Applications Have Changed Why Hasnt the Firewall Dave














- Slides: 38

Applications Have Changed. Why Hasn’t the Firewall? Dave Smith 214. 674. 7854 dsmith@paloaltonetworks. com Von Nguyen 713. 301. 9929 vnguyen@paloaltonetworks. com

About Palo Alto Networks • Founded by security visionary Nir Zuk • World class team with strong security and networking experience • Built family of next generation firewalls with control of 600+ applications • Named Gartner Cool Vendor in 2008 • Best of Interop Grand Prize, Best of Interop Security 2008 Page 2 | © 2008 Palo Alto Networks. Proprietary and Confidential.

Leading Organizations Trust Palo Alto Networks Health Care Financial Services Government Media / Entertainment / Retail Services Page 3 | Mfg / High Tech / Energy © 2007 Palo Alto Networks. Proprietary and Confidential Education

Why Palo Alto Networks?

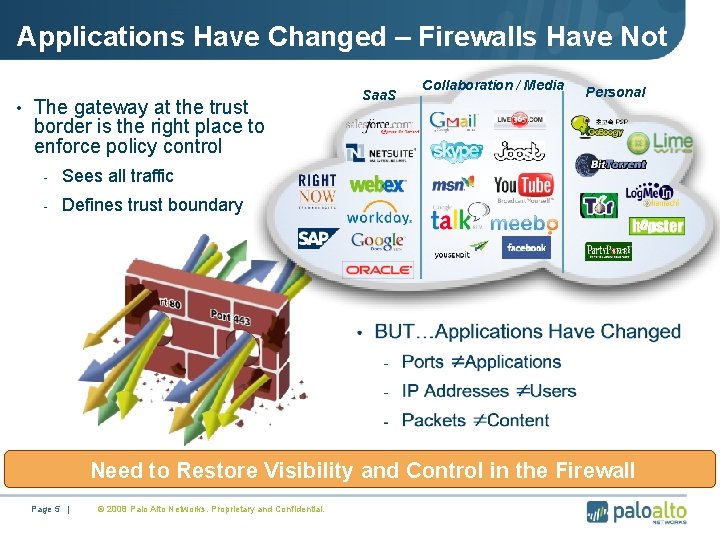
Applications Have Changed – Firewalls Have Not • The gateway at the trust Saa. S Collaboration / Media Personal border is the right place to enforce policy control - Sees all traffic - Defines trust boundary Need to Restore Visibility and Control in the Firewall Page 5 | © 2008 Palo Alto Networks. Proprietary and Confidential.

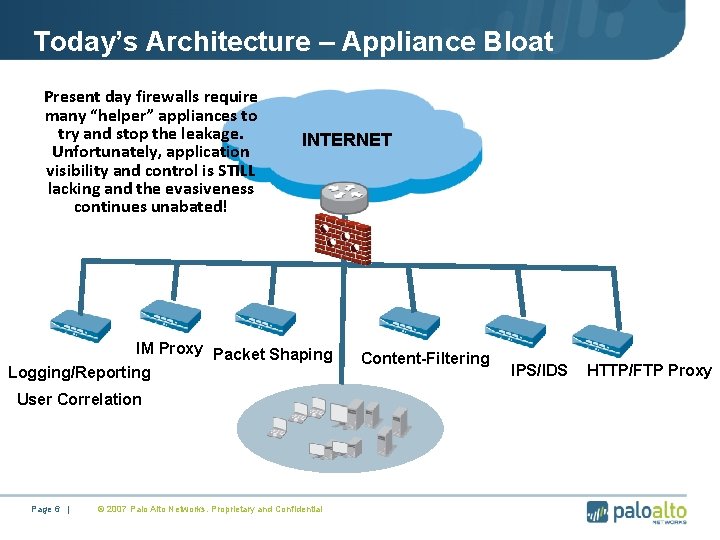
Today’s Architecture – Appliance Bloat Present day firewalls require many “helper” appliances to try and stop the leakage. Unfortunately, application visibility and control is STILL lacking and the evasiveness continues unabated! INTERNET • IM Proxy Packet Shaping Logging/Reporting User Correlation Page 6 | © 2007 Palo Alto Networks. Proprietary and Confidential • Content-Filtering • IPS/IDS • HTTP/FTP Proxy

Palo Alto – Next Generation Firewall Next-generation firewall based on App-ID™ traffic classification technology Identifies over 700+ applications regardless of port, protocol or evasive tactic Policy based decryption, identification and control of SSL applications Application Command Center (ACC) for granular visibility & policy control of applications Flash. Match™ engine for real-time threat prevention Dedicated hardware processing for 10 Gbps in-line operation with no network degradation Designed to transparently augment existing firewall Page 7 | © 2007 Palo Alto Networks. Proprietary and Confidential

