INF 526 Secure Systems Administration Network Monitoring And


































- Slides: 53

INF 526: Secure Systems Administration Network Monitoring And Attack Forensics Prof. Clifford Neuman Lecture 13 12 April 2017 OHE 100 C

Announcements Our scheduled meeting on April 26 th (the last lecture in the semester) will be moved to an alternative date. In that lecture we will review for the final exam. We will also have groups on the criminal enterprise scenario demonstrate their systems and report on their architectures. We will also red-team the servers for each group. Depending on DEN classroom scheduling, I may split the two parts, so that we can record the final exam review, and choose a time that is more convenient to students for the demonstration. 1

Todays Lecture A student presentation on Network Monitoring and Attack Forensics, expanding upon the material presented last week. Discussion of SIEM and its relationship to newer ID systems. Discussion of individual responses to the group project architecture (last weeks assignment). 2

Class Presentation Schedule 4/12 Vishnu Vadlamani - Network Monitoring/Attack Forensics 4/19 Andrew Gronski - Accreditation and acceptance testing 3

INF 526: Secure Systems Administration Student Presentation Network Monitoring and Forensics Vishnu Sarma V Lecture 1 11 January 2017 OHE 100 C

What do we knew ? • Network Monitoring – It helps us to ensure the availability is maintained. – It helps us to ensure Non-Repudiation by telling us: who did what, and when. – It also gives us a bigger picture on what is happening in the network and helps us ensure other principles too. – It gives us options of inspecting at different level of granularity. It has close relationship with Intrusion Detection and Forensics. 5

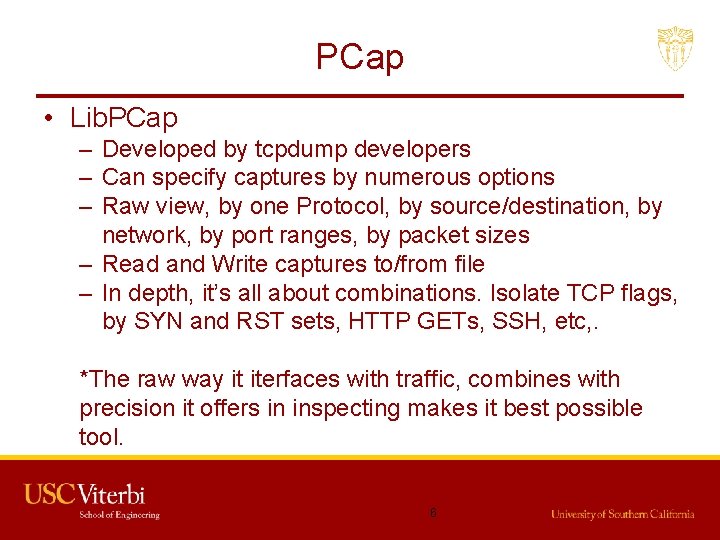
PCap • Lib. PCap – Developed by tcpdump developers – Can specify captures by numerous options – Raw view, by one Protocol, by source/destination, by network, by port ranges, by packet sizes – Read and Write captures to/from file – In depth, it’s all about combinations. Isolate TCP flags, by SYN and RST sets, HTTP GETs, SSH, etc, . *The raw way it iterfaces with traffic, combines with precision it offers in inspecting makes it best possible tool. 6

