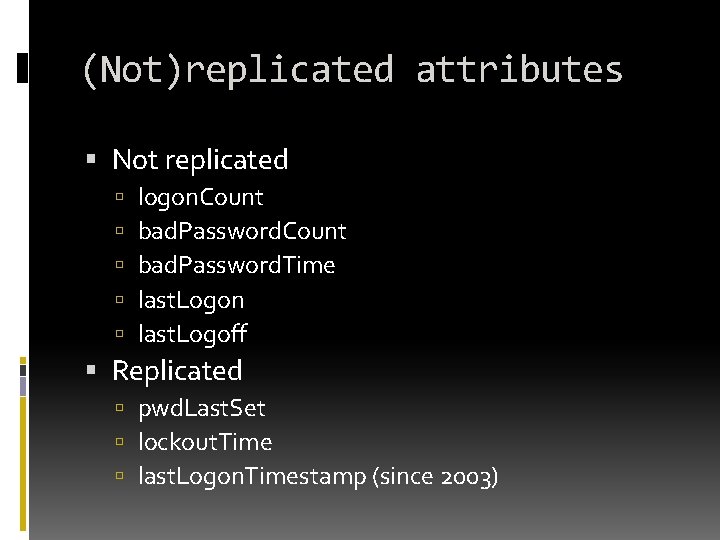
(Not)replicated attributes Not replicated logon. Count bad. Password. Time last. Logon last. Logoff Replicated pwd. Last. Set lockout. Time last. Logon. Timestamp (since 2003)

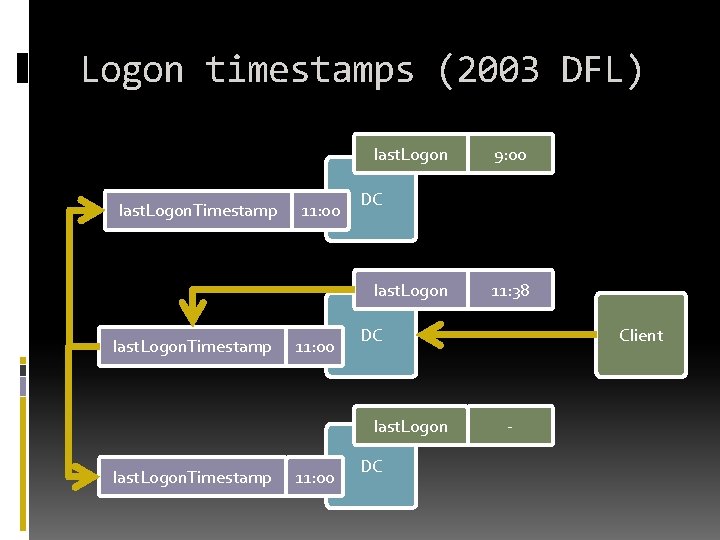
Logon timestamps (2003 DFL) last. Logon. Timestamp 11: 00 DC last. Logon. Timestamp 11: 00 11: 38 DC last. Logon. Timestamp 9: 00 DC Client -

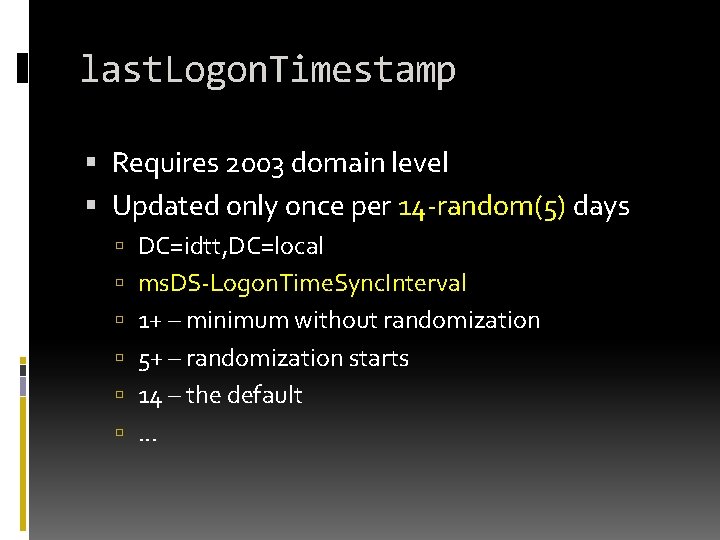
last. Logon. Timestamp Requires 2003 domain level Updated only once per 14 -random(5) days DC=idtt, DC=local ms. DS-Logon. Time. Sync. Interval 1+ – minimum without randomization 5+ – randomization starts 14 – the default . . .

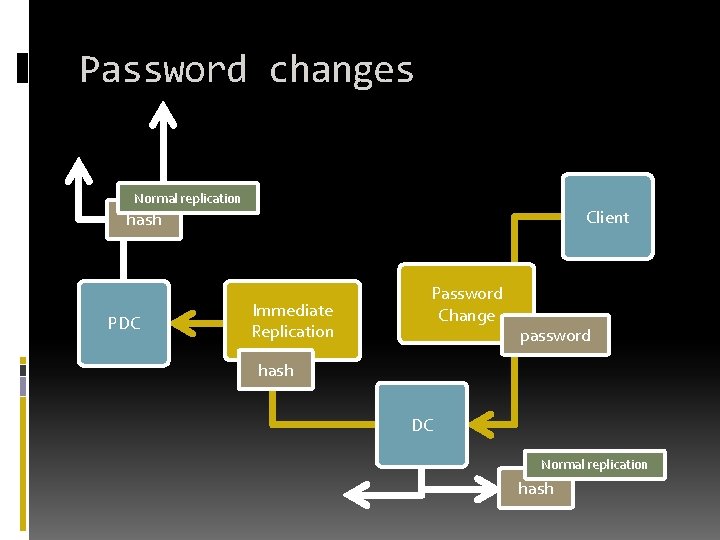
Password changes Normal replication Client hash PDC Immediate Replication Password Change password hash DC Normal replication hash

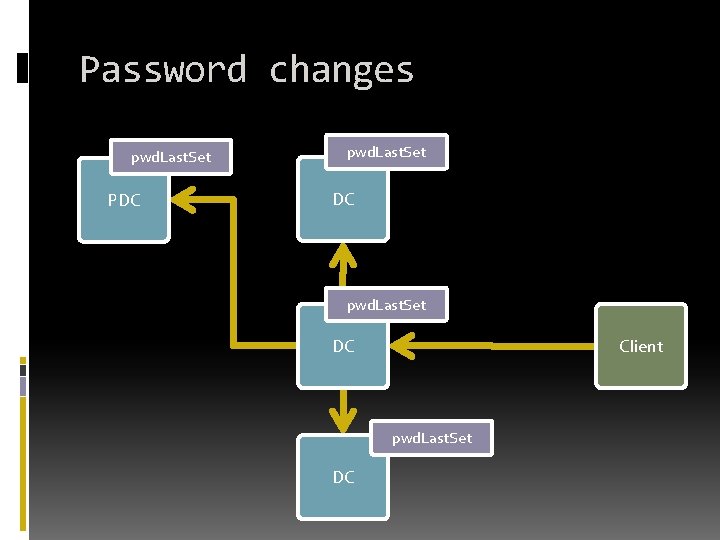
Password changes pwd. Last. Set PDC pwd. Last. Set DC Client pwd. Last. Set DC

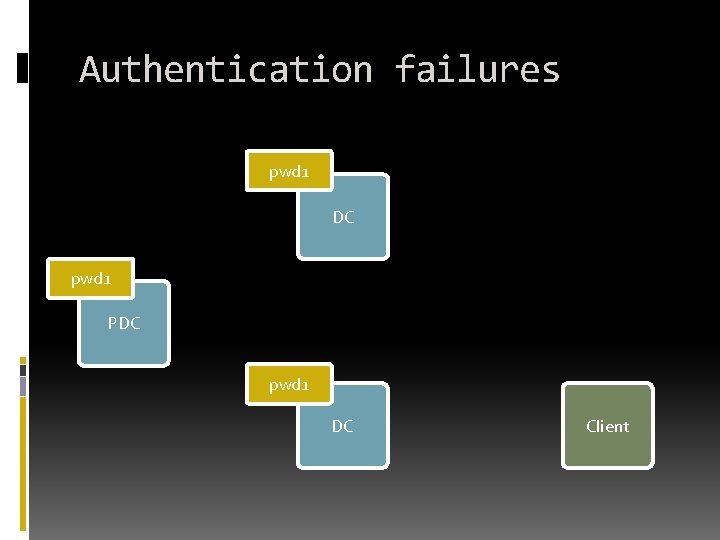
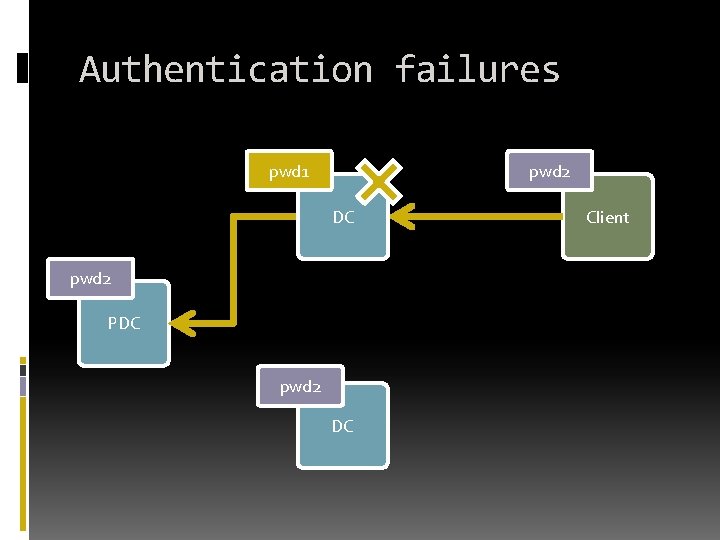
Authentication failures pwd 1 DC pwd 1 PDC pwd 1 DC Client

