i Security Audit Training i Security Products Overview




















- Slides: 122

i. Security Audit Training

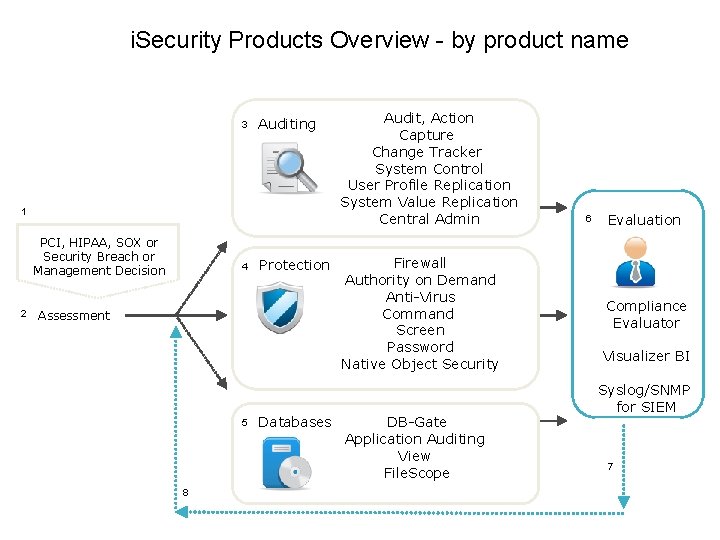
i. Security Products Overview - by product name 3 Auditing 1 PCI, HIPAA, SOX or Security Breach or Management Decision 2 4 Protection Assessment 5 Databases Audit, Action Capture Change Tracker System Control User Profile Replication System Value Replication Central Admin Firewall Authority on Demand Anti-Virus Command Screen Password Native Object Security DB-Gate Application Auditing View File. Scope 8 2 6 Evaluation Compliance Evaluator Visualizer BI Syslog/SNMP for SIEM 7

Audit Features • At-a-glance, user-friendly display of QAUDJRN activity covering all audit types • Reduces disk space by filtering system audit data, leaving only requested data • Easy definition of audit related security rules • Query Wizard enables creating queries quickly without programming • Various report formats include e-mail/HTML/PDF/CSV • Powerful Report Generator includes over 250 predefined reports • Ready-made reports suited to SOX • Enables selecting, sorting and filtering fields in reports • Advanced scheduler runs reports at specified times, e-mailing results to your desktop • Real-time initiation of responses to potential threats and security violations 3

What is Audited • User Activity – When you want to focus on a particular user or group • Object Access – For critical objects • System Security Audit Journal • Real Time Detection – Send alerts etc (in combination with Action) – Populates the i. Security Audit Log

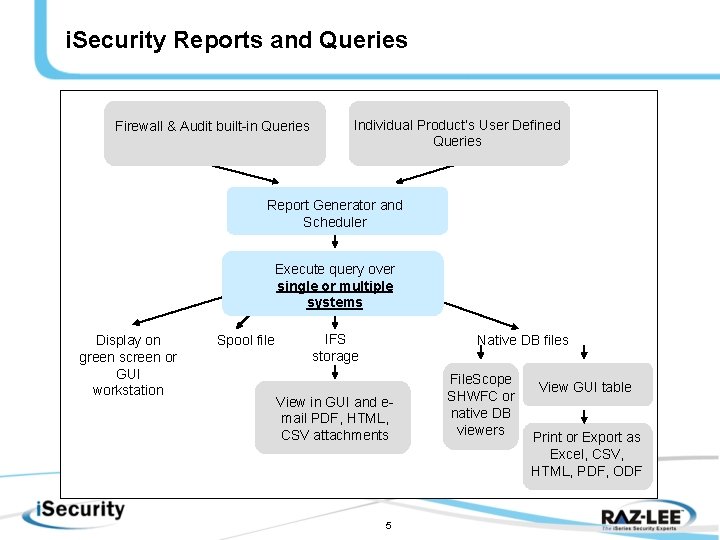
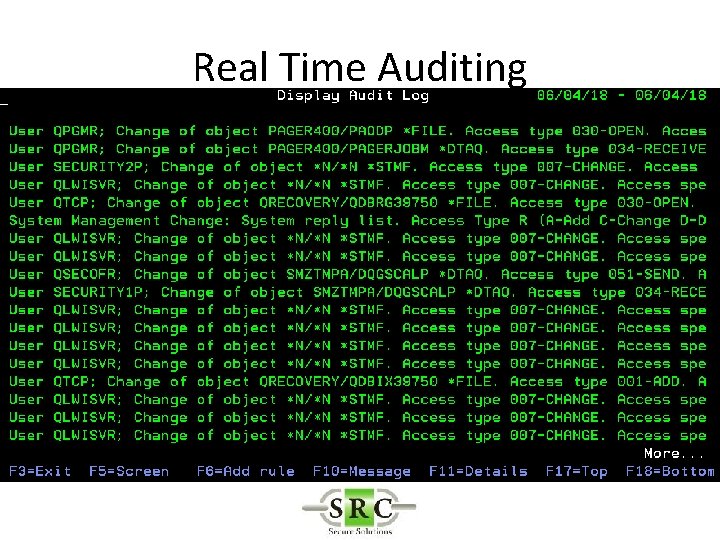
i. Security Reports and Queries Firewall & Audit built-in Queries Individual Product’s User Defined Queries Report Generator and Scheduler Execute query over single or multiple systems Display on green screen or GUI workstation Spool file IFS storage Native DB files View in GUI and email PDF, HTML, CSV attachments 5 File. Scope SHWFC or native DB viewers View GUI table Print or Export as Excel, CSV, HTML, PDF, ODF

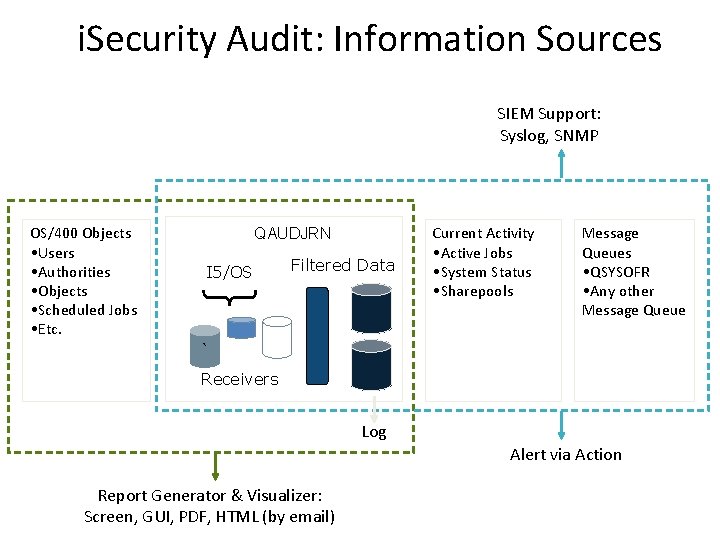
i. Security Audit: Information Sources SIEM Support: Syslog, SNMP OS/400 Objects • Users • Authorities • Objects • Scheduled Jobs • Etc. Current Activity • Active Jobs • System Status • Sharepools QAUDJRN I 5/OS Filtered Data Message Queues Audit • QSYSOFR • Any other Message Queue ` Receivers Log Alert via Action Report Generator & Visualizer: Screen, GUI, PDF, HTML (by email) 6


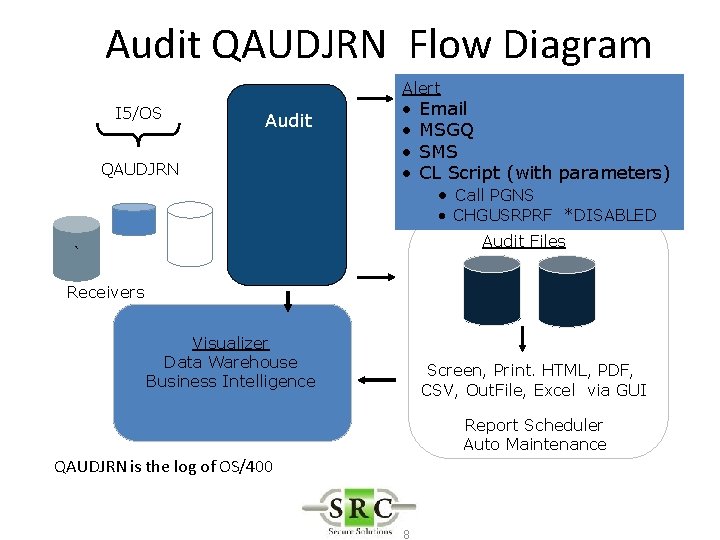
Audit QAUDJRN Flow Diagram I 5/OS Audit QAUDJRN Alert • • Email MSGQ SMS CL Script (with parameters) • Call PGNS • CHGUSRPRF *DISABLED Audit Files ` Receivers Visualizer Data Warehouse Business Intelligence Screen, Print. HTML, PDF, CSV, Out. File, Excel via GUI Report Scheduler Auto Maintenance QAUDJRN is the log of OS/400 8

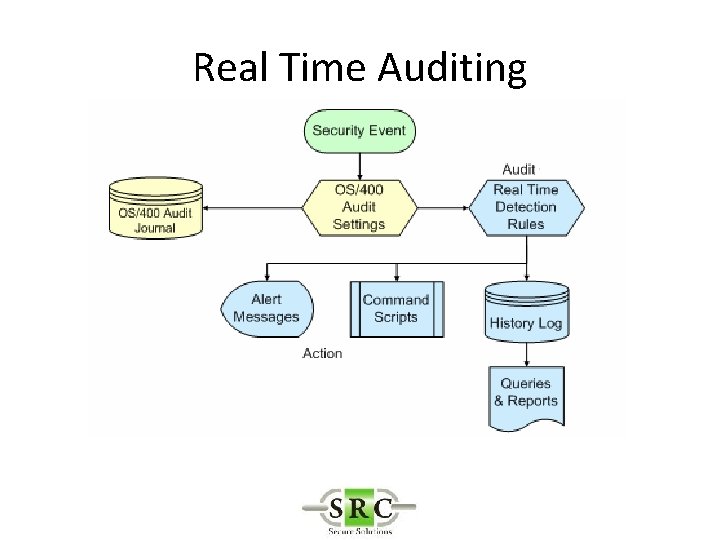
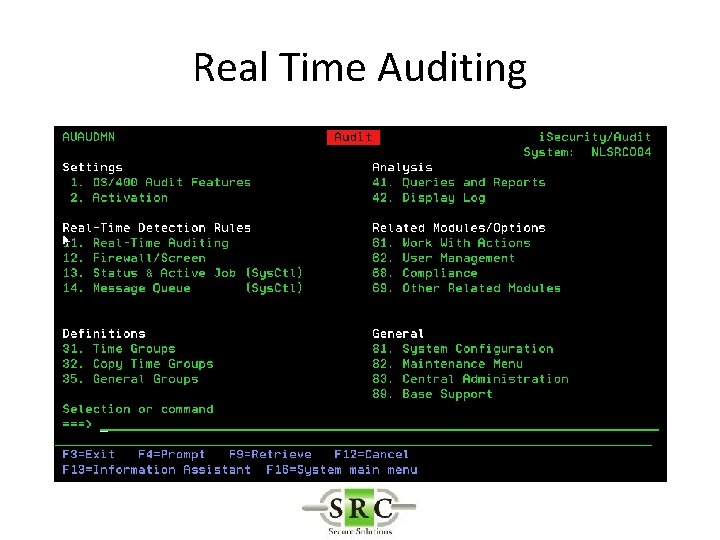
Setting up Audit • Determine which events are to be audited by i 5/OS • Determine which of these events are to be monitored and reported upon by AUDIT (“Real Time Auditing”) • Real-time detection must be activated on your system in order to enable triggering actions and posting events in the Audit history log. It is recommended that you allow OS/400 to activate real-time detection automatically at IPL. • Determine which Users are to be audited • Determine which Objects are to be audited

