INF 526 Secure Systems Administration Configuration Management Prof












































- Slides: 80

INF 526: Secure Systems Administration Configuration Management Prof. Clifford Neuman Lecture 11 29 March 2017 OHE 100 C

Class Presentation Schedule 3/29 Mariam Fahad Bubeshait - Configuration Management 4/5 Mohammed Alsubaie – SIEM and Intrusion Detection 4/12 Vishnu Vadlamani - Network Monitoring/Attack Forensics 4/19 Andrew Gronski - Accreditation and acceptance testing 1

Configuration Management A process for consistently establishing and maintaining the characteristics of the components of a system relevant for the proper functioning of a system. – Proper functioning includes: • Security • Updates and security patches. • Detection and prevention of unauthorized changes. – Components includes all system assets: • • Hardware Software Credentials Licenses – Characteristics includes: • Accounts • Settings • Polices. 2

Purpose of CM • To Maintain Consistency of a system and its attributes with a technical baseline over the systems life. • CM is part of system’s security assurance cycle. • Reduce the management workload for a collection of systems. • Reduce the attack surface of a collection of systems by reducing the differences between individual systems within the collection.

Configuration Management Example Attack Scenarios for Misconfigured Systems • An app server admin console was automatically installed and was not removed. An attacker discovered the standard admin pages and succeeded to log in with default passwords. • Directory listing is not disabled on a server. An attacker discovered she can simply list directories to find any file. • An app server with sample applications that have well known security flaws attackers can use to compromise the server. Slide by Fumiko Uehara INF 526 Students Summer 2016

Any More? Out of Date? Vulnerable Apps?

It Starts with an Inventory • Catalog of systems – What is approved for connection • Prevent access by uncatalogued systems – For each system: • • Serial Number, Tag, MACs, IPs Location, Owner, Admin Make/Model, Hardware Features Include routers, hubs, printers, other network attached items. • Purpose • Software (OS, patches, applications, etc) 16

It Starts with an Inventory • Catalog of software – What is approved for use • Detect unauthorized installs – For each system: • • • Name, Version, Patch Level Checksum License information System requirements Security considerations/implications • Anything else 16

Aspects of Configuration Management • Organizational and Process – Change Management – Admission Policy • Technical – Dependency Management – Patch Management (also organizational) • Live evaluation and detection – Admission Control – Whitelists – Change detection 16

Organization aspects of CM • Identify configuration items to be controlled – document user requirements, system design and development, software version, interface control, data flows and network diagrams, test plans and procedures, etc. – Use schema or comply with organizational policy to provide unique identifiers for each item. • Identify the level of CM to be controlled, and determine the hierarchy of each level – nature of the system, configuration items, components, etc. • Identify all baselines to be managed – user requirements, system requirements, design, development, experimentation, sustainment, etc. Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Configuration Control • Develop a process to track all configuration item changes and intrusion in appropriate baseline. • Build or provide specifications to build work products from the software configuration management system, or physical products from the hardware configuration management system. • Purchase or develop tools for version control of source code, providing version control tracking to the line of code level. Implement an engineering release system to provide hardware version control. Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Configuration Status Accounting • Publish periodic reports describing the current configuration of each configuration item. • Applies to all installed hardware, software, and other controlled assets during the entire life of the system. • The reports should include software version and details of hardware in the system and testing. Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Configuration Audits • Performing periodic verifications of operational baselines for completeness. • Assure that both functional and physical configuration meets the requirements. • Tools, scripts or logs can be used when a change has occurred in a configuration. Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Technical Aspects of CM • Dependency Managers – Linux package managers • Patch Management – Software update options – Software update center (linux) – Windows updates – App Stores • Special Tools – Secuinia, others (later) • New attack vectors – When to update 16

Tools: CM, evaluation and detection • Live evaluation and detection – Admission Control – Whitelists – Change detection 16

