Ondej eveek PM Windows Server GOPAS a s























- Slides: 69

Ondřej Ševeček | PM Windows Server | GOPAS a. s. | MCM: Directory Services | MVP: Enterprise Security | ondrej@sevecek. com | www. sevecek. com | WINDOWS PKI

Outline Hash algorithms Symmetric algorithms Asymmetric algorithms Current algorithms in use Cryptographic standards Operating system support 2

Security Services Confidentiality Data Integrity accidental vs. deliberate modification Authentication plus role-based authentication when more individuals share authentication information Authorization Non-repudiation key establishment and random number

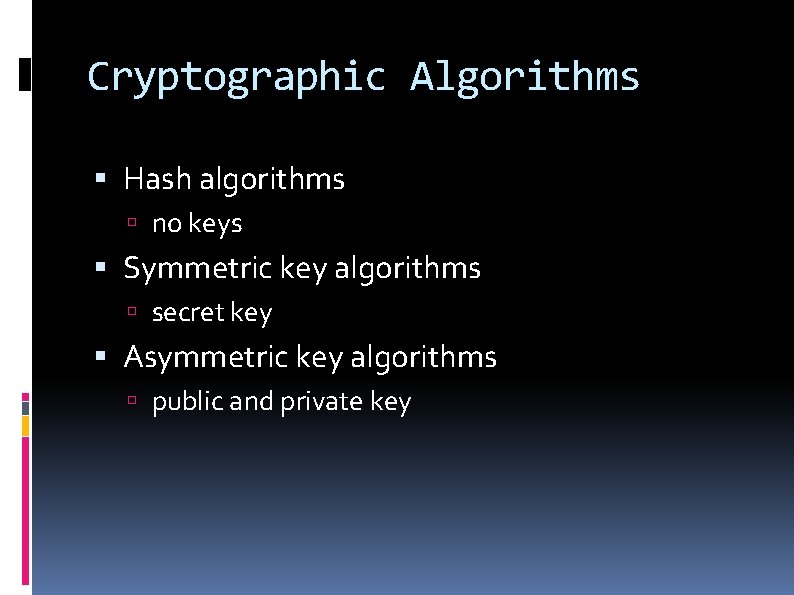
Cryptographic Algorithms Hash algorithms no keys Symmetric key algorithms secret key Asymmetric key algorithms public and private key

Cryptography HASH ALGORITHMS 5

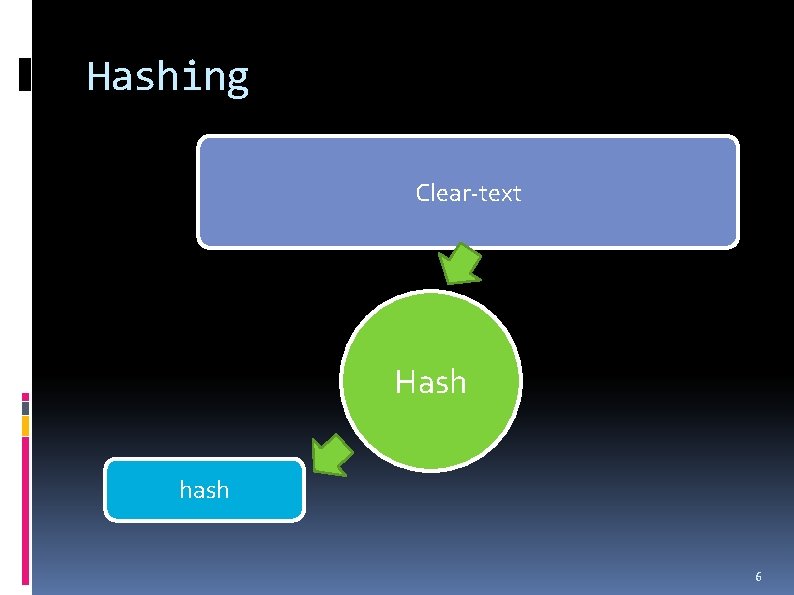
Hashing Clear-text Hash hash 6

Hash Data authentication and integrity in conjunction with keys HMAC – Hashed Message Authentication Code Compression of messages for digital signatures Deriving keys Generation of deterministic random numbers

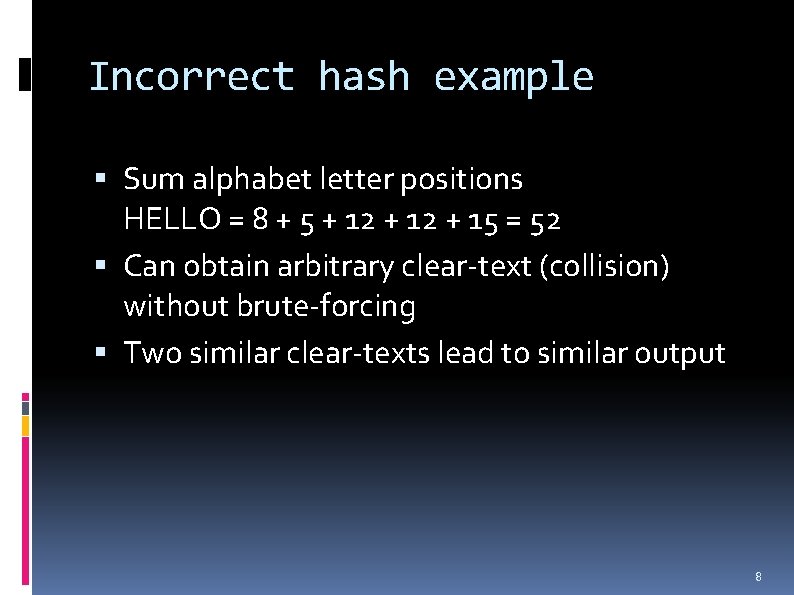
Incorrect hash example Sum alphabet letter positions HELLO = 8 + 5 + 12 + 15 = 52 Can obtain arbitrary clear-text (collision) without brute-forcing Two similar clear-texts lead to similar output 8

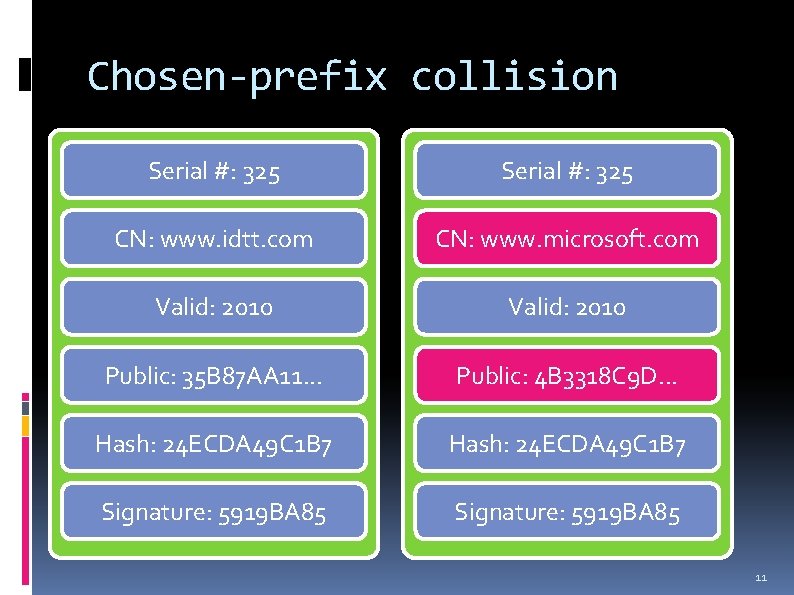
Hash collisions Pure arithmetic collisions limited exploitability Post-signing collisions Chosen-prefix collisions 9

Post-signing collision Name: Ondrej Owes: 100 $ Owes: 1 000 $ To: Kamil Hash: 14 EEDA 49 C 1 B 7 Trash: XX 349%$@#BB. . . Signature: 3911 BA 85 Hash: 14 EEDA 49 C 1 B 7 Signature: 3911 BA 85 10

Chosen-prefix collision Serial #: 325 CN: www. idtt. com CN: www. microsoft. com Valid: 2010 Public: 35 B 87 AA 11. . . Public: 4 B 3318 C 9 D. . . Hash: 24 ECDA 49 C 1 B 7 Signature: 5919 BA 85 11

MD 5 problems Pure arithmetic in 2^112 evaluations Post-signing collisions suspected Chosen-prefix collisions Practically proved for certificates with predictable serial numbers 2^50 12

SHA-1 problems General brute-force attack at 2^80 as about 12 characters complex password Some collisions found at 2^63 pure arithmetic collisions, no exploitation proved 13

Cryptography SYMMETRIC ALGORITHMS 14

Symmetric key Data confidentiality Authentication and integrity MAC – Message Authentication Code, single key to generate, the same to validate Key establishment Generation of deterministic random numbers

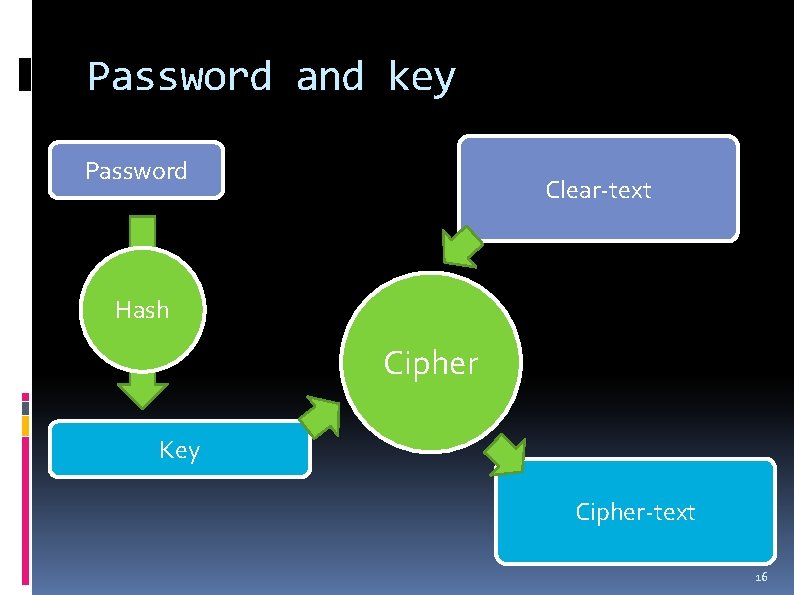
Password and key Password Clear-text Hash Cipher Key Cipher-text 16