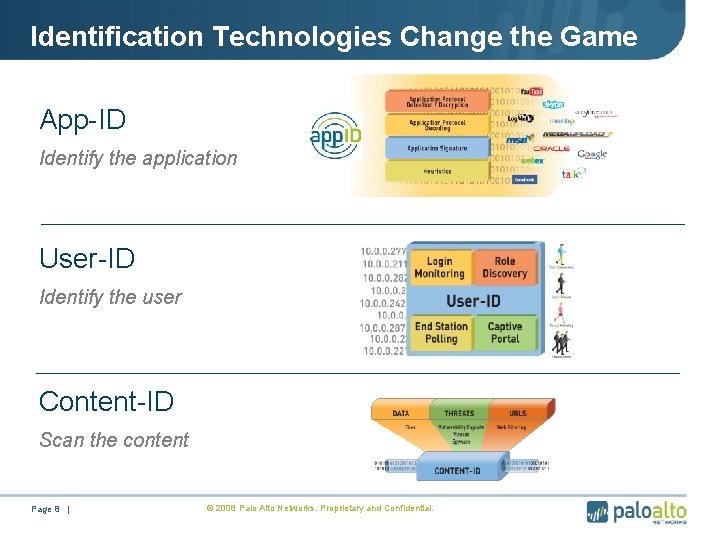
Identification Technologies Change the Game App-ID Identify the application User-ID Identify the user Content-ID Scan the content Page 8 | • © 2008 Palo Alto Networks. Proprietary and Confidential.

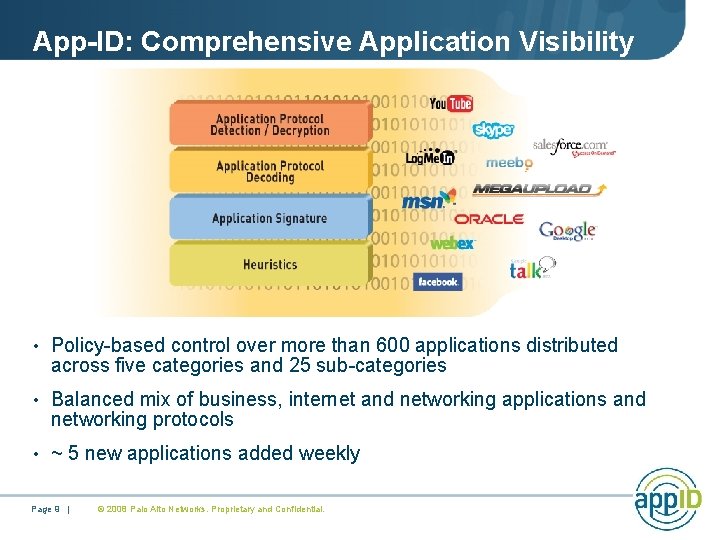
App-ID: Comprehensive Application Visibility • Policy-based control over more than 600 applications distributed across five categories and 25 sub-categories • Balanced mix of business, internet and networking applications and networking protocols • ~ 5 new applications added weekly Page 9 | © 2008 Palo Alto Networks. Proprietary and Confidential.

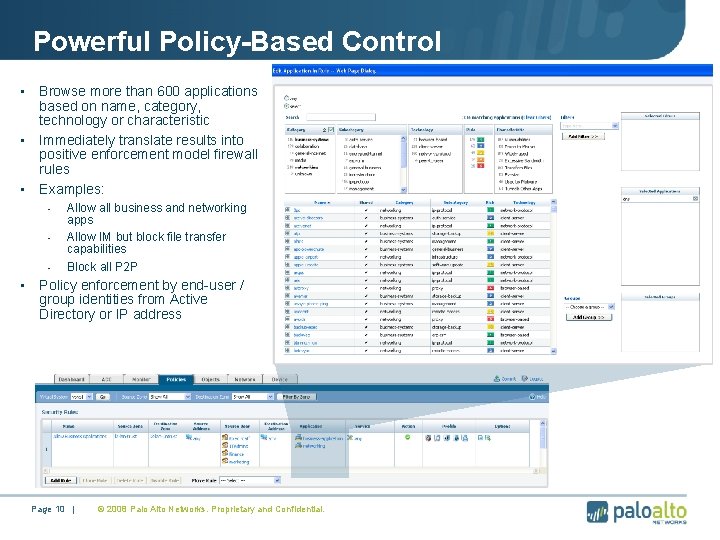
Powerful Policy-Based Control Browse more than 600 applications based on name, category, technology or characteristic • Immediately translate results into positive enforcement model firewall rules • Examples: • - • Allow all business and networking apps Allow IM but block file transfer capabilities Block all P 2 P Policy enforcement by end-user / group identities from Active Directory or IP address Page 10 | © 2008 Palo Alto Networks. Proprietary and Confidential.

