Security 9 1 Introduction to Security Security policy





























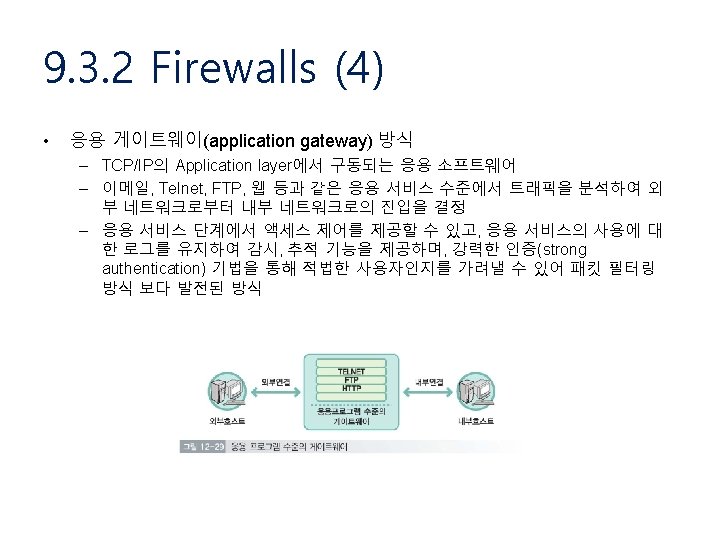















- Slides: 141

Security

9. 1 Introduction to Security • Security policy • Security mechanism


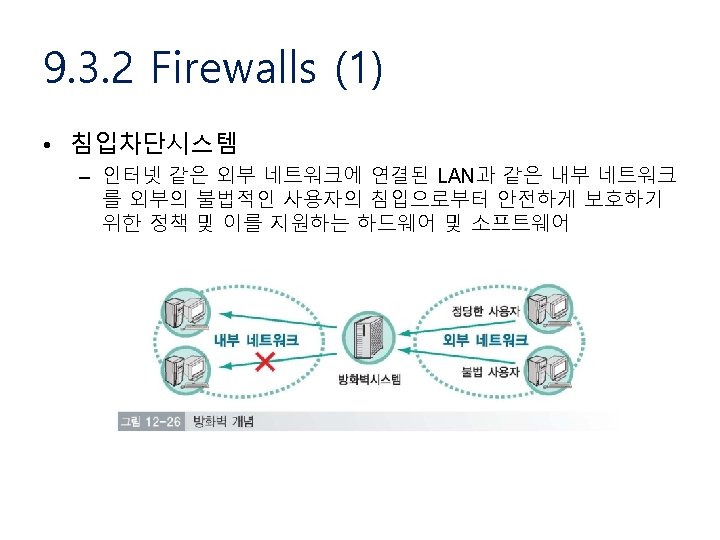
9. 1. 1 Security Threats, Policies, and Mechanisms(2) • The Players – Subject • Entity capable of issuing a request for a service as provided by objects – Channel • The carrier of requests and replies for services offered to subjects – Object • Entity providing services to subjects • 보안 위협 (security threat)의 유형 – – 가로채기 (Interception) 끼어들기 (Interruption) 변경 (Modification) 위조 (Fabrication)

9. 1. 1 Security Threats, Policies, and Mechanisms(3) • The threats Threat Channel Object Interruption Preventing message transfer Denial of Service Inspection Reading the content of Reading the data contained transferred message in an object Modification Changing message content Changing an object’s encapsulated data Fabrication Inserting message Spoofing an object Spoof: 도용

9. 1. 1 Security Threats, Policies, and Mechanisms(4) • Security Policy – System내에서 entity에 사용되거나 금지되는 행위에 대한 정확한 기술 – 정책에 따라서 보안 방법 (security mechanism)을 적용


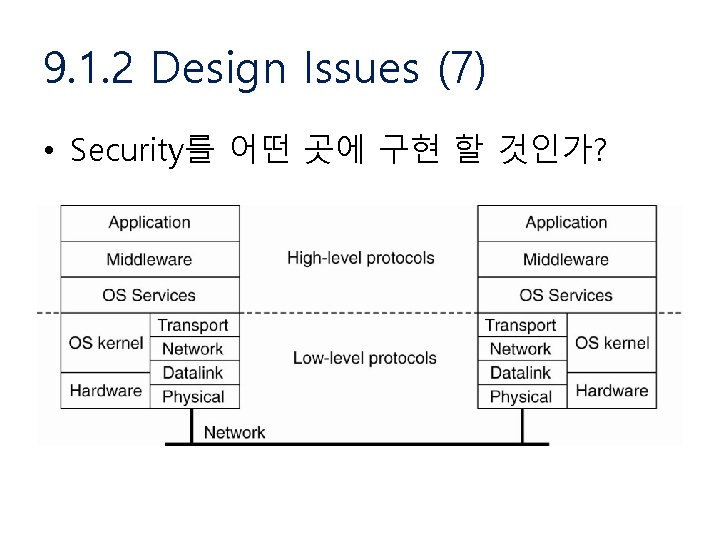
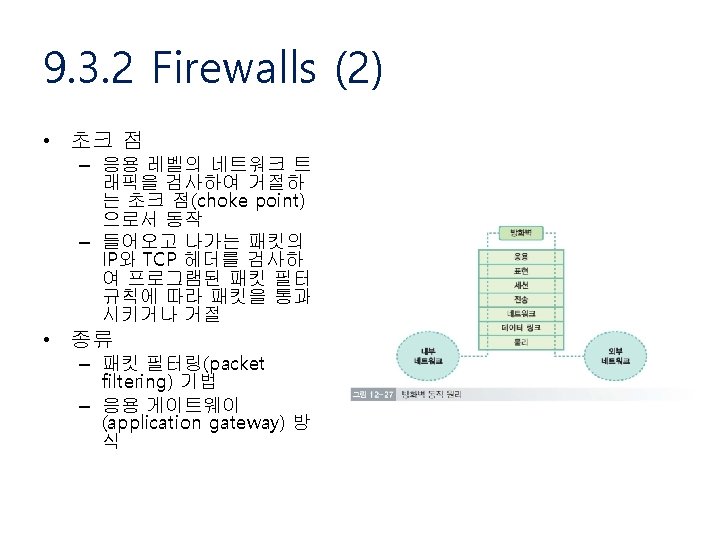
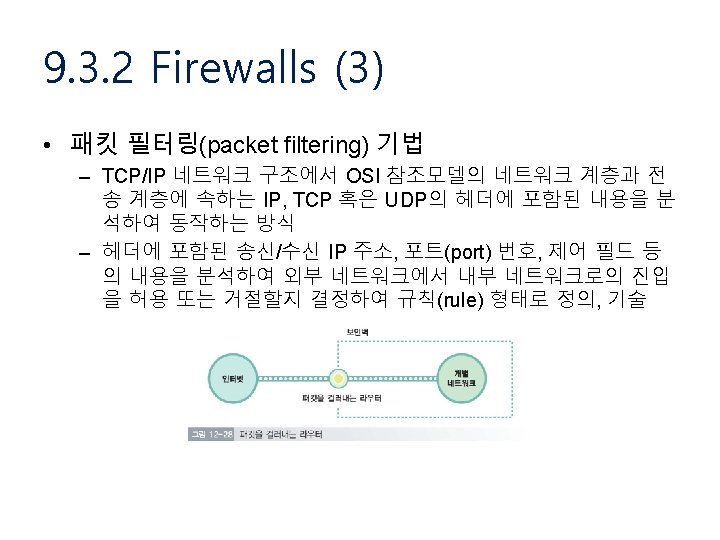
9. 1. 2 Design Issues (1) • Focus of control • Layering of security mechanisms • Simplicity

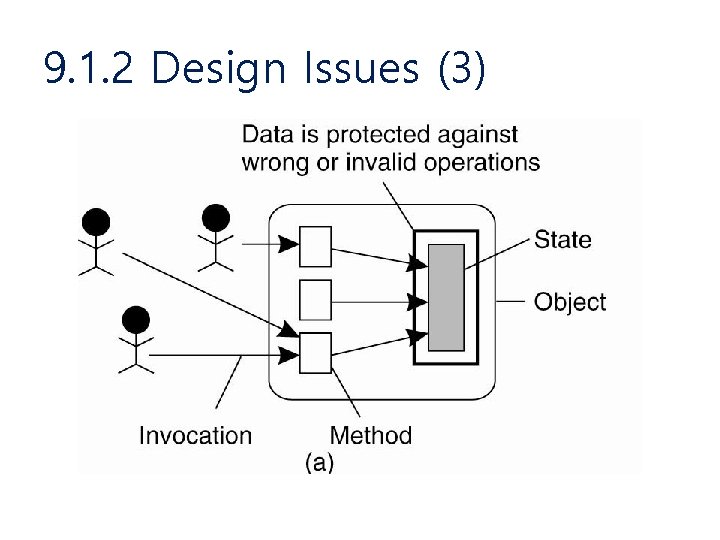
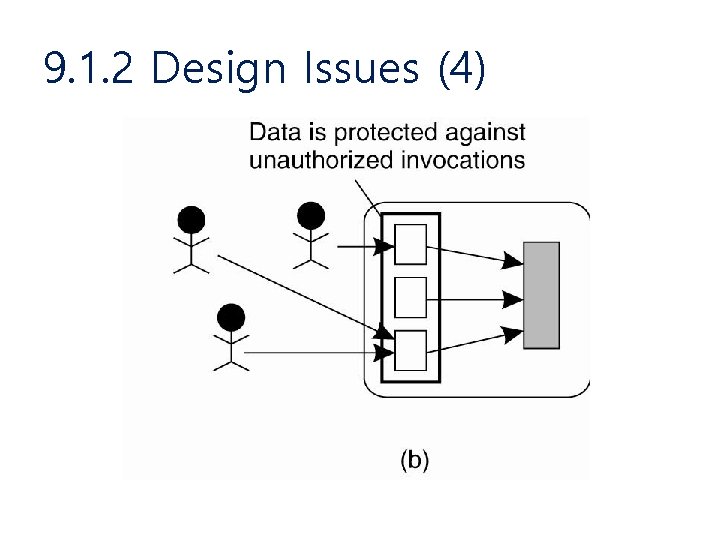
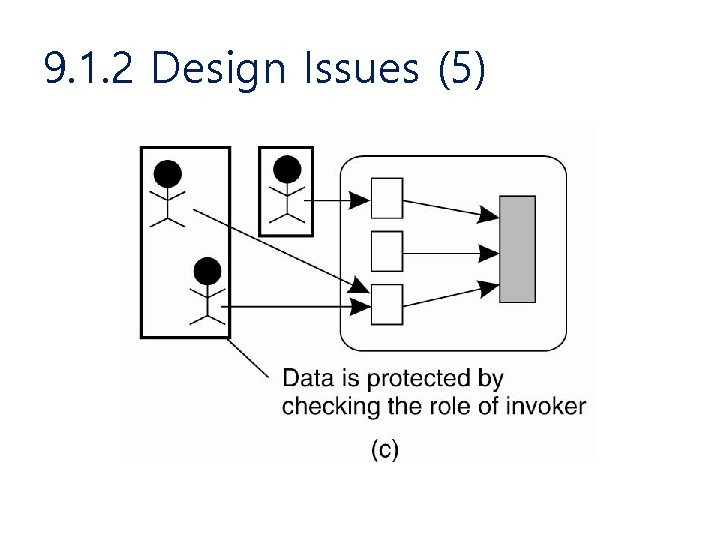
9. 1. 2 Design Issues (2) • Focus of Control – Data is protected against wrong or invalid operations – Data is protected against unauthorized invocations – Data is protected by checking the role of invoker

9. 1. 2 Design Issues (3)

9. 1. 2 Design Issues (4)

9. 1. 2 Design Issues (5)

9. 1. 2 Design Issues (6) • Layering of Security Mechanisms – Trust and security • Security – Technical • Trust – Emotional


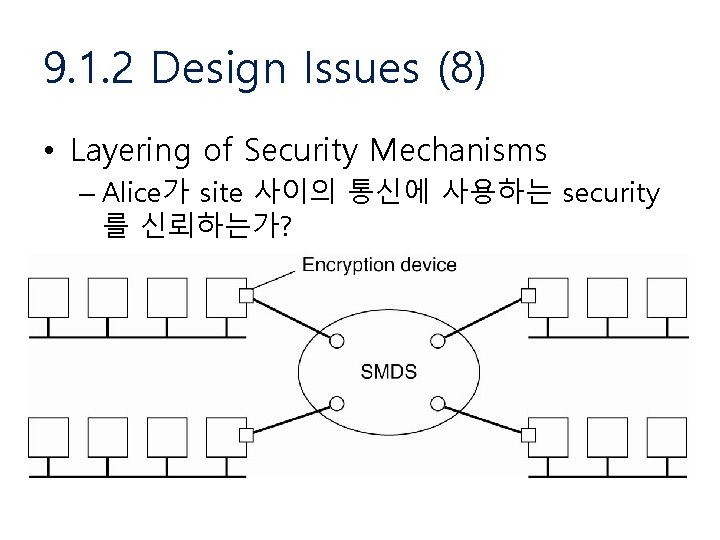
9. 1. 2 Design Issues (8) • Layering of Security Mechanisms – Alice가 site 사이의 통신에 사용하는 security 를 신뢰하는가?


