SECURITY TRAINING AND THREAT AWARENESS Topics 1 Suspicious






















- Slides: 26

SECURITY TRAINING AND THREAT AWARENESS

Topics 1. Suspicious Persons 2. Suspicions Activities 3. Suspicious Objects or Packages 4. Employee Identification 5. Visitor Controls 6. Computer Security 7. Document Security

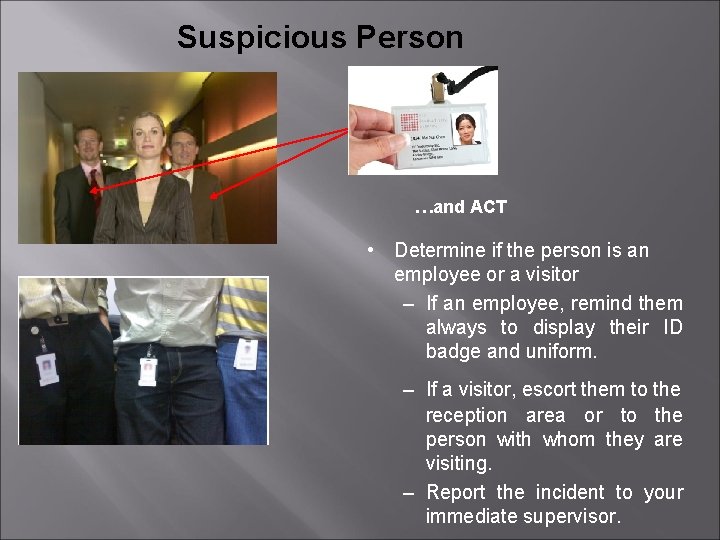
Suspicious Person LOOK FOR…. . • Any person without an employee badge, visitor badge or uniform.

Suspicious Person …and ACT • Determine if the person is an employee or a visitor – If an employee, remind them always to display their ID badge and uniform. – If a visitor, escort them to the reception area or to the person with whom they are visiting. – Report the incident to your immediate supervisor.

Suspicious Persons LOOK FOR…. . Any person in unauthorized/restricted areas

Suspicious Persons AND ACT…. . Get them out of the area If a visitor, escort them to the reception area. Report the incident to your immediate supervisor

Suspicious Person Look for …. Any person: wearing an overcoat on a 95 degree day, or any kind of inappropriate clothing waiting or loitering in an area or hallway asking for an unknown department, person or employee

Suspicious Person LOOK FOR…. Any person: who seems not to belong in the area going door to door, office to office entering a private office unescorted selling items who seems lost

Suspicious Persons Cam 7 1: 17: 23 AM 8/02/06 LOOK FOR …. . Any person: Tampering with somebody’s desk, boxes, personal items, equipment, vehicles, cameras, lights… running, especially if carrying something hiding behind doors, fences, desks, …

Suspicious Persons AND ACT……… Immediately report the incident to your immediate supervisor

Suspicious Activity LOOK FOR … Objects obstructing access points Disconnected or obstructed cameras Broken locks or access control systems Unexplained clutter or debris Objects thrown from a vehicle, especially while traveling at a high speed.

Suspicious Activity ACT … Immediately report any suspicious activity to your supervisor.

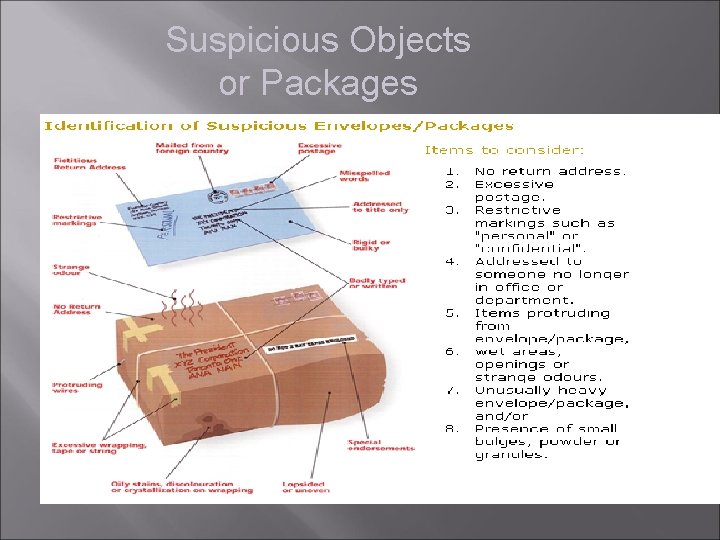
Suspicious Objects or Packages LOOK FOR…. • Unexplained objects or packages that look strange or do not belong to the area • Strange markings on boxes (unknown code, color) or strange characteristics (weight, number, odd shape) • Strange leaking substance (powder, liquid, etc…) • Suspicious objects in the middle of an area (e. g. , hallway, lobby,

Suspicious Objects or Packages

Suspicious Objects or Packages AND ACT……… Immediately report any suspicious packages or objects to your supervisor, security, local police, 911 and/or FBI.

