INF 526 Secure Systems Administration Second Quiz Midterm





















- Slides: 46

INF 526: Secure Systems Administration Second Quiz / Mid-term Prof. Clifford Neuman Lecture 9 8 March 2017 OHE 100 C

INF 526: Secure Systems Administration MID-TERM IN PROGRESS Prof. Clifford Neuman Lecture 9 8 March 2017 OHE 100 C

INF 526: Secure Systems Administration Network Security Components Prof. Clifford Neuman Lecture 9 8 March 2017 OHE 100 C

Secure Network Administration • Secure Host Administration provides fine-grained control of access to a hosts resources. • Secure Network administration assists in controlling access at a coarse level of granularity – – Not to records or files, but to computers and subnets. At most, limits access to services (by port) Confines access to zones Is a second line of defense, and useful as stop-gap when vulnerabilities in host infrastructure are discovered. 3

Elements of Secure Network Administration – Policy • Tells you what access is authorized • Should follow analysis of application information flow requirements. • Can also specify specific flows that are disallowed. – Containment • Many tools to contain information. • Not all effective. • Most available tools support DAC, but MAC is more effective. – Monitoring • Important to discover unintended paths that are exploited • Important to discover insider threats 4

Network Containment Tools • Firewall – Network, Host, Embedded, Application • Virtual Private Network – Encrypted Tunnels between zones • IPSec – Encryption and Integrity between hosts • Virtual LANS – Layer 2 separation • Encryption – Supports other forms of containment 5

Firewalls • Network Based – Protects (or not) entire network. Chewy on inside. – Statefull vs stateless – Limited basis on which to make decisions. • Host Based – Controls access to resources on single host • Embedded – On interface card, but managed separately • Distributed – Single policy (next) implemented at multiple PEP • Application – No routing of packets, just recreation of application messages. Examples: DNS, Web, Email – configuration. 6

Virtual Private Networks • Interconnects two LANs across unprotected network segment. – Creates a secure tunnel connecting to segments. – One segment can be a single host – which is how many of you use a VPN. • Important tool to extend secure perimeter – Allows remote device to operate within your secure environment. – Downside is that the remote device is now on the inside. – Examples: Smartphone, Laptop, Employee Home Machines. • Must apply controls to the device – Need policies for users – That is polices to which users must conform. 7

IPSec and IPv 6 Security • IP Security (IPsec) and the security features in IPv 6 essentially move VPN support into the operating system and lower layers of the protocol stack. • Security is host to host, or host to network, or network to network as with VPN’s – Actually, VPN’s are rarely used host to host, but if the network had a single host, then it is equivalent. • IPSec Implementations also implement a Host Based firewall (Policies on acceptable connections) 16

IPSec Goals • Authentication of hosts – Verify the source of IP packets – Prevention of replays • Verify integrity of packets – Through use of hashes and cryptography • Ensure confidentiality of packets • Protect the payload • Enforce Policy on communication of endpoints. 9

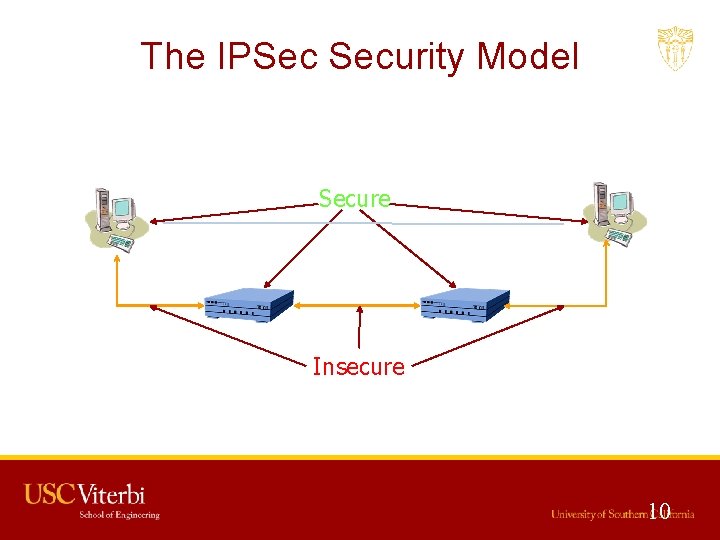
The IPSec Security Model Secure Insecure 10

