Ondej eveek GOPAS a s MCM Directory Services










- Slides: 37

Ondřej Ševeček | GOPAS a. s. | MCM: Directory Services | MVP: Enterprise Security | ondrej@sevecek. com | www. sevecek. com | REMOTE ACCESS TECHNOLOGIES

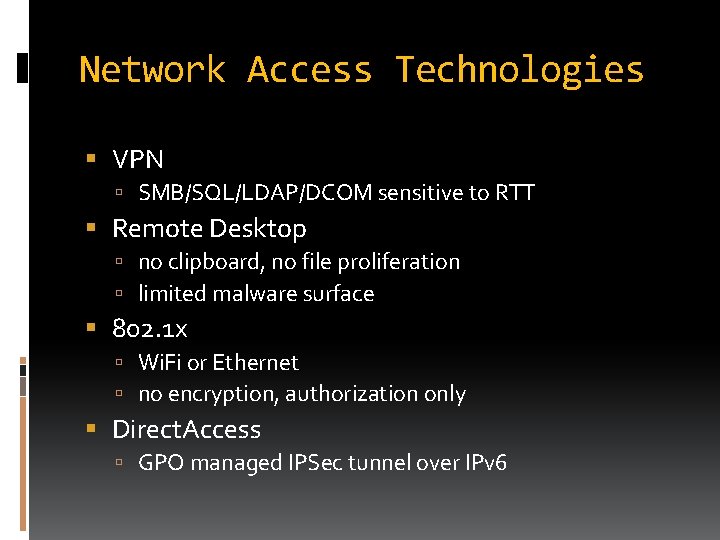
Network Access Technologies VPN SMB/SQL/LDAP/DCOM sensitive to RTT Remote Desktop no clipboard, no file proliferation limited malware surface 802. 1 x Wi. Fi or Ethernet no encryption, authorization only Direct. Access GPO managed IPSec tunnel over IPv 6

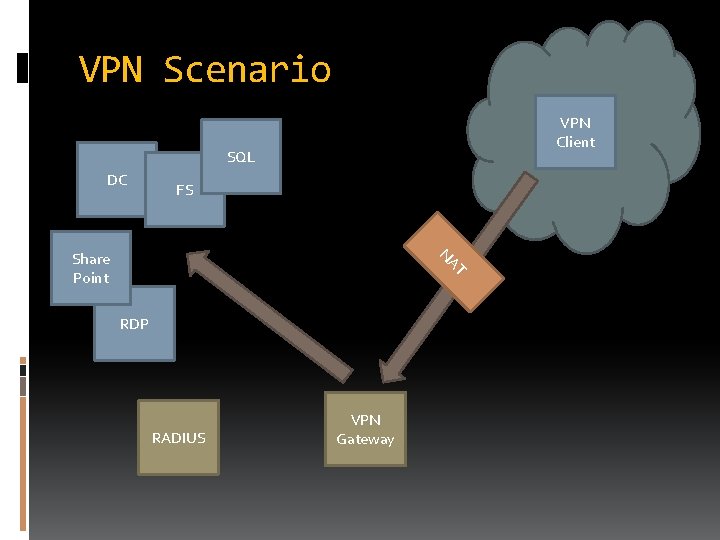
VPN Scenario VPN Client SQL DC FS T NA Share Point RDP RADIUS VPN Gateway

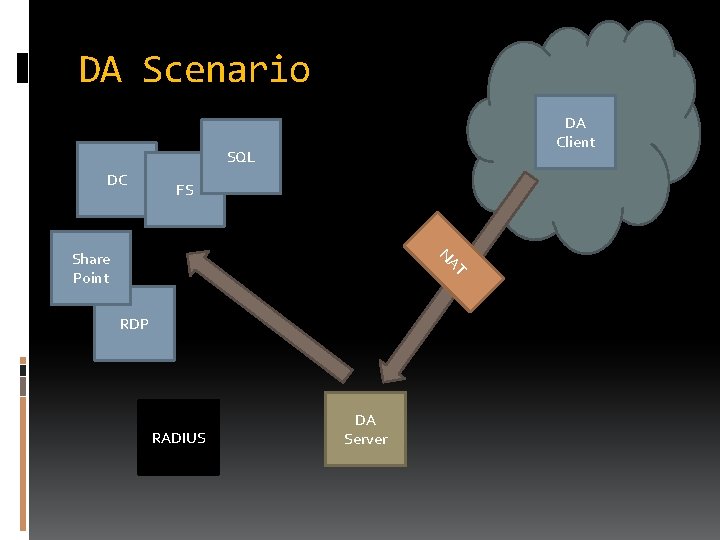
DA Scenario DA Client SQL DC FS T NA Share Point RDP RADIUS DA Server

