Introduction to Symantec Email Security Service Anthony Holmes





- Slides: 15

Introduction to Symantec Email Security Service Anthony Holmes Cloud Architect, EMEA & APJ

Evolving Email Threat Landscape Email is the Delivery mechanism for malware #1 36% 8, 000 55% 30% 72% Increase in ransomware Businesses targeted each month by BEC scams Increase in spear phishing campaigns Users opened phishing emails Incident responders use security analytics to speed detection & response Source: ISTR Report 2017, Email ISTR Report 2017, ISTR Report 2016, Verizon DBIR 2016, 2016 SANS Incident Response Survey Copyright © 2018 Symantec Corporation 2

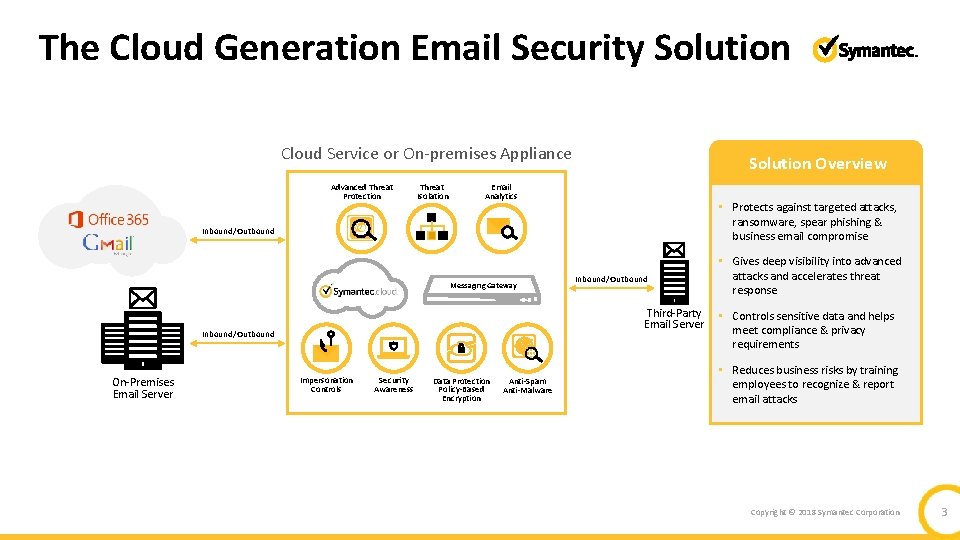
The Cloud Generation Email Security Solution Cloud Service or On-premises Appliance Advanced Threat Protection Threat Isolation Solution Overview Email Analytics • Protects against targeted attacks, ransomware, spear phishing & business email compromise Inbound/Outbound Messaging Gateway Third-Party Email Server Inbound/Outbound On-Premises Email Server Inbound/Outbound Impersonation Controls Security Awareness Data Protection Policy-Based Encryption Anti-Spam Anti-Malware • Gives deep visibility into advanced attacks and accelerates threat response • Controls sensitive data and helps meet compliance & privacy requirements • Reduces business risks by training employees to recognize & report email attacks Copyright © 2018 Symantec Corporation 3

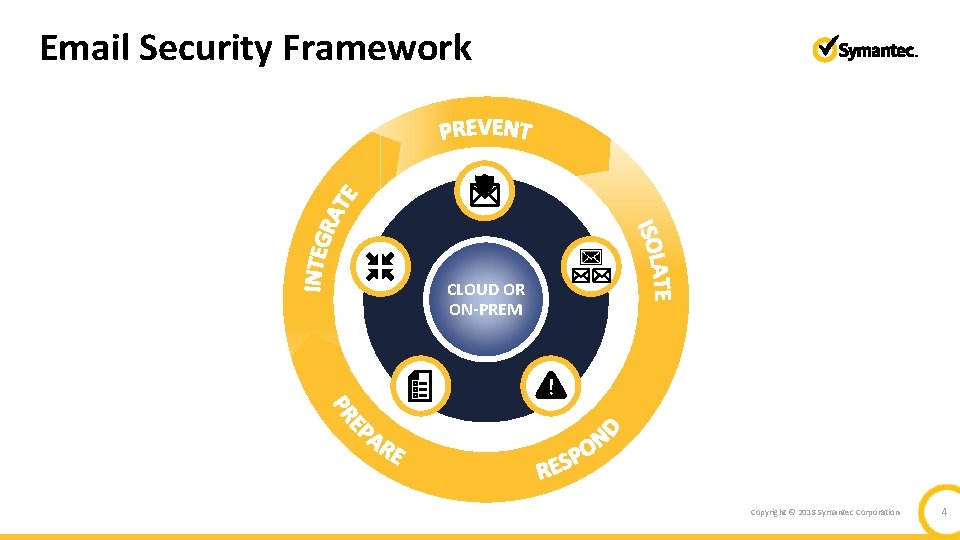
Email Security Framework CLOUD OR ON-PREM Copyright © 2018 Symantec Corporation 4

