CISCO KNOW THE NETWORK PresentationID 2010 Cisco Systems

















- Slides: 31

CISCO KNOW THE NETWORK Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 1

Your Business Priorities What Customers are Saying Business Risk Management Presentation_ID Architecture Planning for Business Growth © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public Financial Management Improve Business Performance 2

What are Top-Of-Mind Concerns for IT Managers? What devices are deployed in our network? Is our network technology current? 4 Is our support coverage in place to ensure maximum network availability? • Downtime 1 • Security breaches 2 • Performance issues 3 1 2 3 4 Presentation_ID ? Netcordia, 2007 EUNIS, 2005 and Infonetics Research, 2005 Vanson Bourne, 2006 Comp. TIA, 2008 © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 3

Network Risks § 43% of network equipment examined at 150 major companies is already at end of life!1 – End of life equipment typically costs more to maintain and is more prone to downtime 1 § Average cost of downtime is $42, 000 per hour, and up to $6. 5 M per hour for certain applications and industries 2 § Average annual downtime cost has been estimated at 3. 6% of the revenue of large enterprises 3 Dimension Data Survey, 2009 Gartner Group, 2004, 2005 3 Infonetics Research, 2005 1 2 Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 4

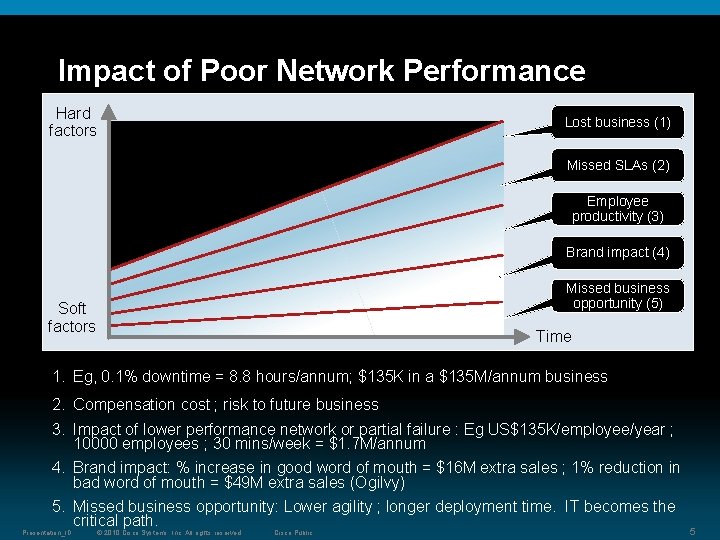
Impact of Poor Network Performance Hard factors Lost business (1) Missed SLAs (2) Employee productivity (3) Brand impact (4) Missed business opportunity (5) Soft factors Time 1. Eg, 0. 1% downtime = 8. 8 hours/annum; $135 K in a $135 M/annum business 2. Compensation cost ; risk to future business 3. Impact of lower performance network or partial failure : Eg US$135 K/employee/year ; 10000 employees ; 30 mins/week = $1. 7 M/annum 4. Brand impact: % increase in good word of mouth = $16 M extra sales ; 1% reduction in bad word of mouth = $49 M extra sales (Ogilvy) 5. Missed business opportunity: Lower agility ; longer deployment time. IT becomes the critical path. Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 5

Advantages of Implementing Network Lifecycle Management § Lowers business risk through reduced network downtime Problem anticipation & avoidance § Provides IT cost savings and increased productivity Network transparency Balancing performance & cost § Prepares for new ICT technologies and applications § Improves competitive advantage through better business support information Source : Gain a Competitive Advantage Through Better Performance of Your IP Network. IDC, October 2009 Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 6

Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 7

What is Know the Network (KTN)? The Know the Network (KTN) solution is a set of business capabilities for collection-led, intelligent installed base management. KTN helps you make informed decisions about your network in regard to risk, performance, and financial management. KTN provides network inventory reports containing uncovered items, Last Date of Support (LDo. S) items, contract status, and site information. KTN is embedded in some existing Cisco programs or may also be offered as a one-time event. Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 8

