Chapter 15 Layer 7 Application Layer The application










- Slides: 39

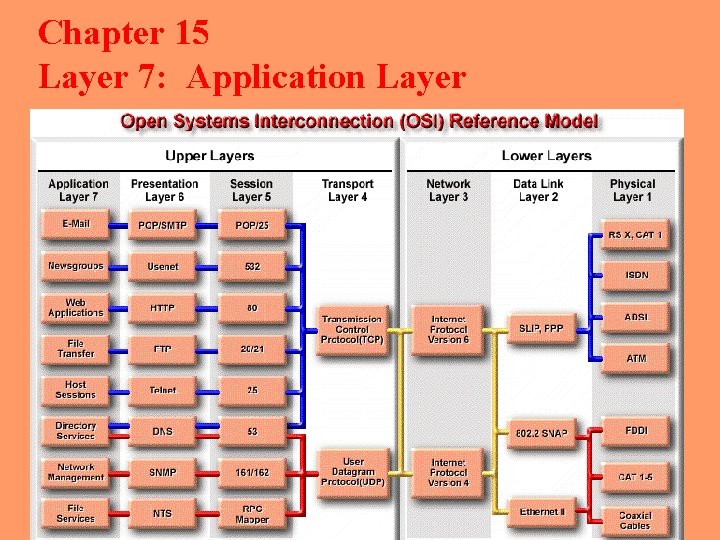
Chapter 15 Layer 7: Application Layer

The application layer (Layer 7 and closest to the user) supports the communicating component of an application. The application layer identifies and establishes the availability of intended communication partners, synchronizes cooperating applications, and establishes agreement on procedures for error recovery and control of data integrity.

The application layer does not provide services to any other OSI layer. • However, it does provide services to application processes lying outside the scope of the OSI model. • Examples of such application processes include spreadsheet programs, word processing programs, and banking terminal programs. • The application layer provides a direct interface for the rest of the OSI model by using NETWORK APPLICATIONS (e. g. www, e-mail, ftp, telnet) or an indirect interface by using standalone applications (e. g. word processors, spreadsheets, presentation managers, network redirector).

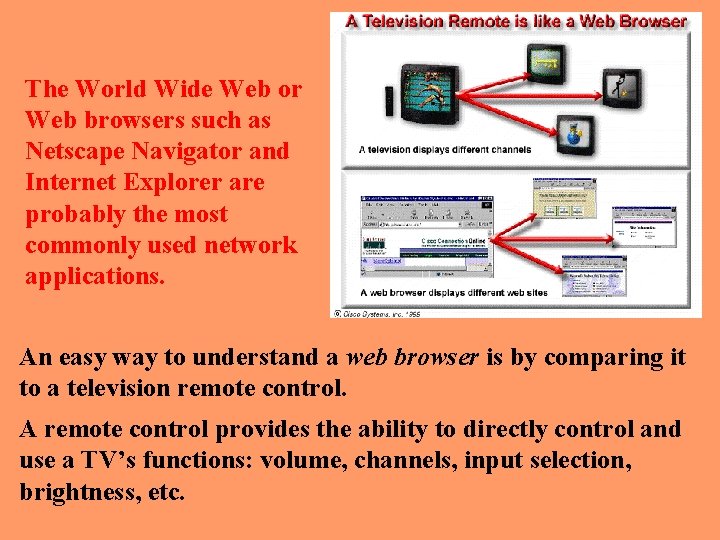
The World Wide Web or Web browsers such as Netscape Navigator and Internet Explorer are probably the most commonly used network applications. An easy way to understand a web browser is by comparing it to a television remote control. A remote control provides the ability to directly control and use a TV’s functions: volume, channels, input selection, brightness, etc.

The interactions that occur between a television and VCR can be used to illustrate the concept of an indirect interface. For example, if you use the controls to send a TV program to a VCR to be recorded, rather than to a screen for immediate viewing, the program can then be retrieved for later viewing.

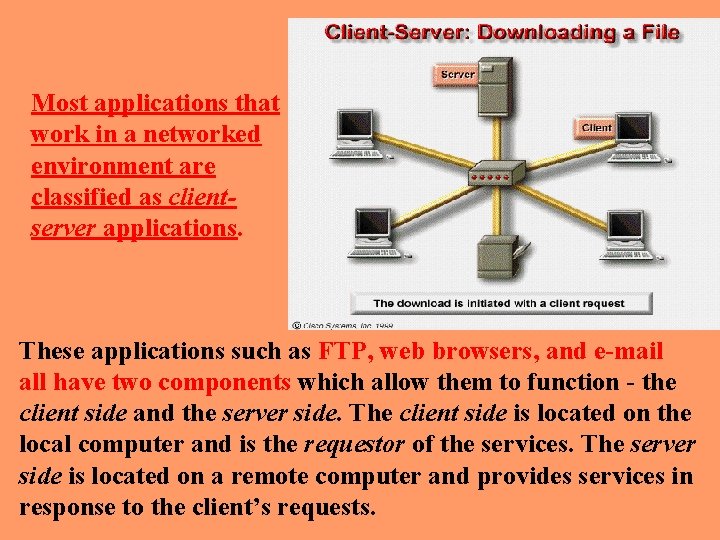
Most applications that work in a networked environment are classified as clientserver applications. These applications such as FTP, web browsers, and e-mail all have two components which allow them to function - the client side and the server side. The client side is located on the local computer and is the requestor of the services. The server side is located on a remote computer and provides services in response to the client’s requests.