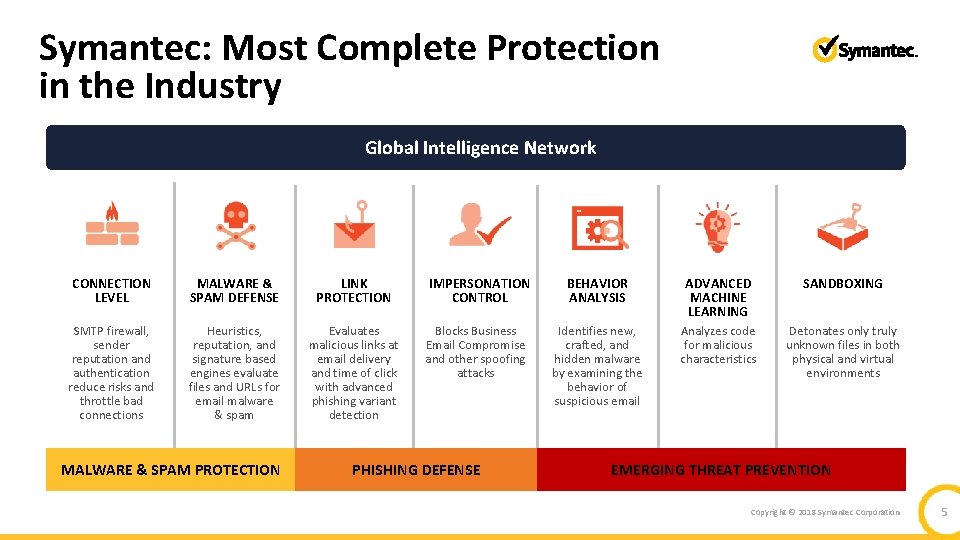
Symantec: Most Complete Protection in the Industry Global Intelligence Network CONNECTION LEVEL MALWARE & SPAM DEFENSE LINK PROTECTION SMTP firewall, sender reputation and authentication reduce risks and throttle bad connections Heuristics, reputation, and signature based engines evaluate files and URLs for email malware & spam Evaluates malicious links at email delivery and time of click with advanced phishing variant detection MALWARE & SPAM PROTECTION IMPERSONATION CONTROL Blocks Business Email Compromise and other spoofing attacks PHISHING DEFENSE BEHAVIOR ANALYSIS ADVANCED MACHINE LEARNING SANDBOXING Identifies new, crafted, and hidden malware by examining the behavior of suspicious email Analyzes code for malicious characteristics Detonates only truly unknown files in both physical and virtual environments EMERGING THREAT PREVENTION Copyright © 2018 Symantec Corporation 5

Business Email Compromise Attacks Are Preying on Users $5 B+ Simple Concept Difficult to Block Large Financial Losses Email sent from CEO requesting large money transfer or sensitive data Low volume emails with generic content and no malicious code or links Average loss from BEC attacks was $210, 000 in 2016 Exposes losses to Business Email Compromise (BEC) fraud over the past 3 years Source: FBI Public Service Announcement, I-050417 -PSA (May 2017) 2400% Increase in BEC attacks since 2015 Copyright © 2018 Symantec Corporation 6

