Power Point Presentation to Accompany Chapter 10 Security













































- Slides: 70

Power. Point Presentation to Accompany Chapter 10 Security & Privacy Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Objectives 1. 2. 3. 4. 5. Discuss various types of cybercrime. Differentiate between different types of malware. Explain how to secure a computer. Discuss safe computing practices. Discuss laws related to computer security and privacy. Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Objective 1: Overview Cybercrime: They Are Out to Get You 1. Define cybercrime and discuss how it affects online activity 2. Discuss the various types of cybercrime, including harassment, phishing, pharming, fraud, identity theft, and hacking Key Terms § Computer fraud § Cyberbullying § Cybercrime § Cyberstalking § Cyberterrorism Visualizing Technology § § § Hacking Hacktivism Identify theft Pharming Phishing Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Cybercrime is criminal activity on the Internet § Personal cybercrime is perpetrated against individuals, as opposed to businesses and other organizations. § These are the crimes that affect you directly and that you need to be alert to.

Cybercrime §Harassment: §Cyberbullying and cyberstalking Fall into the category of harassment. §When the exchange involves two minors, it is called cyberbullying. §When the exchange involves two adults, it is called cyberbullying. §The harassers use e-mail, text messages, IMs, and social networks to embarrass, threaten, or torment someone – often because of their gender, race, religion, nationality, or sexual orientation. §Cyberbullying follows a child beyond the schoolyard and beyond the school day.

Personal Cybercrime HARASSMENT Cyberbullying Harassment involving minors Cyberstalking Harassment involving adults Harassers use e-mail, IM, chat, text messages, and social networks to embarrass, torment, or threaten someone

Cybercrime § Phishing and pharming: § Phishing uses e-mail messages and IMs that appear to be from those you do business with. § They’re designed to trick you into revealing information, such as username and passwords for your accounts. § Pharming redirects you to a phony website even if you type the right address into your browser. § They do this by hijacking the domain name of a company that has either not renewed its registration or has securitycompromised Web servers or by poisoning the DNS server references to a site, much like having the wrong phone number listed in the phone book.

Personal Cybercrime PHISHING AND PHARMING Phishing Uses e-mail messages and IMs that appear to be from those you do business with; designed to trick you into providing usernames and passwords to your accounts Pharming Redirects you to a phony website even if you type the right address into your browser by hijacking the company’s domain

Cybercrime § Fraud § The victim voluntarily and knowingly gives money or property to a person. § Some of the more well-known computer fraud schemes on the Internet involve e-mails claiming you have won a lottery or inherited money.

Cybercrime § Identity theft: § Happens when someone uses your name, Social Security number, or bank or credit card number for financial gain. § Using password-stealing software, keyloggers, and phishing and pharming scams, criminals can easily obtain enough personal information to wreak havoc on an individual, § Victims of identity theft often spend years and thousands of dollars to clear up the mess.

Cybercrime § Identity theft: § Companies that claim to protect you from identity theft have sprung up, but all they really do are things you can and should do yourself. § Monitor your bank and credit card statements, carefully checking each change every month. § Also watch for charges on your phone bills. § Monitor your credit report. § By law, you’re entitled to one free credit report per year from each of the three major credit reporting companies. § Instead of requesting them all at once, space them out every three or four months to keep an eye out for suspicious activity throughout the year. § Use the right website – annualcredit report. com. § If you suspect you might be the victim of identity theft, immediately place a fraud alert on your credit reports.

Personal Cybercrime FRAUD AND IDENTITY THEFT Computer Fraud Schemes that convince you to voluntarily and knowingly give money or property to a person Identity Theft Occurs when someone uses your name, Social Security number, or bank or credit cards for financial gain

Cybercrime & Business HACKING Hacking: The act of gaining unauthorized access to a computer system or network 1. White-hat or “sneakers”: Prevent future hacking 2. Black-hat or “cracker”: Has malicious intent 3. Gray-hat: Illegal but not malicious intent

Cybercrime & Business §Cybercrime Against Organizations § Hacking: § The act of gaining unauthorized access to a computer system or network. § Some people categorize hackers as white-hat, gray-hat, and black-hat depending on their motivation and results of their hacking. § A white-hat hacker’s motivation is to find security holes in a system for the purpose of preventing future hacking. § These are security experts that are paid to hack systems. § They’re sometimes called “sneakers”.