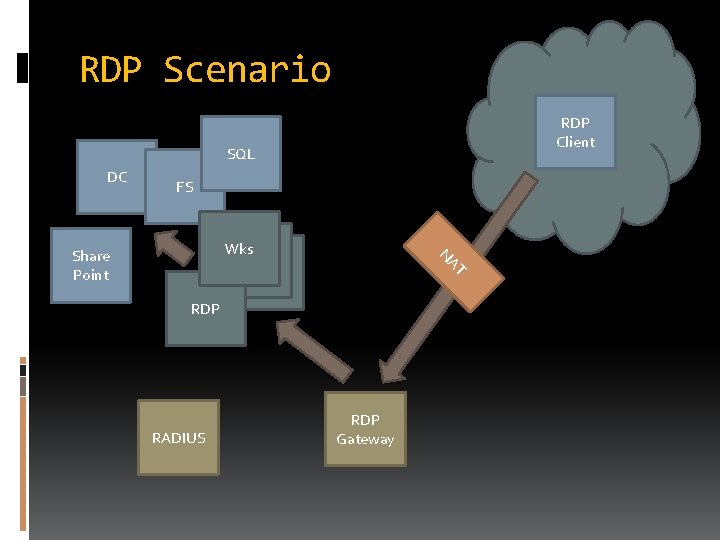
RDP Scenario RDP Client SQL DC FS T NA Wks Wks Share Point RDP RADIUS RDP Gateway

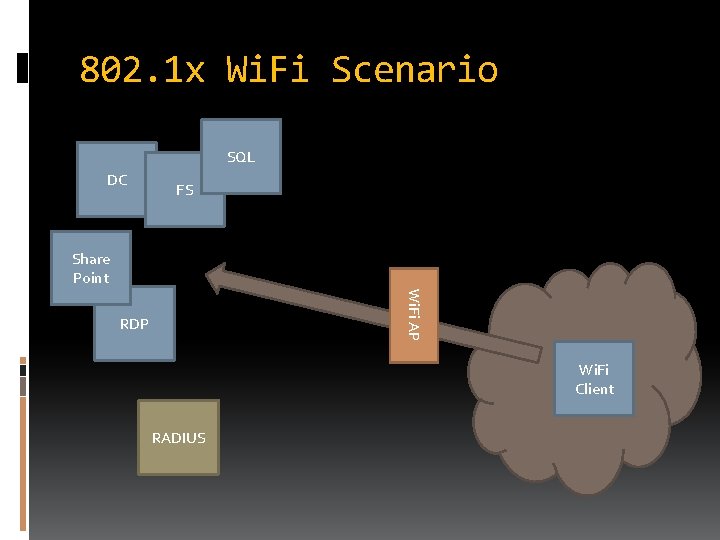
802. 1 x Wi. Fi Scenario SQL DC FS Share Point Wi. Fi AP RDP Wi. Fi Client RADIUS

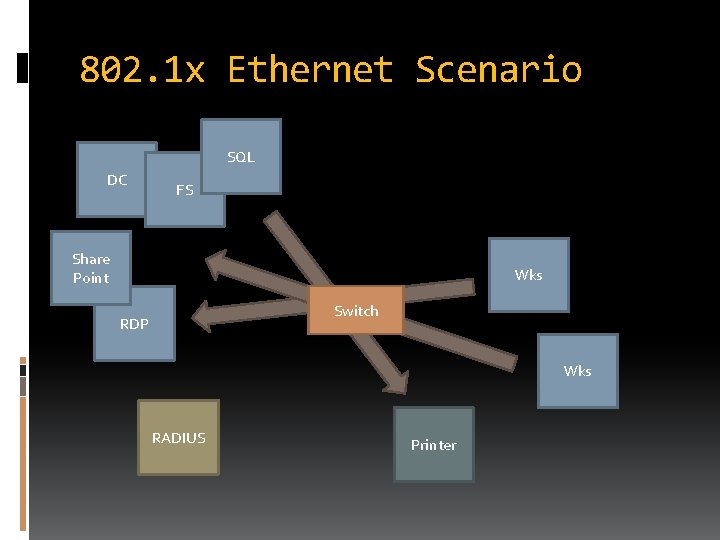
802. 1 x Ethernet Scenario SQL DC FS Share Point Wks Switch RDP Wks RADIUS Printer

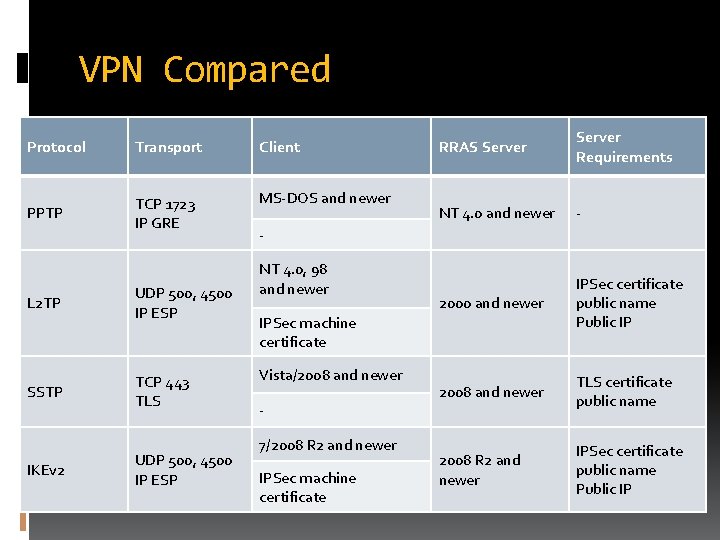
VPN Compared Protocol Transport Client PPTP TCP 1723 IP GRE MS-DOS and newer L 2 TP UDP 500, 4500 IP ESP SSTP TCP 443 TLS IKEv 2 UDP 500, 4500 IP ESP RRAS Server Requirements NT 4. 0 and newer - 2000 and newer IPSec certificate public name Public IP 2008 and newer TLS certificate public name 2008 R 2 and newer IPSec certificate public name Public IP NT 4. 0, 98 and newer IPSec machine certificate Vista/2008 and newer 7/2008 R 2 and newer IPSec machine certificate

