Template for New CISO Presentation to Board of

Template for New CISO Presentation to Board of Directors
delete this slide after use Using this Presentation Template This presentation template will help you organize your first presentation to the board of directors. If you have already presented to your board, you should use a different template for recurring CISO presentations which can be downloaded here. Directions § The core presentation is Slides 7 -29. Other slides contain instructions and additional materials. § Customize these slides based on the unique context of your organization and industry. § Look out for the § Review the guidance in the notes section below each slide. § Use the slides in the appendix section as needed to augment the presentation. box to know which visualizations are modifiable. Editable The risk calculations and visualizations shown in this Power. Point can be automated with Balbix. You can request a demo here or start your free trial.
delete this slide after use You are telling a story… Remember you are communicating about a complex topic with people who typically do not have a deep technical background. Your goal with all your board presentations is to help the Board meet its fiduciary duties. To do this, you will need to inspire the board’s trust and confidence in you and provide assurance that your function is effectively managing information risk. This 1 st presentation will play a foundational role in setting you up properly with the Board. Your best bet is to tell a compelling and simple story. It is more important to be interesting than to be complete!
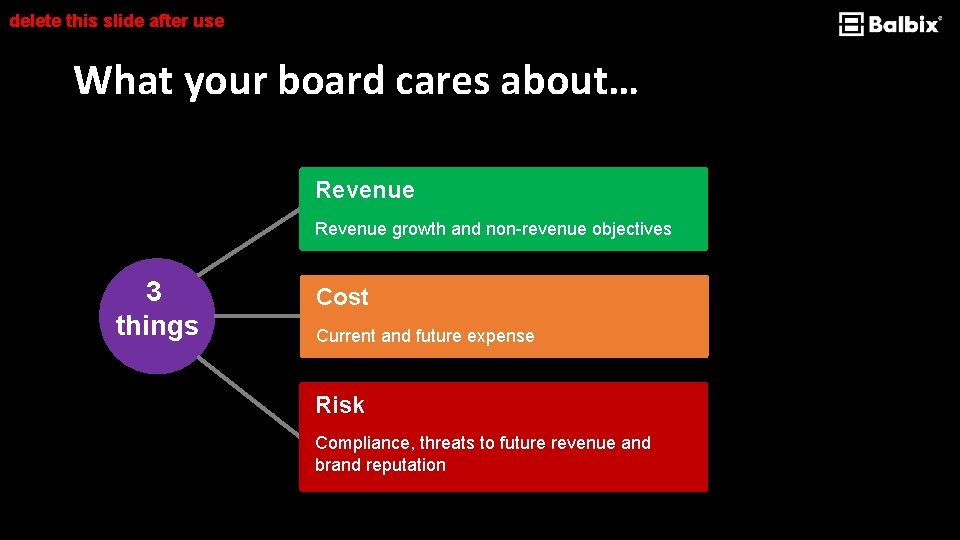
delete this slide after use What your board cares about… Revenue growth and non-revenue objectives 3 things Cost Current and future expense Risk Compliance, threats to future revenue and brand reputation

delete this slide after use Objectives of this 1 st Presentation § § Introduce yourself to the Board Also re-introduce the Infosec function to the Board § § § Explain how cybersecurity risks present board-level business risks Set up a framework for future discussions with the Board Introduce your strategic vision and roadmap for the Infosec function of your organization
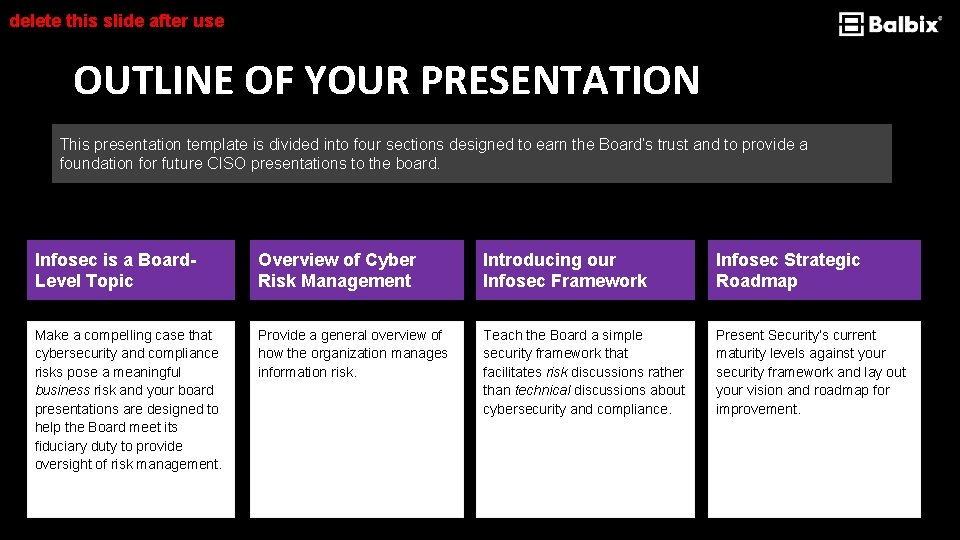
delete this slide after use OUTLINE OF YOUR PRESENTATION This presentation template is divided into four sections designed to earn the Board’s trust and to provide a foundation for future CISO presentations to the board. Infosec is a Board. Level Topic Overview of Cyber Risk Management Introducing our Infosec Framework Infosec Strategic Roadmap Make a compelling case that cybersecurity and compliance risks pose a meaningful business risk and your board presentations are designed to help the Board meet its fiduciary duty to provide oversight of risk management. Provide a general overview of how the organization manages information risk. Teach the Board a simple security framework that facilitates risk discussions rather than technical discussions about cybersecurity and compliance. Present Security’s current maturity levels against your security framework and lay out your vision and roadmap for improvement.