Cybercrime & Business §Cybercrime Against Organizations § Hacking: § Black-hat hackers hack into systems for malicious purpose, such as theft or vandalism. § Sometimes referred to as “crackers”. § Gray-hat hackers hack into systems illegally but not for malicious intent. § A gray-hat hacker might break into a system to prove he can or to expose a system’s vulnerability.

Cybercrime & Business CYBERTERRORISM §Cyberterrorism: §An unlawful attack against computers or networks that’s done to intimidate a government or its people for a political or social agenda. §Cyberterrorists are not just attacking computers; they are actually attacking the information systems to cause harm. §The majority of attacks are unsuccessful and unreported, yet experts believe threats are growing. §Potential targets include the financial sector and infrastructure, such as communications, utilities, transportation, and hospitals. §

Social Network Attacks § § § Adware and other malware Suspicious emails and notifications Phishing and "Please send money" scams Clickjacking Malicious script scams Social Networking Attacks (Facebook) facebook. com/help/security Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

What steps should you take to prevent identity theft? How have you implemented these in your activities? Are there other things you should be doing? Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Objective 2: Overview Malware: Pick Your Poison 1. Define the different types of malware 2. Differentiate among the different types of malware Key Terms § Adware § Botnet § Cookie § Denial-of-service attack § Keylogger § Logic bomb § Malware § Payload Visualizing Technology § § § § Rootkit Spam Spyware Time bomb Trojan horse Virus Worm Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Malware is malicious software that includes many different types of programs that are designed to be harmful or malicious.

Spam and Cookies Spam: Mass, unsolicited e-mail • Popular because it is easy and inexpensive. • No paper to print, no envelopes to stuff, and no postage. • Other forms include fax spam, IM spam, text message spam • It costs businesses millions of dollars each year.

Spam and Cookies: Small text files that help websites identify you when you return. • Your personal information isn’t stored in the cookie. • The site recognizes you because there’s a cookie on your computer. • Whenever you visit a site and click the Remember me or Keep me logged in button, the website puts a cookie on your computer. • Cookies are also used without you choosing them.

Spam and Cookies: §While cookies are useful, they could be used to collect information that you don’t want to share. §Modern browsers include protection against potentially harmful cookies.

Spam and Cookies A cookie on the computer allows the website to recognize the user and personalize the site

Adware and Spyware Adware shows you ads. § Ads appear as pop-ups or banner ads in websites and in software. § Some free software that’s distributed as adware gives you the option to purchase a full version without ads. § Ads generate income for the software developer and allow the user to try a program for free. § Adware can use CPU cycles and Internet bandwidth, which can reduce PC performance. § Some adware is more insidious because it monitors your Internet connection and slows down your browsing dramatically. § For this reason, adware is sometimes lumped together with spyware.

Adware and Spyware is a form of malware that secretly gathers personal information about you. § The information is sent back to a third party that may use it for anything from targeted advertisements to identity theft. § Spyware is usually installed inadvertently by a user who clicks on a pop-up or installs a freeware program that includes tracking features. § The information about the tracking feature might be buried in the license agreement that most people simply accept without reading or understanding. § Sometimes, you can choose not to install these extra features by simply unchecking them in the installer. § Spyware can be very difficult to remove and can even cause your security program to stop running.

Adware and Spyware A Netflix banner ad on the AIM screen

Viruses § A program that replicates itself and infects computers. § A virus needs a host file to travel on (a game). § The attack (the payload)may corrupt or delete files or it may even erase an entire disk. § A virus may use the e-mail program on the infected computer to send out copies of itself and infect other machines.

Viruses § Virus hoaxes are common in e-mail messages. § Although they don’t contain a virus, they often trick users into behavior that can be harmful, such as searching for and deleting files that the computer actually needs. § One place to check to see if a message is a hoax is Hoax-slayer. com.

Bombs Logic Bomb § Behaves like a virus in that it performs a malicious act, yet does not replicate itself. § Attacks when certain conditions are met § An employee’s name being removed from a DB. Time Bomb § When trigger is a specific time or event, a logic bomb is called a time bomb. § April Fool’s Day § Friday the 13 th

Worms § Like a virus, they are self-replicating, but do not need a host to travel. § Travel over networks, including the Internet. § Once a system on a network is infected, The worm scans the network for other vulnerable machines to infect and spreads over the network without any human intervention.