Automated Tools: Ansible • Free software developed by Red Hat • Written in Python, can run on multiple platforms • Use Playbook written in YAML to perform tasks • Use SSH to communicate from the management machine. • Target servers do not need to install agent files Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Automated Tools: Ansible • Example of tasks and handlers – Install Word. Press configuration file, and restart httpd tasks: - name: install Word. Press configuration file template: src=wordpress. conf dest=/etc/httpd/conf. d/wordpress. conf notify: - restart httpd handlers: - name: restart httpd service: name=httpd state=restarted Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Some other Tools • Chef – Written in Ruby, can be easily customized. – Can run on multiple platforms. • Puppet – Written in Ruby. – Can run on multiple platforms. – for large scale systems • CFEngine – Can run on multiple platforms. – Describe the final state in which one wants to end up. The agent then ensures that the necessary steps are taken to end up. • Microsoft Power. Shell DSC – Standard since Power. Shell 5. 0 (Windows 8. 1), desired scale configuration Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Automated Tools Detection: Tripwire • Open source and enterprise developed by Tripwire, Inc. – Two versions, Open Source Version is not mainained or upgraded • Detect changes to file system objects • When first initialized, scans the file system and stores information in a database. Later, the same files are scanned and the results compared against the stored values in the database. Changes are reported to the user by emails. Slide by Fumiko Uehara INF 526 Students Summer 2016 16

File Integrity Monitoring • Act of validating the integrity of operating system and application software files • Calculate file signatures (Hash values) and compare it to baseline • Should be performed periodically Slide by Fumiko Uehara INF 526 Students Summer 2016 16

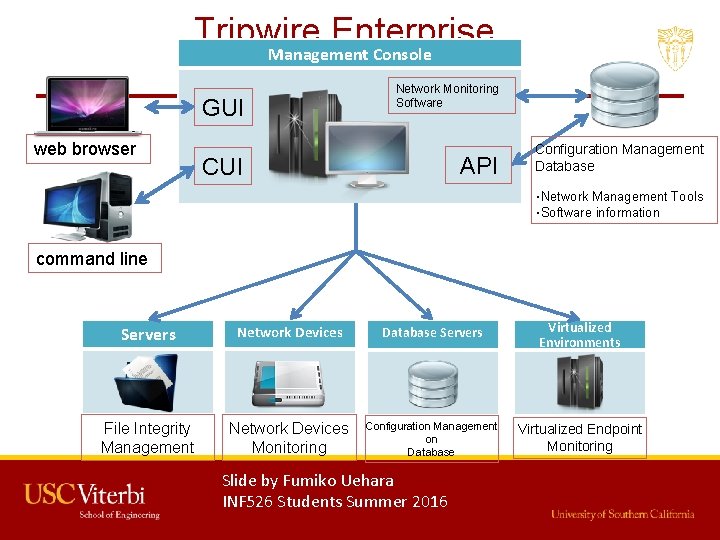
Tripwire Enterprise Management Console GUI web browser Network Monitoring Software API CUI Configuration Management Database ・Network Management Tools ・Software information command line Servers Network Devices Database Servers Virtualized Environments File Integrity Management Network Devices Monitoring Configuration Management on Database Virtualized Endpoint Monitoring Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Open Source Integrity Tools • Tripwire (some versions) – runs on Linux • AFICK – Another File Integrity Chec. Ker – Perl based, deployment on Windows, Linux, Unix, Solaris. • AIDE – Advanced Intrusion Detection Environment – runs on Linux Slide by Fumiko Uehara INF 526 Students Summer 2016 16

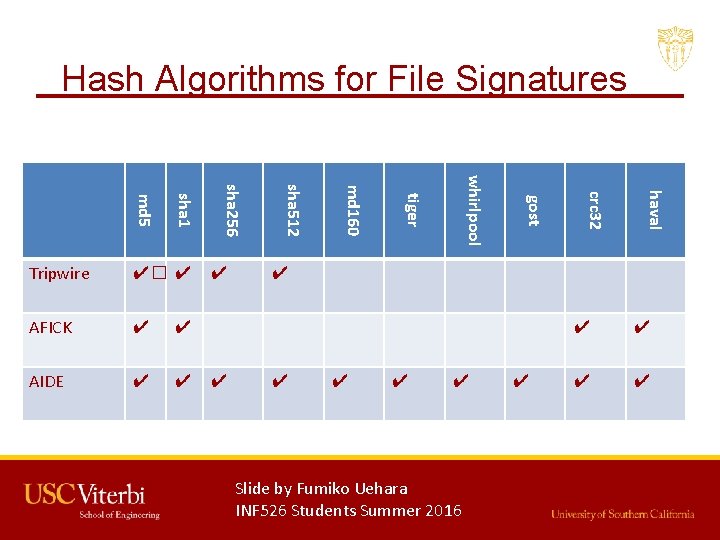
Hash Algorithms for File Signatures ✔ haval ✔ crc 32 ✔ gost AIDE whirlpool ✔ tiger ✔ md 160 AFICK ✔ sha 512 ✔� ✔ sha 256 sha 1 md 5 Tripwire ✔ ✔ ✔ Slide by Fumiko Uehara INF 526 Students Summer 2016 ✔ ✔ ✔ 16

