Chapter 12 Network Security Security Policy Life Cycle




















- Slides: 49

Chapter 12 Network Security

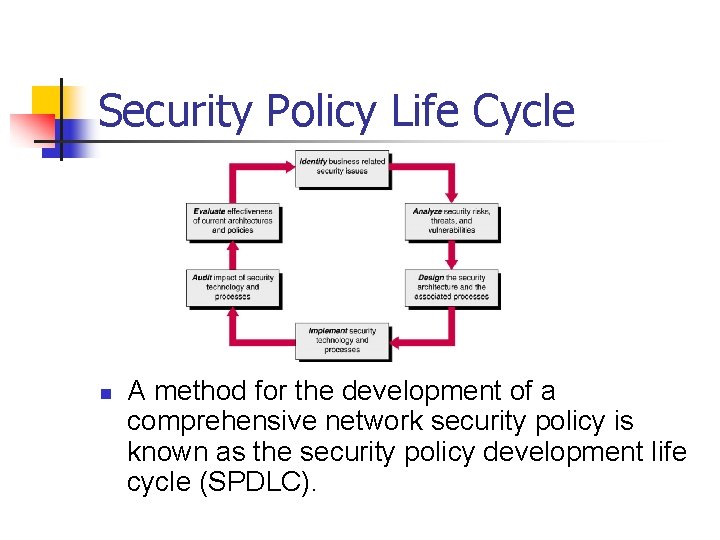
Security Policy Life Cycle n A method for the development of a comprehensive network security policy is known as the security policy development life cycle (SPDLC).

Network Security n n n A successful network security implementation requires a marriage of technology and process. Roles and responsibilities and corporate standards for business processes and acceptable network related behavior must be clearly defined, effectively shared, universally understood, and vigorously enforced for implemented network security technology to be effective. Process definition and setting of corporate security standards must precede technology evaluation and implementation.

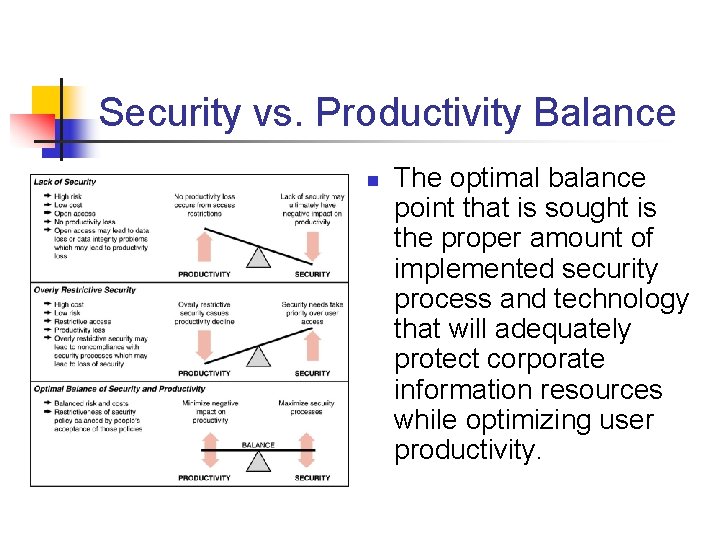
Security vs. Productivity Balance n The optimal balance point that is sought is the proper amount of implemented security process and technology that will adequately protect corporate information resources while optimizing user productivity.