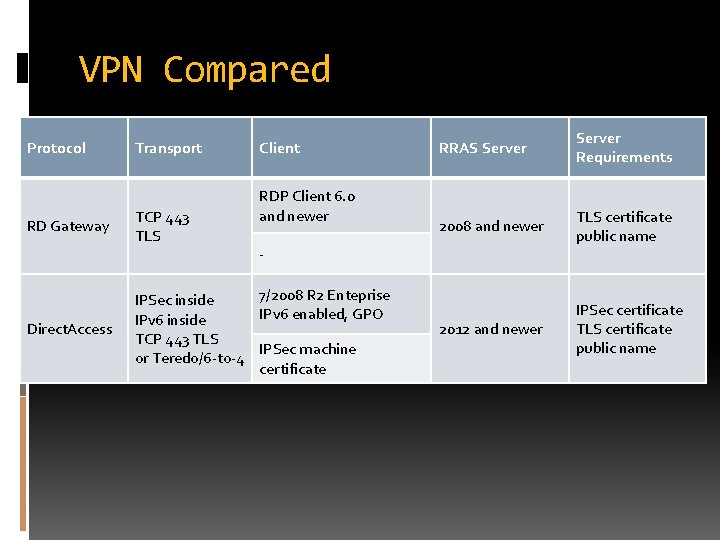
VPN Compared Protocol RD Gateway Direct. Access Transport TCP 443 TLS Client RDP Client 6. 0 and newer RRAS Server Requirements 2008 and newer TLS certificate public name 2012 and newer IPSec certificate TLS certificate public name - 7/2008 R 2 Enteprise IPSec inside IPv 6 enabled, GPO IPv 6 inside TCP 443 TLS IPSec machine or Teredo/6 -to-4 certificate

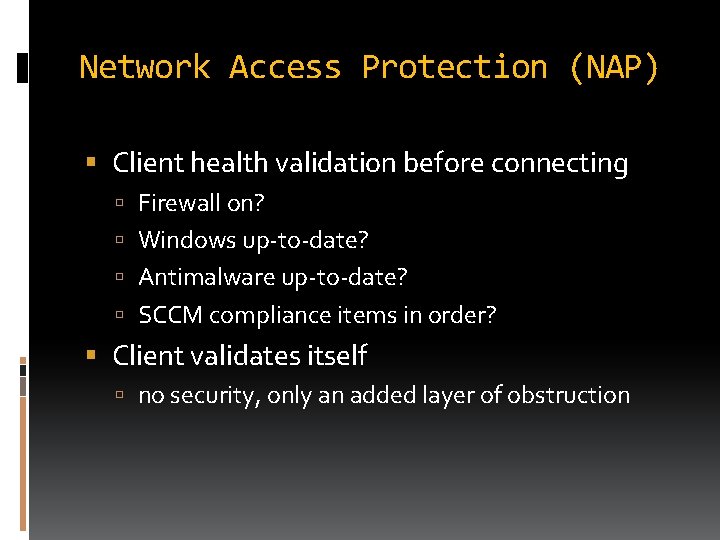
Network Access Protection (NAP) Client health validation before connecting Firewall on? Windows up-to-date? Antimalware up-to-date? SCCM compliance items in order? Client validates itself no security, only an added layer of obstruction

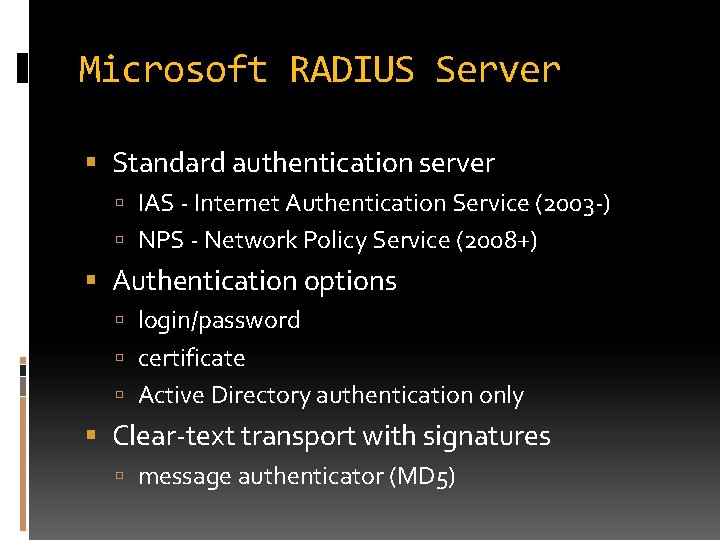
Microsoft RADIUS Server Standard authentication server IAS - Internet Authentication Service (2003 -) NPS - Network Policy Service (2008+) Authentication options login/password certificate Active Directory authentication only Clear-text transport with signatures message authenticator (MD 5)