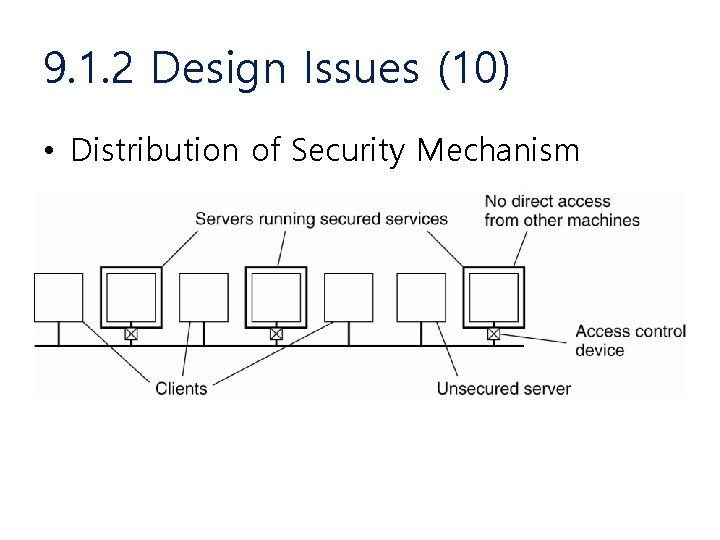
9. 1. 2 Design Issues (10) • Distribution of Security Mechanism




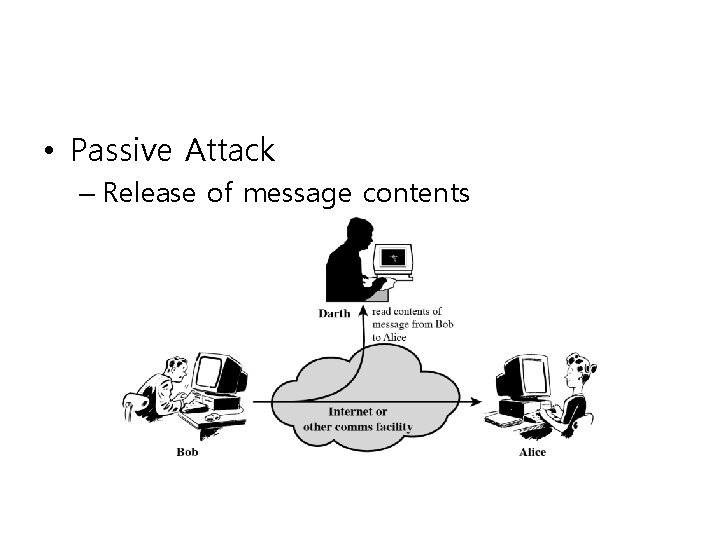
• Passive Attack – Release of message contents

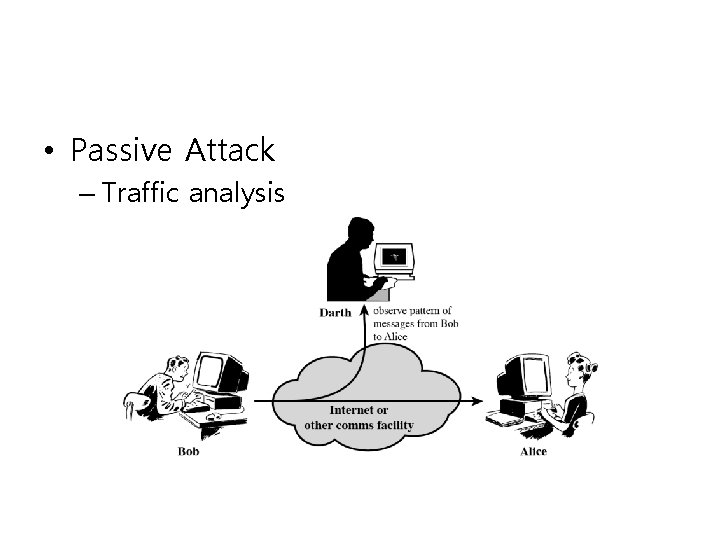
• Passive Attack – Traffic analysis


• Active Attack – 비합법적 메시지 생성 • • Creating illegitimate message 가장 - Masquerade (who) 재현 - Replay (when) 변경 - Modification of message (what) – 합법적 메시지를 거부 • Denying legitimate message • 거절 - Repudiation – 시스템 자원을 이용하지 못하도록 함 • Making system facilities unavailable

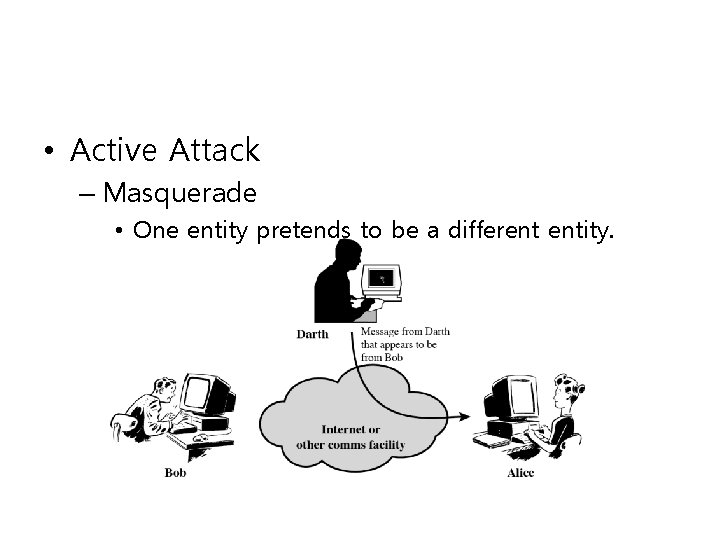
• Active Attack – Masquerade • One entity pretends to be a different entity.

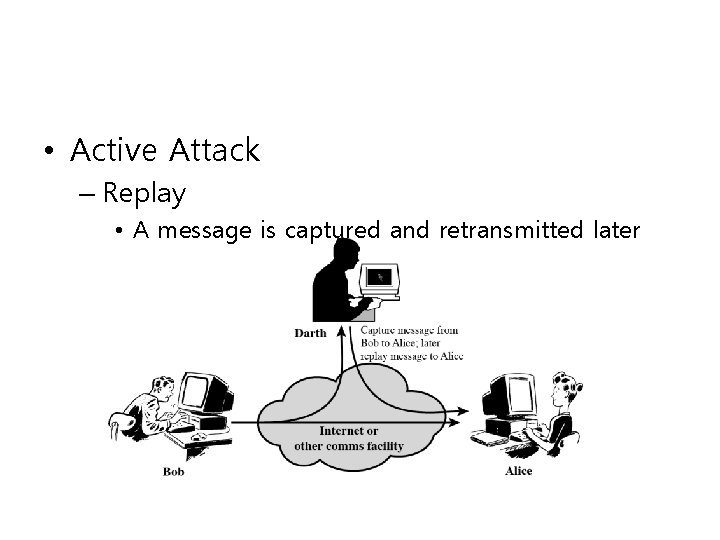
• Active Attack – Replay • A message is captured and retransmitted later

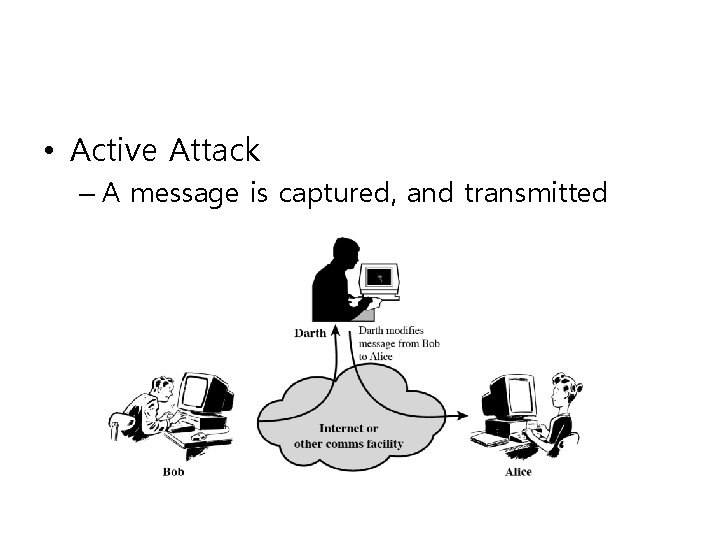
• Active Attack – A message is captured, and transmitted

• Active Attack – Repudiation • Denial of sending or receiving legitimate message

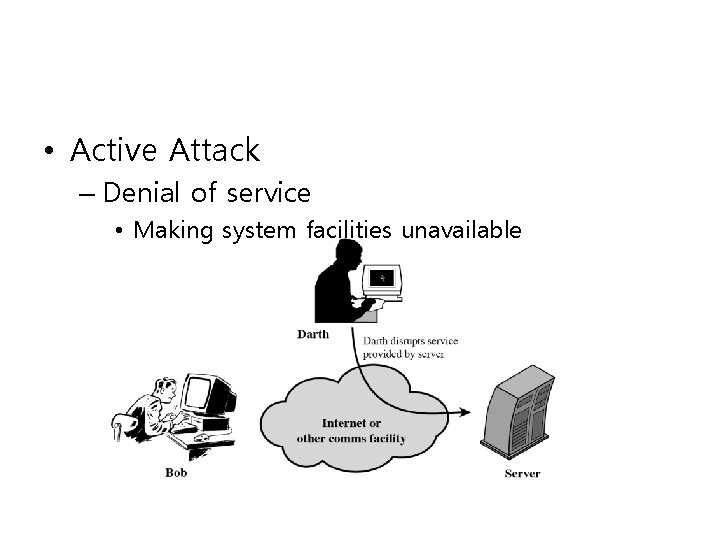
• Active Attack – Denial of service • Making system facilities unavailable

• Active Attack – 예방하기 어려움 • Because of new vulnerabilities – So, the goal is to detect active attacks and to recover as soon as possible. Vulnerability: 취약성


• DES • RSA • MD 5



9. 2 Security Channel (2) Both parties know who is on the other side (authenticated) Both parties know that messages cannot be tampered with (integrity) Both parties know messages cannot leak away (confidentiality)


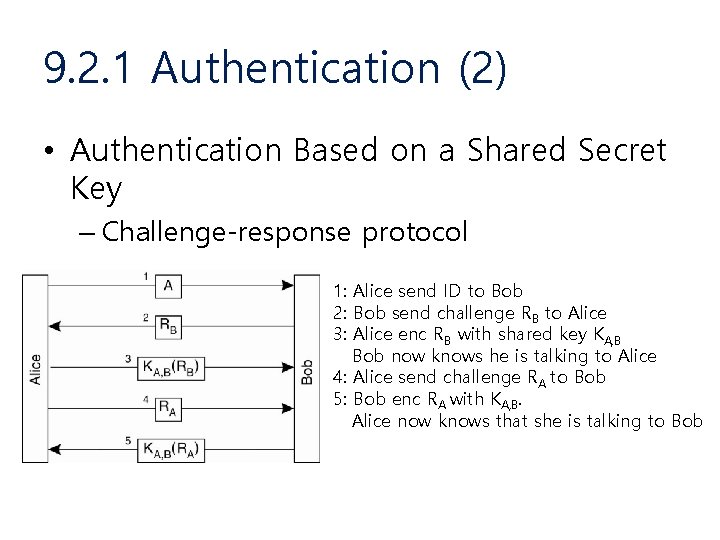
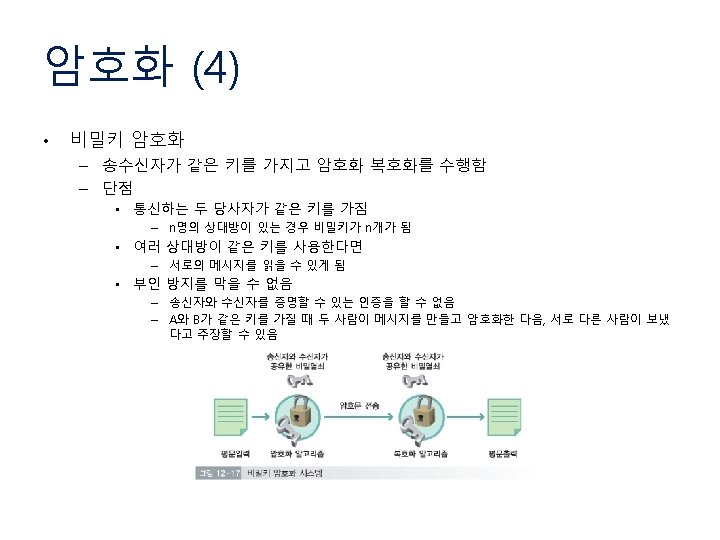
9. 2. 1 Authentication (2) • Authentication Based on a Shared Secret Key – Challenge-response protocol 1: Alice send ID to Bob 2: Bob send challenge RB to Alice 3: Alice enc RB with shared key KA, B Bob now knows he is talking to Alice 4: Alice send challenge RA to Bob 5: Bob enc RA with KA, B. Alice now knows that she is talking to Bob