File Signature Bypass Issues • Default MD 5 signature can be bypassed by tools. • Having a wide variety of simultaneous cryptographic generation algorithms can help to detect evasion through signature weaknesses. Slide by Fumiko Uehara INF 526 Students Summer 2016 16

How was detected change caused • Tripwire, AFICK and AIDE note that something has happened – Modified? Executed? • Need correlation with other logs ※Enterprise version does Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Protecting the Tools • Tripwire – Require two passphrases longer than eight characters • AFICK – Calculate MD 5 signature of itself right after the first installation – Can boot from CDROM • AIDE – Signed and stored in the Ubuntu repository, automatically verified during the download and installation Slide by Fumiko Uehara INF 526 Students Summer 2016 16

Placement of CM Functions • Central to the Enterprise • On each system • In the Network • On storage or other servers • Relationship to SIEM 16

Minimization in CM • Create a few standard configurations – Fewer different systems to configure and possibly get wrong. • Automate the configuration of machines within groups. – So that you don’t leave one out of the update cycle 16

Push vs Pull • Most end user systems pull updates – Windows updates – Linux software updater • Much server infrastructure changes based on a push model. – Ansible (red hat) 16

Configuration Management Mariam Bubshait

Resources Secure Provisioning Provision: to setup or supply credentials or other access to resources Systems users and controls should be properly provisioned before they are allowed to connect to your system It is important that you: § Configure your resources on your network to support a specific function § Establish a known secure baseline for your devices/systems per your security policies § Make sure that systems are up to a specific level of security required before allowing them to connect to your systems § Test the system to verify that they consistently function properly and Make sure that your security controls are working to keep out unauthorized individuals § § monitor unauthorized changes on your network or specific systems If change is needed, follow a structured approach using configuration management (CM)

Configuration Management (CM) Definition: CM refers to the process of systematically handling changes to a system in a way that it maintains integrity over time. Configuration Management can mean: § how your network devices are configured § what version of application you are running § what was the last patch installed on your device/system § baselines hardware and applications that run on your devices/systems

Why configuration management Mass deployment and fast provisioning: CM tools automate the deployment efficiently and quickly Faster recovery from critical events: a CM tool should roll back the application automatically to a stable version in case of failure. Elimination of snowflake servers: By using a configuration management tool, the procedure necessary for bringing up a new server or updating an existing one will be all documented in the provisioning scripts Replicated environment

Basic Configuration Management (CM) comprises a collection of activities focused on establishing and maintaining the integrity of products and systems, through control of the processes for initializing, changing, and monitoring the configurations of those products and systems. A Configuration Item (CI) is an identifiable part of a system (e. g. , hardware, software, firmware, documentation, or a combination thereof) that is a discrete target of configuration control processes. A Baseline Configuration is a set of specifications for a system, or CI within a system, that has been formally reviewed and agreed on at a given point in time, and which can be changed only through change control procedures. The baseline configuration is used as a basis for future builds, releases, and/or changes. A Configuration Management Plan (CM Plan) is a comprehensive description of the roles, responsibilities, policies, and procedures that apply when managing the configuration of products and systems.

Security Configuration Management (SCM) The configuration of an information system and its components has a direct impact on the security posture of the system Changes to the configuration of an information system are often needed to stay up to date with changing business functions and services, and information security needs These changes can adversely impact the previously established security posture Security-Focused Configuration Management (SCM) is the management and control of secure configurations for an information system to enable security and facilitate the management of risk. SCM builds on the general concepts, processes, and activities of configuration management by attention on the implementation and maintenance of the established security requirements of the organization and information systems.