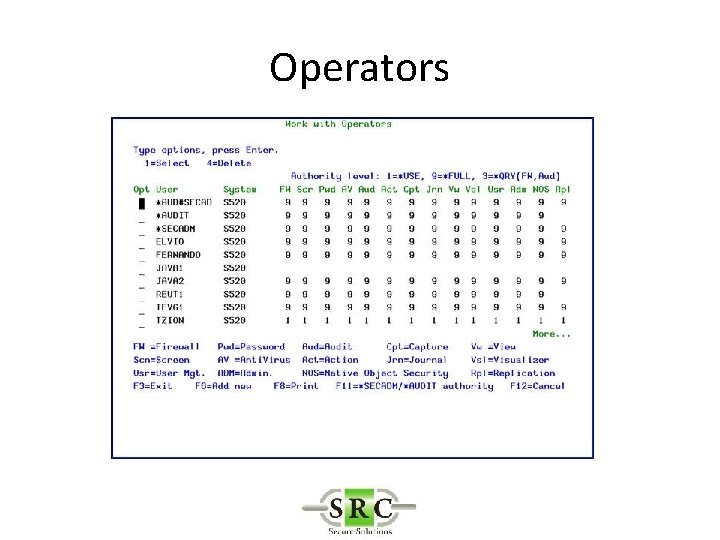
Operators

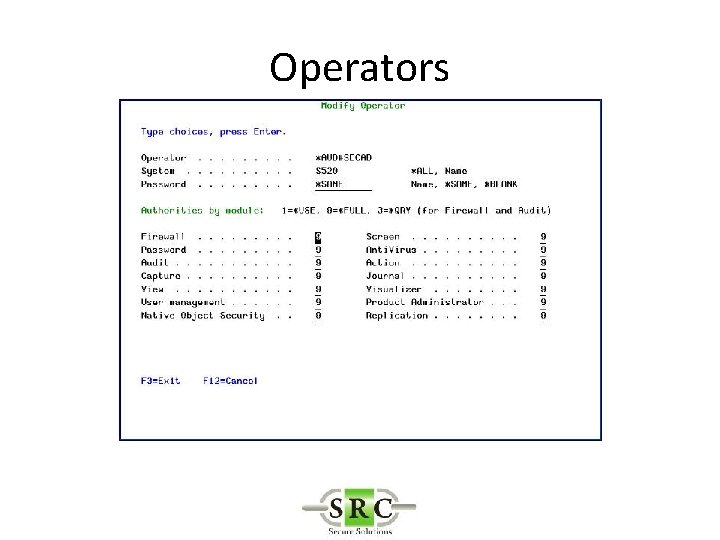
Operators

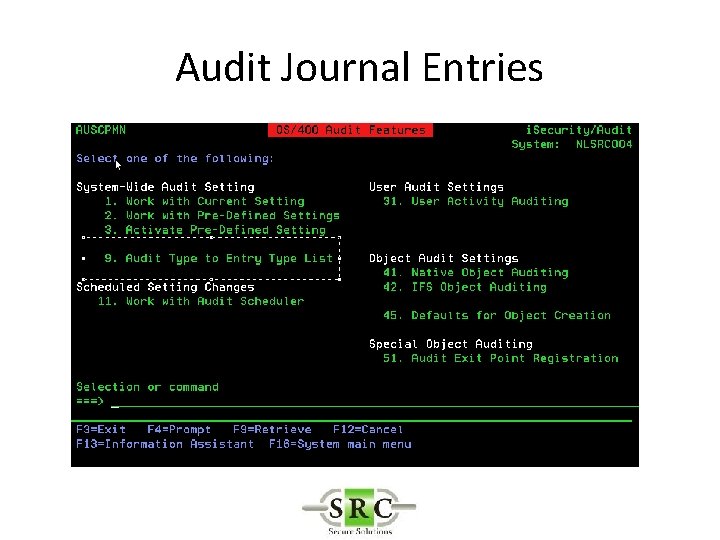
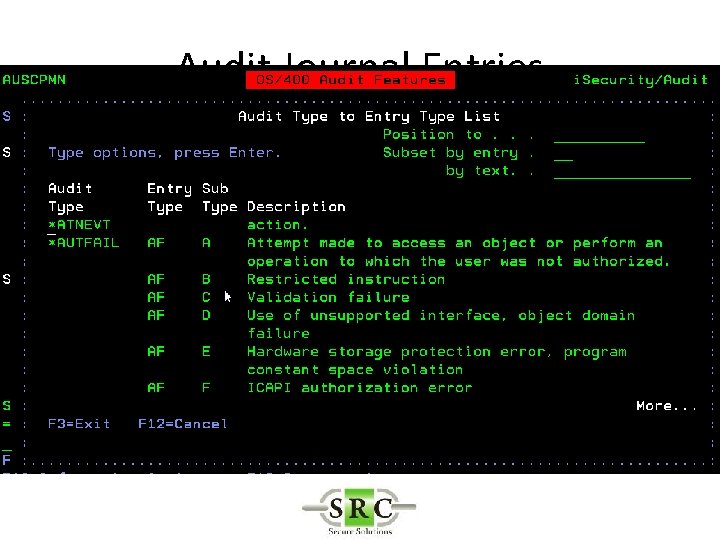
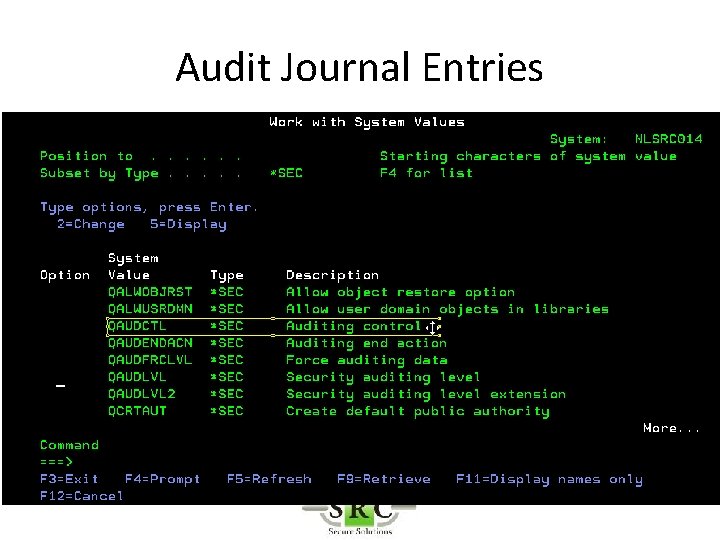
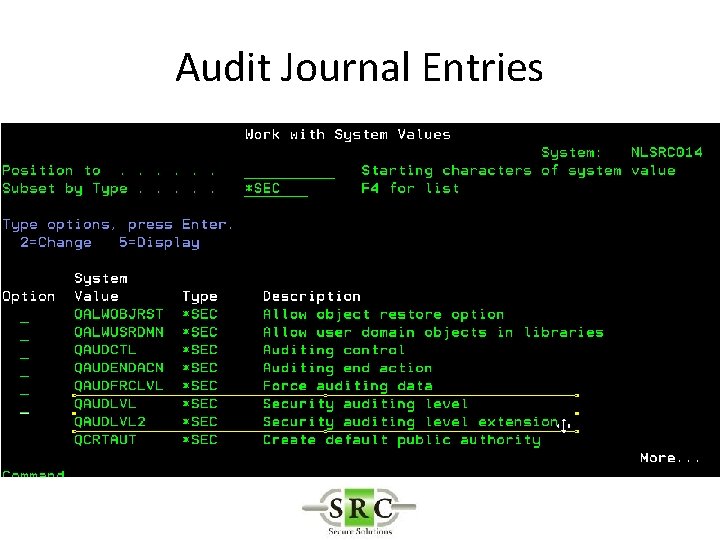
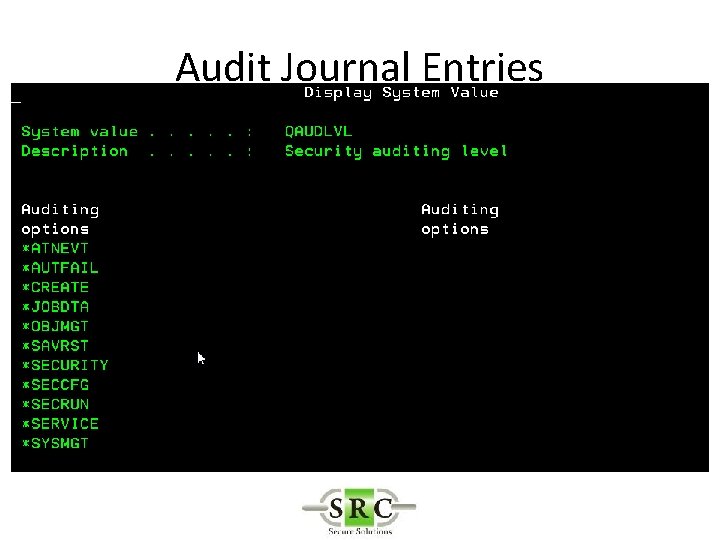
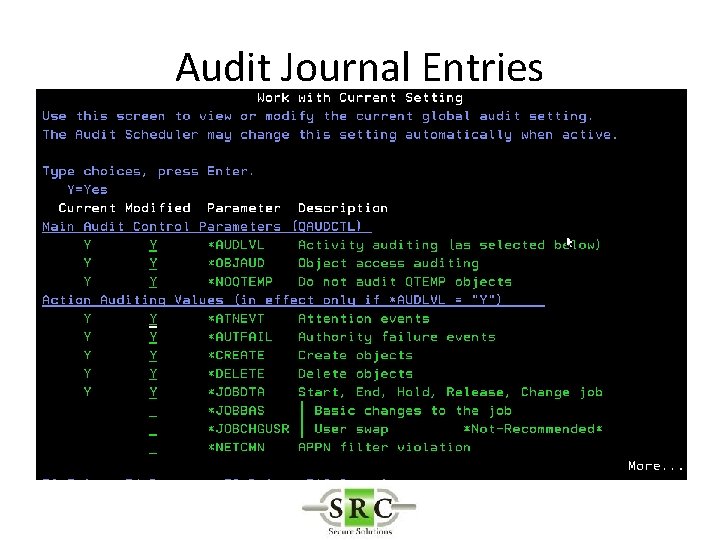
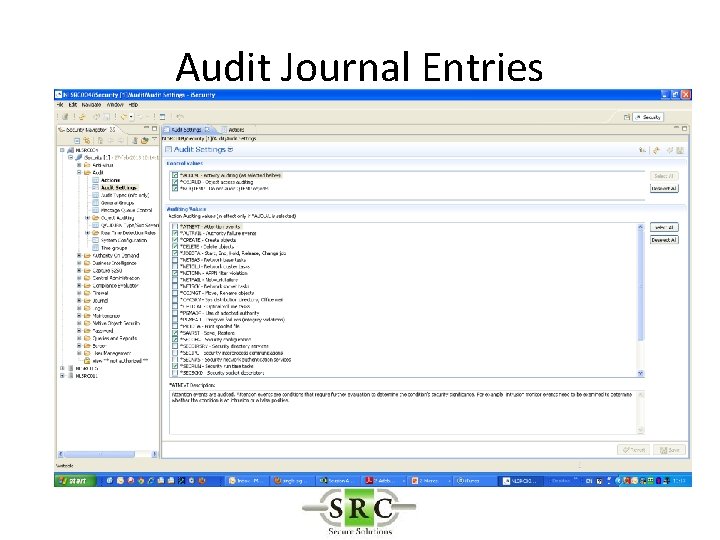
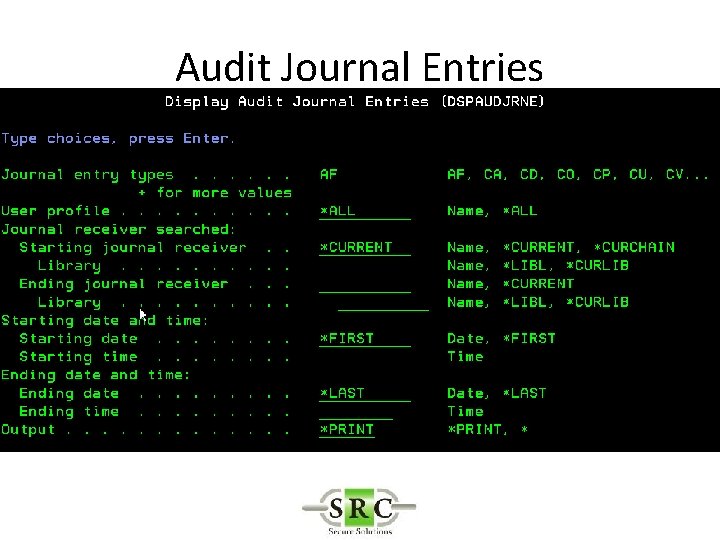
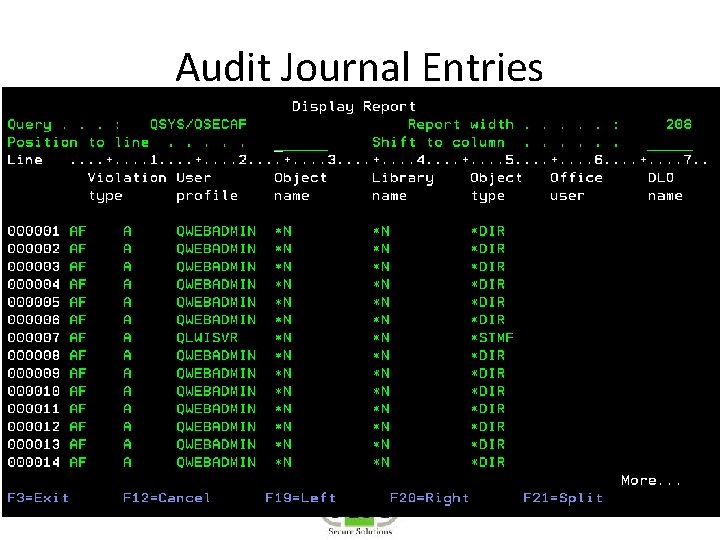
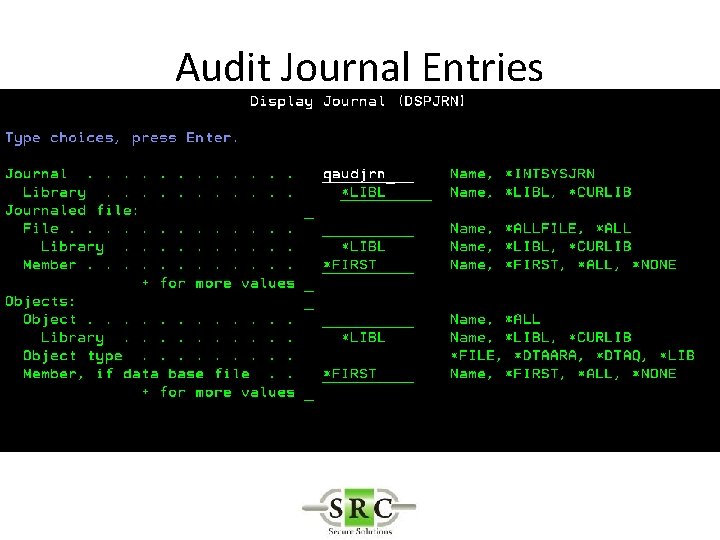
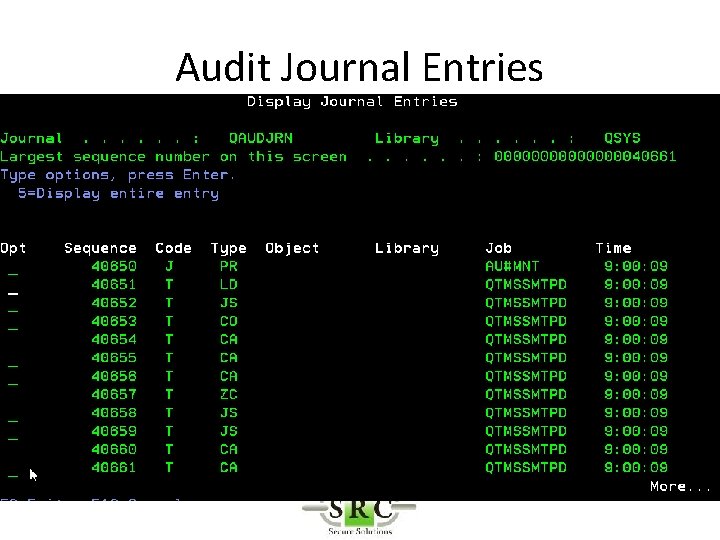
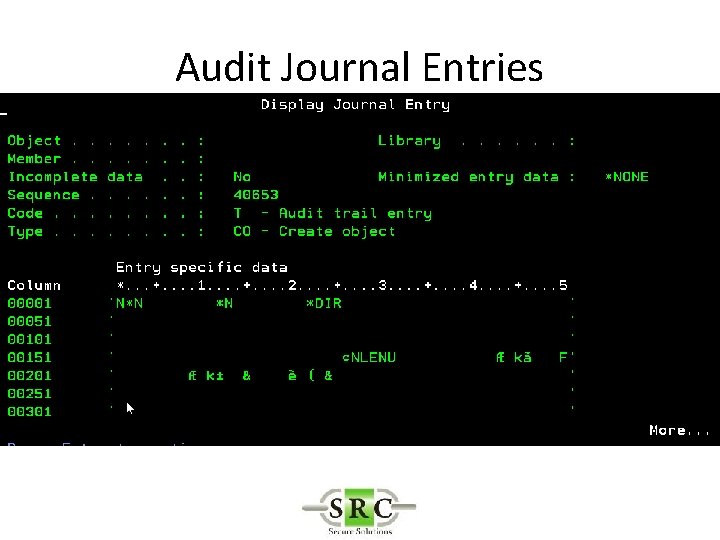
Audit Journal Entries • Define in System Values • DSPSECAUD • QAUDCTL – determines if i 5/OS auditing is active at high level – *AUDLVL for detail audit types – *OBJAUD all auditable objects are audited – *NOQTEMP • QAUDLVL & QAUDLVL 2

Audit Journal Entries • CHGOBJAUD – Auditing of a specific OS/400 object • CHGAUD – Auditing at object level using Path • CHGDLOAUD – Auditing of Document Library Objects • CHGUSRAUD – Auditing at User Level