<company name> Information Security Update May 20, 2021 Add Your Logo Here
![ABOUT ME My Experience § XXX § YYY [insert photo] Jane Smith § ZZZ ABOUT ME My Experience § XXX § YYY [insert photo] Jane Smith § ZZZ](http://slidetodoc.com/presentation_image_h2/41bcdcf5be47dabcc945eb2164f75b7e/image-8.jpg)
ABOUT ME My Experience § XXX § YYY [insert photo] Jane Smith § ZZZ Education and Certifications § Degrees Chief Information Security Officer Jane. Smith@company. com § Certifications

Infosec is a Board-Level Topic AGENDA Overview of Cyber Risk Management Introducing our Infosec Framework Infosec Strategic Roadmap
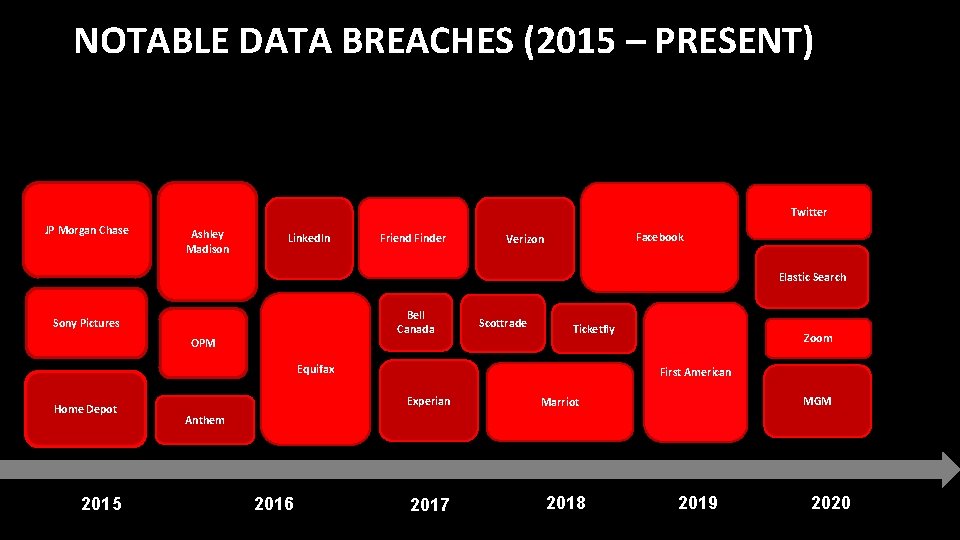
NOTABLE DATA BREACHES (2015 – PRESENT) Twitter JP Morgan Chase Ashley Madison Linked. In Friend Finder Facebook Verizon Elastic Search Bell Canada Sony Pictures OPM Scottrade Ticketfly Equifax Home Depot 2015 Zoom First American Experian MGM Marriot Anthem 2016 2017 2018 2019 2020
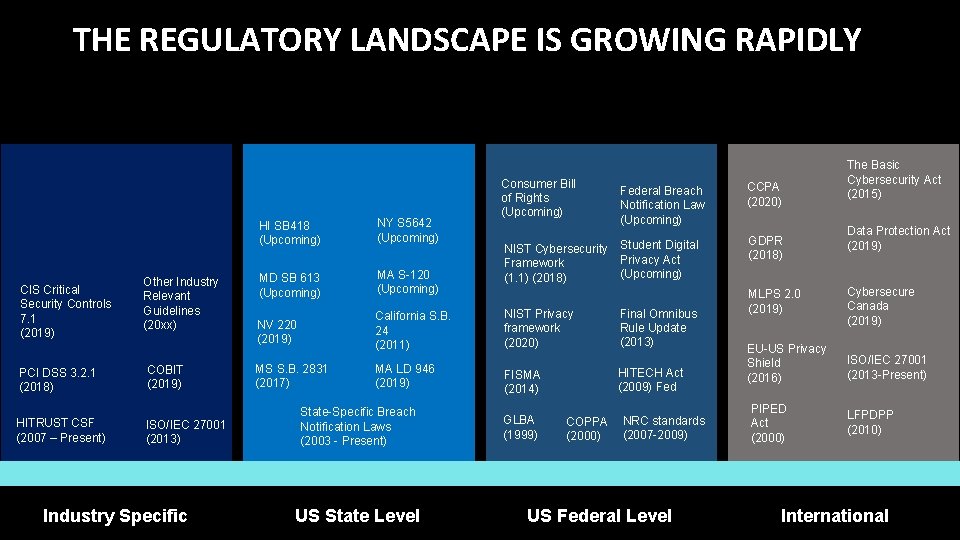
THE REGULATORY LANDSCAPE IS GROWING RAPIDLY CIS Critical Security Controls 7. 1 (2019) PCI DSS 3. 2. 1 (2018) HITRUST CSF (2007 – Present) Other Industry Relevant Guidelines (20 xx) COBIT (2019) ISO/IEC 27001 (2013) Industry Specific HI SB 418 (Upcoming) NY S 5642 (Upcoming) MD SB 613 (Upcoming) MA S-120 (Upcoming) NV 220 (2019) California S. B. 24 (2011) MS S. B. 2831 (2017) MA LD 946 (2019) State-Specific Breach Notification Laws (2003 - Present) US State Level Consumer Bill of Rights (Upcoming) NIST Cybersecurity Framework (1. 1) (2018) Federal Breach Notification Law (Upcoming) CCPA (2020) Student Digital Privacy Act (Upcoming) GDPR (2018) NIST Privacy framework (2020) Final Omnibus Rule Update (2013) FISMA (2014) HITECH Act (2009) Fed GLBA (1999) COPPA (2000) NRC standards (2007 -2009) US Federal Level The Basic Cybersecurity Act (2015) Data Protection Act (2019) MLPS 2. 0 (2019) Cybersecure Canada (2019) EU-US Privacy Shield (2016) ISO/IEC 27001 (2013 -Present) PIPED Act (2000) LFPDPP (2010) International
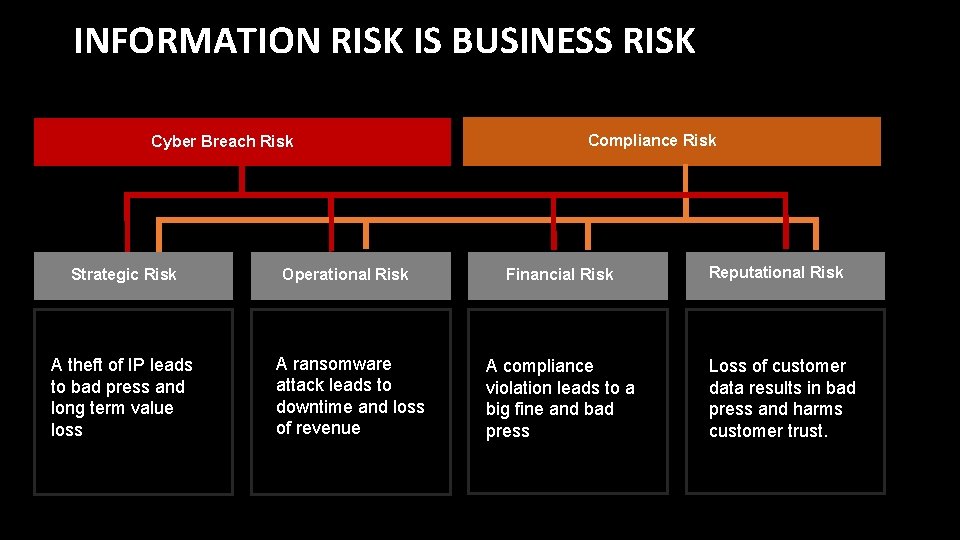
INFORMATION RISK IS BUSINESS RISK Cyber Breach Risk Compliance Risk Strategic Risk Operational Risk Financial Risk A theft of IP leads to bad press and long term value loss A ransomware attack leads to downtime and loss of revenue A compliance violation leads to a big fine and bad press Reputational Risk Loss of customer data results in bad press and harms customer trust.