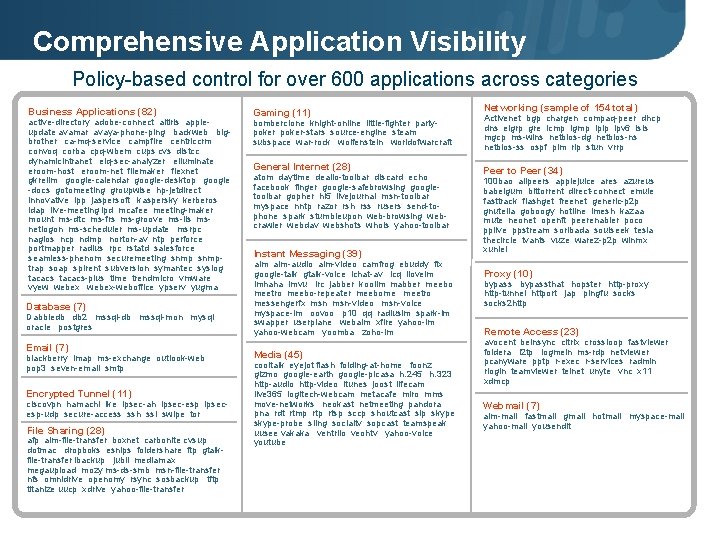
Comprehensive Application Visibility Policy-based control for over 600 applications across categories Business Applications (82) active-directory adobe-connect altiris appleupdate avamar avaya-phone-ping backweb bigbrother ca-mq-service campfire centriccrm convoq corba cpq-wbem cups cvs distcc dynamicintranet eiq-sec-analyzer elluminate eroom-host eroom-net filemaker flexnet gkrellm google-calendar google-desktop google -docs gotomeeting groupwise hp-jetdirect innovative ipp jaspersoft kaspersky kerberos ldap live-meeting lpd mcafee meeting-maker mount ms-dtc ms-frs ms-groove ms-iis msnetlogon ms-scheduler ms-update msrpc nagios ncp ndmp norton-av ntp perforce portmapper radius rpc rstatd salesforce seamless-phenom securemeeting snmptrap soap spirent subversion symantec syslog tacacs-plus time trendmicro vmware vyew webex-weboffice ypserv yugma Database (7) Dabbledb db 2 mssql-db mssql-mon mysql oracle postgres Email (7) blackberry imap ms-exchange outlook-web pop 3 seven-email smtp Encrypted Tunnel (11) ciscovpn hamachi ike ipsec-ah ipsec-esp ipsecesp-udp secure-access ssh ssl swipe tor File Sharing (28) afp aim-file-transfer boxnet carbonite cvsup dotmac dropboks esnips foldershare ftp gtalkfile-transfer ibackup jubii mediamax megaupload mozy ms-ds-smb msn-file-transfer nfs omnidrive openomy rsync sosbackup tftp titanize uucp xdrive yahoo-file-transfer Page 11 | Gaming (11) Networking (sample of 154 total) General Internet (28) Peer to Peer (34) bomberclone knight-online little-fighter partypoker-stars source-engine steam subspace war-rock wolfenstein worldofwarcraft atom daytime dealio-toolbar discard echo facebook finger google-safebrowsing googletoolbar gopher hi 5 livejournal msn-toolbar myspace nntp razor rsh rss rusers send-tophone spark stumbleupon web-browsing webcrawler webdav webshots whois yahoo-toolbar Instant Messaging (39) aim-audio aim-video camfrog ebuddy fix google-talk gtalk-voice ichat-av icq iloveim imhaha imvu irc jabber koolim mabber meebo meetro meebo-repeater meebome meetro messengerfx msn-video msn-voice myspace-im oovoo p 10 qq radiusim spark-im swapper userplane webaim xfire yahoo-im yahoo-webcam yoomba zoho-im Media (45) cooltalk eyejot flash folding-at-home foonz gizmo google-earth google-picasa h. 245 h. 323 http-audio http-video itunes joost lifecam live 365 logitech-webcam metacafe miro mms move-networks neokast netmeeting pandora pna rdt rtmp rtsp sccp shoutcast sip skype-probe sling socialtv sopcast teamspeak uusee vakaka ventrilo veohtv yahoo-voice youtube © 2007 Palo Alto Networks. Proprietary and Confidential Activenet bgp chargen compaq-peer dhcp dns eigrp gre icmp igmp ipip ipv 6 isis mgcp ms-wins netbios-dg netbios-ns netbios-ss ospf pim rip stun vrrp 100 bao allpeers applejuice ares azureus babelgum bittorrent direct-connect emule fasttrack flashget freenet generic-p 2 p gnutella goboogy hotline imesh kazaa mute neonet openft peerenabler poco pplive ppstream soribada soulseek tesla thecircle tvants vuze warez-p 2 p winmx xunlei Proxy (10) bypassthat hopster http-proxy http-tunnel httport jap pingfu socks 2 http Remote Access (23) avocent beinsync citrix crossloop fastviewer foldera l 2 tp logmein ms-rdp netviewer pcanyware pptp r-exec r-services radmin rlogin teamviewer telnet unyte vnc x 11 xdmcp Webmail (7) aim-mail fastmail gmail hotmail myspace-mail yahoo-mail yousendit