Worms § Conflicker is a computer worm, first released in 2008, that has had many different variations. § It initially took advantage of a flaw in several versions of Windows. § Conflicker prevented infected computers from connecting to software update websites and disabled antivirus software. § In 2010, when it appeared that the virus waning, it instead changed its behavior, making it even more difficult to prevent.

Worms § It’s estimated that millions of computers are infected with Conflicker. § On April 1, 2009, millions of e-mail spam messages were sent oout by computers infected with the Conflicker worm. § These computers were part of a massive botnet (a network of computer zombies or bots controlled by a master. § The message was an advertisement for a fake antispyware program that, when installed, infected more machines.

Worms § The ability to control millions of machines has the potential to cause real harm. § A botnet could be used to send out spam and viruses or to launch a denial-of service attack. § Perpetrated by sending out so much traffic that it cripples a server or a network.

Trojan Horse §A Trojan horse or Trojan, is a program that appears to be a legitimate program but is actually something malicious instead. §Trojans might install adware, a toolbar, or a keylogger, or open a back door. § A keylogger is a computer program that captures information a user enters on a keyboard. § Keyloggers might be installed as a Trojan and reside unnoticed on an infected machine. They wait for the user to enter usernames, passwords, and credit card numbers and gather this information.

Trojan Horse §A famous Trojan is the Sinowal Trojan horse, which was used by criminals to steal more than 500, 000 banking passwords and credit card numbers over three years.

Rootkit A rootkit is a set of programs that allows someone to gain control over a computer system while hiding the fact that the computer has been compromised. § A rootkit is almost impossible to detect and also allows the machine to become further infected by masking the behavior of other malware.

Rootkit § Over one million computer viruses/Trojans/worms have been identified, and the number has grown exponentially in the past few years. § Understanding the threats your computer faces is the first step in preventing these programs from infecting your machine.

Malware § Malicious software § Includes: § § § Visualizing Technology Spam Adware and spyware Viruses Worms Trojan horses Rootkits Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Visit the U. S. Computer Emergency Readiness Team website at us-cert. gov/cas/tips. Select the Guidelines for Publishing Information Online link and read about it. Write a 2 - to 3 -paragraph summary of the tip. Which of these suggestions do you follow? Are there any that you disagree with? Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Objective 3: Overview Shields Up! 1. Discuss the important steps to keep a system secure 2. List the different software needed to keep your system secure 3. List the different hardware needed to keep your system secure 4. Discuss why it is important to keep the OS up-to-date Key Terms § Antispyware software § Antivirus program § Firewall § NAT Visualizing Technology § § Router Security suite SSID Wireless encryption Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

How to Protect Your Computer SOFTWARE § You shouldn’t run another software-based router at the same time because they can conflict with each other, causing connectivity issues.

How to Protect Your Computer SOFTWARE § § § Today, many antivirus programs protect against viruses, Trojans, worms, and even some spyware. Most new computers come with a trial version of antivirus software installed. Antivirus software scans files on your computer, called “signature checking”, to search for known viruses. It uses virus definition files to keep track of the newest threats. Outdated definition files leave a machine vulnerable to attack.

How to Protect Your Computer SOFTWARE § Good antivirus software also uses heuristic methods. § § Monitoring your machine for suspicious activity, to catch new viruses that are not in the definition files. Some very good free programs include AVG Free, Avast, and Microsoft Security Essentials. Many ISPs provide free antivirus and other security software to their customers. It’s important to only have one antivirus program running on your computer because multiple programs will interfere with each other and slow down your computer’s performance.

How to Protect Your Computer SOFTWARE § § Antispyware software is necessary to prevent adware and spyware software from installing itself on your computer. These infections aren’t always caught by ordinary antivirus programs. Windows 7 comes with Windows Defender, and antispyware program that includes both real-time protection and scanning. Real-time protection monitors your system for suspicious behavior (a program trying to change your home page or other Windows settings).

How to Protect Your Computer SOFTWARE § § § You can run scans to detect and remove any spyware that’s already installed on your computer. Other popular, effective, and free antispyware programs for personal use include Ad-Ware, Spybot Search and Destroy, and Malwarebytes Anti. Malware. You can download these and other programs from CNET’s download. com.

How to Protect Your Computer SOFTWARE § § § Security suites are packages of security software that include a combination of features. The advantage to using a suite is that you get “complete” protection, but they can be expensive and use a lot of system resources. The main complaint that many people have is that they decrease the system performance.