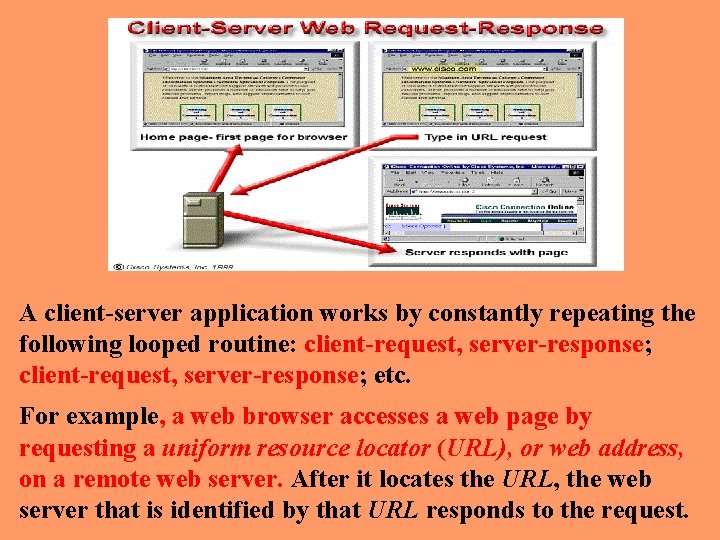
A client-server application works by constantly repeating the following looped routine: client-request, server-response; etc. For example, a web browser accesses a web page by requesting a uniform resource locator (URL), or web address, on a remote web server. After it locates the URL, the web server that is identified by that URL responds to the request.

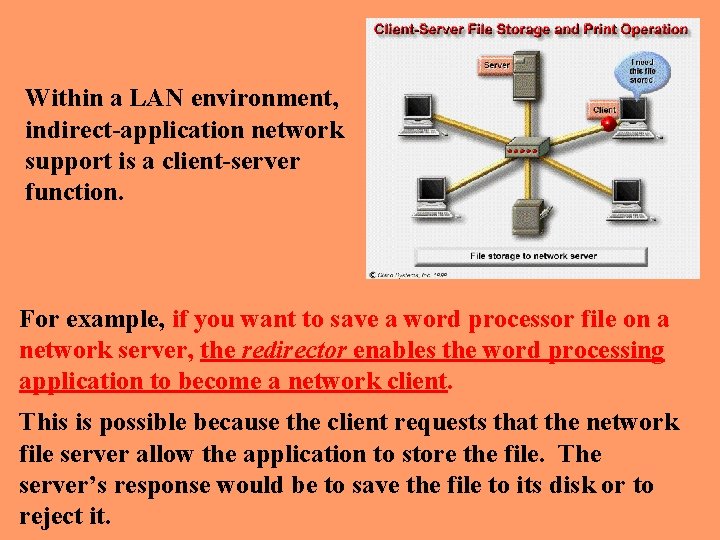
Within a LAN environment, indirect-application network support is a client-server function. For example, if you want to save a word processor file on a network server, the redirector enables the word processing application to become a network client. This is possible because the client requests that the network file server allow the application to store the file. The server’s response would be to save the file to its disk or to reject it.

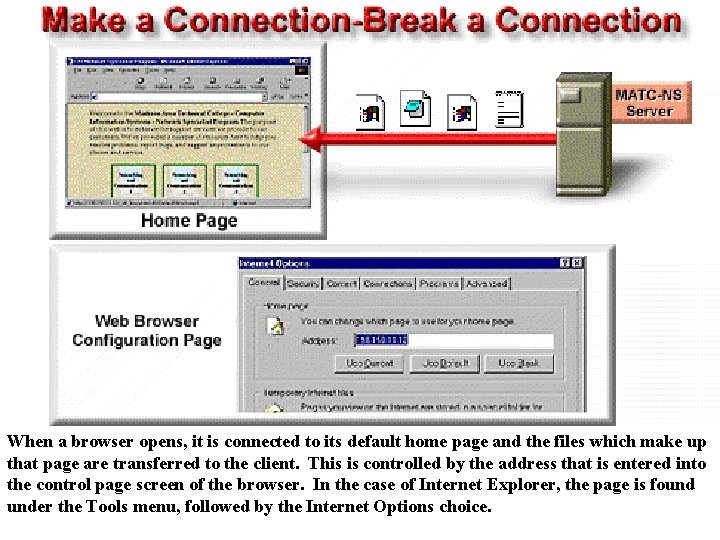
When a browser opens, it is connected to its default home page and the files which make up that page are transferred to the client. This is controlled by the address that is entered into the control page screen of the browser. In the case of Internet Explorer, the page is found under the Tools menu, followed by the Internet Options choice.