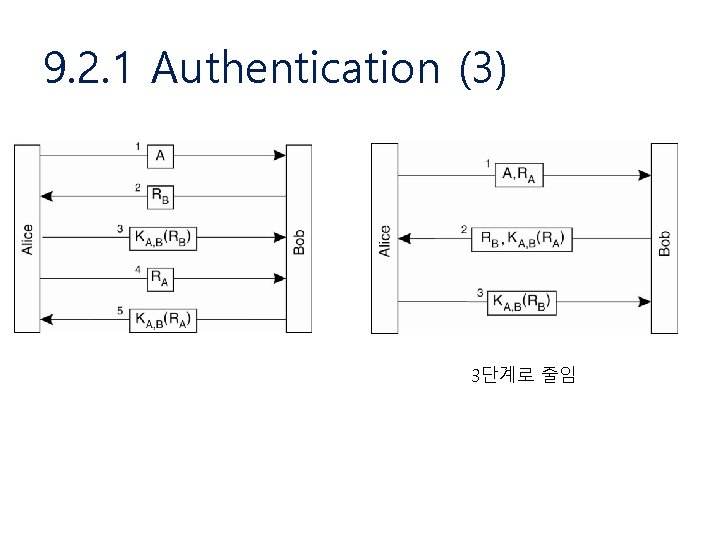
9. 2. 1 Authentication (3) 3단계로 줄임


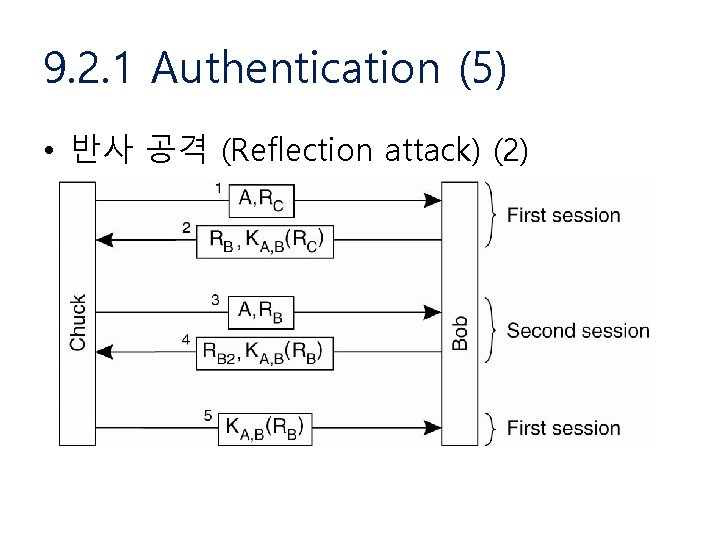
9. 2. 1 Authentication (5) • 반사 공격 (Reflection attack) (2)

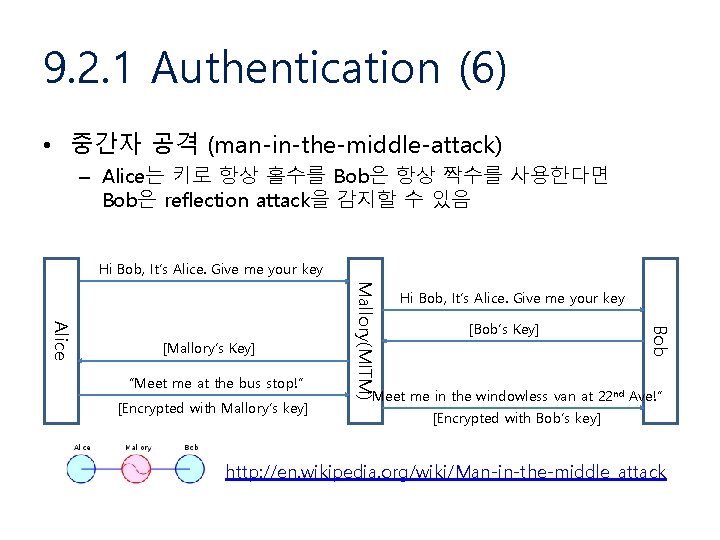
9. 2. 1 Authentication (6) • 중간자 공격 (man-in-the-middle-attack) – Alice는 키로 항상 홀수를 Bob은 항상 짝수를 사용한다면 Bob은 reflection attack을 감지할 수 있음 Hi Bob, It’s Alice. Give me your key [Encrypted with Mallory’s key] [Bob’s Key] Bob “Meet me at the bus stop!” Mallory(MITM) Alice [Mallory’s Key] Hi Bob, It’s Alice. Give me your key “Meet me in the windowless van at 22 nd Ave!” [Encrypted with Bob’s key] http: //en. wikipedia. org/wiki/Man-in-the-middle_attack

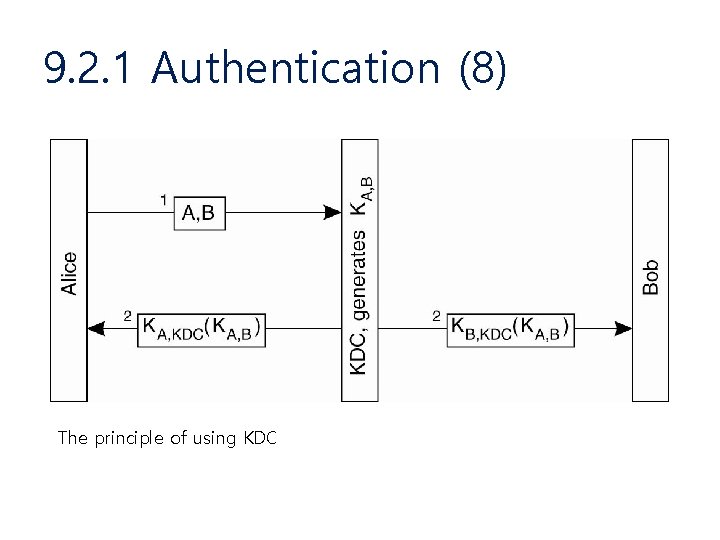
9. 2. 1 Authentication (7) • Authentication Using a Key Distributor Center (KDC) – One of problem with using Shared secret key for authentication is scalability • N host – – N-1 host와 키를 공유 각 host는 N-1개의 key를 관리 전체 시스템은 N(N-1)/2의 key를 관리 N이 매우 크다면? • KDC – Host의 키를 관리

9. 2. 1 Authentication (8) The principle of using KDC

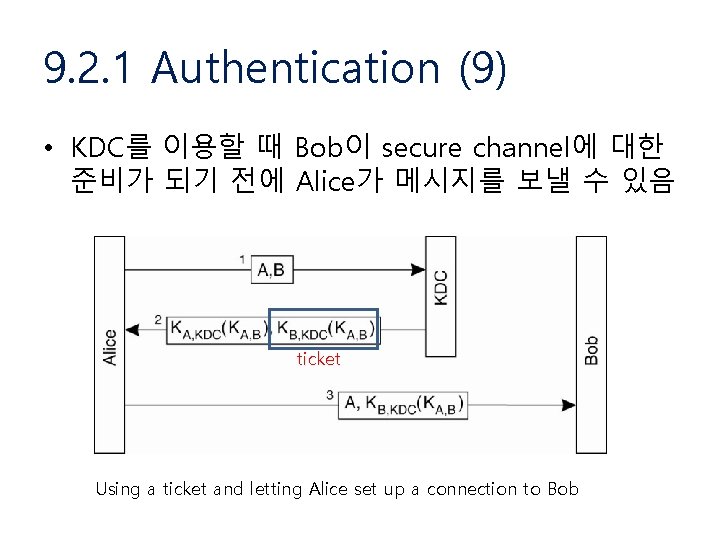
9. 2. 1 Authentication (9) • KDC를 이용할 때 Bob이 secure channel에 대한 준비가 되기 전에 Alice가 메시지를 보낼 수 있음 ticket Using a ticket and letting Alice set up a connection to Bob

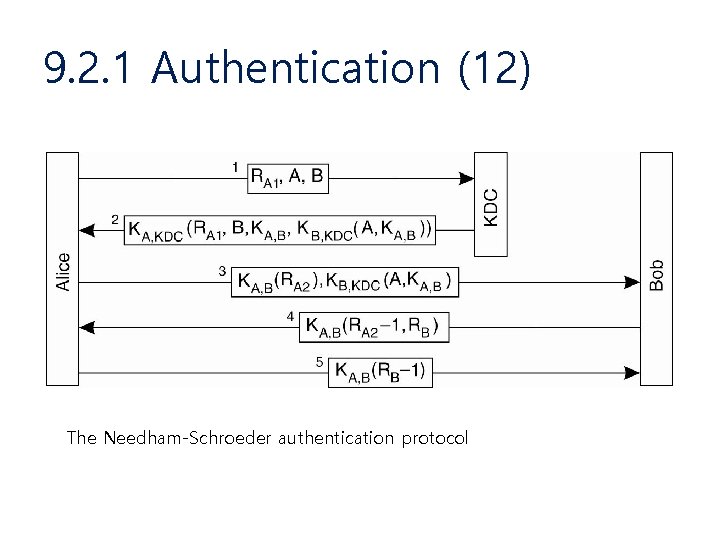
9. 2. 1 Authentication (10) • Needham-schroeder authentication protocol – 1978년 대칭키와 trent 개념을 사용하여 제안 • Define – Trent (KDC), Cathy : 인증서버 – Alice (A), Bob (B) – KA: Alice의 비밀 키 – KB: Bot의 비밀 키 – KS: 세션 키 – RARB: 무작위수(nonce)


9. 2. 1 Authentication (12) The Needham-Schroeder authentication protocol

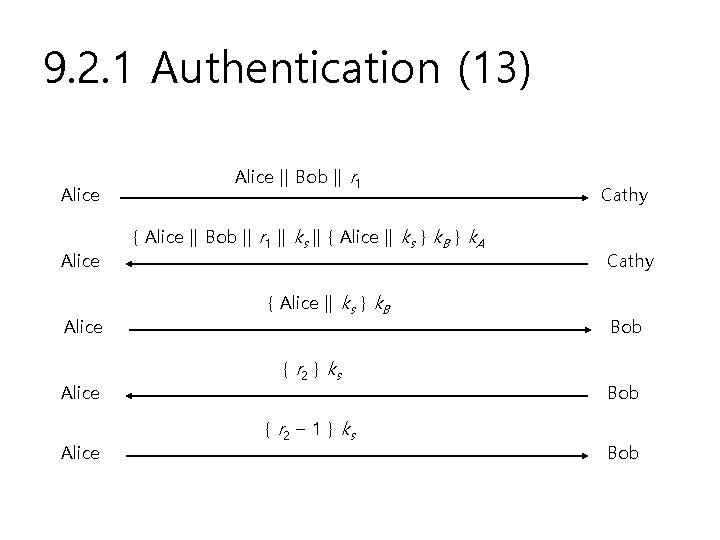
9. 2. 1 Authentication (13) Alice Alice || Bob || r 1 { Alice || Bob || r 1 || ks || { Alice || ks } k. B } k. A { Alice || ks } k. B { r 2 } k s { r 2 – 1 } k s Cathy Bob Bob


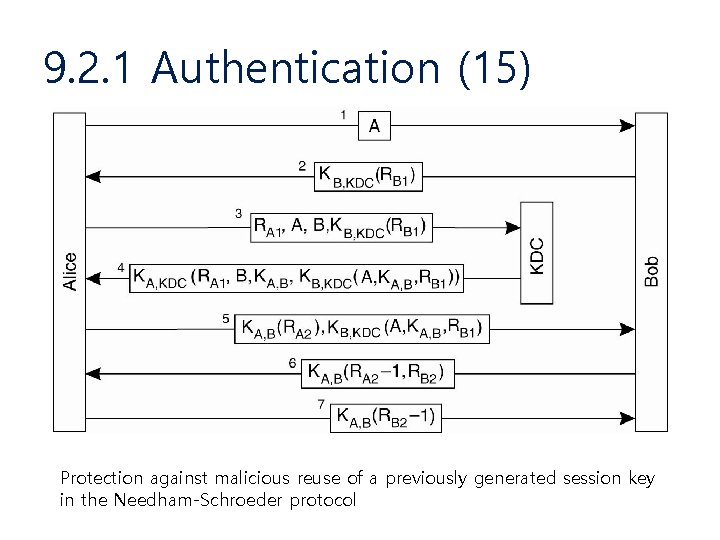
9. 2. 1 Authentication (15) Protection against malicious reuse of a previously generated session key in the Needham-Schroeder protocol