How to Protect Your Computer HARDWARE At home you should use a router (a device that connects two or more networks together) between your computers and the Internet. § Acts like a firewall. § It can prevent unauthorized access to your network. § The default setup of most home routers has this feature enabled, and you can customize it by using the router utility. § You might set restrictions on the type of traffic that can access your network, restrict the time of day that a computer can access the Internet, or define which sites can or cannot be accessed (parental controls). § You might need to customize your router to allow certain applications through.

How to Protect Your Computer HARDWARE § Another important security feature of a router is called network address translation (NAT). § The router faces the public network (Internet) and has a public IP address that it uses to communicate with the network, but inside your house, the router supplies each device with a private IP address that’s only valid on your private network. § To the outside world, only the router is visible, so it shields the rest of your devices. § The devices inside your network can communicate with each other directly, but any outside communication must go through the router.

How to Protect Your Computer HARDWARE § A wireless router has all the features described but also provides a wireless access point to your network. § This can be a potential security risk if it’s not properly secured. § Use the router setup utility to change the SSID (service set identifier), or wireless network name, and enable and configure wireless encryption. § Wireless encryption adds security to a wireless network by encrypting transmitted data. § You should use the strongest form of wireless encryption that’s supported by the devices and operating systems on your network.

How to Protect Your Computer OPERATING SYSTEM § § The operating system is the most important piece of security software on your computer. It’s absolutely critical that you keep it patched and up to date. § § § Many times, malware threats are only capable of infecting machines because they were unpatched. The Conflicker worm can’t infect a properly patched Windows computer, yet it has infected millions of machines because they were unpatched. By default, Windows computers are configured to automatically install updates, but you have the option to change that setting.

Use the Internet to find out what might happen if you use the Windows firewall and another firewall at the same time. Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Objective 4: Overview An Ounce of Prevention Is Worth a Pound of Cure 1. Discuss why practicing safe computing is critical to protecting your system and your personal information 2. Discuss strong passwords and encryption 3. Discuss the importance of an acceptable use policy Key Terms § Acceptable use policy (AUP) § Ciphertext § Encryption § User Account Control (UAC) Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

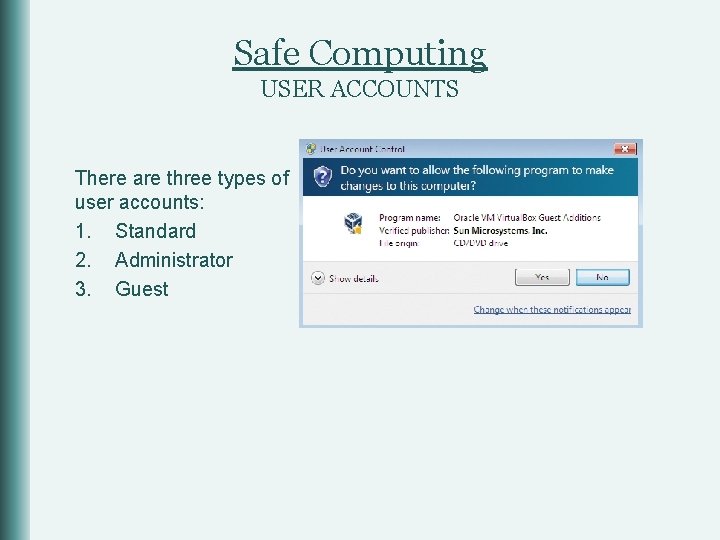
Safe Computing USER ACCOUNTS There are three types of user accounts: 1. Standard 2. Administrator 3. Guest

Safe Computing USER ACCOUNTS §Standard Account: §A standard account for everyday computing. §Administrator Account: §An administrator account for making changes, installing software, configuring settings, and completing other tasks. §Guest Account: §A guest account for users that need temporary access to a system.

Safe Computing USER ACCOUNTS §User Account Control (UAC) will notify you before changes are made to your computer. §It prevents malware from making changes to your system without your knowledge. § Do not turn this feature off. § It’s important to always read the message in the UAC box before clicking Yes. § Some malware infects computers by tricking users into clicking fake Windows notifications.