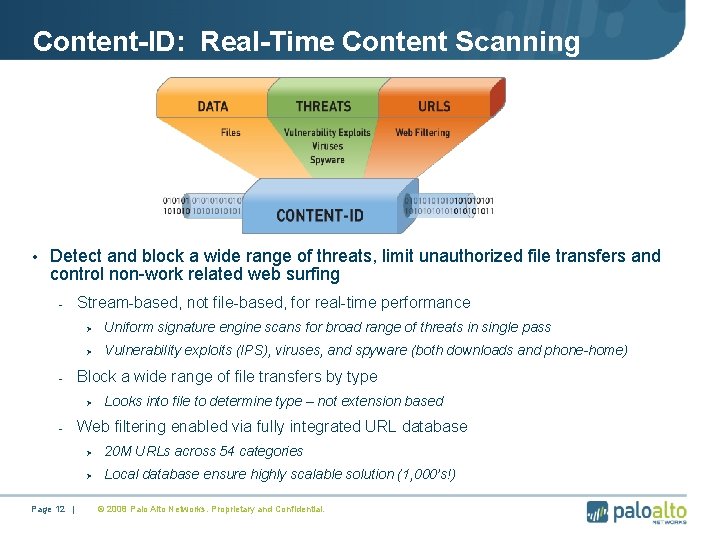
Content-ID: Real-Time Content Scanning • Detect and block a wide range of threats, limit unauthorized file transfers and control non-work related web surfing - - Stream-based, not file-based, for real-time performance Ø Uniform signature engine scans for broad range of threats in single pass Ø Vulnerability exploits (IPS), viruses, and spyware (both downloads and phone-home) Block a wide range of file transfers by type Ø - Page 12 | Looks into file to determine type – not extension based Web filtering enabled via fully integrated URL database Ø 20 M URLs across 54 categories Ø Local database ensure highly scalable solution (1, 000’s!) © 2008 Palo Alto Networks. Proprietary and Confidential.

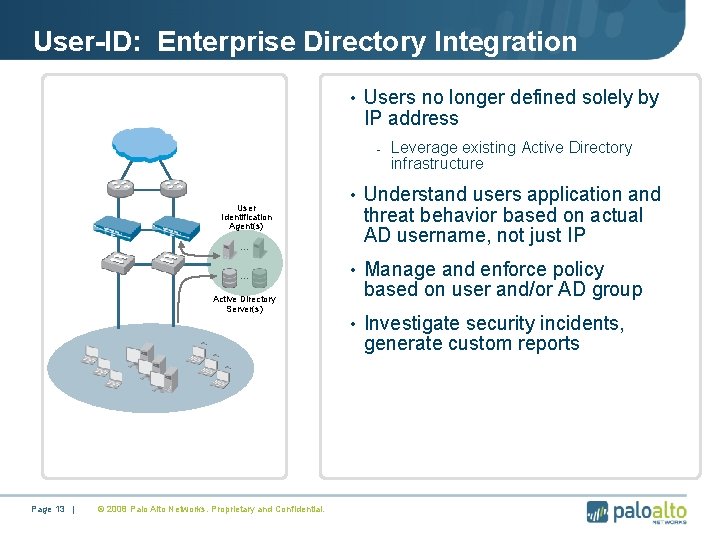
User-ID: Enterprise Directory Integration • Users no longer defined solely by IP address - User Identification Agent(s) … … Active Directory Server(s) Leverage existing Active Directory infrastructure • Understand users application and threat behavior based on actual AD username, not just IP • Manage and enforce policy based on user and/or AD group • Investigate security incidents, generate custom reports Page 13 | © 2008 Palo Alto Networks. Proprietary and Confidential.

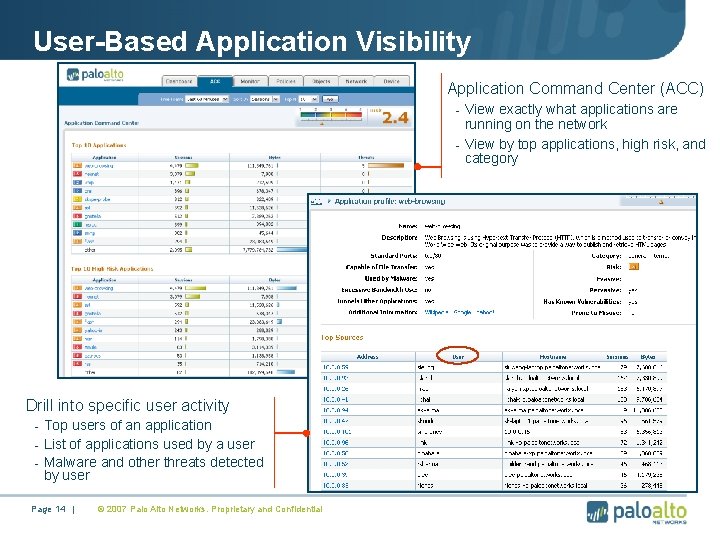
User-Based Application Visibility Application Command Center (ACC) - View exactly what applications are running on the network - View by top applications, high risk, and category Drill into specific user activity - Top users of an application - List of applications used by a user - Malware and other threats detected by user Page 14 | © 2007 Palo Alto Networks. Proprietary and Confidential

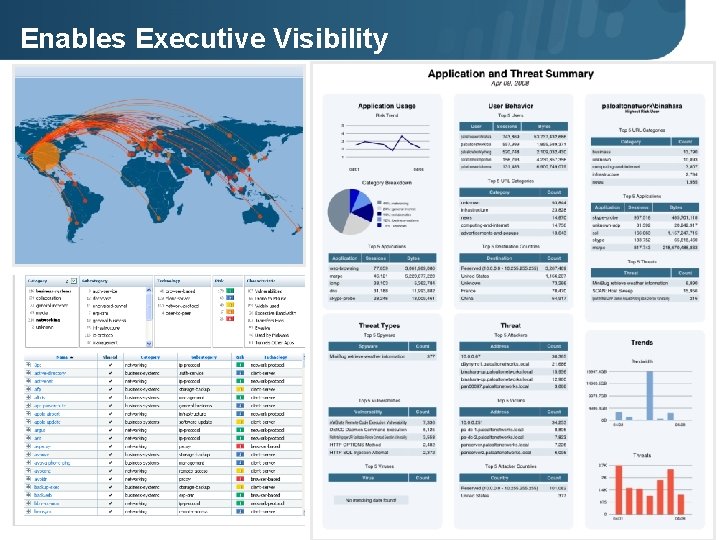
Enables Executive Visibility Page 15 | © 2008 Palo Alto Networks. Proprietary and Confidential.