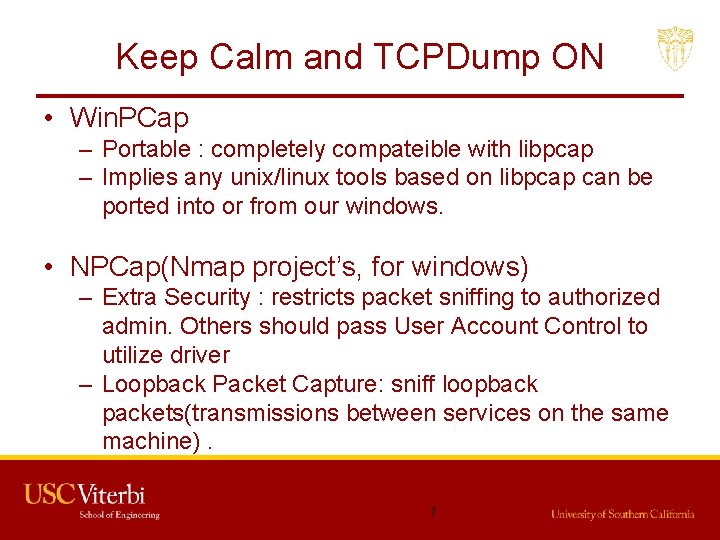
Keep Calm and TCPDump ON • Win. PCap – Portable : completely compateible with libpcap – Implies any unix/linux tools based on libpcap can be ported into or from our windows. • NPCap(Nmap project’s, for windows) – Extra Security : restricts packet sniffing to authorized admin. Others should pass User Account Control to utilize driver – Loopback Packet Capture: sniff loopback packets(transmissions between services on the same machine). 7

NTAR • Network Trace Archival and Retrieval library. • New file format especially targeted to the percapture and per-packet details. • Main idea is to overcome the limits of current libpcap/winpcap dump format. Other purposes are: Extensibility, Portability. * Under development. 8

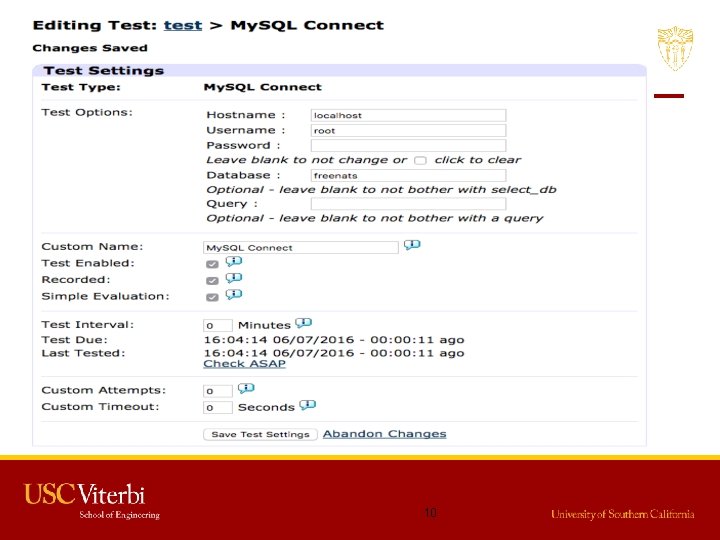
Free. NATS by David Cutting • Free Network Automatic Testing System • Monitoring and reporting system with a wide range of test types, reporting/alerting options, publishable views, SLA reporting and more. • Web – Time to connect, connection status, size of response. • Protocol-based(SMTP, IMAP, My. SQL, DNS, . . ) • Remote monitoring and testing. (pull or push) • Extensible – Can add more tests by extending Free. NATS_Local_Test class. (PHP based) 9

10

• www. purplepixie. org/freenats/ 11

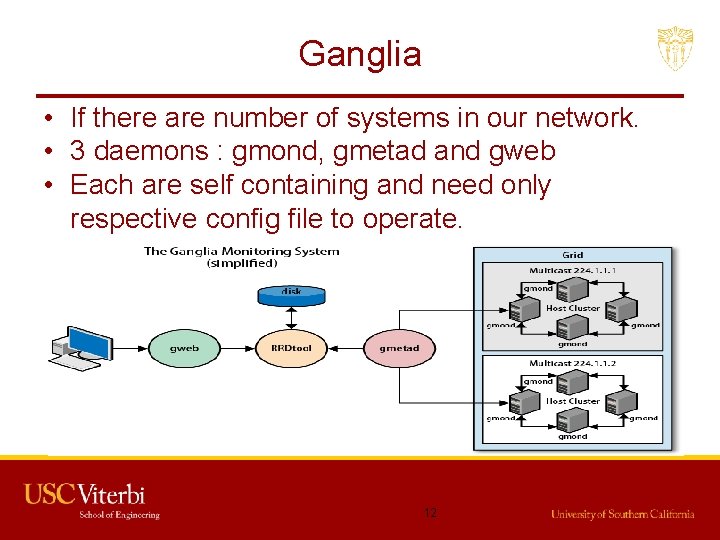
Ganglia • If there are number of systems in our network. • 3 daemons : gmond, gmetad and gweb • Each are self containing and need only respective config file to operate. 12