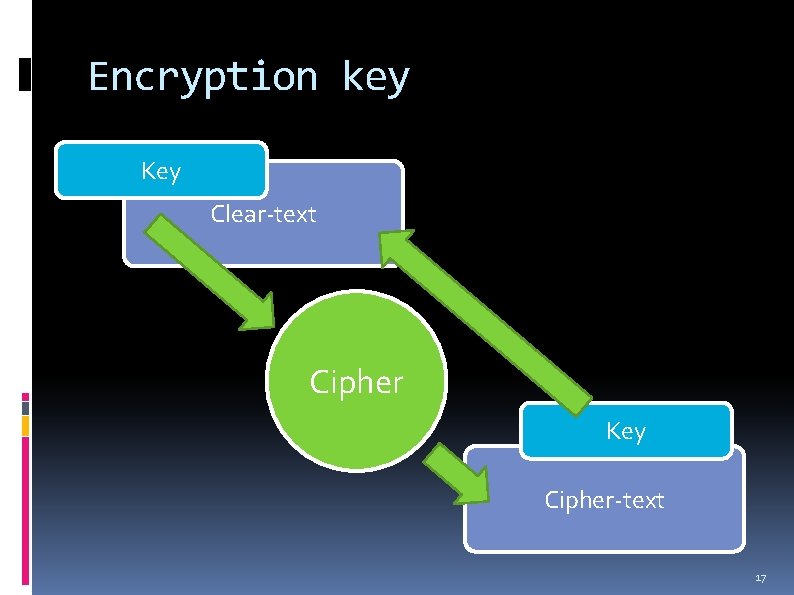
Encryption key Key Clear-text Cipher Key Cipher-text 17

Cryptography ASYMMETRIC ALGORITHMS 18

Asymmetric keys Digital signatures Key establishment Generation of random numbers

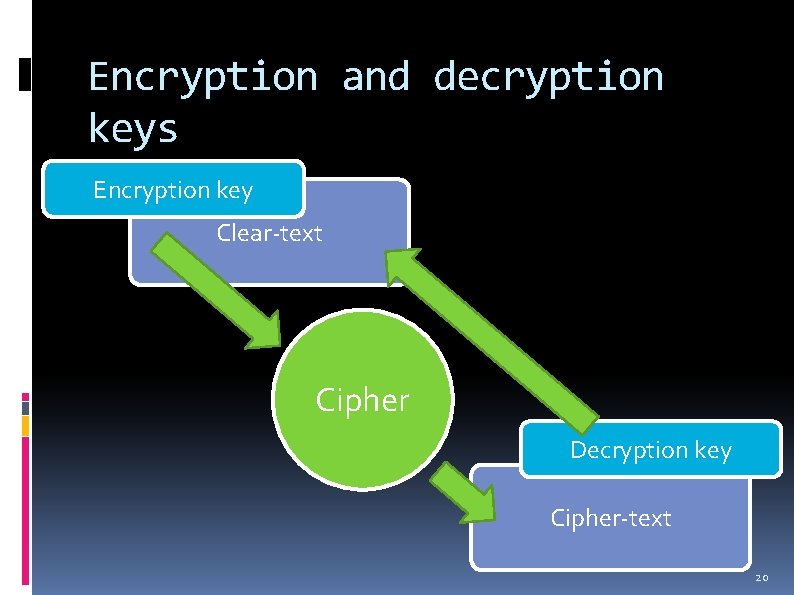
Encryption and decryption keys Encryption key Clear-text Cipher Decryption key Cipher-text 20

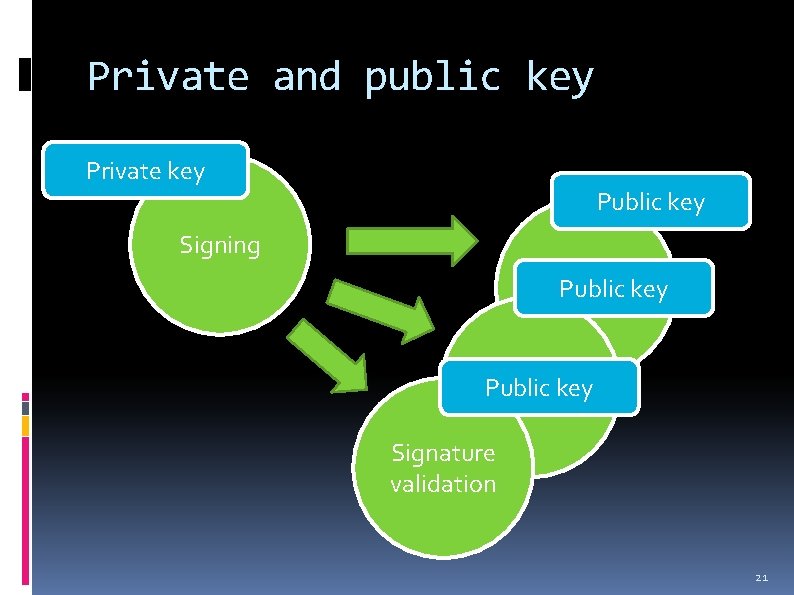
Private and public key Private key Public key Signing Signature Public key validation Signature validation 21

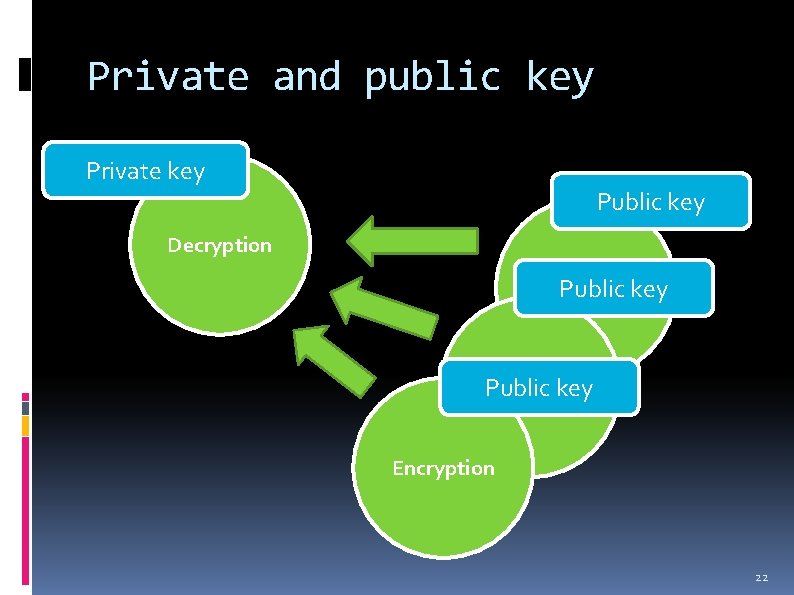
Private and public key Private key Public key Decryption Signature Public key validation Encryption 22

Performance considerations Asymmetric algorithms use large keys EC is about 10 times smaller Encryption/decryption time about 100 x longer symmetric is faster

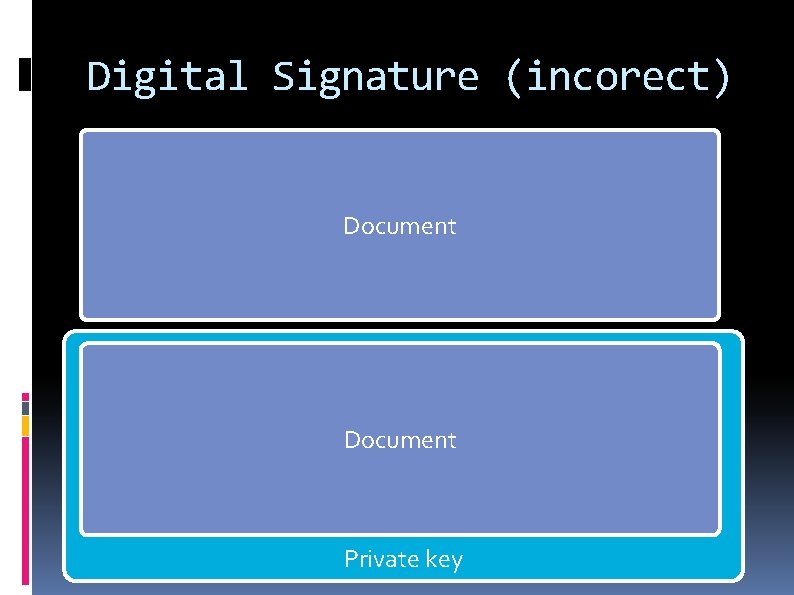
Digital Signature (incorect) Document Private key