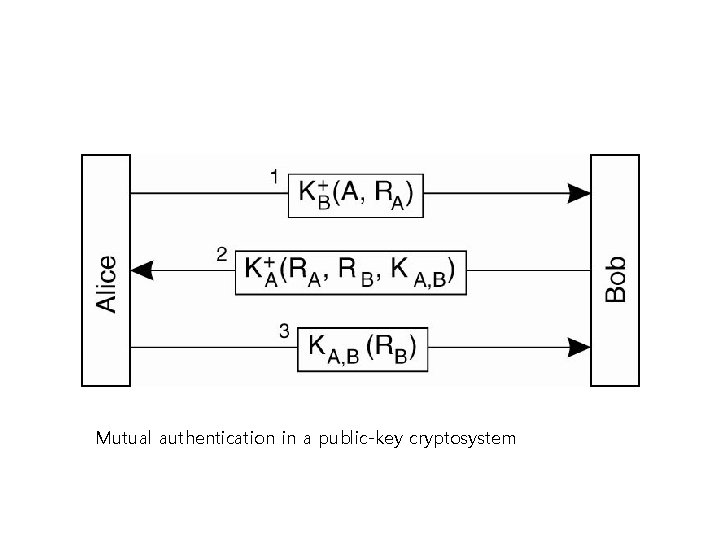
Mutual authentication in a public-key cryptosystem


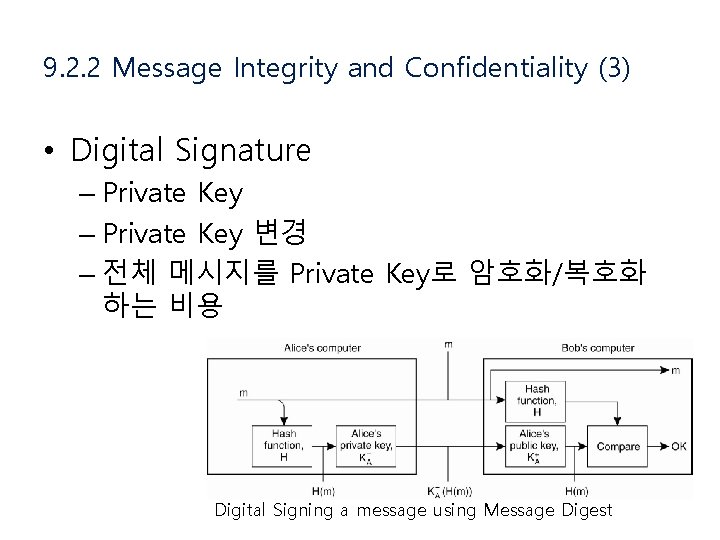
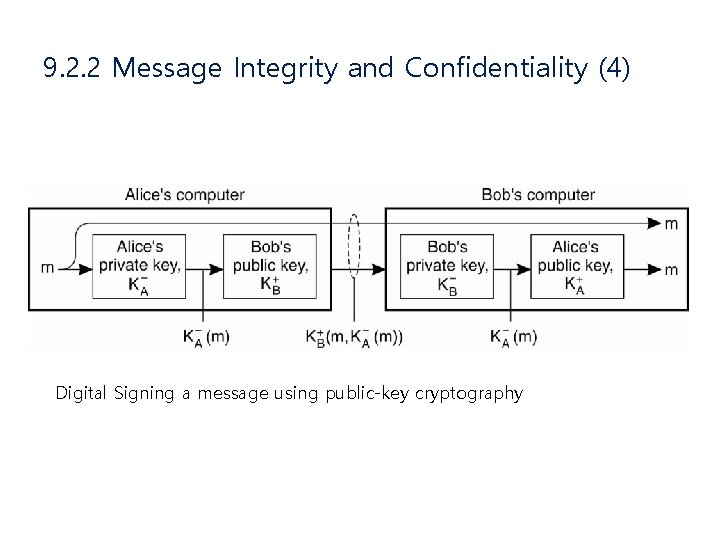
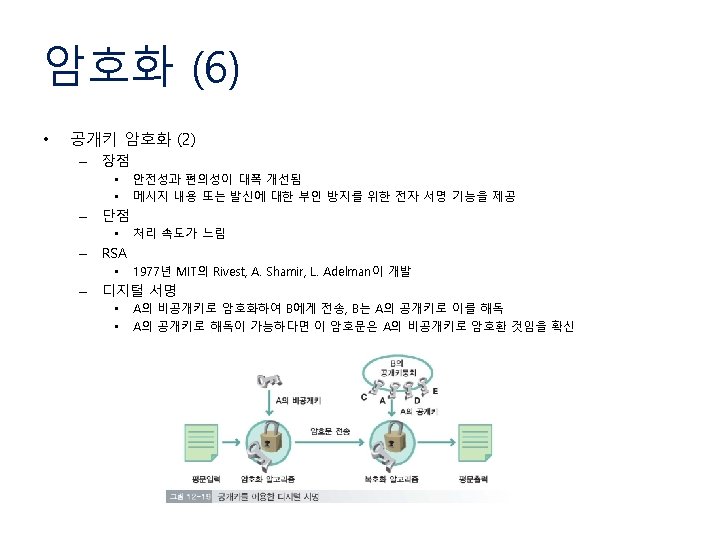
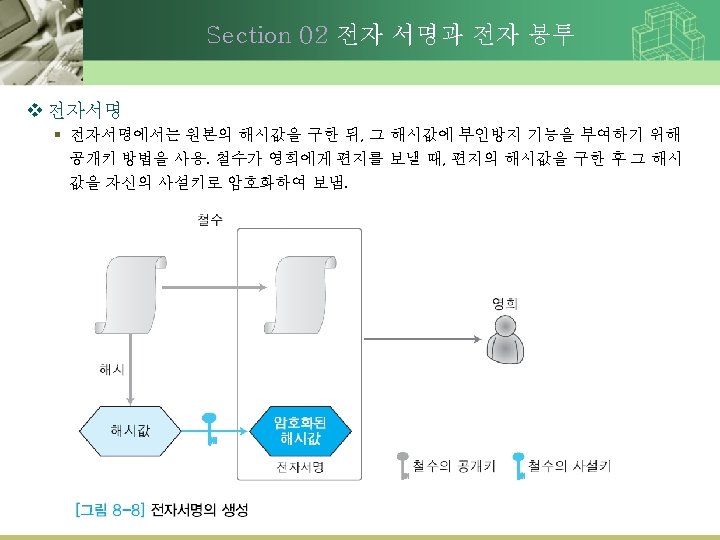
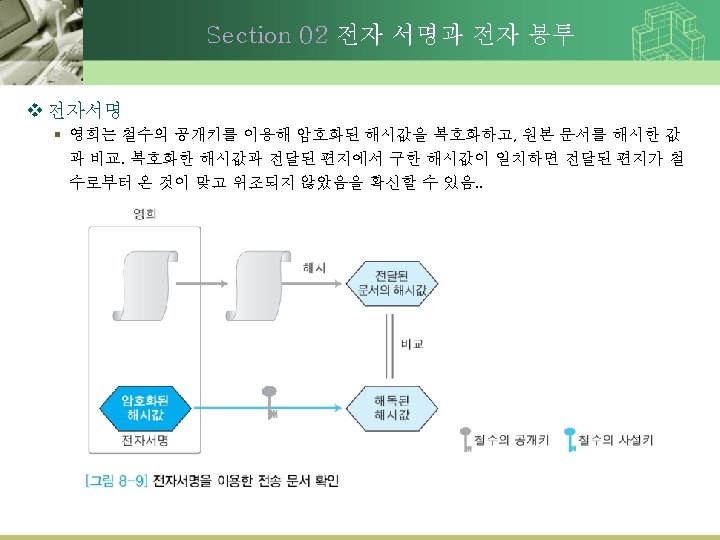
9. 2. 2 Message Integrity and Confidentiality (2) • Digital Signature – E-mail을 통한 거래에 서로 신뢰할 수 있는가? • 서명을 통하여 메시지가 변조되지 않았음을 증명 하도록 함 Digital Signing a message using public-key cryptography

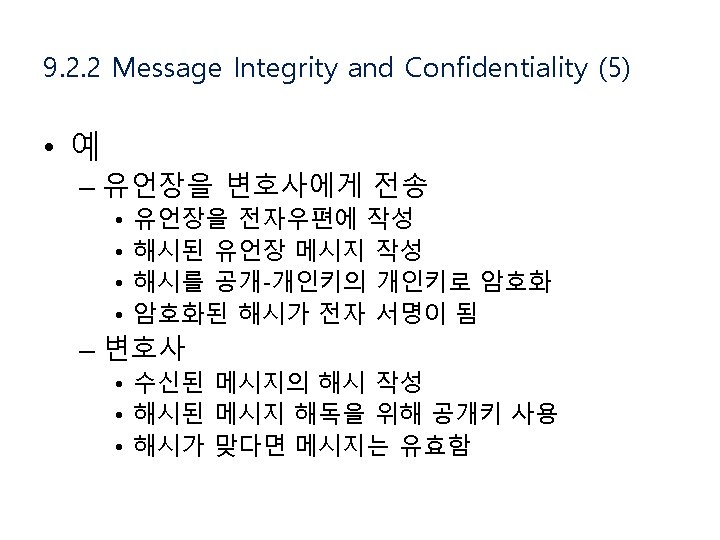
9. 2. 2 Message Integrity and Confidentiality (3) • Digital Signature – Private Key 변경 – 전체 메시지를 Private Key로 암호화/복호화 하는 비용 Digital Signing a message using Message Digest



9. 2. 2 Message Integrity and Confidentiality (6) • Session Keys

9. 2. 2 Message Integrity and Confidentiality (4) Digital Signing a message using public-key cryptography

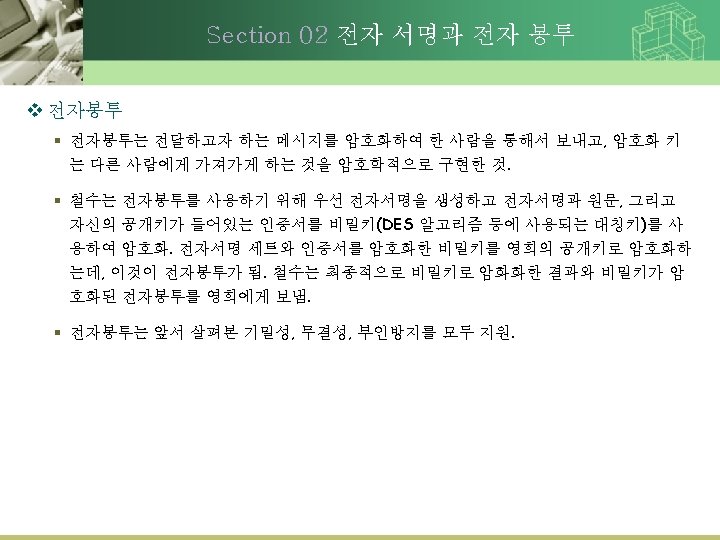
9. 2. 3 Secure Group Communication • 통신 Group 사이의 보안 – Confidential Group Communication • Secrete Key Share • Separate Share Key • Public-key cryptosystem – Secure Replicated Servers • Byzantine Failure • 모든 서버의 응답 확인 – Replication Transparency 위배 • Secrete Sharing – 각각의 key를 공유하지만 전체가 key를 알지 못하도록 함 – 모두 참여할 때만 key를 드러내도록 함