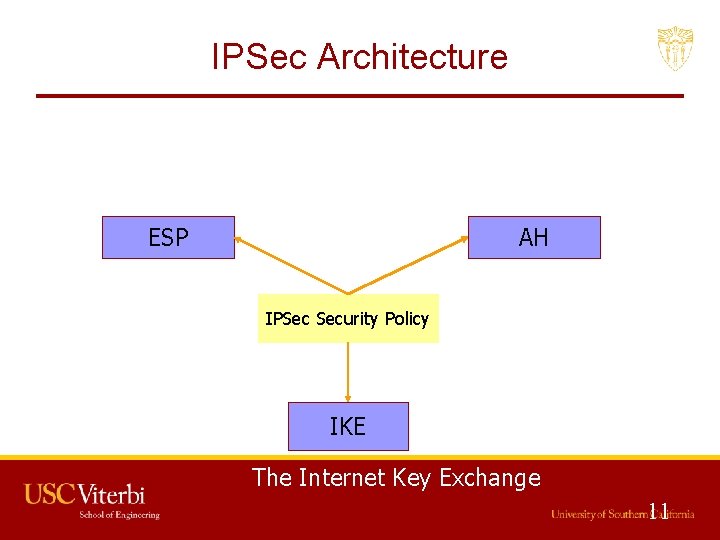
IPSec Architecture ESP AH Encapsulating Security Payload Authentication Header IPSec Security Policy IKE The Internet Key Exchange 11

IPSec Architecture • IPSec provides security in three situations: – Host-to-host, host-to-gateway and gateway-togateway • IPSec operates in two modes: – Transport mode (for end-to-end) – Tunnel mode (for VPN) 12

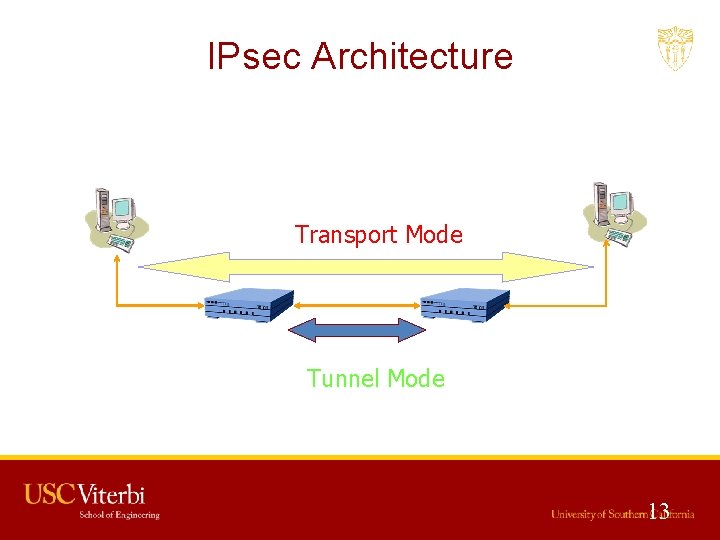
IPsec Architecture Transport Mode Router Tunnel Mode 13

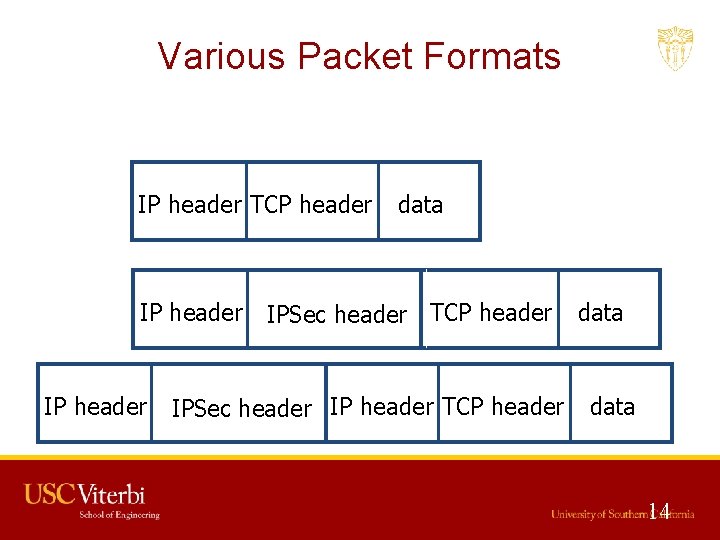
Various Packet Formats Original IP header TCP header Transport Tunnel IPmode header mode Tunnel IPmode header data IPSec header TCP header IPSec header IP header TCP header data 14