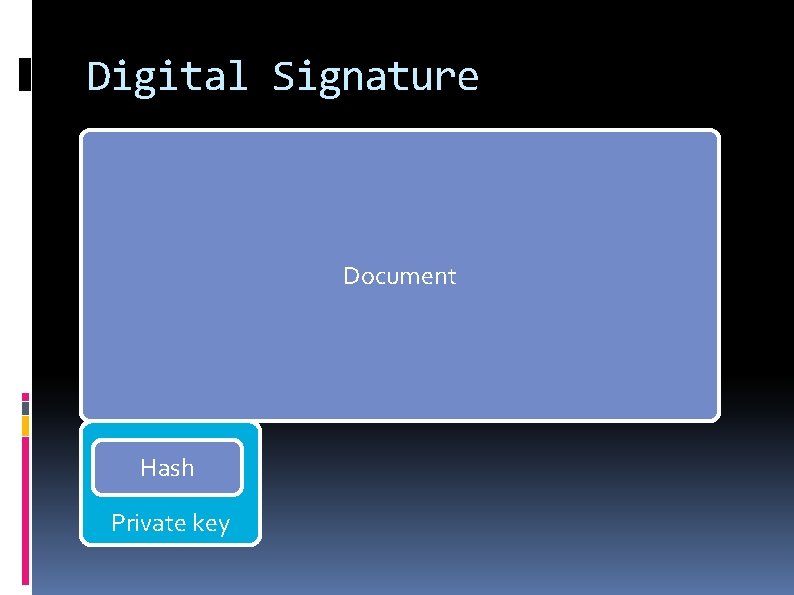
Digital Signature Document Hash Private key

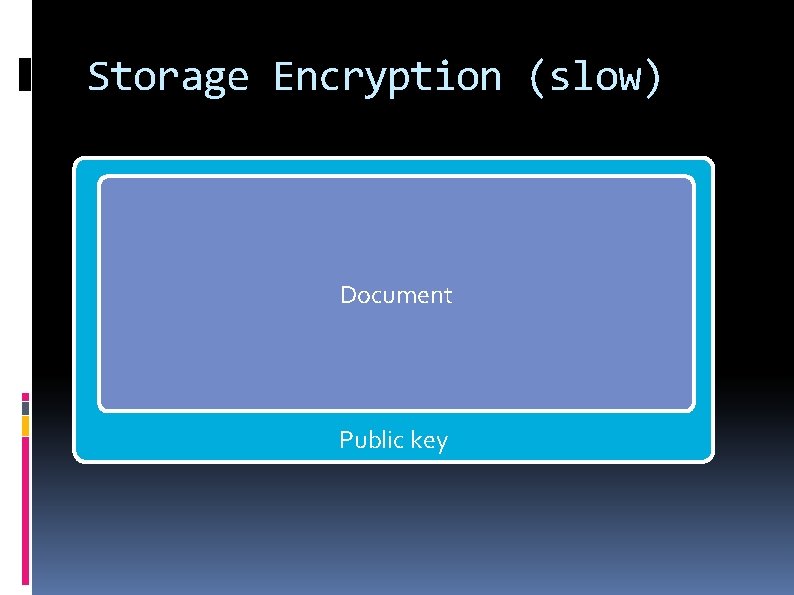
Storage Encryption (slow) Document Public key

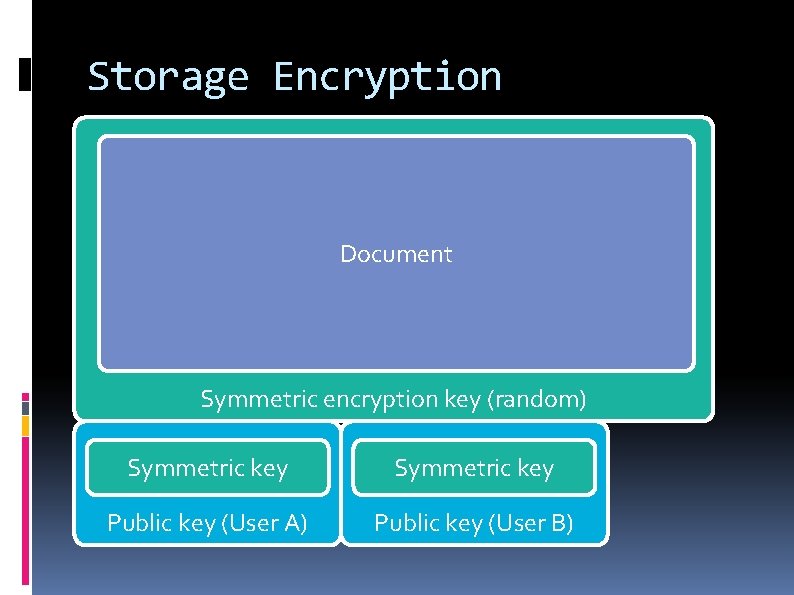
Storage Encryption Document Symmetric encryption key (random) Symmetric key Public key (User A) Public key (User B)

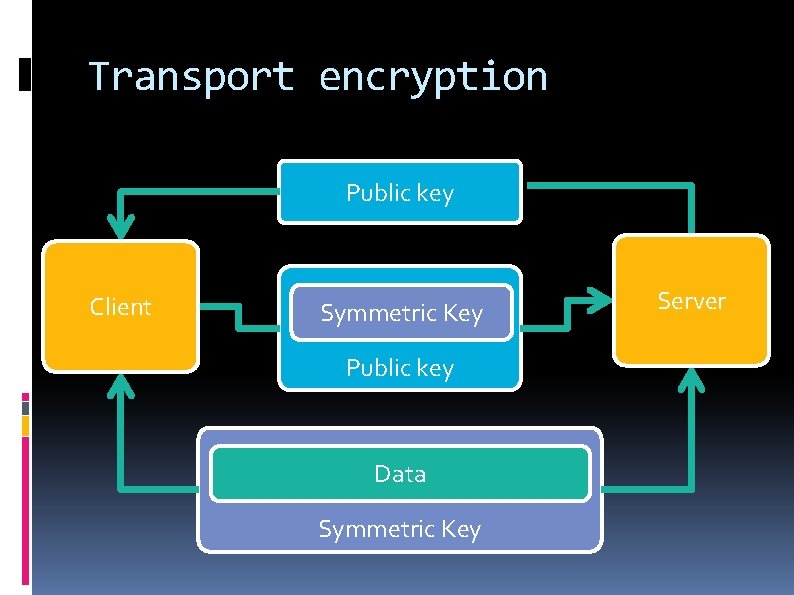
Transport encryption Public key Client Symmetric Key Public key Data Symmetric Key Server

Diffie-Hellman Key Exchange Asymmetric algorithm for key exchange most commonly used for key exchange Automatically generates the same encryption key for symmetric encryption on both sides

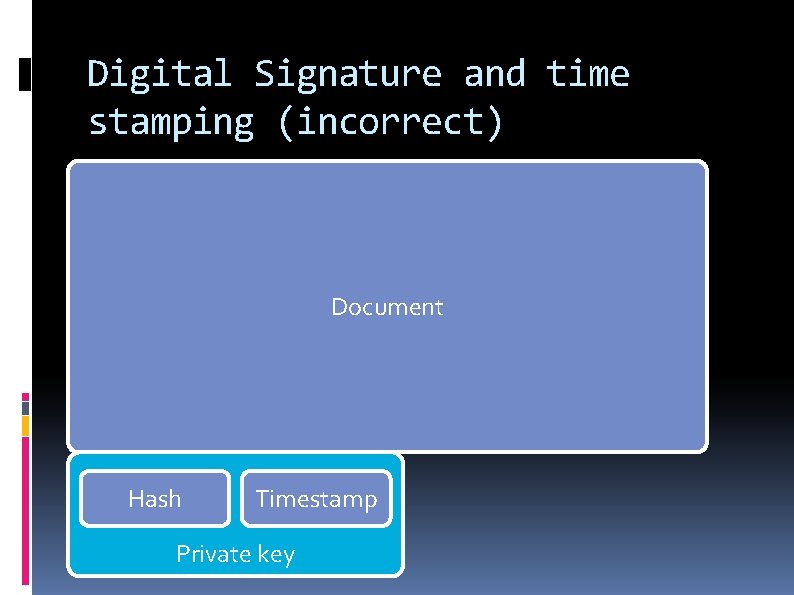
Digital Signature and time stamping (incorrect) Document Hash Timestamp Private key

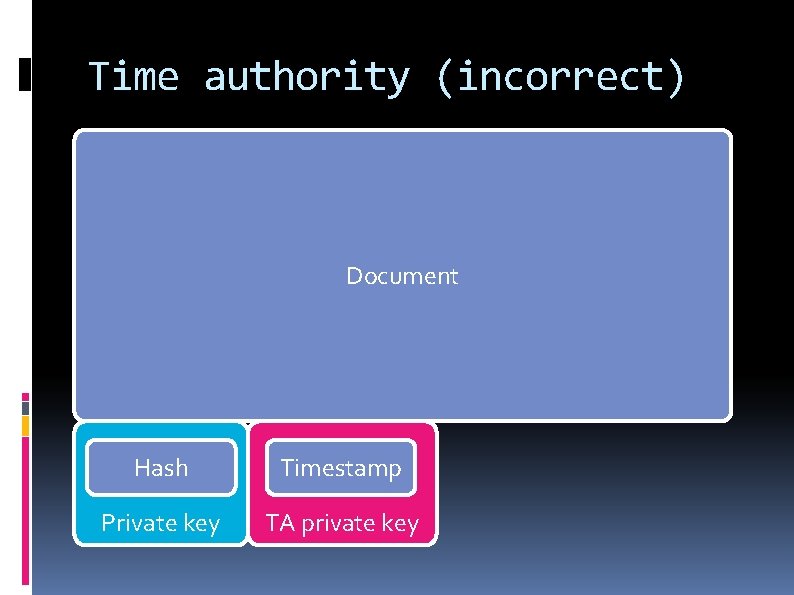
Time authority (incorrect) Document Hash Timestamp Private key TA private key

