Ing Ondej eveek GOPAS a s MCM Directory








- Slides: 12

Ing. Ondřej Ševeček | GOPAS a. s. | MCM: Directory Services | MVP: Enterprise Security | CEH | ondrej@sevecek. com | www. sevecek. com | SMART CARD AND CERTIFICATE LOGON

Smart card logon Motivation Kerberos smart card logon vs. TLS client certificate authentication CA requirements Certificate requirements Enrollment agents

Motivation Passwords shorter than 12 chars are insecure Can be cracked from AD, local databases, password caches, NLTM and Kerberos traffic, LDAP simple bind, stored passwords, … Windows passwords are MD 4 Certificates are SHA-1 or SHA 2 random keys, not transported easily without smart cards

SHA-1 problems General brute-force attack at 2^80 4

Windows passwords 8 characters password? 80^8 possible passwords 2^x = 80^8 ? ? x * log 2 = 8 * log 80 x = 8 * log 80 / log 2 x ~= 51 10 characters ~= 2^63 12 characters ~= 2^76 5

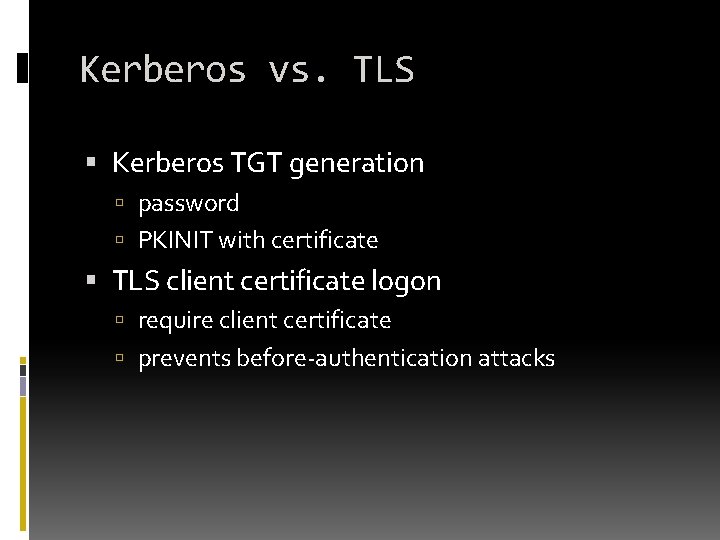
Kerberos vs. TLS Kerberos TGT generation password PKINIT with certificate TLS client certificate logon require client certificate prevents before-authentication attacks

CA requirements Trusted NTAuth trusted CRL/OCSP available

Certificate Requirements Domain Controllers name of the domain Smart Card Logon + Kerberos Authentication User certificates Kerberos PKINIT: Smart Card Logon TLS client certificate auth: Client Authentication

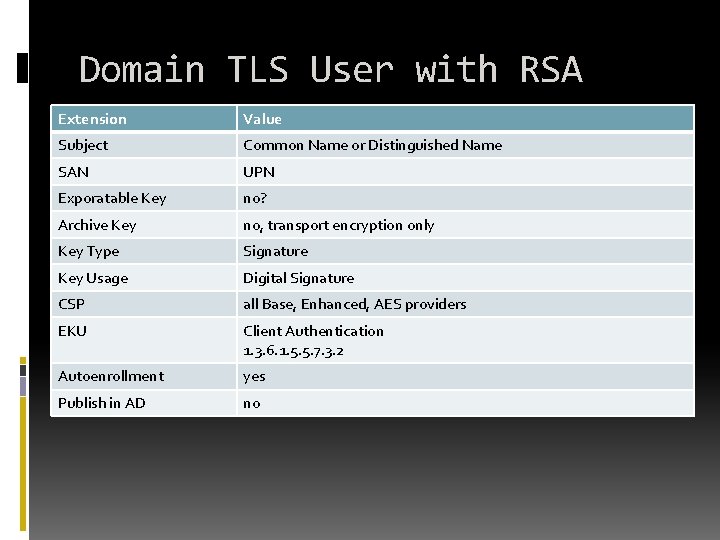
Domain TLS User with RSA Extension Value Subject Common Name or Distinguished Name SAN UPN Exporatable Key no? Archive Key no, transport encryption only Key Type Signature Key Usage Digital Signature CSP all Base, Enhanced, AES providers EKU Client Authentication 1. 3. 6. 1. 5. 5. 7. 3. 2 Autoenrollment yes Publish in AD no

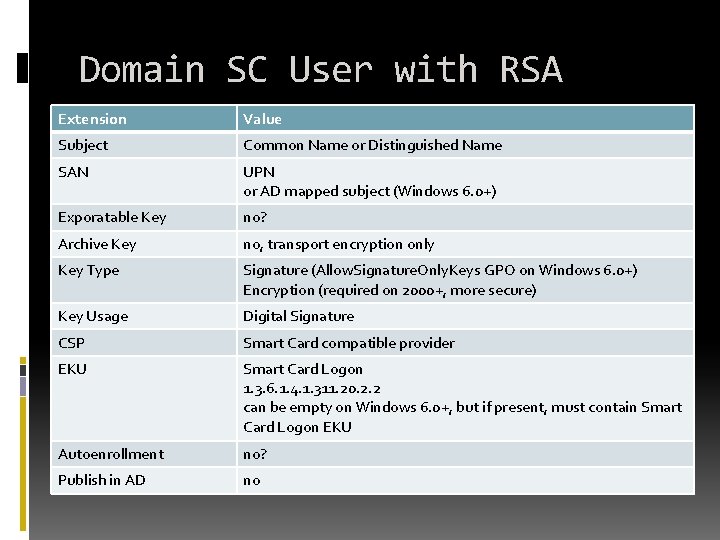
Domain SC User with RSA Extension Value Subject Common Name or Distinguished Name SAN UPN or AD mapped subject (Windows 6. 0+) Exporatable Key no? Archive Key no, transport encryption only Key Type Signature (Allow. Signature. Only. Keys GPO on Windows 6. 0+) Encryption (required on 2000+, more secure) Key Usage Digital Signature CSP Smart Card compatible provider EKU Smart Card Logon 1. 3. 6. 1. 4. 1. 311. 20. 2. 2 can be empty on Windows 6. 0+, but if present, must contain Smart Card Logon EKU Autoenrollment no? Publish in AD no

Enrollment Agent aka Registration Authority (RA) Generates requests signed by its own RA certificate AD CS can apply more granular policies

Ing. Ondřej Ševeček | GOPAS a. s. | MCM: Directory Services | MVP: Enterprise Security | CEH | ondrej@sevecek. com | www. sevecek. com | Smart card and certificate logon THANK YOU!




