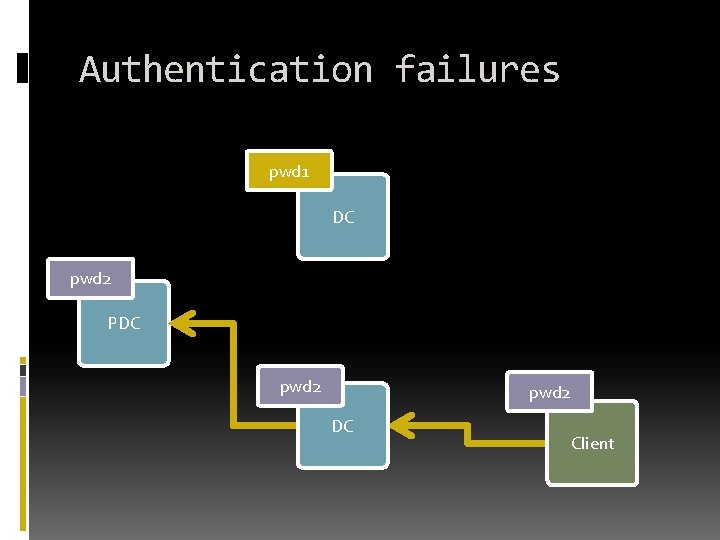
Authentication failures pwd 1 DC pwd 2 PDC pwd 2 DC Client

Authentication failures pwd 1 pwd 2 DC pwd 2 PDC pwd 2 DC Client

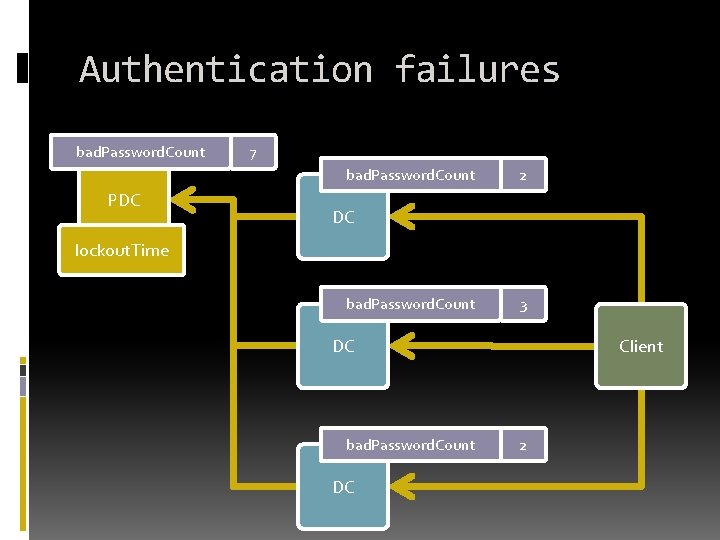
Authentication failures bad. Password. Count 7 bad. Password. Count PDC 2 DC lockout. Time bad. Password. Count 3 DC bad. Password. Count DC Client 2

Active Directory Client Interactions DC LOCATION

Client Applications Kerberos and NTLM authentication Secure Channel password changes, NTLM pass-through, Kerberos PAC validation Group Policy client DFS client Certificate Autoenrollment client

Client Applications NPS (IAS), RRAS, TMG (ISA), RD Gateway (TS Gateway) group membership, Dial-In tab RD Host (Terminal Server) Remote Control tab etc. , Licensing servers DHCP Server authorization IIS account and group membership for SSL certificate authentication WDS computer MAC addresses or GUIDs

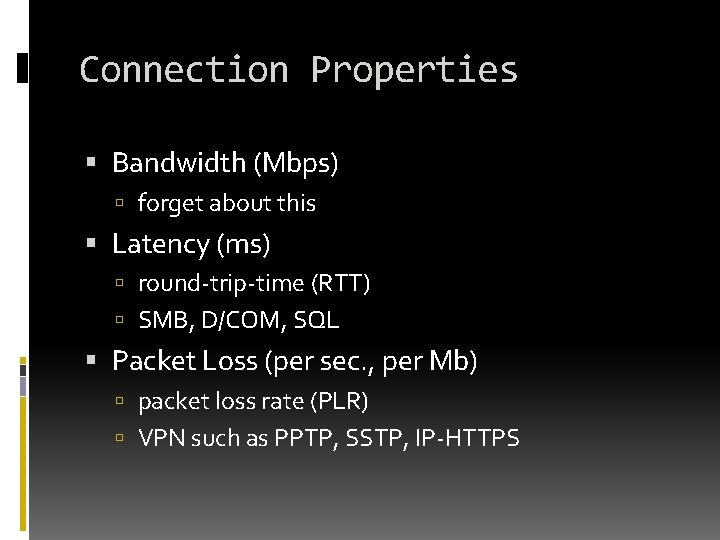
Connection Properties Bandwidth (Mbps) forget about this Latency (ms) round-trip-time (RTT) SMB, D/COM, SQL Packet Loss (per sec. , per Mb) packet loss rate (PLR) VPN such as PPTP, SSTP, IP-HTTPS

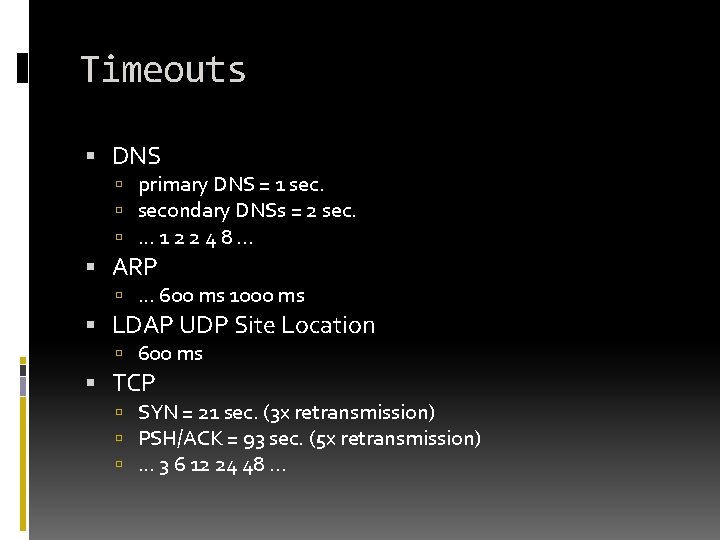
Timeouts DNS primary DNS = 1 secondary DNSs = 2 sec. . . . 1 2 2 4 8. . . ARP . . . 600 ms 1000 ms LDAP UDP Site Location 600 ms TCP SYN = 21 sec. (3 x retransmission) PSH/ACK = 93 sec. (5 x retransmission) . . . 3 6 12 24 48. . .

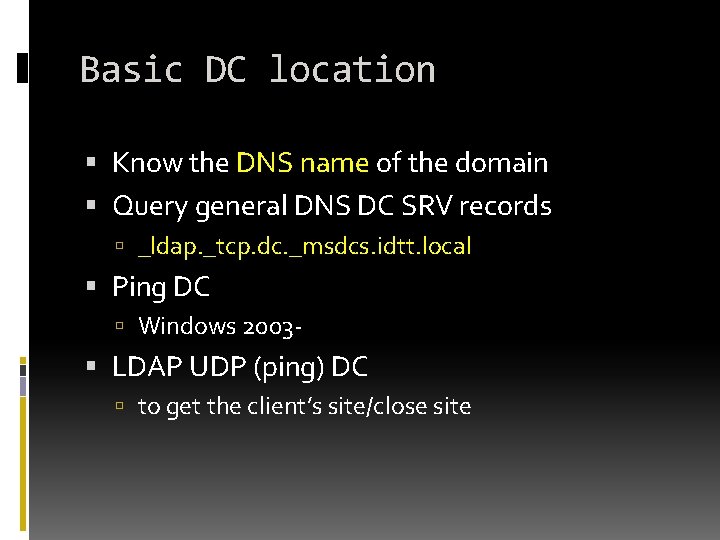
Basic DC location Know the DNS name of the domain Query general DNS DC SRV records _ldap. _tcp. dc. _msdcs. idtt. local Ping DC Windows 2003 - LDAP UDP (ping) DC to get the client’s site/close site

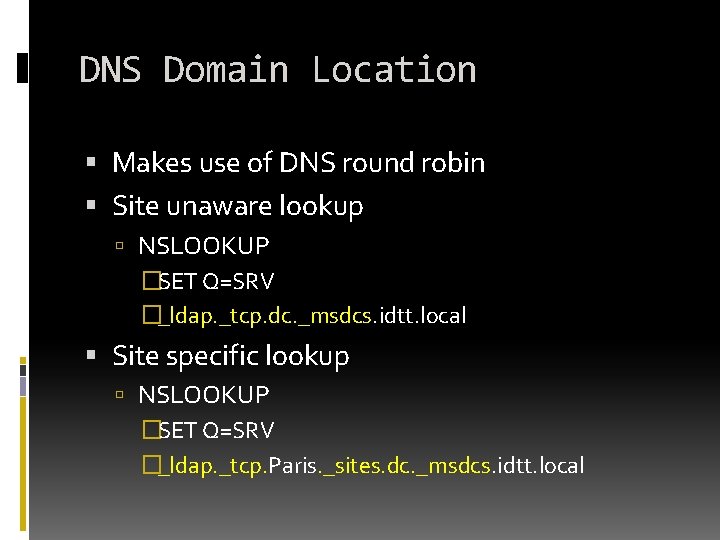
DNS Domain Location Makes use of DNS round robin Site unaware lookup NSLOOKUP �SET Q=SRV �_ldap. _tcp. dc. _msdcs. idtt. local Site specific lookup NSLOOKUP �SET Q=SRV �_ldap. _tcp. Paris. _sites. dc. _msdcs. idtt. local