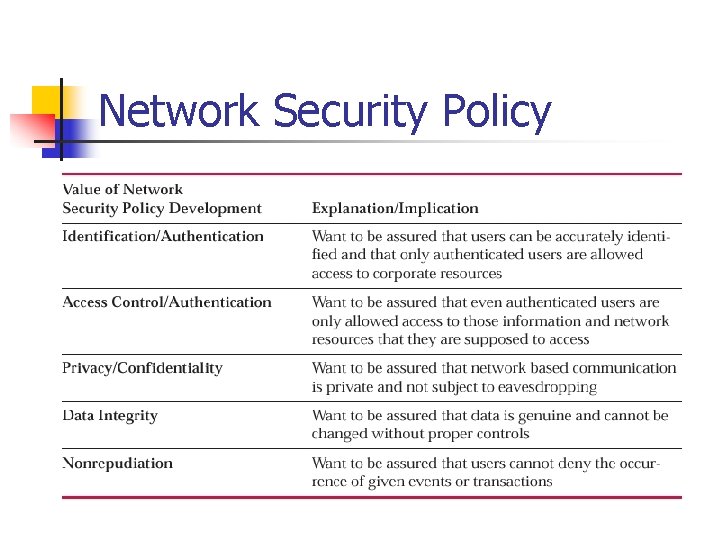
Network Security Policy

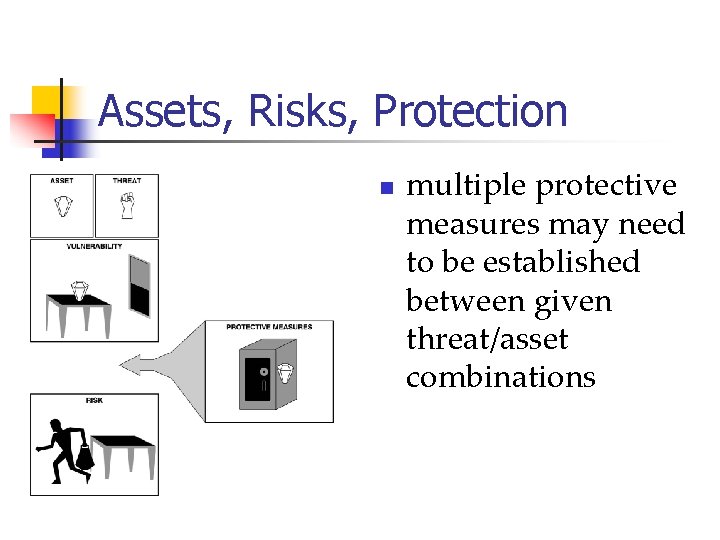
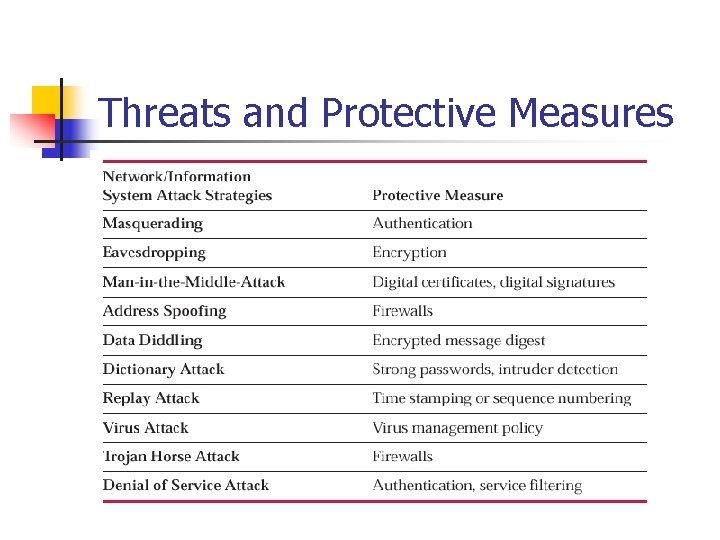
Assets, Risks, Protection n multiple protective measures may need to be established between given threat/asset combinations

Protective Measures n The major categories of potential protective measures are: n n n Virus protection Firewalls Authentication Encryption Intrusion detection

Threats and Protective Measures

n n Once policies have been developed, it is up to everyone to support those policies in their own way. Having been included in the policy development process, users should also be expected to actively support the implemented acceptable use policies.

Executive’s Responsibilities

Management's Responsibilities

Acceptable Use Policy Development

User’s Responsibilities

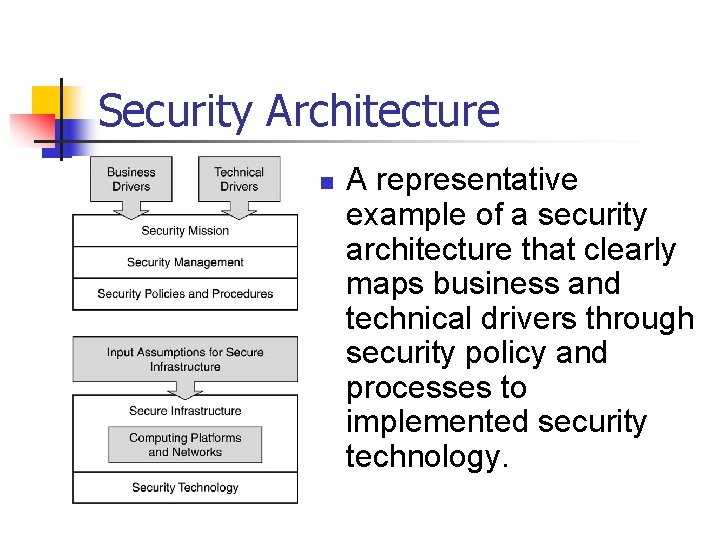
Security Architecture n A representative example of a security architecture that clearly maps business and technical drivers through security policy and processes to implemented security technology.

CSF for Network Security Policy

Virus Protection n Virus protection is often the first area of network security addressed by individuals or corporations. A comprehensive virus protection plan must combine policy, people, processes, and technology to be effective. Too often, virus protection is thought to be a technology based quick fix.

