CISA REVIEW The material provided in this slide














































- Slides: 48

CISA REVIEW The material provided in this slide show came directly from Certified Information Systems Auditor (CISA) Review Material 2010 by ISACA.

CISA REVIEW Chapter 2 – Governance Learning Objectives • • Evaluate the effectiveness of IT governance structure to ensure adequate board control over the decisions, directions and performance of IT, so it supports the organization's strategies and objectives Evaluate IT organizational structure and human resources (personnel) management to ensure that they support the organization's strategies and objectives Evaluate the IT strategy and process for their development, approval, implementation and maintenance to ensure that they support the organization's strategies and objectives Evaluate the organization's IT policies, standards, procedures and processes for their development, approval, implementation and maintenance to ensure that they support the IT strategy and comply with regulatory and legal requirements Evaluate management practices to ensure compliance with the organization's IT strategy, policies, standards and procedures Evaluate IT resource investment, use and allocation practices to ensure alignment with the organization's strategies and objectives Evaluate risk management practices to ensure that the organization's IT-related risks are properly managed Evaluate monitoring and assurance practices to ensure that the board and executive management receive sufficient and timely information about IT performance

CISA REVIEW Chapter 2 – Governance • IT governance is used to ensure that an organization's IT objectives are in alignment with its enterprise objectives. To ensure successful implementation of IT governance, an IS auditor needs to make certain that the organization's IS strategies are in alignment with the organization's business strategies. The IS auditor must also ensure that IS strategies comply with all local, regional and federal laws and regulations. • Other critical elements of an IS auditor's role in IT governance is to ensure that IS policies exist and adequately reflect the approved IS strategies, and that IS standards and procedures effectively enforce and communicate IS policies.

CISA REVIEW Chapter 2 – Governance • IT governance implies a system in which all stakeholders, including the board, internal customers and related areas such as finance, have the necessary input into the decision making process. This prevents a single stakeholder, typically IT, being blamed for poor decisions. It also prevents users from later complaining that the system does not behave or perform as expected. • The best way to implement IT governance so it has the most positive impact is to have collaborative senior management sponsorship between the business and IT operations. Lower management levels may have some success but when governance is departmental only, problems arise with projects that transcend departments that are not consistently managed using the same guidance.

CISA REVIEW Chapter 2 – Governance IT governance encompasses: • Information systems • Technology and communication • Business, legal and other issues such as regulatory compliance and security • All concerned stakeholders, directors, senior management, process owners, IT suppliers, users and auditors

CISA REVIEW Chapter 2 – Governance Chief executive officers (CEOs), chief financial officers (CFOs) and chief information officers (CIOs) agree that the strategic alignment between IT and enterprise objectives is a critical success factor for an organization.

CISA REVIEW Chapter 2 – Process Improvement IT governance is concerned that IT delivers value to the business and that IT risks are managed. The first is driven by strategic alignment of IT with the business. The second is driven by embedding accountability into the enterprise, which cannot be accomplished without effective measuring and reporting.

CISA REVIEW Chapter 2 – Governance • • • An IS auditor should assess the following organizational IT governance elements: Alignment of the IT function with the organization's mission, vision, values, objectives and strategies Achievement of IT function performance objectives established by the business (effectiveness and efficiency) including the measures used to determine success Legal, environmental, information quality, and fiduciary and security requirements The control environment of the organization The inherent risks within the IT environment The organization's documentation and contractual commitments

CISA REVIEW Chapter 2 – IT Strategy Committee As an industry best practice, all organizations should create an IT strategy committee. To incorporate IT governance into enterprise governance, a successful IT strategy committee must assist the board by: • Providing advice on strategy, IT value, risks and performance • Overseeing the enterprise's IT-related matters by ensuring that the board has the internal and external information it requires for effective IT governance decision-making

CISA REVIEW Chapter 2 – IT Steering Committee In addition to the IT strategy committee, an organization's senior management should appoint an IT planning or steering committee. The responsibilities and duties of this committee should be defined in a formal charter and include overseeing the IT function and its activities, and ensuring that the IT department is in agreement with the organization's mission and objectives.