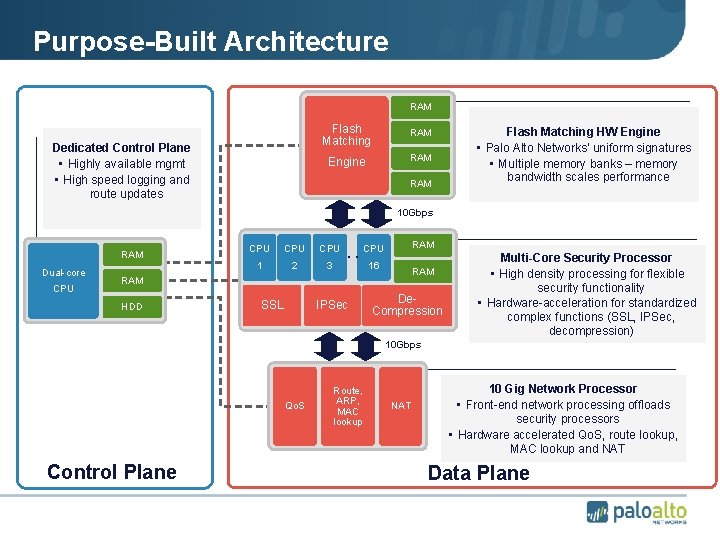
Purpose-Built Architecture RAM Dedicated Control Plane • Highly available mgmt • High speed logging and route updates Flash Matching RAM Engine RAM Flash Matching HW Engine • Palo Alto Networks’ uniform signatures • Multiple memory banks – memory bandwidth scales performance 10 Gbps RAM Dual-core CPU CPU 1 2 3 . . RAM CPU 16 RAM HDD SSL IPSec De. Compression Multi-Core Security Processor • High density processing for flexible security functionality • Hardware-acceleration for standardized complex functions (SSL, IPSec, decompression) 10 Gbps Qo. S Control Plane Route, ARP, MAC lookup NAT 10 Gig Network Processor • Front-end network processing offloads security processors • Hardware accelerated Qo. S, route lookup, MAC lookup and NAT Data Plane

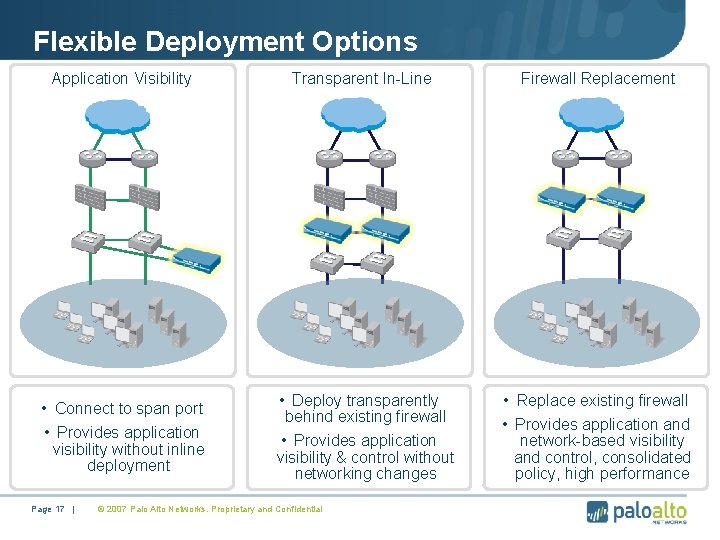
Flexible Deployment Options Application Visibility Transparent In-Line Firewall Replacement • Connect to span port • Provides application visibility without inline deployment • Deploy transparently behind existing firewall • Provides application visibility & control without networking changes • Replace existing firewall • Provides application and network-based visibility and control, consolidated policy, high performance Page 17 | © 2007 Palo Alto Networks. Proprietary and Confidential