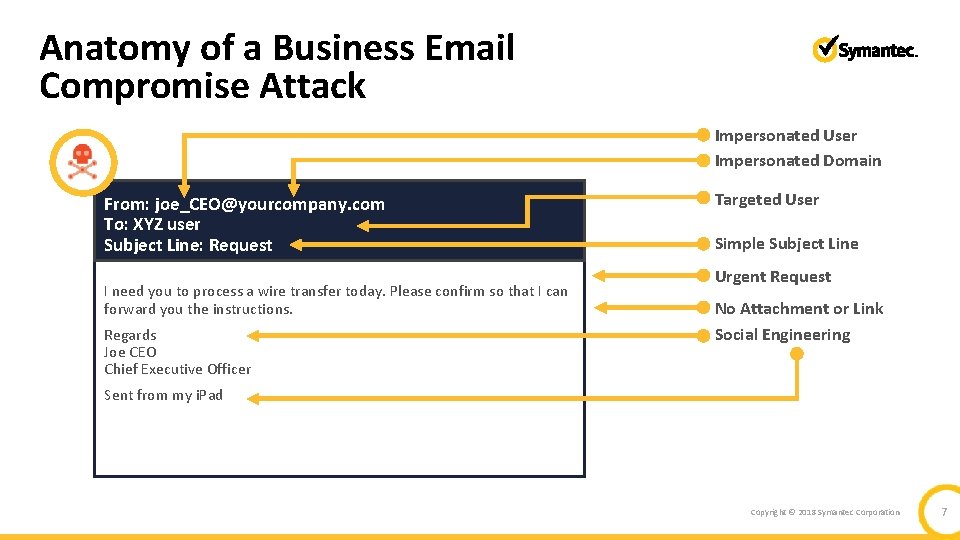
Anatomy of a Business Email Compromise Attack Impersonated User Impersonated Domain From: joe_CEO@yourcompany. com To: XYZ user Subject Line: Request I need you to process a wire transfer today. Please confirm so that I can forward you the instructions. Regards Joe CEO Chief Executive Officer Targeted User Simple Subject Line Urgent Request No Attachment or Link Social Engineering Sent from my i. Pad Copyright © 2018 Symantec Corporation 7

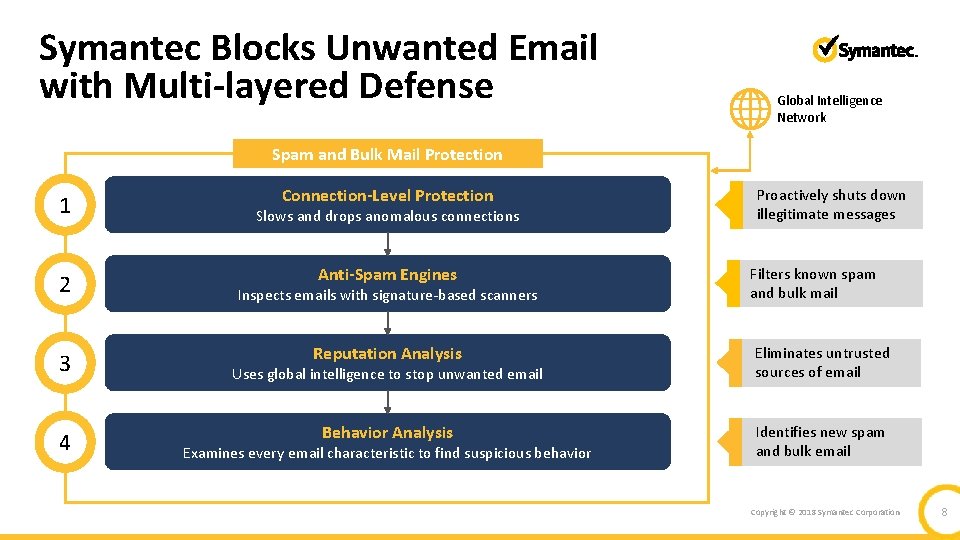
Symantec Blocks Unwanted Email with Multi-layered Defense Global Intelligence Network Spam and Bulk Mail Protection 1 2 3 4 Connection-Level Protection Slows and drops anomalous connections Proactively shuts down illegitimate messages Anti-Spam Engines Filters known spam and bulk mail Reputation Analysis Eliminates untrusted sources of email Behavior Analysis Identifies new spam and bulk email Inspects emails with signature-based scanners Uses global intelligence to stop unwanted email Examines every email characteristic to find suspicious behavior Copyright © 2018 Symantec Corporation 8