CISA REVIEW Chapter 2 – IT Steering Committee The primary functions of the IT steering committee include the following: • Review the long- and short-range plans of the IT department to ensure that they are in accordance with the organization's objectives. • Review and approve major acquisitions of hardware and software within the limits approved by the board of directors. • Approve and monitor major projects and the status of IT plans and budgets; establish priorities; approve standards and procedures; and monitor overall IT performance. • Review and approve sourcing strategies for select, or all, IT activities, including insourcing or outsourcing, and the globalization or offshoring of functions. • Review adequacy of resources and allocation of resources in terms of time, personnel and equipment. • Make decisions regarding centralization vs. decentralization and assignment of responsibility. • Support development and implementation of an enterprisewide information security management program. • Report to the board of directors on IT activities.

CISA REVIEW Chapter 2 – IT Steering Committee • • • In order to effectively coordinate and monitor an organization's IT resources and IT steering committee must: Receive the appropriate management information from IT departments, user departments and audits Monitor performance and institute appropriate action to achieve desired results Meet regularly and report to senior management Maintain formal minutes to document the committee's activities and decisions Serve as a general review board for major IT projects and avoid becoming involved in routine operations

CISA REVIEW Chapter 2 – Strategic Planning An important element of strategic planning is to make sure that business and IT management work together toward a common goal. To do this: • IT management needs to have a better understanding of business issues and business unit management should also have a solid understanding of the reality of IT constraints. • All parties involved should have the ability to understand relate strategic plans between business needs and IT. Strategic plans should address how IT resources will addvalue to the business. IT resources add-value by mitigating risk and delivering and protecting information and allocating resources accordingly.

CISA REVIEW Chapter 2 – Policies and Procedures IT governance also includes overseeing the policies and procedures developed to guide and control information systems and related resources.

CISA REVIEW Chapter 2 – Information Security Policy Information security policies should guide the organization by defining what needs to be protected, responsibilities for protection, and the strategy that will be followed for protection. Information security policies should be developed in accordance with business requirements, and relevant laws and regulations. An organization's management should demonstrate support for and commitment to information security by issuing and maintaining information security policies that contain a clear direction.

CISA REVIEW Chapter 2 – Information Security Policy An organization's information security policy should be approved by management and: • Define the overall objective and scope of the organization's information security • Align the goals and principles of information security with the business strategy and objectives • Set the framework for risk assessment and risk management

CISA REVIEW Chapter 2 – Information Security Policy After an information security policy is approved by management, it should be published and communicated. The communication of this policy must be: • Communicated to all users in the organization, including internal and external workers, third parties and outsourcers • Provided in a form that is accessible and understandable to the intended reader

CISA REVIEW Chapter 2 – Information Security Management • • Information security management involves leading and facilitating the implementation of an organization wide IT security program to assure that the organization's information and the information-processing resources under its control are properly protected. This includes but is not limited to: Developing business continuity and disaster recovery plans (BCP and DRP) related to IT department functions in support of the organization's critical business processes Applying risk management principles to assess the risks to IT assets Mitigate risks to an appropriate level as determined by management Monitor the remaining residual risks

CISA REVIEW Chapter 2 – Information Access • • • Typical information security policies addressing information access include the following: Individuals are granted access to only those resources at or below a specific level of sensitivity. Labels are used to indicate the sensitivity level of electronically stored documents. Policy-based controls may be characterized as either mandatory or discretionary. Controls should not disrupt the usual work flow more than necessary or place too much burden on administrators, auditors or authorized users. Access controls must adequately protect all the organization's resources.