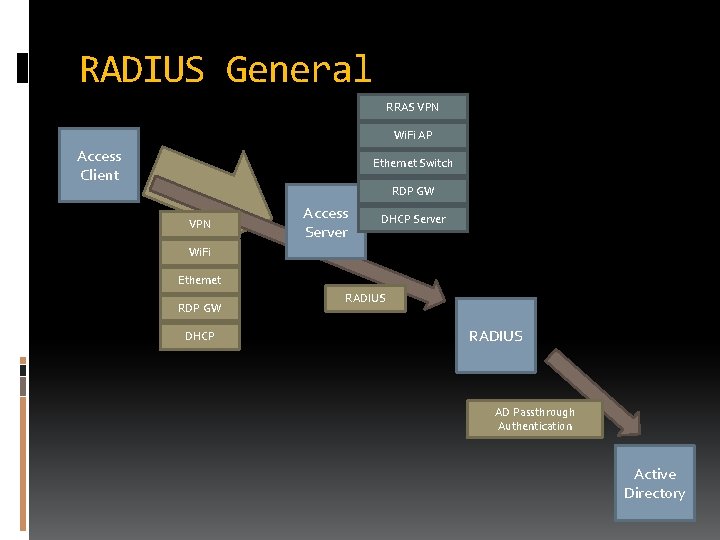
RADIUS General RRAS VPN Wi. Fi AP Access Client Ethernet Switch RDP GW VPN Access Server DHCP Server Wi. Fi Ethernet RDP GW DHCP RADIUS AD Passthrough Authentication Active Directory

RADIUS Terminology RRAS VPN Wi. Fi AP Access Client Ethernet Switch RDP GW VPN RADIUS Client DHCP Server Wi. Fi Ethernet RDP GW DHCP RADIUS AD Passthrough Authentication Active Directory

Authentication Methods PAP, SPAP clear, hash resp. CHAP MD 5 challenge response Store passwords using reversible encryption MS-CHAP NTLM equivalent DES(MD 4) MS-CHAPv 2 NTLMv 2 equivalent plus improvements (time constraints) HMAC-MD 5 (MD 4) EAP-TLS, PEAP client authentication certificate in user profile or in smart/card No authentication sometimes the authentication occurs on the Access Server itself (RD Gateway)

PPTP issues MPPE encryption proprietary, RC 4 Encrypted by authentication products "by" password or "by" certificate PAP/SPAP/EAP travels in clear

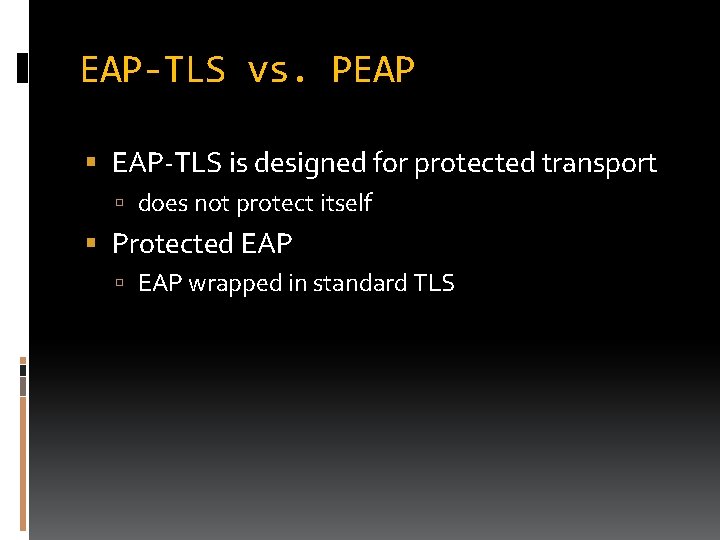
EAP-TLS vs. PEAP EAP-TLS is designed for protected transport does not protect itself Protected EAP wrapped in standard TLS