Ganglia • Gmond: Big bang in a few bytes. – Operates on it’s own host. – XML format dumps in transmission (port 8649) 13

Ganglia • Gmetad : Bringing it all together – Architecture allows to completely removing the need for the poller to know what services to poll from which hosts. – Needs a list of hostnames(atleast host per cluster) – Cluster will then inform the poller as to what metrics are available and will provide corresponding values. – Many shell scripts readily available to collect XML dumps, parse them and write them to RRDtool. – Python replacable for gmetad for plug-in architecture making it easier to write custom data-handling logic. 14

Ganglia • Gweb: Next-Gen Data Analysis – Visualization UI – Supports click-dragging in graphs to change time period – Fully functional URL interface, so you can embed graphs into other programs via predictable URLs. – Data in various textual formats (CSV, JSON, and more) Open source project grew out of UCB and can hanle clusters with 2000 nodes. 15

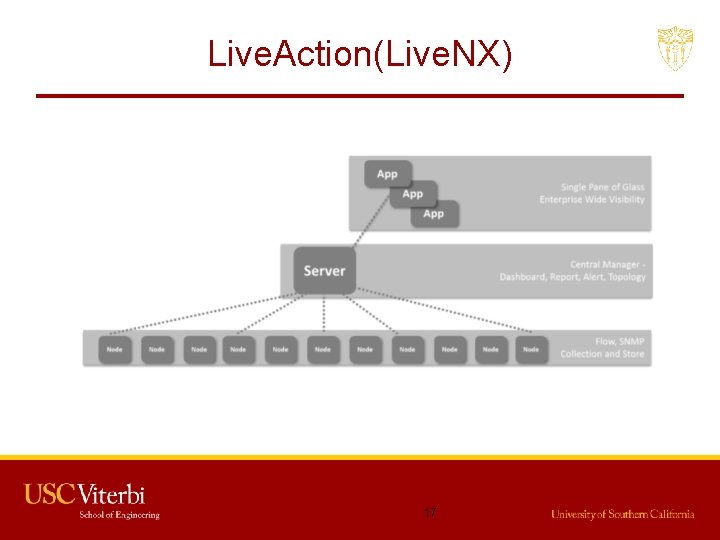
Live. Action(Live. NX) • Combines network topology, device and flow visualizations • Direct interactive monitoring and configuration of Qo. S, Net. Flow, LAN, Routing and other features inside Cisco Systems. • 3 -tier architecture • Nodes will initiate communication from security zone to server, In case of loss of communication, server of that particular node may initiate. • Visualization, decision making, control, Improve 16

Live. Action(Live. NX) 17

Give them a visit • https: //www. slac. stanford. edu/xorg/nmtftools. html • https: //en. wikipedia. org/wiki/Comparison_of_net work_monitoring_systems#Legend 18

SCAPY • Very powerful interactive packet manipulation program. • Decode packets, send them on wire, capture them, match requests and results. • Can replace hping, 85% of nmap, arpspoof, arpsk, arping, tcpdump, p 0 f and many more. • What makes it different ? Because its your own tool. • Probe once and interpret many times. • http: //www. secdev. org/projects/scapy/ 19