After the processing is completed, the connection is broken and must be re-established for the next processing request to take place. This is one of the two ways that communication processing takes place. The second method, as illustrated in the Telnet and FTP examples, establishes a connection to the server and maintains that connection until all processing is performed. The client computer terminates the connection when the user determines that he/she has finished. All communication activity falls into one of these two categories.

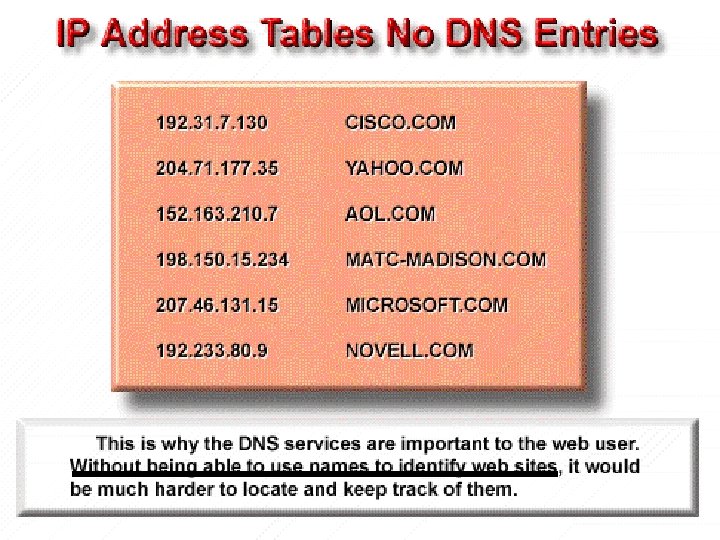
In the network layer chapter, you learned that the Internet is built on a hierarchical addressing scheme. This allows for routing that is based on address classes (IP) as opposed to individual addresses. The problem this creates for the user is associating the correct address with the Internet site.




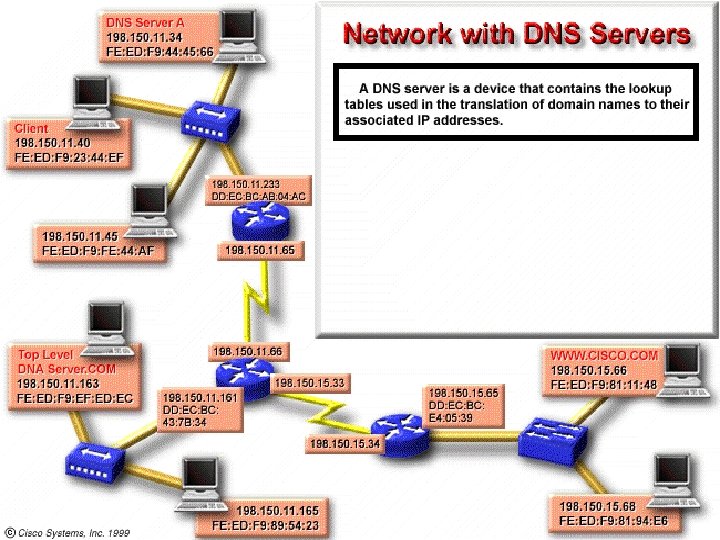
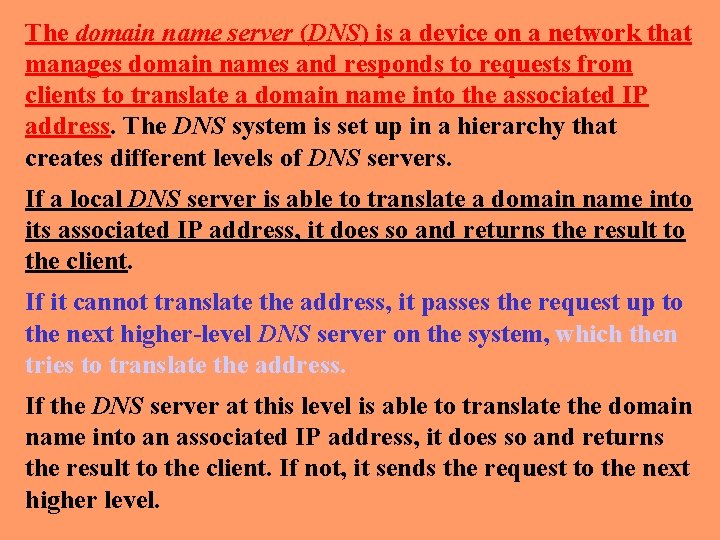
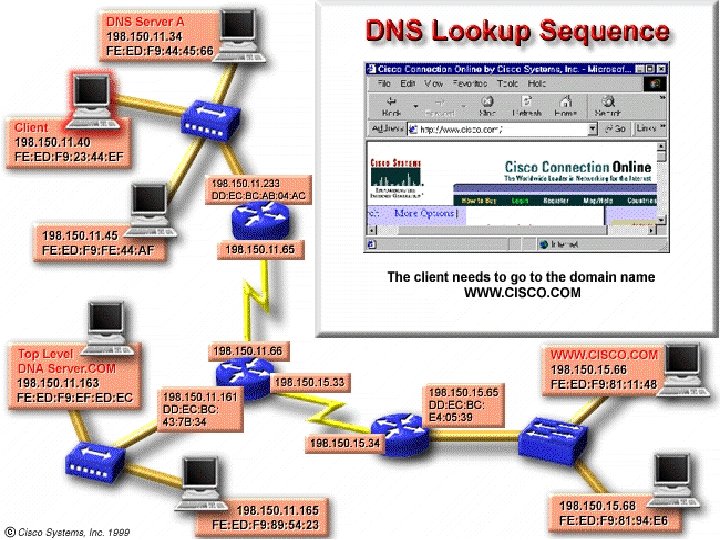
The domain name server (DNS) is a device on a network that manages domain names and responds to requests from clients to translate a domain name into the associated IP address. The DNS system is set up in a hierarchy that creates different levels of DNS servers. If a local DNS server is able to translate a domain name into its associated IP address, it does so and returns the result to the client. If it cannot translate the address, it passes the request up to the next higher-level DNS server on the system, which then tries to translate the address. If the DNS server at this level is able to translate the domain name into an associated IP address, it does so and returns the result to the client. If not, it sends the request to the next higher level.