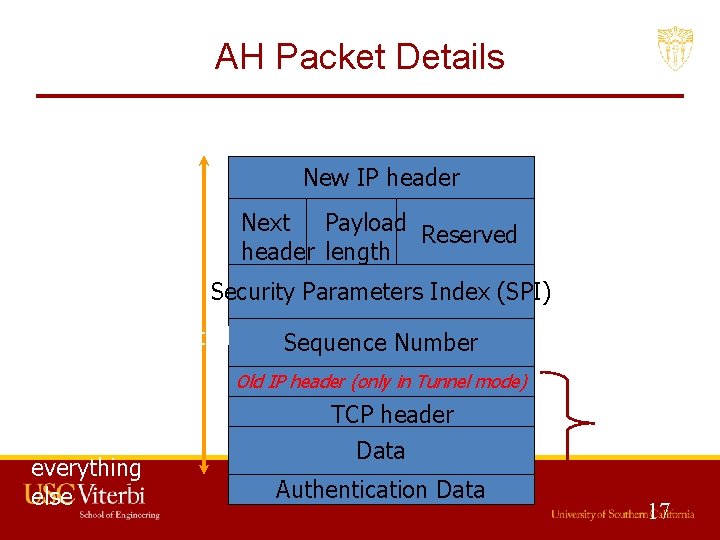
Authentication Header (AH) • Provides source authentication – Protects against source spoofing • Provides data integrity • Protects against replay attacks – Use monotonically increasing sequence numbers – Helps Protect against dos attacks • NO protection for confidentiality! 15

AH Details • Use 32 -bit monotonically increasing sequence number to avoid replay attacks • Use cryptographically strong hash algorithms to protect data integrity (96 -bit) – Use symmetric key cryptography – HMAC-SHA-96, HMAC-MD 5 -96 16

AH Packet Details New IP header Next Payload Reserved header length Security Parameters Index (SPI) Authenticated Sequence Number Old IP header (only in Tunnel mode) Hash of everything else Encapsulated TCP or IP packe TCP header Data Authentication Data 17

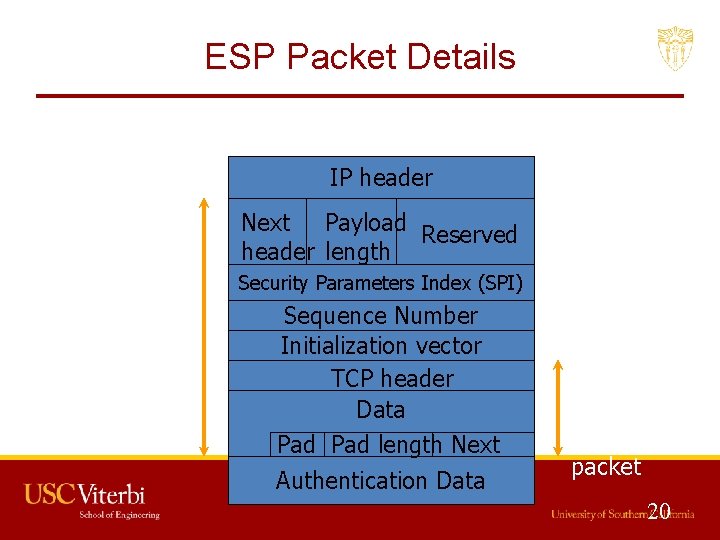
Encapsulating Security Payload (ESP) • Provides all that AH offers, and • in addition provides data confidentiality – Uses symmetric key encryption 18

ESP Details • Same as AH: – Use 32 -bit sequence number to counter replaying attacks – Use integrity check algorithms • Only in ESP: – Data confidentiality: • Uses symmetric key encryption algorithms to encrypt packets 19

ESP Packet Details IP header Next Payload Reserved header length Security Parameters Index (SPI) Authenticated Sequence Number Initialization vector TCP header Data Pad length Next Authentication Data Encrypted TCP packet 20

Internet Key Exchange (IKE) • Exchange and negotiate security policies • Establish security sessions – Identified as Security Associations • Key exchange • Key management • Can be used outside IPsec as well 21

IPsec/IKE Acronyms • Security Association (SA) – Collection of attribute associated with a connection – Is asymmetric! • One SA for inbound traffic, another SA for outbound traffic • Similar to ciphersuites in SSL • Security Association Database (SADB) – A database of SAs 22