I Know What You Surfed Last Weekend • Network Forensics – Different from Host-Based Forensics. – Poses special challenges in several areas including: • Acquisition : difficult to locate specific evidence – from wireless access points to web proxies to central log servers • Content : Unlike filesystems, lack of granularity desired • Storage : Commonly, Network devices don’t employ secondary or persistent storage. Very much volatile that sometimes might not survive a reset of device. • Privacy : There may be legal issues involving privacy that are unique to network based acquisition techniques. 20

OSCAR • Network Forensics Investigative Methodology – – – Obtain Information Strategize Collect evidence Analyze Report • Obtaining information on incident, environment, legal issues, Time frame, Goals, etc, . • It is especially important to Strategize in network forensics. 21

OSCAR • Collect evidence as soon as possible and make the cryptographically verifiable copies. • Analyze only the copies with tools that are reputable and reliable. • Don’t ever forget to document everything you do! 22

OSCAR • Forensic investigation can passively acquire network traffic by intercepting it as it is transmitted across cables or through equipment such as hubs and switches. • BPF (Berkeley Packet Filter Language) • Can be impacted by hardware limitations and configuration constraints. • Trivial protocols, web and proprietary Interfaces, port scanning, vulnerability scanning. 23

Case Study • Mr. X remotely infiltrates a facility lab network over internet. • Environment : Facility is instrumented to capture flow and record data. Staff notices a port scanning from expternal IP(Ip address and timestamp noted) • Challenge : Identify any compromised systems, Determine what attacker found, evaluate risk of data exfiltration. 24

Case Study • Now, we get the information on network architecture in Obtaining information phase as : – Facility has • Internal network (192. 168. 30. 0/24) • DMZ : (10. 30. 0/24) • The Internet. (let’s assume one of our submets as the internet. 172. 30. 1. 0/24) 25

Case Study • Assuming out facility uses Cisco equipment, corresponding softwares and services – We obtain cisco-asa-nfcapd. zip – A zip archive containing flow records from the perimeter Cisco ASA, stored by the nfdump collector utility (nfcapd) in 5 minute increments. – Also, argus-collector. ra- An Argus archive containing flow record data collected from Internal and DMZ subnets. 26

Case Study • As, we have an IP address of attacker say 172. 30. 1. 77 – We browse the archive dump filtering with IP. – We might find a pattern, that attacker has performed a quick port scan on one of system(server). – Using same nfdump we might also find the ports that are open and our attacker might successfully connected to. (let’s say TCP port 22) – Port 22 are SSH usually targeted for password brute force attacks. 27

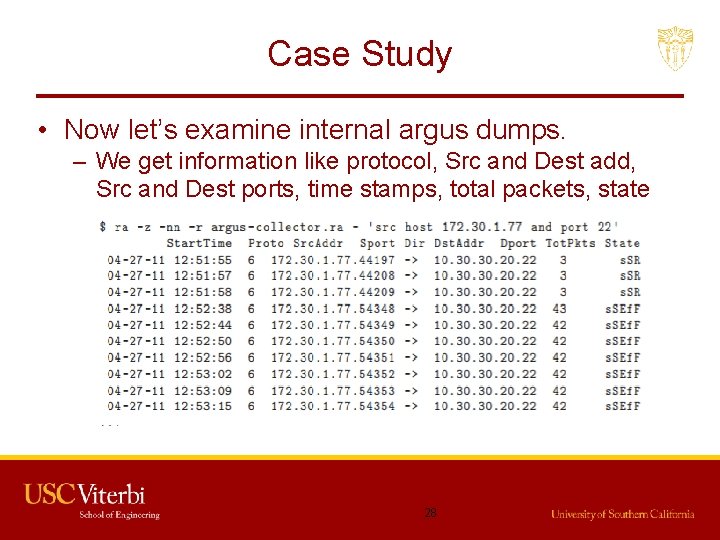
Case Study • Now let’s examine internal argus dumps. – We get information like protocol, Src and Dest add, Src and Dest ports, time stamps, total packets, state 28