Computer applications -- Netscape Navigator and Internet Explorer are browsers -- are classified "above" the 7 layers of the OSI model. It is only when such programs make network requests and require network services that they are dealing with OSI layer 7 protocols such as POP 3, DNS, http, and ftp. Not everything fits within the OSI model.

Each application program type is associated with its own application protocol. Although, there are more program and protocol types available, the following are the main focus of this chapter: · E-mail programs support the POP 3 application layer protocol for electronic mail. · File utility programs use the FTP protocol for copying and moving files between remote sites. · Remote access programs use the Telnet protocol for directly connecting to remote resources. · Network data gathering and monitoring use the SNMP protocol. · The world wide web uses the HTTP protocol. It is important to re-emphasize the fact that the application layer is just another protocol layer in the OSI or TCP/IP models.

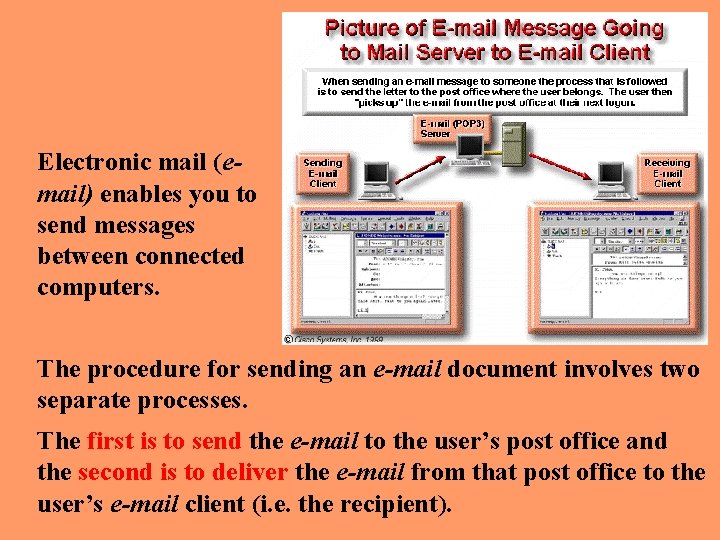
Electronic mail (email) enables you to send messages between connected computers. The procedure for sending an e-mail document involves two separate processes. The first is to send the e-mail to the user’s post office and the second is to deliver the e-mail from that post office to the user’s e-mail client (i. e. the recipient).

Examine the e-mail address. This is an example of what it may look like: slhain@mpsaz. org It consists of two parts: the recipient’s name (located before the @ sign), and the recipient’s post office address (after the @ sign). The recipient’s name is only important after the message arrives at the post office address, which is a DNS entry that represents the IP address of the post office server.

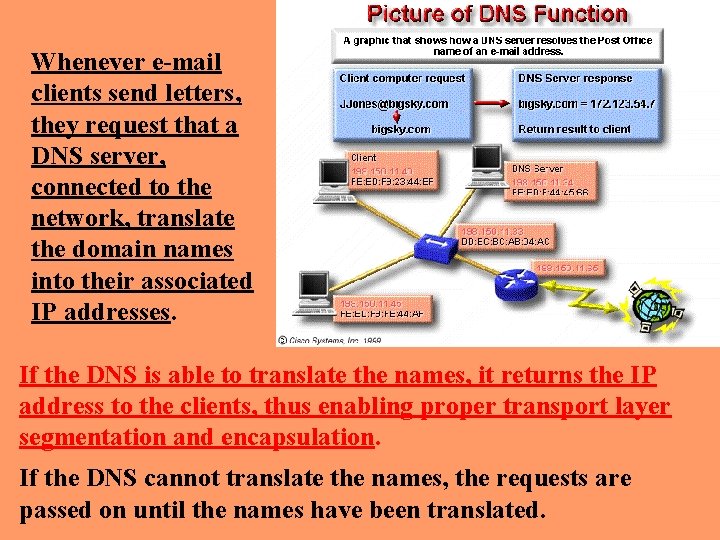
Whenever e-mail clients send letters, they request that a DNS server, connected to the network, translate the domain names into their associated IP addresses. If the DNS is able to translate the names, it returns the IP address to the clients, thus enabling proper transport layer segmentation and encapsulation. If the DNS cannot translate the names, the requests are passed on until the names have been translated.