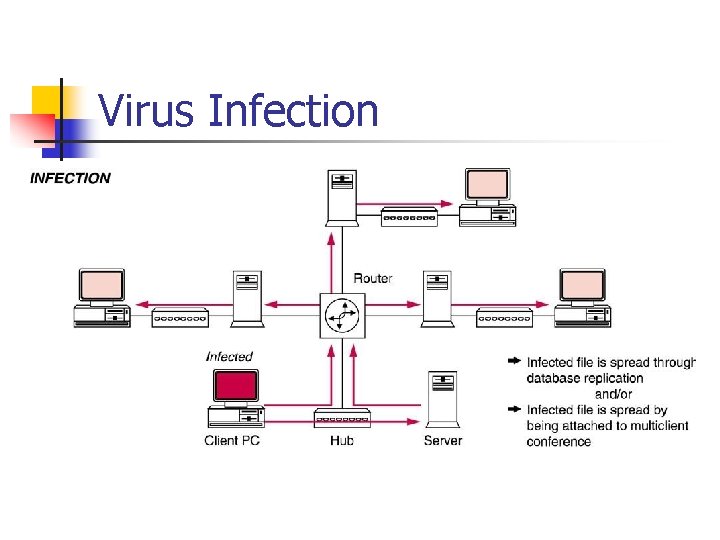
Virus Infection

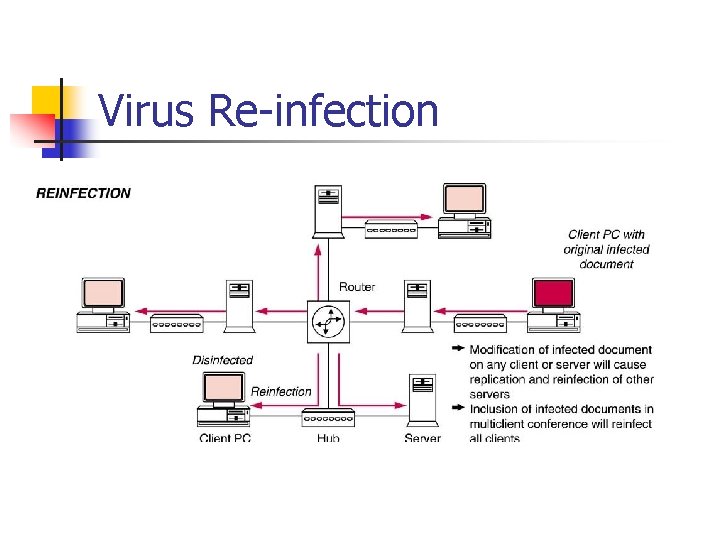
Virus Re infection

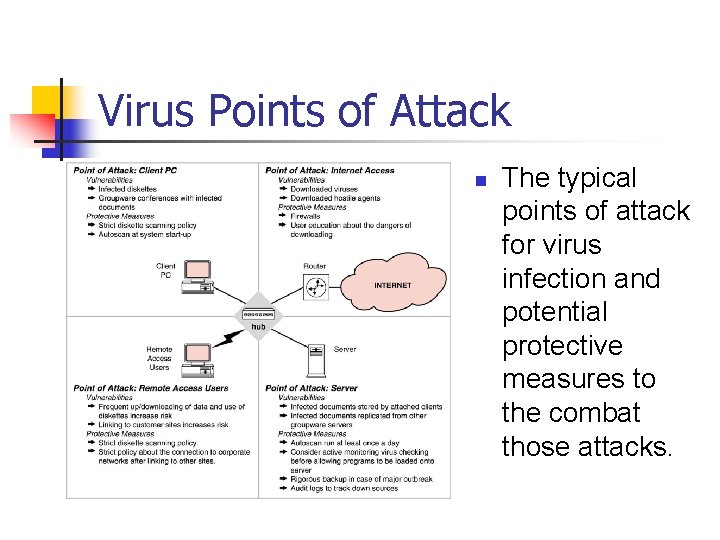
Virus Points of Attack n The typical points of attack for virus infection and potential protective measures to the combat those attacks.

Anti virus Strategies

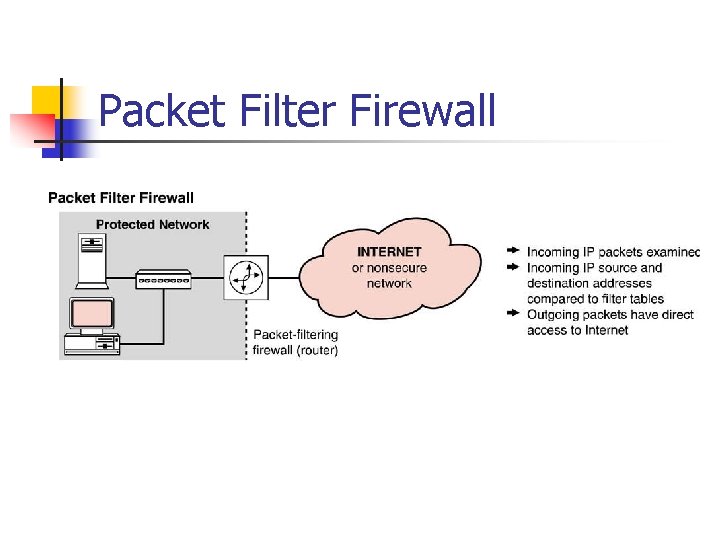
Firewalls n n n When a company links to the Internet, a two way access point out of as well as into that company’s confidential information systems is created. Firewall software usually runs on a dedicated server that is connected to, but outside of, the corporate network. All network packets entering the firewall are filtered or examined