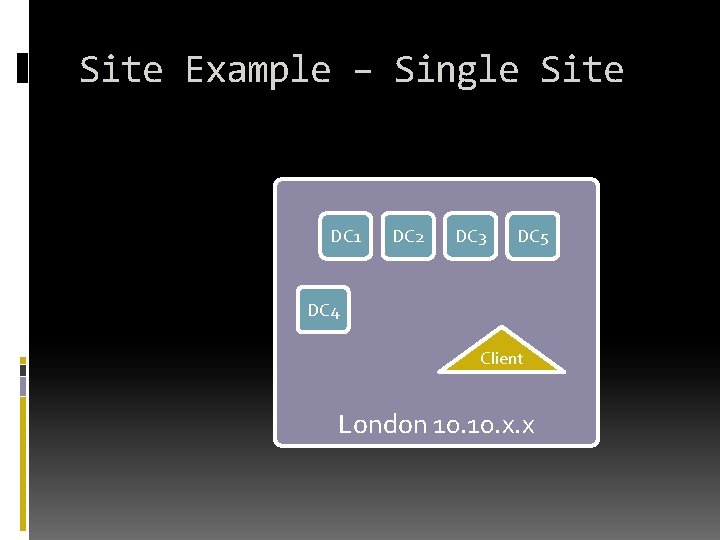
Site Example – Single Site DC 1 DC 2 DC 3 DC 5 DC 4 Client London 10. x. x

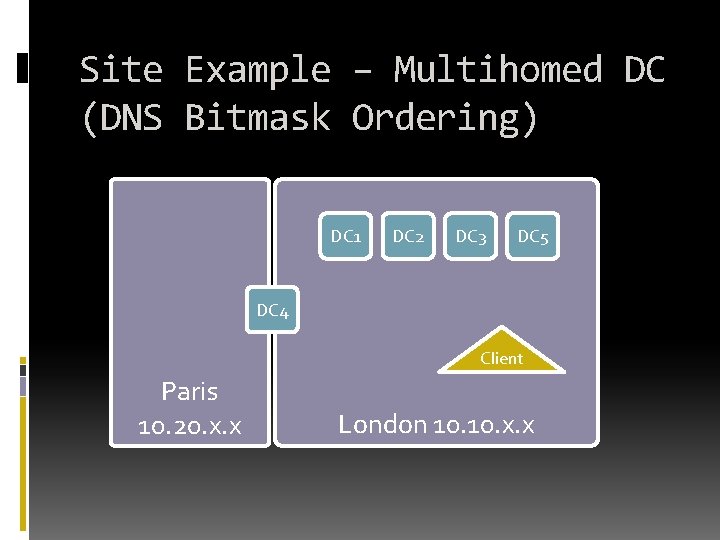
Site Example – Multihomed DC (DNS Bitmask Ordering) DC 1 DC 2 DC 3 DC 5 DC 4 Client Paris 10. 20. x. x London 10. x. x

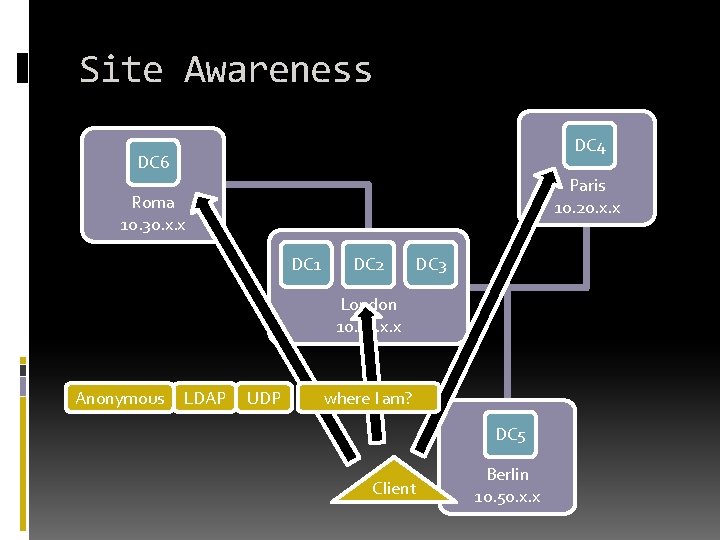
Site Awareness DC 4 DC 6 Paris 10. 20. x. x Roma 10. 30. x. x DC 1 DC 2 DC 3 London 10. x. x Anonymous LDAP UDP where I am? DC 5 Client Berlin 10. 50. x. x

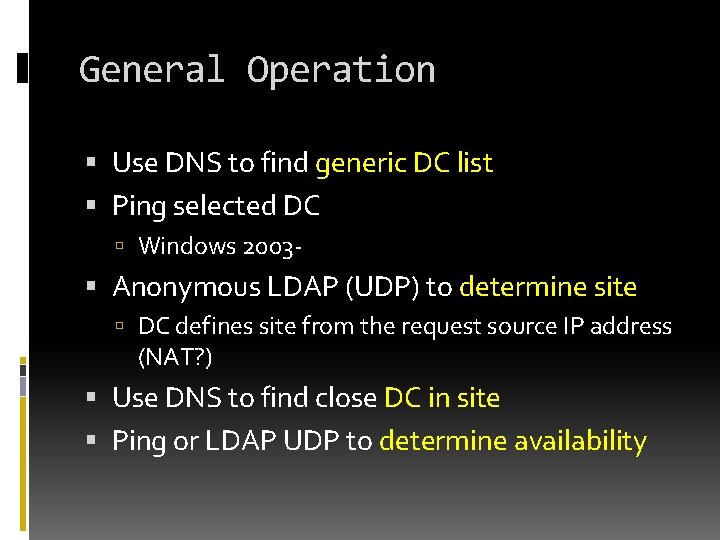
General Operation Use DNS to find generic DC list Ping selected DC Windows 2003 - Anonymous LDAP (UDP) to determine site DC defines site from the request source IP address (NAT? ) Use DNS to find close DC in site Ping or LDAP UDP to determine availability

DC Locator Net. Logon Service nltest /sc_query: idtt no network access nltest /sc_verify: idtt tries to authenticate with the DC nltest /sc_reset: idtt always performs new DNS lookup nltest /dsgetsite anonymous query against selected DC

DFS Client (MUP) Multiple UNC provider (MUP) driver Determines its own DFS server referrals obtains the list of DFS root servers from AD using the default DC from Netlogon SYSVOL may be accessed from a different DC DFSUTIL /PKTINFO Windows Server 2003/Windows XP DFSUTIL CACHE REFERRAL Windows Server 2008/Windows Vista

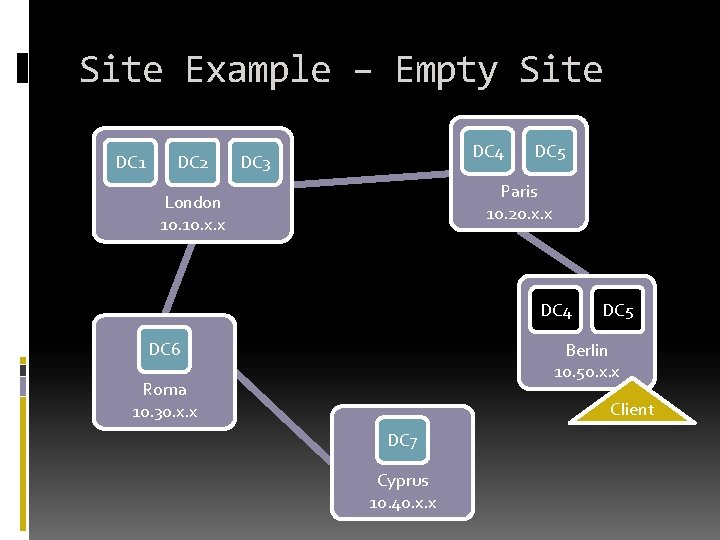
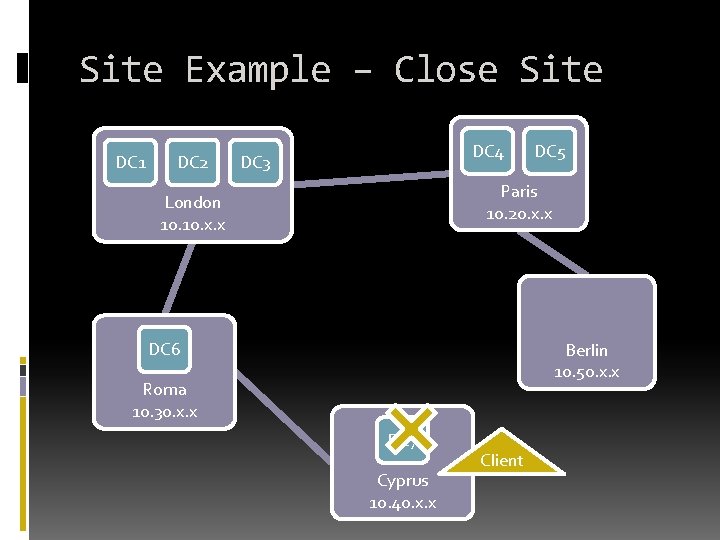
Site Example – Empty Site DC 1 DC 2 DC 4 DC 3 DC 5 Paris 10. 20. x. x London 10. x. x DC 4 DC 6 DC 5 Berlin 10. 50. x. x Roma 10. 30. x. x Client DC 7 Cyprus 10. 40. x. x

Automatic Site Coverage Each DC registers itself for its neighboring empty sites HKLMSystemCurrent. Control. SetServicesN etlogon Auto. Site. Coverage = DWORD = 1/0 GPO: Sites Covered by the DC Locator DNS SRV Records

Active Directory Troubleshooting MISPLACED OR CONFUSED CLIENTS

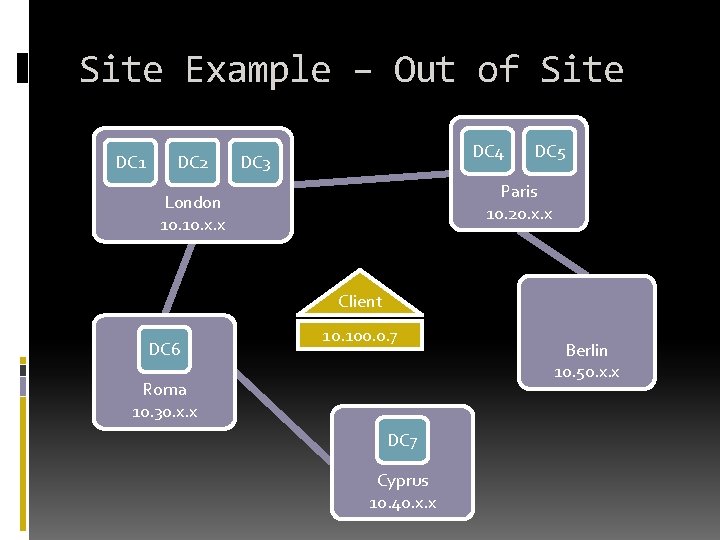
Site Example – Out of Site DC 1 DC 2 DC 4 DC 3 DC 5 Paris 10. 20. x. x London 10. x. x Client DC 6 10. 100. 0. 7 Roma 10. 30. x. x DC 7 Cyprus 10. 40. x. x Berlin 10. 50. x. x

