Access Control and Site Security Chapter 2 Panko



























































- Slides: 89

Access Control and Site Security Chapter 2 Panko, Corporate Computer and Network Security Copyright 2004 Prentice-Hall

Access Control Processes

Figure 2 -1: Access Control n Access Control ¡ Access control is the policy-driven limitation of access to systems, data, and dialogs ¡ Prevent attackers from gaining access, stopping them if they do 3

Figure 2 -1: Access Control n n First Steps ¡ Enumeration of Resources ¡ Sensitivity of Each Resource Next, who Should Have Access? ¡ Can be made individual by individual ¡ More efficient to define by roles (logged-in users, system administrators, project team members, etc. ) 4

Figure 2 -1: Access Control n What Access Permissions (Authorizations) Should They Have? ¡ Access permissions (authorizations) define whether a role or individual should have any access at all ¡ If so, exactly what the role or individual should be allowed to do to the resource. ¡ Usually given as a list of permissions for users to be able to do things (read, change, execute program, etc. ) for each resource 5

Figure 2 -1: Access Control n How Should Access Control Be Implemented? ¡ For each resource, need an access protection plan for how to implement protection in keeping with the selected control policy ¡ For a file on a server, for instance, limit authorizations to a small group, harden the server against attack, use a firewall to thwart external attackers, etc. ¡ … 6

Figure 2 -1: Access Control n Policy-Based Access Control and Protection ¡ Have a specific access control policy and an access protection policy for each resource ¡ Focuses attention on each resource ¡ Guides the selection and configuration of firewalls and other protections ¡ Guides the periodic auditing and testing of protection plans 7

Password-Based Access Control

Figure 2 -2: Server Password Cracking: shibboleth n n Reusable Passwords ¡ A password you use repeatedly to get access to a resource on multiple occasions ¡ Bad because attacker will have time to learn it; then can use it Difficulty of Cracking Passwords by Guessing Remotely ¡ Usually cut off after a few attempts ¡ However, if can steal the password file, can crack passwords at leisure 9

Figure 2 -2: Server Password Cracking n Hacking Root ¡ Super accounts (can take any action in any directory) ¡ Hacking root in UNIX ¡ Super accounts in Windows (administrator) and Net. Ware (supervisor) ¡ Hacking root is rare; usually can only hack an ordinary user account ¡ May be able to elevate the privileges of the user account to take root action 10

Figure 2 -2: Server Password Cracking n Physical Access Password Cracking ¡ l 0 phtcrack n Lower-case L, zero, phtcrack n Password cracking program n Run on a server (need physical access) n Or copy password file and run l 0 phtcrack on another machine. 11

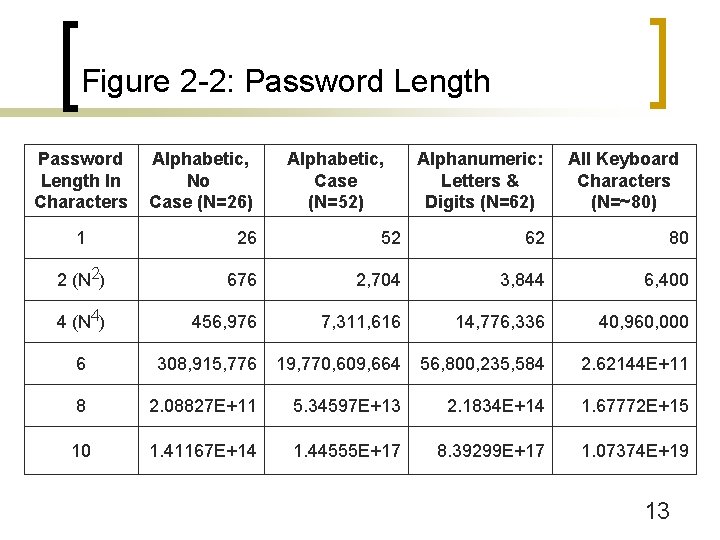
Figure 2 -2: Server Password Cracking n Physical Access Password Cracking ¡ Brute-force password guessing n Try all possible character combinations n Longer passwords take longer to crack n Using more characters also takes longer ¡ Alphabetic, no case (26 possibilities) ¡ Alphabetic, case (52) ¡ Alphanumeric (letters and numbers) (62) ¡ All keyboard characters (~80) 12

Figure 2 -2: Password Length In Characters Alphabetic, No Case (N=26) Alphabetic, Case (N=52) Alphanumeric: Letters & Digits (N=62) All Keyboard Characters (N=~80) 1 26 52 62 80 2 (N 2) 676 2, 704 3, 844 6, 400 4 (N 4) 456, 976 7, 311, 616 14, 776, 336 40, 960, 000 6 308, 915, 776 19, 770, 609, 664 56, 800, 235, 584 2. 62144 E+11 8 2. 08827 E+11 5. 34597 E+13 2. 1834 E+14 1. 67772 E+15 10 1. 41167 E+14 1. 44555 E+17 8. 39299 E+17 1. 07374 E+19 13

Figure 2 -2: Server Password Cracking n Physical Access Password Cracking ¡ Brute Force Attacks n Try all possible character combinations n Slow with long passwords length ¡ Dictionary attacks n Try common words (“password”, “ouch, ” etc. ) n There are only a few thousand of these n Cracked very rapidly ¡ Hybrid attacks n Common word with single digit at end, etc. 14

Figure 2 -2: Server Password Cracking n Password Policies ¡ Good passwords n At least 6 characters long n Change of case not at beginning n Digit (0 through 9) not at end n Other keyboard character not at end n Example: tri. V 6#ial 15