Security Configuration Management (SCM) Roles identification and recording of configurations that impact the security posture of the information system and the organization the consideration of security risks in approving the initial configuration the analysis of security implications of changes to the information system configuration documentation of the approved/implemented changes. As changes to information systems are made, baseline configurations are updated, specific configuration settings confirmed, and configuration items tracked, verified, and reported

Configuration Change Management It is the documented process for managing and controlling changes to the configuration of an information system or its constituent CIs. It involves: § systematic proposal § Justification § Implementation § test/evaluation § Review § disposition of changes to the system, including upgrades and modifications. Ø Configuration change control is applied to include changes to components of the information system, changes to the configuration settings for information technology products, emergency/unscheduled changes, and changes to remediate flaws. Ø Changes are controlled from the time the change is proposed to the implementation and testing of the change Ø The emphasis here is put on the management of change to maintain the secure, approved baseline of the information system

Tools: Salt. Stack is a Python-based open-source configuration management software and remote execution engine it supports Linux and Windows platforms Configuration management system called Salt States Salt functions on a master/minion topology. A master server acts as a central control bus for the clients, which are called minions. The minions connect back to the master. It also can run in a standalone mode provides configuration management functions by automating the packaging and provisioning of code into an organization's operational IT environment Salt. Stack is written in Python so It can use scripts written directly in Python, or can render other scripts, such as those written in YAML or JSON, through the use of the Py. DSL Salt renderer Salt is capable of storing configuration directives, and then instructing other machines to follow those directives by doing things like installing software, making configuration changes to the software, and then reporting back on the progress and success or failures of the installation.

Salt. Stack CM scenario: installing LAMP stack on Red Hat Salt. Stack formulas and states can be used for tasks such as installing a package, configuring and starting a service, setting up users or permissions, and many other common tasks. set up an Apache web server, and a My. SQL database server for the web application to use. define the database server first # /srv/salt/mysql. sls mysql: pkg. installed: - name: mysql-server service. running: - enable: True - require: - pkg: mysql-server Because this example does not include any files other than the declaration, we can store it simply as /srv/salt/mysql. sls

Salt. Stack CM scenario: installing LAMP stack on Red Hat the Apache installation is more complex, because it includes a configuration file. It is copied up to the web server using file. managed function , which supports enhanced functionality such as templating. To accommodate this, we create an apache/ directory inside of /srv/salt/ # /srv/salt/apache/init. sls httpd: pkg. installed: - name: httpd - file: httpd service. running: - enable: True - require: - pkg: httpd file. managed: - name: /etc/conf/httpd. conf - source: salt: //httpd. conf - require: - pkg: httpd

Salt. Stack CM scenario: installing LAMP stack on Red Hat # /srv/salt/top. sls base: web*: - apache db*: - mysql This definition will ensure that any servers whose names start with “web” (such as web 01 or even web 01. example. com) will have the Apache state applied to them and any servers whose names start with “db” (such as db 01 or db 01. example. com) will have the My. SQL state applied to them. To apply these states to all servers: salt ‘*’ state. highstate A highstate is the combination of state data (packages, services, files, etc. ) that will be applied to the target system

Salt. Stack: Addressing configuration drift if the httpd. conf file gets changed on the server, Salt. Stack will set it right back where it needs to be, and report to the user what changes were made to enforce the correct state. But what about package versions? When a pkg. installed state is declared, Salt. Stack will check with the underlying package manager to see if that package is already installed. If it is, then the state has been achieved, and no further action is performed. if it is not installed, it will tell the package manager to install that package, which will normally search for the latest available version of that package and install that.

Salt. Stack: Addressing configuration drift Problem: this can result in a number of servers containing different versions of a package, which can result in issues that can be difficult to troubleshoot. Solution: set the pkg. latest state instead, to always make sure that all servers are always running the latest version of a package: httpd: pkg. latest: - name: httpd New problem: As soon as a new version is made available, all of the servers will try to download and install it. If you’re not expecting a new version, or you haven’t had time to perform your own internal testing. Solution: lock down packages to a specific version: httpd: pkg. installed: - name: httpd - version: 2. 2. 15 This ensures that packages will not be upgraded until the state declaration has been explicitly updated to do so.

Tools: Secunia CSI is a Windows based Vulnerability and Patch Management Software Solution that completes and targets the Patch Management process. It combines Vulnerability Intelligence, Vulnerability Scanning, and Patch Creation with Patch Deployment Tool Integration collect specific metadata from primarily. EXE, . DLL, and. OCX files on the system being scanned. This data is collected and then sent to Secunia's Secure Data Processing Cloud where it is processed and parsed. The data is then matched against Secunia File Signatures, metadata to an actual product installation. This matching process results in an exact version extracted from metadata The inventory of software is then compared against the unique Secunia Advisory and Vulnerability Database

Tools: Secunia CSI The result is a precise inventory of products, their versions, the security state of each, and a detailing of vulnerabilities and their criticality and impact. Assess scanning result and patch using WSUS and SCCM

THANK YOU Questions?