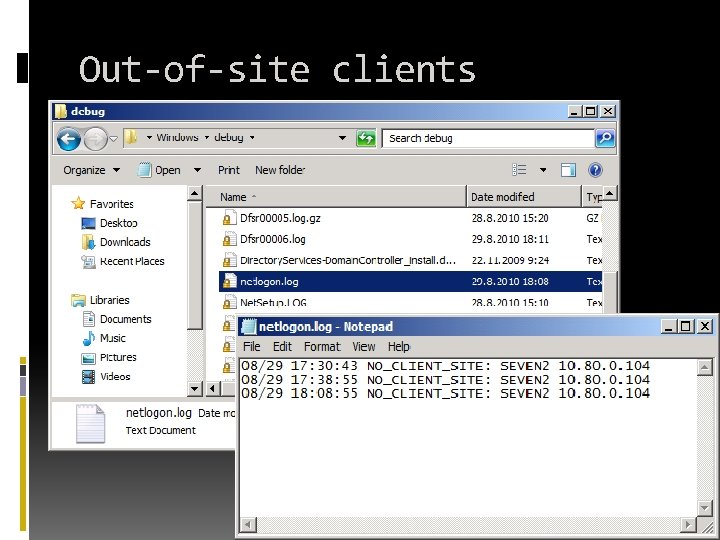
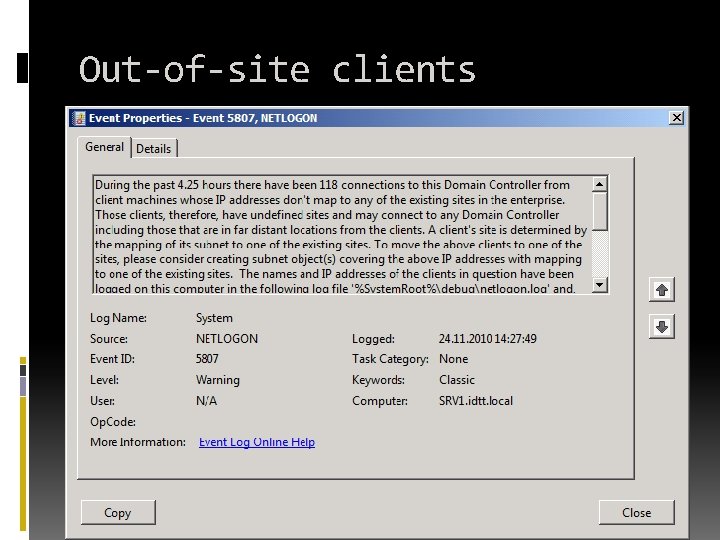
Out-of-site clients

Out-of-site clients

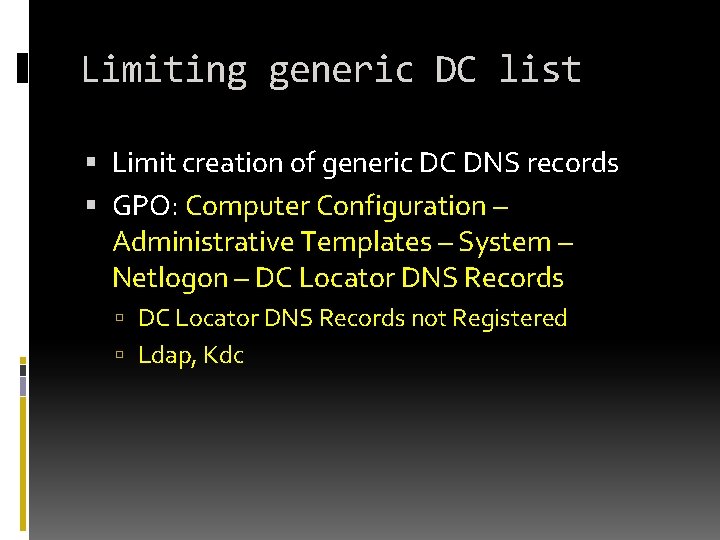
Limiting generic DC list Limit creation of generic DC DNS records GPO: Computer Configuration – Administrative Templates – System – Netlogon – DC Locator DNS Records not Registered Ldap, Kdc

DC Stickiness When one close selected, client sticks to it even when moved into a different site must reset secure channel Force rediscovery interval GPO Vista+ hotfix for Windows XP also registry value Force. Rediscovery. Interval

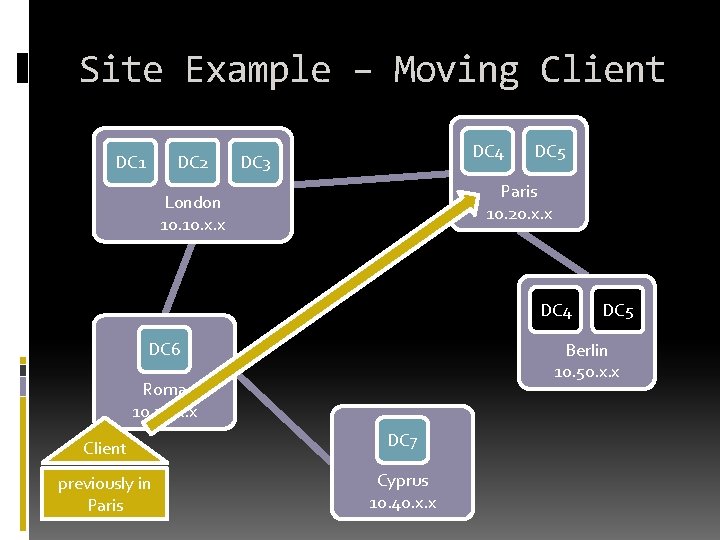
Site Example – Moving Client DC 1 DC 2 DC 4 DC 3 DC 5 Paris 10. 20. x. x London 10. x. x DC 4 DC 6 DC 5 Berlin 10. 50. x. x Roma 10. 30. x. x Client DC 7 previously in Paris Cyprus 10. 40. x. x

Active Directory Troubleshooting CLIENT FAILOVER

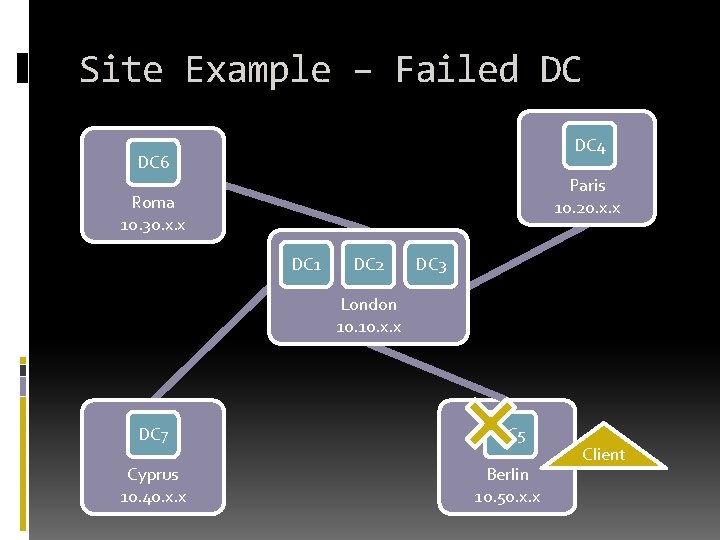
Site Example – Failed DC DC 4 DC 6 Paris 10. 20. x. x Roma 10. 30. x. x DC 1 DC 2 DC 3 London 10. x. x DC 7 DC 5 Cyprus 10. 40. x. x Berlin 10. 50. x. x Client

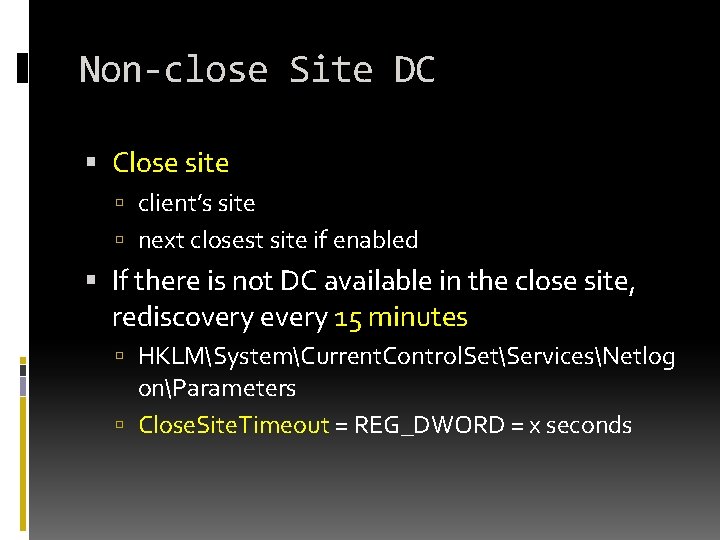
Non-close Site DC Close site client’s site next closest site if enabled If there is not DC available in the close site, rediscovery every 15 minutes HKLMSystemCurrent. Control. SetServicesNetlog onParameters Close. Site. Timeout = REG_DWORD = x seconds

Site Example – Close Site DC 1 DC 2 DC 4 DC 3 DC 5 Paris 10. 20. x. x London 10. x. x DC 6 Berlin 10. 50. x. x Roma 10. 30. x. x DC 7 Cyprus 10. 40. x. x Client