Case Study • Legend for state(Man ra) • From this we can see that attacker first initiated a connection to 10. 30. 20: 22 three times. – Sent a TCP SYN, receiver SYN-ACK, sent a RST – Now attacker nows port is open 29

Case Study – Now we see that attacker has successfully finished a TCP handshake. – And then say we saw a ful TCP connection established with no FIN packets for a longer period of times. – Consider graph reports of data flow at respective timeline to know the risk of exfiltration. Make sure the checks continue from our DMZ server to any internal servers or machines in a similar fashion. – Make sure to document the timeline of the attacker performing different actions throughout his attack. 30

Tools • • • • Bin. Walk Bulk-extractor Capstone Chntpw Cuckoo Dc 3 dd Ddrescue DFF di. Strom 3 Dumpzilla Extundelete Foremost Galleta Guymager P 0 f Volatility and Xplico • • FTK The Sleuth. Kit IDA Encase Snort Bro Wire. Shark Crypt. Cat 31

IDA pro • Multi-platform hosted interactive, programmable, multi-processor disassembler and debugger augmented by a complete plugin programming environment. • Reverse Engineering : In hacking this would enable us to use a known signature and build unknown signature with same capabilities. • Key Features Like, Sony Hack to North Korea. – Hostile code Analysis – Vulnerability Research – Privacy Protection 32

Any Combinations • So Not just mentioned tools or specific tools forensics and monitoring. • Any combination of tools with corresponding functionalities can form a powerful Forensic toolkit. • Even Be. EF like frameworks are used in correspondence with network monitoring in forensic analysis. 33

Thank You Questions ? 34

References • http: //cryptcat. sourceforge. net/ • http: //nc 110. sourceforge. net/ - netcat • https: //sharkfest. wireshark. org/sharkfest. 12/presentations/MB 7_Network_Forensics_Analysis-A_Hands-on_Look. pdf • https: //news. asis. io/sites/default/files/Network%20 Forensics%20201 2. pdf • www. Lynda. com • Wikipedia • https: //www. wonderhowto. com/ 35

SIEM and Beyond http: //www. networkworld. com/article/3145408/security/goodbye-siem-hello-soapa. html Security Operations and Analytics (Platform Architecture) An evolution, not something different. Its all about detection in one form or another. Intrusion detection – originally monolithic. SIEM – Management of data about incidents and events. Rules defined processing to identify current state and intrusions. Provided ability to push down on the data to investigate. Analytics are the tools (including big data) that allow us to reason about the collected data. 36

What is SIEM Currently While originally expanded as “Security Incident and Event Management”, many currently expand the acronym as “Security Information and Event Management”. – That is because most of the activities revolve around the management of security information. • • Collecting data from logs Collecting data from sensors Creating a common format to represent such data Storing such data – User interfaces for visualizing this stored data – Simple rules/signatures for prompting notification 37

What is SIEM useful for • • • It is the evolved state of previous work in intrusion detection. It is very useful for manual forensics, as a central repository of all “artifacts”. It is a source of data that may be used for more advanced detection and diagnosis. 38

Enter SOAPA Do we need a new name? No Did we need a new name when SIEM came around? No But, marketers always want something new so… Security Operations and Analytics Platform Architecture – Goal is to support AI, Machine Learning, Neural Networks, and similar “Big Data”, “Data Science”, and “Data Analytics” to provide insight on the data. 39

SOAPA Components • • SIEM Endpoint Detection / Response Tools Incident Response Platforms Network Security Analytics Machine Learning Algorithms Vulnerability Scanners and Security Asset Managers Malware Sandboxes Threat Intelligence Now let’s discuss these in terms of the material already covered in this course. From http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 40

SOAPA – SIEM Component • This is the repository for collected data, and the source information on which other components will operate. 41