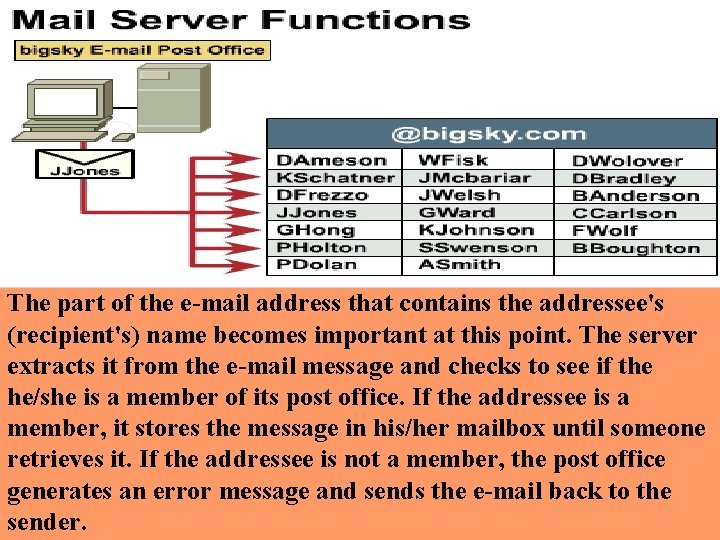
The part of the e-mail address that contains the addressee's (recipient's) name becomes important at this point. The server extracts it from the e-mail message and checks to see if the he/she is a member of its post office. If the addressee is a member, it stores the message in his/her mailbox until someone retrieves it. If the addressee is not a member, the post office generates an error message and sends the e-mail back to the sender.

The second part of the emailing process is the receiving process. E-mail message recipients must use the e-mail client software on their computers to establish requests to the e-mail post offices. When message recipients click the "Get Mail" or "Retrieve Mail" buttons on the e-mail client, they are usually prompted for a password. After they enter the password and click "OK", the e-mail software builds a request for the post office servers, which then extract the post office addresses from the configuration data that was entered when their e-mail software was configured. The process then uses another DNS lookup to find the IP addresses of the servers. Finally, the requests are then segmented and sequenced by the Transport Layer.

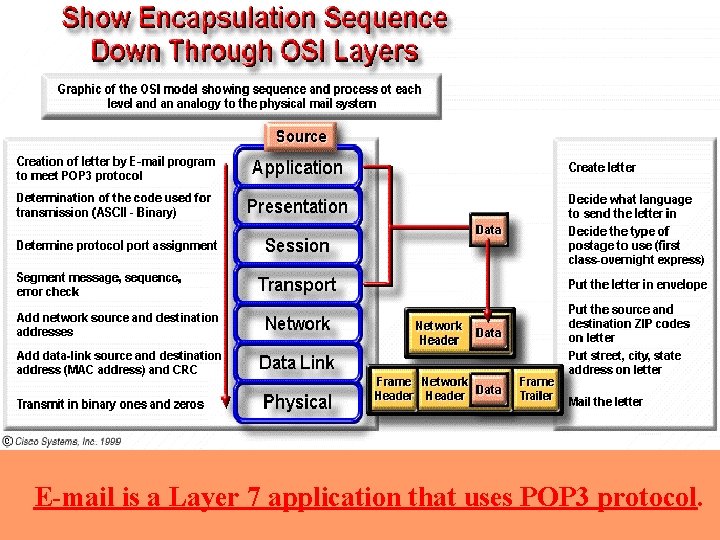
E-mail is a Layer 7 application that uses POP 3 protocol.

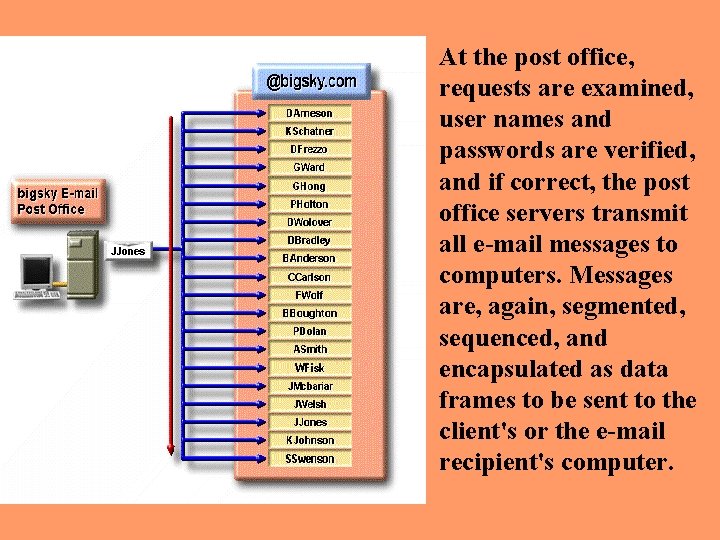
At the post office, requests are examined, user names and passwords are verified, and if correct, the post office servers transmit all e-mail messages to computers. Messages are, again, segmented, sequenced, and encapsulated as data frames to be sent to the client's or the e-mail recipient's computer.