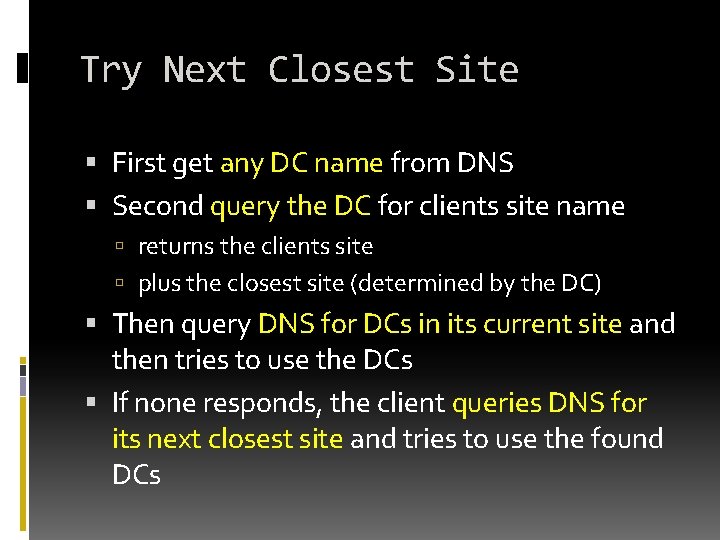
Try Next Closest Site First get any DC name from DNS Second query the DC for clients site name returns the clients site plus the closest site (determined by the DC) Then query DNS for DCs in its current site and then tries to use the DCs If none responds, the client queries DNS for its next closest site and tries to use the found DCs

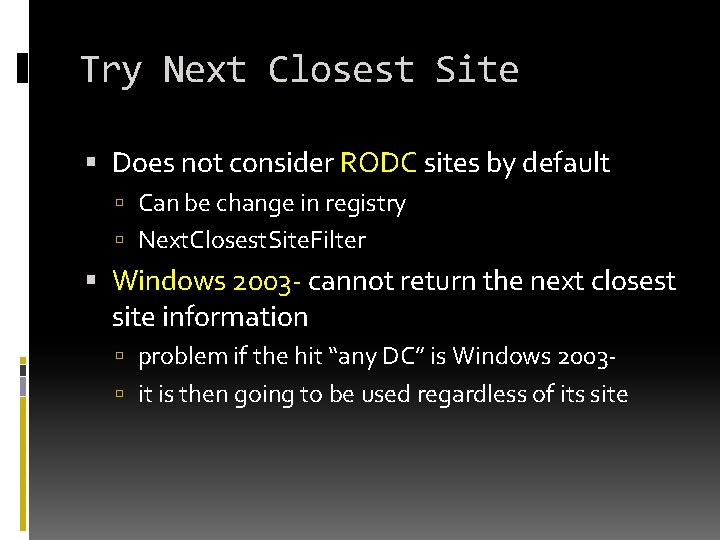
Try Next Closest Site Does not consider RODC sites by default Can be change in registry Next. Closest. Site. Filter Windows 2003 - cannot return the next closest site information problem if the hit “any DC” is Windows 2003 it is then going to be used regardless of its site

Client Rules Recap Windows 2003 In current site In any site Windows Vista+ with Next closest site In current site In the closest site In any site If the client is out of any site, find any dc consider creating subnets for VPNs etc.

Active Directory Client Interactions SITE DESIGN

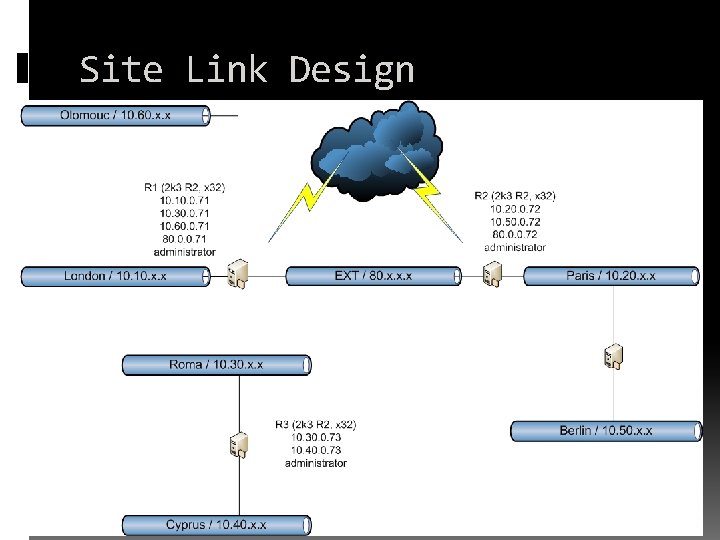
Site Link Design

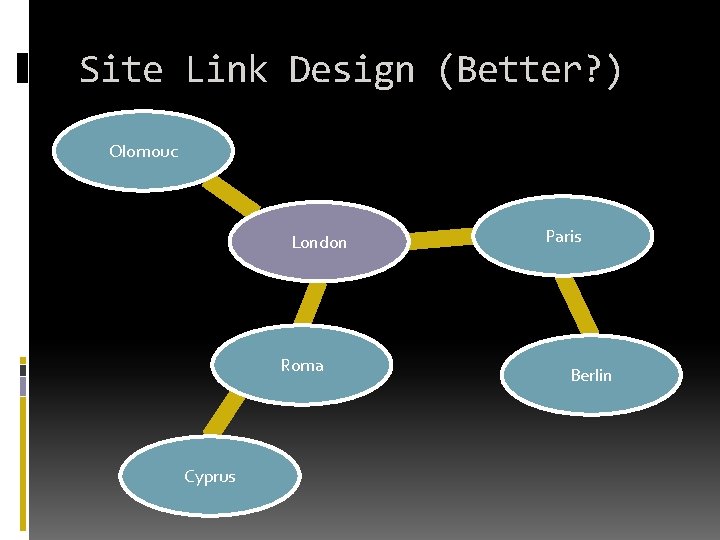
Site Link Design (Better? ) Olomouc London Roma Cyprus Paris Berlin

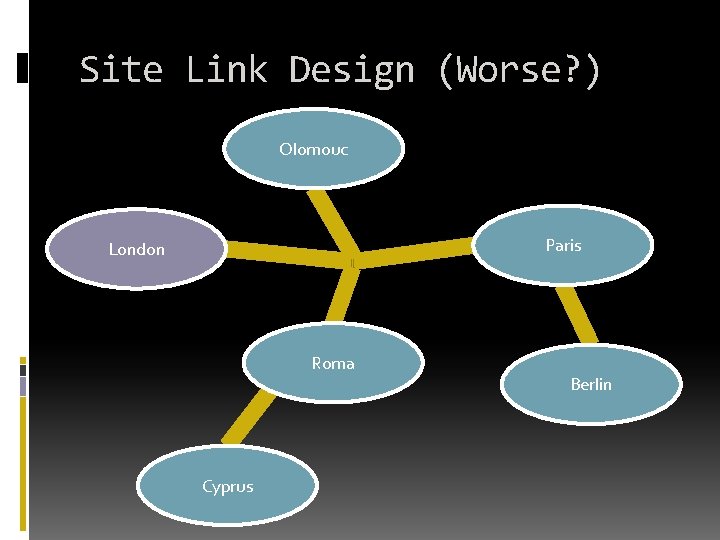
Site Link Design (Worse? ) Olomouc Paris London Roma Cyprus Berlin

Active Directory Client Interactions DNS INTEGRATION

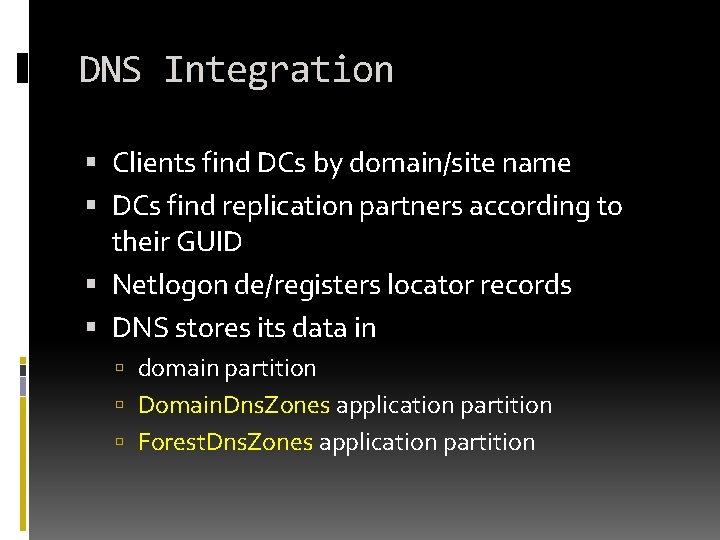
DNS Integration Clients find DCs by domain/site name DCs find replication partners according to their GUID Netlogon de/registers locator records DNS stores its data in domain partition Domain. Dns. Zones application partition Forest. Dns. Zones application partition

Netlogon de/registration Netlogon registers its own records at startup and deregisters them at shutdown requires DNS registration enabled on at least one network adapter %windir%System 32Confignetlogon. dns It does not touch others’ records Autosite coverage turned on by default

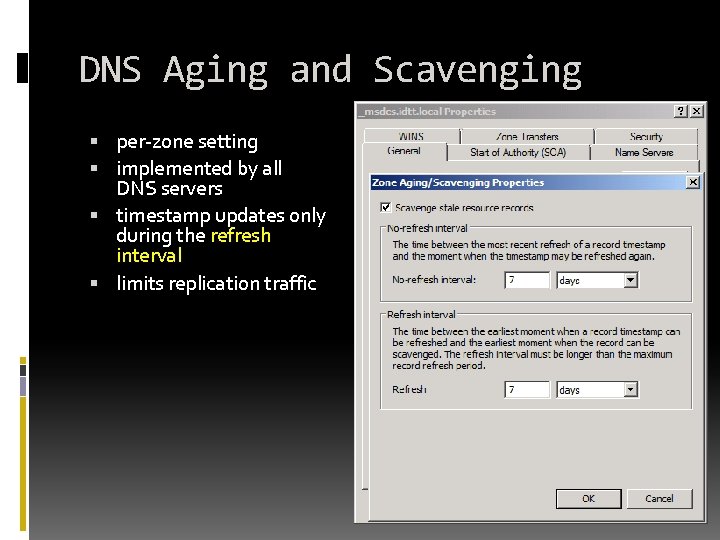
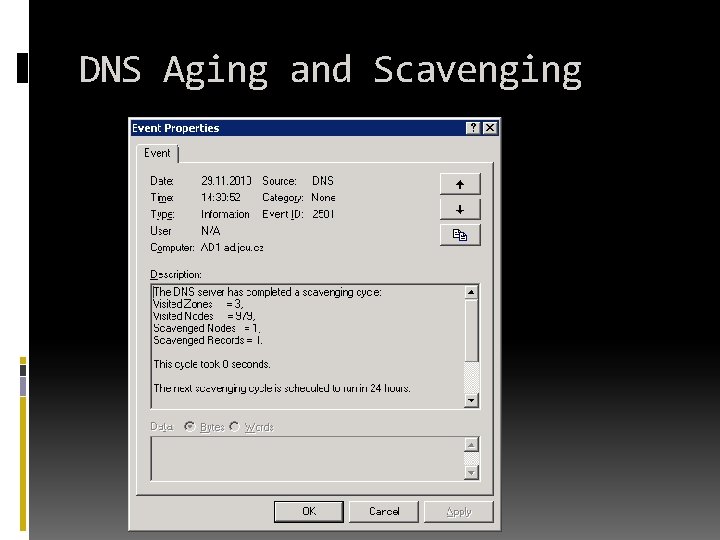
AD Integrated Zones Offer Secure Dynamic Update Timestamping trimmed to whole hour Aging and scavenging records deleted by default between 14 -21 days of their age