THE BOARD’S ROLE IN CYBER RISK OVERSIGHT 5 Principles of Effective Cyber Risk Oversight: Guidance by National Assoc. of Corporate Directors 1 Boards should approach cybersecurity as an enterprise-wide risk management issue, not just an IT issue 2 Boards should understand the legal implications of cyber risk as they apply to the company’s specific circumstances 3 Boards should have adequate access to cybersecurity expertise, and discussions about cyber-risk management should be given regular and adequate time on the board meeting agenda 4 Boards should set the expectation that management will establish an enterprise-wide cyber-risk management framework 5 Board-management discussion about cyber risk should include identification of which risks to avoid, accept, and mitigate or transfer through insurance, as well as specific plans Source: National Association of Corporate Directors, Cyber-Risk Oversight Handbook, 2020

Infosec is a Board-Level Topic AGENDA Overview of Cyber Risk Management Introducing our Infosec Framework Infosec Strategic Roadmap
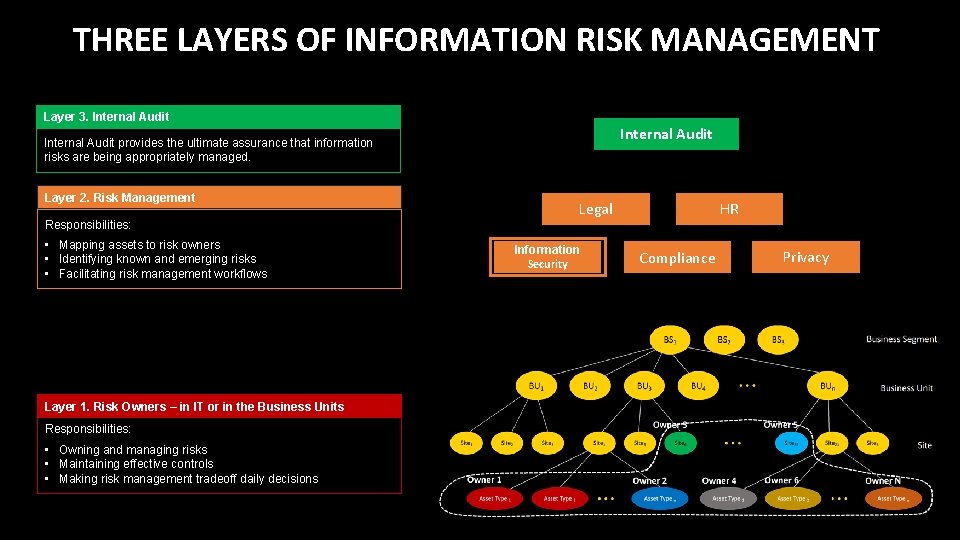
THREE LAYERS OF INFORMATION RISK MANAGEMENT Layer 3. Internal Audit provides the ultimate assurance that information risks are being appropriately managed. Layer 2. Risk Management Responsibilities: • Mapping assets to risk owners • Identifying known and emerging risks • Facilitating risk management workflows Layer 1. Risk Owners – in IT or in the Business Units Responsibilities: • Owning and managing risks • Maintaining effective controls • Making risk management tradeoff daily decisions Legal Information Security HR Compliance Privacy
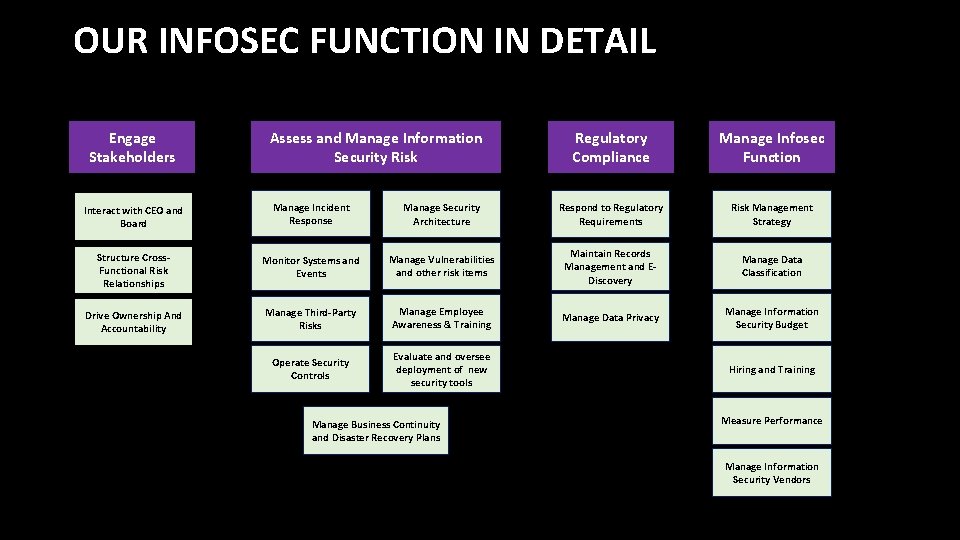
OUR INFOSEC FUNCTION IN DETAIL Engage Stakeholders Assess and Manage Information Security Risk Regulatory Compliance Manage Infosec Function Interact with CEO and Board Manage Incident Response Manage Security Architecture Respond to Regulatory Requirements Risk Management Strategy Structure Cross. Functional Risk Relationships Monitor Systems and Events Manage Vulnerabilities and other risk items Maintain Records Management and EDiscovery Manage Data Classification Drive Ownership And Accountability Manage Third-Party Risks Manage Employee Awareness & Training Manage Data Privacy Manage Information Security Budget Operate Security Controls Evaluate and oversee deployment of new security tools Manage Business Continuity and Disaster Recovery Plans Hiring and Training Measure Performance Manage Information Security Vendors