IPsec/IKE Acronyms • Security Parameter Index (SPI) – A unique index for each entry in the SADB – Identifies the SA associated with a packet • Security Policy Database (SPD) – Store policies used to establish SAs 23

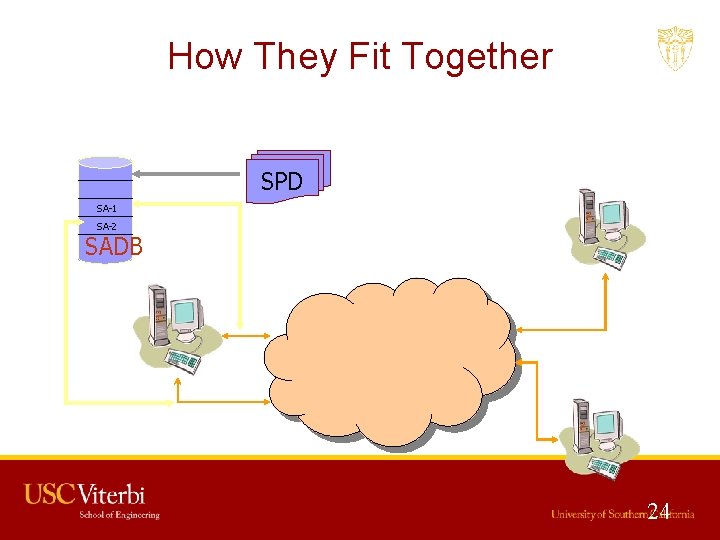
How They Fit Together SPD SA-1 SA-2 SADB SPI 24

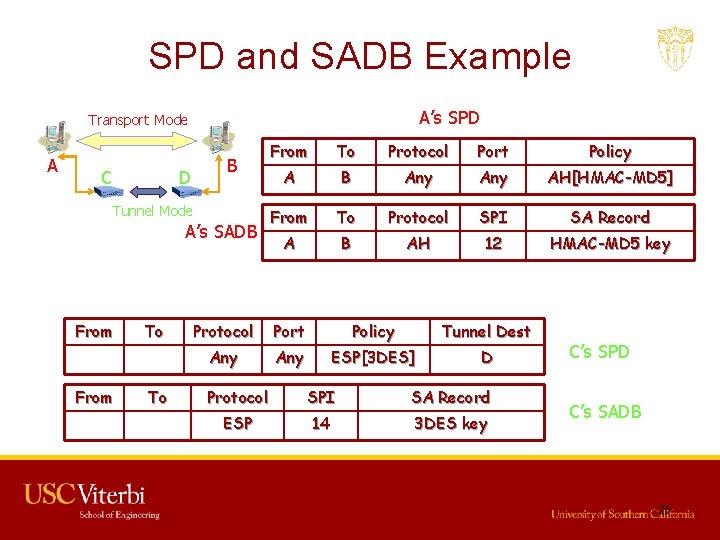
SPD and SADB Example A’s SPD Transport Mode A C B D Tunnel Mode A’s SADB From To Protocol Port Policy A B Any AH[HMAC-MD 5] From To Protocol SPI SA Record A B AH 12 HMAC-MD 5 key From To Protocol Port Policy Tunnel Dest Asub Bsub Any ESP[3 DES] D From To Protocol SPI SA Record Asub Bsub ESP 14 3 DES key C’s SPD C’s SADB 25

IPsec Policy • Phase 1 policies are defined in terms of protection suites • Each protection suite – Must contain the following: • • Encryption algorithm Hash algorithm Authentication method Diffie-Hellman Group – May optionally contain the following: • Lifetime • … 26

IPSec Policy • Phase 2 policies are defined in terms of proposals • Each proposal: – May contain one or more of the following • • AH sub-proposals ESP sub-proposals IPComp sub-proposals Along with necessary attributes such as – Key length, life time, etc 27

IPSec Policy Example • In English: – All traffic to 128. 104. 120. 0/24 must be: • • Use pre-hashed key authentication DH group is MODP with 1024 -bit modulus Hash algorithm is HMAC-SHA (128 bit key) Encryption using 3 DES • In IPSec: – [Auth=Pre-Hash; DH=MODP(1024 -bit); HASH=HMAC-SHA; ENC=3 DES] 28

IPsec Policy Example • In English: – All traffic to 128. 104. 120. 0/24 must use one of the following: • AH with HMAC-SHA or, • ESP with 3 DES as encryption algorithm and (HMAC-MD 5 or HMAC-SHA as hashing algorithm) • In IPsec: – [AH: HMAC-SHA] or, – [ESP: (3 DES and HMAC-MD 5) or (3 DES and HMAC-SHA)] 29