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

Audit Journal Entries

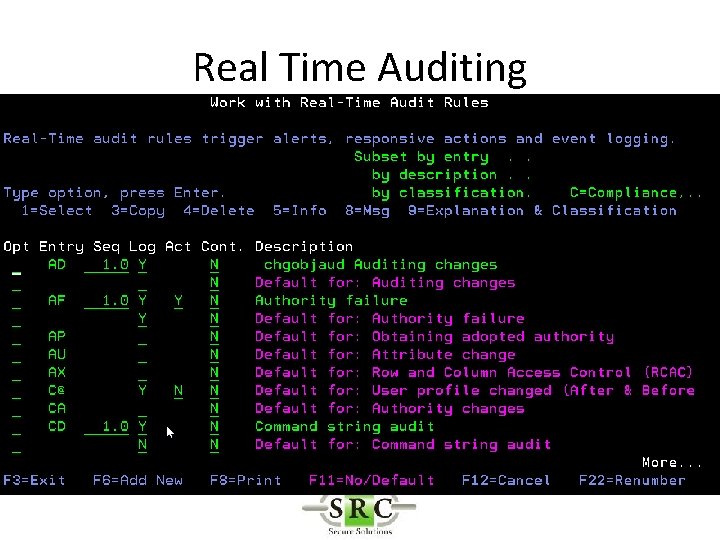
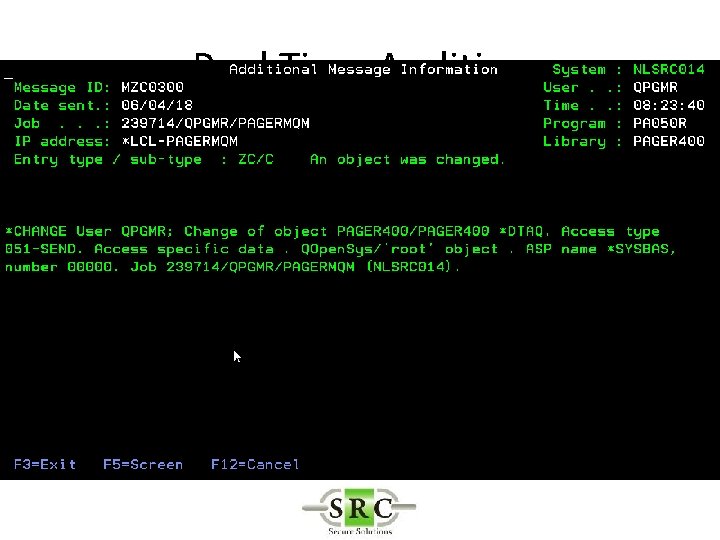
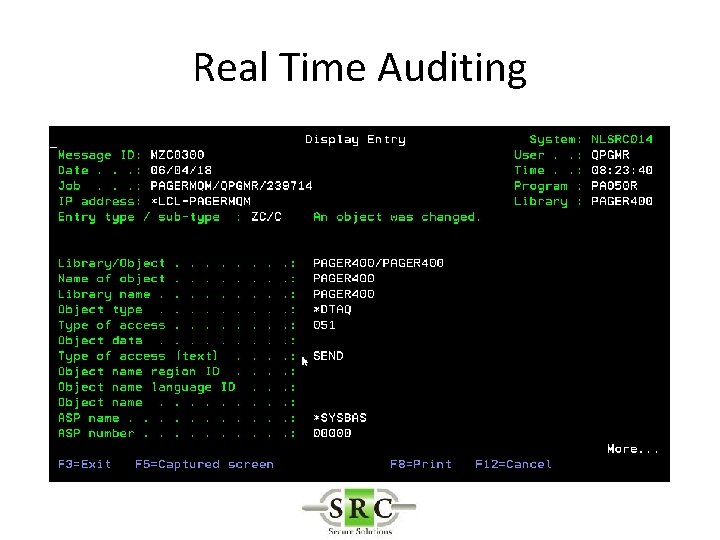
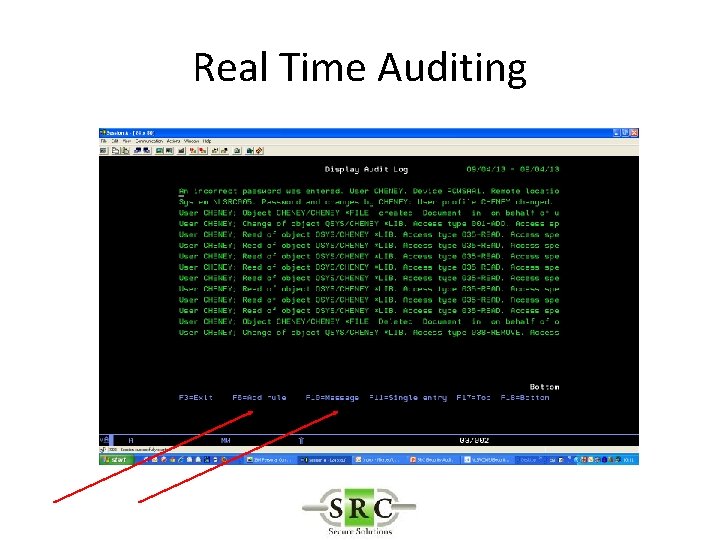
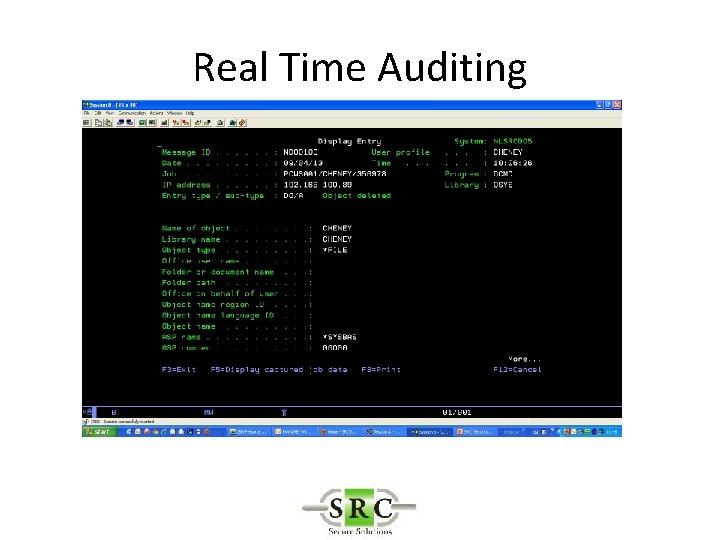
Real Time Auditing • Copies selected i 5/OS journal entries into the AUDIT log files • Allows selection of specific entries thus reducing space required on system • Improves readability • Allows action* to be taken on specific entries • Create SYSLOGs • Export to Visualizer

Real Time Auditing

Real Time Auditing

Real Time Auditing

Real Time Auditing

Real Time Auditing

Real Time Auditing

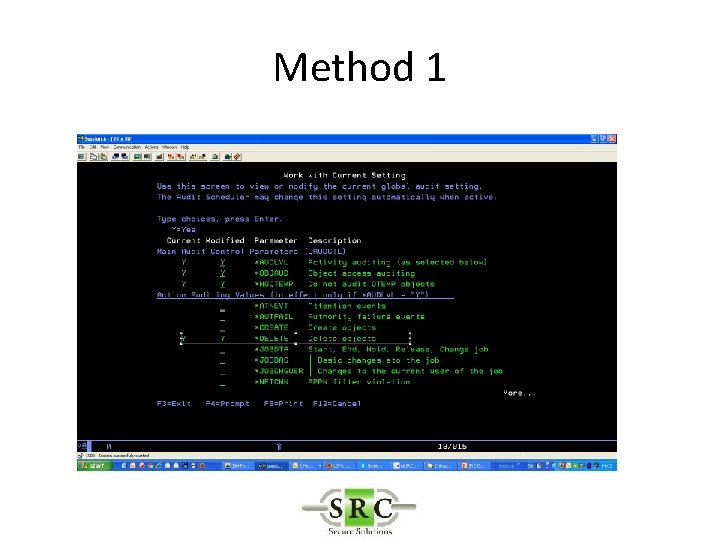
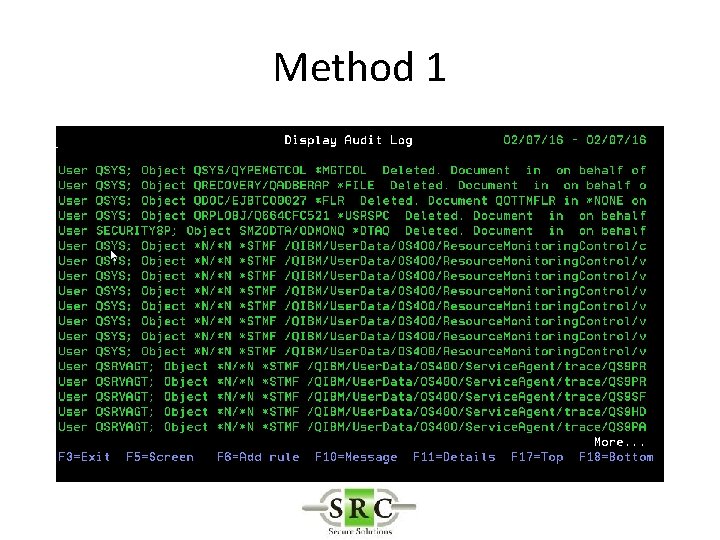
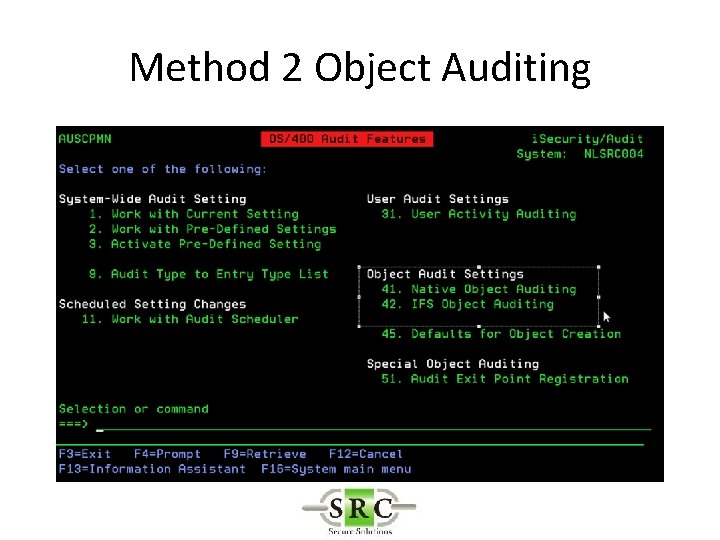
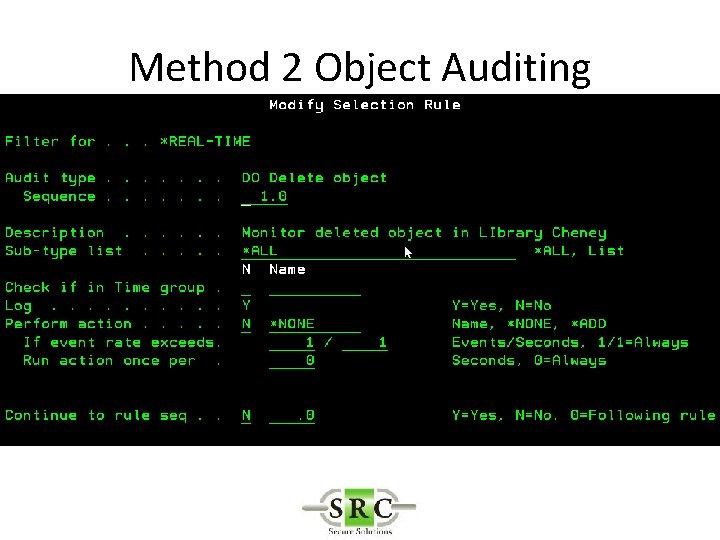
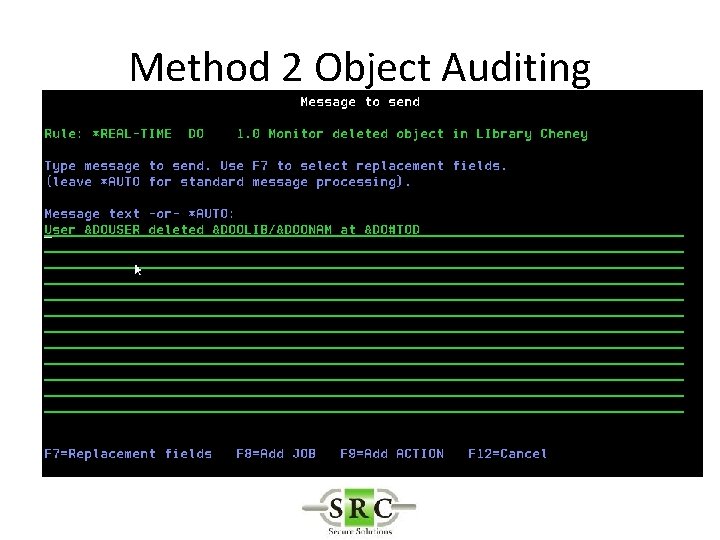
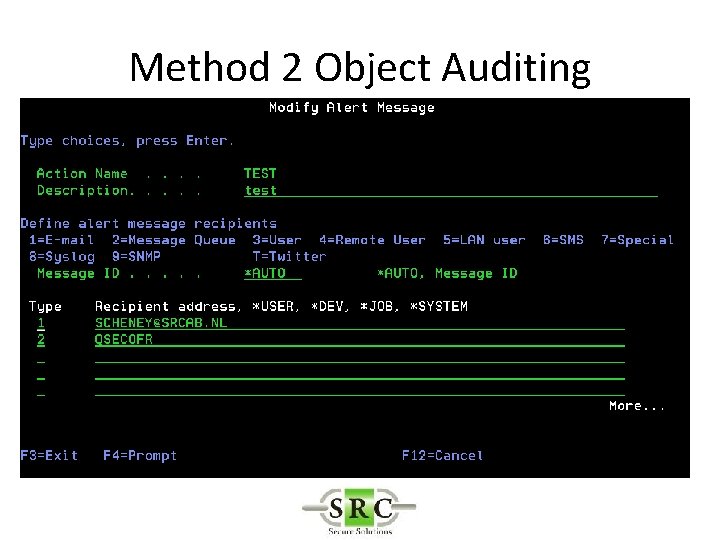
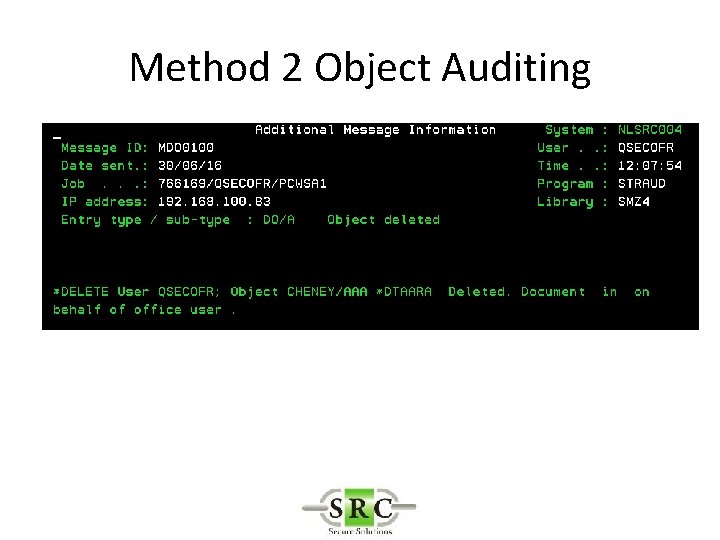
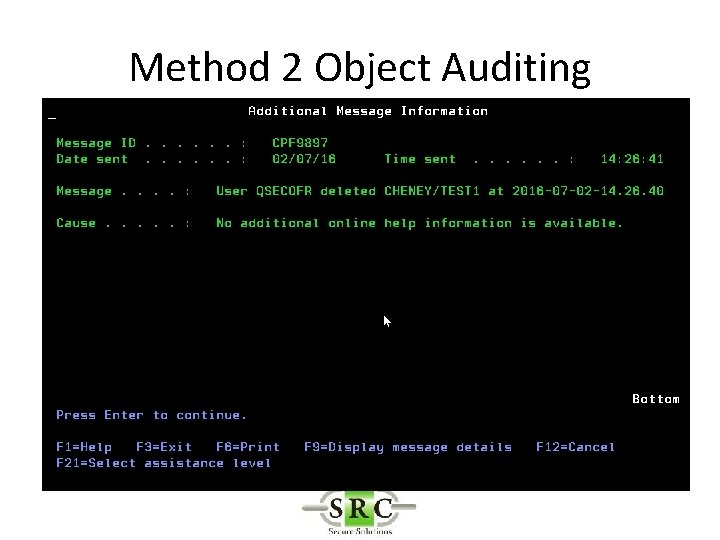
Real Time Auditing • Example -Auditing the deletion of an object – Method 1 – *DELETE (all deletes) creates too many log entries – Method 2 – Object Auditing – Method 3 – User Auditing