Infosec is a Board-Level Topic AGENDA Overview of Cyber Risk Management Introducing our Infosec Framework Infosec Strategic Roadmap
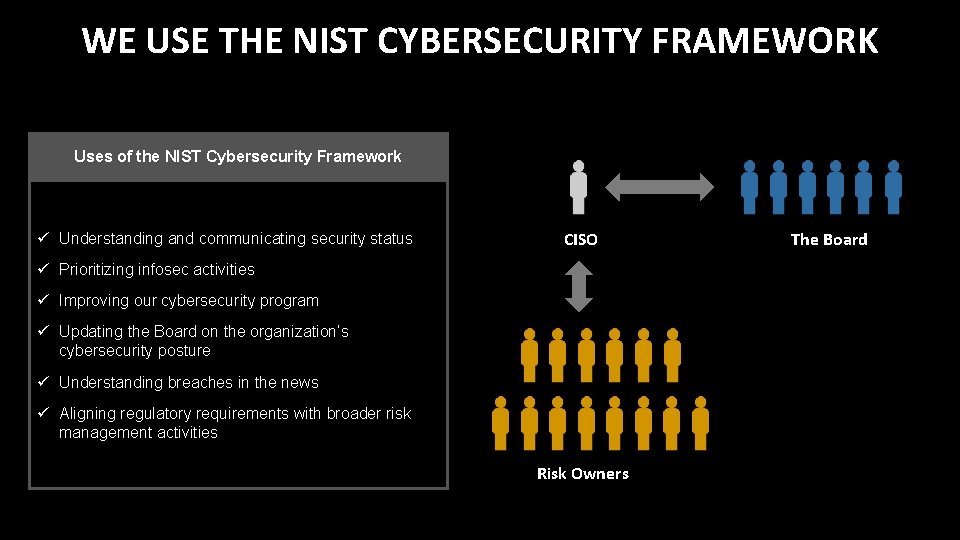
WE USE THE NIST CYBERSECURITY FRAMEWORK Uses of the NIST Cybersecurity Framework ü Understanding and communicating security status CISO ü Prioritizing infosec activities ü Improving our cybersecurity program ü Updating the Board on the organization’s cybersecurity posture ü Understanding breaches in the news ü Aligning regulatory requirements with broader risk management activities Risk Owners The Board

WE USE THE NIST CYBERSECURITY FRAMEWORK Capability Description Identify What processes and assets need protection? Protect Implement appropriate safeguards to ensure protection of the enterprise’s assets Detect Implement appropriate mechanisms to identify the occurrence of cybersecurity incidents Respond Develop techniques to contain the impacts of cybersecurity events Recover Implement the appropriate processes to restore capabilities and services impaired due to cybersecurity events
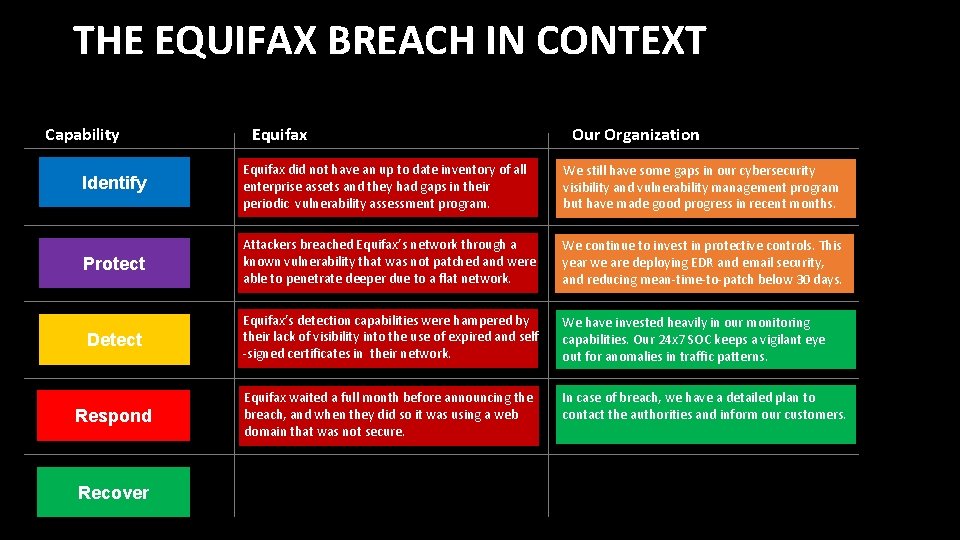
THE EQUIFAX BREACH IN CONTEXT Capability Equifax Our Organization Identify Equifax did not have an up to date inventory of all enterprise assets and they had gaps in their periodic vulnerability assessment program. We still have some gaps in our cybersecurity visibility and vulnerability management program but have made good progress in recent months. Protect Attackers breached Equifax’s network through a known vulnerability that was not patched and were able to penetrate deeper due to a flat network. We continue to invest in protective controls. This year we are deploying EDR and email security, and reducing mean-time-to-patch below 30 days. Detect Equifax’s detection capabilities were hampered by their lack of visibility into the use of expired and self -signed certificates in their