Figure 2 -2: Server Password Cracking n Password Policies ¡ ¡ Testing and enforcing password policies n Run password cracking program against own servers n Caution: requires approval! Sys. Admins have been fired for doing this without permission— and should be Password duration policies: How often passwords must be changed 16

Figure 2 -2: Server Password Cracking n Password Policies ¡ Password sharing policies: Generally, forbid shared passwords n Removes ability to learn who took actions; loses accountability n Usually is not changed often or at all because of need to inform all sharers 17

Figure 2 -2: Server Password Cracking n Password Policies ¡ Disabling passwords that are no longer valid n As soon as an employee leaves the firm, etc. n As soon as contractors, consultants leave n In many firms, a large percentage of all accounts are for people no longer with the firm 18

Figure 2 -2: Server Password Cracking n Password Policies ¡ Lost passwords n Password resets: Help desk gives new password for the account n Opportunities for social engineering attacks n Leave changed password on answering machine n Biometrics: voice print identification for requestor (but considerable false rejection rate) New: Not In Book 19

Figure 2 -2: Server Password Cracking n Password Policies ¡ Lost passwords n Automated password resets ¡ Employee goes to website ¡ Must answer a question, such as “In what city were you born? ” ¡ Problem of easily-guessed questions that can be answered with research 20

Figure 2 -5: UNIX/etc/passwd File Entries Without Shadow Password File User Name User ID GCOS Shell plee: 6 babc 345 d 7256: 47: 3: Pat Lee: /usr/plee/: /bin/csh Password Group ID Home Directory With Shadow Password File Plee: x: 47: 3: Pat Lee: /usr/plee/: /bin/csh The x indicates that the password is stored in a separate shadow password file 21

Figure 2 -5: UNIX/etc/passwd File Entries n n Unix passwd File ¡ Contains the username, password, and other information is semi-standard form ¡ In the /etc directory that is accessible to anyone ¡ Anyone can steal the passwd file and crack the passwords Unix Shadow File ¡ Newer versions of Unix store passwords in a protected shadow file ¡ In the passwd file, there is an x in the password position 22

Figure 2 -2: Server Password Cracking n Password Policies ¡ Encrypted (hashed) password files (Figure 2 -4) n Passwords not stored in readable form n Encrypted with DES or hashed with MD 5 n In UNIX, etc/passwd puts x in place of password n Encrypted or hashed passwords are stored in a different (shadow) file to which only highlevel accounts have access 23

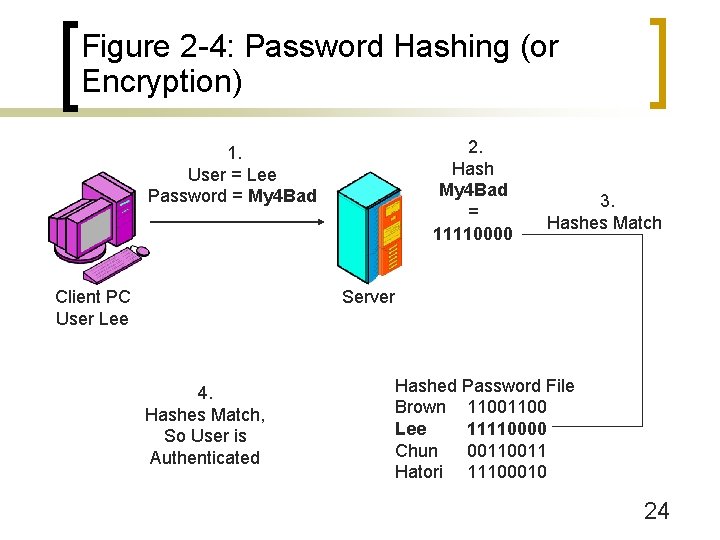
Figure 2 -4: Password Hashing (or Encryption) 2. Hash My 4 Bad = 11110000 1. User = Lee Password = My 4 Bad Client PC User Lee 3. Hashes Match Server 4. Hashes Match, So User is Authenticated Hashed Password File Brown 1100 Lee 11110000 Chun 0011 Hatori 11100010 24

Figure 2 -2: Server Password Cracking n Password Policies ¡ Windows passwords n Obsolete LAN manager passwords (7 characters maximum) should not be used n Windows NTLM passwords are better n Option (not default) to enforce strong passwords 25

Figure 2 -2: Server Password Cracking n Shoulder Surfing ¡ n Watch someone as they type their password Keystroke Capture Software ¡ Professional versions of windows protect RAM during password typing ¡ Consumer versions do not ¡ Trojan horse throws up a login screen later, reports its finding to attackers 26

Figure 2 -2: Server Password Cracking n Windows Client PC Software ¡ Consumer version login screen is not for security n Windows professional and server versions provide good security with the login password ¡ BIOS passwords allow boot-up security n Can be disabled by removing the PC’s battery n But during a battery removal, the attacker will be very visible ¡ Screen savers with passwords allow away-fromdesk security after boot-up 27

Building Security

Figure 2 -6: Building Security n Building Security Basics ¡ Single point of (normal) entry to building ¡ Fire doors, etc. : use closed-circuit television (CCTV) and alarms to monitor them ¡ Security centers n Monitors for closed-circuit TV (CCTV) n n Videotapes that must be retained (Don’t reuse too much or the quality will be bad) Alarms 29

Figure 2 -6: Building Security n Building Security Basics ¡ Interior doors to control access between parts of the building n Piggybacking: holding the door open so that someone can enter without identification defeats this protection ¡ Enforcing policies: You get what you enforce ¡ Training security personnel ¡ Training all employees 30