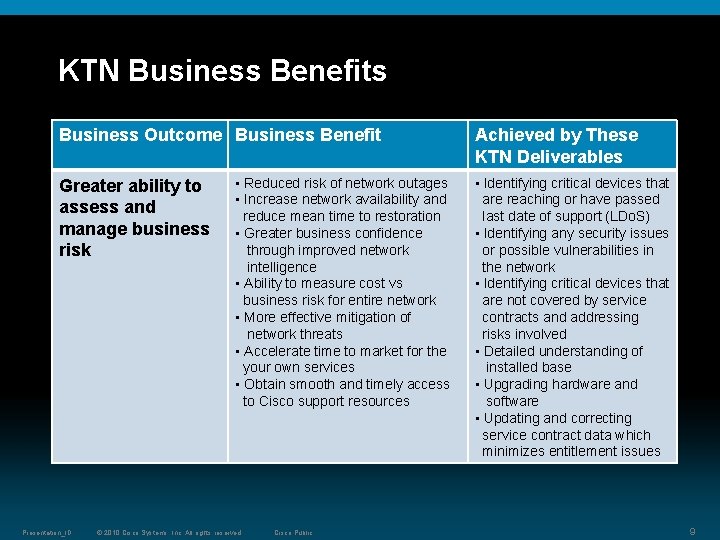
KTN Business Benefits Business Outcome Business Benefit Greater ability to assess and manage business risk Presentation_ID • Reduced risk of network outages • Increase network availability and reduce mean time to restoration • Greater business confidence through improved network intelligence • Ability to measure cost vs business risk for entire network • More effective mitigation of network threats • Accelerate time to market for the your own services • Obtain smooth and timely access to Cisco support resources © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public Achieved by These KTN Deliverables • Identifying critical devices that are reaching or have passed last date of support (LDo. S) • Identifying any security issues or possible vulnerabilities in the network • Identifying critical devices that are not covered by service contracts and addressing risks involved • Detailed understanding of installed base • Upgrading hardware and software • Updating and correcting service contract data which minimizes entitlement issues 9

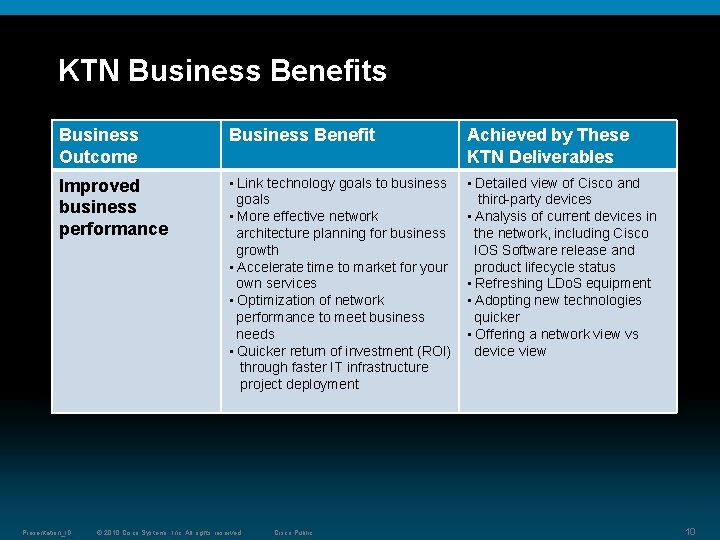
KTN Business Benefits Business Outcome Business Benefit Achieved by These KTN Deliverables Improved business performance • Link technology goals to business goals • More effective network architecture planning for business growth • Accelerate time to market for your own services • Optimization of network performance to meet business needs • Quicker return of investment (ROI) through faster IT infrastructure project deployment • Detailed view of Cisco and third-party devices • Analysis of current devices in the network, including Cisco IOS Software release and product lifecycle status • Refreshing LDo. S equipment • Adopting new technologies quicker • Offering a network view vs device view Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 10

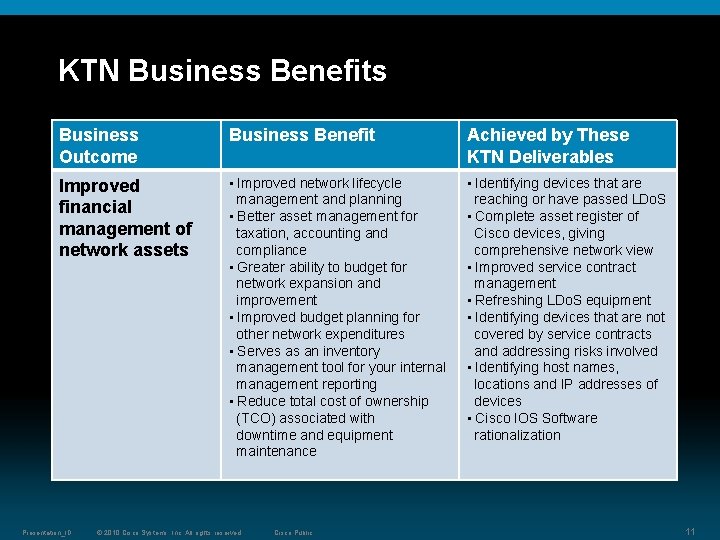
KTN Business Benefits Business Outcome Business Benefit Achieved by These KTN Deliverables Improved financial management of network assets • Improved network lifecycle management and planning • Better asset management for taxation, accounting and compliance • Greater ability to budget for network expansion and improvement • Improved budget planning for other network expenditures • Serves as an inventory management tool for your internal management reporting • Reduce total cost of ownership (TCO) associated with downtime and equipment maintenance • Identifying devices that are reaching or have passed LDo. S • Complete asset register of Cisco devices, giving comprehensive network view • Improved service contract management • Refreshing LDo. S equipment • Identifying devices that are not covered by service contracts and addressing risks involved • Identifying host names, locations and IP addresses of devices • Cisco IOS Software rationalization Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 11

Critical Questions to Consider Presentation_ID 1 Do you have multiple sites and complex networks? 2 Are you concerned about hidden risks in your network? 3 Do you want to know what is in your network and take steps to ensure your devices are adequately covered in terms of service and support? 4 Do you want to perform a network refresh or migrate to new technologies but do not have a baseline inventory of current equipment? 5 Are you expanding your business and want to determine enhancements needed to meet your business growth? 6 Are you going through mergers and acquisitions? Do you want to consolidate or audit your network assets? 7 Are you moving to a different location and would like to obtain a detailed inventory of your equipment? 8 Do you want to review your installed base and rationalize the number of resellers you are dealing with? © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 12

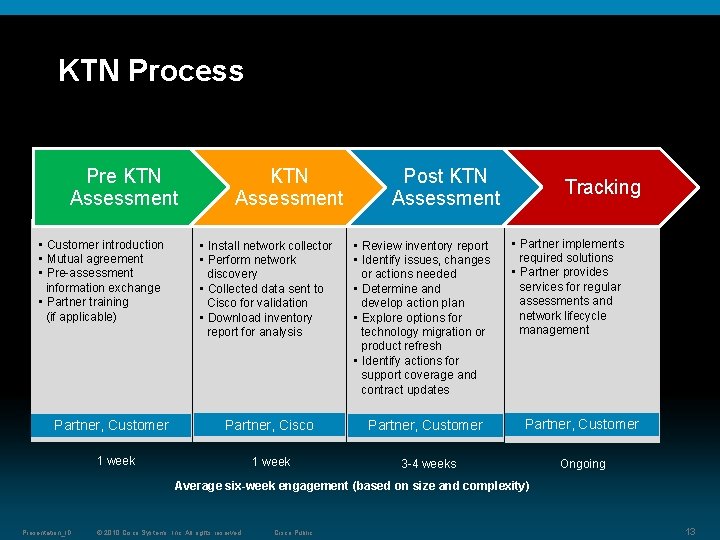
KTN Process Pre KTN Assessment • Customer introduction • Mutual agreement • Pre-assessment information exchange • Partner training (if applicable) Partner, Customer KTN Assessment Post KTN Assessment Tracking • Partner implements required solutions • Partner provides services for regular assessments and network lifecycle management • Install network collector • Perform network discovery • Collected data sent to Cisco for validation • Download inventory report for analysis • Review inventory report • Identify issues, changes or actions needed • Determine and develop action plan • Explore options for technology migration or product refresh • Identify actions for support coverage and contract updates Partner, Cisco Partner, Customer 1 week 3 -4 weeks Ongoing 1 week Average six-week engagement (based on size and complexity) Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 13

Frequently Asked Questions Will the KTN network collection process: • Compromise our network security? • Affect our network performance? The KTN network collection process uses a strictly read-only application. It does not modify any part of the network or change any configuration details. The collected network data transmitted to Cisco is encrypted. Only very small amounts of data are being collected. The network bandwidth used and network traffic generated are negligible, so the effect on network performance is miniscule. Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 14

Frequently Asked Questions What happens to our network data that Cisco analyzes to produce a network inventory report? Data collected during the course of a KTN engagement follows all established global Cisco security and privacy protocols as outlined in the Cisco Systems Inc. Online Privacy Statement. • Cisco does not share collected data with any third party, unless given prior written consent from the Cisco reseller or end customer. • All data is transmitted from the network to Cisco using industry standard encryption. • All data is handled behind a Cisco IT firewall, and is protected in the same manner as all other business critical Cisco data. • All network collection data is maintained on an internal Cisco server with licensed virus protection software. • Access to any network collection data is limited solely to Cisco account teams servicing the reseller/customer and/or the reseller leading the KTN engagement. • Customers, of course, are free to share their data with others as they choose. • During report processing, access to the network collection data is limited to Cisco. employees necessary to the creation of the network inventory report. These employees access the data strictly through Cisco’s secure servers. Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 15

Frequently Asked Questions Is there a list of third-party vendors and devices that the KTN collection process can report on? When third party devices are discovered, what information is reported? One of the current KTN network collectors will discover devices of all vendors as long as they support Simple Network Management Protocol (SNMP). The current KTN network collector does not report on service coverage, product security alerts (PSIRTs) or field notices for third-party devices. End-of-life milestones are provided for some third-party devices including those from Nortel (now Avaya) and Juniper. With most of the vendors, it will discover information based on generic MIBs, such as IP and MAC addresses, and system description. With entity MIB supported equipment it will discover cards, ports, and so on. With Cisco and, to some extent, Nortel, Juniper, and HP (Pro. Curve), it will also discover internal device configuration, memory used, configuration files (Cisco device only), and some other data that is stored in the vendor private MIBs. Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 16

Frequently Asked Questions Will the KTN network collection provide information on items in the network that are supported or managed by another Cisco partner? To protect partner proprietary information, Cisco has implemented procedures so that partners have visibility to information in network inventory reports that pertains only to the contracts registered to their Cisco. com user ID. If the network collection is done by Partner A, the serial number product ID, and item type of the devices managed by Partner B are provided. Service contract-related information is blocked and replaced with “Other” when a device is covered by a service contract not registered to the partner’s Cisco. com User ID. Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 17

Business Transformation Putting the Interaction Where the Customer Is Customer Experience/ Innovation 1 Acquire and retain customers 2 Manage customer relationships Productivity/ Operating Expense 2 Lower company operating costs Drive innovative new market offering/ business practices Improve workforce productivity Improve quality of products and services Support globalization Source: Forrester Report “State of the CIO Agenda” January 2009: 600 Business/506 IT Executives Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 18

Business Transformation: The New Borderless Organization Anyone Employee, Partner, Customer Communities Person to Person, Person to Device, Device to Device Anything Borderless Experience Securely, Reliably and Seamlessly Anywhere Presentation_ID Work, Home, On the Go… © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public Always Works, Instant Access, Instant Response Anytime 19

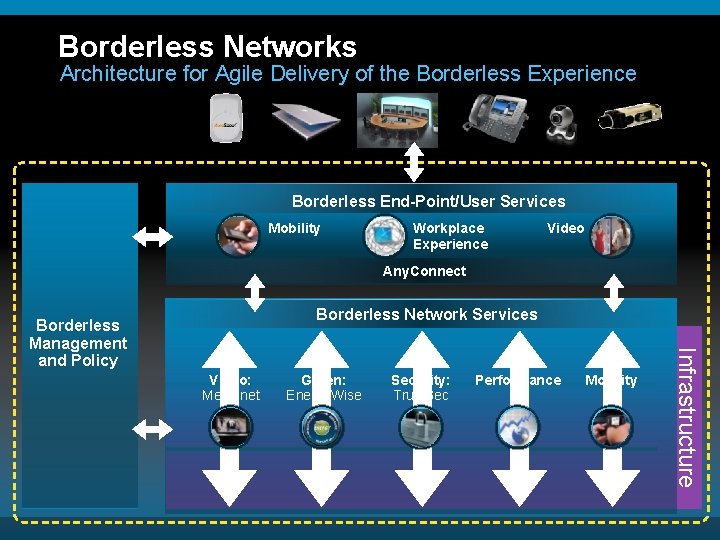
Borderless Networks Architecture for Agile Delivery of the Borderless Experience New Innovations Borderless End-Point/User Services Mobility Workplace Experience Video Any. Connect Borderless Network Services Video: Medianet Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Green: Energy. Wise Cisco Public Security: Trust. Sec Performance Mobility Infrastructure Borderless Management and Policy 20

KTN is the Enabler Business Transformation through Borderless Networks Business Transformation Borderless Network Scaling the Network Architecture Network Availability and Performance Network Asset and Lifecycle Management Know the Network Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 21

Support Through the Lifecycle of Your Network Architecture Borderless Networks Vision Solutions-Led Approach Architectural Assessment Architectural Blueprint Absorb, Manage, and Scale Technology Identify business issues and a path for resolving them through discovery Map your capabilities, services, and solutions against blueprint; gauge readiness Based on proven, tested reference architectures Improve performance, availability, security, operational excellence Services from Cisco and Our Partners Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 22

Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 23

Backup Slides Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 24

Cisco Borderless Networks Accelerated Business Growth § Technology innovation § Architectural leadership § Borderless Professional Services Industry-Leading TCO § End-to-end energy efficiency § Seamless wired-wireless experience § Proven investment protection § Trusted security and identity § Ease of operations § Extended security for the Borderless Enterprise § Flexible pricing Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Trusted Access Cisco Public 25

Borderless Experiences Media-rich Sessions Over Wireless Access Throughout the Day Secure, Encrypted Business Communications Personalized Content, Smartphone and Digital Signage Based on Identity, Profile and Location 8: 00 am 11: 00 am 4: 00 pm Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 26

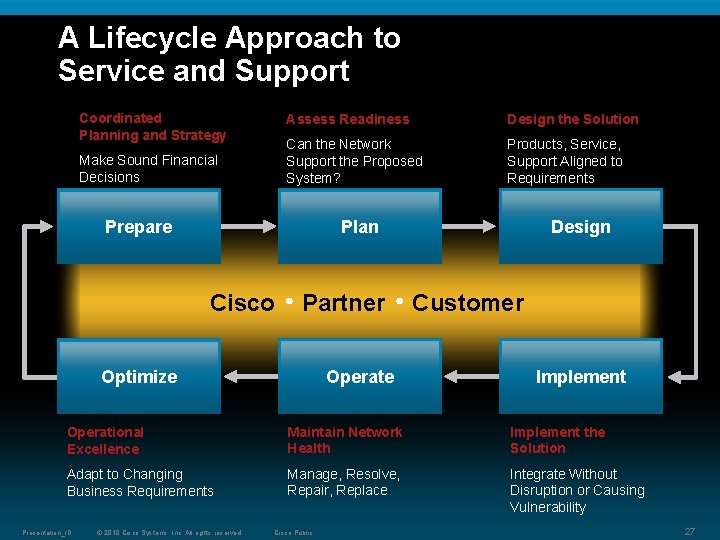
A Lifecycle Approach to Service and Support Coordinated Planning and Strategy Make Sound Financial Decisions Assess Readiness Design the Solution Can the Network Support the Proposed System? Products, Service, Support Aligned to Requirements Prepare Plan Cisco Partner Optimize Operate Design Customer Implement Operational Excellence Maintain Network Health Implement the Solution Adapt to Changing Business Requirements Manage, Resolve, Repair, Replace Integrate Without Disruption or Causing Vulnerability Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 27

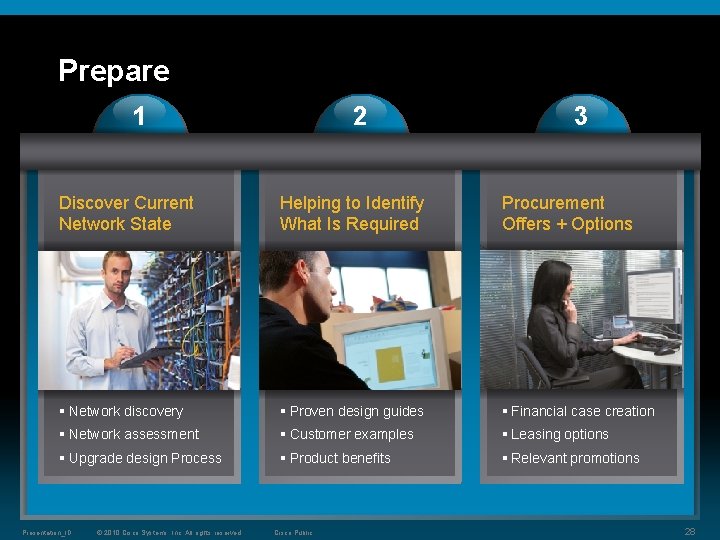
Prepare 1 2 3 Discover Current Network State Helping to Identify What Is Required Procurement Offers + Options § Network discovery § Proven design guides § Financial case creation § Network assessment § Customer examples § Leasing options § Upgrade design Process § Product benefits § Relevant promotions Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 28

Plan § Review your IT infrastructure and determine if it truly enables your business goals § Fully understand your current network capabilities and perform a gap analysis § Jointly develop an action plan Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public 29

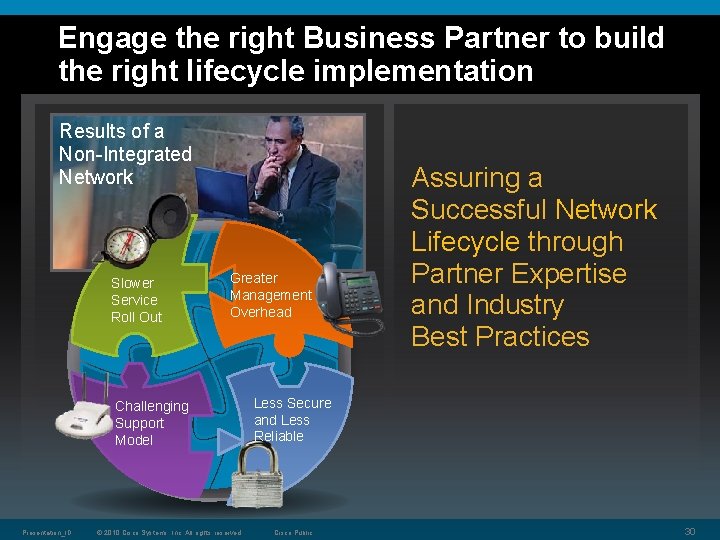
Engage the right Business Partner to build the right lifecycle implementation Results of a Non-Integrated Network Slower Service Roll Out Greater Management Overhead Challenging Support Model Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Assuring a Successful Network Lifecycle through Partner Expertise and Industry Best Practices Less Secure and Less Reliable Cisco Public 30

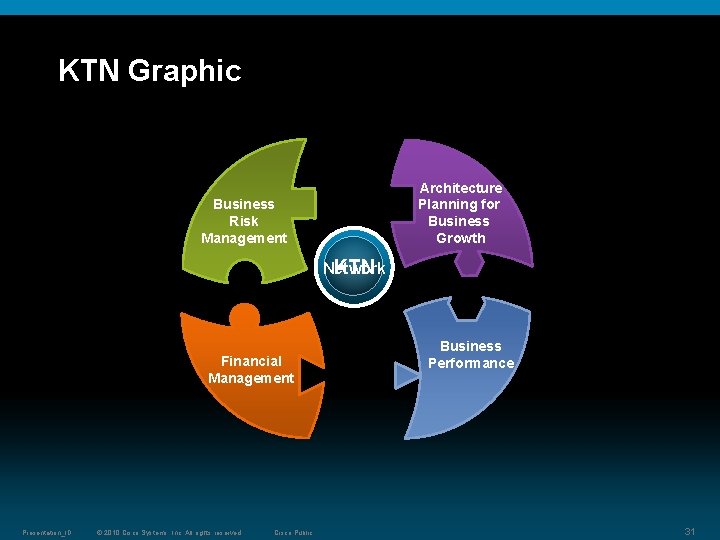
KTN Graphic Architecture Planning for Business Growth Business Risk Management Network KTN Financial Management Presentation_ID © 2010 Cisco Systems, Inc. All rights reserved. Cisco Public Business Performance 31