network. We have invested heavily in our monitoring capabilities. Our 24 x 7 SOC keeps a vigilant eye out for anomalies in traffic patterns. Respond Equifax waited a full month before announcing the breach, and when they did so it was using a web domain that was not secure. In case of breach, we have a detailed plan to contact the authorities and inform our customers. Recover
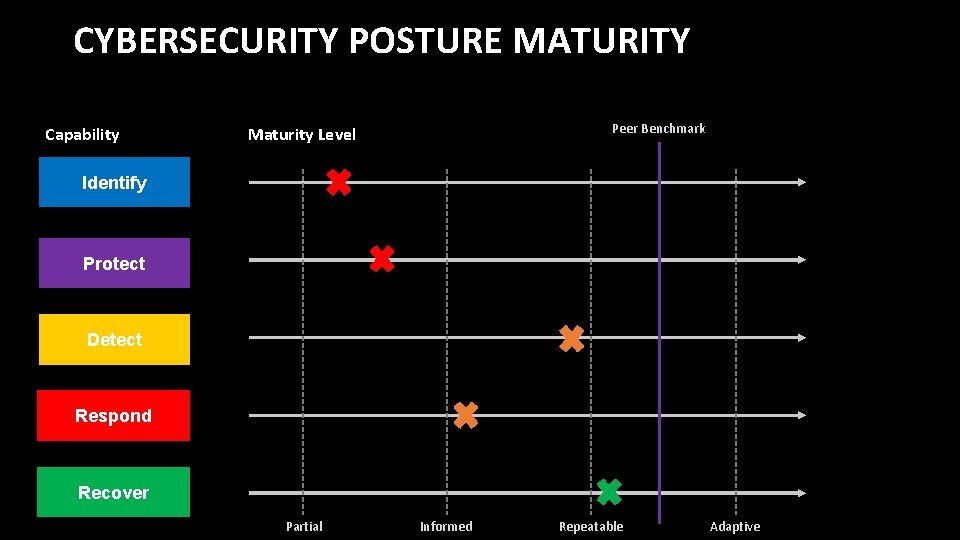
CYBERSECURITY POSTURE MATURITY Capability Peer Benchmark Maturity Level Identify Protect Detect Respond Recover Partial Informed Repeatable Adaptive

CYBERSECURITY KPIs: RISK, LIKELIHOOD & IMPACT Breach Risk Trend $17 M Risk Editable 48% $35 M Likelihood Impact 40 35 30 $M 25 20 15 10 5 0 Q 3 '19 Q 4 '19 Q 1 '20 There is a 48% chance that we will have an impact of $35 M from a cybersecurity event this year. Q 2 '20
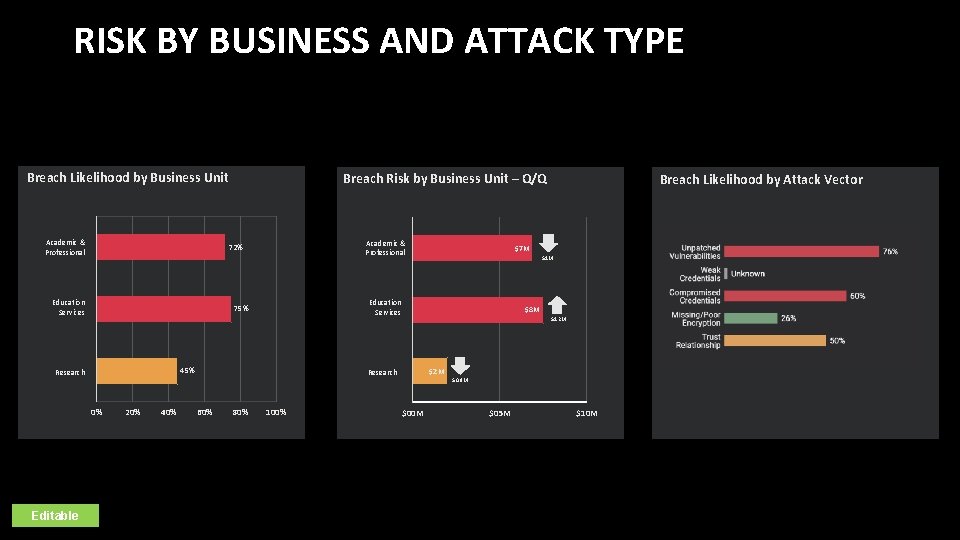
RISK BY BUSINESS AND ATTACK TYPE Breach Likelihood by Business Unit Academic & Professional 72% Education Services 45% 0% 20% 40% 80% $1 M $8 M $1. 2 M $2 M Research 60% 100% Breach Likelihood by Attack Vector $7 M Education Services 75% Research Editable Breach Risk by Business Unit – Q/Q $0. 9 M $00 M $05 M $10 M
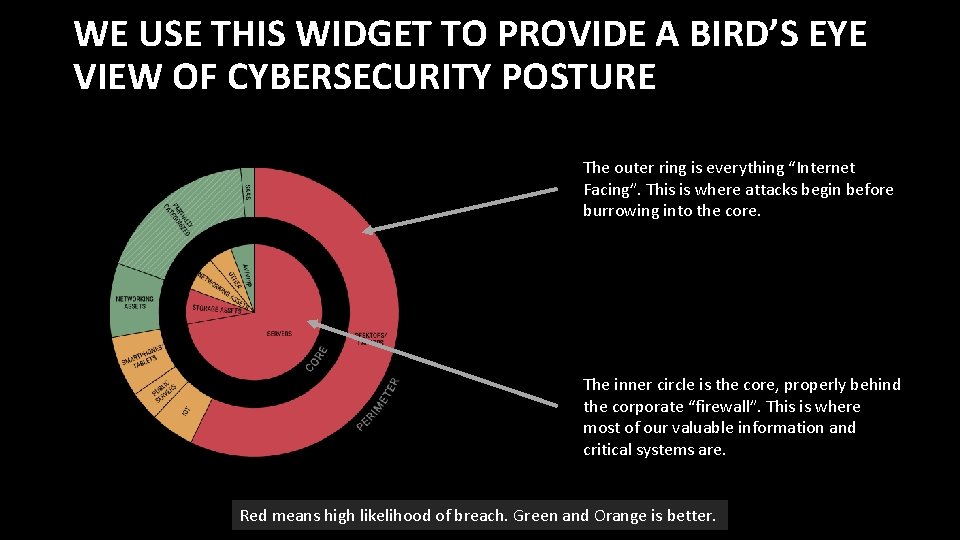
WE USE THIS WIDGET TO PROVIDE A BIRD’S EYE VIEW OF CYBERSECURITY POSTURE The outer ring is everything “Internet Facing”. This is where attacks begin before burrowing into the core. The inner circle is the core, properly behind the corporate “firewall”. This is where most of our valuable information and critical systems are. Red means high likelihood of breach. Green and Orange is better.
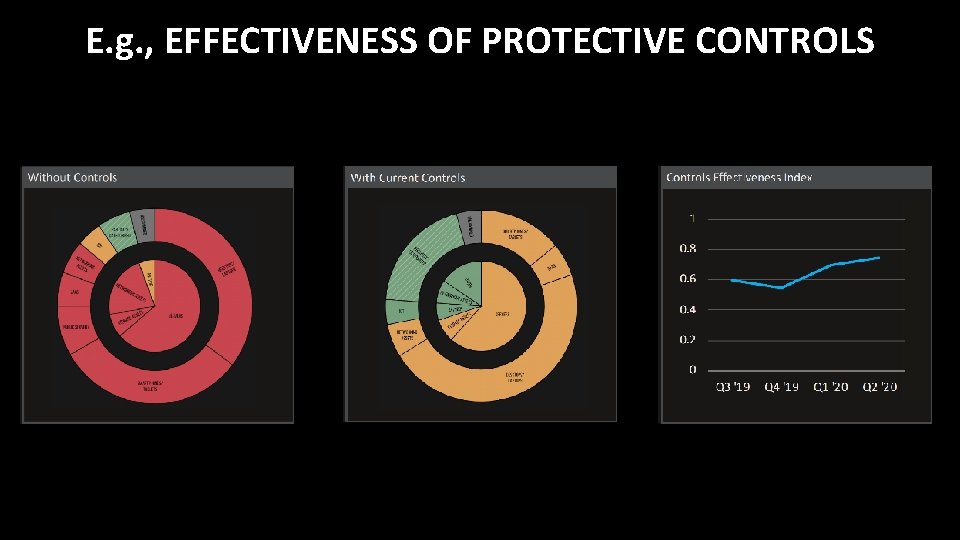
E. g. , EFFECTIVENESS OF PROTECTIVE CONTROLS
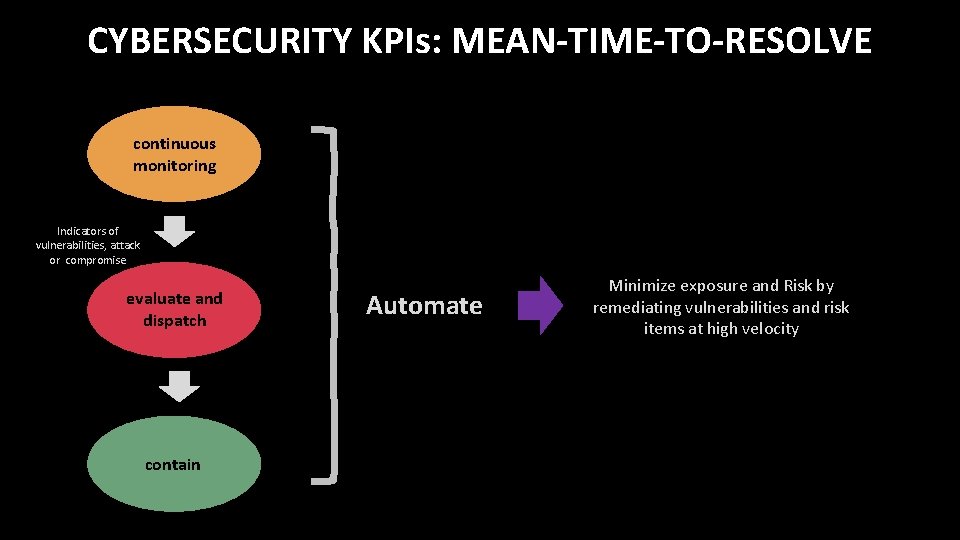
CYBERSECURITY KPIs: MEAN-TIME-TO-RESOLVE continuous monitoring Indicators of vulnerabilities, attack or compromise evaluate and dispatch contain Automate Minimize exposure and Risk by remediating vulnerabilities and risk items at high velocity

Infosec is a Board-Level Topic AGENDA Overview of Cyber Risk Management Introducing our Infosec Framework Infosec Strategic Roadmap
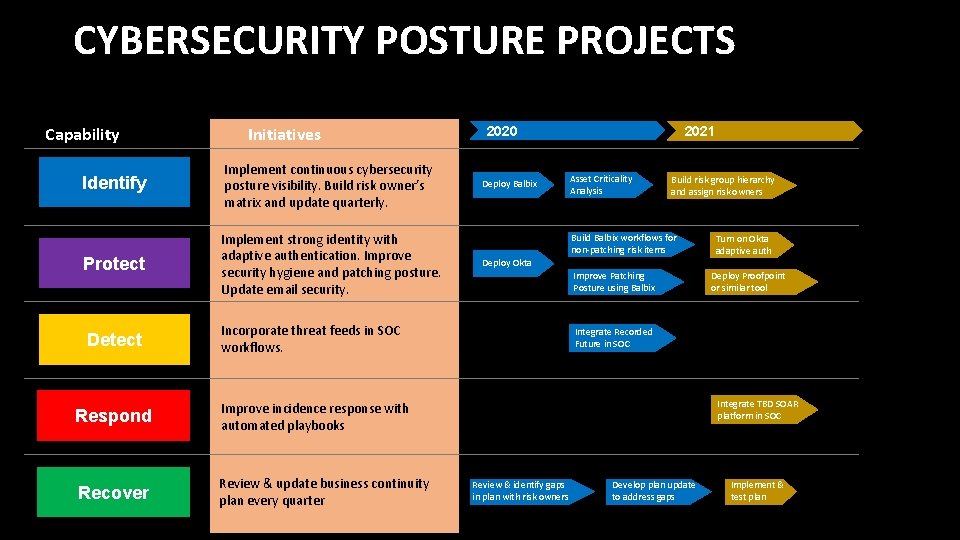