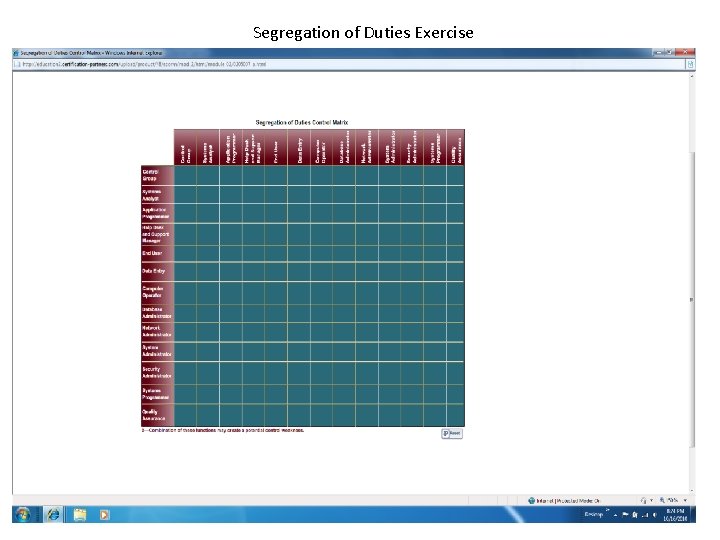
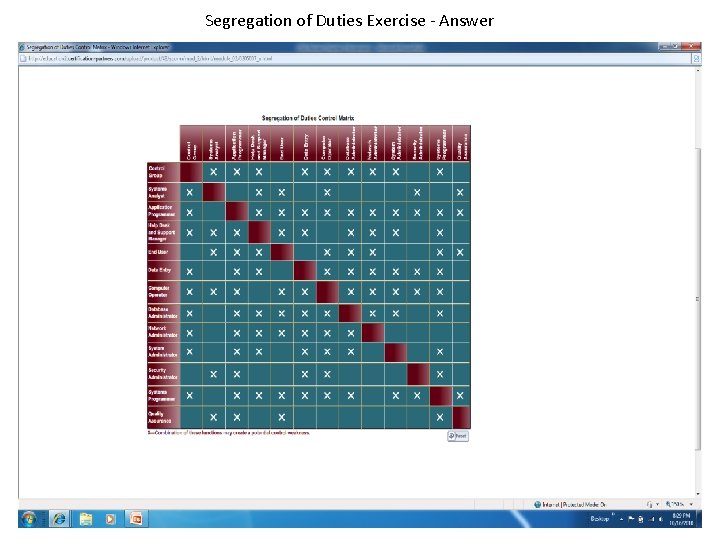
CISA REVIEW Chapter 2 – Segregation of Duties • The purpose of segregating duties is to aid an organization in reducing some of its business risks through the identification of compensating controls. • For example, when duties are segregated, access to the computer, the production data library, the production programs, the programming documentation, and the operating system and associated utilities can be limited, and potential damage from the actions of any one person is, therefore, reduced.

CISA REVIEW Chapter 2 – Segregation of Duties Several control mechanisms can be used to enforce segregation of duties. Examples of these controls are: • Transaction authorization • Assets/data ownership • Access to data Proper segregation prevents misappropriation of assets, misstated financial statements, inaccurate financial documentation (i. e. , errors or irregularities), and improper use of funds or not detecting data modifications.

CISA REVIEW Chapter 2 – Segregation of Duties Transaction authorization is the responsibility of the data owner. Authorization is delegated to the degree that it relates to the particular level of responsibility of the authorized individual in the department. Periodic checks must be performed by management and audit to determine that adequate authorization policies and procedures exist and are implemented.

CISA REVIEW Chapter 2 – Segregation of Duties Ownership of assets/data must be determined and assigned appropriately. The data owner usually is assigned to a particular user department, and his/her duties should be specific and in writing. The owner of the data has responsibility for determining authorization levels required to limit the exposure of data being accessed by people without a justification to see, modify or use it.