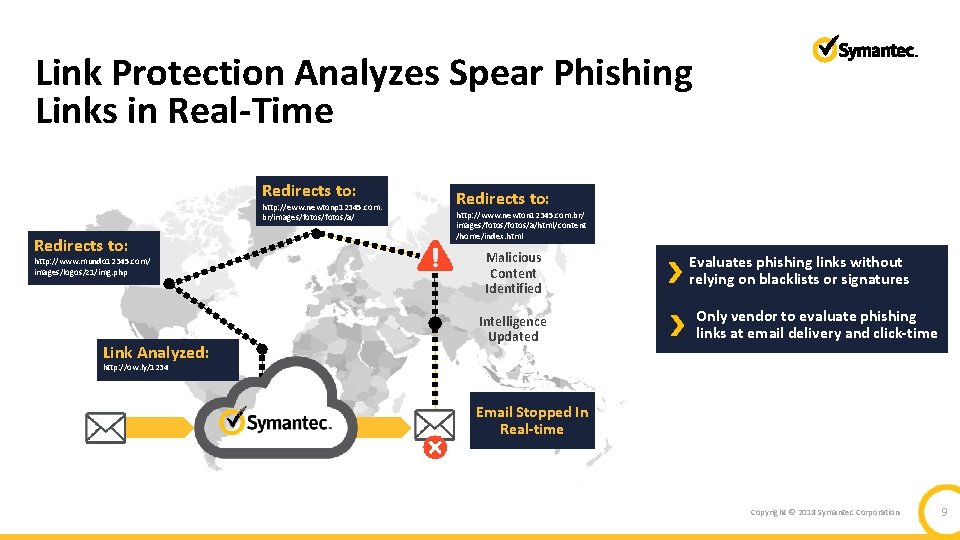
Link Protection Analyzes Spear Phishing Links in Real-Time Redirects to: http: //eww. newtonp 12345. com. br/images/fotos/a/ Redirects to: http: //www. mundo 12345. com/ images/logos/z 1/img. php Link Analyzed: Redirects to: http: //www. newton 12345. com. br/ images/fotos/a/html/content /home/index. html Malicious Content Identified Intelligence Updated Evaluates phishing links without relying on blacklists or signatures Only vendor to evaluate phishing links at email delivery and click-time http: //ow. ly/1234 Email Stopped In Real-time Copyright © 2018 Symantec Corporation 9

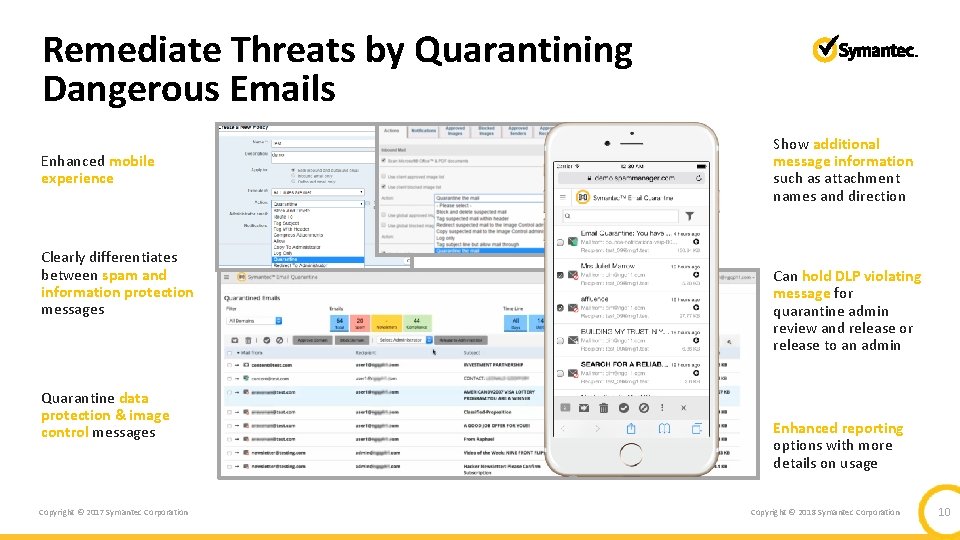
Remediate Threats by Quarantining Dangerous Emails Enhanced mobile experience Clearly differentiates between spam and information protection messages Quarantine data protection & image control messages Copyright © 2017 Symantec Corporation Show additional message information such as attachment names and direction Can hold DLP violating message for quarantine admin review and release or release to an admin Enhanced reporting options with more details on usage Copyright © 2018 Symantec Corporation 10