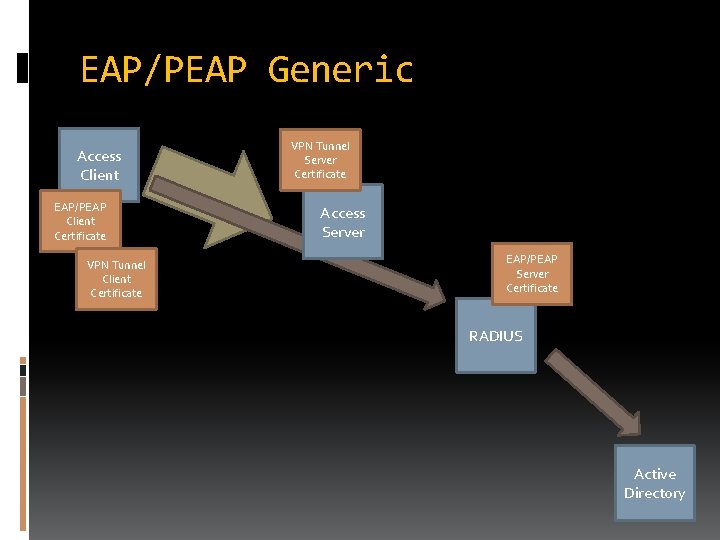
EAP/PEAP Generic Access Client EAP/PEAP Client Certificate VPN Tunnel Server Certificate Access Server EAP/PEAP Server Certificate RADIUS Active Directory

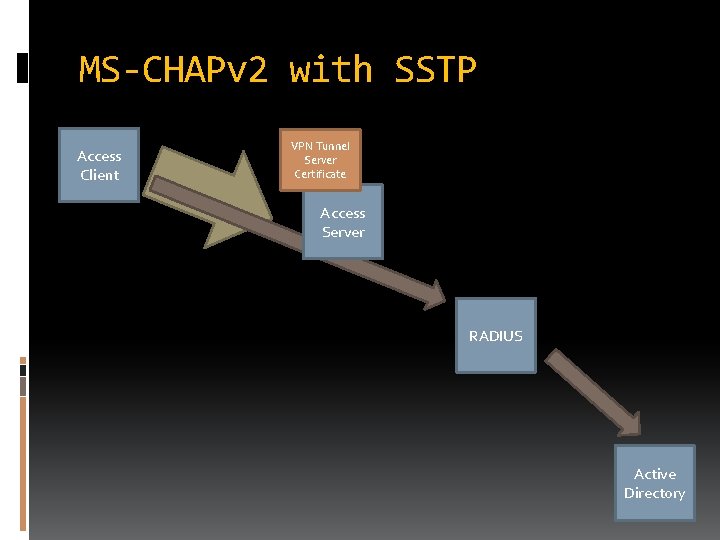
MS-CHAPv 2 with SSTP Access Client VPN Tunnel Server Certificate Access Server RADIUS Active Directory

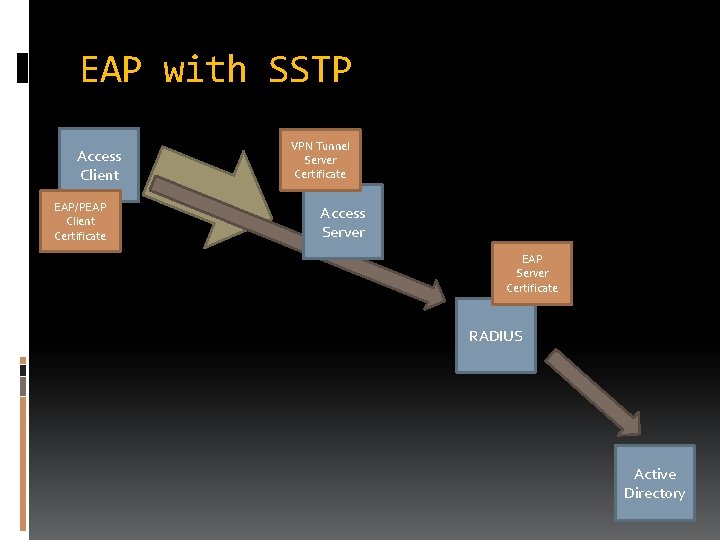
EAP with SSTP Access Client EAP/PEAP Client Certificate VPN Tunnel Server Certificate Access Server EAP Server Certificate RADIUS Active Directory

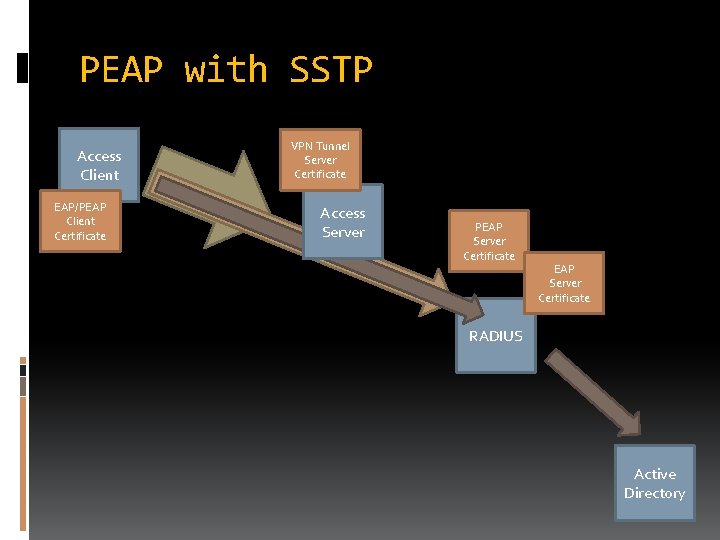
PEAP with SSTP Access Client EAP/PEAP Client Certificate VPN Tunnel Server Certificate Access Server PEAP Server Certificate RADIUS Active Directory