E-mail messages themselves are normally sent as ASCII text, but the attachments that are sometimes included with them can be audio, video, graphic, or many other types of data. To correctly receive and send attachments, the encoding schemes must be the same on both the sending and the receiving computer. The two most common formats for e-mail attachments are MIME and uuencode (Unix).

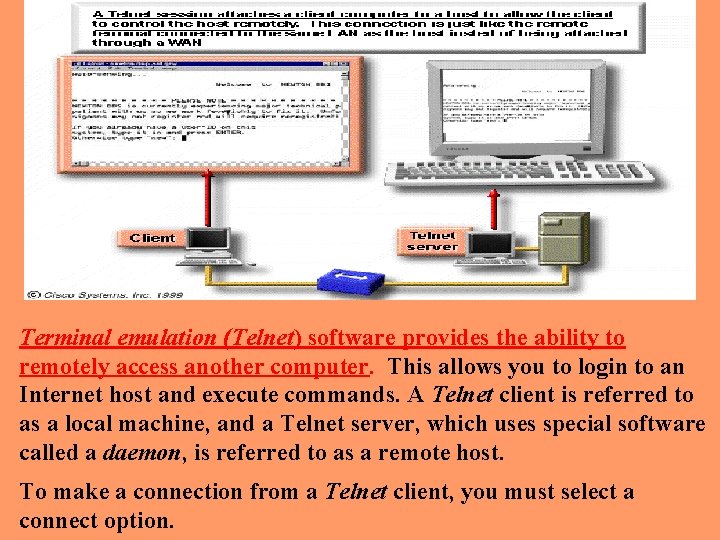
Terminal emulation (Telnet) software provides the ability to remotely access another computer. This allows you to login to an Internet host and execute commands. A Telnet client is referred to as a local machine, and a Telnet server, which uses special software called a daemon, is referred to as a remote host. To make a connection from a Telnet client, you must select a connect option.

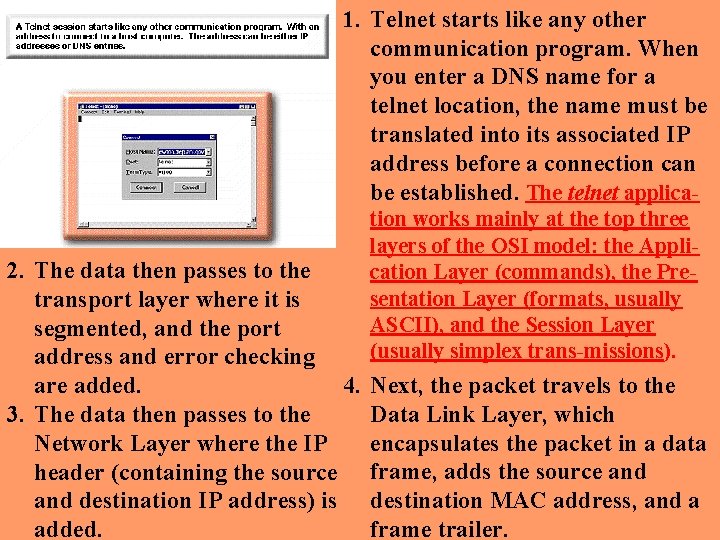
1. Telnet starts like any other communication program. When you enter a DNS name for a telnet location, the name must be translated into its associated IP address before a connection can be established. The telnet applica 2. The data then passes to the transport layer where it is segmented, and the port address and error checking 4. are added. 3. The data then passes to the Network Layer where the IP header (containing the source and destination IP address) is added. tion works mainly at the top three layers of the OSI model: the Application Layer (commands), the Presentation Layer (formats, usually ASCII), and the Session Layer (usually simplex trans-missions). Next, the packet travels to the Data Link Layer, which encapsulates the packet in a data frame, adds the source and destination MAC address, and a frame trailer.