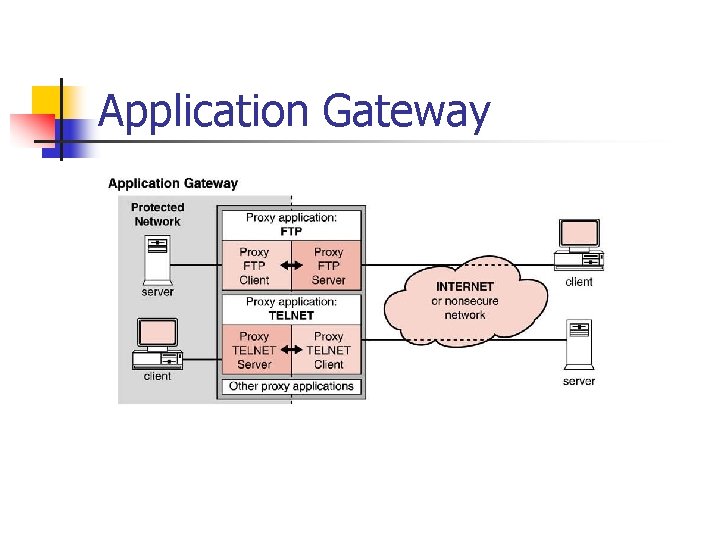
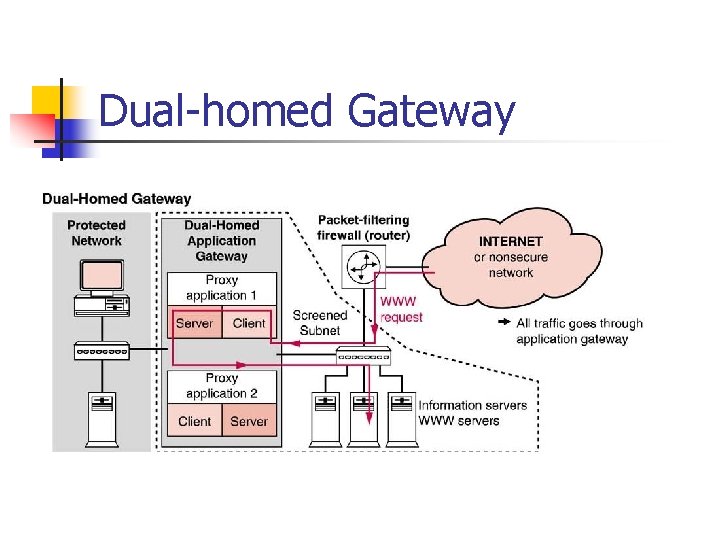
Firewalls n n Firewalls provide a layer of isolation between the inside network and the outside network. The underlying assumption in such a design scenario is that all of the threats come from the outside network. Incorrectly implemented firewalls can actually exacerbate the situation by creating new, and sometimes undetected, security holes. There a number of Firewall types…