Figure 2 -6: Building Security n Building Security Basics ¡ Phone stickers with security center phone number ¡ Thwarting piggybacking by employee education and sanctions for allowing it ¡ Dumpster diving by keeping Dumpsters in locked, lighted area ¡ Drive shredding programs for discarded disk drives that do more than reformat drives 31

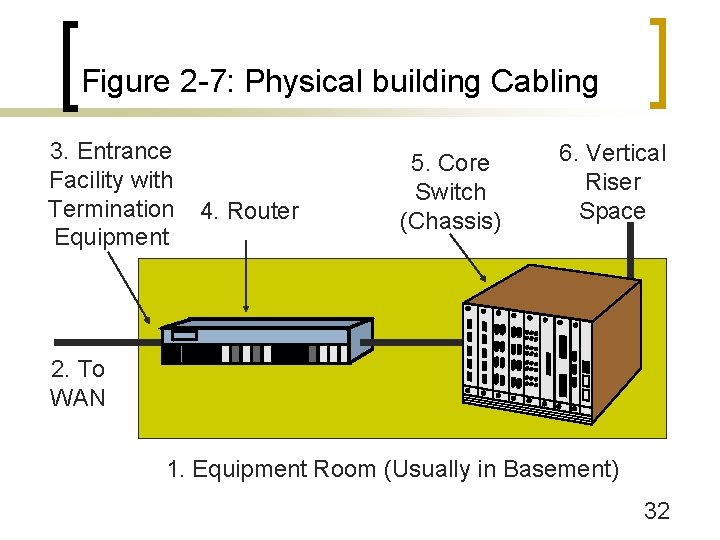
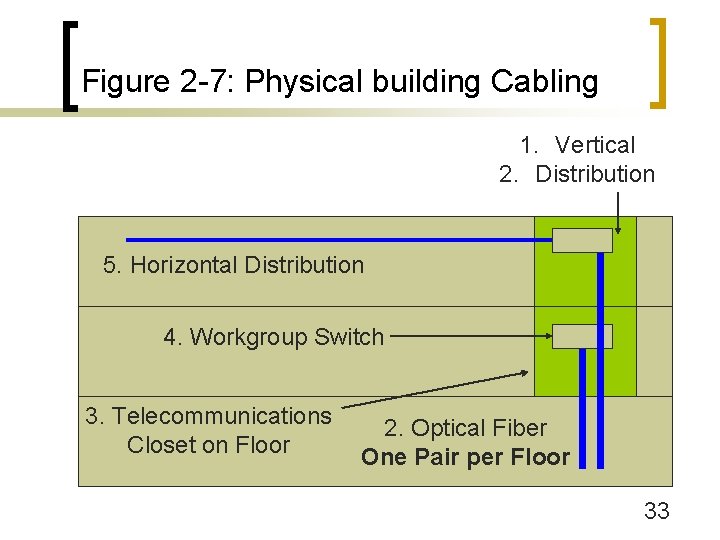
Figure 2 -7: Physical building Cabling 3. Entrance Facility with Termination Equipment 4. Router 5. Core Switch (Chassis) 6. Vertical Riser Space 2. To WAN 1. Equipment Room (Usually in Basement) 32

Figure 2 -7: Physical building Cabling 1. Vertical 2. Distribution 5. Horizontal Distribution 4. Workgroup Switch 3. Telecommunications Closet on Floor 2. Optical Fiber One Pair per Floor 33

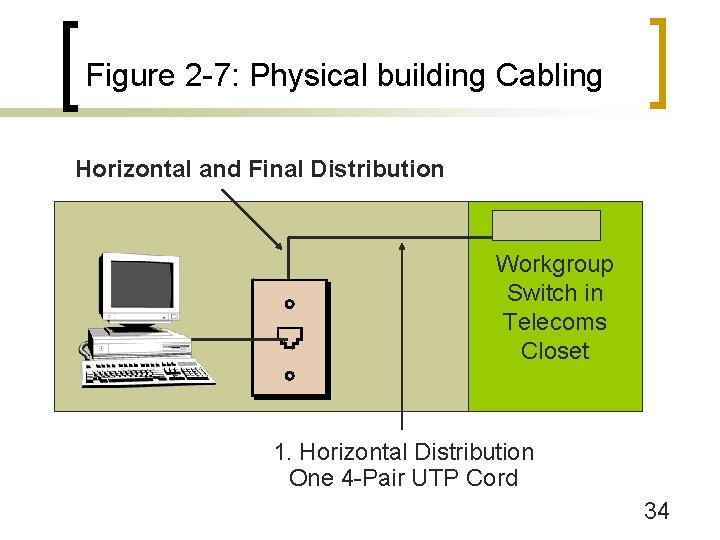
Figure 2 -7: Physical building Cabling Horizontal and Final Distribution Workgroup Switch in Telecoms Closet 1. Horizontal Distribution One 4 -Pair UTP Cord 34

Figure 2 -6: Building Security n Data Wiring Security ¡ Telecommunications closets should be locked ¡ Wiring conduits should be hard to cut into ¡ Servers rooms should have strong access security 35

Access Cards and Tokens

Figure 2 -8: Access Cards n Magnetic Stripe Cards n Smart Cards ¡ Have a microprocessor and RAM ¡ More sophisticated than mag stripe cards ¡ Release only selected information to different access devices 37

Figure 2 -8: Access Cards n Tokens ¡ Small device with constantly-changing password ¡ Or device that can plug into USB port or another port New n Proximity Tokens New ¡ Use short-range radio transmission ¡ Can be detected and tested without physical contact ¡ Allows easier access; used in Tokyo subways 38