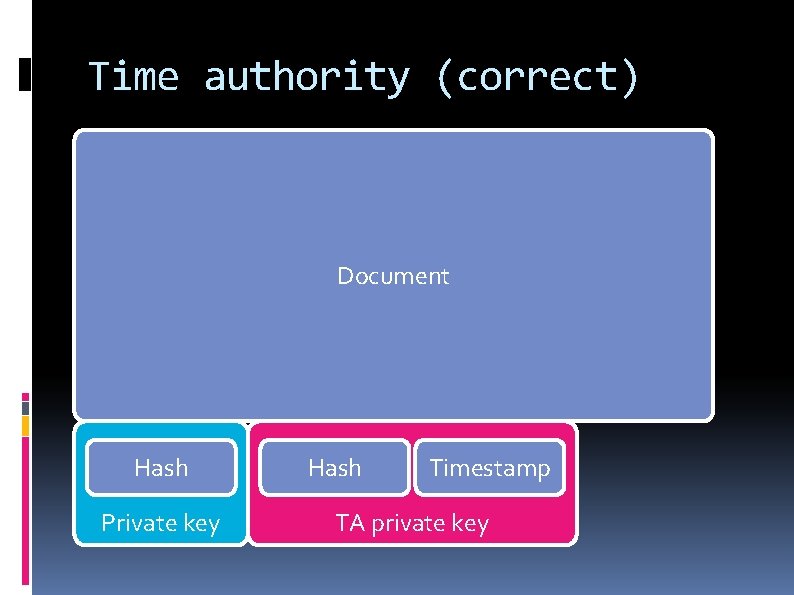
Time authority (correct) Document Hash Private key Hash Timestamp TA private key

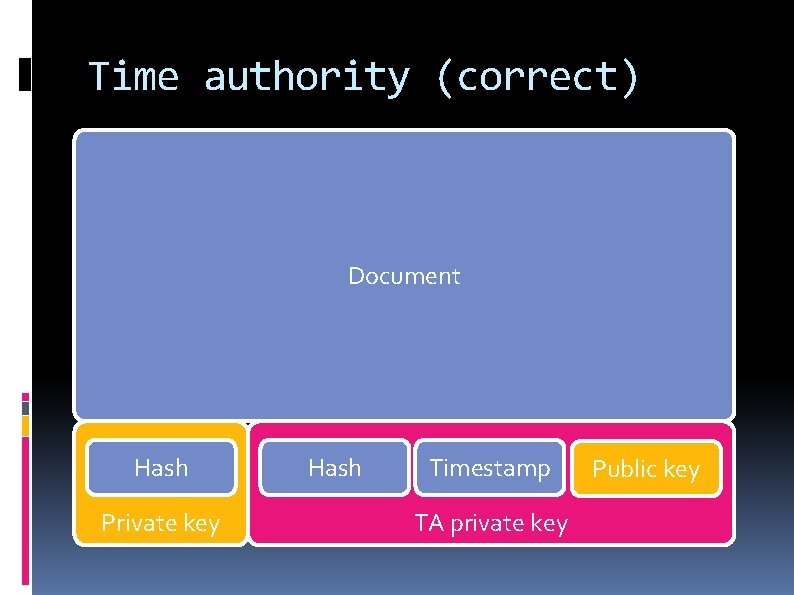
Time authority (correct) Document Hash Private key Hash Timestamp TA private key Public key

Random Number Generators Deterministic RNG use cryptographic algorithms and keys to generate random bits attack on randomly generated symmetric keys DNS cache poisoning Nondeterministic RNG (true RNG) use physical source that is outside human control smart cards, tokens HSM – hardware security modules

Random Number Generators Crypt. Gen. Random() hashed Vista+ AES (NIST 800 -900) 2003 - DSS (FIPS 186 -2) Entropy from system time, process id, thread id, tick counter, virtual/physical memory performance counters of the process and system, free disk clusters, user environment, context switches, exception count, …

Random Number Generators new Random() just a time seed several instances created simultaneously may have the same seed

Cryptography CURRENT ALGORITHMS 37

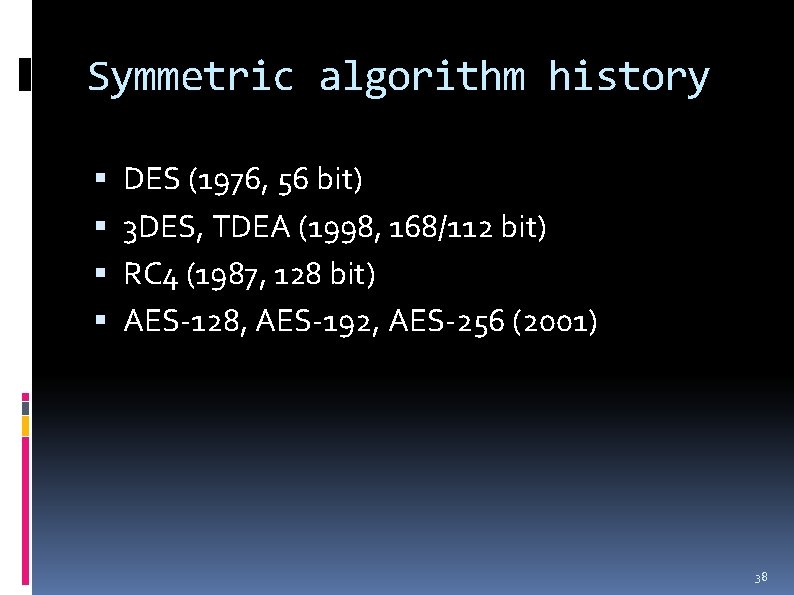
Symmetric algorithm history DES (1976, 56 bit) 3 DES, TDEA (1998, 168/112 bit) RC 4 (1987, 128 bit) AES-128, AES-192, AES-256 (2001) 38

Hash algorithm history MD 4 (1990, 128 bit) MD 5 (1991, 128 bit) SHA-1 (1995, 160 bit) SHA-224, SHA-256, SHA-384, SHA-512 (2001) 39

Asymmetric algorithm history RSA (1973) DSA (1991) ECDSA (2000) ECDH (2000) 40

Cryptography CRYPTOGRAPHIC STANDARDS 41

US standards FIPS – Federal Information Processing Standards provides standard algorithms NIST – National Institute for Standards and Technology approves the algorithms for US government non- classified but sensitive use latest NIST SP 800 -57, March 2007 NSA – National Security Agency Suite-B for Secure and Top Secure (2005)

Hash functions (SP 800 -57) SHA-1 hash size output is 160 SHA-224, SHA-256, SHA-384, SHA-512 hash size output is 224, 256, 384, 512

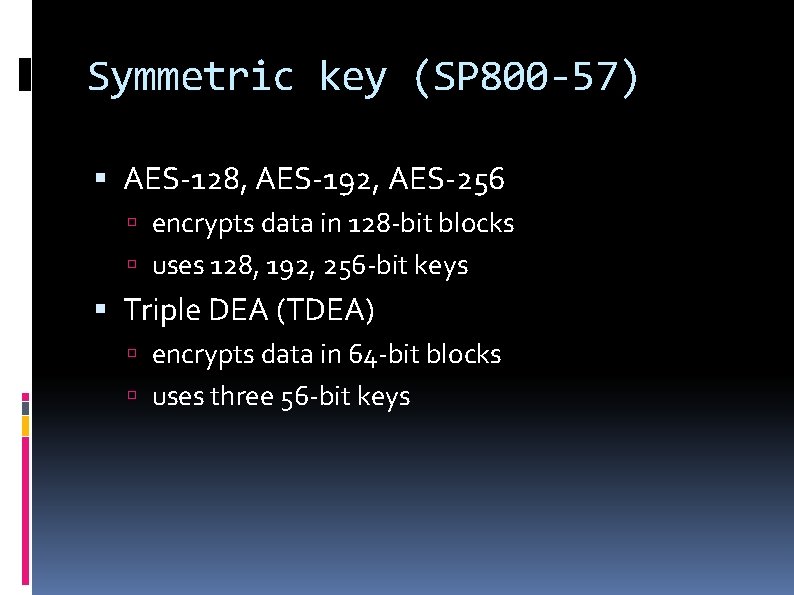
Symmetric key (SP 800 -57) AES-128, AES-192, AES-256 encrypts data in 128 -bit blocks uses 128, 192, 256 -bit keys Triple DEA (TDEA) encrypts data in 64 -bit blocks uses three 56 -bit keys

Digital Signatures (SP 800 -57) DSA (Digital Signature Algorithm) key sizes of 1024, 2048 and 3072 -bit produces 320, 448, 512 -bit signatures RSA (Rivest – Shamir – Adleman) key sizes according to FIPS 186 -3 ECDSA (Elliptic Curve DSA) key sizes of at least 160 -bit produces 2 x key length signatures types of curves specified in FIPS 186 -3