SOAPA Endpoint Tools “Security analysts often want to dig deep into security alerts by monitoring and investigating host behavior, so EDR (i. e. Carbon. Black, Countertack, Crowd. Strike, Guidance Software, etc. ) is an essential component of SOAPA. ” -- Computerworld article • Not just processing collected data, but allowing the administrator to push down and view live data at the end point, perhaps even more detailed than the data that is being forwarded to the SIEM. Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 42

SOAPA Incident Response “Aside from collecting, processing and analyzing security data, cybersecurity professionals want to prioritize alerts and remediate problems as soon as possible. These requirements are giving rise to IRPs such as Hexadite, Phantom, Resilient Systems (IBM), Service. Now and Swimlane” -- Computerworld article • Automated mitigation in an integrated manner is an important advance. • Intrusion response techniques – as discussed in CSci 530 – provide guidance on the kinds of response that is possible. • Integration with knowledge bases of what are your critical assets, what connections can be safely cut off, and what is the impact of a new threat can be useful in prioritizing those responses. – Some may be automated – Others may be advice • Especially important in Cyber-Physical systems Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 43

SOAPA Security Analytics “SIEM’s log analysis and EDR host behavior monitoring are complemented by flow and packet analysis in SOAPA, provided by vendors such as Arbor Networks, Blue Coat/Symantec, Cisco (Lancope) and RSA. ” -- Computerworld article • Not much new here. Just the detail of the data of which analytics are performed. One can look at collected packets, as per the network forensics topics we discussed previously. Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 44

SOAPA Machine Learning “While these tools have received an inordinate degree of industry hype, there’s little doubt that machine learning will be baked into security analytics henceforth, thus vendors such as Bay Dynamics, Caspida (Splunk), Exabeam, Niara, Sqrrl and Varonis should be included in SOAPA” -- Computerworld article • • • This is where the real difference is. It is the application of big data science to the data collected through the SIEM functionaility. These tools should be able to find clustering that is indicative of previously unseen attacks (i. e. zero days). Some SIEM solutions claim to have modules (fairly limited) for this kind of analysis, and now marketers want a new name for the use of these kinds of techniques. Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 45

SOAPA Asset Vulnerability Scanning “Part of security operations is knowing which alerts should be prioritized. These decisions must be driven by solid data from vulnerability management systems (i. e. Qualys, Rapid 7, Tanium) and other tools that monitor the state of systems and network configurations (i. e. Red. Seal, Skybox, Verodin, etc. ). ” -- Computerworld article • We have talked about these kinds of tools, though probably not man of them by name. These tools need to be better integrated into the SIEM environment, so that the tools are run on a regular basis, and the information can then be matched with configuration management information to identify what needs fixing in your environment. Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 46

SOAPA Malware Intelligence “This technology represents another key pivot point for understanding targeted attacks that may use zero-day malware. Sandboxes from Fire. Eye, Fidelis and Trend Micro are definitely part of SOAPA. ” -- Computerworld article • I’m not exactly sure how this capability integrates with other aspects of SOAPA. This is part of a total solution, but the integration eludes me. Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 47

SOAPA Threat Intelligence “Enterprise organizations want to compare internal network anomalies with malicious “in-the-wild” activities, so SOAPA extends to threat intelligence sources and platforms (i. e. Bright. Point (Service. Now), Fire. Eye/i. Sight Partners, Recorded. Future, Threat. Connect, Threat. Quotient, etc. ). ” -- Computerworld article • This extends the sources of information outside the enterprise. • As security administrators you need to keep up to date on the latest attacks. This is threat intelligence. • If properly encoded and integrated with an ID platform, this will enable you to identify new intrusions (zero days), and flag such traffic as related to particular groups or classes of criminals that are exploiting such techniques. Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 48

SOAPA Summary • SOAPA provides for better integration of many of the security technologies that should be deployed within your organization. Quote from http: //www. networkworld. com/article/3145408/ security/goodbye-siem-hello-soapa. html 49