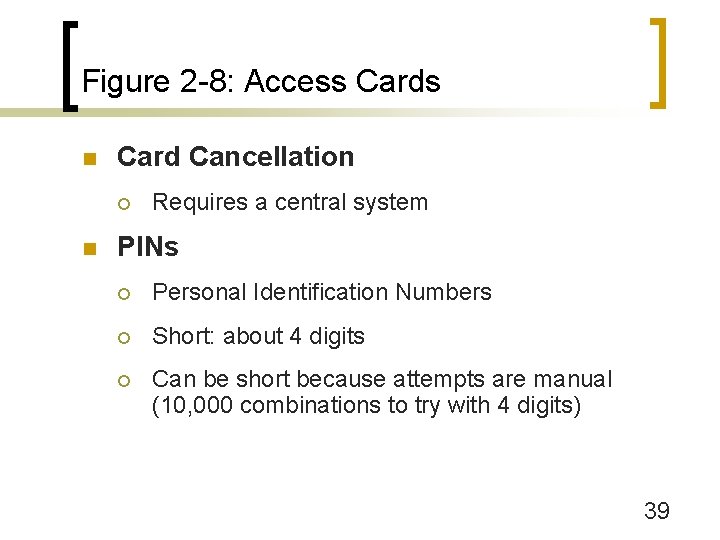
Figure 2 -8: Access Cards n Card Cancellation ¡ n Requires a central system PINs ¡ Personal Identification Numbers ¡ Short: about 4 digits ¡ Can be short because attempts are manual (10, 000 combinations to try with 4 digits) 39

Figure 2 -8: Access Cards n PINs ¡ Should not allow obvious combinations (1111, 1234) or important dates ¡ Provide two-factor authentication n E. g. , PIN and card n Don’t allow writing PIN on card 40

Biometric Authentication

Figure 2 -9: Biometric Authentication n n Biometric Authentication ¡ Authentication based on body measurements and motions ¡ Because you always bring your body with you Biometric Systems (Figure 2 -10) ¡ Enrollment ¡ Later access attempts n Acceptance or rejection 42

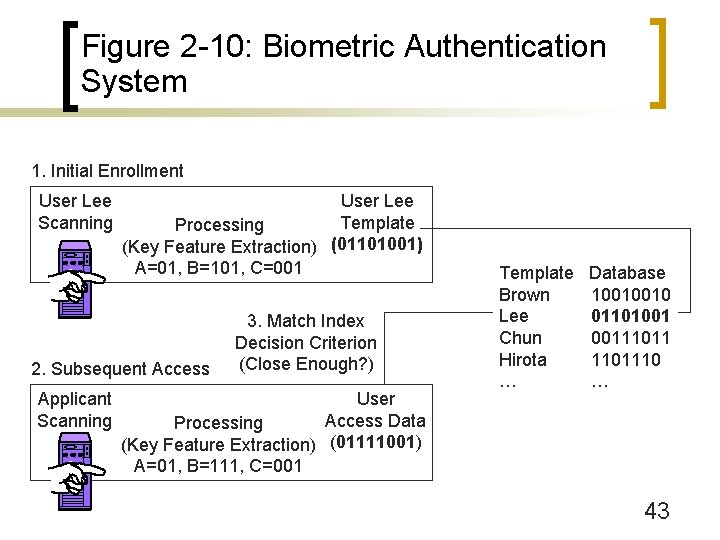
Figure 2 -10: Biometric Authentication System 1. Initial Enrollment User Lee Scanning User Lee Template Processing (Key Feature Extraction) (01101001) A=01, B=101, C=001 2. Subsequent Access Applicant Scanning 3. Match Index Decision Criterion (Close Enough? ) User Access Data Processing (Key Feature Extraction) (01111001) A=01, B=111, C=001 Template Brown Lee Chun Hirota … Database 10010010 01101001 0011101110 … 43

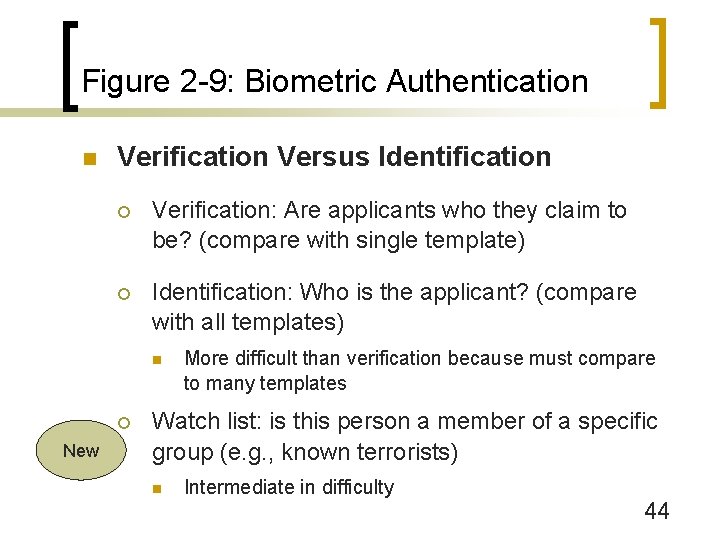
Figure 2 -9: Biometric Authentication n Verification Versus Identification ¡ Verification: Are applicants who they claim to be? (compare with single template) ¡ Identification: Who is the applicant? (compare with all templates) n ¡ New More difficult than verification because must compare to many templates Watch list: is this person a member of a specific group (e. g. , known terrorists) n Intermediate in difficulty 44

Figure 2 -9: Biometric Authentication n Verification Versus Identification ¡ Verification is good for replacing passwords in logins ¡ Identification is good for door access and other situations where entering a name would be difficult 45