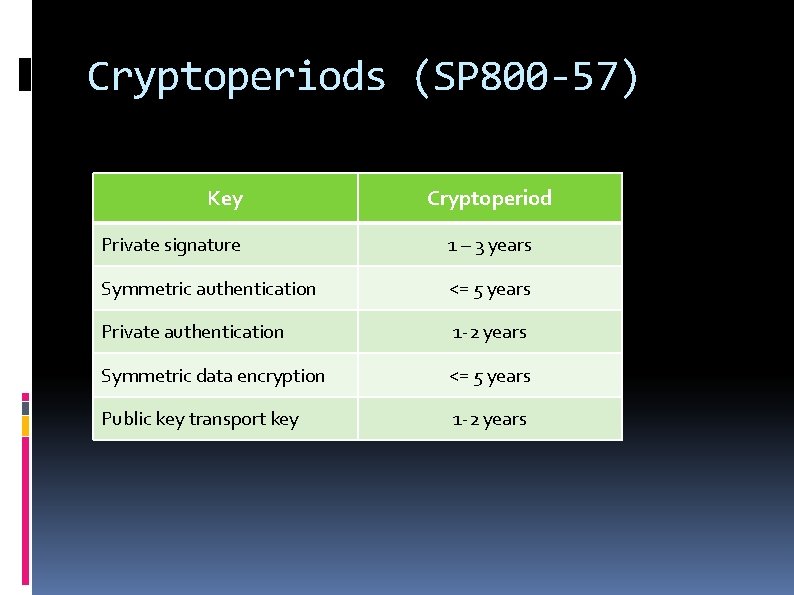
Cryptoperiods (SP 800 -57) Key Cryptoperiod Private signature 1 – 3 years Symmetric authentication <= 5 years Private authentication 1 -2 years Symmetric data encryption <= 5 years Public key transport key 1 -2 years

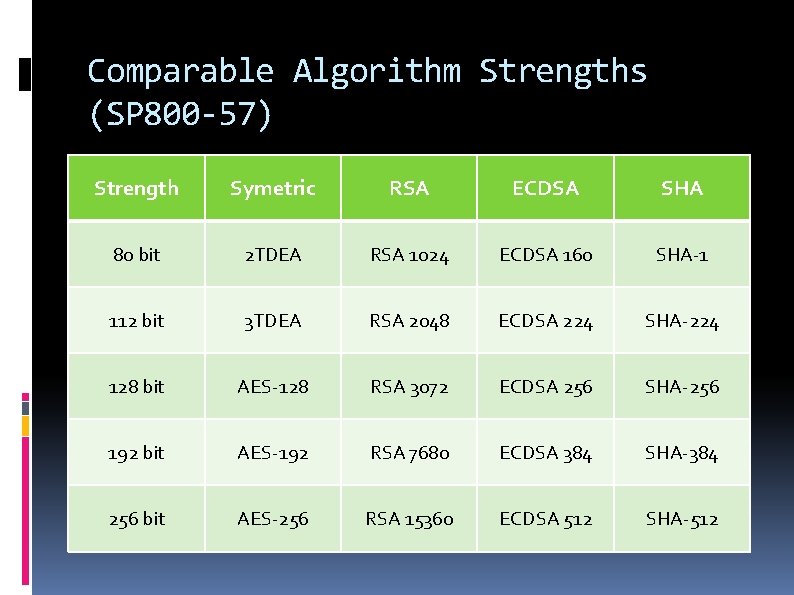
Comparable Algorithm Strengths (SP 800 -57) Strength Symetric RSA ECDSA SHA 80 bit 2 TDEA RSA 1024 ECDSA 160 SHA-1 112 bit 3 TDEA RSA 2048 ECDSA 224 SHA-224 128 bit AES-128 RSA 3072 ECDSA 256 SHA-256 192 bit AES-192 RSA 7680 ECDSA 384 SHA-384 256 bit AES-256 RSA 15360 ECDSA 512 SHA-512

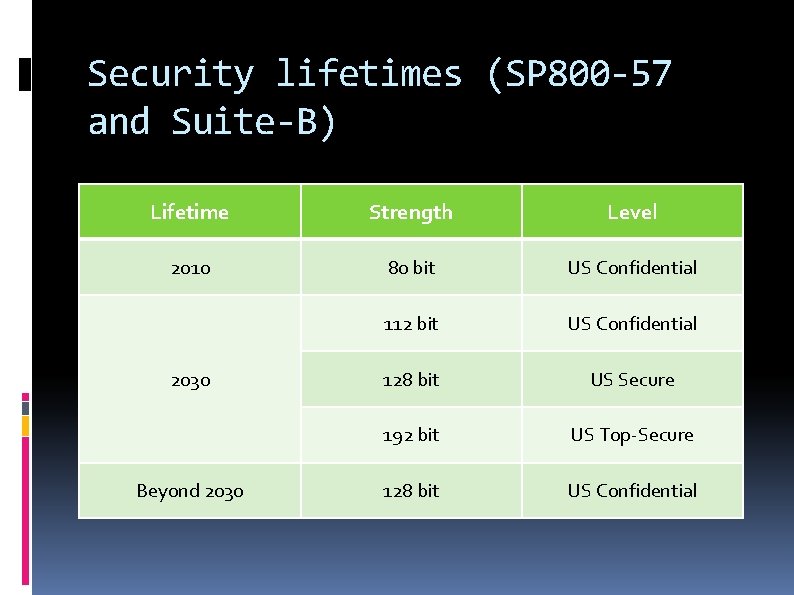
Security lifetimes (SP 800 -57 and Suite-B) Lifetime Strength Level 2010 80 bit US Confidential 112 bit US Confidential 128 bit US Secure 192 bit US Top-Secure 128 bit US Confidential 2030 Beyond 2030

Cryptography OPERATING SYSTEM SUPPORT 49

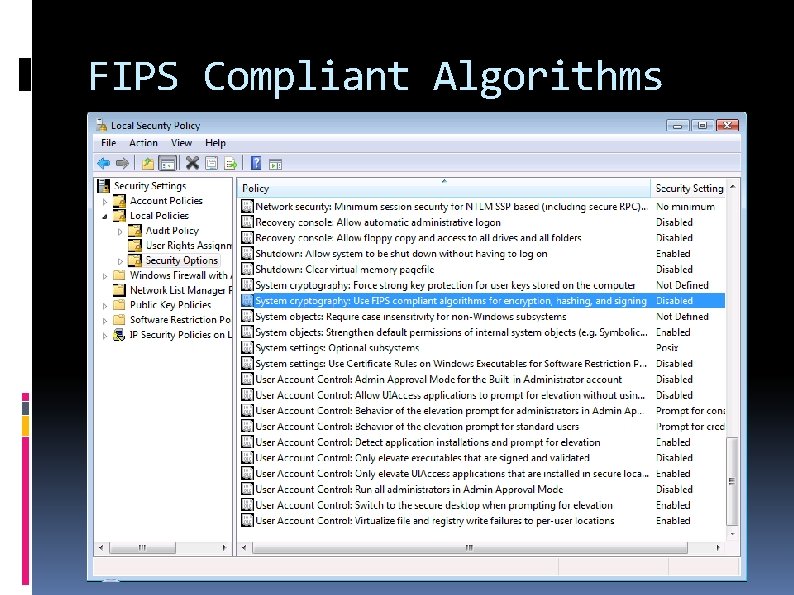
FIPS Compliant Algorithms

Cryptographic Providers Cryptographic Service Provider – CSP Windows 2000+ DLL loaded into client processes can use only V 1 and V 2 templates Cryptography Next Generation – CNG Windows Vista+ different API functions, isolated private keys use only V 3 templates enables use of ECC CERTUTIL -CSPLIST 51

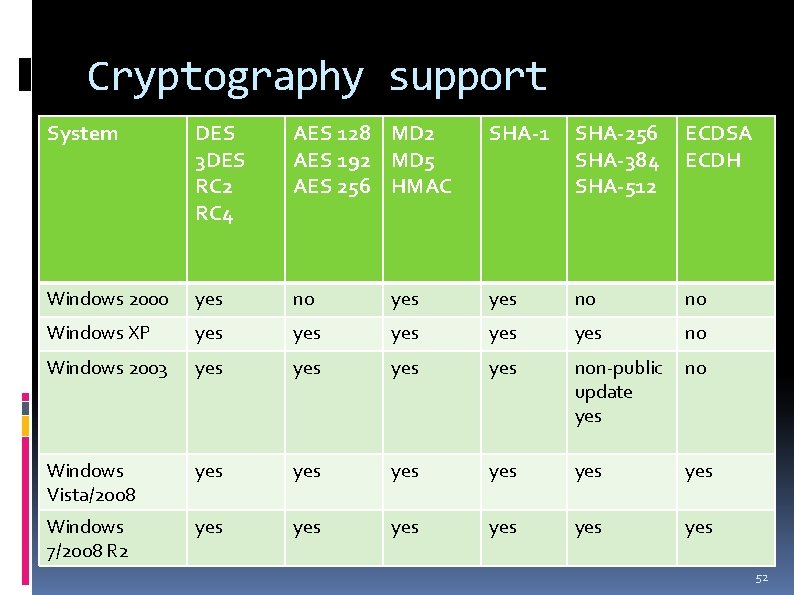
Cryptography support System DES 3 DES RC 2 RC 4 AES 128 MD 2 AES 192 MD 5 AES 256 HMAC SHA-1 SHA-256 SHA-384 SHA-512 ECDSA ECDH Windows 2000 yes no no Windows XP yes yes yes no Windows 2003 yes yes non-public update yes no Windows Vista/2008 yes yes yes Windows 7/2008 R 2 yes yes yes 52