Method 1

Method 1

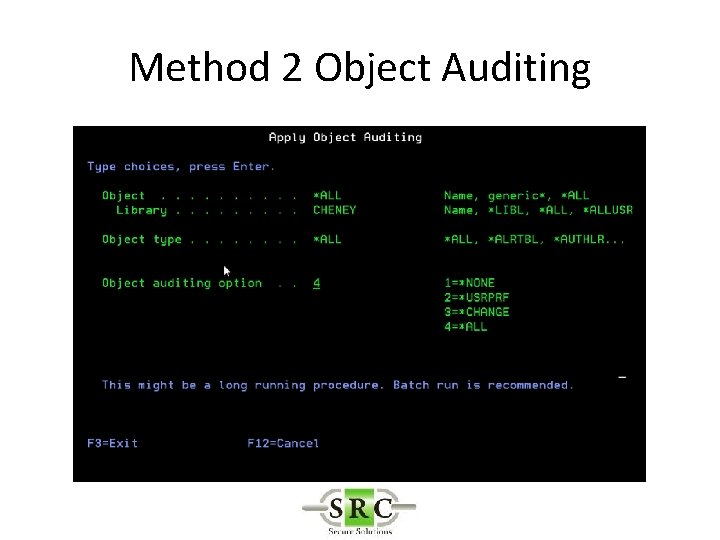
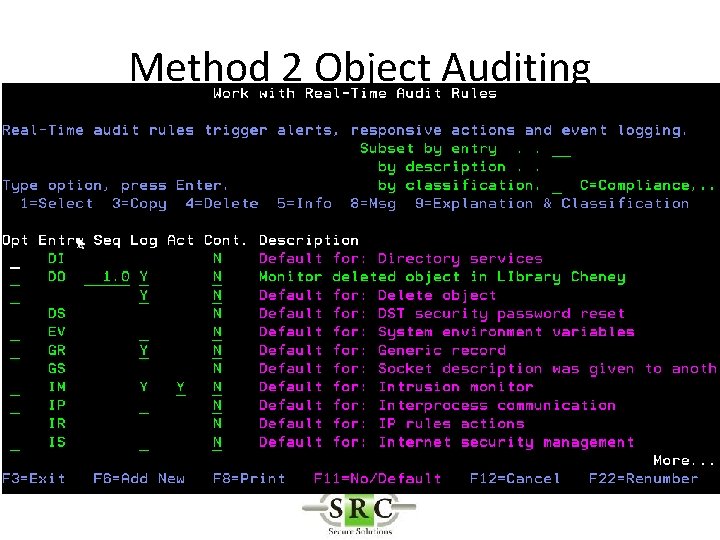
Method 2 Object Auditing

Method 2 Object Auditing

Method 2 Object Auditing

Method 2 Object Auditing

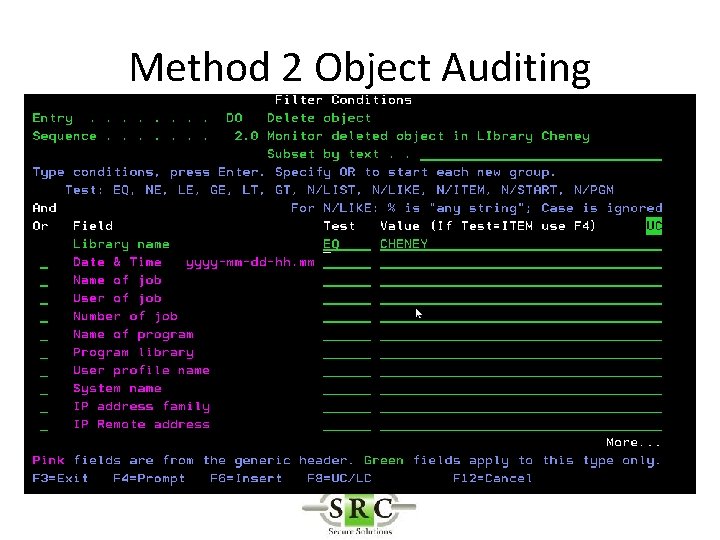
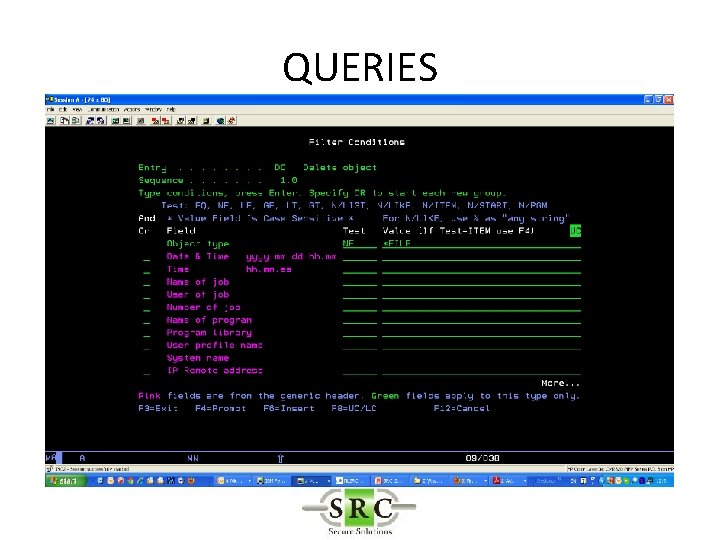
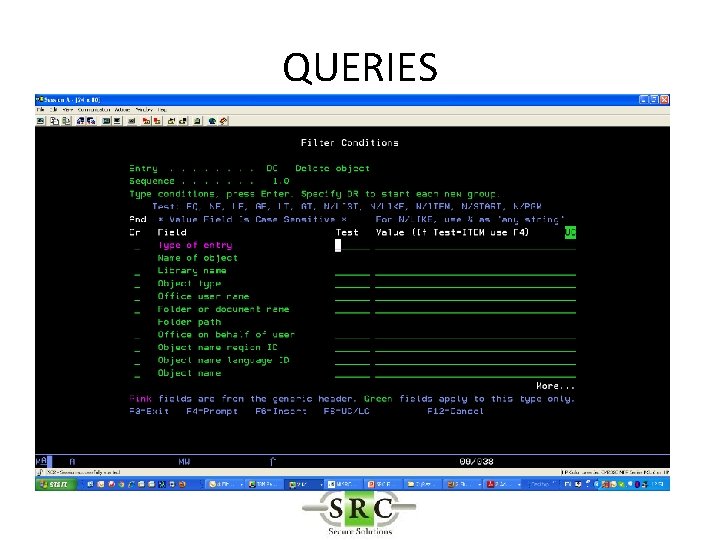
Filter Conditions • Filter criteria to limit application of Real-Time detection Rules to certain conditions • Will reduce the amount of data in the logs • Will allow selection for Action & Messaging (separate product) • Uses SQL like operators (EQ, NE, LE, GE etc)

Method 2 Object Auditing

Method 2 Object Auditing

Method 2 Object Auditing

Method 2 Object Auditing

Method 2 Object Auditing

Method 2 Object Auditing

Method 2 Object Auditing

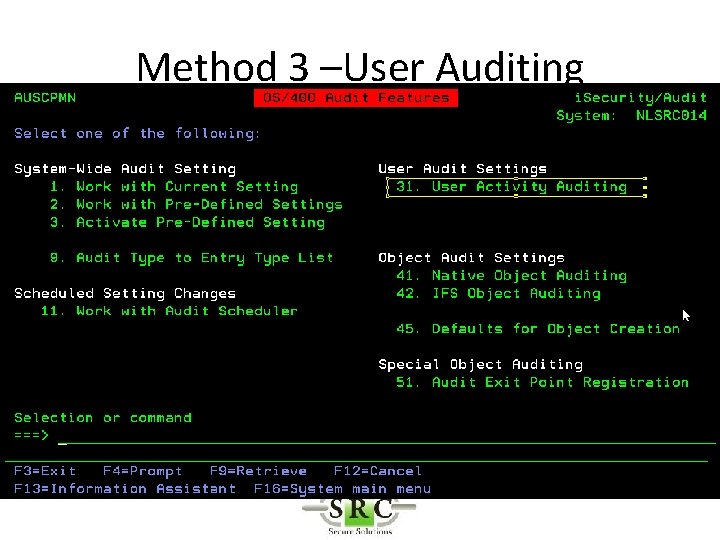
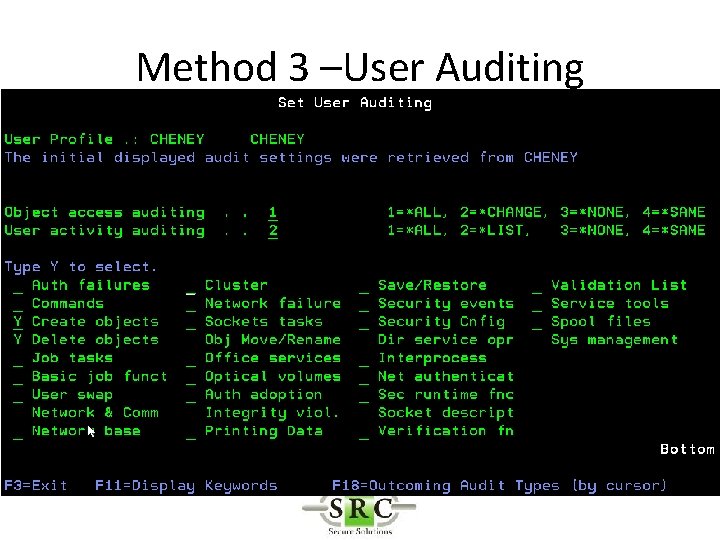
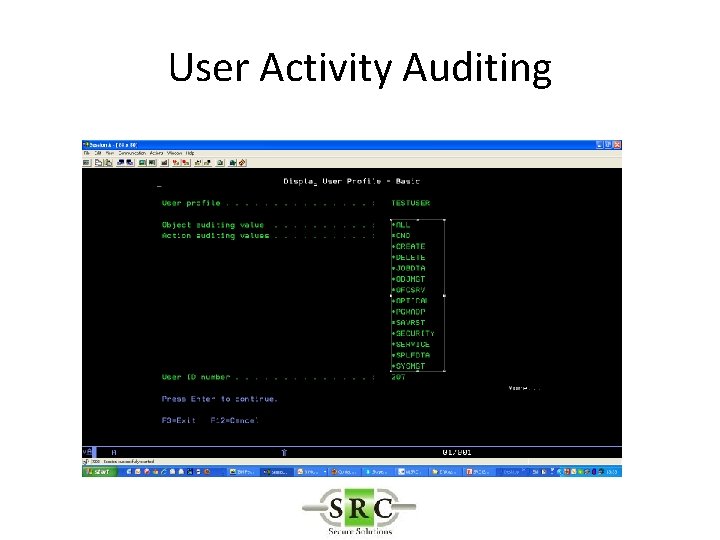
User Activity Auditing • Audit Powerful Users • Forensic auditing • User specific auditing (objects, commands, save/restore etc) • Requires AUDLVL set ‘on’ to create Audit Journal Entries

User Activity Auditing • Will log information only for selected users as opposed to all users • Example If *DELETE object is set on at a global level the audit log will be filled with many delete logs from everyday routines. • Selecting at User level will reduce logging to only the “interesting” users. • Independent of general auditing settings

Method 3 –User Auditing

Method 3 –User Auditing

Real Time Auditing

Real Time Auditing

Real Time Auditing

Real Time Auditing

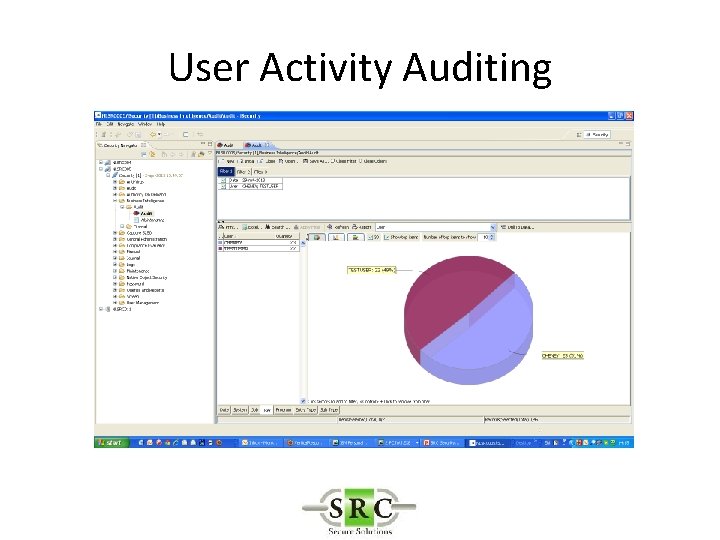
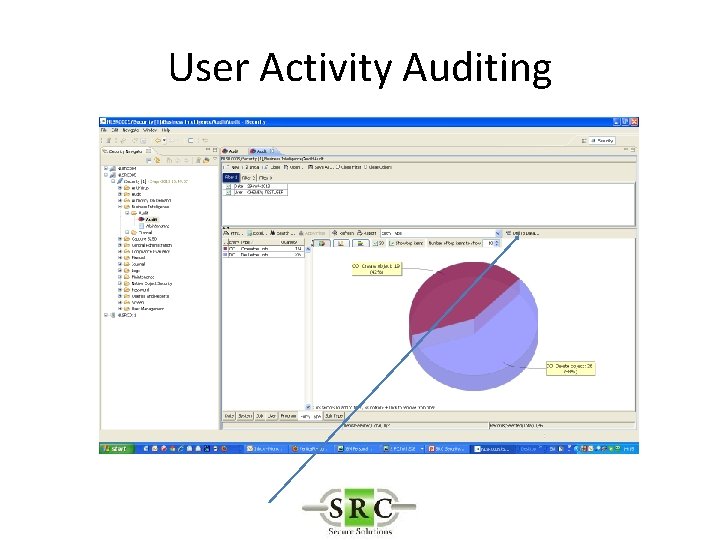
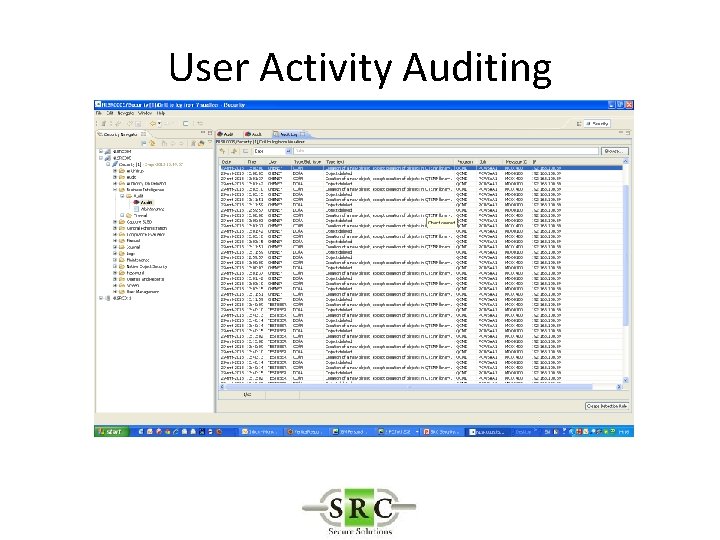
User Activity Auditing