CISA REVIEW Chapter 2 – Segregation of Duties Controls over access to data are provided by a combination of physical, system, and application security and personnel controls in the user area and the information process facility.

CISA REVIEW Chapter 2 – Segregation of Duties Information technology and end-user departments should be organized so any single individual does not have too much control or responsibility over critical functions. With segregation of duties, the misuse of data or fraud can be detected in a timely manner and in the normal course of business processes.

Segregation of Duties Exercise

Segregation of Duties Exercise - Answer

CISA REVIEW Chapter 2 – Compensating Controls Of course there will be situations were weaknesses exist with segregation of duties (e. g. smaller organizations with fewer staff). In these situations, compensating controls can be used. Compensating controls include: • Audit trails • Reconciliation • Exception reporting • Transaction logs • Supervisor reviews • Independent reviews

CISA REVIEW Chapter 2 – Compensating Controls Audit trails are an essential component of all welldesigned systems. Audit trails enable the user departments and IS auditor to re-create the actual transaction flow from the point of origination to its existence on an updated file. In the absence of adequate segregation of duties, good audit trails may be an acceptable compensating control. The IS auditor should be able to determine who initiated the transaction, the time of day and date of entry, the type of entry, what fields of information it contained, and what files it updated.

CISA REVIEW Chapter 2 – Compensating Controls Audit trails are an essential component of all welldesigned systems. Audit trails enable the user departments and IS auditor to re-create the actual transaction flow from the point of origination to its existence on an updated file. In the absence of adequate segregation of duties, good audit trails may be an acceptable compensating control. The IS auditor should be able to determine who initiated the transaction, the time of day and date of entry, the type of entry, what fields of information it contained, and what files it updated.

CISA REVIEW Chapter 2 – Compensating Controls Reconciliation is ultimately the responsibility of the user department. In some organizations, limited reconciliation of applications may be performed by the data control group with the use of control totals and balancing sheets. This type of independent verification increases the level of confidence that the application processed successfully and the data are in proper balance.

CISA REVIEW Chapter 2 – Compensating Controls Exception reporting should be handled at the supervisory level and should require evidence, such as initials on a report, noting that the exception has been handled properly. Management should also ensure that exceptions are resolved in a timely manner.

CISA REVIEW Chapter 2 – Compensating Controls A transaction log may be manual or automated. An example of a manual log is a record of transactions (grouped or batched) before they are submitted for processing. An automated transaction log or journal provides a record of all transactions processed, and it is maintained by the computer system.

CISA REVIEW Chapter 2 – Compensating Controls Supervisory reviews may be performed through observation and inquiry or remotely.

CISA REVIEW Chapter 2 – Compensating Controls Independent reviews are carried out to compensate for mistakes or intentional failures in following prescribed procedures. These are particularly important when duties in a small organization cannot be appropriately segregated. Such reviews will help detect errors or irregularities.

CISA REVIEW Chapter 2 – Risk Management Effective IT governance will enable an organization to manage and execute appropriate measures to mitigate risks and reduce potential impacts on information resources to an acceptable level. To achieve this level of risk management, an organization must maintain: • A collective understanding of the organizations threat, vulnerability and risk profile consistent with the management's risk philosophy and position • An understanding of risk exposure and potential consequences of compromise including the regulatory, legal, operational and brand impacts • An awareness of risk management priorities based on potential consequences • Risk mitigation sufficient to achieve acceptable consequences from residual risk • Risk acceptance/deference based on an understanding of the potential consequences of residual risk

CISA REVIEW Chapter 2 – Risk Management Risk management is the process an organization must go through to: • Identify any vulnerabilities and threats to its information resources • Decide on the countermeasures to take which may reduce any risk to an acceptable level An organization must define its risk appetite and its identified risk exposure before it can develop effective risk management strategies or determine what roles and responsibilities are necessary.