Second Exercise - Criminal Enterprises • Chosen because of differences in the high level principles. – Not because I expect you to implement these kinds of systems in your future endeavors. – But you may be called upon to break some of these systems if later employed by government organizations. • Your organization must: – – – Accept Bitcoin as payment (not really, but it must accept something that stands in for bitcoin) Manage an inventory of stolen account identifiers with passwords Control access to such information Prevent collection of evidence or intelligence by third parties. Note, do not deal in any illegal goods, but use dummy information to stand in for such goods. Also, do not use terms associated with such illegals goods or information in communications, make up new names for this dummy information. 50

Group Report for Lab Exercise 2 By Tuesday April 18 th please submit a report including: • A network diagram: – including your virtual machines and other systems like client browsers – Show containment regions • A description of all software components used in the implementation of your scenario, including: – Application software components (e. g. databases, servers) – Security software components – Administration and management software components • For each software component: – Describe where it is installed – Where obtained (or written yourself), and version information » How you manage updates – A table listing the authorized information flows. • For the system as a whole – List tools used to monitor, detect and recover from intrusions – What kind of red-teaming or pen-testing you performed – A risk assessment – what threats do you defend against, how do you mitigate impact of an attack, what are you still vulnerable to, and justification for your decisions regarding such threats. 51

By the Final Lecture in two weeks Alternate Date for April 26 th • Each group should prepare a report describing: – User documentation for their application (high level) – Their network and server architecture (what servers are on what VM’s and how they are interconnected) – A risk assessment/vulnerability analysis enumerating the risks, explaining the mitigation of those risks, and listing those threats that are not defended against (i. e. where you accept the risks). – A description of the steps taken for pen testing of your system. • Each group will have 20 minutes to present, and then 20 minutes to demonstrate their project. We will have 20 minutes following gthe presentations and demonstrations for limited pen-testing. – Procedures and Rules to be determined 52
 Network security monitoring tools open source
Network security monitoring tools open source Byzantine empire 526 ce
Byzantine empire 526 ce Brb 526
Brb 526 Byzantine empire 526 ce
Byzantine empire 526 ce What is the value of the underlined digit 526
What is the value of the underlined digit 526 Salmo 526 completo
Salmo 526 completo Network security process
Network security process Ece 526
Ece 526 Ece 526
Ece 526 Network systems design using network processors
Network systems design using network processors Can we make operating systems reliable and secure
Can we make operating systems reliable and secure Network management standards
Network management standards Infinitive without to
Infinitive without to How to design a local area network
How to design a local area network Srx4000 spec
Srx4000 spec Juniper advanced threat protection
Juniper advanced threat protection Secure network gateway
Secure network gateway Define network administration
Define network administration Introduction to network administration
Introduction to network administration Network operating system administration
Network operating system administration Network administration syllabus
Network administration syllabus Insurance accounting and systems association
Insurance accounting and systems association D'infinity h character table
D'infinity h character table In4matx 121
In4matx 121 Inf1900
Inf1900 Mag inf
Mag inf Blood supply of brain
Blood supply of brain Artere thyroidienne inf
Artere thyroidienne inf Ma da infinitiiv harjutused
Ma da infinitiiv harjutused Inf 110
Inf 110 Inf 101
Inf 101 Inf 327
Inf 327 Inf
Inf Inf 3 form
Inf 3 form Define:inf
Define:inf Cyclopeptide mushroom
Cyclopeptide mushroom Manifestversion
Manifestversion Mononukeloza
Mononukeloza Inf smartwatch
Inf smartwatch Cpu.inf
Cpu.inf I inf
I inf Inf hartsol
Inf hartsol Plexus hypogastricus inf
Plexus hypogastricus inf A medence csontjai
A medence csontjai Eurodatabase
Eurodatabase Inf schule scratch
Inf schule scratch Bare verbs list
Bare verbs list Considerações finais
Considerações finais Inf
Inf Inf
Inf Inf
Inf Torrent 1331x
Torrent 1331x Inf
Inf Inf
Inf