RADIUS Clients configuration IP address of the device can translate from DNS, but must match IP address of the device (no reverse DNS) Shared secrets MD 5(random message authenticator + shared secret) NETSH NPS DUMP Export. PSK=YES

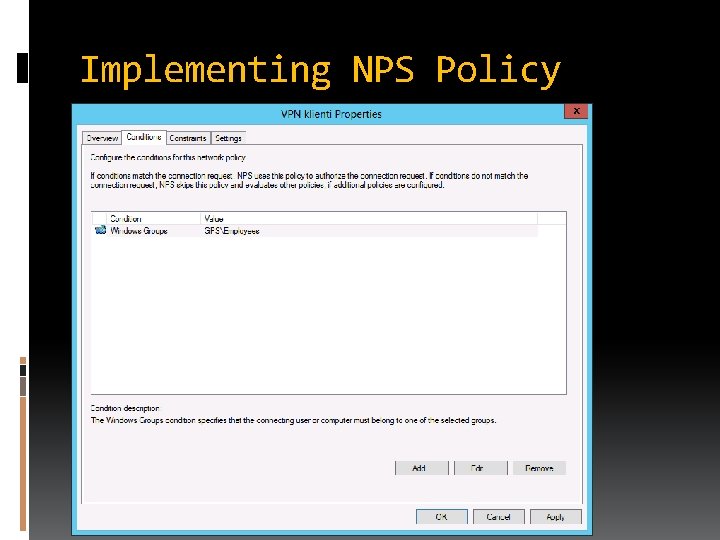
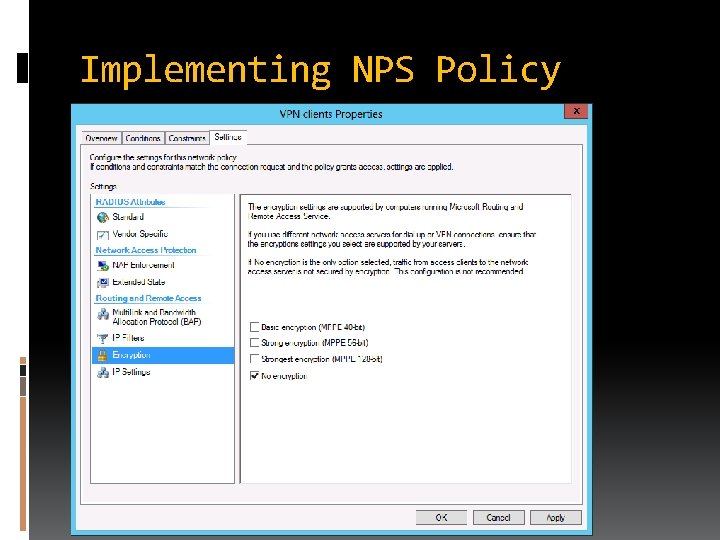
Implementing NPS Policy