Safe Computing PASSWORDS 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. Use at least eight characters Use at least one number If allowed, use special characters Mix uppercase and lowercase letters Use different passwords for different accounts Use difficult passwords for banks and credit cards Change default passwords Change passwords on regular basis Do not use words found in dictionary Do not use personal identifiers Do not write them down

Safe Computing PASSWORDS § § § Some people prefer to use a password manager to store passwords rather than trying to remember them all individually. Some of these programs can also generate passwords for you, which are more secure than the passwords people normally create because they’re randomly generated. When you create a new account, you’re asked for a lot of information to help identify you.

Safe Computing PASSWORDS § § Think about your answers carefully so it’s hard for someone to guess but also so you’re not giving away too much personal information. Select questions that are hard for other people to answer, and use good passwords following the rules of the site.

Safe Computing ENCRYPTION § Any time you send information across a network, there’s the potential for someone to intercept it.

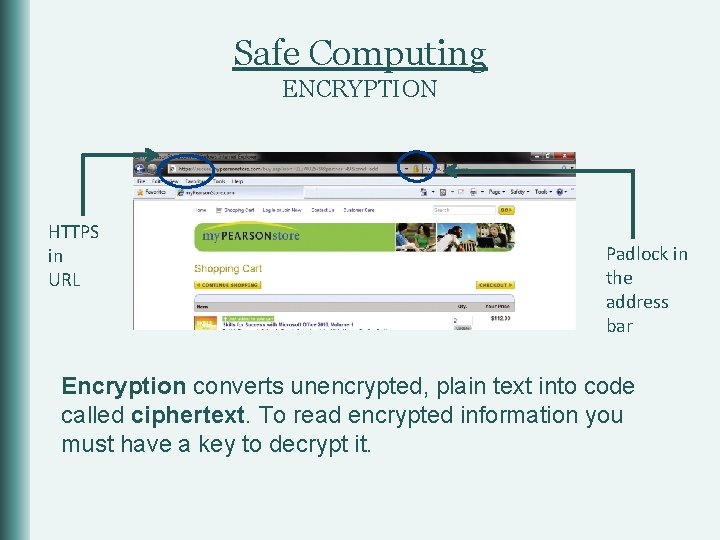
Safe Computing ENCRYPTION HTTPS in URL Padlock in the address bar Encryption converts unencrypted, plain text into code called ciphertext. To read encrypted information you must have a key to decrypt it.

Safe Computing ENCRYPTION § § § This prevents the thief from being able to read the information. When you log in to a website, be sure you’re using a secure connection. Verify that the address bar of your browser shows https, which indicates that the site is encrypted. This assures that your information is safe to send. If the connection uses http, then your information is sent in plain text.

Safe Computing ACCEPTABLE USE POLICIES § § § Many businesses and schools have an acceptable use policy (AUP) that computer and network users must abide by. They force users to practice safe computing and thus prevent a lot of potential problems from affecting the systems. The restrictions you have depend on the type of business and the type of information you need access to.

Do you have multiple user accounts? Is your everyday account a standard user account or an administrator account? Is it password protected? What steps do you take to protect your information when you surf the Web?

Visit staysafeonline. org/teach-online-safety/higher-education/ and read the Internet Higher Education tips and the STOP. THINK. CONNECT. tips and advice sheet. Use this advice to craft an AUP for your college classmates. Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Objective 5: Overview The Law Is on Your Side 1. Discuss the responsibility of the Internet Crime Complaint Center (IC 3) 2. Discuss current laws in place to protect users on the Internet Key Term § Internet Crime Complaint Center (IC 3) Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Laws, Security and Privacy § Because crimes are varied, there is no single authority responsible for investigating cybercrime § Internet Crime Complaint Center (IC 3): Place for victims to report cybercrimes (website: ic 3. gov); reports are processed and forwarded to the appropriate agency § Agencies include the FBI, Secret Service, Immigration and Customs, Postal Inspection Service, and ATF

Current Laws § Computer Fraud and Abuse Act: Passed in 1986, makes it a crime to access classified information § Amendments between 1988 and 2002 added additional cybercrimes § USA Patriot Antiterrorism Legislation (2001) and Cyber Security Enhancement Act (2002): Include provisions for fighting cybercrime § Convention on Cybercrime Treaty: Drafted by Council of Europe, signed by over 40 countries including U. S. , Canada, and Japan

As of this writing, the Cybersecurity Enhancement Act of 2010 was still being debated. What is the status of this act? Have there been any other cybercrime laws passed since then? Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. Printed in the United States of America. Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Visualizing Technology Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall