Defense Security Service DSS Update DSS Changing With













- Slides: 16

Defense Security Service

DSS Update DSS Changing With A Changing Security Environment

DSS Update FY 12 in Review: • Conducted 8, 162 security vulnerability assessments • Identified 12, 700 security vulnerabilities, tracked all through mitigation • 3, 150 FCL requests processed vice 2, 500 in FY 11 § Issued 1, 968 facility security clearances (1, 558 final, 410 interims) • Issued 6, 574 accreditations § 2, 397 ATOs, average 83 days § 2, 479 IATOs, average 15 days § 1, 698 Straight to ATO, average 14 days • 234, 686 Adjudication actions § IRTPA - average 8 days • Made 355 cyber notifications

DSS Update FY 12 in Review • Changed vernacular: § Assessments vs Inspections § Vulnerabilities vs Deficiencies and Findings • New Workload Prioritization – “Right Facility at the Right Time” § Focus on identification and mitigation of security vulnerabilities • Security Rating Matrix • Implemented Cyber Notification Process • Initiated pre-CCRI visits and continued preparation to assume mission from DISA • DISCO merged into the Do. DCAF § Stand-up of Personnel Security Management and Oversight for Industry (PSMO-I)

DSS Update FY 12 in Review • VOI Survey Results § 94% satisfied/somewhat satisfied with DSS guidance and support § 87% agree that their facility has a strong partnership with DSS § 90% rated DSS as excellent/good in the area of industrial security program vulnerability identification and mitigation • Two New Regional Directors Selected – Southern Region and Capital Region • Partnership with Industry § 17 exchanges § 17 active industry partners § 25 exchanges planned for FY 13

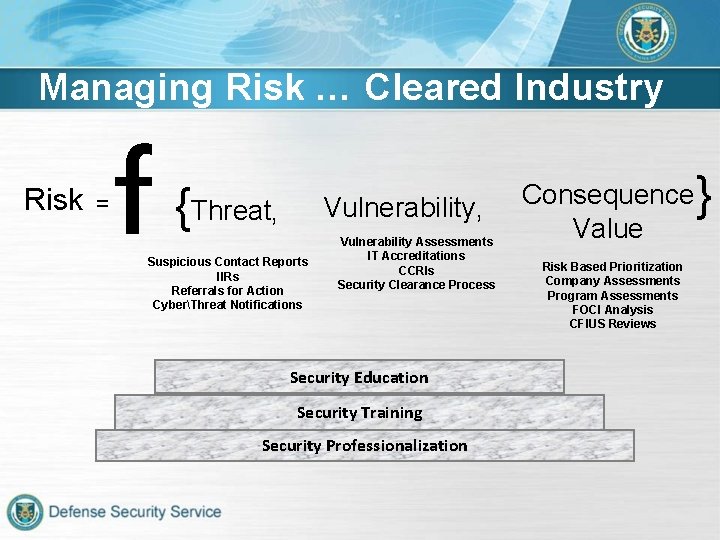
Managing Risk … Cleared Industry = f { Vulnerability, Threat, Suspicious Contact Reports IIRs Referrals for Action CyberThreat Notifications Vulnerability Assessments IT Accreditations CCRIs Security Clearance Process Security Education Security Training Security Professionalization Consequence Value Risk Based Prioritization Company Assessments Program Assessments FOCI Analysis CFIUS Reviews { Risk

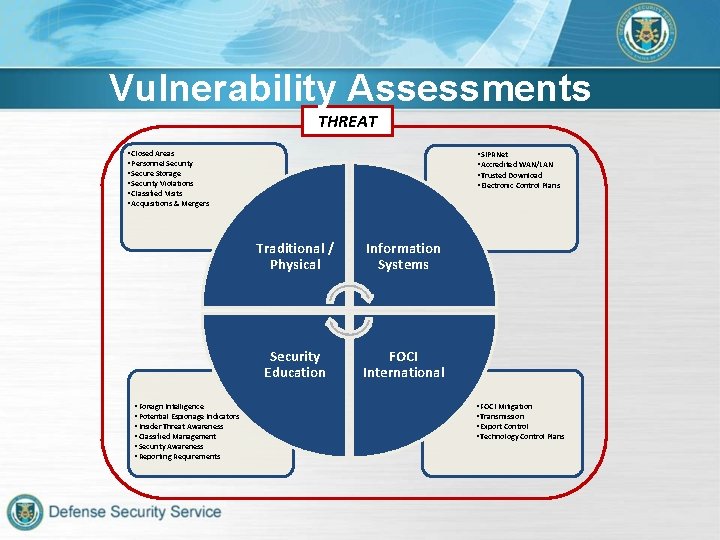
Vulnerability Assessments THREAT • Closed Areas • Personnel Security • Secure Storage • Security Violations • Classified Visits • Acquisitions & Mergers • Foreign Intelligence • Potential Espionage Indicators • Insider Threat Awareness • Classified Management • Security Awareness • Reporting Requirements • SIPRNet • Accredited WAN/LAN • Trusted Download • Electronic Control Plans Traditional / Physical Information Systems Security Education FOCI International • FOCI Mitigation • Transmission • Export Control • Technology Control Plans