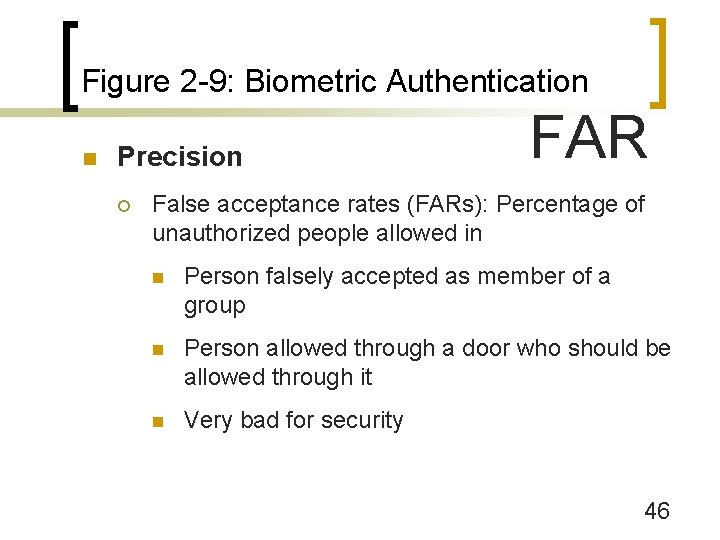
Figure 2 -9: Biometric Authentication n Precision ¡ FAR False acceptance rates (FARs): Percentage of unauthorized people allowed in n Person falsely accepted as member of a group n Person allowed through a door who should be allowed through it n Very bad for security 46

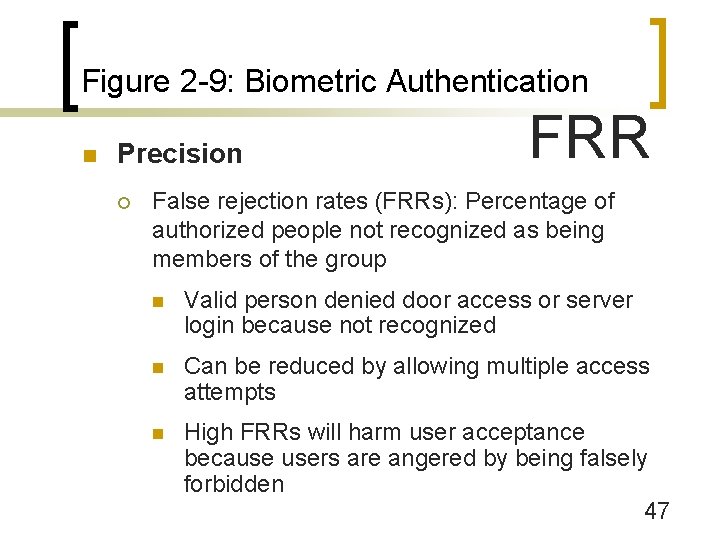
Figure 2 -9: Biometric Authentication n Precision ¡ FRR False rejection rates (FRRs): Percentage of authorized people not recognized as being members of the group n Valid person denied door access or server login because not recognized n Can be reduced by allowing multiple access attempts n High FRRs will harm user acceptance because users are angered by being falsely forbidden 47

Figure 2 -9: Biometric Authentication n Precision ¡ Vendor claims for FARs and FRRs tend to be exaggerated because they often perform tests under ideal circumstances ¡ For instance, having only small numbers of users in the database ¡ For instance, by using perfect lighting, extremely clean readers, and other conditions rarely seen in the real world 48

Figure 2 -9: Biometric Authentication n User Acceptance is Crucial ¡ Strong user resistance can kill a system ¡ Fingerprint recognition may have a criminal connotation ¡ Some methods are difficult to use, such as iris recognition, which requires the eye to be lined up carefully. n These require a disciplined group 49

Figure 2 -9: Biometric Authentication n Biometric Methods ¡ New Fingerprint recognition n Dominates the biometric market today n Based on a finger’s distinctive pattern of whorls, arches, and loops n Simple, inexpensive, well-proven n Weak security: can be defeated fairly easily with copies n Useful in modest-security areas 50

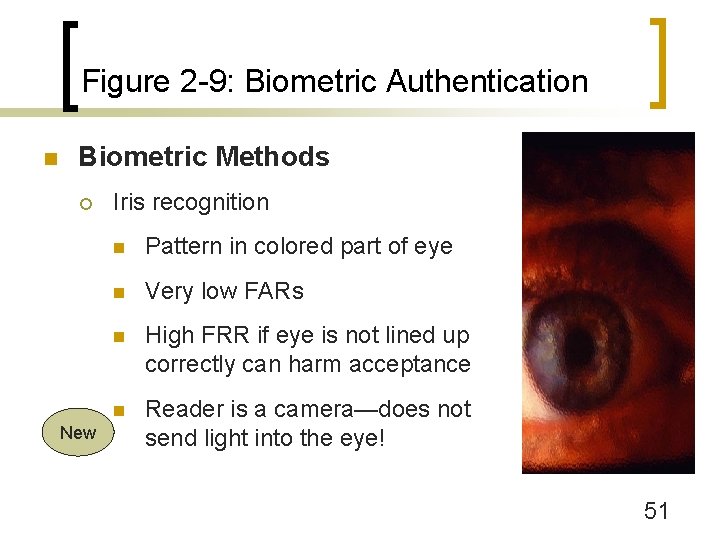
Figure 2 -9: Biometric Authentication n Biometric Methods ¡ New Iris recognition n Pattern in colored part of eye n Very low FARs n High FRR if eye is not lined up correctly can harm acceptance n Reader is a camera—does not send light into the eye! 51