Presentations of Project 1 • It is time to wrap up exercise - each group has prepare a report describing: – User documentation for their application (high level) – Their network and server architecture (what servers are on what VM’s and how they are interconnected) – A risk assessment/vulnerability analysis enumerating the risks, explaining the mitigation of those risks, and listing those threats that are not defended against (i. e. where you accept the risks). – A description of the steps taken for pen testing of your system. • We will use 40 minutes of this weeks lecture to demonstrate the operation of your systems. – Once I have seen the normal operation of the systems, I will plan a session in a future week in which we will try additional pen-testing. 46

INF 526: Secure Systems Administration Banking System – Group 1 Abdullah Binkulaib Edward Guerrerobognoli Jikun Li Dan Dmytrisin Myles Wright-Walker Ankit Srivastav

System Overview

System Data Classes • Public – Information openly available through website • Account holder - personal information, which includes name, account number, email address, DOB, mobile number and legal documents’ numbers • Account balances - information including current balance, transaction history, recipients’ names and account numbers, and saved bills • Corporate information - employee records, employee access controls, corporate policies • Vendor information - including all data about vendors and data that handled by third parties • Highly Sensitive - bank instrument information, shareholder information, total assets maintained by institution, contracts and agreements 49

System User Classes • • Network Administrator - has overall access to the backend systems to install and configure. Does not have direct access to user accounts. External vendors – hardware or software vendors that have components within the banking system. Account holders - have active accounts with the bank, able to access accounts from web or mobile platforms. They are able to update some personal information, balances, transfer funds, deposits and withdrawals and pay bills. Bank Manager - Oversee transactions above a certain threshold, monitor transactions and oversee daily balances. Branch tellers and customer services representatives – handle services that have been asked in person and that includes cash deposit, cash withdrawal, open a new account, and other services. Potential customers – General web users browsing website exploring for information about products and services offered. Other Banking institutes – credit card companies, other banking institutions. 50

Protection Domains • Public – Isolated systems that are front facing and are faced to higher exposure. These areas have external data flows with no access to internal networks • DMZ Zone – Creates an isolated boundary for front facing systems that have high expose to unsecured networks. These systems have controlled and isolated communications with internal systems. • Internal Banking System – Protected systems within the internal banking infrastructure. This network is protected from external access, and access is highly controlled in terms of whom has access and where systems are accessible from. 51

System Hardware and Software System Hardware System Software • • • • End user devices Firewall/ Router Network Switches Servers Cloud infrastructure ATM’s Banking system portal Webserver Email DNS Database Intrusion Detection and Intrusion Prevention Behavior and user analytics Anti-Virus/ Anti-Malware Audit handling End user device operating systems 52

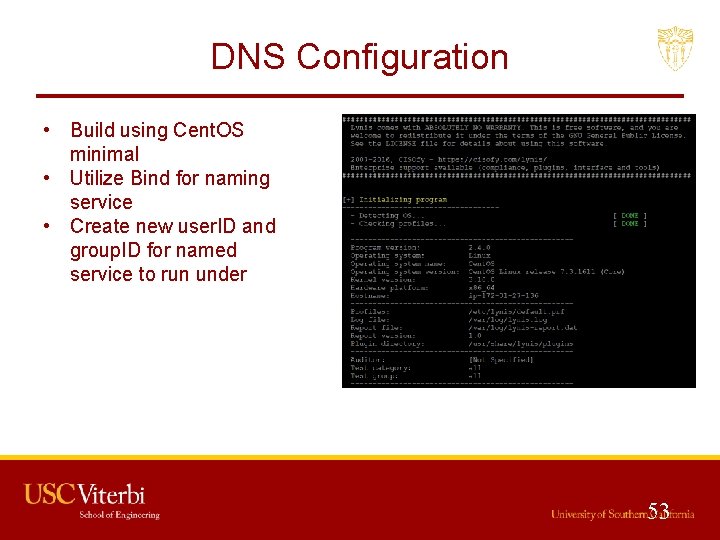
DNS Configuration • Build using Cent. OS minimal • Utilize Bind for naming service • Create new user. ID and group. ID for named service to run under 53