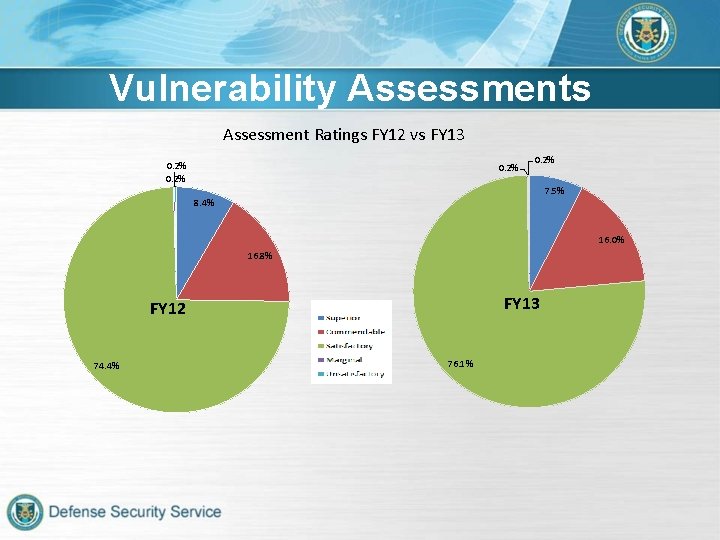
Vulnerability Assessments Assessment Ratings FY 12 vs FY 13 0. 2% 7. 5% 8. 4% 16. 0% 16. 8% FY 13 FY 12 74. 4% 76. 1%

Vulnerability Assessments Top Ten Vulnerabilities (49% of total): • 02 -200 Personnel Security Clearances - General (incl. 02 -200 B Deny Access for Deny Revoke or Suspension PCLs) • 02 -202 Procedures for Completing the Electronic Version of the SF 86 (incl. 02 -202 A SF 86 Data Protection and Official Use, 02 -202 B SF 86 Data Retention and Destruction) • 03 -107 Refresher Training • 08 -602 Audit Capability (incl. 08 -602 A 1 Automated Audit Trail, 08 -602 A 3 Audit Trail Analysis) • 03 -102 FSO Training • 01 -304 Individual Culpability Reports • 01 -206 Security Reviews (incl. 01 -206 B Contractor Reviews) • 01 -302 Reports to be Submitted to the CSA (incl. 01 -302 G Change Conditions Affecting the FCL) • 02 -212 Consultants • 10 -706 NATO Briefings

Vulnerability Assessments • Top Ten Acute/Critical Vulnerabilities (59% of total): • 08 -602 Audit Capability (incl. 08 -602 A 3 Audit Trail Analysis) • 02 -200 - PERSONNEL SECURITY CLEARANCES - General (incl. 02 -200 B Deny Access for Deny Revoke or Suspension PCLs) • 08 -202 Accreditation • 01 -302 Reports to be Submitted to the CSA (incl. 01 -302 G Change Conditions Affecting the FCL) • 02 -104 PCLs Required in Connection with the FCL • 02 -201 Investigative Requirements • 08 -305 Malicious Code • 01 -303 Reports of Loss, Compromise, or Suspected Compromise • 08 -311 Configuration Management • 05 -309 Changing Combinations (incl. 05 -309 B Employee with Knowledge Combination Change)

IT Vulnerabilities Top five deficiencies we’re seeing in System Security Plans: • SSP was incomplete or missing attachments • Inaccurate or incomplete configuration diagram • Sections in general procedures contradict protection profile • Integrity & availability not properly addressed • SSP was not tailored to the system Top five vulnerabilities we’re seeing during visits: • Inadequate auditing controls • Security Relevant Objects not protected • Inadequate configuration management • Improper session controls • Identification & authentication controls

CI Integration CI Award • 20% of industry is reporting – Only 10% reporting “actionable” SCRs § Goal is 40% of industry reporting “actionable” SCRs • Cyber Incident reporting has doubled, still ~ three (3) percent New CI awareness and analytical products • Better define threat • More timely, focused products -- individual company assessments • Expanded distribution of products • Pushing classified threat, including cyber • Deeper look into supply chain and unclassified subcontract vulnerabilities New CI course, Thwarting the Enemy • 40, 000 course completions in first year

Education and Training • Training Initiatives • Two curriculum tracks for FSOs • American Council on Education (ACE) Credit Equivalency recommendations for • • several courses Two new awareness courses available outside of STEPP Professionalization

Looking ahead • Continuous Evaluation Pilot • New CI Resources • FSO Toolkit • Call Center Transition • Rating Matrix II • Technology § OBMS § CAC/PKI § 254 database • Electronic Fingerprint

Social Media @DSSPublic. Affair @The. CDSE Like Us on facebook 15

Questions? 16