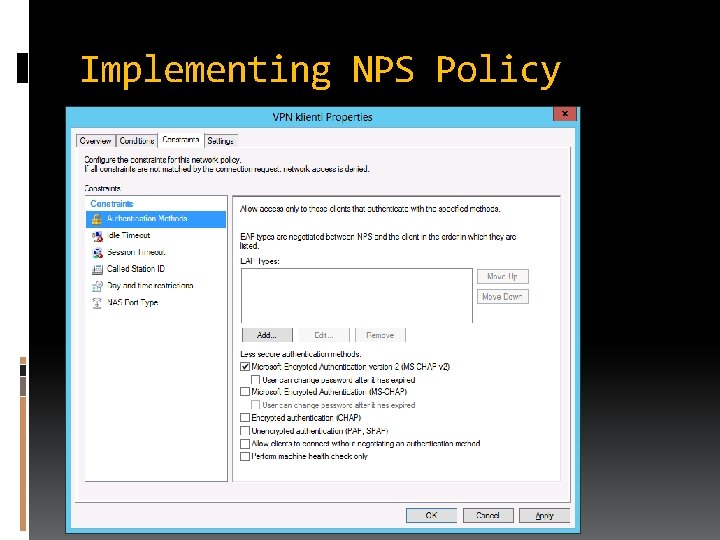
Implementing NPS Policy

Implementing NPS Policy

Implementing NPS Policy

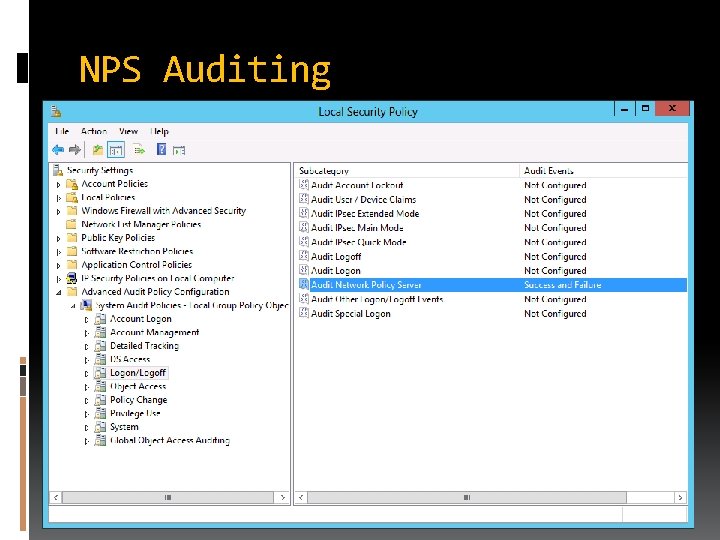
NPS Auditing

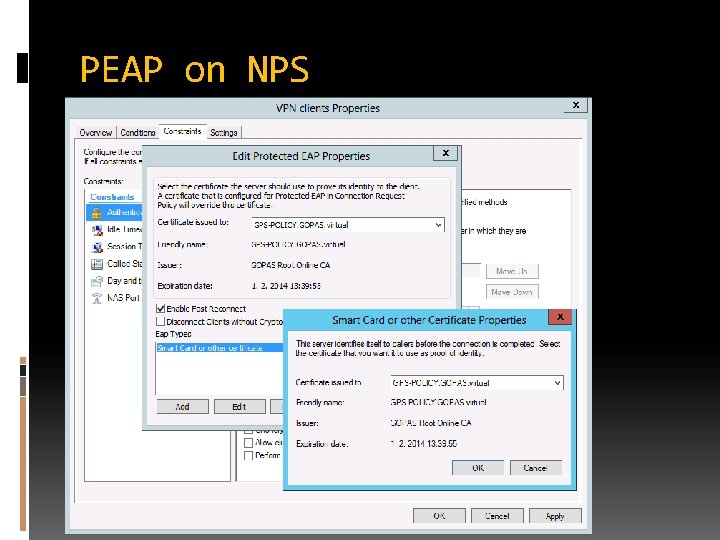
PEAP on NPS

PEAP on NPS

VPN Client Notes Validates CRL SSTP does not use CRL cache HKLMSystemCCSServicesSSTPSvcParameters No. Cert. Revocation. Check = DWORD = 1 IPSec set global ipsec strongcrlcheck 0 HKLMSystemCCSServicesPolicy. Agent Strong. Crl. Check = 0 = disabled Strong. Crl. Check = 1 = fail only if revoked Strong. Crl. Check = 2 = fail even if CRL not available HKLMSystemCCSServicesIPSec Assume. UDPEncapsulation. Context. On. Send. Rule = 2

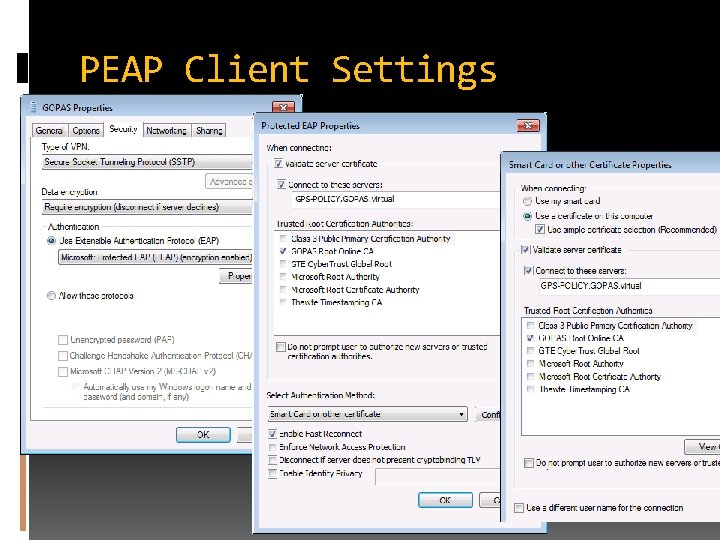
PEAP Client Settings

VPN Client Configuration Group Policy Preferences limited options Connection Manager Administration Kit (CMAK) create VPN installation packages

802. 1 x Notes Required services WLAN Autoconfig (Wlan. Svc) Wired Autoconfig (Doc 3 Svc) Group Policy Settings Windows XP SP 3 and newer full configuration options

802. 1 x Authentication User authentication login/password client certificate in user profile or in smart card Computer authentication MACHINE$ login/password client certificate in the local computer store Computer authentication with user reauthentication since Windows 7 works like charm