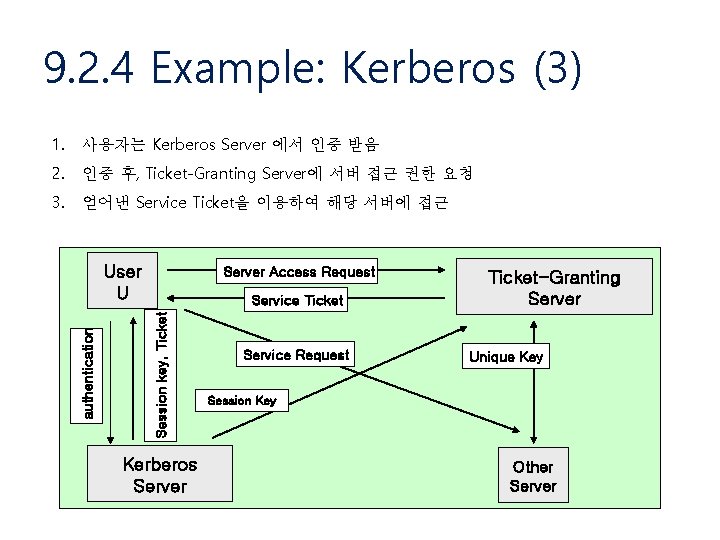
9. 2. 4 Example: Kerberos (3) 1. 사용자는 Kerberos Server 에서 인증 받음 2. 인증 후, Ticket-Granting Server에 서버 접근 권한 요청 3. 얻어낸 Service Ticket을 이용하여 해당 서버에 접근 Server Access Request Service Ticket Session key, Ticket authentication User U Kerberos Server Service Request Ticket-Granting Server Unique Key Session Key Other Server

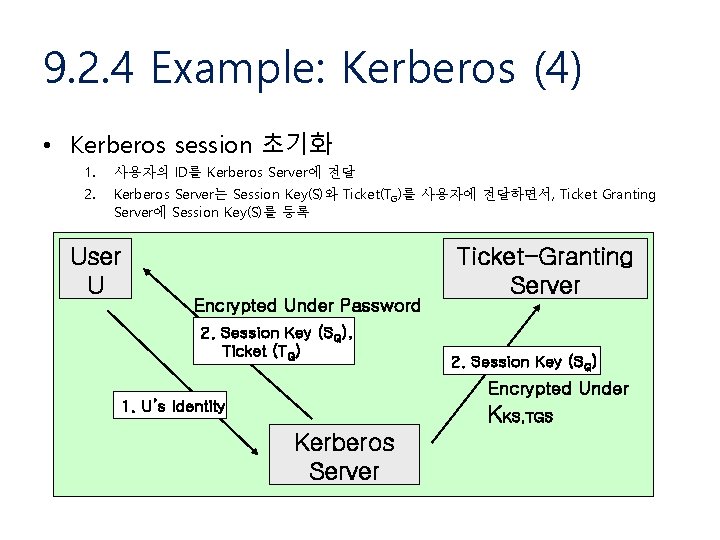
9. 2. 4 Example: Kerberos (4) • Kerberos session 초기화 1. 사용자의 ID를 Kerberos Server에 전달 2. Kerberos Server는 Session Key(S)와 Ticket(TG)를 사용자에 전달하면서, Ticket Granting Server에 Session Key(S)를 등록 User U Encrypted Under Password 2. Session Key (SG), Ticket (TG) Ticket-Granting Server 2. Session Key (SG) Encrypted Under 1. U’s Identity KKS, TGS Kerberos Server

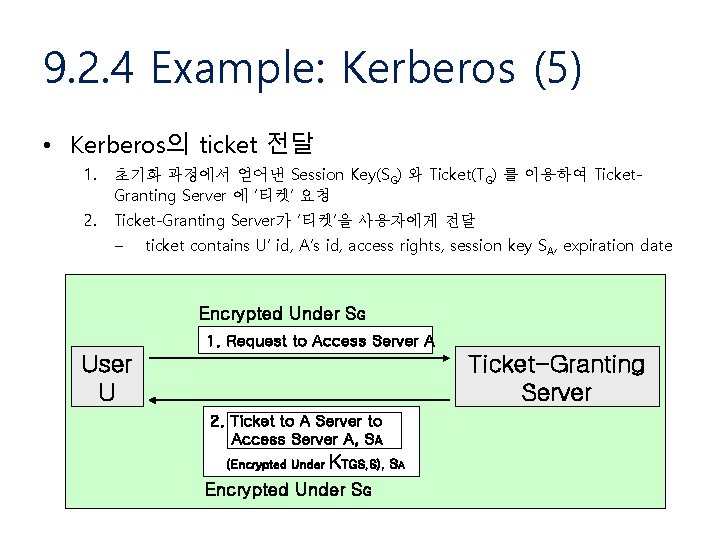
9. 2. 4 Example: Kerberos (5) • Kerberos의 ticket 전달 1. 초기화 과정에서 얻어낸 Session Key(SG) 와 Ticket(TG) 를 이용하여 Ticket. Granting Server 에 ‘티켓’ 요청 2. Ticket-Granting Server가 ‘티켓’을 사용자에게 전달 – ticket contains U’ id, A’s id, access rights, session key SA, expiration date Encrypted Under SG 1. Request to Access Server A User U Ticket-Granting Server 2. Ticket to A Server to Access Server A, SA (Encrypted Under KTGS, S), SA Encrypted Under SG

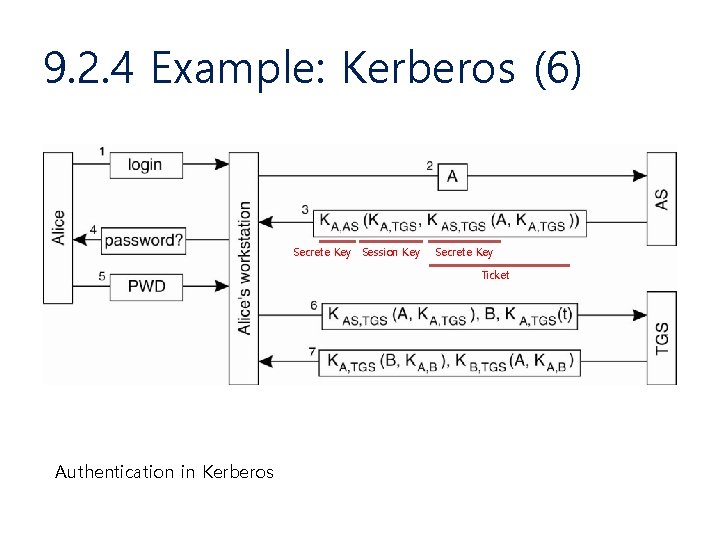
9. 2. 4 Example: Kerberos (6) Secrete Key Session Key Secrete Key Ticket Authentication in Kerberos

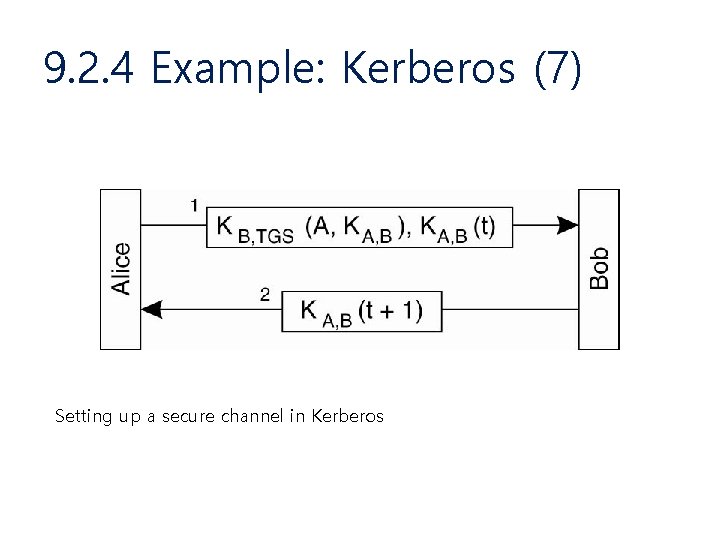
9. 2. 4 Example: Kerberos (7) Setting up a secure channel in Kerberos

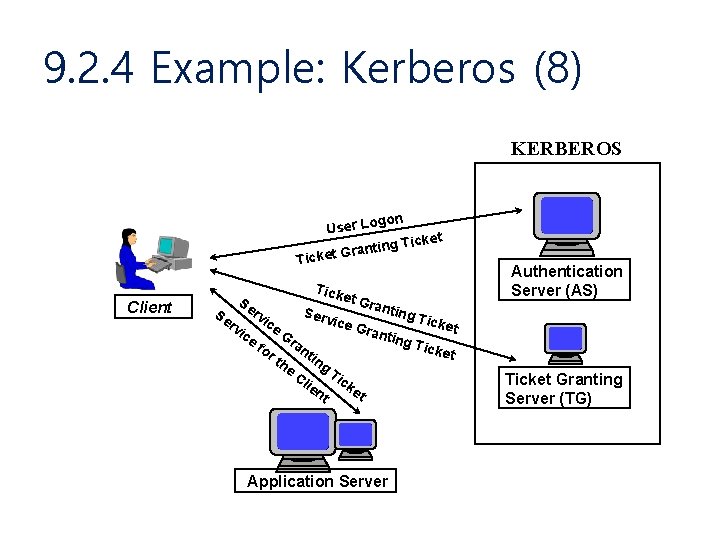
9. 2. 4 Example: Kerberos (8) KERBEROS gon User Lo t g Ticke n i t n a r et G Tick Client Tick Se et G rant ing T ic icke i c rv e Gr e t ic a G n ting e r an Tick fo et tin rt he g Ti Cl c ie nt ket Se rv Serv Application Server Authentication Server (AS) Ticket Granting Server (TG)

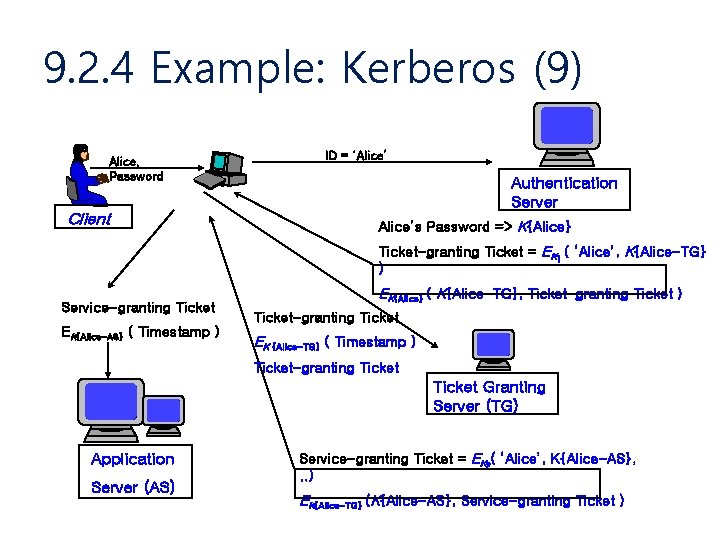
9. 2. 4 Example: Kerberos (9) Alice, Password Client ID = ‘Alice’ Authentication Server Alice’s Password => K{Alice} Ticket-granting Ticket = EK 1 ( ‘Alice’, K{Alice-TG} ) Service-granting Ticket EK{Alice-AS} ( Timestamp ) EK{Alice} ( K{Alice-TG}, Ticket-granting Ticket ) Ticket-granting Ticket EK {Alice-TG} ( Timestamp ) Ticket-granting Ticket Granting Server (TG) Application Server (AS) Service-granting Ticket = EK 2( ‘Alice’, K{Alice-AS}, . . ) EK{Alice-TG} (K{Alice-AS}, Service-granting Ticket )

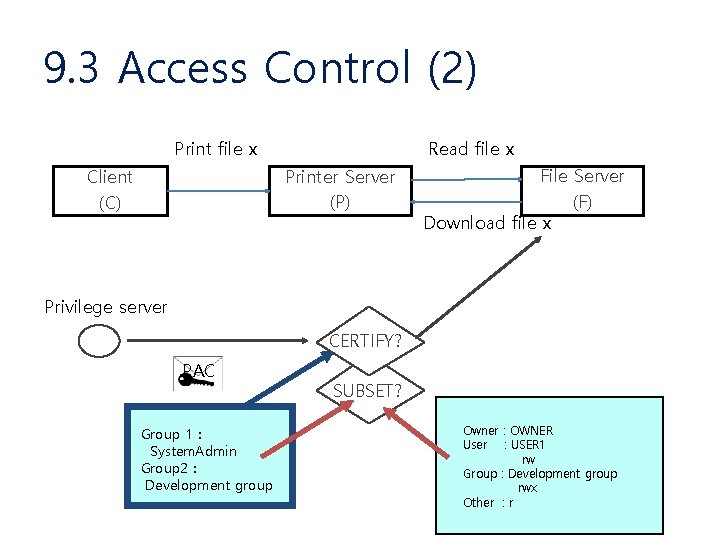
9. 3 Access Control (1) • RBAC (Role Based Access Control) – Subject • Role – Object • ACL (Access Control List) – Ticket = Subject's role + Security 증표 • LPP (Least Privilege Principle) – Privilege per application session • Authentication + Authorization – User Side (인증서버) • Login 인증 + Role 허가 + Security 증표 – Server • Security 증표 인증 + 액세스 허가

9. 3 Access Control (2) Print file x Read file x Printer Server (P) Client (C) File Server (F) Download file x Privilege server CERTIFY? PAC Group 1 : System. Admin Group 2 : Development group SUBSET? Owner : OWNER User : USER 1 rw Group : Development group rwx Other : r