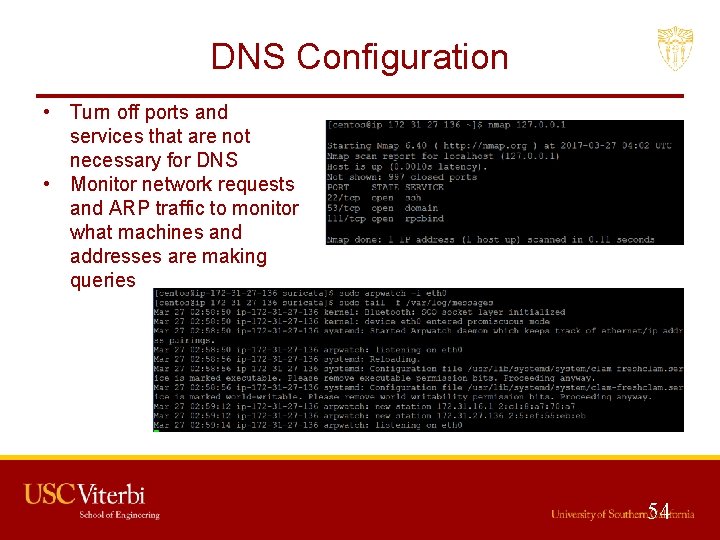
DNS Configuration • Turn off ports and services that are not necessary for DNS • Monitor network requests and ARP traffic to monitor what machines and addresses are making queries 54

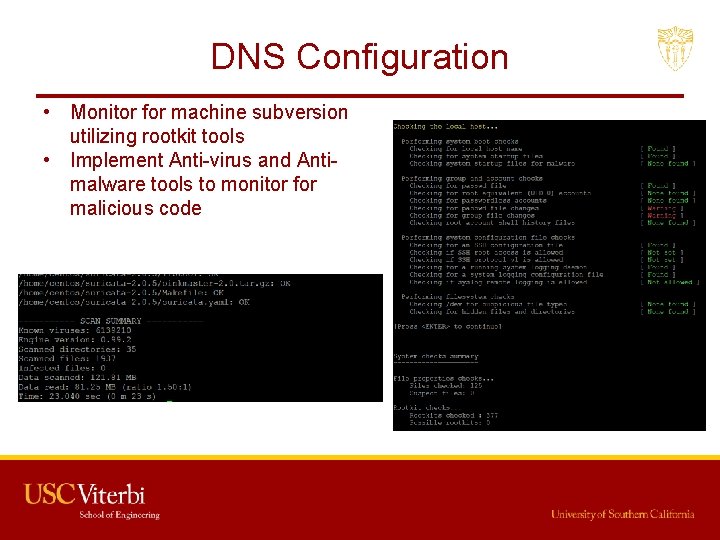
DNS Configuration • Monitor for machine subversion utilizing rootkit tools • Implement Anti-virus and Antimalware tools to monitor for malicious code

Firewall • The firewall serves as a frontend protection layer to the whole banking system. All the traffic headed to the web server will first go through the firewall. For security reasons, we have created a set of rules and properties which will dictate the route for the incoming traffic. We will now discuss the setup and operation of the firewall.

Firewall ● ● ● To setup a firewall, we have used pfsense, an open source firewall featuring load balancing, unified threat management, mulit-wan and many more. We have setup a pfsense vm which will act as a firewall/router and then we have setup a centos 7 vm to access the firewall page and configure it. In the pfsense vm, we have created two network – one for the external using bridged adapter and the other one as internal network named intnet. The whole system will be running on the intnet network.

Firewall ● ● Two interfaces are being used – em 0 for wan with address range 192. 168. 1. 1/29 with dhcp and static arp and em 1 for lan with address range 172. 168. 1. 1/29. The centos vm was configured with only an internal network – intnet, from where it can reach the firewall host page, where we can setup the rules and properties of the firewall. In the centos 7 vm, we have setup two firewall rules – server_pass : which will only allow packets to go through server after inspection and reject_all : all the other packets which are not going to server will be rejected. Each VM, i. e Web Server, Database and DNS have been assigned a static lan address, making it easier for detection and authentication.

Firewall ● ● A port rule : serve_port has been established to open certain ports solely for interacting with the web server and all the remainings are closed. A seperate rule is established fail_safe with a dedicated port and address which can be used to access and reconfigure the firewall if the actual system is not functioning.

Web Server • The web server was first installed on a local machine running Cent. OS 7 (minimal). • In order to have all VM’s in a one environment to have them communicate to each other, Amazon Web Services was suggested to use. • AWS offers launching instances where they have public and private IP’s; so the web server is finally installed on a AWS instance that running AMI. • The web server was running Apache 2. 4. 6 (Cent. OS), and now is running Apache/2. 4. 25 (Amazon).