User Activity Auditing

User Activity Auditing

User Activity Auditing

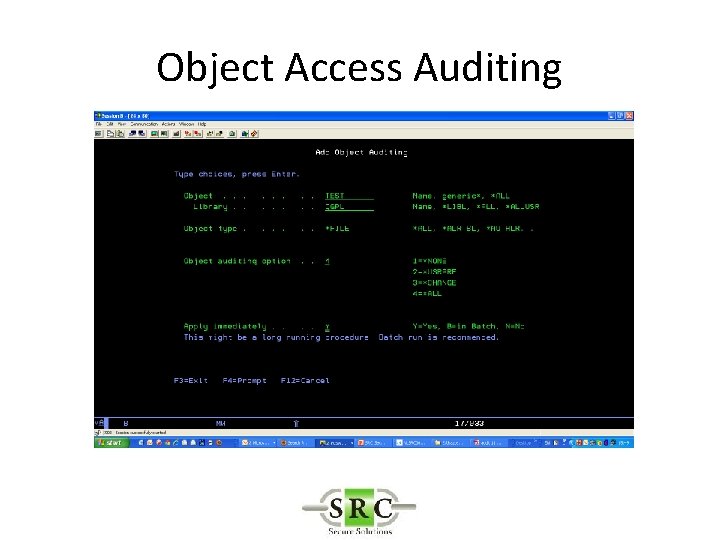
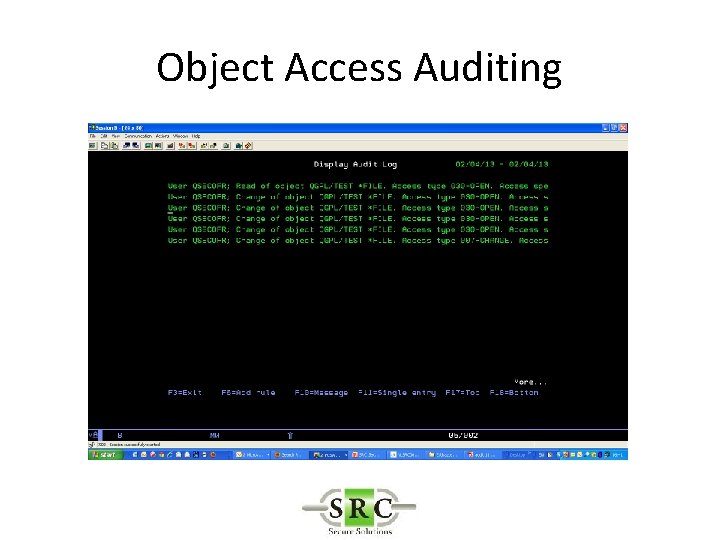
Object Access Auditing • Log access to critical objects – Database files – Source code – Important libraries – Independent of general auditing settings (*CHANGE etc)

Object Access Auditing

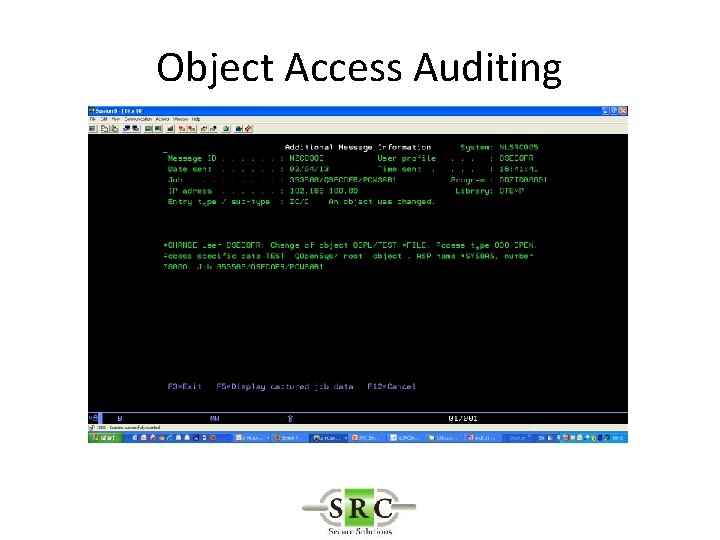
Object Access Auditing • Object auditing value (OBJAUD) • *NONE • Using or changing this object does not cause an audit entry to be sent to the security journal. • *USRPRF • The user profile of the user accessing this object is used to determine if an audit record is be sent for this access. The OBJAUD keyword of the CHGUSRAUD command is used to turn auditing on for a specific user. • *CHANGE • All change accesses to this object by all users are logged. • *ALL • All change or read accesses to this object by all users are logged.

Object Access Auditing

Object Access Auditing

Object Access Auditing

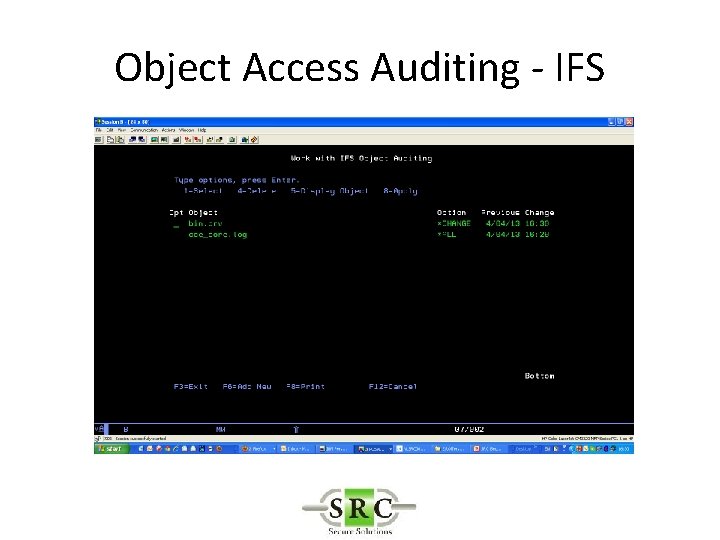
Object Access Auditing - IFS

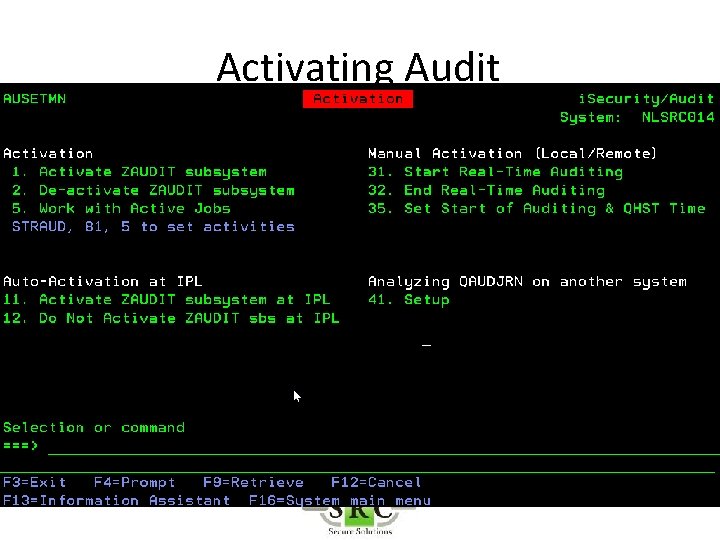
Activating Audit

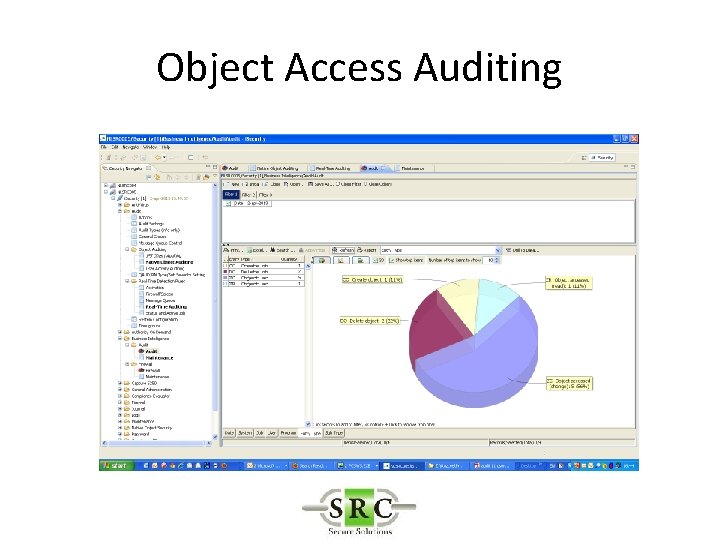
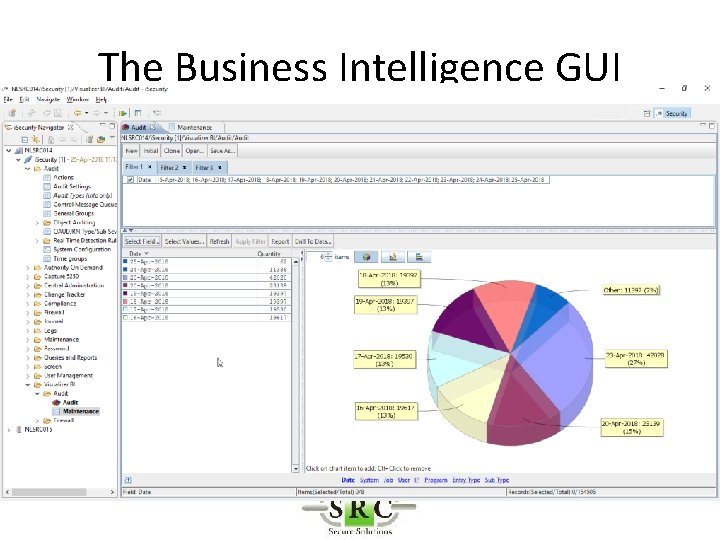
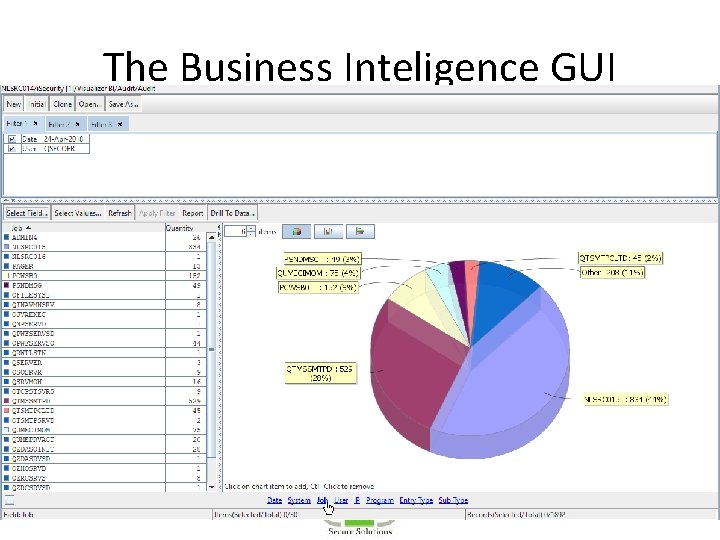
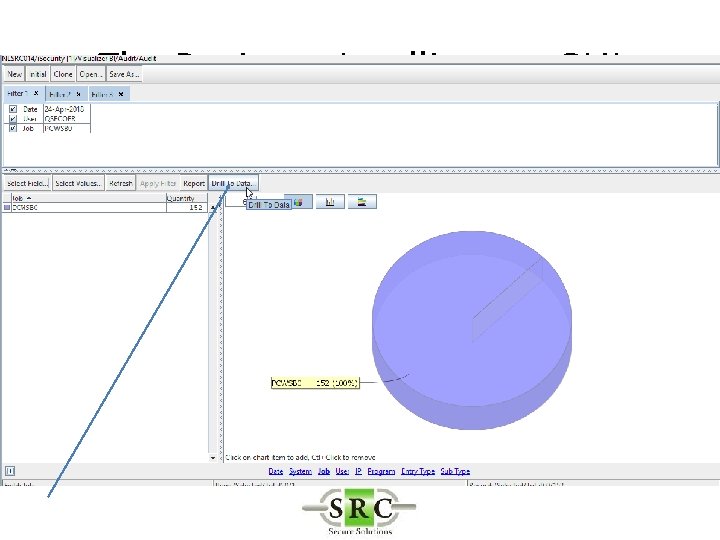
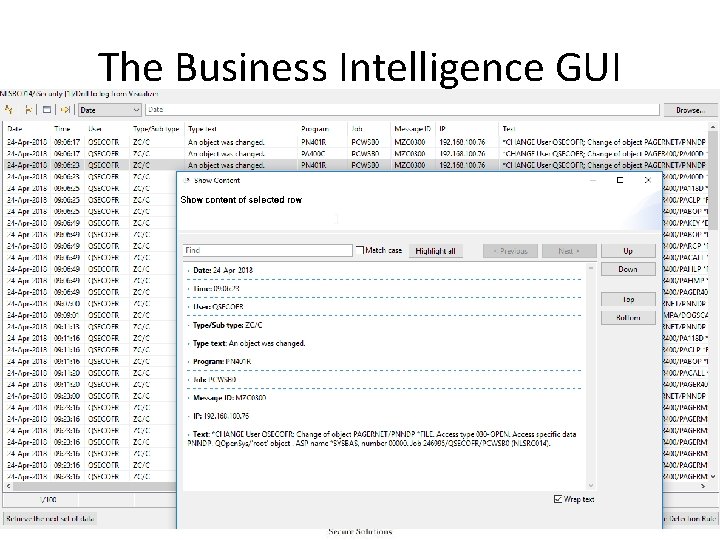
The Business Intelligence GUI

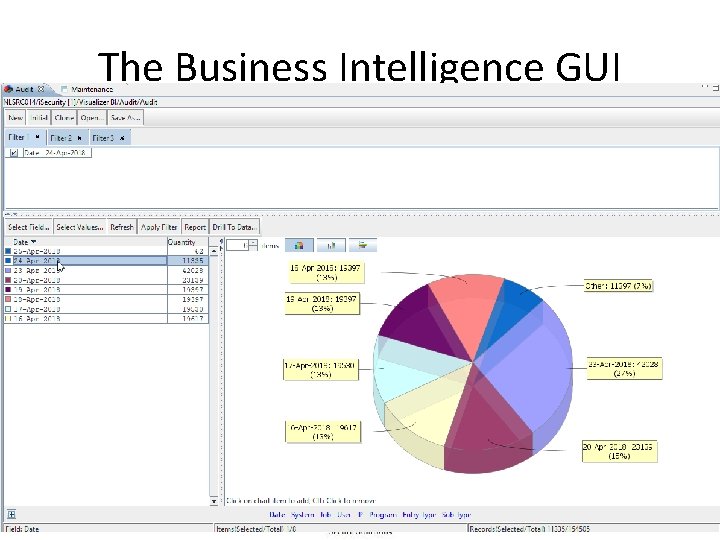
The Business Intelligence GUI

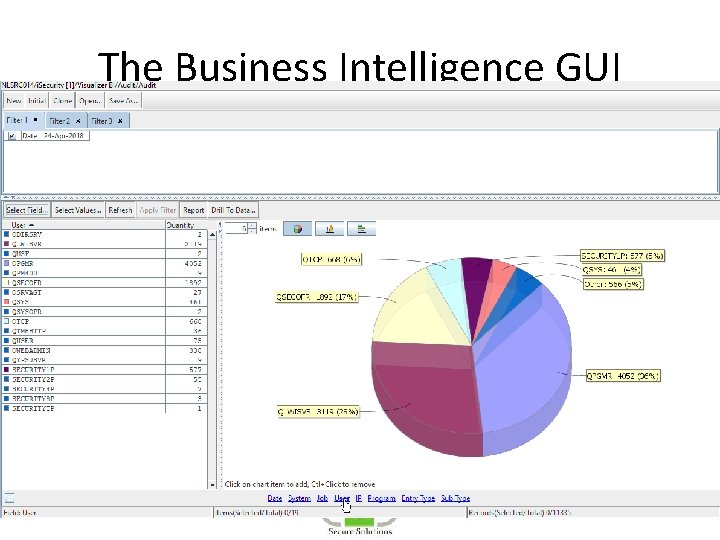
The Business Intelligence GUI

The Business Inteligence GUI

The Business Intelligence GUI

The Business Intelligence GUI

Queries & Reports • 250+ pre-defined queries & reports • Use Query Wizard to refine or create new ones • Display Log for quick & easy overview • Report Scheduler