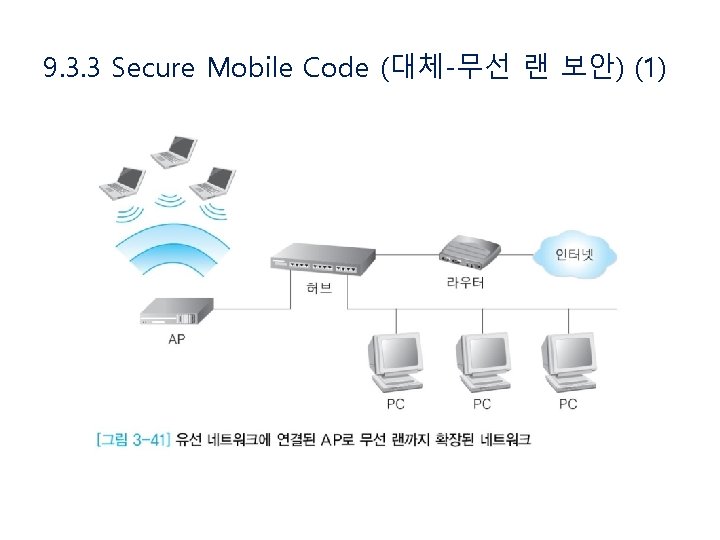
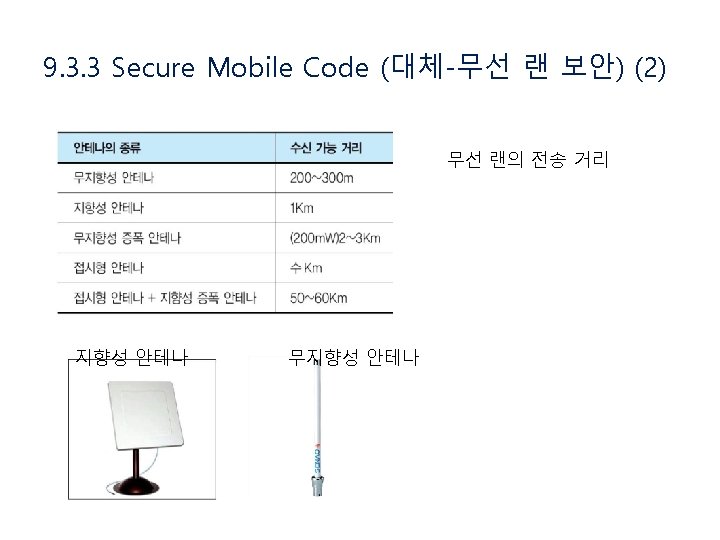
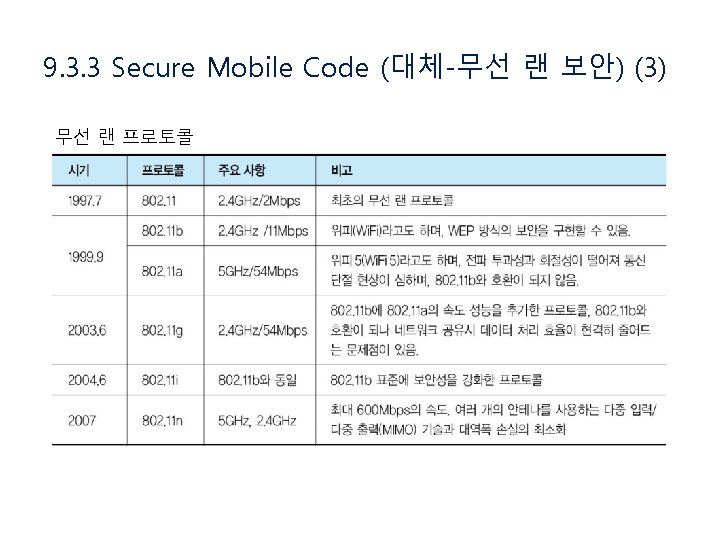
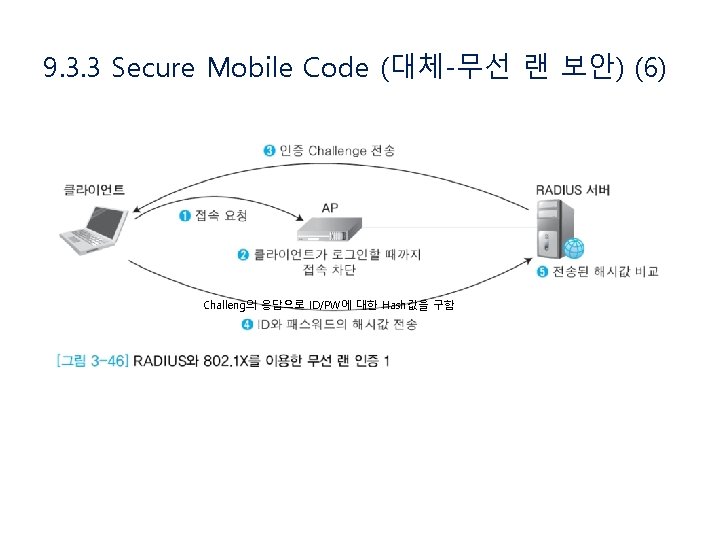
9. 3. 3 Secure Mobile Code (대체-무선 랜 보안) (1)






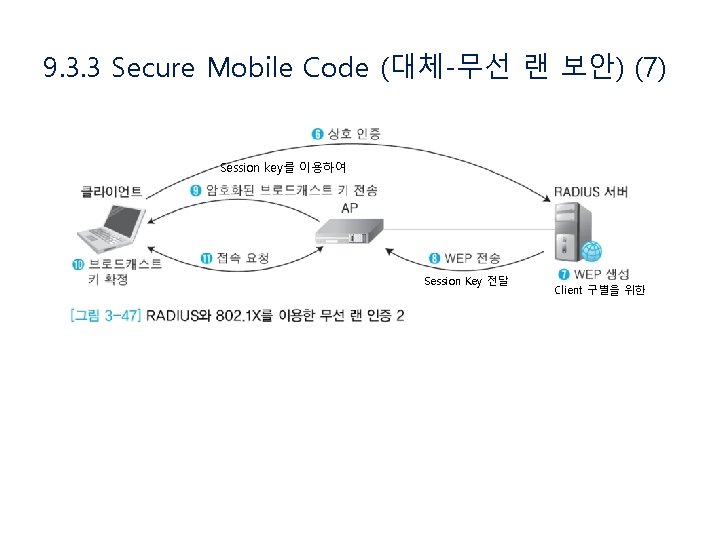
9. 3. 3 Secure Mobile Code (대체-무선 랜 보안) (7) Session key를 이용하여 Session Key 전달 Client 구별을 위한


9. 3. 4 Denial of Service (2)


9. 3. 4 Denial of Service (4)


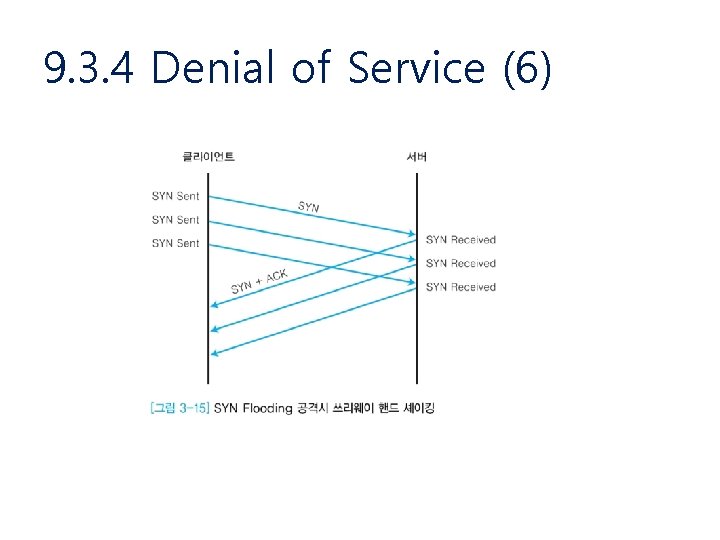
9. 3. 4 Denial of Service (6)


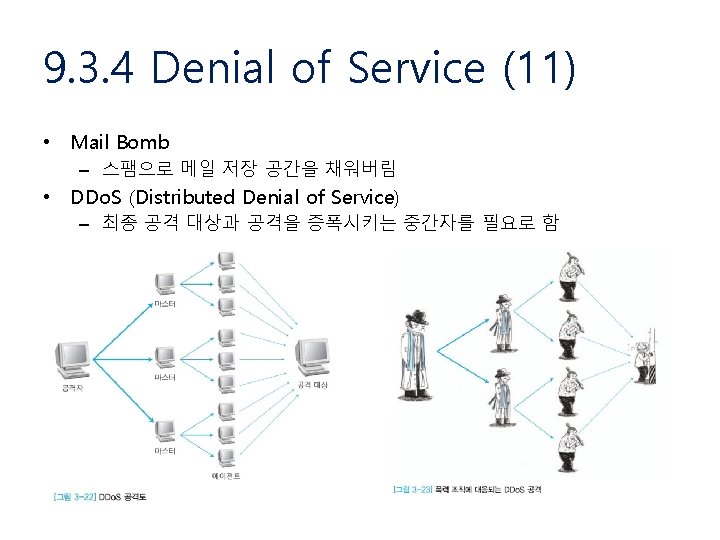
9. 3. 4 Denial of Service (8)

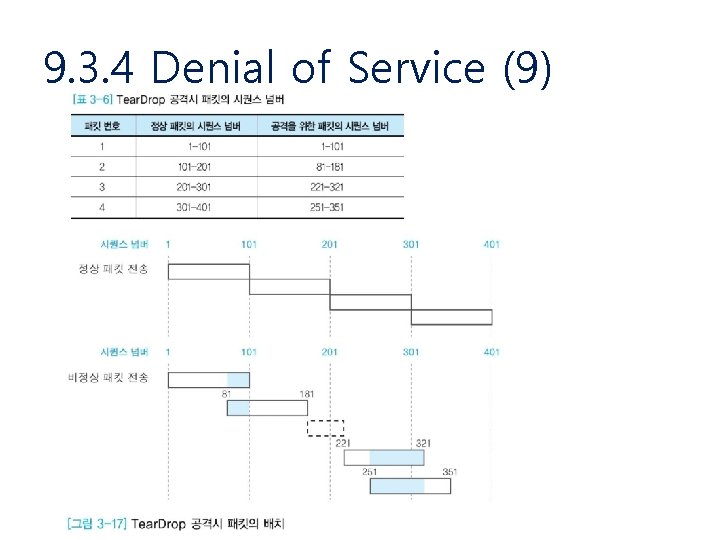
9. 3. 4 Denial of Service (9)