Web Server • The normal operation of the system: – A login page will serve the authentication of the user. – After valid credential, the user is able to perform services as the functional requirements. – The dashboard serves the user with quick access to the services and shows the transactions history.

Web Server – Update Info. • Assumption: – For security purpose, no immediate information updating is available. Therefore, when updating personal information, the client will send the request and changes will be in pending situation until the information approved by the designated department.

Web server – Check Balance/Transfer • Check Account Balance: – basically shows the current available balance in the account. • Transfer funds: Assumption: – The user will be able to transfer limited funds (as stated in the security policy section) to another account by account number and within the sane bank. – The transfer could be immediate transfer or deferred transfer. (using the transfer date field)

Web server – Check deposit Assumption: • The system will ask the user for the amount and the account number where the check will be deposited to, and then accepts two images for the front and the back of the check and store them in the user’s account. Then, the designated employee will review and validate this deposit if all information matched. (no image processing is involved)

Web server – Authorization/Cookies • Authorization Run Apache from non-privileged account – Use a separate non-privileged user for Apache to protect other services running in case of any security hole. • Cookies Disable Trace HTTP Request – By default Trace method is enabled in Apache. Having this enabled can allow Cross Site Tracing attack and potentially giving an option to a hacker to steal cookie information. Let’s see how it looks like in default configuration.

Web server – SSL • Enable SSL/TLS on the Server (in my case, with a self-signed digital certificate): – A self-signed SSL/TLS X. 509 certificate is cryptologically identical to a CA-signed certificate. “The difference is social, not mathematical” – Create a stronger key with a 4096 bit RSA private key. – Password protection for the RSA key; this results in a 4096 -bit RSA private key that has been encrypted with the AES-128 cipher.

Web server – SSL • Disable SSL version 2 and 3: – The POODLE attack, discovered in 2014, exploits a weakness in SSL version 3 that allows an attacker to impersonate (Man-in-The-Middle attack) a web site. Therefore, the server should disable support SSL version 2 and 3.

Web Server – SSL • Disable RC 4 cipher support: – RC 4, a fast cipher used to encrypt SSL/TLS data-streams, is known to have several serious weaknesses. The fix is to disable RC 4 support in ssl. conf

Email • SASL – Simple Authentication and Security Layer (SASL) is a framework for authentication and data security in Internet protocols. It decouples authentication mechanisms from application protocols, in theory allowing any authentication mechanism supported by SASL to be used in any application protocol that uses SASL. 69


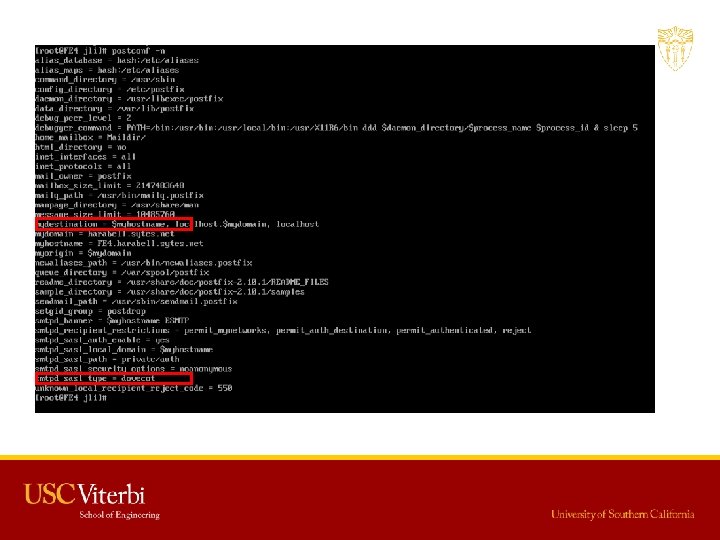
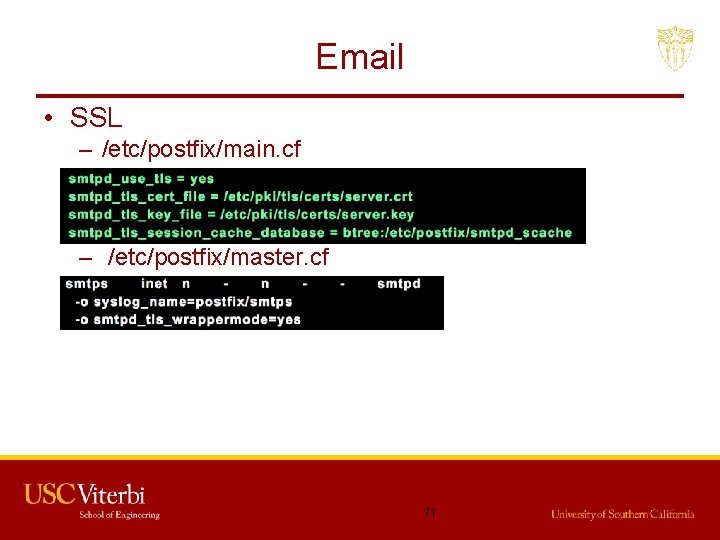
Email • SSL – /etc/postfix/main. cf – /etc/postfix/master. cf 71