Figure 2 -9: Biometric Authentication n Biometric Methods ¡ Face recognition n Can be put in public places for surreptitious identification (identification without citizen or employee knowledge). More later. ¡ Hand geometry: shape of hand ¡ Voice recognition n High error rates n Easy to fool with recordings 52

Figure 2 -9: Biometric Authentication n Biometric Methods ¡ ¡ Keystroke recognition n Rhythm of typing n Normally restricted to passwords n Ongoing during session could allow continuous authentication Signature recognition n Pattern and writing dynamics 53

Figure 2 -9: Biometric Authentication n Biometric Standards ¡ Almost no standardization ¡ Worst for user data (fingerprint feature databases) ¡ Get locked into single vendors 54

Figure 2 -9: Biometric Authentication n Can Biometrics be Fooled? ¡ Airport face recognition n Identification of people passing in front of a camera n False rejection rate: rate of not identifying person as being in the database n Fail to recognize a criminal, terrorist, etc. n FRRs are bad 55

Figure 2 -9: Biometric Authentication n Can Biometrics be Fooled? ¡ Airport face recognition n 4 -week trial of face recognition at Palm Beach International Airport n Only 250 volunteers in the user database (unrealistically small) n Volunteers were scanned 958 times during the trial n Only recognized 455 times! (47%) n 53% FRR 56

Figure 2 -9: Biometric Authentication n Can Biometrics be Fooled? ¡ Airport face recognition n Recognition rate fell if wore glasses (especially tinted), looked away n Would be worse with larger database n Would be worse if photographs were not good 57

Figure 2 -9: Biometric Authentication n Can Biometrics be Fooled? ¡ DOD Tests indicate poor acceptance rates when subjects were not attempting to evade n 270 -person test n Face recognition recognized person only 51 percent of time n Even iris recognition only recognized the person 94 percent of the time! 58

Figure 2 -9: Biometrics Authentication n Can Biometrics be Fooled? ¡ Other research has shown that evasion is often successful for some methods n German c’t magazine fooled most face and fingerprint recognition systems n Prof. Matsumoto fooled fingerprint scanners 80 percent of the time with a gelatin finger created from a latent (invisible to the naked eye) print on a drinking glass 59

802. 11 Wireless LAN Security

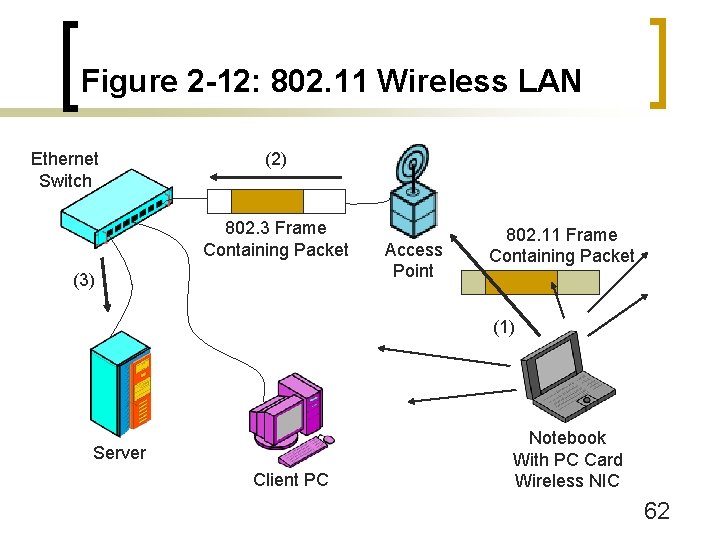
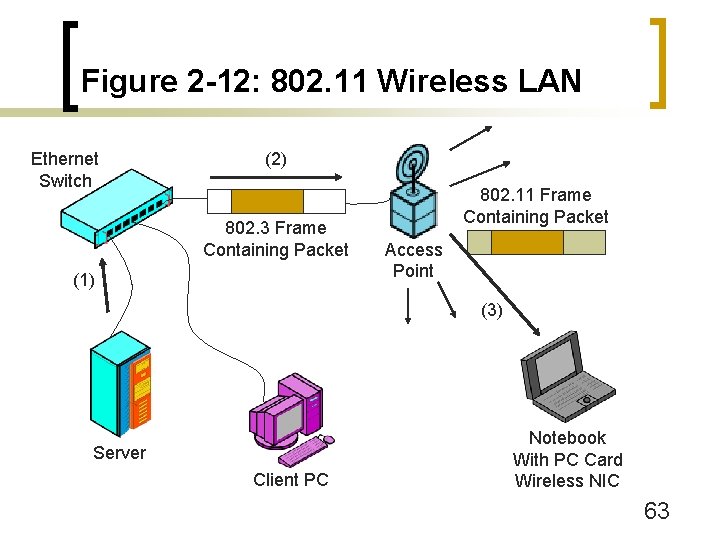
Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n 802. 11 Wireless LAN Family of Standards n Basic Operation (Figure 2 -12 on next slide) ¡ Main wired network for servers (usually 802. 3 Ethernet) ¡ Wireless stations with wireless NICs ¡ Access points are bridges that link 802. 11 LANs to 802. 3 Ethernet LANs 61

Figure 2 -12: 802. 11 Wireless LAN Ethernet Switch (2) 802. 3 Frame Containing Packet (3) Access Point 802. 11 Frame Containing Packet (1) Server Client PC Notebook With PC Card Wireless NIC 62

Figure 2 -12: 802. 11 Wireless LAN Ethernet Switch (2) 802. 3 Frame Containing Packet (1) 802. 11 Frame Containing Packet Access Point (3) Server Client PC Notebook With PC Card Wireless NIC 63

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n Basic Operation ¡ Propagation distance: farther for attackers than users n Attackers can have powerful antennas and amplifiers n Attackers can benefit even if they can only read some messages n Don’t be lulled into complacency by internal experiences with useable distances 64