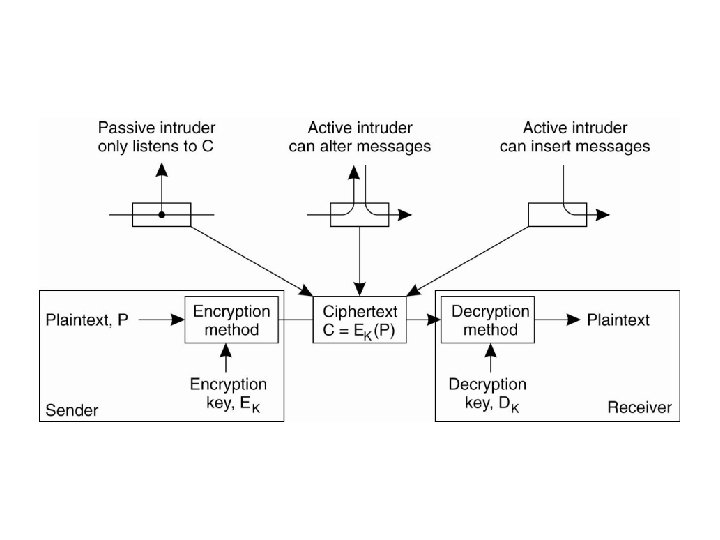
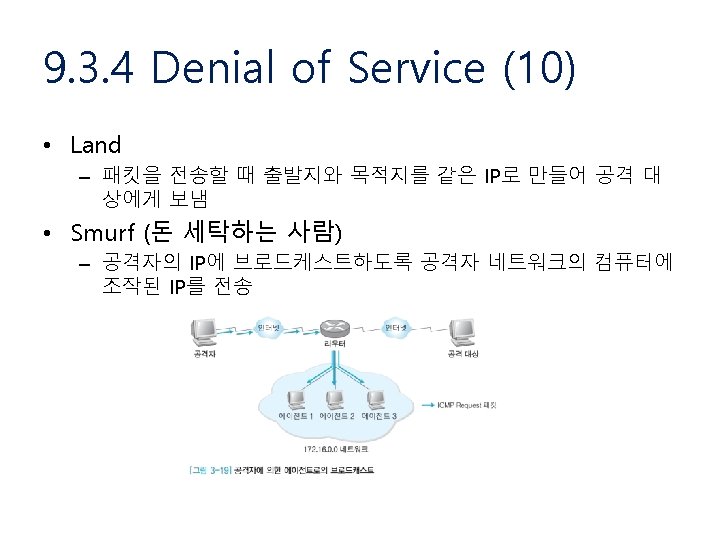
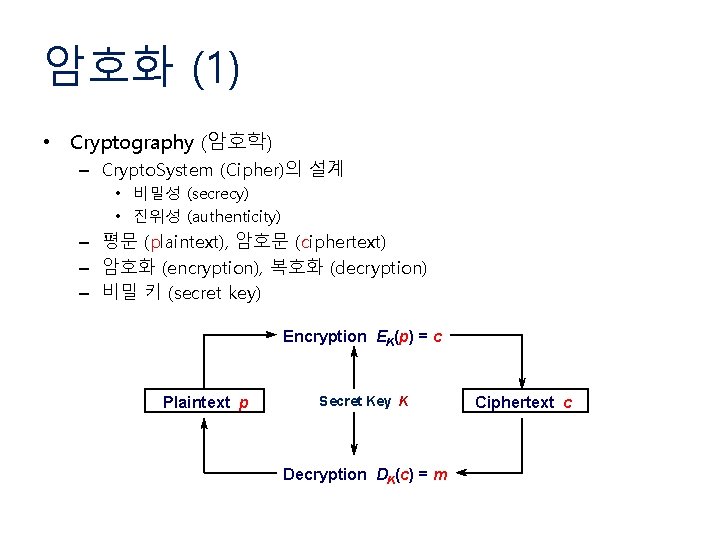
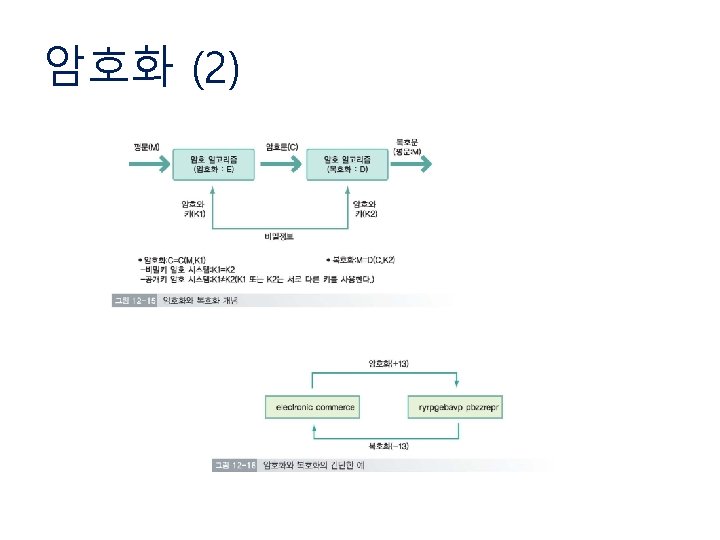
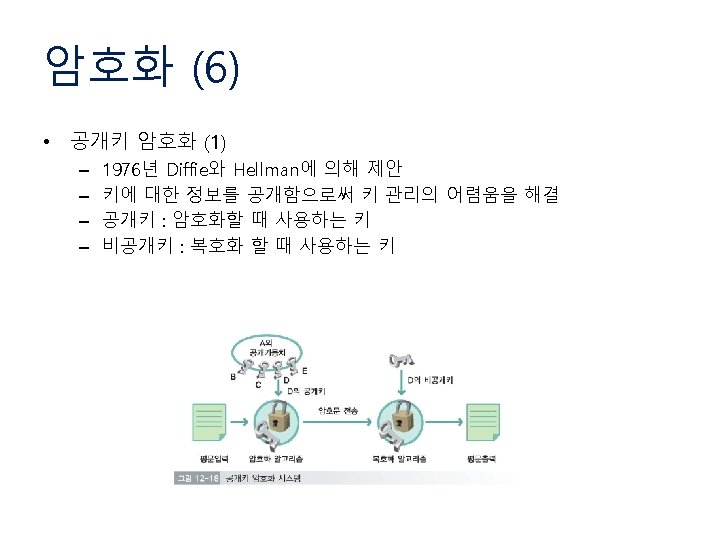
암호화 (1) • Cryptography (암호학) – Crypto. System (Cipher)의 설계 • 비밀성 (secrecy) • 진위성 (authenticity) – 평문 (plaintext), 암호문 (ciphertext) – 암호화 (encryption), 복호화 (decryption) – 비밀 키 (secret key) Encryption EK(p) = c Plaintext p Secret Key K Decryption DK(c) = m Ciphertext c







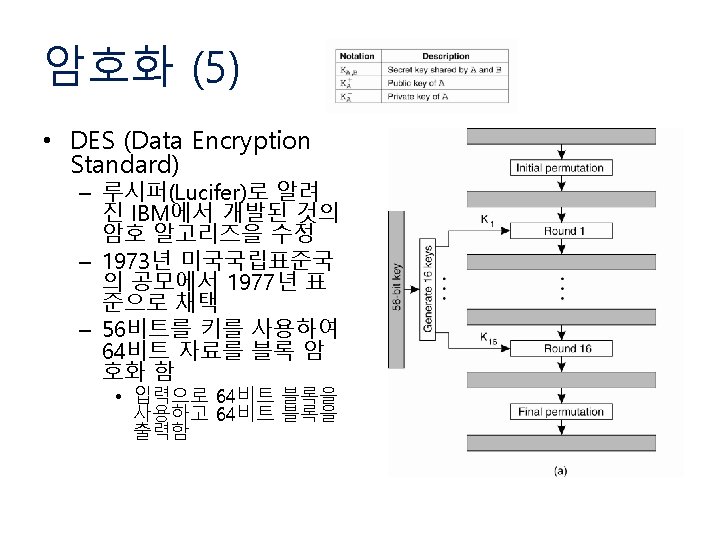
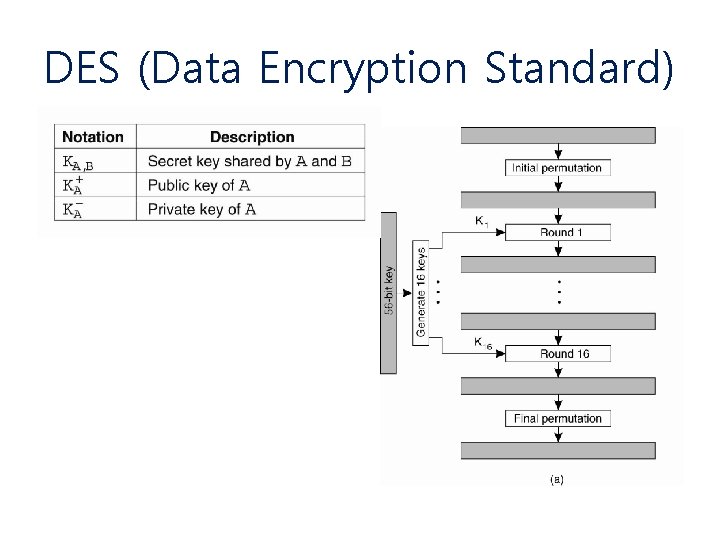
DES (Data Encryption Standard)



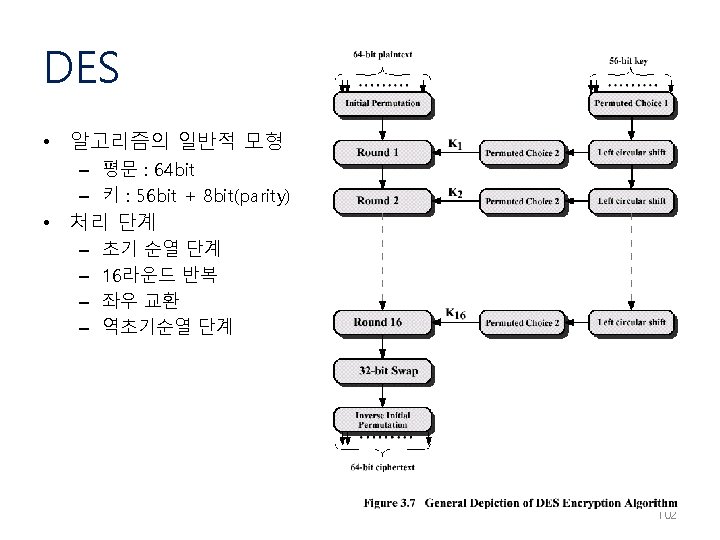
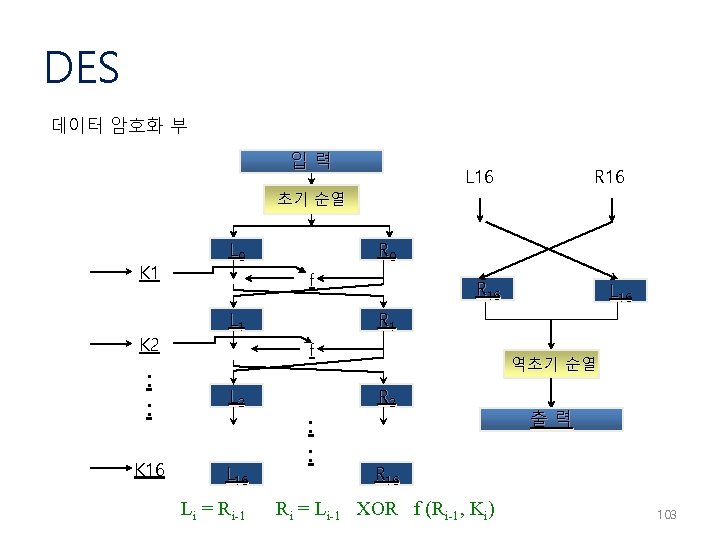
DES 데이터 암호화 부 입력 L 16 R 16 초기 순열 K 1 K 2 L 0 R 0 f L 1 R 16 R 1 f : : L 2 K 16 Li = Ri-1 L 16 : : 역초기 순열 R 2 출력 R 16 Ri = Li-1 XOR f (Ri-1, Ki) 103

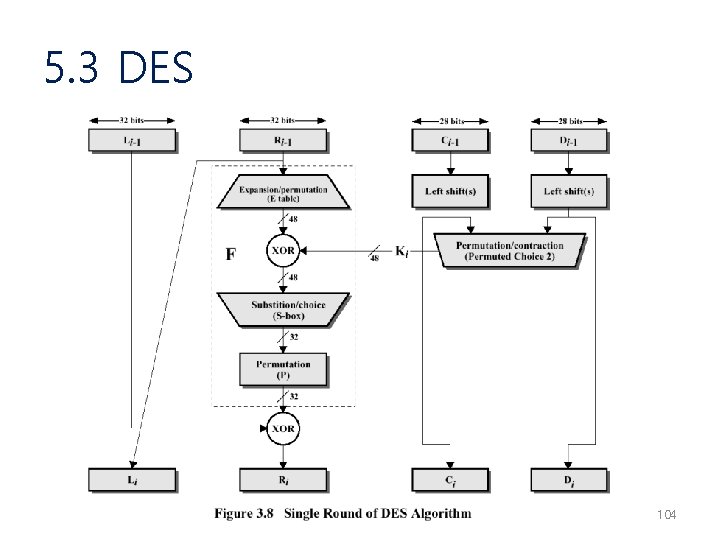
5. 3 DES 104

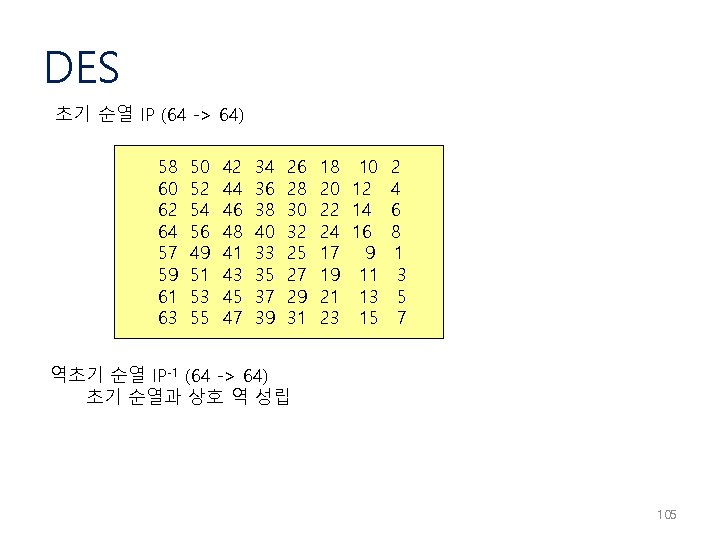
DES 초기 순열 IP (64 -> 64) 58 60 62 64 57 59 61 63 50 52 54 56 49 51 53 55 42 44 46 48 41 43 45 47 34 36 38 40 33 35 37 39 26 28 30 32 25 27 29 31 18 10 20 12 22 14 24 16 17 9 19 11 21 13 23 15 2 4 6 8 1 3 5 7 역초기 순열 IP-1 (64 -> 64) 초기 순열과 상호 역 성립 105