Database • Secure My. SQL installation – Improved secure installation method • Consists of two databases – Bank Account Information - Confidential – User Account Information - Confidential • AES 128 -bit encryption on databases • Webserver account used to check against table with user accounts • Stores images on another table

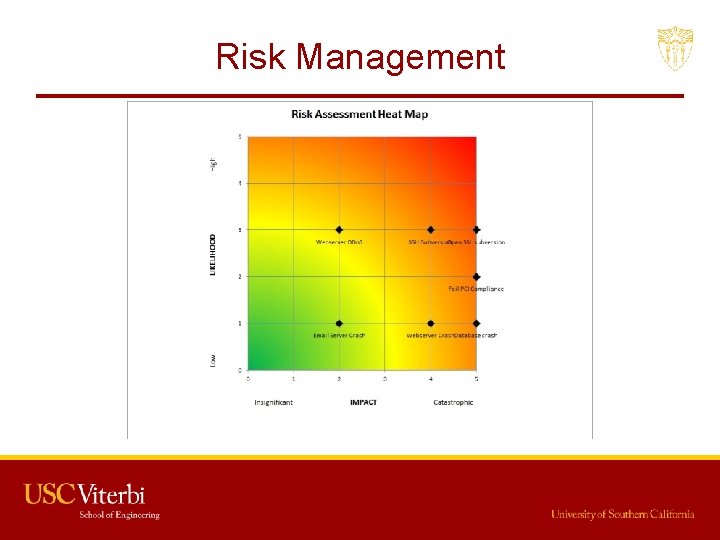
Risk Management • Greatest risks involve the backend collapsing or failing to meet regulations that may shut the business down • Risks involving the front end still exist • Solutions to preventing back end compromise – Redundancy – Regular compliance checking – Patching • Solutions to prevent front end compromise – Load Balancing – Patching

Risk Management

Vulnerability Management/Pen Test • Nessus scans were initiated on all nodes to identify vulnerabilities • Nmap scans were initiated on all nodes to identify open ports • Next steps would involve patching, and documenting ports that are open – Need to justify the need for having open ports

Thank you. .

Second Exercise - Criminal Enterprises • Chosen because of differences in the high level principles. – Not because I expect you to implement these kinds of systems in your future endeavors. – But you may be called upon to break some of these systems if later employed by government organizations. • Your organization must: – – – Accept Bitcoin as payment (not really, but it must accept something that stands in for bitcoin) Manage an inventory of stolen account identifiers with passwords Control access to such information Prevent collection of evidence or intelligence by third parties. Note, do not deal in any illegal goods, but use dummy information to stand in for such goods. Also, do not use terms associated with such illegals goods or information in communications, make up new names for this dummy information. 77

Initial Homework Assignment (due before 3/29 class) • Submit as email to inf 526@csclass. info • System Structure for Criminal Enterprise Case Study • Consider the description of the system to be used for the fsecond exercise – as discussed in previous slide. – – – Enumerate the classes of data Enumerate the classes of users Identify the protection domains Enumerate the systems (hardware) Enumerate the systems (software components) • This write-up is expected to be about 3 pages in length (could be more or less) – It will be shared later with your group members to begin discussion for the group architecture. 78

Teams for Second Exercise • Group A – Enrolled: Srivastav, Binkulaib, Dmytrisin, Alsubaie, Bubshait, Gronski – Advisors: haiboz, jaskaran, rajattan • Group B – Enrolled: Guerrerobognoli, Li, Wright-Walker, Jackoski, Vadlamani, Zhang – Advisors: sajmani, slakkadi, tosirisu, wang 907 79