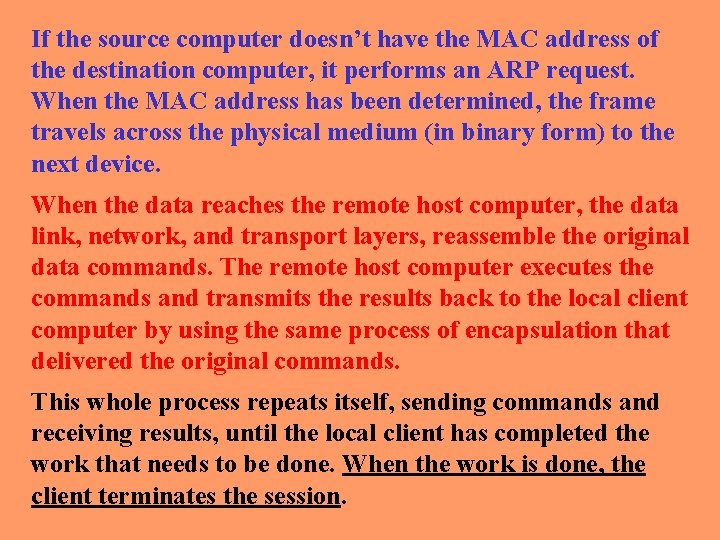
If the source computer doesn’t have the MAC address of the destination computer, it performs an ARP request. When the MAC address has been determined, the frame travels across the physical medium (in binary form) to the next device. When the data reaches the remote host computer, the data link, network, and transport layers, reassemble the original data commands. The remote host computer executes the commands and transmits the results back to the local client computer by using the same process of encapsulation that delivered the original commands. This whole process repeats itself, sending commands and receiving results, until the local client has completed the work that needs to be done. When the work is done, the client terminates the session.

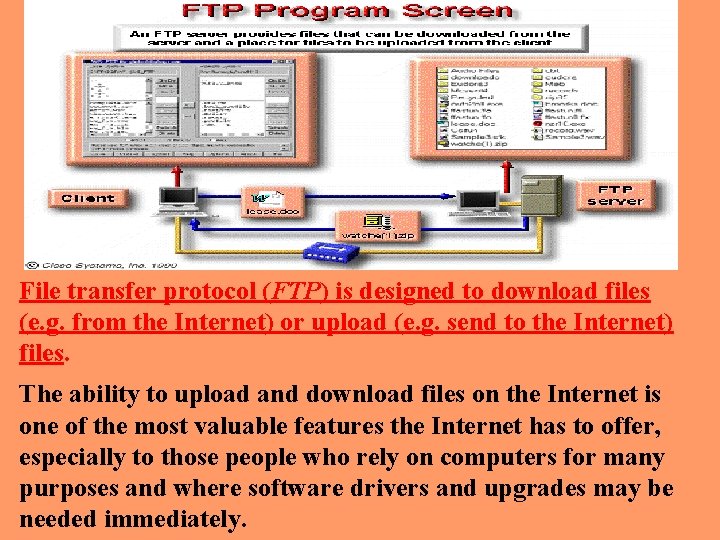
File transfer protocol (FTP) is designed to download files (e. g. from the Internet) or upload (e. g. send to the Internet) files. The ability to upload and download files on the Internet is one of the most valuable features the Internet has to offer, especially to those people who rely on computers for many purposes and where software drivers and upgrades may be needed immediately.

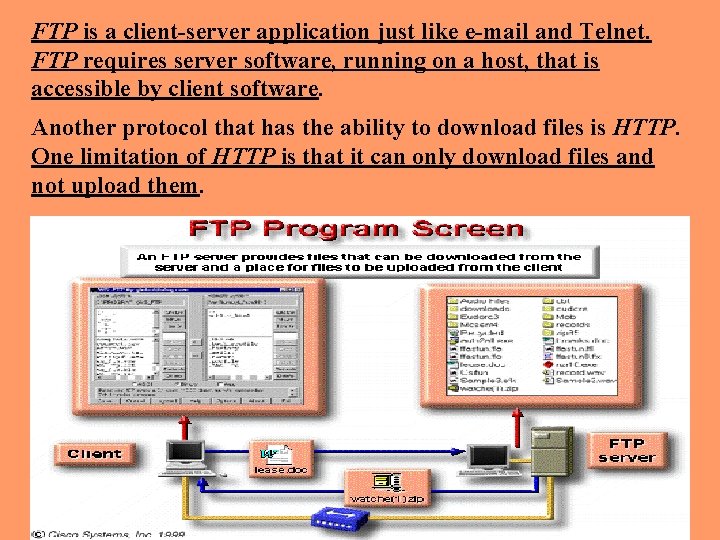
FTP is a client-server application just like e-mail and Telnet. FTP requires server software, running on a host, that is accessible by client software. Another protocol that has the ability to download files is HTTP. One limitation of HTTP is that it can only download files and not upload them.

An FTP session is established the same way in which a Telnet session is established. The main purpose of the FTP protocol is to transfer files from one computer to another by copying and moving files from server to client and client to server. FTP establishes a second connection, a data link between the computers, across which the data is transferred. Data transfer can occur in ASCII mode or binary mode. These two modes determine how the data file is transferred between the stations. When the file transfer is complete, the data connection is terminated automatically.

Hyper. Text Transfer Protocol (HTTP) works with the World Wide Web. A Web browser (along with all the other network applications covered in this chapter) is a client-server application, which means that it requires both a client and a server component in order to function. A Web browser presents data in multimedia formats on web pages that use text, graphics, sound, and video.