Automatically Remediate Email Threats in Office 365 Clawback emails from Office 365 after they’ve been delivered Contain threats and stop missed email attacks from spreading 2 Symantec GIN 1 Email scanned and delivered 3 Remediation Speed remediation of potential issues Copyright © 2017 Symantec Corporation Copyright © 2018 Symantec Corporation 11

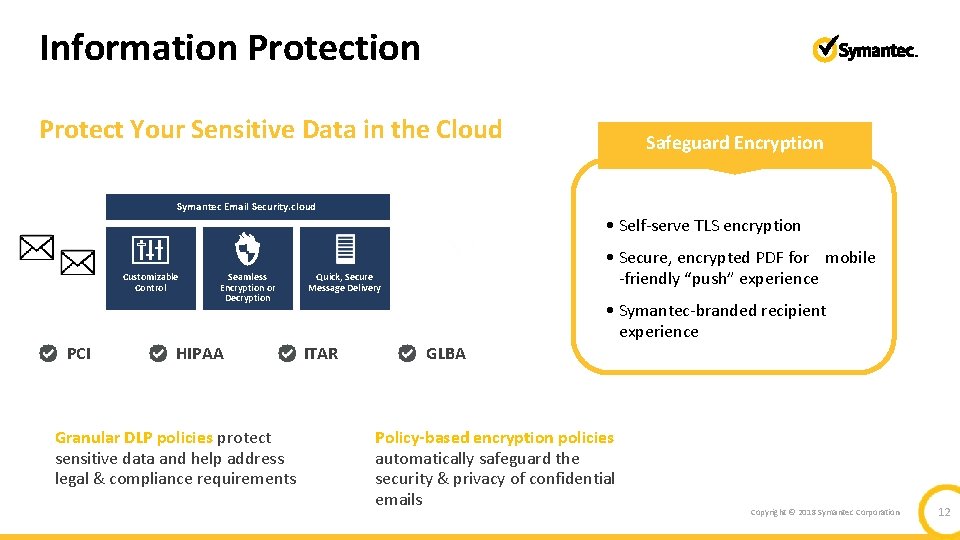
Information Protect Your Sensitive Data in the Cloud Safeguard Encryption Symantec Email Security. cloud • Self-serve TLS encryption Customizable Control PCI Seamless Encryption or Decryption HIPAA Granular DLP policies protect sensitive data and help address legal & compliance requirements Quick, Secure Message Delivery ITAR Advanced Detection Technologies GLBA Multi-Channel Coverage • Secure, encrypted PDF for mobile -friendly “push” experience • Symantec-branded recipient experience Policy-based encryption policies automatically safeguard the security & privacy of confidential emails Copyright © 2018 Symantec Corporation 12