Packet Filter Firewall

Application Gateway

Trusted Gateway

Dual homed Gateway

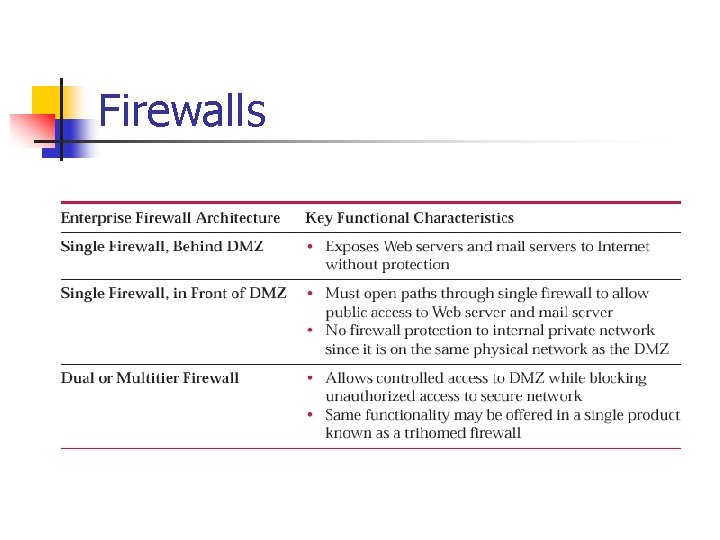
Firewalls

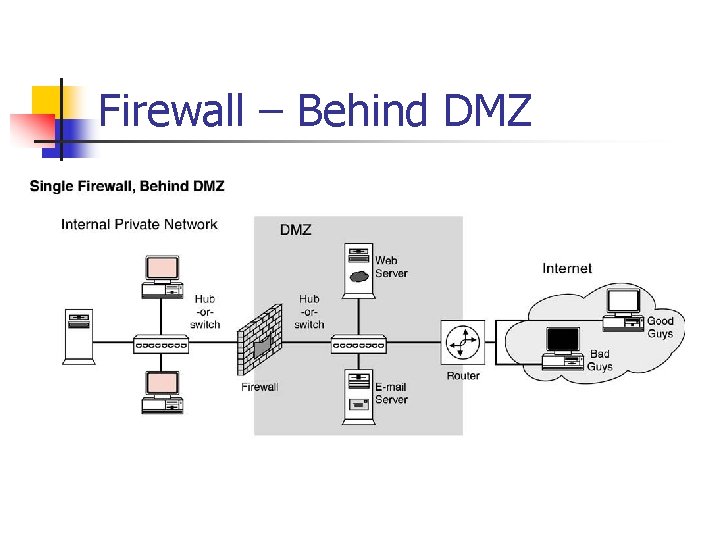
Firewall – Behind DMZ

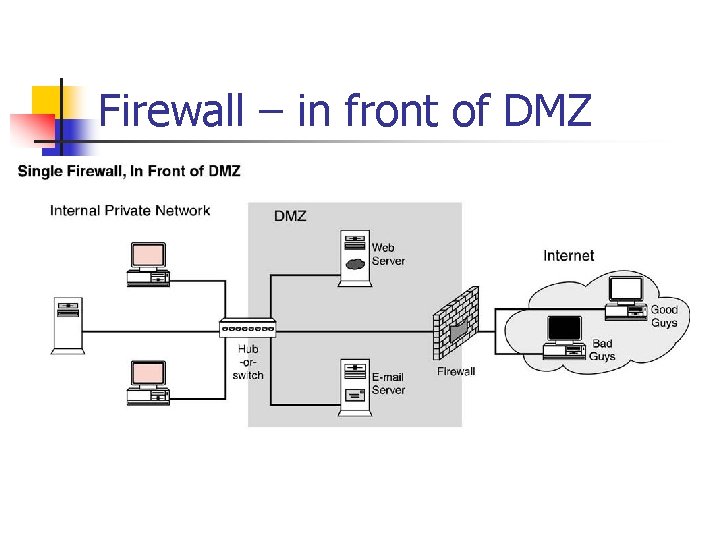
Firewall – in front of DMZ

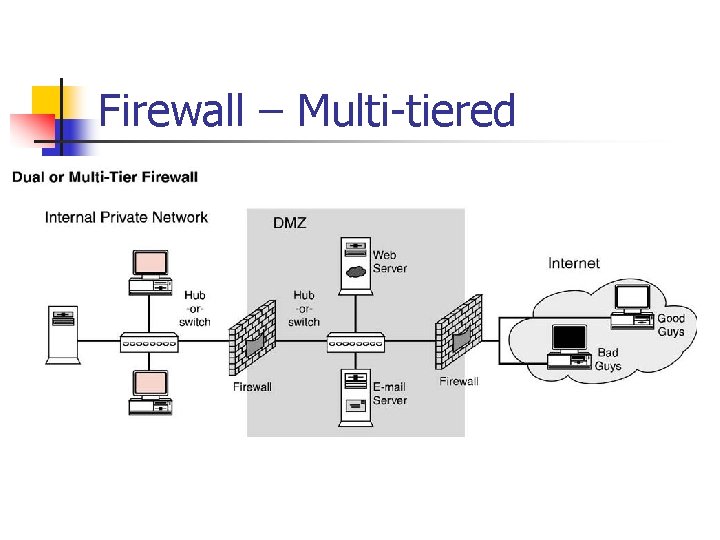
Firewall – Multi tiered

Authentication and Access Control n n The purpose of authentication is to ensure that users attempting to gain access to networks are really who they claim to be. Password protection was the traditional means to ensure authentication. Password protection by itself is no longer sufficient to ensure authentication. A wide variety of technology has been developed to ensure that users really are who they say they are.