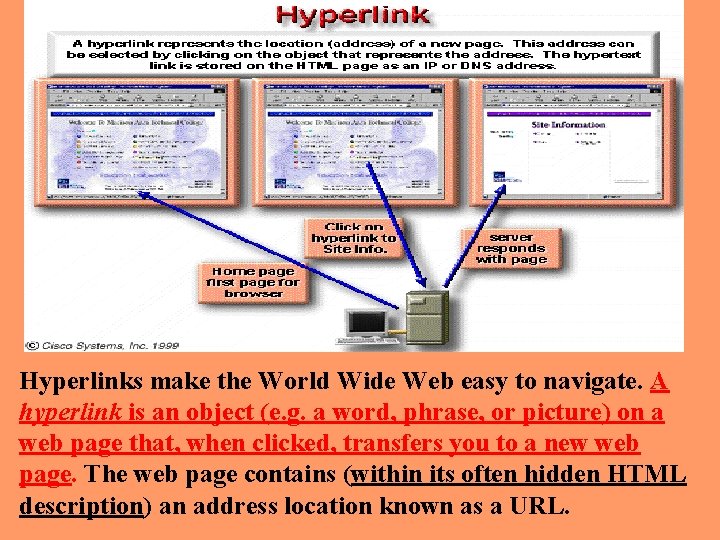
Hyperlinks make the World Wide Web easy to navigate. A hyperlink is an object (e. g. a word, phrase, or picture) on a web page that, when clicked, transfers you to a new web page. The web page contains (within its often hidden HTML description) an address location known as a URL.


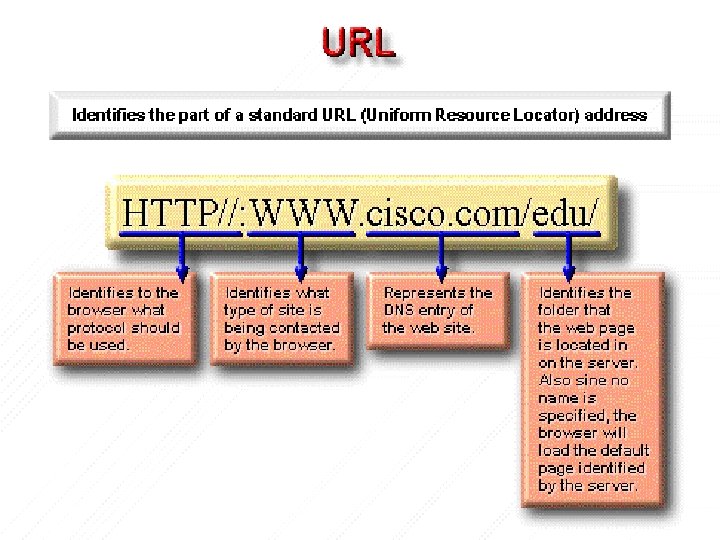
The Web browser first examines the protocol to determine if it needs to shell to, or open, another program, then determines the IP address of the Web server (by using DNS resolution on the domain name). After that, the transport, network, data-link, and physical layers initiate a session with the Web server. The data that is transferred to the HTTP server contains the folder name of web page location. (Note: The data can also contain a specific file name for an HTML page). If no name is given, the server uses a default name (as specified in the server’s configuration). The server responds to the request by sending all of the text, audio, video, and graphic files, as specified in the HTML page, to the Web client. The client browser reassembles all the files to create a view of the web page and then terminates the session.

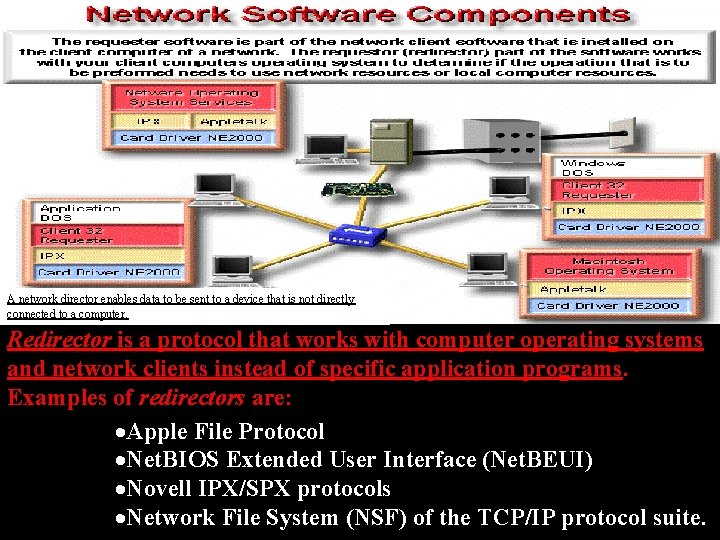
A network director enables data to be sent to a device that is not directly connected to a computer. Redirector is a protocol that works with computer operating systems and network clients instead of specific application programs. Examples of redirectors are: ·Apple File Protocol ·Net. BIOS Extended User Interface (Net. BEUI) ·Novell IPX/SPX protocols ·Network File System (NSF) of the TCP/IP protocol suite.

Redirector allows a network administrator to assign remote resources to logical names on the local client. When you select one of these logical names to perform an operation such as saving a file, or printing a file, the network redirector sends the selected file to the proper remote resource on the network for processing. If the resource is on a local computer, the redirector ignores the request