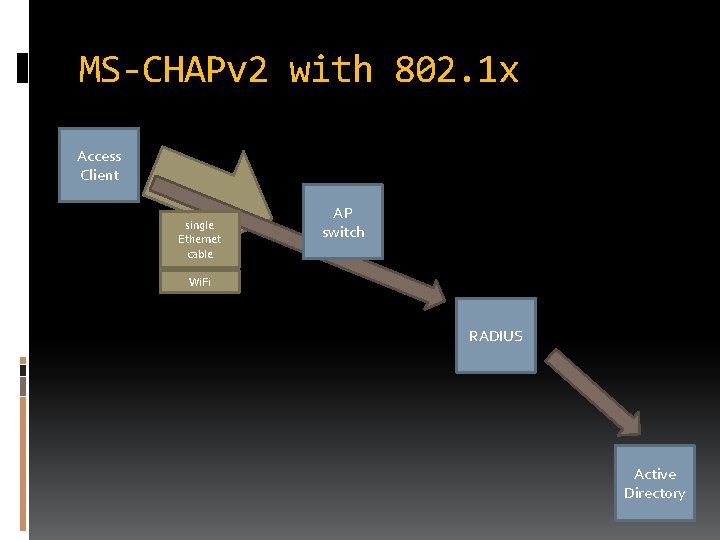
MS-CHAPv 2 with 802. 1 x Access Client single Ethernet cable AP switch Wi. Fi RADIUS Active Directory

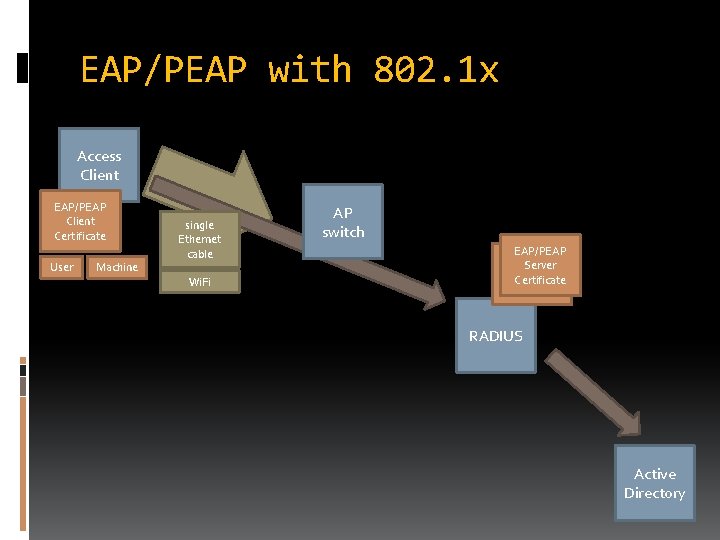
EAP/PEAP with 802. 1 x Access Client EAP/PEAP Client Certificate User Machine single Ethernet cable Wi. Fi AP switch EAP/PEAP EAP-TLS Server Certificate RADIUS Active Directory

RD Proxy Troubleshooting RPCPING -t ncacn_http -e 3388 -s localhost (local TSGateway COM service) -v 3 (verbose output 1/2/3) -a connect (conntect/call/pkt/integrity/privacy) -u ntlm (nego/ntlm/schannel/kerberos/kernel) -I "kamil, gps, *" -o Rpc. Proxy=gps-wfe. gopas. virtual: 443 -F ssl -B msstd: gps-wfe. gopas. virtual -H ntlm (RPCover. HTTP proxy authentication ntlm/basic) -P "proxykamil, gps, *" -U NTLM (HTTP proxy authentication ntlm/basic) rpcping -t ncacn_http -e 3388 -s localhost -v 3 -a connect -u ntlm -I "kamil, gps, Pa$$w 0 rd" -o Rpc. Proxy=rdp. gopas. cz: 443 -F ssl -B msstd: rdp. gopas. cz -H ntlm -P "kamil, gps, Pa$$w 0 rd"

RPC Proxy Troubleshooting https: //rpcserver/Rpc. Proxy. dll https: //rpcserver/Rpc. With. Cert/Rpc. Proxy. dll
 Evolve windows xp
Evolve windows xp Ondej
Ondej Stek audit
Stek audit Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Ondej
Ondej Alex karasulu
Alex karasulu Vds virtual directory services
Vds virtual directory services Ad u
Ad u Mcm agenda
Mcm agenda Mcm chemistry
Mcm chemistry Mcm authenticator
Mcm authenticator Desired packaging
Desired packaging Recarga mcm
Recarga mcm Mcm
Mcm Mcm betekenis
Mcm betekenis Minimo comune denominatore frazioni algebriche
Minimo comune denominatore frazioni algebriche Creature framework mcm
Creature framework mcm Mandiri cash
Mandiri cash Ecuaciones con fracciones algebraicas 4 eso
Ecuaciones con fracciones algebraicas 4 eso Mcm audience
Mcm audience Mcm icm
Mcm icm Mcm 2012
Mcm 2012 Multipli di 24
Multipli di 24 Mcm de expresiones algebraicas
Mcm de expresiones algebraicas C-m-c m-c-m
C-m-c m-c-m Mcm anomaly
Mcm anomaly Factores primos de un polinomio
Factores primos de un polinomio 3150 mcm
3150 mcm Rdo mcm
Rdo mcm Conjunto
Conjunto Emm
Emm Active directory alapok
Active directory alapok Adyen directory lookup
Adyen directory lookup