Virtual LANS (VLANS) • Basic discussion that follows is from Gregory Laffoon at Purdue University. 30

Configuring your VLAN Presented by Gregory Laffoon 31

What is a VLAN? • A virtual local area network (VLAN) is a group of hosts with a common set of requirements that communicate as if they were attached to the same broadcast domain regardless of their physical location. 32

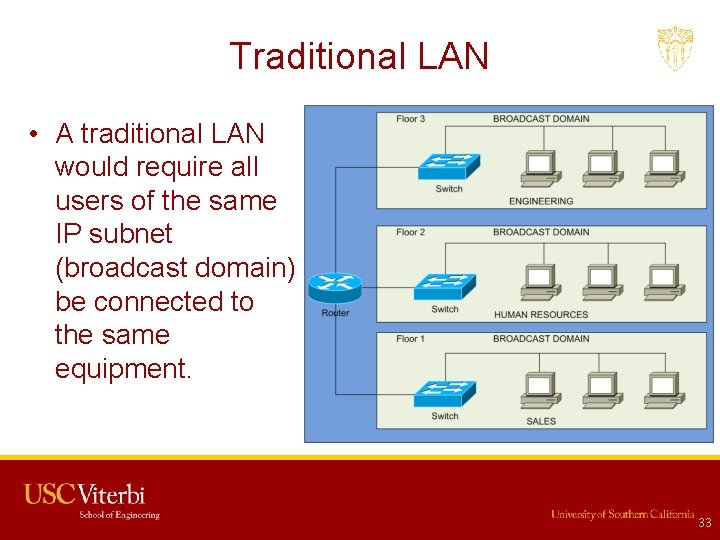
Traditional LAN • A traditional LAN would require all users of the same IP subnet (broadcast domain) be connected to the same equipment. 33

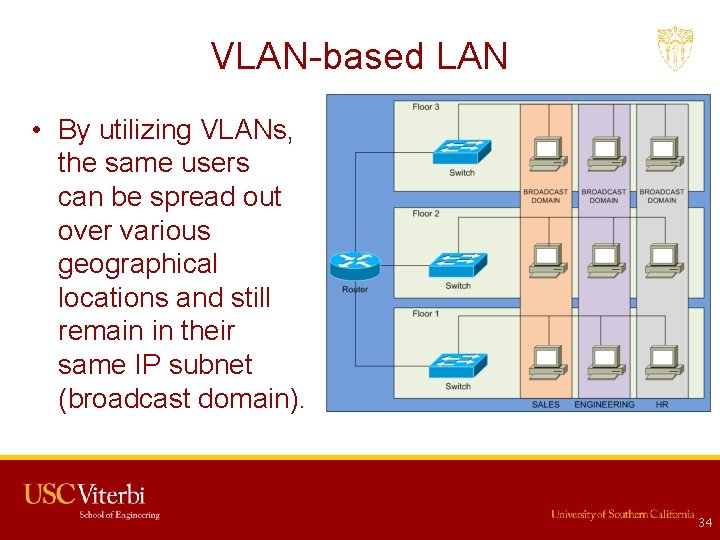
VLAN-based LAN • By utilizing VLANs, the same users can be spread out over various geographical locations and still remain in their same IP subnet (broadcast domain). 34

How VLANs Work? • VLANs are identified by a number – Valid ranges 1 -4094 • On a VLAN-capable switch, you assign ports with the appropriate VLAN number • The switch then only allows data to be sent between ports with the same VLAN 35

How VLANs Work? • Since almost every network is larger than a single switch, there needs to be a way to have traffic sent between two different switches • One way to do it is to assign a port on each switch with a VLAN and run a cable between the switches – Not very feasible or cost effective 36