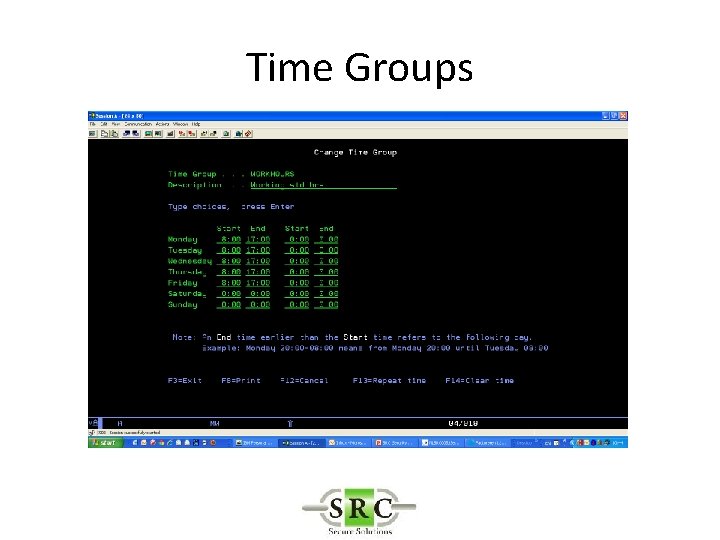
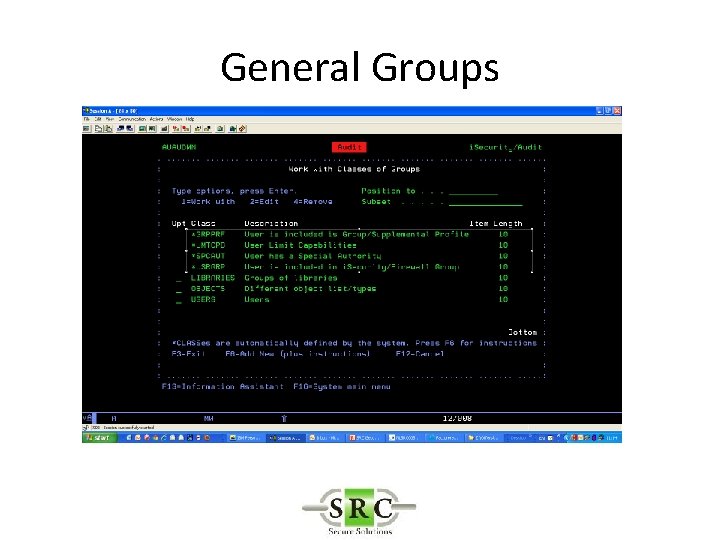
Queries & Reports • Groups • Used in queries also in settings • Time Groups – Shifts – Weekends – Etc • General Groups – User Groups (%group) » When *generic doesn’t work » To define users sharing the same authority – Object » Files, commands etc

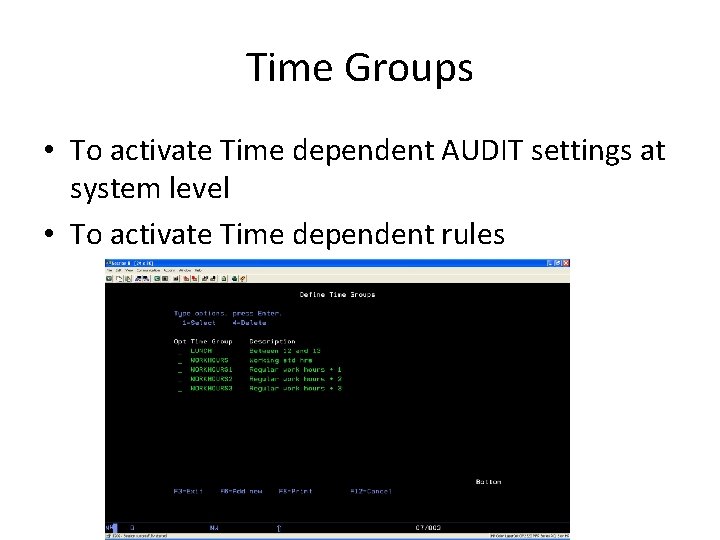
Time Groups • To activate Time dependent AUDIT settings at system level • To activate Time dependent rules

Time Groups

General Groups • Groups are built of – CLASS (TYPE) = e. g. OBJECTS, USERS, • GROUP = e. g. FINLIB, FINUSERS – ITEM = eg list of users within a group or… • *CLASSES – automatically defined by i. Security

General Groups

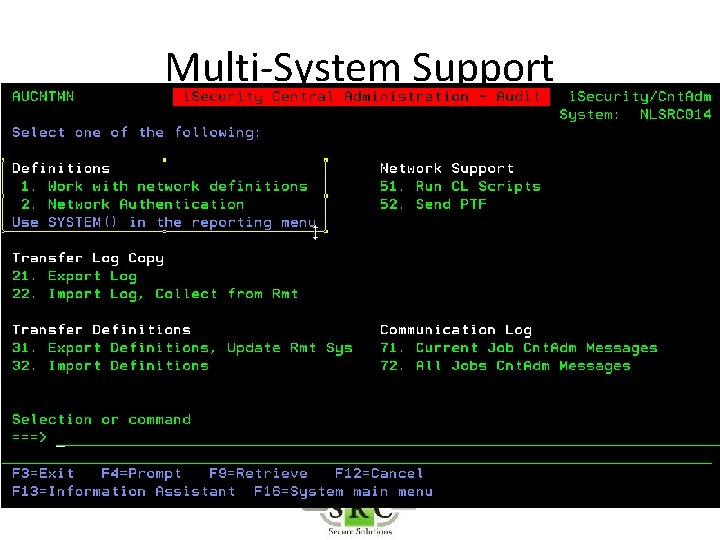
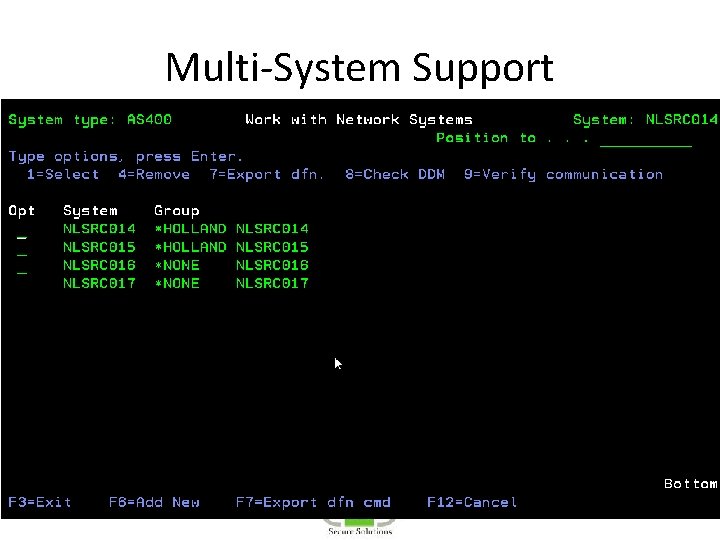
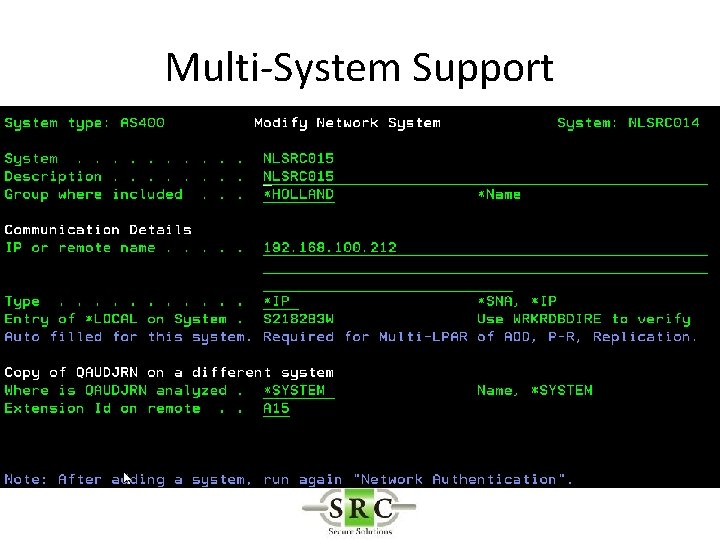
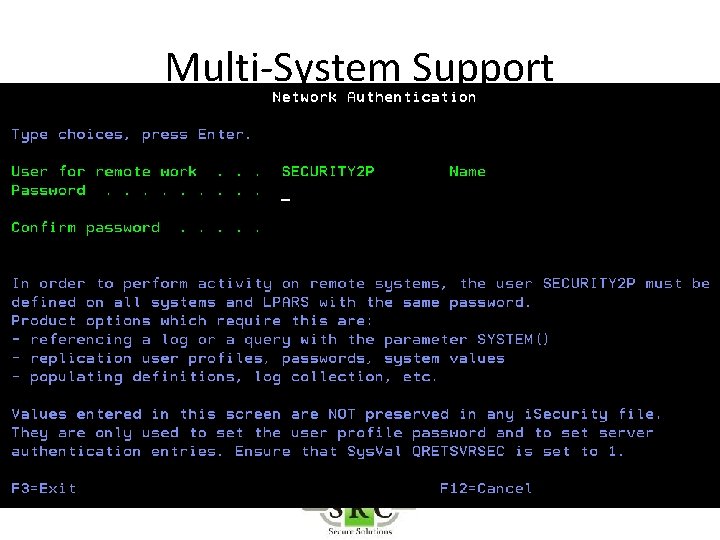
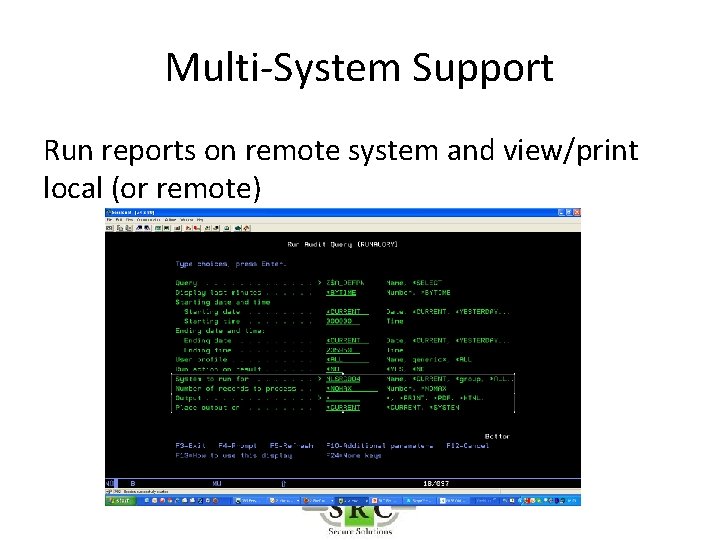
Multi-System Support • Run Remote reports on Local system – Copy Log from Remote to Local – *DDM server must be started on both systems • Run Remote Reports on Remote system – Requires *REXEC

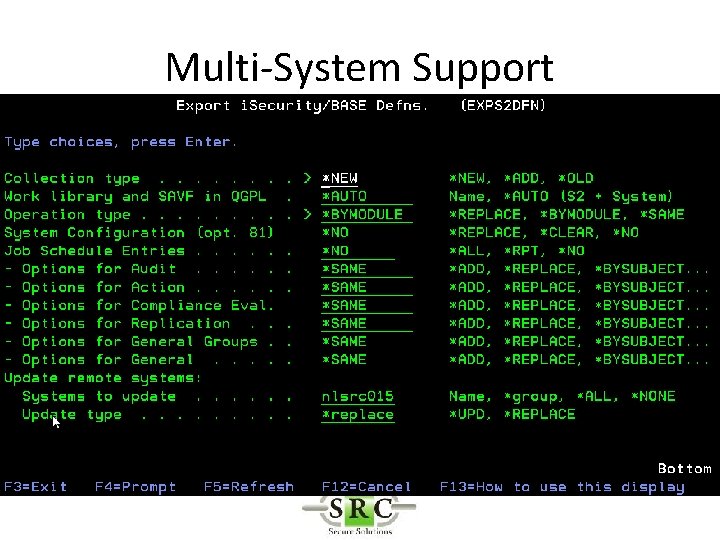
Multi-System Support • Export configuration to other systems • Export new versions and PTFs to other systems (ISECSETUP) – Upgrades – Keys – PTFs

Multi-System Support

Multi-System Support

Multi-System Support

Multi-System Support

Multi-System Support Run reports on remote system and view/print local (or remote)

Multi-System Support

ISECSETUP • • **Multi-System/Multi-Lpar assisting programs ** (c) Raz-Lee 2011 • • The attached programs are intended to automate the process of: - Install/upgrade products licensed to the System/Lpar - Apply the authorization code - Perform automatic authorization code change at SWAP (hot or regular) • • • *Preparation* ------Download the attached to a previously created *SAVF. - CRTLIB ISECSETUP -or- CLRLIB ISECSETUP if it exists - RSTOBJ *ALL QTEMP *SAVF RSTLIB(ISECSETUP) SAVF(. . . ) • • • *Adding products to install/upgrade* ------------------If only authorization code change is required, skip this part. Download the products using the links sent to you separately, UNZIP each of them and move the. A 2 P file to a corresponding *SAVF in library ISECSETUP. The corresponding names are based on first 2 chars: GS. . . -> SMZ 8 AU. . . -> SMZ 4 VW. . . -> SMZ 5 AV. . . -> SMZV FS. . . -> SMZ 1 JR. . . -> SMZJ CA. . . -> SMZC OD. . . -> SMZO DB. . . -> SMZB WS. . . -> SMZ 7 TL. . . -> SMZ 2 CS. . . -> SMZ 6 OS. . . -> SMZ 9 DS. . . -> SMZD TR. . . -> SMZT MG. . . -> SMZM • • • *Distribution* -------Distribute the ISECSETUP to all Systems/Lpars. In each use: - CALL ISECSETUP/SETUPALL *ALL to install/upgrade & set authorization - CALL ISECSETUP/SETUPALL *AUT to set authorization (regular swap) - Add ISECSETUP/SETUPEXIT to QIBM_QWC_RESUME for hot swap • • • *Activity Log* -------Use DSPMSG QGPL/SETUPALL to display