CYBERSECURITY POSTURE PROJECTS Capability Initiatives Identify Implement continuous cybersecurity posture visibility. Build risk owner’s matrix and update quarterly. Protect Implement strong identity with adaptive authentication. Improve security hygiene and patching posture. Update email security. Detect Incorporate threat feeds in SOC workflows. Respond Improve incidence response with automated playbooks Recover Review & update business continuity plan every quarter 2020 Deploy Balbix 2021 Asset Criticality Analysis Build risk group hierarchy and assign risk owners Build Balbix workflows for non-patching risk items Deploy Okta Improve Patching Posture using Balbix Turn on Okta adaptive auth Deploy Proofpoint or similar tool Integrate Recorded Future in SOC Integrate TBD SOAR platform in SOC Review & identify gaps in plan with risk owners Develop plan update to address gaps Implement & test plan
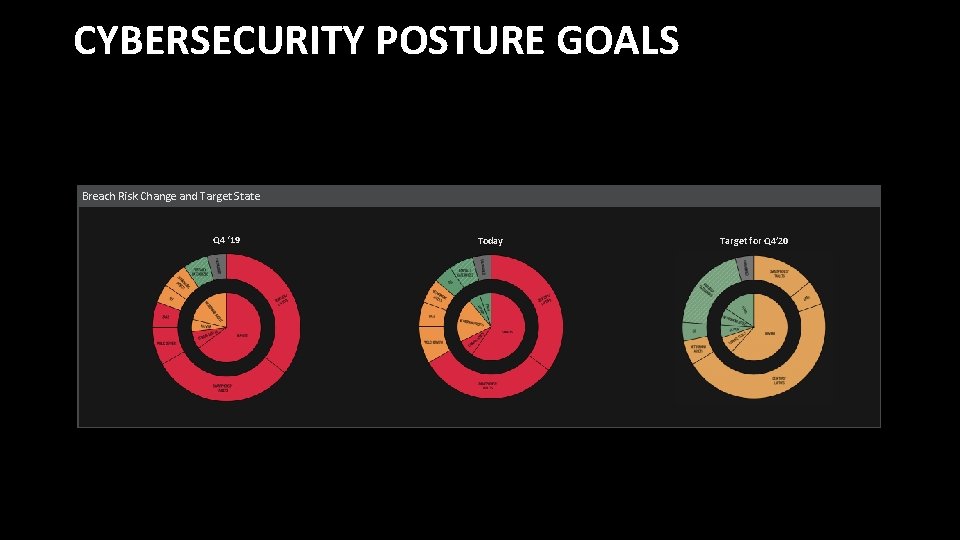
CYBERSECURITY POSTURE GOALS Breach Risk Change and Target State Q 4 ‘ 19 Today Target for Q 4’ 20
Q&A
delete this slide after use If you found these slides useful… Balbix can help you with many critical pieces of your Infosec program. The Balbix platform uses AI to help discover and analyze your assets and attack surface to Identify areas of greatest risk. This is foundational to effective capabilities for Protect , Detect , Respond and Recover. Balbix also enables you automate critical elements of your cybersecurity program and quantify changes in risk as you improve your cybersecurity posture. The next few slides has some additional examples of this. Start your free Balbix trial >>>
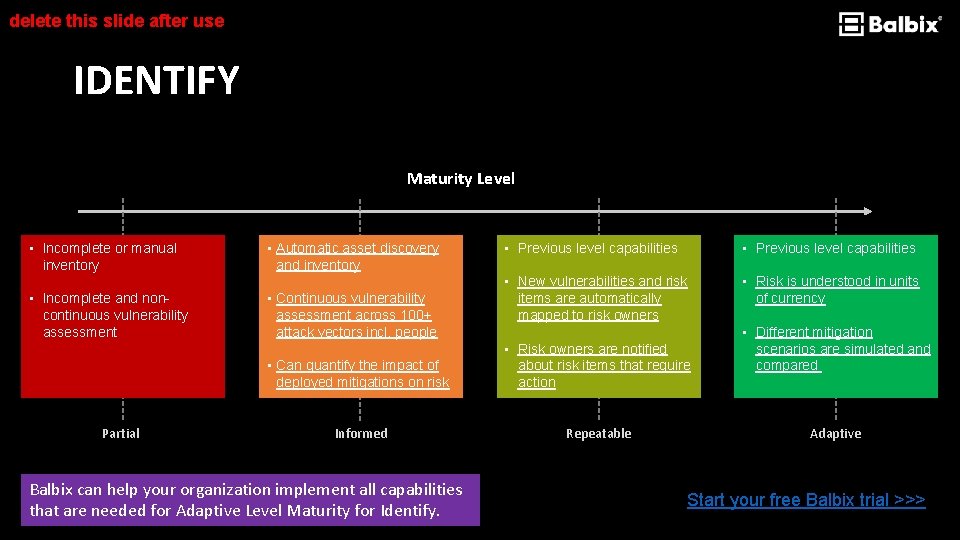
delete this slide after use IDENTIFY Maturity Level • Incomplete or manual inventory • Incomplete and noncontinuous vulnerability assessment Partial • Automatic asset discovery and inventory • Continuous vulnerability assessment across 100+ attack vectors incl. people • Previous level capabilities • New vulnerabilities and risk items are automatically mapped to risk owners • Risk is understood in units of currency • Can quantify the impact of deployed mitigations on risk • Risk owners are notified about risk items that require action Informed Repeatable Balbix can help your organization implement all capabilities that are needed for Adaptive Level Maturity for Identify. • Different mitigation scenarios are simulated and compared Adaptive Start your free Balbix trial >>>