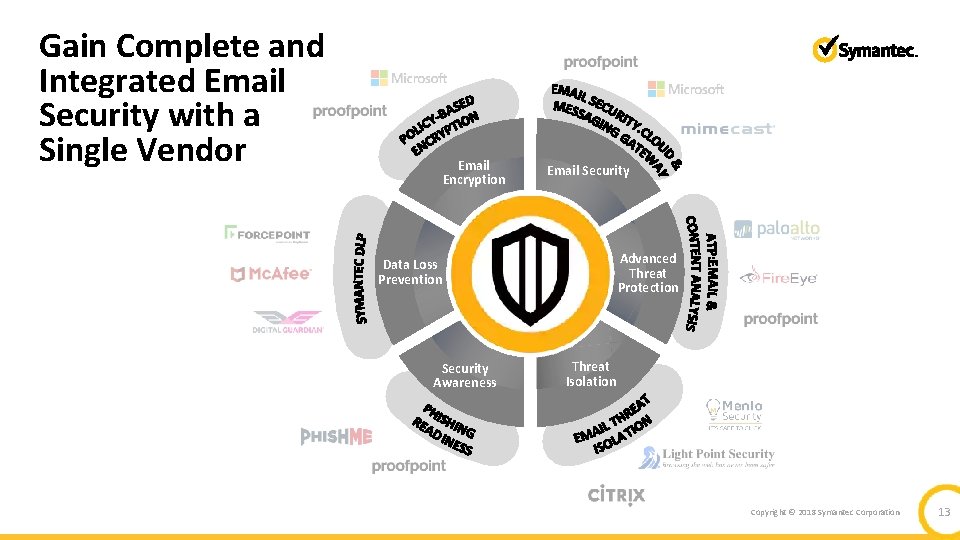
Gain Complete and Integrated Email Security with a Single Vendor Email Encryption Email Security Advanced Threat Protection Data Loss Prevention Security Awareness Threat Isolation Copyright © 2018 Symantec Corporation 13

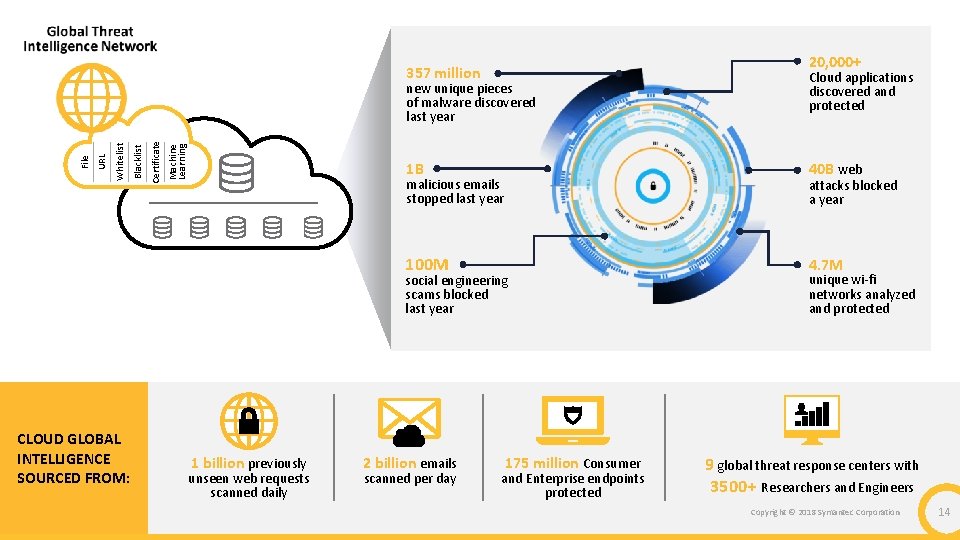
20, 000+ 357 million Machine Learning Certificate Blacklist Whitelist URL File new unique pieces of malware discovered last year 1 B 40 B web 100 M 4. 7 M malicious emails stopped last year social engineering scams blocked last year CLOUD GLOBAL INTELLIGENCE SOURCED FROM: 1 billion previously unseen web requests scanned daily Cloud applications discovered and protected 2 billion emails scanned per day 175 million Consumer and Enterprise endpoints protected attacks blocked a year unique wi-fi networks analyzed and protected 9 global threat response centers with 3500+ Researchers and Engineers Copyright © 2018 Symantec Corporation 14

Thank you