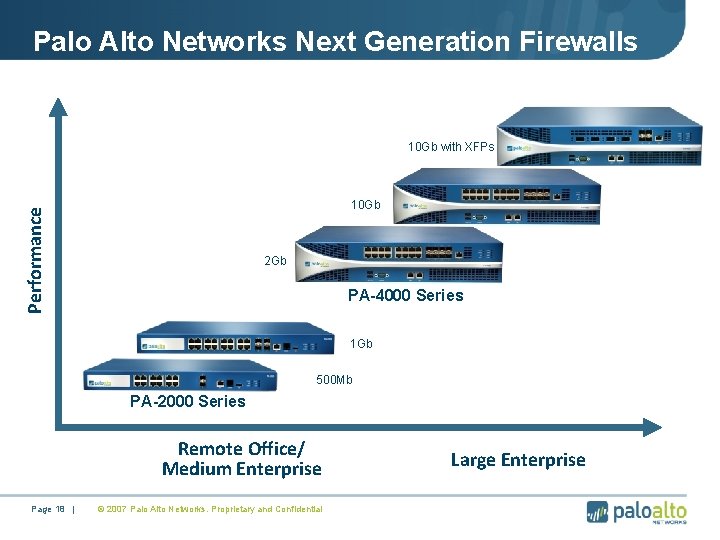
Palo Alto Networks Next Generation Firewalls 10 Gb with XFPs Performance 10 Gb 2 Gb • PA-4000 Series • 1 Gb • 500 Mb • PA-2000 Series Remote Office/ Medium Enterprise Page 18 | © 2007 Palo Alto Networks. Proprietary and Confidential Large Enterprise

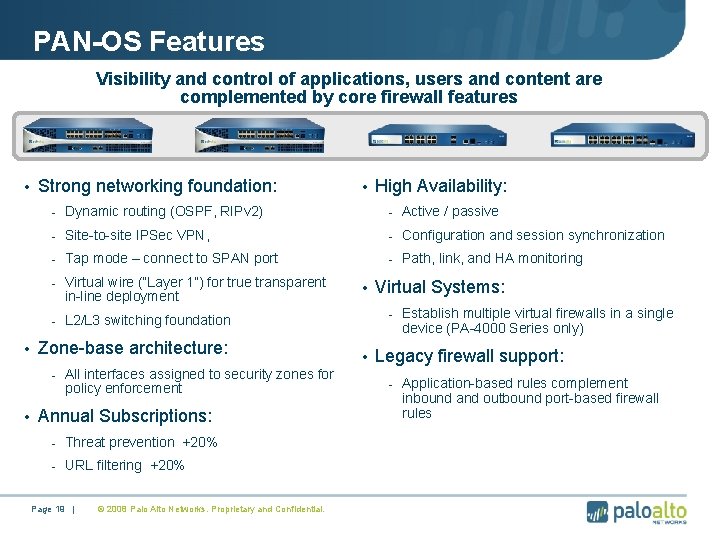
PAN-OS Features Visibility and control of applications, users and content are complemented by core firewall features • Strong networking foundation: • High Availability: - Dynamic routing (OSPF, RIPv 2) - Active / passive - Site-to-site IPSec VPN, - Configuration and session synchronization - Tap mode – connect to SPAN port - Path, link, and HA monitoring - Virtual wire (“Layer 1”) for true transparent in-line deployment - L 2/L 3 switching foundation • Zone-base architecture: - All interfaces assigned to security zones for policy enforcement • Annual Subscriptions: - Threat prevention +20% - URL filtering +20% Page 19 | © 2008 Palo Alto Networks. Proprietary and Confidential. • Virtual Systems: - Establish multiple virtual firewalls in a single device (PA-4000 Series only) • Legacy firewall support: - Application-based rules complement inbound and outbound port-based firewall rules

PA-4000 Series Specifications PA-4060 PA-4050 PA-4020 • • • • • 10 Gbps FW 5 Gbps threat prevention 2, 000 sessions 4 XFP interfaces 4 SFP interfaces $80, 000 10 Gbps FW 5 Gbps threat prevention 2, 000 sessions 16 copper gigabit 8 SFP interfaces $60, 000 2 Gbps FW 2 Gbps threat prevention 500, 000 sessions 16 copper gigabit 8 SFP interfaces $35, 000 - 2 U, 19” rack-mountable chassis - Dual AC power supply, Removable 80 GB hard drive - Dedicated out-of-band management port - 2 dedicated HA ports - DB 9 console port Page 20 | © 2008 Palo Alto Networks. Proprietary and Confidential.

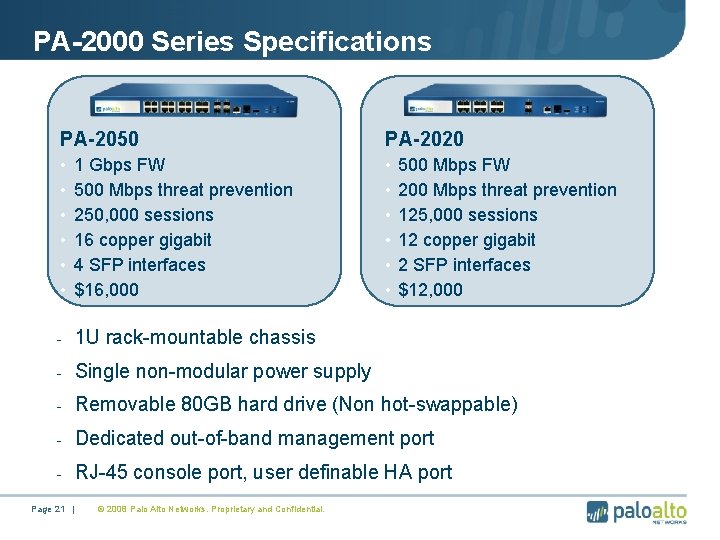
PA-2000 Series Specifications PA-2050 PA-2020 • • • 1 Gbps FW 500 Mbps threat prevention 250, 000 sessions 16 copper gigabit 4 SFP interfaces $16, 000 • • • - 1 U rack-mountable chassis - Single non-modular power supply - Removable 80 GB hard drive (Non hot-swappable) - Dedicated out-of-band management port - RJ-45 console port, user definable HA port Page 21 | © 2008 Palo Alto Networks. Proprietary and Confidential. 500 Mbps FW 200 Mbps threat prevention 125, 000 sessions 12 copper gigabit 2 SFP interfaces $12, 000