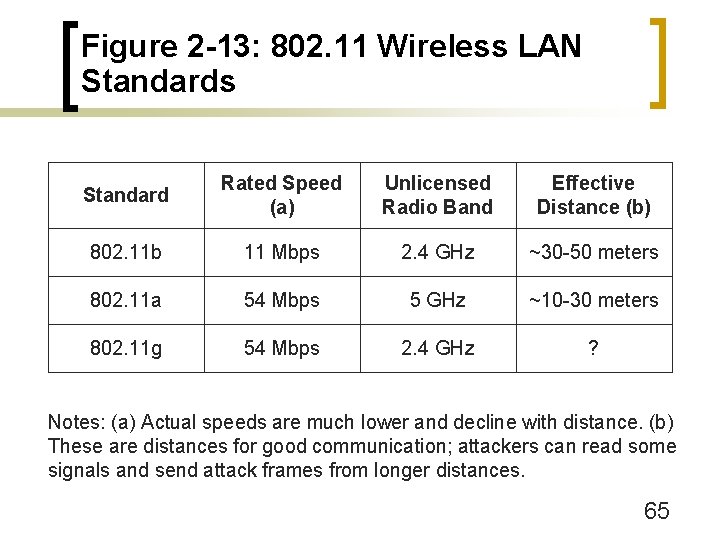
Figure 2 -13: 802. 11 Wireless LAN Standards Standard Rated Speed (a) Unlicensed Radio Band Effective Distance (b) 802. 11 b 11 Mbps 2. 4 GHz ~30 -50 meters 802. 11 a 54 Mbps 5 GHz ~10 -30 meters 802. 11 g 54 Mbps 2. 4 GHz ? Notes: (a) Actual speeds are much lower and decline with distance. (b) These are distances for good communication; attackers can read some signals and send attack frames from longer distances. 65

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n Apparent 802. 11 Security ¡ Spread spectrum transmission does not provide security n Signal is spread over a broad range of frequencies n Methods used by military are hard to detect n 802. 11 spread spectrum methods are easy to detect so devices can find each other n Used in 802. 11 to prevent frequency-dependent propagation problems rather than for security 66

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n Apparent 802. 11 Security ¡ SSIDs n Mobile devices must know the access point’s service set identifier (SSID) to talk to the access point n Usually broadcast frequently by the access point for ease of discovery, so offers no security. n Sent in the clear in messages sent between stations and access points 67

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n Wired Equivalent Privacy (WEP) ¡ Biggest security problem: Not enabled by default ¡ 40 -bit encryption keys are too small n Nonstandard 128 -bit (really 104 -bit) keys are reasonable interoperable 68

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n Wired Equivalent Privacy (WEP) ¡ ¡ Shared passwords n Access points and all stations use the same password n Difficult to change, so rarely changed n People tend to shared passwords too widely Flawed security algorithms n Algorithms were selected by cryptographic amateurs 69

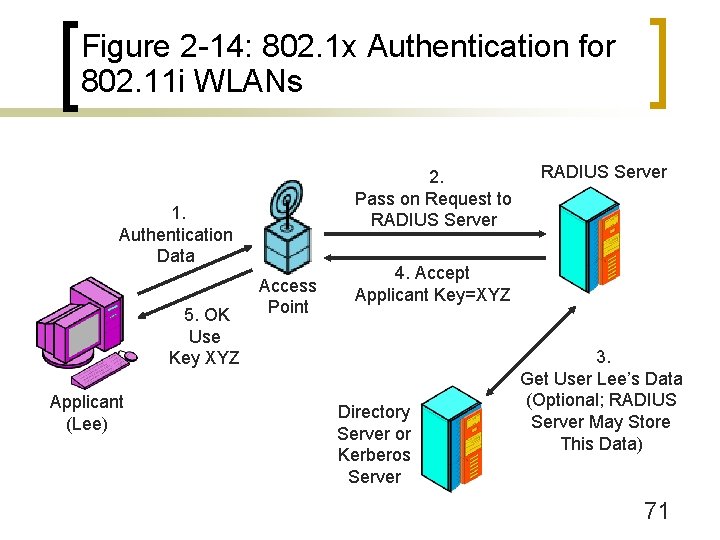
Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n 802. 1 x and 802. 11 i (Figure 2 -14) ¡ Authentication server ¡ User data server ¡ Individual keys give out at access point 70

Figure 2 -14: 802. 1 x Authentication for 802. 11 i WLANs 2. Pass on Request to RADIUS Server 1. Authentication Data 5. OK Use Key XYZ Applicant (Lee) Access Point RADIUS Server 4. Accept Applicant Key=XYZ Directory Server or Kerberos Server 3. Get User Lee’s Data (Optional; RADIUS Server May Store This Data) 71

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security New Presentation n 802. 1 x and 802. 11 ¡ ¡ Control access when the user connects to the network n At a wired RJ-45 jack n At a wireless access point 802. 1 x is a general approach to port authentication n 802. 11 i is the implementation of 802. 1 x on 802. 11 wireless LANs 72