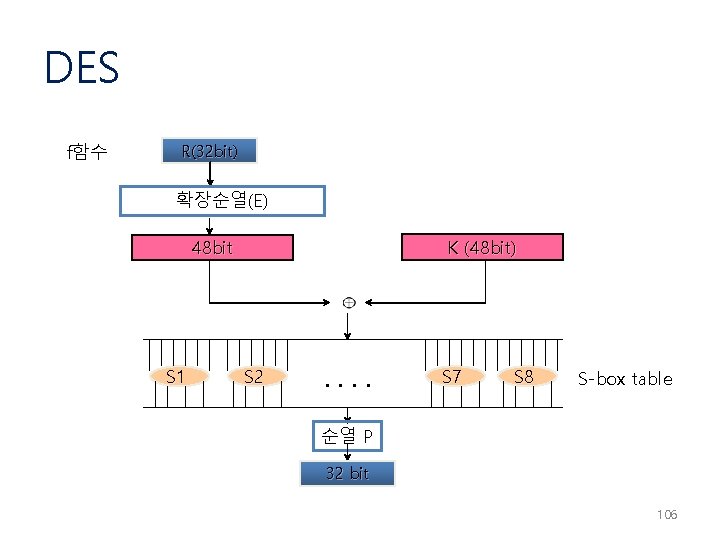
DES f함수 R(32 bit) 확장순열(E) K (48 bit) 48 bit S 1 S 2 . . S 7 S 8 S-box table 순열 P 32 bit 106

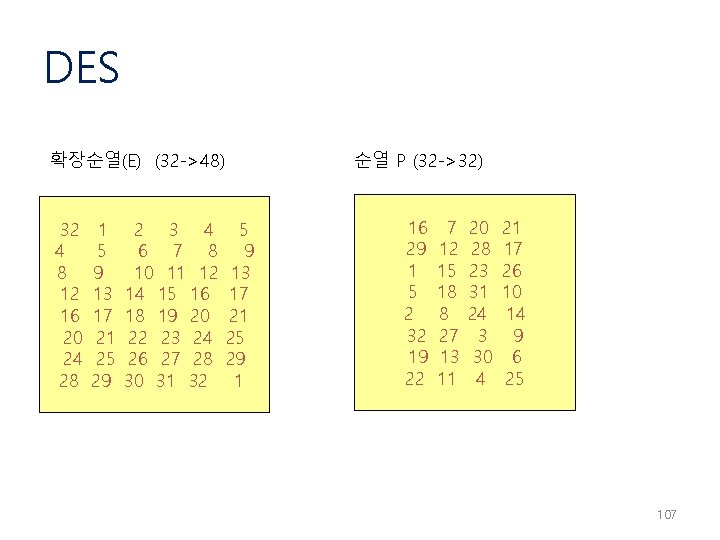
DES 확장순열(E) (32 ->48) 32 4 8 12 16 20 24 28 1 5 9 13 17 21 25 29 2 3 4 6 7 8 10 11 12 14 15 16 18 19 20 22 23 24 26 27 28 30 31 32 순열 P (32 ->32) 5 9 13 17 21 25 29 1 16 29 1 5 2 32 19 22 7 12 15 18 8 27 13 11 20 28 23 31 24 3 30 4 21 17 26 10 14 9 6 25 107

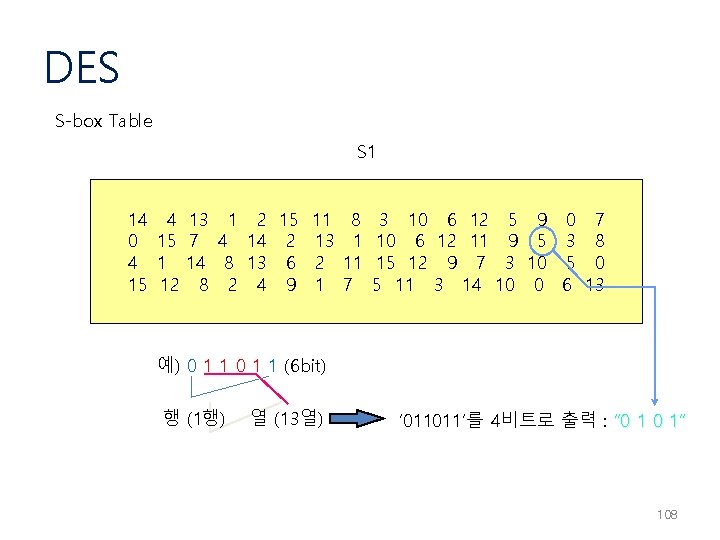
DES S-box Table S 1 14 4 13 1 2 15 11 8 3 10 6 12 5 9 0 7 0 15 7 4 14 2 13 1 10 6 12 11 9 5 3 8 4 1 14 8 13 6 2 11 15 12 9 7 3 10 5 0 15 12 8 2 4 9 1 7 5 11 3 14 10 0 6 13 예) 0 1 1 (6 bit) 행 (1행) 열 (13열) ‘ 011011’를 4비트로 출력 : “ 0 1” 108


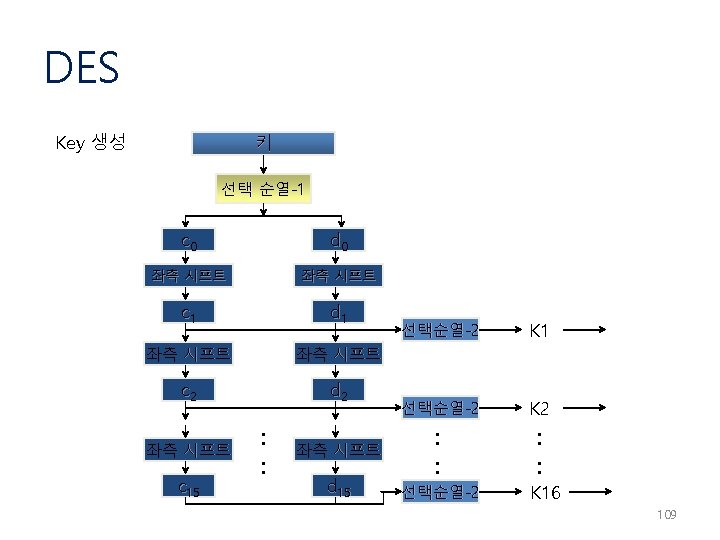
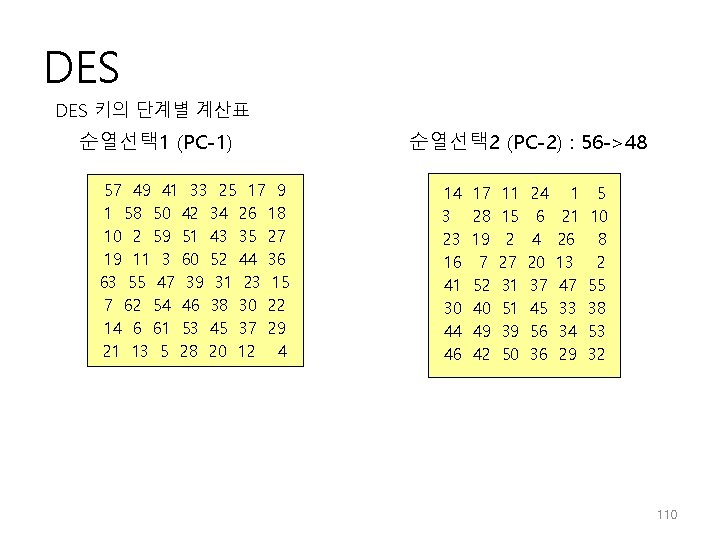
DES 키의 단계별 계산표 순열선택 1 (PC-1) 57 49 41 33 25 17 9 1 58 50 42 34 26 18 10 2 59 51 43 35 27 19 11 3 60 52 44 36 63 55 47 39 31 23 15 7 62 54 46 38 30 22 14 6 61 53 45 37 29 21 13 5 28 20 12 4 순열선택 2 (PC-2) : 56 ->48 14 3 23 16 41 30 44 46 17 28 19 7 52 40 49 42 11 15 2 27 31 51 39 50 24 6 4 20 37 45 56 36 1 21 26 13 47 33 34 29 5 10 8 2 55 38 53 32 110

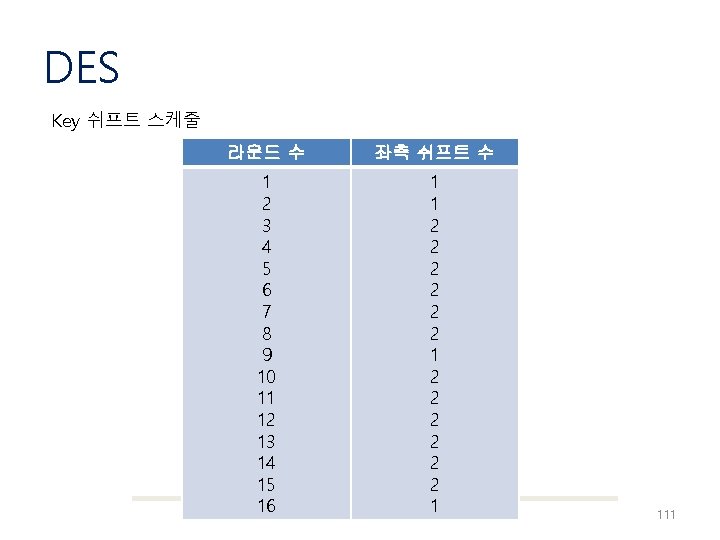
DES Key 쉬프트 스케줄 라운드 수 좌측 쉬프트 수 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 1 1 2 2 2 1 111



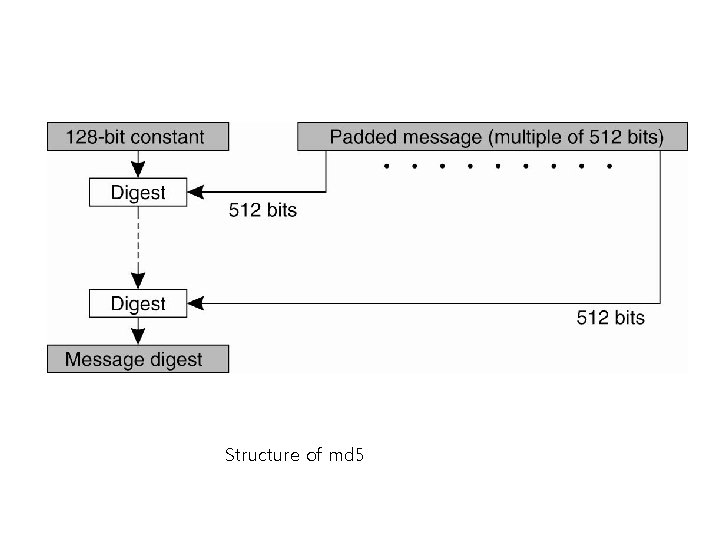
Structure of md 5

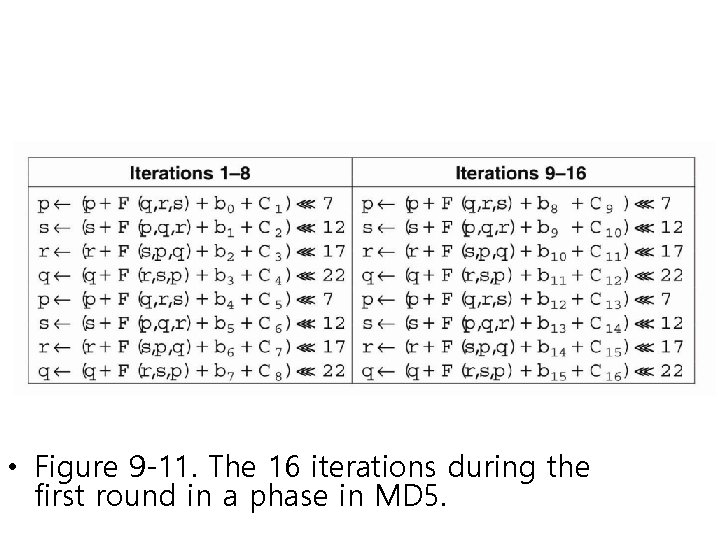
• Figure 9 -11. The 16 iterations during the first round in a phase in MD 5.

