Customer Use Case Examples

Palo Alto Networks - Use Cases MANY SOLUTION USE CASES and BENEFITS • Application Visibility & Control • User-based App Visibility & Control “We now know what we didn’t know. And it’s scary what our users and contractors were doing. ” • Real-time Threat Prevention ………. • Monitor & Control Web Surfing Mark Rein Senior Director, Information Technology Mercy Medical Center • Consolidate Security Devices @ Wire • Identify & Control SSL • Content Security & DLP Speed • Firewall Replacement • Significant Human and Capital ROI Page 23 | © 2007 Palo Alto Networks. Proprietary and Confidential

Customer Example: Nordson Corporation Problem • Needed cost-effective remote office security solution • Was looking at a complex 3 -box solution Solution “The PA-4020 has simplified the tasks of managing security at our remote site. And it gives us visibility that no one else can match, telling us exactly which applications are on the network. ” • PA-4000 Series deployed as primary ………. • Complete coverage - firewall, application Tim Harr Manager, Corporate Information Technologies, Nordson firewall for visibility and control over applications and threats • Consolidates multiple devices Results control, threat prevention - one box • Easy remote management - one UI • Deployed in 3 locations internationally including headquarters Industry: Manufacturing Statistics: 30 Countries, 4100 employees, 2007 revenue - US$994 M Page 24 | © 2008 Palo Alto Networks. Proprietary and Confidential.

Customer Example: Greenhill Capital Problem • No visibility into which applications were running on the network • Couldn’t control webmail, attachments and unmonitored email a major issue “The PA-4000 Series enables us to manage applications and users – which are far more relevant to our business that ports and protocols. ” • Tired of adding appliances and vendors to security racks Solution • PA-4000 Series deployed as the firewall for visibility and control over applications ………. John Shaffer Greenhill Results • Complete coverage - firewall, application control, threat prevention - one box • Easy remote management - one UI • Easier vendor management – one support line, one vendor Industry: Financial Services, M&A research and analysis Statistics: 250 employees, 2007 revenue - US$400 M Page 25 | © 2008 Palo Alto Networks. Proprietary and Confidential.

Customer Example: Constellation Energy Problem • Lack of visibility and control over applications traversing the network. • Want to be more proactive to enable more rapid deployment of new businesses and technology “The PA-4000 Series helps us be proactive in our security, allowing us to set and enforce application policies and protect our business assets much more effectively. ” ………. Frank Chambers Director of Information Security Management, Constellation Energy • Heavy traffic across (2) DS 3 pipes was forcing them to look at costly OC 3 expansion Solution • PA-4000 Series provides unmatched visibility and control over applications and web traffic traversing the centralized Internet connections Results • Constellation found significant amounts of Industry: Energy, Energy Trading Statistics: F 117, 9700 employees, 2007 revenue - US$21 B Page 26 | © 2008 Palo Alto Networks. Proprietary and Confidential. IM and P 2 P traffic traversing the network – which it is now able to control

Customer Example: San. Disk Corporation Problem • Unable to manage applications on the network – concerned about various “threats” moving over rogue applications “With Palo Alto Networks, we are now for the first time able to identify rogue applications on the network such as P 2 P and Skype, and then block them accordingly. ” Solution • PA-4000 Series brings increased visibility and control over applications and web traffic Results ………. • Able to see which applications and users Justin Smith Senior Network Engineer San. Disk • Able to take action – created policies to are utilizing the network permit/deny groups or specific applications/users • Provide a level of assurance that networks are being used for business purposes Industry: High-Tech Manufacturing Statistics: 3000 employees, 2007 revenue - US$3. 9 B Page 27 | © 2008 Palo Alto Networks. Proprietary and Confidential.

Customer Example: Sisters of Mercy Health Problem • Couldn’t manage which applications ran on the network • Application-level threats impacting business “Palo Alto Networks enables us to provide real-time access to critical applications while stopping threats and risky applications. ” ………. Dan Schulte Manager of Network Security Sisters of Mercy Health System • IPS up for renewal Solution • PA-4000 Series consolidates firewall, URL filtering and threat prevention • Enables visibility and control over applications, web traffic and threats Results • Visibility and control of applications • Able to stop a broad range of threats (exploits, viruses, spyware) Industry: Health Care Statistics: 9 US States, 28, 000 employees, over 4000 beds Page 28 | © 2008 Palo Alto Networks. Proprietary and Confidential.