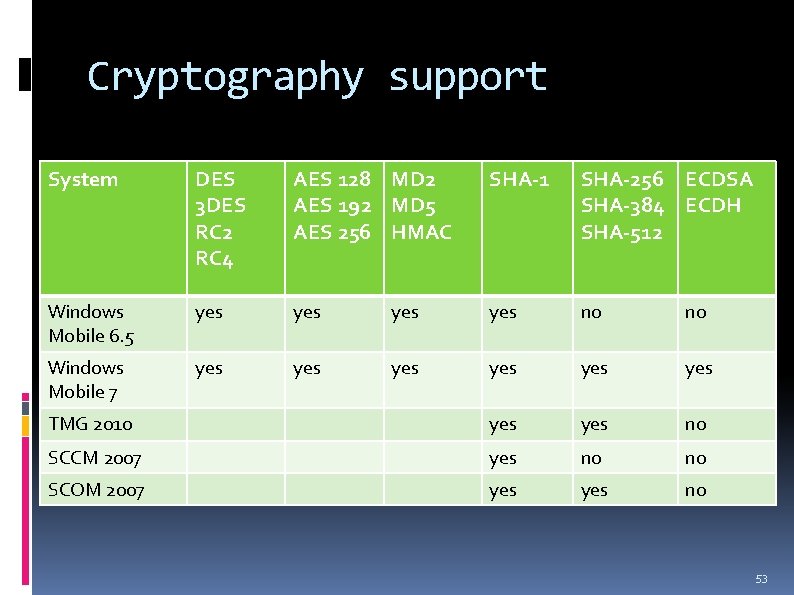
Cryptography support System DES 3 DES RC 2 RC 4 AES 128 MD 2 AES 192 MD 5 AES 256 HMAC SHA-1 SHA-256 ECDSA SHA-384 ECDH SHA-512 Windows Mobile 6. 5 yes yes no no Windows Mobile 7 yes yes yes TMG 2010 yes no SCCM 2007 yes no no SCOM 2007 yes no 53

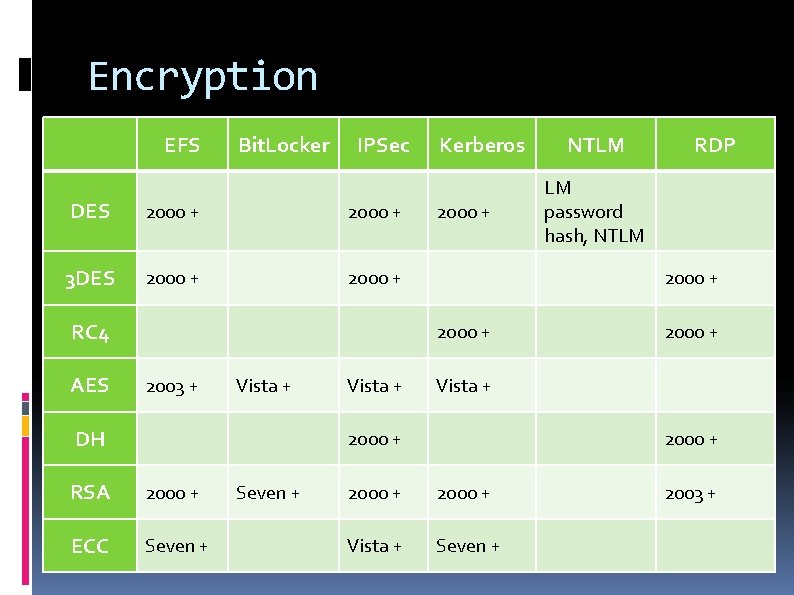
Encryption EFS Bit. Locker IPSec DES 2000 + 3 DES 2000 + RC 4 AES Kerberos 2000 + Vista + DH Vista + 2000 + ECC Seven + LM password hash, NTLM 2000 + Vista + 2000 + RSA RDP 2000 + 2003 + NTLM 2000 + Vista + Seven + 2003 +

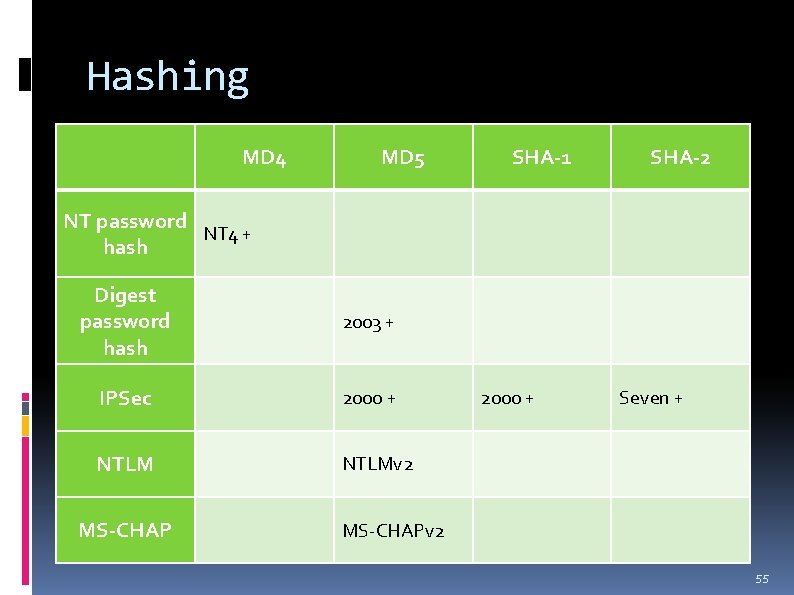
Hashing MD 4 MD 5 SHA-1 SHA-2 NT password NT 4 + hash Digest password hash 2003 + IPSec 2000 + NTLMv 2 MS-CHAP 2000 + Seven + MS-CHAPv 2 55

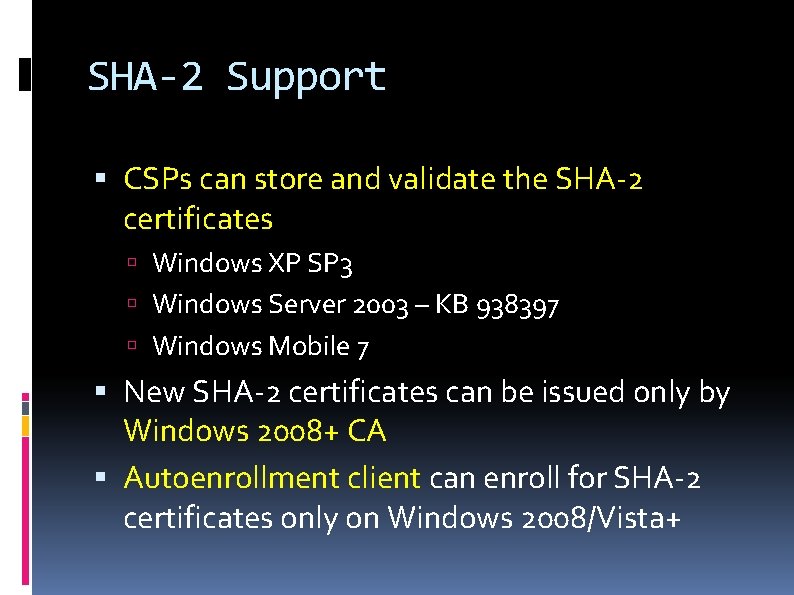
SHA-2 Support CSPs can store and validate the SHA-2 certificates Windows XP SP 3 Windows Server 2003 – KB 938397 Windows Mobile 7 New SHA-2 certificates can be issued only by Windows 2008+ CA Autoenrollment client can enroll for SHA-2 certificates only on Windows 2008/Vista+

CNG Not Supported EFS Windows 2008/Vista user encryption certificates VPN/Wi. Fi Client (EAPTLS, PEAP Client) Windows 2008/7 user or computer certificate authentication TMG 2010 server certificates on web listeners Outlook 2003 user email certificates for signatures or encryption Kerberos Windows 2008/Vista- DC certificates System Center Operations Manager 2007 R 2 System Center Configuration Manager 2007 R 2

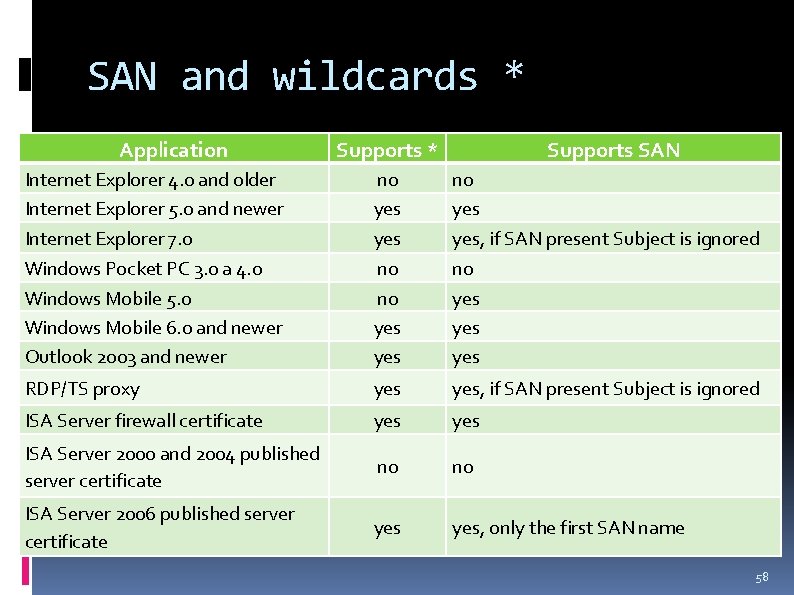
SAN and wildcards * Application Supports * Supports SAN Internet Explorer 4. 0 and older Internet Explorer 5. 0 and newer no yes Internet Explorer 7. 0 yes, if SAN present Subject is ignored Windows Pocket PC 3. 0 a 4. 0 Windows Mobile 5. 0 Windows Mobile 6. 0 and newer Outlook 2003 and newer no no yes yes yes RDP/TS proxy yes, if SAN present Subject is ignored ISA Server firewall certificate yes ISA Server 2000 and 2004 published server certificate no no ISA Server 2006 published server certificate yes, only the first SAN name 58