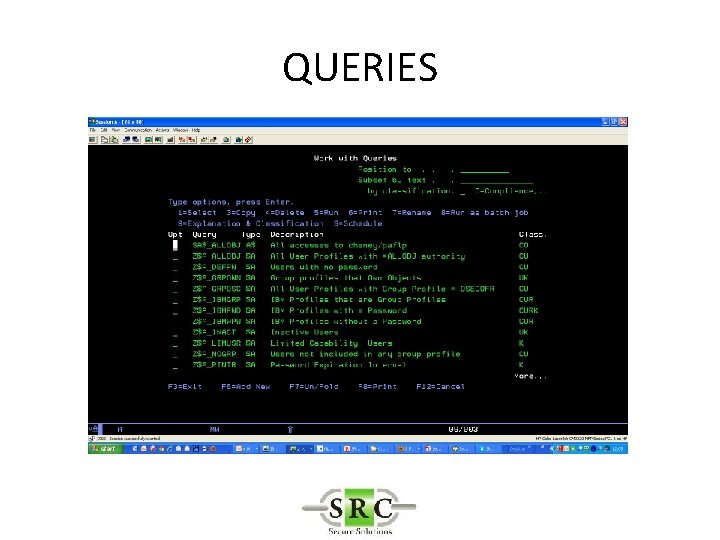
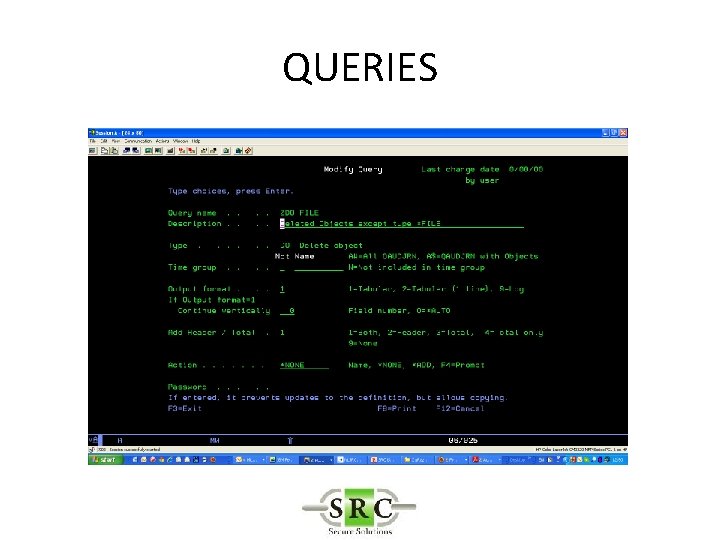
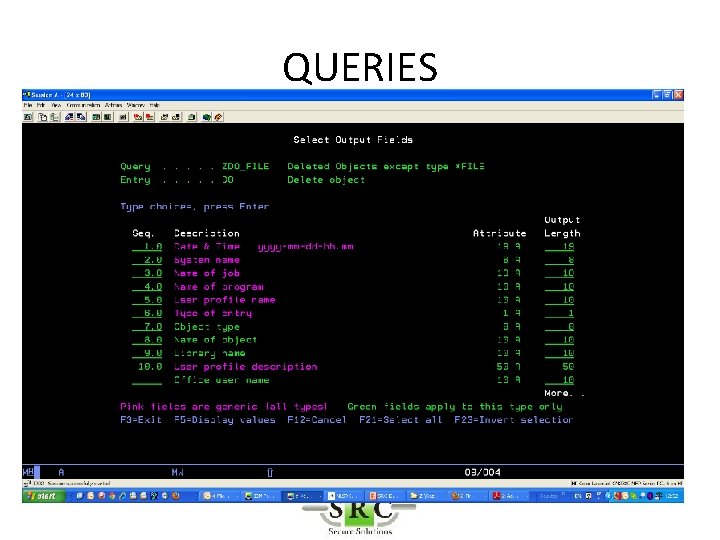
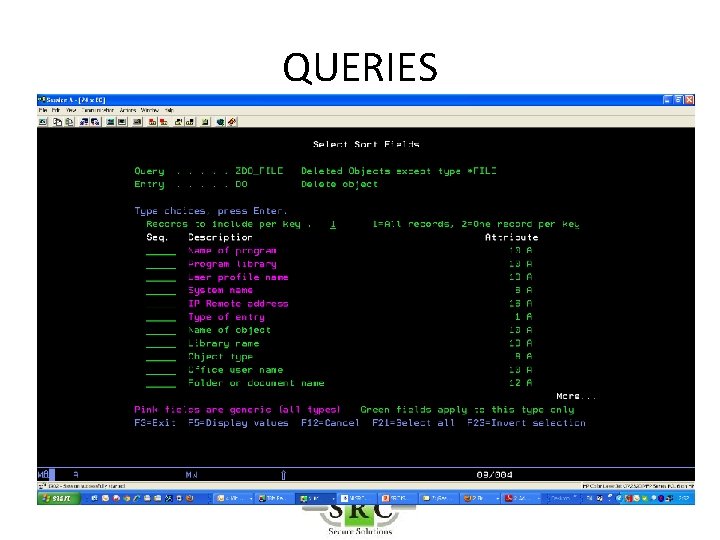
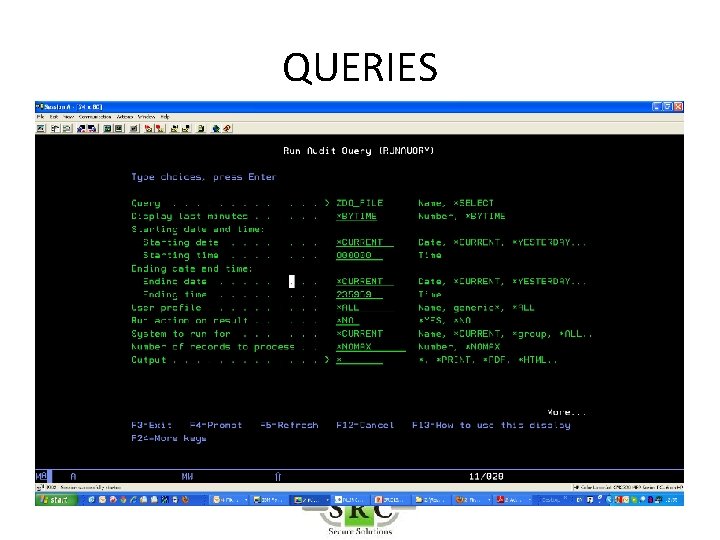
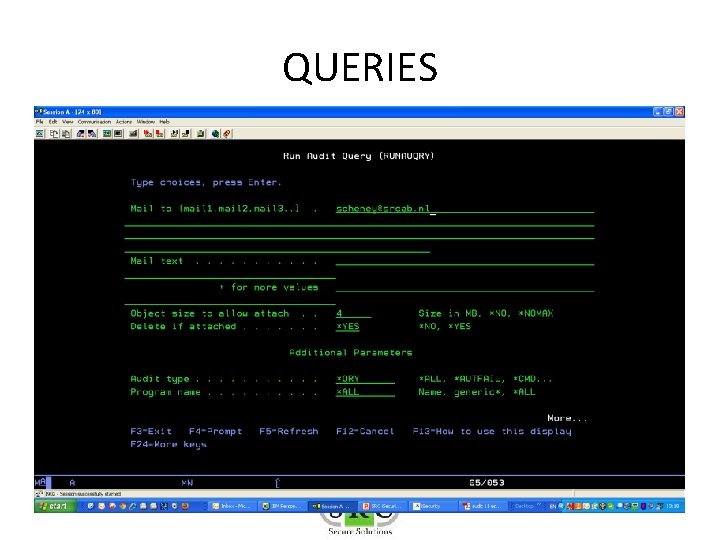
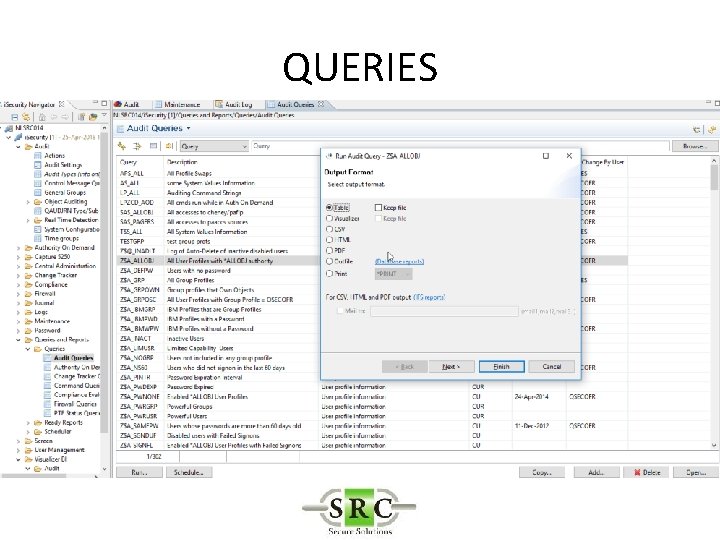
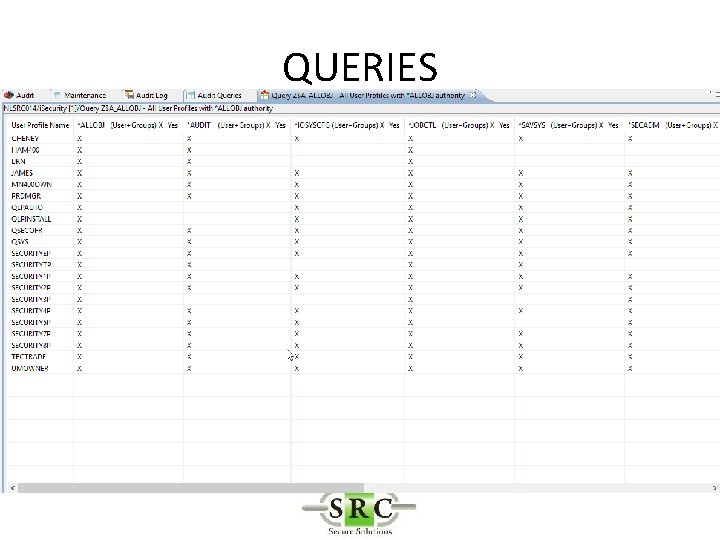
QUERIES • Over 250 pre-defined queries & reports – Z$ = Configurationreports (eg Users with high authority) – ZAD = Auditing Changes – ZAF = Authority Failures – ZC = Object changes – etc • Copy/change/create queries using Wizard • Display, Print, HTML, PDF, email, BI • Schedule

QUERIES

QUERIES

QUERIES

QUERIES

QUERIES

QUERIES

QUERIES

QUERIES

QUERIES

QUERIES

QUERIES

Examples • Users logging on outside office hours • AUDJRN entry types = JS/S, JS/E job start & job end • Select only interactive (log-on) jobs • Shift settings for outside office hours OR collect at all times and select outside office hours during query

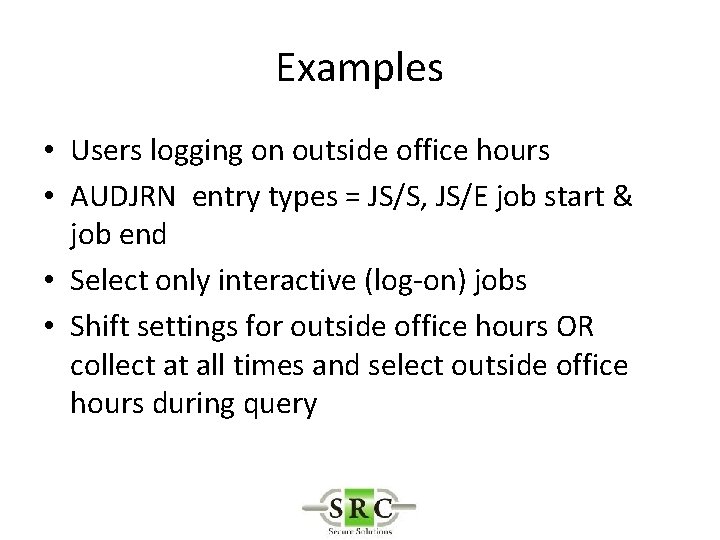
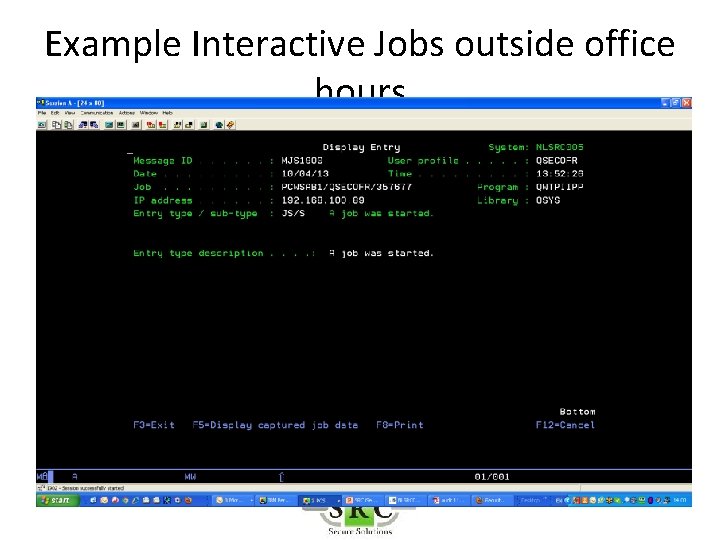
Example Interactive Jobs outside office hours • Ensure that JS entries are audited – Audit setting *JOBDTA is set ON

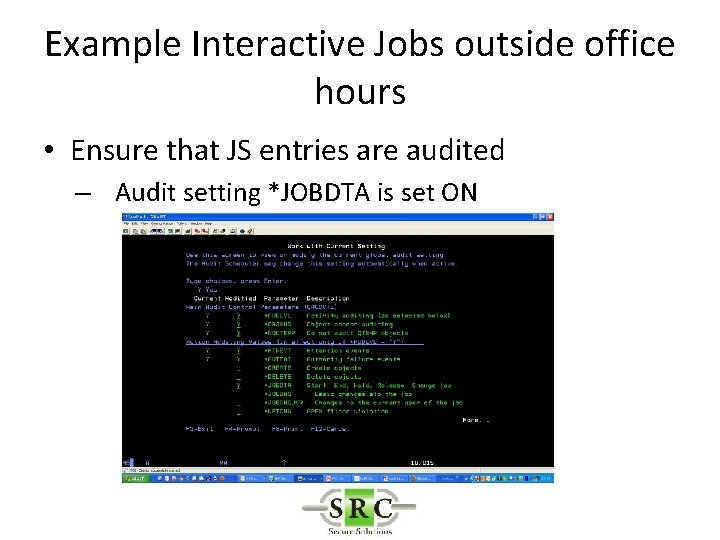
Example Interactive Jobs outside office hours • Ensure that the JS entries are copied to the Real-Time AUDIT LOG

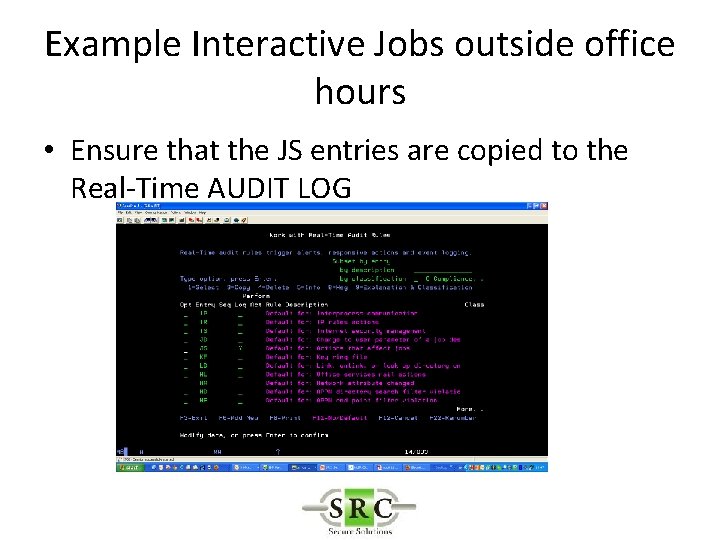
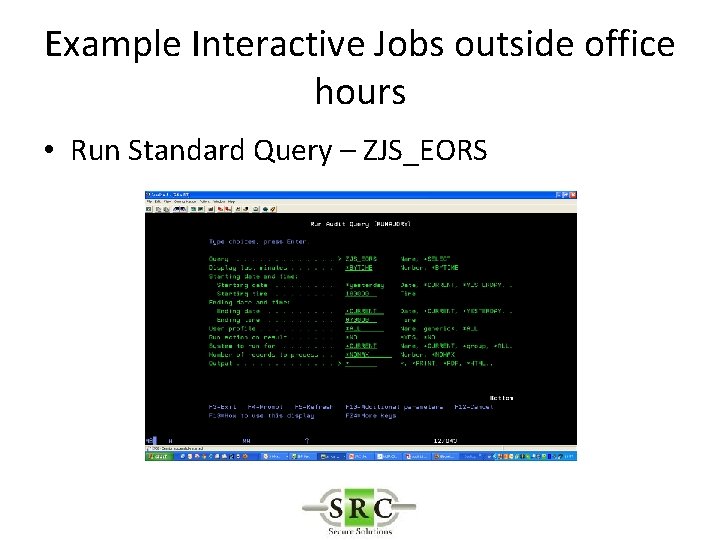
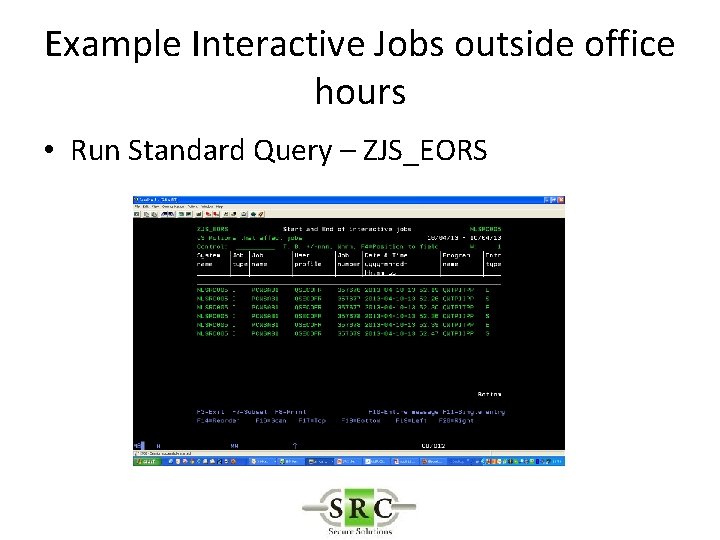
Example Interactive Jobs outside office hours • Run Standard Query – ZJS_EORS