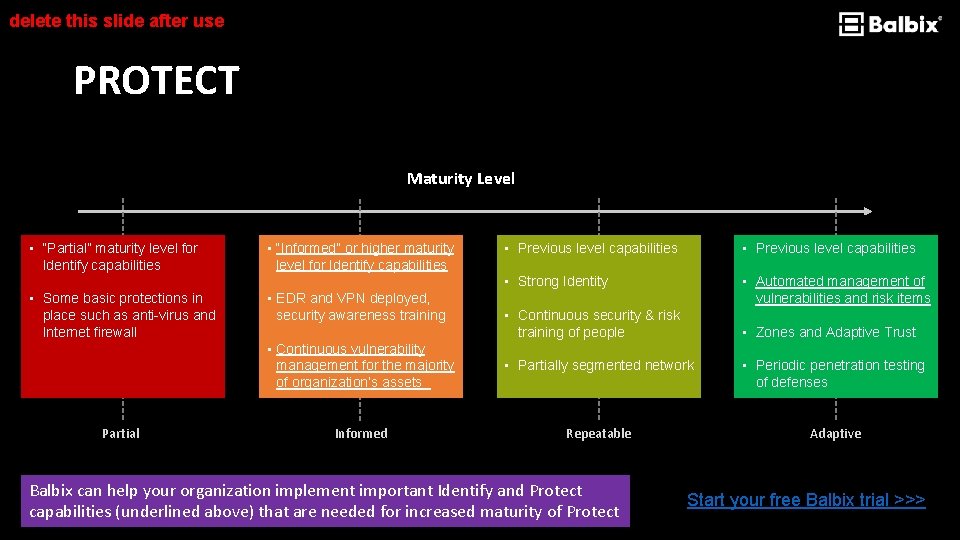
delete this slide after use PROTECT Maturity Level • “Partial” maturity level for Identify capabilities • Some basic protections in place such as anti-virus and Internet firewall Partial • “Informed” or higher maturity level for Identify capabilities • EDR and VPN deployed, security awareness training • Previous level capabilities • Strong Identity • Automated management of vulnerabilities and risk items • Continuous security & risk training of people • Zones and Adaptive Trust • Continuous vulnerability management for the majority of organization’s assets • Partially segmented network • Periodic penetration testing of defenses Informed Repeatable Adaptive Balbix can help your organization implement important Identify and Protect capabilities (underlined above) that are needed for increased maturity of Protect Start your free Balbix trial >>>
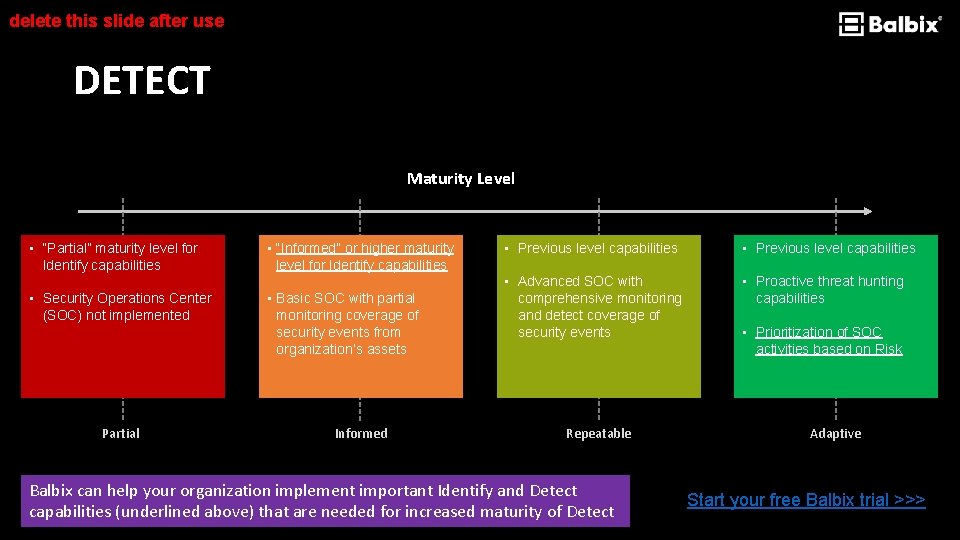
delete this slide after use DETECT Maturity Level • “Partial” maturity level for Identify capabilities • Security Operations Center (SOC) not implemented Partial • “Informed” or higher maturity level for Identify capabilities • Basic SOC with partial monitoring coverage of security events from organization’s assets Informed • Previous level capabilities • Advanced SOC with comprehensive monitoring and detect coverage of security events • Proactive threat hunting capabilities Repeatable Balbix can help your organization implement important Identify and Detect capabilities (underlined above) that are needed for increased maturity of Detect • Prioritization of SOC activities based on Risk Adaptive Start your free Balbix trial >>>
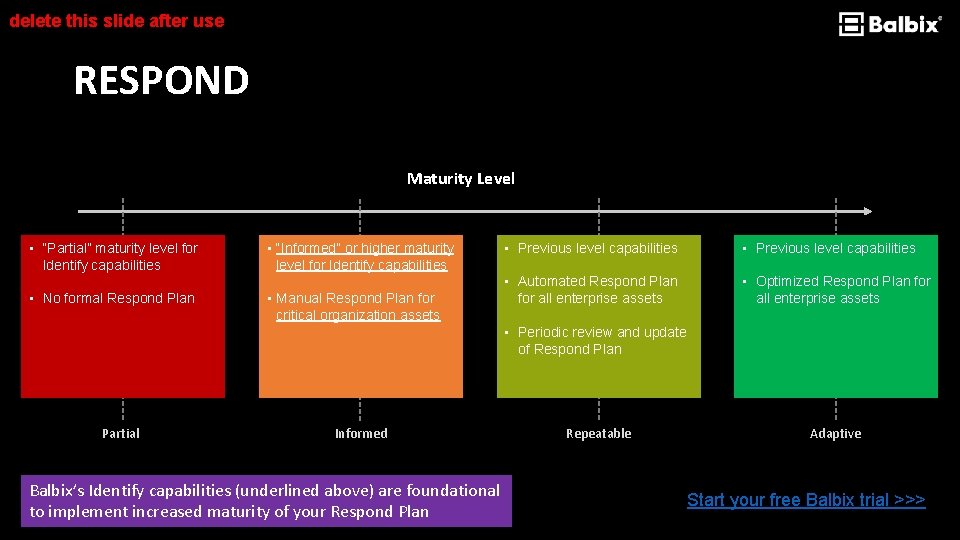