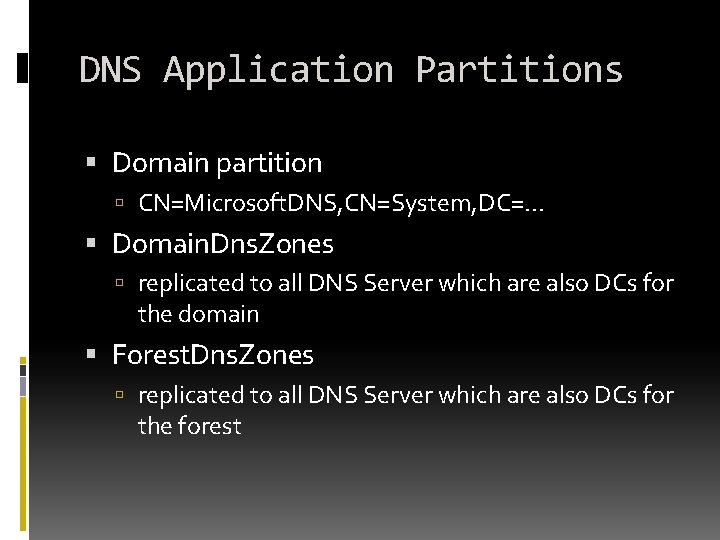
DNS Application Partitions Domain partition CN=Microsoft. DNS, CN=System, DC=. . . Domain. Dns. Zones replicated to all DNS Server which are also DCs for the domain Forest. Dns. Zones replicated to all DNS Server which are also DCs for the forest

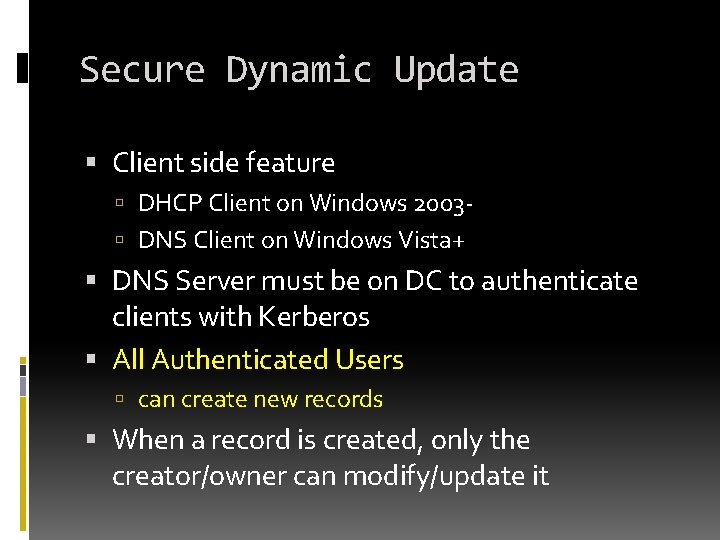
Secure Dynamic Update Client side feature DHCP Client on Windows 2003 DNS Client on Windows Vista+ DNS Server must be on DC to authenticate clients with Kerberos All Authenticated Users can create new records When a record is created, only the creator/owner can modify/update it

Secure Dynamic Updates done regularly by clients every hour by default Default TTL is 20 minutes Disable DHCP dynamic updates insecure!

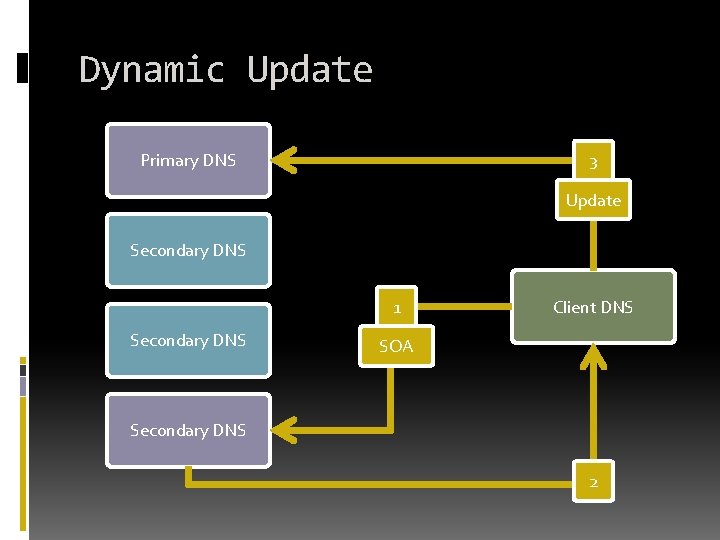
Dynamic Update Primary DNS 3 Update Secondary DNS 1 Secondary DNS Client DNS SOA Secondary DNS 2

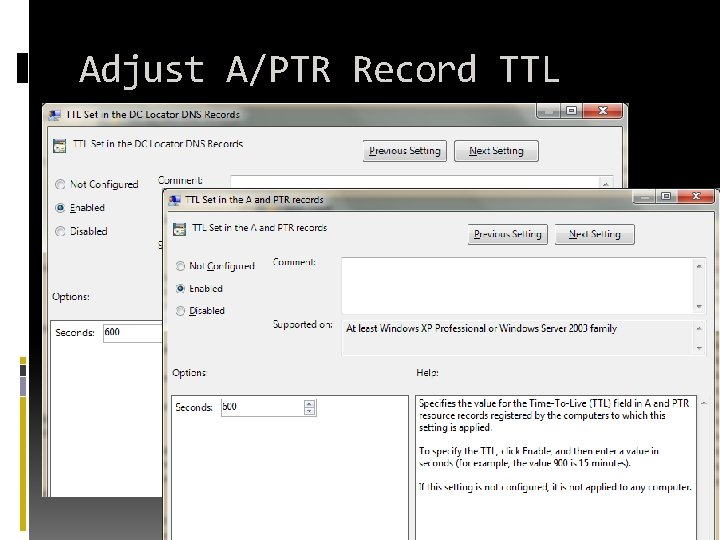
Adjust A/PTR Record TTL

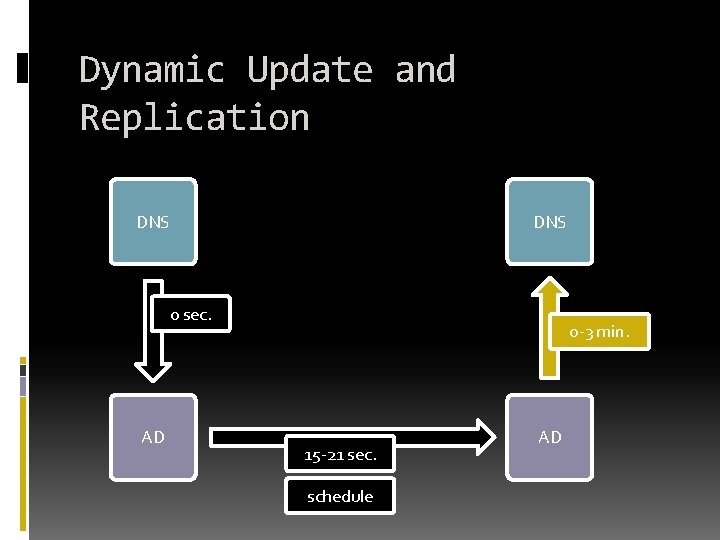
Dynamic Update and Replication DNS 0 sec. AD 0 -3 min. 15 -21 sec. schedule AD

Dynamic Update and Replication

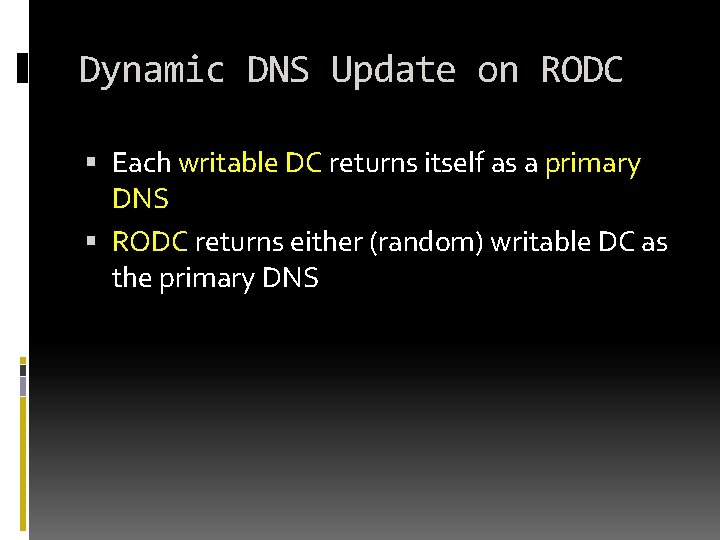
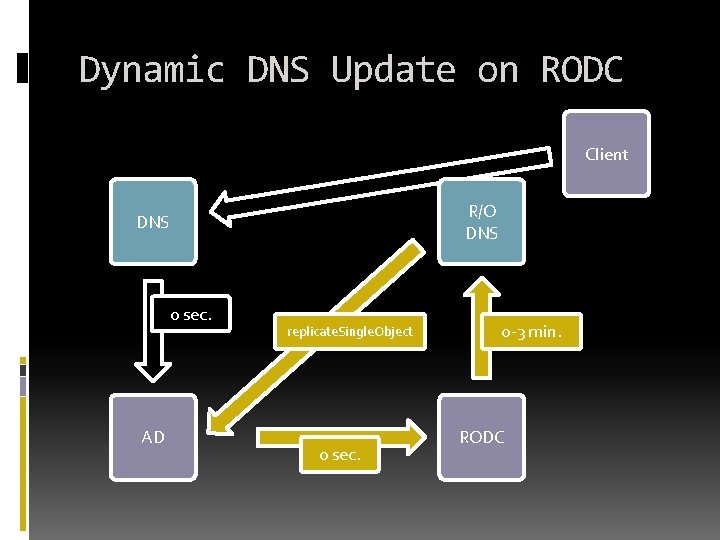
Dynamic DNS Update on RODC Each writable DC returns itself as a primary DNS RODC returns either (random) writable DC as the primary DNS

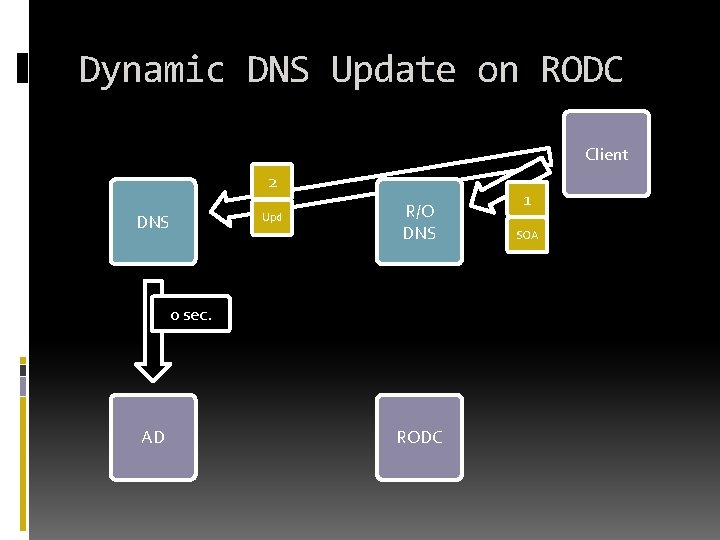
Dynamic DNS Update on RODC Client 2 DNS Upd R/O DNS 0 sec. AD RODC 1 SOA

Dynamic DNS Update on RODC Client R/O DNS 0 sec. AD replicate. Single. Object 0 sec. 0 -3 min. RODC

Time stamping/Aging Record Created timestamp trimmed to whole hour No-refresh period starts by default 7 days timestamp does not change if the record does not change Refresh period follows by default next 7 days timestamp gets updated at the first update

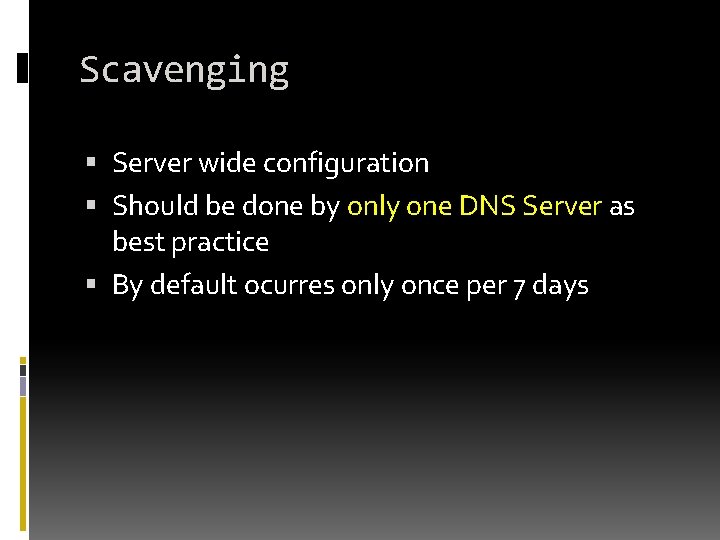
Scavenging Server wide configuration Should be done by only one DNS Server as best practice By default ocurres only once per 7 days

DNS Aging and Scavenging per-zone setting implemented by all DNS servers timestamp updates only during the refresh interval limits replication traffic

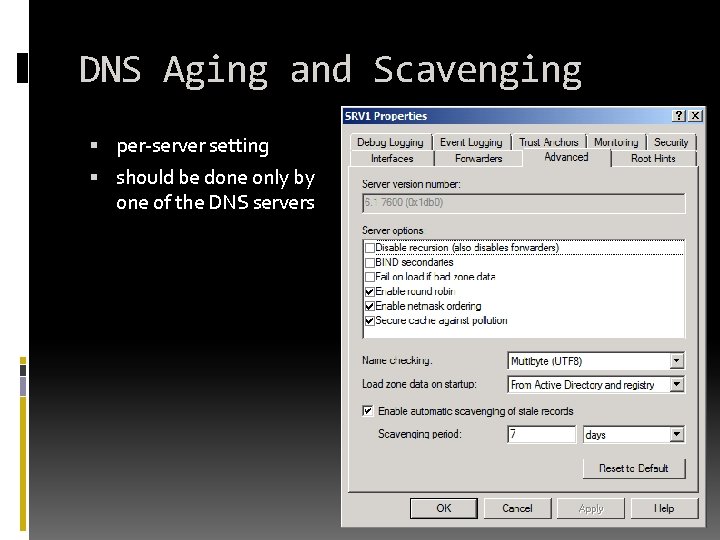
DNS Aging and Scavenging per-server setting should be done only by one of the DNS servers

DNS Aging and Scavenging

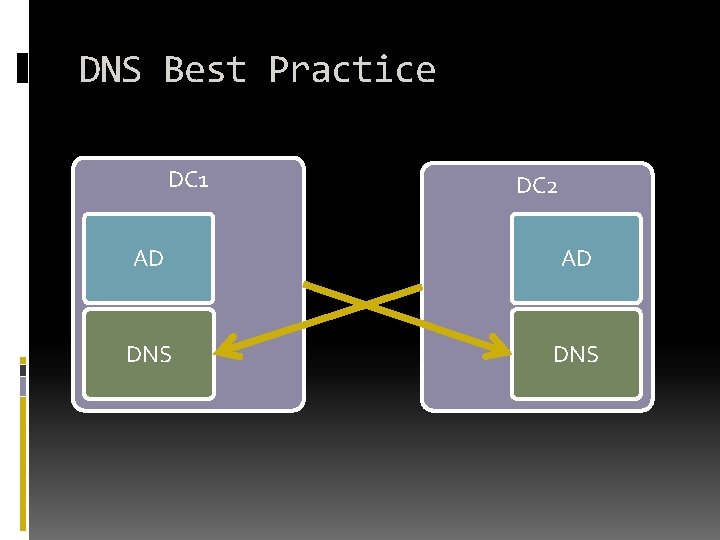
DNS Best Practice DC 1 DC 2 AD AD DNS

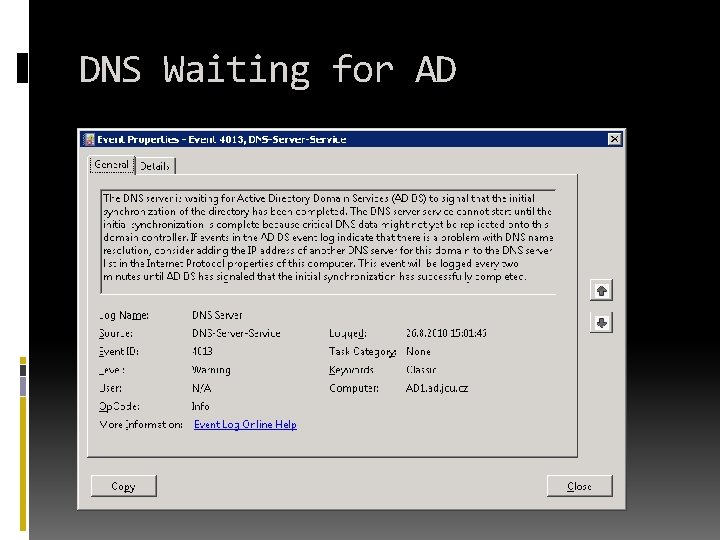
DNS Waiting for AD

DNS Best-Practice Reasons Faster boot time without errors and timeouts Deregistration at shutdown is recorded in live DNS Server would have problems replicate if sent into shutting -down DC

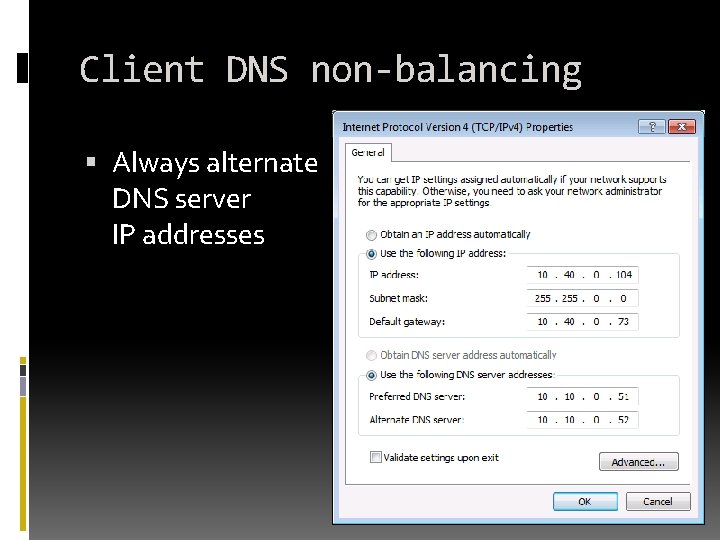
Client DNS balancing Clients do not balance DNS servers queries/updates use the first one always if possible DHCP server does not use round robin Configuration must be done “manually” manual on servers more DHCP scopes for clients