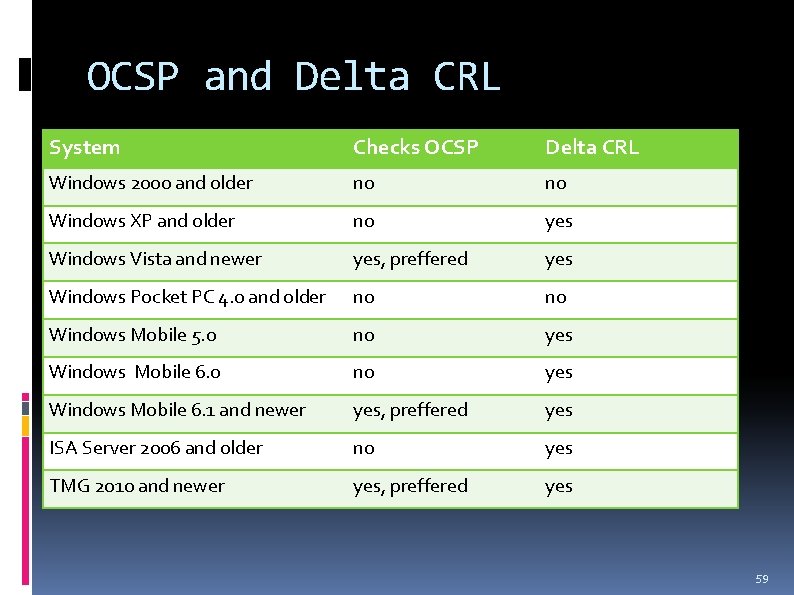
OCSP and Delta CRL System Checks OCSP Delta CRL Windows 2000 and older no no Windows XP and older no yes Windows Vista and newer yes, preffered yes Windows Pocket PC 4. 0 and older no no Windows Mobile 5. 0 no yes Windows Mobile 6. 1 and newer yes, preffered yes ISA Server 2006 and older no yes TMG 2010 and newer yes, preffered yes 59

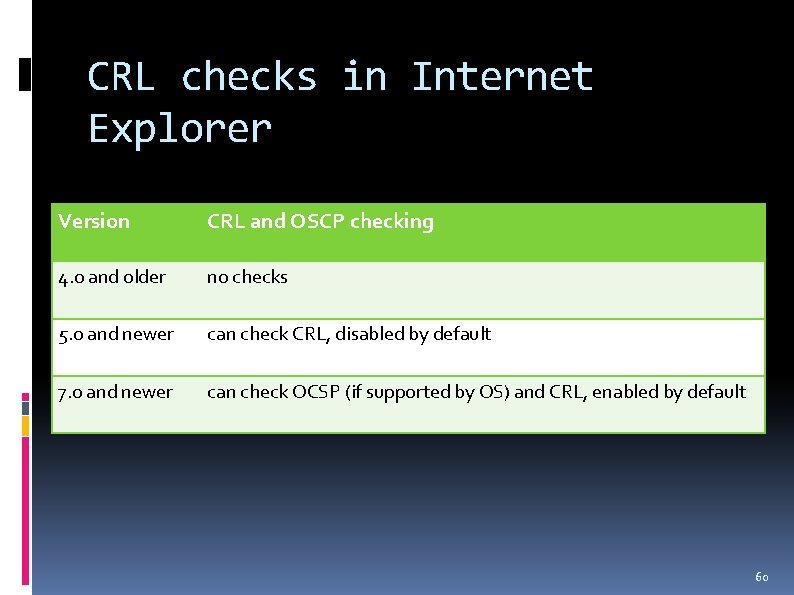
CRL checks in Internet Explorer Version CRL and OSCP checking 4. 0 and older no checks 5. 0 and newer can check CRL, disabled by default 7. 0 and newer can check OCSP (if supported by OS) and CRL, enabled by default 60

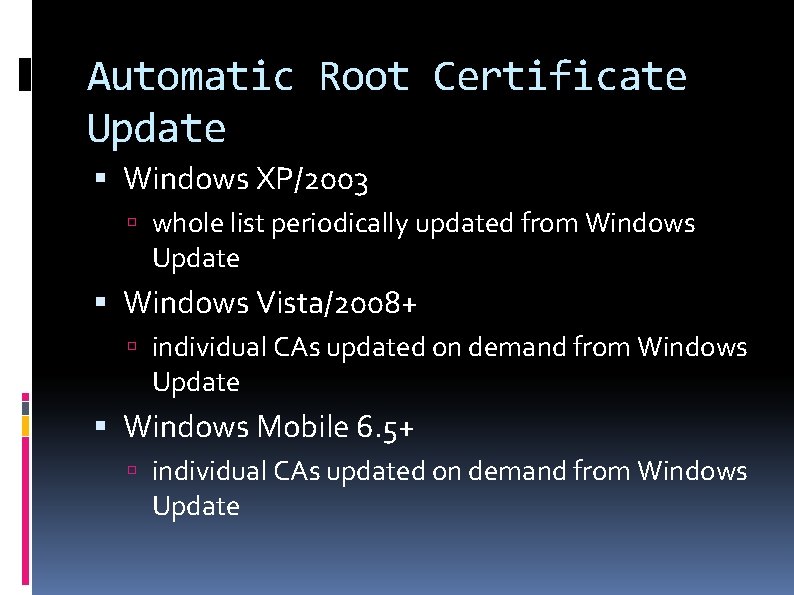
Automatic Root Certificate Update Windows XP/2003 whole list periodically updated from Windows Update Windows Vista/2008+ individual CAs updated on demand from Windows Update Windows Mobile 6. 5+ individual CAs updated on demand from Windows Update

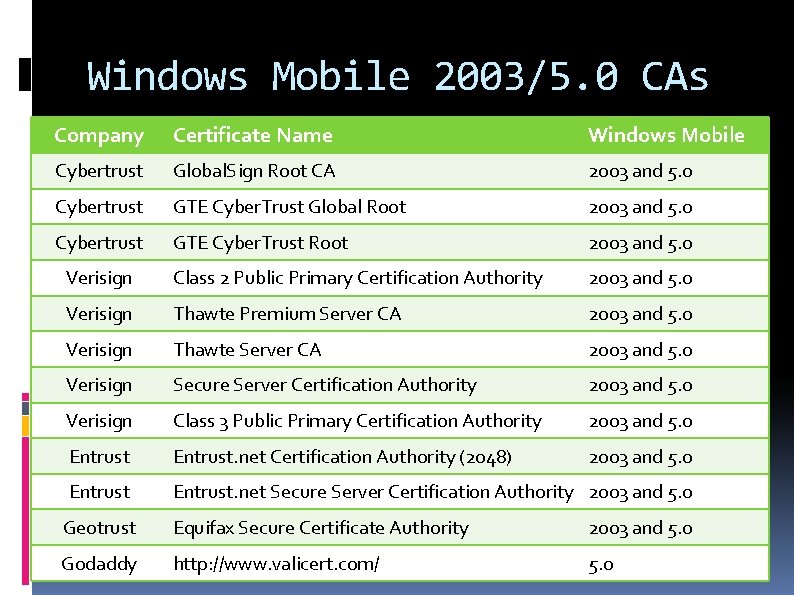
Windows Mobile 2003/5. 0 CAs Company Certificate Name Windows Mobile Cybertrust Global. Sign Root CA 2003 and 5. 0 Cybertrust GTE Cyber. Trust Global Root 2003 and 5. 0 Cybertrust GTE Cyber. Trust Root 2003 and 5. 0 Verisign Class 2 Public Primary Certification Authority 2003 and 5. 0 Verisign Thawte Premium Server CA 2003 and 5. 0 Verisign Thawte Server CA 2003 and 5. 0 Verisign Secure Server Certification Authority 2003 and 5. 0 Verisign Class 3 Public Primary Certification Authority 2003 and 5. 0 Entrust. net Certification Authority (2048) 2003 and 5. 0 Entrust. net Secure Server Certification Authority 2003 and 5. 0 Geotrust Equifax Secure Certificate Authority 2003 and 5. 0 Godaddy http: //www. valicert. com/ 5. 0 62

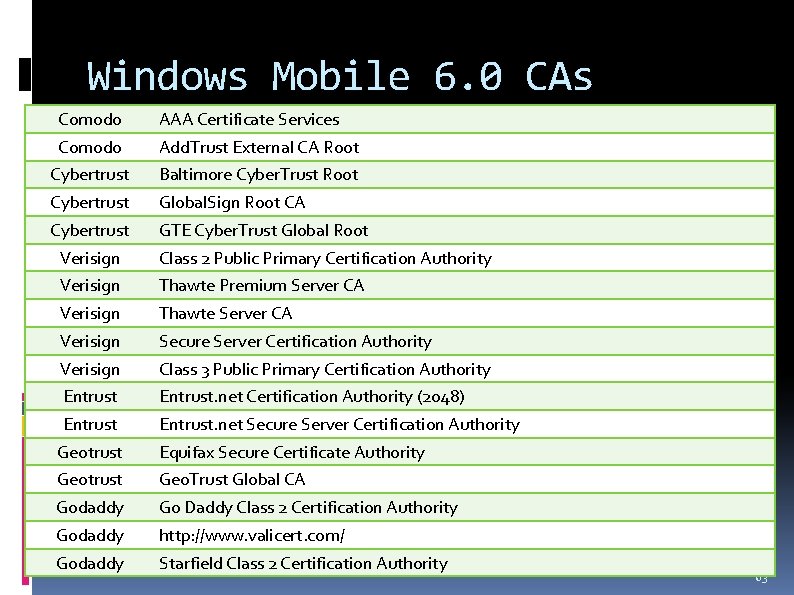
Windows Mobile 6. 0 CAs Comodo AAA Certificate Services Comodo Add. Trust External CA Root Cybertrust Baltimore Cyber. Trust Root Cybertrust Global. Sign Root CA Cybertrust GTE Cyber. Trust Global Root Verisign Class 2 Public Primary Certification Authority Verisign Thawte Premium Server CA Verisign Thawte Server CA Verisign Secure Server Certification Authority Verisign Class 3 Public Primary Certification Authority Entrust. net Certification Authority (2048) Entrust. net Secure Server Certification Authority Geotrust Equifax Secure Certificate Authority Geotrust Geo. Trust Global CA Godaddy Go Daddy Class 2 Certification Authority Godaddy http: //www. valicert. com/ Godaddy Starfield Class 2 Certification Authority 63