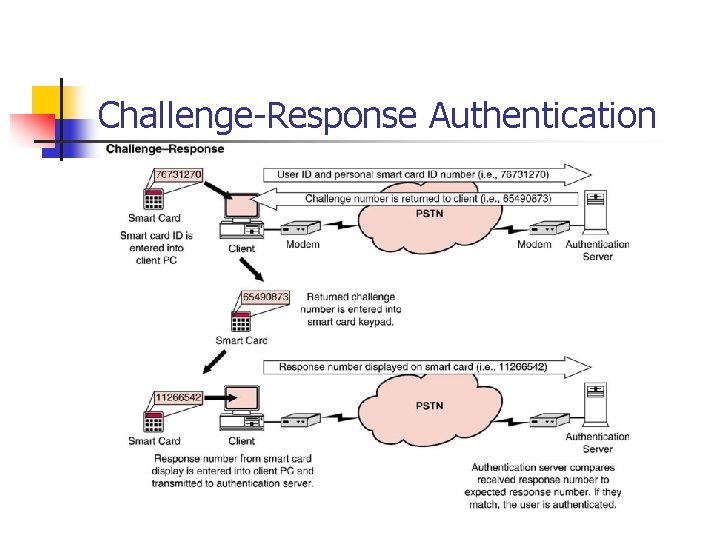
Challenge Response Authentication

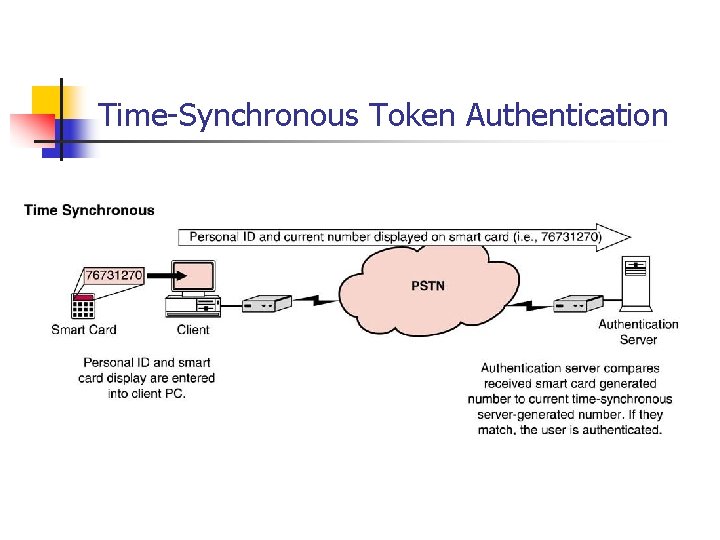
Time Synchronous Token Authentication

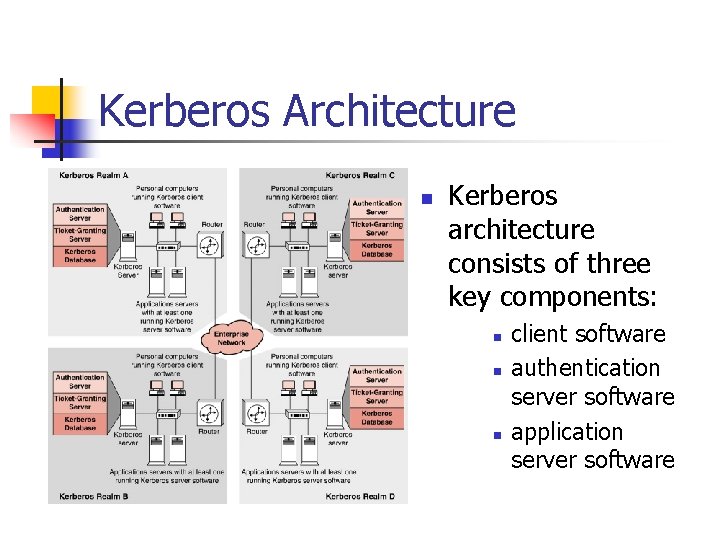
Kerberos Architecture n Kerberos architecture consists of three key components: n n n client software authentication server software application server software

Encryption n n Encryption involves the changing of data into an indecipherable form before transmission. If the transmitted data are somehow intercepted, they cannot be interpreted. The changed, unmeaningful data is known as ciphertext. Encryption must be accompanied by decryption, or changing the unreadable text back into its original form.

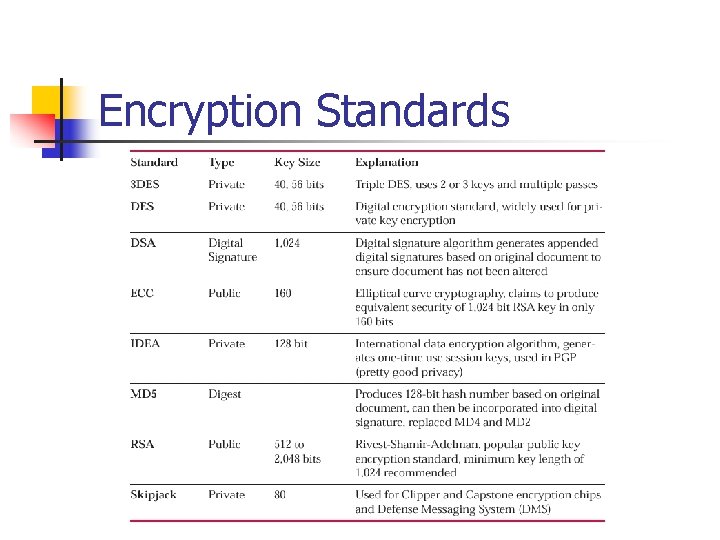
Encryption Standards

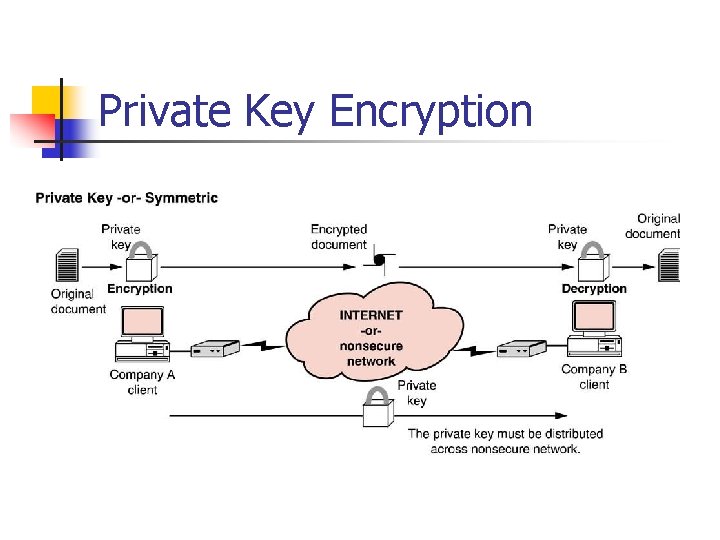
Private Key Encryption

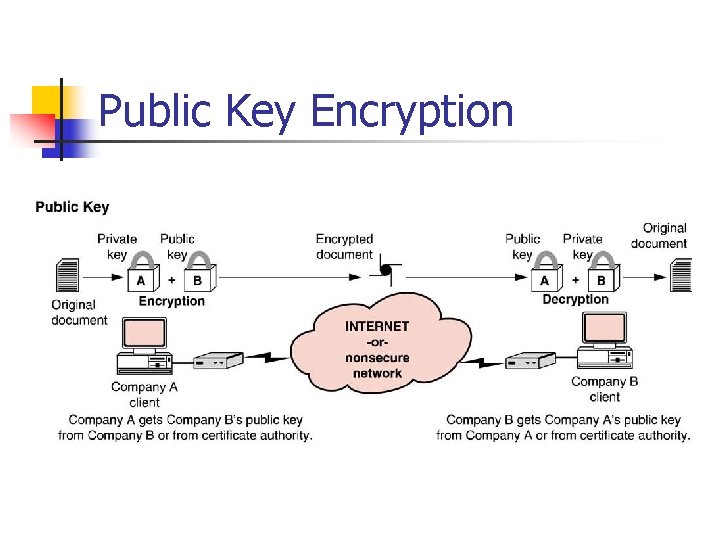
Public Key Encryption

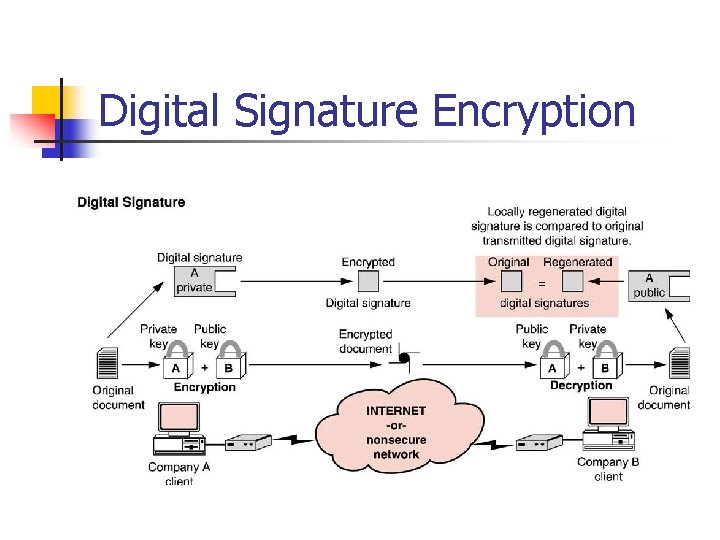
Digital Signature Encryption

Security Design Strategies n n Make sure that router operating system software has been patched Identify those information assets that are most critical to the corporation, and protect those servers first. Implement physical security constraints to hinder physical access to critical resources such as servers. Monitor system activity logs carefully

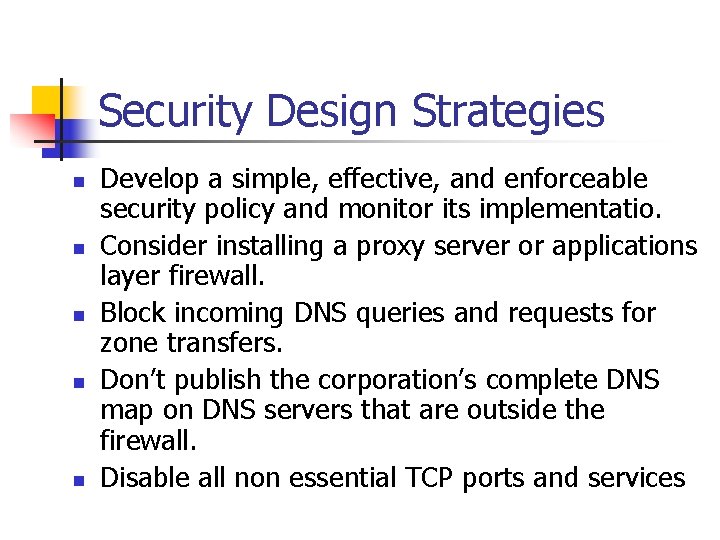
Security Design Strategies n n n Develop a simple, effective, and enforceable security policy and monitor its implementatio. Consider installing a proxy server or applications layer firewall. Block incoming DNS queries and requests for zone transfers. Don’t publish the corporation’s complete DNS map on DNS servers that are outside the firewall. Disable all non essential TCP ports and services

Security Design Strategies n n Install only software and hardware that you really need on the network. Allow only essential traffic into and out of the corporate network and elimi nate all other types by blocking with routers or firewalls. Investigate the business case for outsourcing Web hosting services so that the corporate Web server is not physically on the same network as the rest of the corporate information assets. Use routers to filter traffic by IP address.

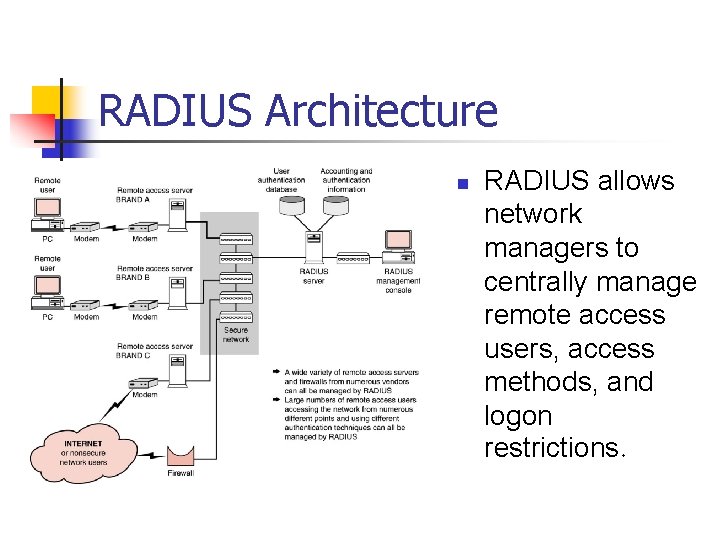
RADIUS Architecture n RADIUS allows network managers to centrally manage remote access users, access methods, and logon restrictions.