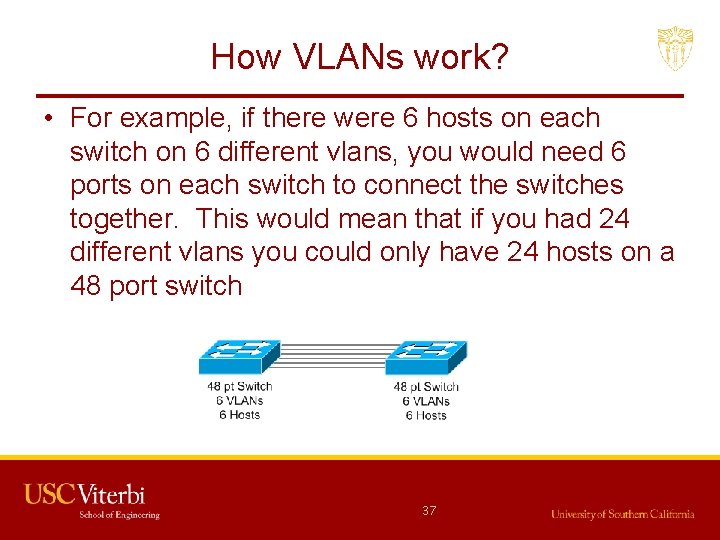
How VLANs work? • For example, if there were 6 hosts on each switch on 6 different vlans, you would need 6 ports on each switch to connect the switches together. This would mean that if you had 24 different vlans you could only have 24 hosts on a 48 port switch 37

How VLANs work? • A single connection between two switches can be used to send traffic for all vlans • 802. 1 q – Provides a VLAN tag in front of the Layer 2 frame 38

How VLANs work? • You enable 802. 1 q tagging (trunking) on the ports between the switches • The switch receives the frame with the 802. 1 q header and strips it off • It determines what VLAN and sends the data to the appropriate port 39

Benefits of VLANs • Geographically separated users on the same IP subnet (broadcast domain) • Limit the size of broadcast domains and limit broadcast activity • Security benefits by keep hosts separated by VLAN and limiting what devices can talk to those hosts 40

Benefits of VLANs • Cost savings as you don’t need additional hardware and cabling • Operational benefits because changing a user’s IP subnet (Broadcast Domain) is in software 41

Drawbacks of VLANs • VLANs work at Layer 2 and that layer doesn’t handle redundancy in an efficient manner • So when the network becomes mission critical, it is hard to provide fast convergence times for users when utilizing VLANs that span across multiple buildings 42

Network Policy Management • Telling containment technologies what to allow • Coordinated policy management is important • Commercial Tools to Manage Multiple Firewalls – E. g. Redseal Networks http: //www. redsealnetworks. com/files/Red. Seal_Corporate_Brochure_02172014. pdf – Many other Tools • Distributed Firewalls – Distributed Embedded Firewalls • Adventium Labs • One PAP and PSP, but multiple PEPs and PDPs – Firewall on network cards, but not managed by host, instead managed centrally. 43

Network Monitoring • Taps for Intrusion Detection Systems – Provides high bandwidth feed of all data flowing through a router or firewall. – Data analytics may be applied or simple high bandwidth pattern recognition. • Deep Packet Inspection – Required knowledge of protocols and applications. • What makes monitoring more difficult – Encryption – False Positives • Filtering out expected traffic 44

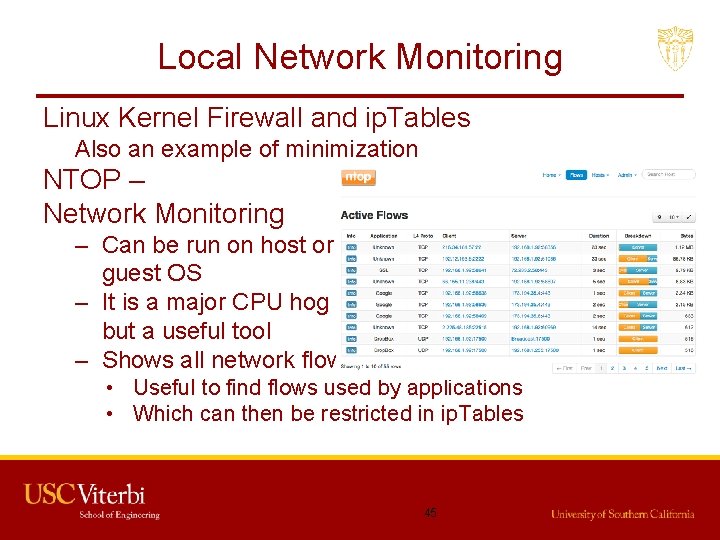
Local Network Monitoring Linux Kernel Firewall and ip. Tables Also an example of minimization NTOP – Network Monitoring – Can be run on host or guest OS – It is a major CPU hog but a useful tool – Shows all network flows in real time • Useful to find flows used by applications • Which can then be restricted in ip. Tables 45