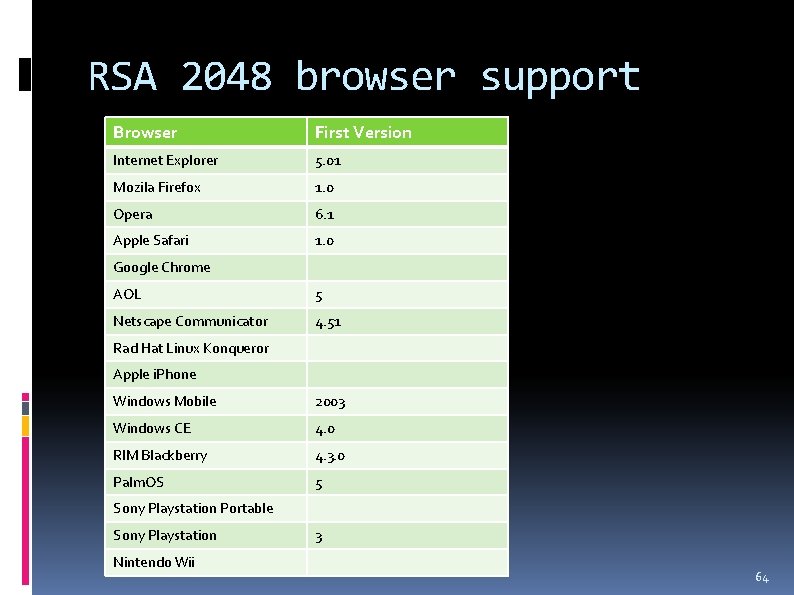
RSA 2048 browser support Browser First Version Internet Explorer 5. 01 Mozila Firefox 1. 0 Opera 6. 1 Apple Safari 1. 0 Google Chrome AOL 5 Netscape Communicator 4. 51 Rad Hat Linux Konqueror Apple i. Phone Windows Mobile 2003 Windows CE 4. 0 RIM Blackberry 4. 3. 0 Palm. OS 5 Sony Playstation Portable Sony Playstation Nintendo Wii 3 64

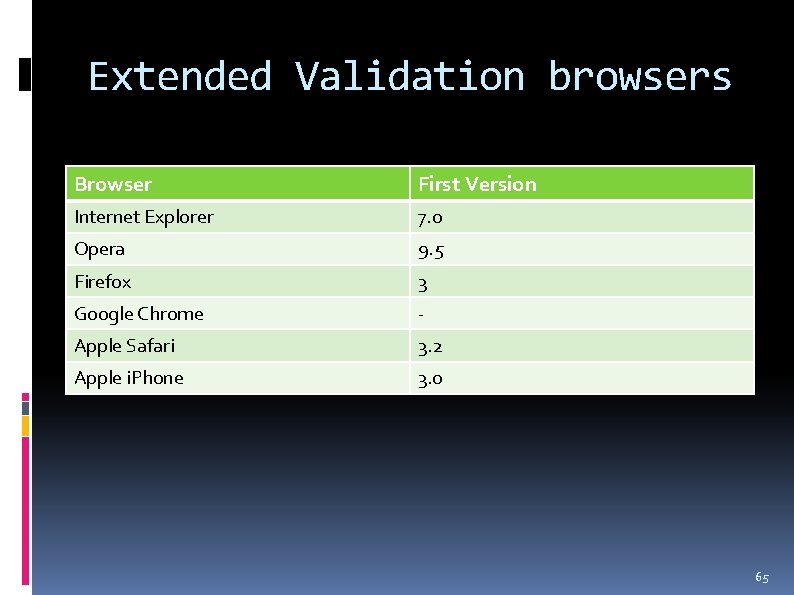
Extended Validation browsers Browser First Version Internet Explorer 7. 0 Opera 9. 5 Firefox 3 Google Chrome - Apple Safari 3. 2 Apple i. Phone 3. 0 65

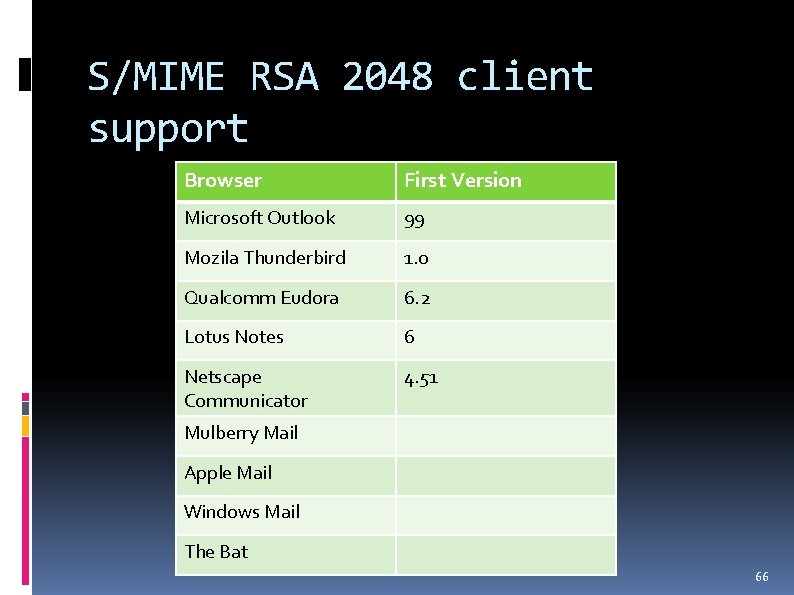
S/MIME RSA 2048 client support Browser First Version Microsoft Outlook 99 Mozila Thunderbird 1. 0 Qualcomm Eudora 6. 2 Lotus Notes 6 Netscape Communicator 4. 51 Mulberry Mail Apple Mail Windows Mail The Bat 66

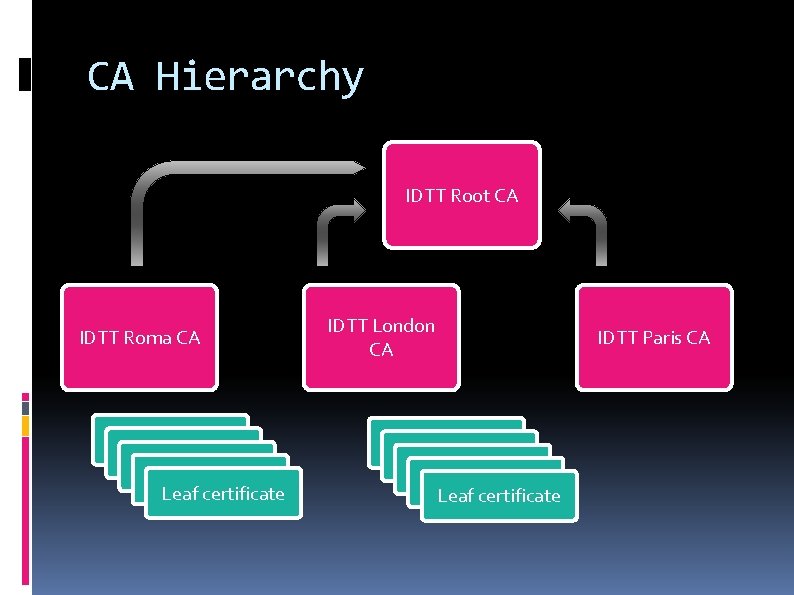
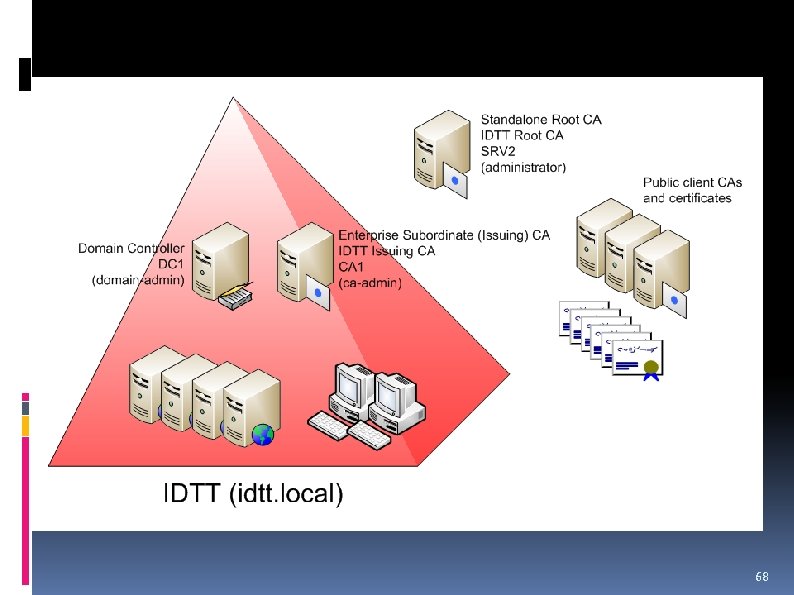
CA Hierarchy IDTT Root CA IDTT Roma CA Leaf certificate Leaf certificate IDTT London CA Leaf certificate Leaf certificate IDTT Paris CA

68

Ondřej Ševeček | PM Windows Server | GOPAS a. s. | MCM: Directory Services | MVP: Enterprise Security | ondrej@sevecek. com | www. sevecek. com | THANK YOU!