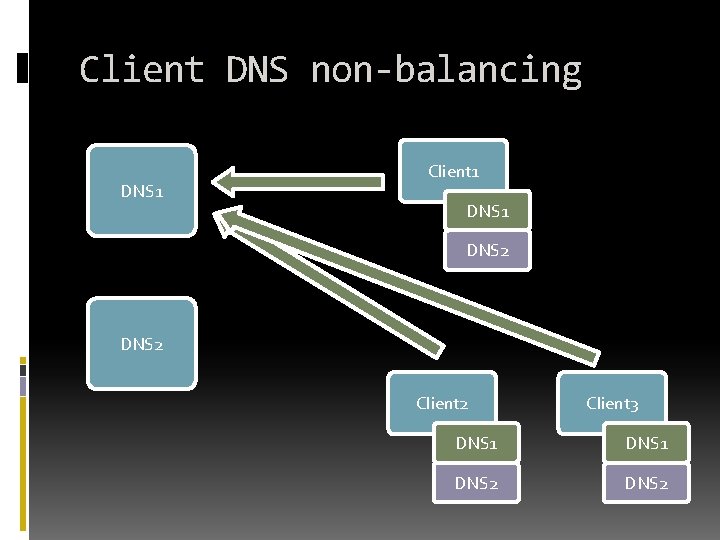
Client DNS non-balancing Always alternate DNS server IP addresses

Client DNS non-balancing DNS 1 Client 1 DNS 2 Client 3 DNS 1 DNS 2

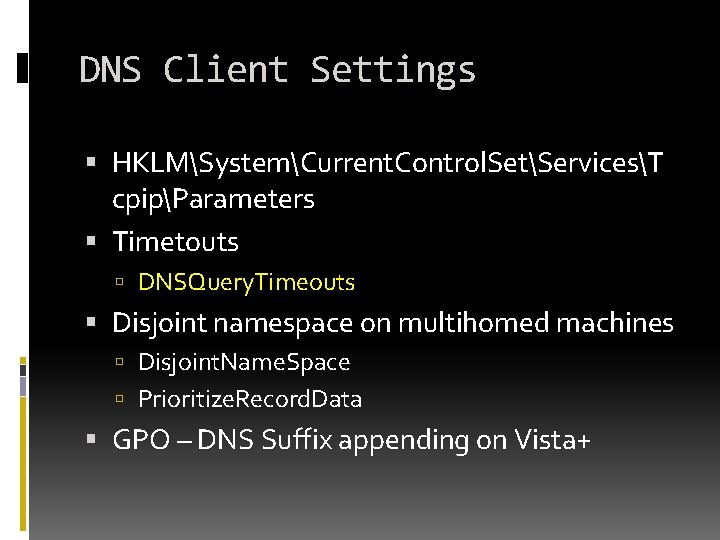
DNS Client Settings HKLMSystemCurrent. Control. SetServicesT cpipParameters Timetouts DNSQuery. Timeouts Disjoint namespace on multihomed machines Disjoint. Name. Space Prioritize. Record. Data GPO – DNS Suffix appending on Vista+

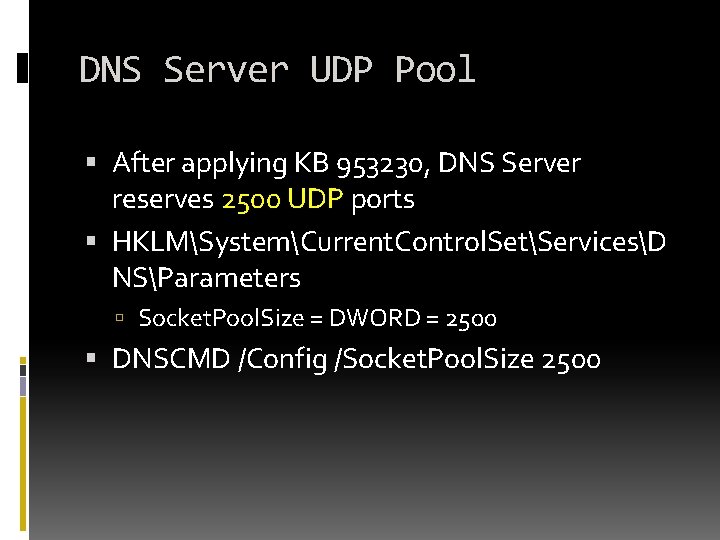
DNS Server UDP Pool After applying KB 953230, DNS Server reserves 2500 UDP ports HKLMSystemCurrent. Control. SetServicesD NSParameters Socket. Pool. Size = DWORD = 2500 DNSCMD /Config /Socket. Pool. Size 2500

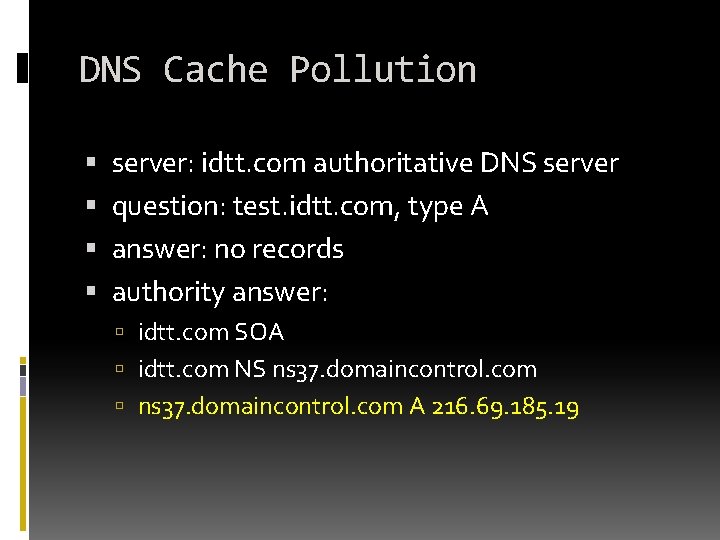
DNS Cache Pollution server: idtt. com authoritative DNS server question: test. idtt. com, type A answer: no records authority answer: idtt. com SOA idtt. com NS ns 37. domaincontrol. com A 216. 69. 185. 19

Active Directory Troubleshooting GENERAL BEST PRACTICE

General Best Practice Create and assign subnets for any possible client IP Limit the general (site unaware) DNS registration of DCs Enable Try next closest site and Force rediscovery options Enable DNS Aging and Scavenging Alter clients’ DNS settings to rotate the DNS server addresses

Ondřej Ševeček | GOPAS a. s. | MCM: Directory Services | MVP: Enterprise Security | ondrej@sevecek. com | www. sevecek. com | THANK YOU!
 Eveek
Eveek Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Stakeholder classification
Stakeholder classification Ondej
Ondej Mcm authenticator
Mcm authenticator Minimo comune denominatore
Minimo comune denominatore Mcm package
Mcm package Recarga mcm
Recarga mcm Mdm vs mam vs mcm
Mdm vs mam vs mcm Anticyclisch budgetteren
Anticyclisch budgetteren Creature framework mcm
Creature framework mcm Quanti sono i multipli di 5
Quanti sono i multipli di 5 Mandiri cash manajemen
Mandiri cash manajemen Ecuaciones algebraicas 4 eso
Ecuaciones algebraicas 4 eso Mcm audience
Mcm audience Mcm/icm
Mcm/icm Mcm
Mcm Mcm 2012
Mcm 2012 Mcm de expresiones algebraicas
Mcm de expresiones algebraicas Anomaly mcm
Anomaly mcm Factores primos lineales de un polinomio
Factores primos lineales de un polinomio 3150-mcm
3150-mcm Master chemical mechanism
Master chemical mechanism Rdo mcm
Rdo mcm Algoritmo de euclides
Algoritmo de euclides Cmc and mcm
Cmc and mcm Mcm agenda
Mcm agenda Active directory disaster recovery best practices
Active directory disaster recovery best practices General graph directory
General graph directory Cladogram
Cladogram Administering active directory
Administering active directory Symbolic link 삭제
Symbolic link 삭제 Distributed dbms architecture ppt
Distributed dbms architecture ppt Hicsis
Hicsis Privileged access workstations
Privileged access workstations Active directory fundamentals
Active directory fundamentals Fat32 root directory
Fat32 root directory Jndi name
Jndi name What was directory
What was directory Active directory replication troubleshooting
Active directory replication troubleshooting Active directory grundlagen
Active directory grundlagen Usb root directory
Usb root directory Adyen directory lookup
Adyen directory lookup Unix directory tree
Unix directory tree Active directory alapok
Active directory alapok Jjeds johnson and johnson
Jjeds johnson and johnson Wisconsin one stop business portal
Wisconsin one stop business portal Directory file in unix
Directory file in unix Rejestr systemu windows
Rejestr systemu windows Mmu staff directory icems
Mmu staff directory icems Umass logon
Umass logon Active directory alapok
Active directory alapok Njhealth.com
Njhealth.com Unc active directory
Unc active directory Ospital ng maynila directory
Ospital ng maynila directory Gestione utenti active directory
Gestione utenti active directory Active directory
Active directory Mastercard track trade directory
Mastercard track trade directory Pakistan importers directory
Pakistan importers directory Napster directory
Napster directory Active directory dynamic access control
Active directory dynamic access control Owasp vulnerable web applications directory
Owasp vulnerable web applications directory Iowa nrcs directory
Iowa nrcs directory How to create a directory in python
How to create a directory in python Dasny directory
Dasny directory Active directory two way trust
Active directory two way trust Jeus8 deploy 오류
Jeus8 deploy 오류 Exchange best practice analyzer
Exchange best practice analyzer Cii directory
Cii directory Introduction to active directory
Introduction to active directory Alex karasulu
Alex karasulu Samba active directory domain controller
Samba active directory domain controller Site topology
Site topology Exfat 할당 단위 크기
Exfat 할당 단위 크기 Advantages and disadvantages of active directory
Advantages and disadvantages of active directory Active directory 原理
Active directory 原理 Ibm software group
Ibm software group Lab 5: manage active directory accounts (module 4)
Lab 5: manage active directory accounts (module 4) Sas certification registration
Sas certification registration Idaho dbe directory
Idaho dbe directory Active directory cleanup tools
Active directory cleanup tools Cs342 bilkent
Cs342 bilkent Active directory design document
Active directory design document Active directory consolidation best practices
Active directory consolidation best practices Walsall social services
Walsall social services