Example Interactive Jobs outside office hours • Run Standard Query – ZJS_EORS

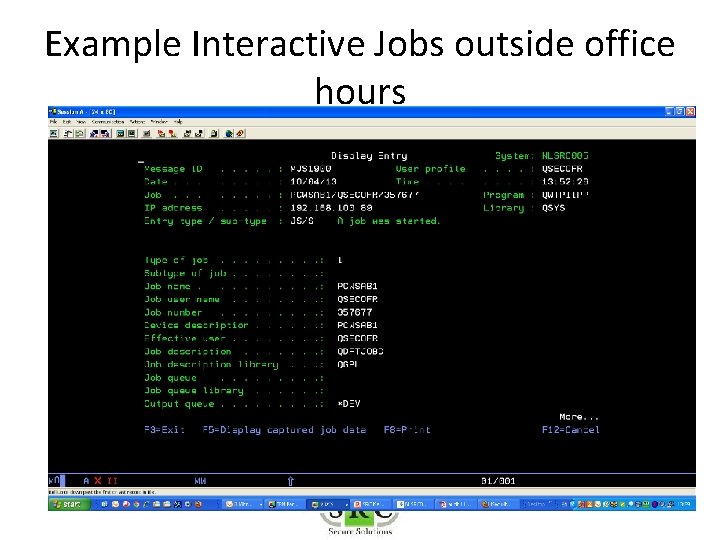
Example Interactive Jobs outside office hours

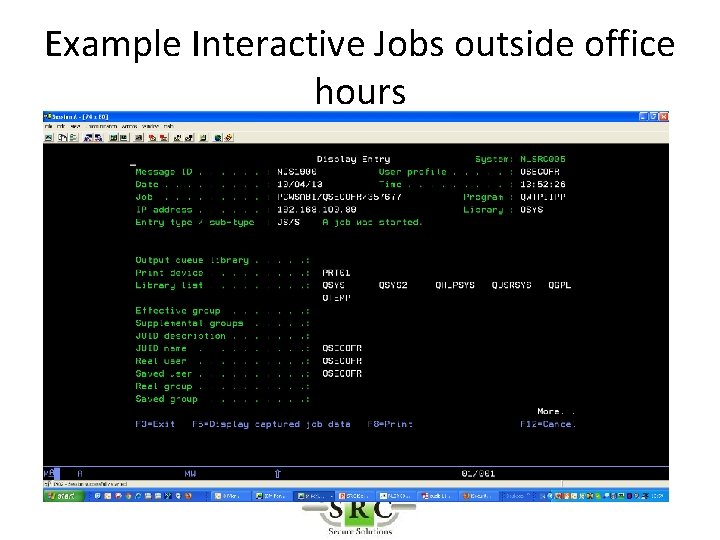
Example Interactive Jobs outside office hours

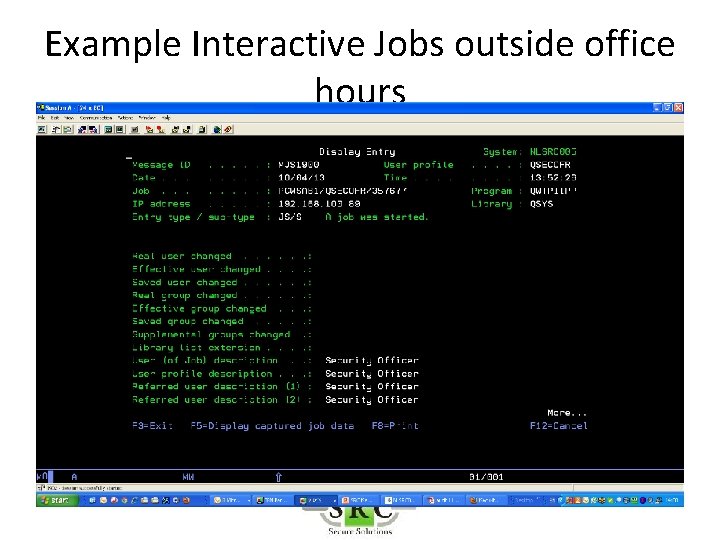
Example Interactive Jobs outside office hours

Example Interactive Jobs outside office hours

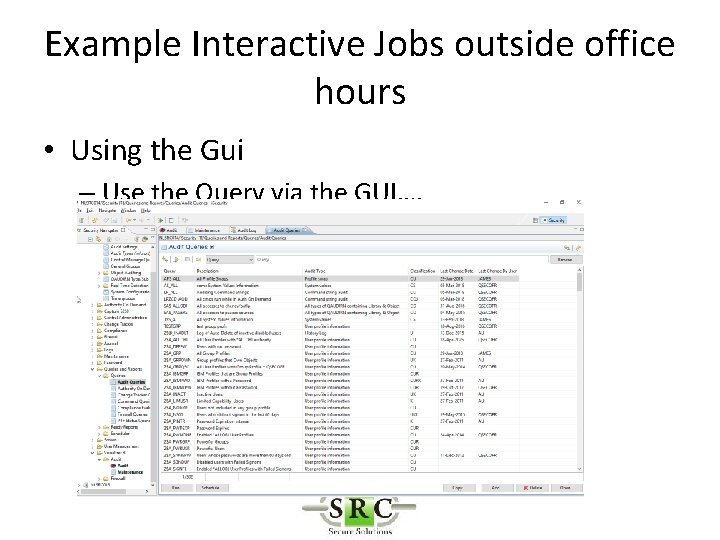
Example Interactive Jobs outside office hours • Using the Gui – Use the Query via the GUI….

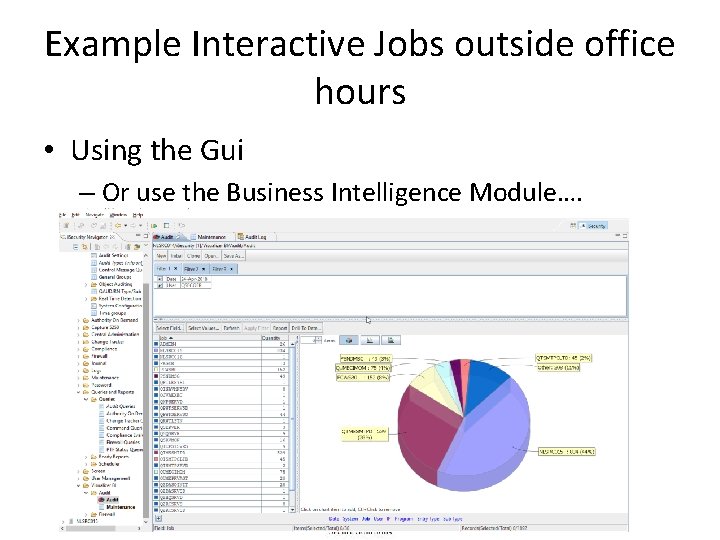
Example Interactive Jobs outside office hours • Using the Gui – Or use the Business Intelligence Module….

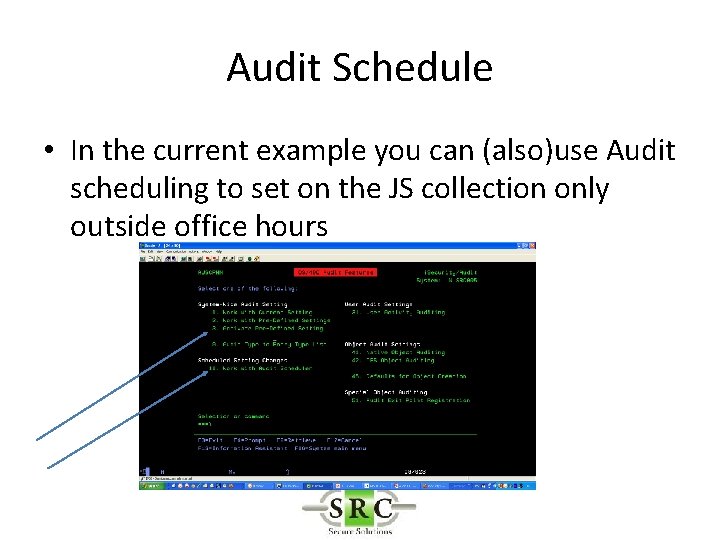
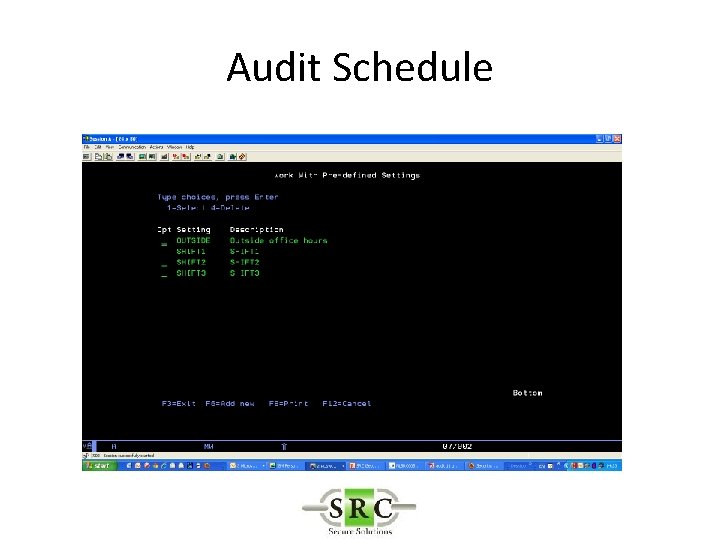
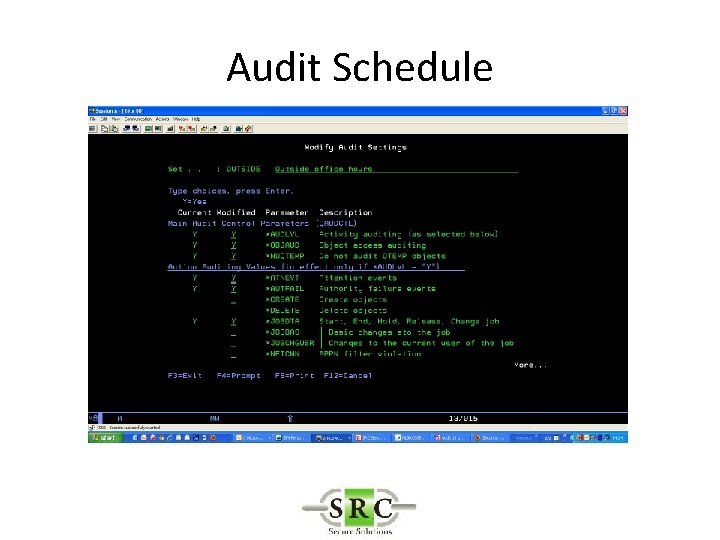
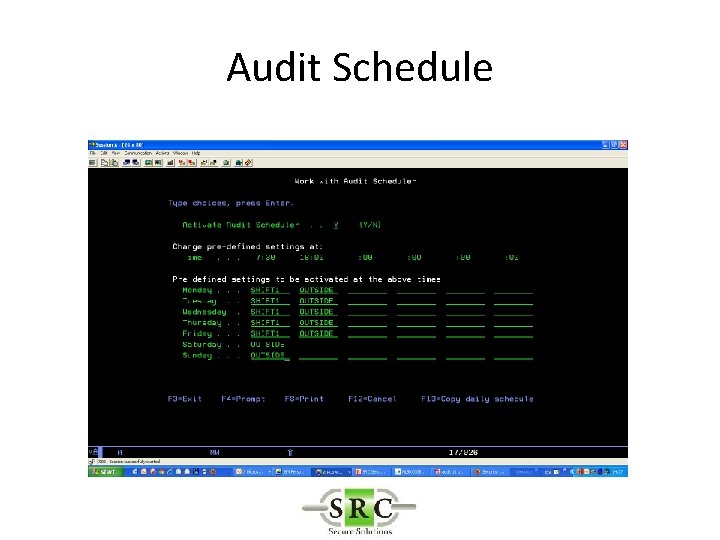
Audit Schedule • In the current example you can (also)use Audit scheduling to set on the JS collection only outside office hours

Audit Schedule

Audit Schedule

Audit Schedule

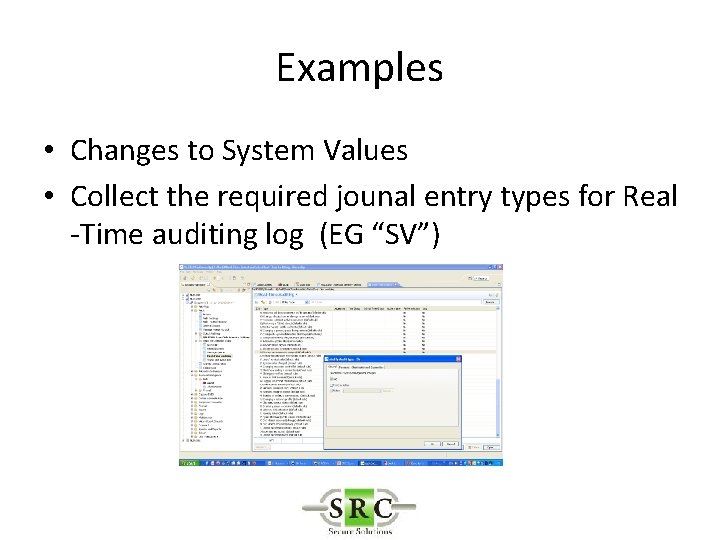
Examples • Changes to System Values • Look through the Audit Entry list to see which entries you need to add to the Audit Journal. – *SECURITY , *SYSMGT, etc?

Examples • Changes to System Values • Collect the required jounal entry types for Real -Time auditing log (EG “SV”)

Examples • Changes to System Values • Copy/Change a standard query (e. g. ZSV_ALL) to creat list of ‘interesting’ events

Examples • All activities of users with SECOFR rights • User Activity Auditing to select required users • No need to activate lower level global auditing as user auditing will create these entries.

Examples • All activities of users with SECOFR rights • Collect the required jounal entry types for Real -Time auditing log • Change/Run appropriate query eg ZC@_OBJ (Users with All Object Auth) – In other words –look around for standard queries with similar intentions and change accordingly

Installation & System Configuration • Use the Manual! – Installation – Activation – Operators – Syslog – Systems in Network – Housekeeping – etc