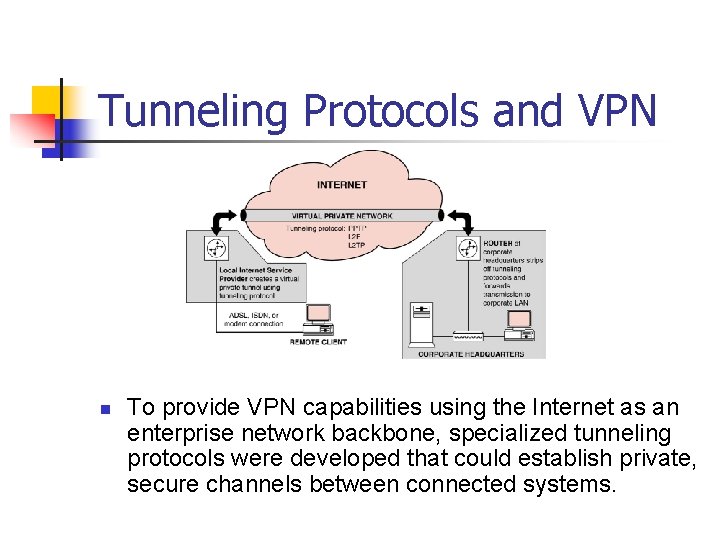
Tunneling Protocols and VPN n To provide VPN capabilities using the Internet as an enterprise network backbone, specialized tunneling protocols were developed that could establish private, secure channels between connected systems.

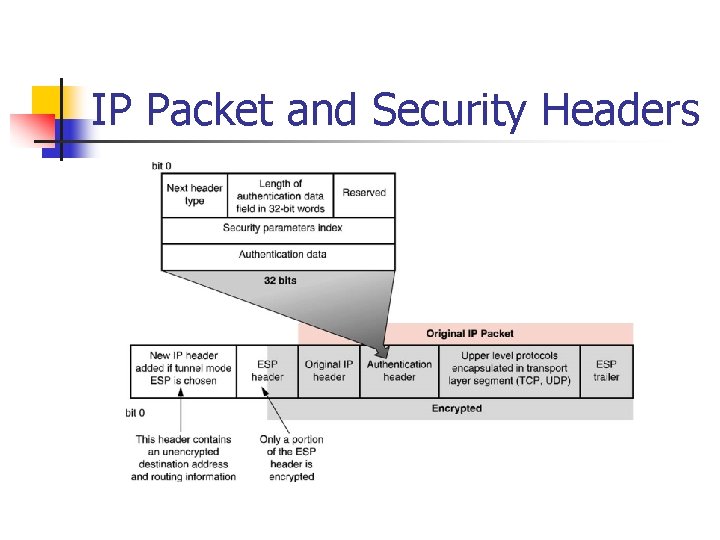
IP Packet and Security Headers

Government Impact n n Government agencies play a major role in the area of network security. The two primary functions of these various government agencies are: n n Standards making organizations that set standards for the design, implementation, and certification of security technology and systems. Regulatory agencies that control the export of security technology to a company’s international locations

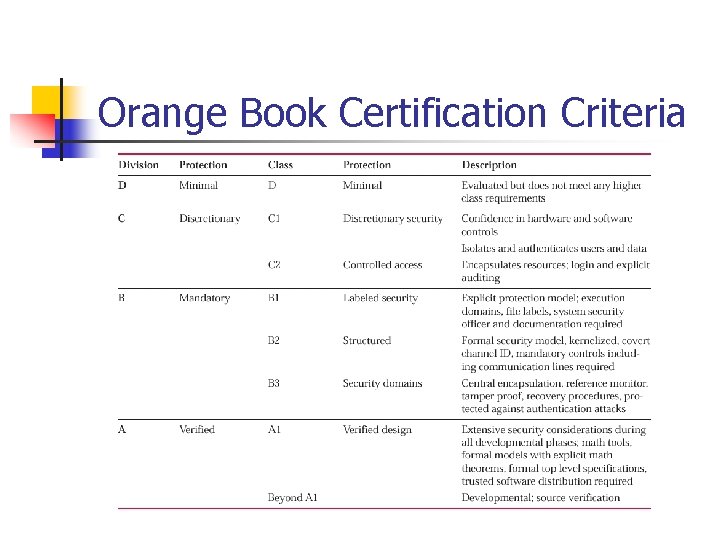
Orange Book Certification n The primary focus of the Orange Book is to provide confidential protection of sensitive information based on these requirements: n n n Security policy Marking Identification Accountability Assurance Continuous protection:

Orange Book Certification Criteria

Copyright 2004 n Copyright 2004 John Wiley & Sons, Inc. All rights reserved. Reproduction or translation of this work beyond that permitted in section 117 of the 1976 United States Copyright Act without express permission of the copyright owner is unlawful. Request for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. The purchaser may make back-up copies for his/her own use only and not for distribution or resale. The Publisher assumes no responsibility for errors, omissions, or damages caused by the use of these programs or from the use of the information herein.