CISA REVIEW Chapter 2 – Risk Management When an organization finds risk, depending on the type of risk and its significance to the business, management and the board have five options: • Avoid the risk • Mitigate the risk • Transfer the risk • Accept the risk • Eliminate the risk

CISA REVIEW Chapter 2 – Risk Management Once risks have been identified, an organization must evaluate existing controls or develop new controls to reduce the vulnerabilities to an acceptable level of risk. The strength of a control can be measured in terms of its inherent or design strength and the likelihood of its effectiveness. Elements of controls that should be considered when evaluating control strength include whether the controls are: • Preventive or detective • Manual or programmed • Formal or ad hoc

CISA REVIEW Chapter 2 – Risk Management Once controls have been applied, any remaining risk is called residual risk. Residual risks can be used by management to identify those areas where they can reduce risk even further or where more control is required.

CISA REVIEW Chapter 2 – Process Improvement Typically, organizations need to measure where they are and where improvement is required, and continuously monitor this improvement. Cost-benefit also needs to be considered along with the following questions: • What are industry peers doing, and how is your organization placed in relation to them? • How is your organization placed with regard to industry good practices? • Based on these comparisons, can your organization be said to be doing enough? • How can your organization identify what is required to be done to reach an adequate level of management and control over its IT processes?

CISA REVIEW Chapter 2 – Process Improvement An organization has different levels of process maturity when compared to their peers. In order to assess their maturity level the organization should provide: • A set of requirements and the enabling aspects at the different maturity levels • A scale where the difference can be made measurable • A scale that lends itself to comparison • The basis for setting as-is and to-be positions • Support for gap analysis to determine what needs to be done to achieve a chosen level • Taken together, a view of how IT is managed in the enterprise

CISA REVIEW Chapter 2 – IT Balanced Scorecard Goals and metrics that comprise the IT balanced scorecard can be defined at three levels: • IT goals and metrics that define what the business expects from IT and how to measure it • Process goals and metrics that define what the IT process must deliver to support IT's objectives and how to measure it • Activity goals and metrics that establish what needs to happen inside the process to achieve the required performance and how to measure it

CISA REVIEW Chapter 2 – HR All organizations should have a variety of policies regarding human resource issues. Examples of these policies are training, scheduling and time reporting, employee performance evaluations, and required vacations. • Training • Scheduling and Time Reporting • Employee Performance Evaluations • Vacations Organizations should also have a published code of conduct that specifies all employees' responsibilities to the organization.

CISA REVIEW Chapter 2 – HR An IS auditor has several responsibilities when evaluating elements of IT human resource management and how it affects an organization's IT governance. These responsibilities include looking for indicators of potential staffing weaknesses or problems such as: • High staff turnover • Inexperienced staff • Lack of succession plans • Lack of adequate training Additionally, an IS auditor reviewing an organization's IT resource management should verify that job descriptions, human resource manuals, and organizational charts are in place, accurate and updated regularly.

CISA REVIEW Chapter 2 – IT Resource Allocation When developing an IS strategic plan, senior management is responsible for identifying cost-effective IT solutions to address the organization's problems and opportunities. It is important that the strategic planning process encompasses not just the delivery of new systems and technology, but considers the returns being achieved from investments in existing technology. This can be done using the following: • Considering the return on investment (ROI) and total cost of ownership for all endeavors • Understanding allocation practices • Effective budgeting • Change management

CISA REVIEW Chapter 2 – IT Resource Allocation What are the strategic issues that need to be addressed relative to value? • A clear and shared understanding of the expected benefits • Clear accountability for realizing the benefits • Relevant metrics • An effective benefits realization process

CISA REVIEW Chapter 2 – IT Resource Allocation How do post implementation reviews impact value? A post implementation review is a review of the implementation process against the methodology and budgeting of the project, and measuring the expected results against the success metrics. The IS auditor and the IT project team need to review results and develop steps for improvement.