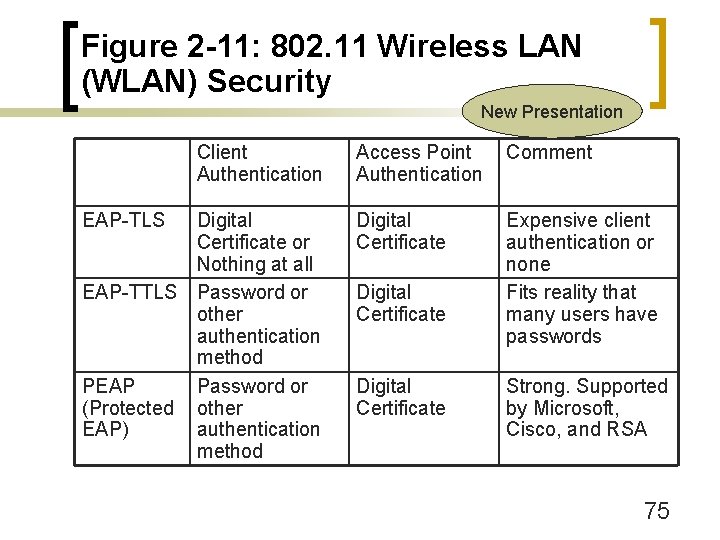
Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security New Presentation n 802. 1 x and 802. 11 ¡ Extensible Authentication Protocol (EAP) n Supports multiple forms of authentication ¡ EAP-TLS ¡ EAP-TTLS ¡ PEAP 73

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security New Presentation n 802. 1 x and 802. 11 ¡ Extensible Authentication Protocol (EAP) n Authentication mechanisms ¡ Passwords n Simple and inexpensive to implement n Low security ¡ Digital Certificate n Complex and expensive to install digital certificates on many devices n Very strong authentication 74

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security New Presentation Client Authentication EAP-TLS Digital Certificate or Nothing at all EAP-TTLS Password or other authentication method PEAP Password or (Protected other EAP) authentication method Access Point Authentication Comment Digital Certificate Expensive client authentication or none Fits reality that many users have passwords Digital Certificate Strong. Supported by Microsoft, Cisco, and RSA 75

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security New Presentation n TLS ¡ n The default for 802. 11 i security but choice of either digital certificates for clients or no client authentication is undesirable PEAP and TTLS ¡ Very similar in terms of the authentication methods they support ¡ PEAP is supported by Microsoft, Cisco, and RSA ¡ TTLS is supported by a consortium of other vendors 76

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security New Presentation n 802. 1 x and 802. 11 i (Figure 2 -14) ¡ After authentication, the client must be given a key for confidentiality ¡ Temporal Key Integrity Protocol (TKIP) is used in 802. 11 i and 802. 1 x n ¡ Key changed every 10, 000 frames to foil data collection for key guessing This is an Advanced Encryption Standard (AES) key 77

Wi-Fi and WPA n New: Not in Book Wi-Fi Alliance ¡ Industry group that certifies 802. 11 systems ¡ Created the Wi-Fi Protected Access (WPA) system in 2002 ¡ WPA is basically 802. 11 i n But does not use AES keys n Many installed wireless products can be upgraded to WPA n Stop-gap measure before 802. 11 i 78

802. 11 i Today n 802. 11 i standard was released in July 2004 ¡ n New: Not in Book But products started appearing in 2003 What must firms do? ¡ Throw out WEP-only products n ¡ In security, legacy technologies are not acceptable Decide if it can have WPA and 802. 11 i products co-exist 79

Figure 2 -11: 802. 11 Wireless LAN (WLAN) Security n Virtual Private Networks (VPNs) ¡ Add security on top of network technology to compensate for WLAN weaknesses ¡ Discussed in Chapter 8 WLAN, etc. VPN 80

The Situation Today in Wireless Security n Wireless security is poor in most installations today n The situation is improving, and technology will soon be good n But old installations are likely to remain weak links in corporate security 81

Topics Covered n Policy-Driven Access Control ¡ Identify resources ¡ Create an access policy for each ¡ Let the policy drive implementation and testing 82

Topics Covered n Password-Based Access Control ¡ Reusable passwords are inexpensive because built into servers ¡ Usually weak because people often pick cracked passwords ¡ Hacking root is a key goal ¡ Password resets are necessary but dangerous 83

Topics Covered n Building Security ¡ Single point of (normal) entry to building ¡ Fire doors, etc. : use CCTV and alarms ¡ Security centers ¡ Interior doors locked (but piggybacking) ¡ Dumpster diving control ¡ Securing building wiring, including telecommunications closets 84

Topics Covered n Access Cards and Tokens ¡ Magnetic strip cards ¡ Smart cards with CPU and Memory ¡ Tokens n Tokens with constantly-changing passwords n Tokens that plug into USB ports ¡ Proximity cards with radio communication ¡ Pins can be short because of manual entry 85

Topics Covered n Biometric Authentication ¡ Can replace reusable passwords ¡ Fingerprint scanning dominates biometrics n Inexpensive, somewhat secure ¡ Iris recognition is more precise ¡ Face recognition can be done surreptitiously ¡ Identification vs verification vs watch list ¡ FARs and FRRs ¡ Often easily deceived by attackers 86

Topics Covered n 802. 11 Wireless LAN Security ¡ Signals travel outside building, allowing drive-by hacking ¡ Initial security was WEP ¡ n Often not even turned on n Very easily cracked because uses shared static key for both confidentiality and authentication Some firms added passwords and/or VPNs to allow secure communication anyway 87

Topics Covered n 802. 11 Wireless LAN Security ¡ Now, 802. 11 i security n Based on 802. 1 x security for wired LANs n Sophisticated authentication n ¡ EAP supports multiple methods ¡ Not a single standard, so problems with equipment interoperability Strong AES confidentiality 88

Topics Covered n 802. 11 Wireless LAN Security ¡ ¡ Now, 802. 11 i security n Requires an infrastructure ¡ Central authentication server n Adequate for corporate needs Today n Buy only 802. 11 i equipment n See if can keep WPA (post-WEP/pre-802. 11 i) products n Discard WEP products 89