delete this slide after use RESPOND Maturity Level • “Partial” maturity level for Identify capabilities • No formal Respond Plan • “Informed” or higher maturity level for Identify capabilities • Manual Respond Plan for critical organization assets • Previous level capabilities • Automated Respond Plan for all enterprise assets • Optimized Respond Plan for all enterprise assets • Periodic review and update of Respond Plan Partial Informed Balbix’s Identify capabilities (underlined above) are foundational to implement increased maturity of your Respond Plan Repeatable Adaptive Start your free Balbix trial >>>
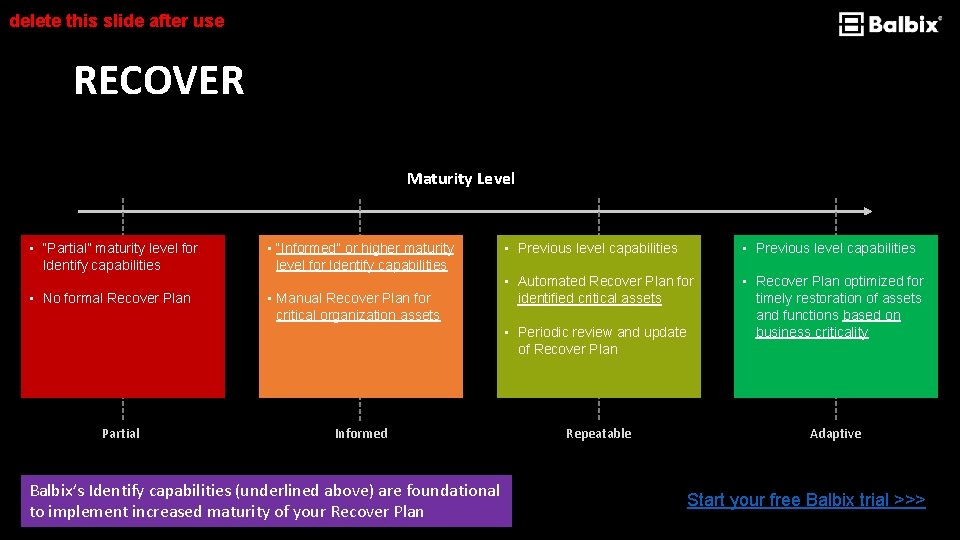
delete this slide after use RECOVER Maturity Level • “Partial” maturity level for Identify capabilities • No formal Recover Plan • “Informed” or higher maturity level for Identify capabilities • Manual Recover Plan for critical organization assets • Previous level capabilities • Automated Recover Plan for identified critical assets • Recover Plan optimized for timely restoration of assets and functions based on business criticality • Periodic review and update of Recover Plan Partial Informed Balbix’s Identify capabilities (underlined above) are foundational to implement increased maturity of your Recover Plan Repeatable Adaptive Start your free Balbix trial >>>
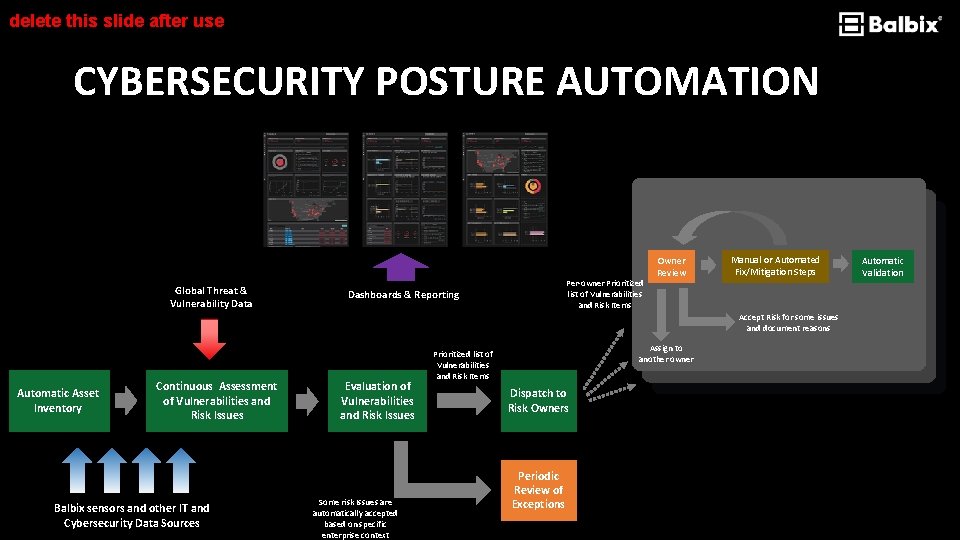
delete this slide after use CYBERSECURITY POSTURE AUTOMATION Global Threat & Vulnerability Data Per-owner Prioritized list of Vulnerabilities and Risk Items Dashboards & Reporting Owner Review Manual or Automated Fix/Mitigation Steps Accept Risk for some issues and document reasons Automatic Asset Inventory Continuous Assessment of Vulnerabilities and Risk Issues Balbix sensors and other IT and Cybersecurity Data Sources Evaluation of Vulnerabilities and Risk Issues Some risk Issues are automatically accepted based on specific enterprise context Assign to another owner Prioritized list of Vulnerabilities and Risk Items Dispatch to Risk Owners Periodic Review of Exceptions Automatic Validation
LEARN MORE ABOUT BALBIX In 30 minutes, we will show Balbix can help you automate your cybersecurity posture. With Balbix, you will use AI, automation and gamification to discover, prioritize and mitigate your unseen vulnerabilities at high velocity. Request a Demo https: //www. balbix. com/request-a-demo/ A single, comprehensive view of cybersecurity posture
delete this slide after use Good Luck! Start your free Balbix trial >>>
- Slides: 39