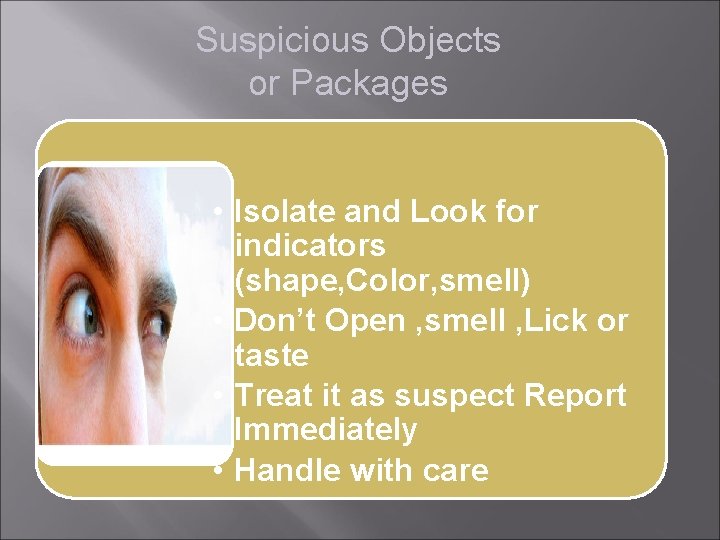
Suspicious Objects or Packages • Isolate and Look for indicators (shape, Color, smell) • Don’t Open , smell , Lick or taste • Treat it as suspect Report Immediately • Handle with care

Employee Identification Your Responsibilities While on company property Your company identification badge must be properly displayed and worn at all times. Your company uniform (if applicable) must be worn at all times. Properly secure and protect your ID badge, uniform, keys and access control card, etc.

Visitor Controls Visitor Pre-meeting Requirements Inform your visitor of the company’s visitor policies including photo identification, check in with receptionist prior to their visit. Visitor Entrance Requirements Ensure that your visitor has logged in and has been issued a visitor badge

Visitor Controls Visitor Escort Requirements You must escort your visitors at ALL times Do not leave your visitor unattended Visitor Exit Requirements Ensure that your visitor has logged out and has returned the visitor badge to the guard or receptionist

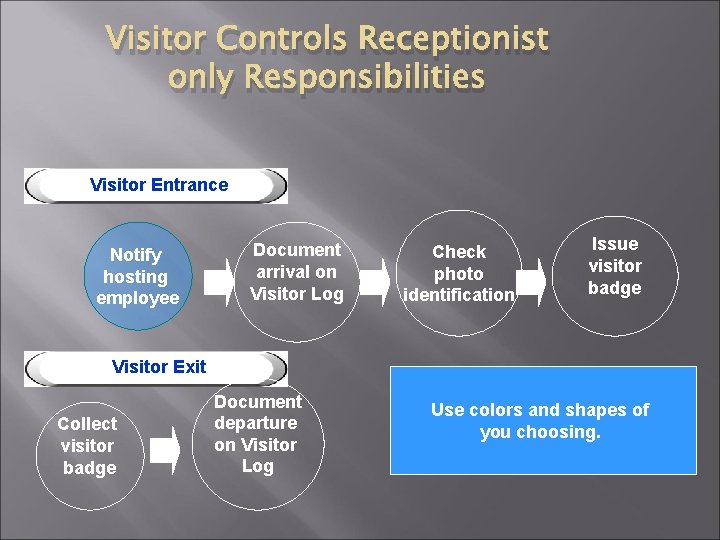
Visitor Controls Receptionist only Responsibilities Visitor Entrance Notify hosting employee Document arrival on Visitor Log Check photo identification Issue visitor badge Visitor Exit Collect visitor badge Document departure on Visitor Log Use colors and shapes of you choosing.

Computer Security Do not share access to your computer with strangers Log-off when you leave your computer Passwords should be changed every 60 to 90 days Do not share your password with anyone Do not write down your password.

Computer Security Selecting a Password Use hard-to-guess passwords Do not use the same password in more than one place A password should have a mix of letters, numbers and symbols I Love to be Secure i. L 2 bs@ Always on time to work !Ao. T 2 wx My Password is Very Secure My. P 1 VS# Yo Quiero Taco Bell yqtb!10

Computer Security Electronic Mail Restrictions • Do not use company e-mail for private business activities, amusement or entertainment. • Do not send e-mail containing racist, sexist, threatening or other objectionable language. • Do not join mailing lists. • Do not open unknown or unexpected e-mail attachments.

Let’s review… • Suspicious persons • Suspicious activity • Suspicious objects or packages • Employee identification • Visitor controls • Computer security • Document security • Information technology security

Security is not out of reach if you practice it every day.

QUESTIONS?