Customer Example: Louis Dreyfus Energy Problem • Firewalls couldn’t stop threats Solution • PA-4000 Series enables visibility and “Palo Alto Networks enables us not only to stop threats, but to understand how our networks are being used. ” Results • Visibility and control of applications • Able to stop a broad range of threats (exploits, viruses, spyware) ………. Dave Baker Manager, Systems Administration Louis-Dreyfus Highbridge Energy Industry: Financial Services Statistics: 290 employees, 2007 enterprise value – US$1 B Page 29 | control over applications and threats © 2008 Palo Alto Networks. Proprietary and Confidential. • Very happy with customer responsiveness and support

Customer Example: ESPN Problem • ISS IPS was struggling to handle ESPN’s traffic load Solution • PA-4000 Series deployed primarily as a “We needed an IPS that could keep up with our business, and that could deal with today’s threats. ” threat prevention solution • Enables visibility and control over threats and applications Results • Visibility and control of applications ………. Scott Messina Director of Security ESPN • Able to stop a broader range of threats (exploits, viruses, spyware) than previous IPS • Integrates with Active Directory for user- and group-specific policy • Performance that keeps pace with Industry: Media Statistics: over 50 outlets – television, radio, publishing, ESPN. com Page 30 | © 2008 Palo Alto Networks. Proprietary and Confidential. business

Customer Example: Nicolet National Bank Problem • Couldn’t maintain security posture in the face of evasive application traffic • Couldn’t control data leaving network • Too many appliances “We can now meet bank examiners expectations regarding visibility and control on our network. ” ………. Jon Biskner AVP and Chief Information Security Officer, Nicolet National Bank Industry: Financial Services/Banking Statistics: Regional; 6 branches, over $530 M in assets Page 31 | © 2008 Palo Alto Networks. Proprietary and Confidential. Solution • PA-4000 Series deployed as primary firewall for visibility and control over applications and threats Results • Visibility, control and easier compliance • Reducing and simplifying security infrastructure

Customer Example: City and Schools of Staunton Problem • Existing port-based firewall could not keep up with traffic – slowing the business of the city • Couldn’t manage which applications ran “Our legacy firewall simply couldn’t deliver in terms of performance or visibility. The PA-4000 Series keeps pace easily, and provides a level of visibility and control that translates into real and enforceable acceptable use policies. ” on the network • Application-level threats impacting business Solution • PA-4000 Series consolidates multiple devices - enables visibility and control over applications, threats and web traffic ………. Results Kurt Plowman Chief Technology Officer City of Staunton • High-speed firewall Industry: Government Statistics: over 2000 employees and students Page 32 | © 2008 Palo Alto Networks. Proprietary and Confidential. • Visibility and control of applications • Able to stop a broad range of threats (exploits, viruses, spyware)

Customer Example: Lenox Hill Radiology “After evaluating the PA-4000 Series, its ability to control applications and perform access control, as well as inspect content for threats and vulnerabilities – all through an easy, simple management structure – just blew us away. ” Problem • Application-level threats impacting business • Looking at IPS + AV to stop threats Solution • PA-4000 Series deployed as primary firewall enabling application visibilty and control • Replaces multiple security appliances (firewall, IPS, Proxy, AV) ………. Joe Funaro IT Director Lenox Hill Radiology Results • Visibility and control of applications • Able to stop a broad range of threats (exploits, viruses, spyware) Industry: Health Care Statistics: 3 locations in New York Metro area, 400 employees Page 33 | © 2008 Palo Alto Networks. Proprietary and Confidential. • Firewall + application visibility + threat blocking in one policy, one appliance

Customer Example: Western & Southern Insurance Problem • Couldn’t tell what was on the network, despite firewall, IPS, DLP. Couldn’t catch L 7 threats “We had every security device imaginable, all inline, but couldn’t stop layer 7 threats. ” ………. Solution • PA-4000 Series enables visibility and control over applications Results • Visibility into what’s on network Doug Ross Chief Technology Officer Western & Southern Financial Group • Enable positive use of applications while controlling port-agile apps, ID malicious code on desktops that nothing else could find • Long term, consolidate FW, URL Industry: Financial Services Statistics: $4. 8 B, Ranked 480 on Fortune 1000 list, privately held Page 34 | © 2008 Palo Alto Networks. Proprietary and Confidential. filtering, IPS devices as they near end-of-life

Customer Example: Sonic Solutions Problem • Had no control over port 80 traffic, no ability to understand which users were doing what “Our existing security solution is blind to traffic flowing across port 80. Palo Alto Networks provides us with user-based application visibility and control” • PA-4000 Series for application visibility and control Results • Visibility and control over applications ………. and users traversing the network Roger Blakely VP of Information Security Sonic Solutions Industry: High tech, software development Statistics: 600 employees, multiple sites worldwide Page 35 | Solution © 2008 Palo Alto Networks. Proprietary and Confidential. • Long term will enable replacement of Cisco PIX and Fortinet firewalls

Customer Example: Garland ISD Problem • Students circumventing IT security controls with tools such as Utra. Surf and TOR - No visibility into user behavior, application use “Not only did the PA-4000 Series give us total control over all applications, we saw a significant performance increase in our network performance. ” • Existing firewalls not keeping up ………. Results Neil Moss Network Engineer Garland ISD - Rate of change in applications - Sheer throughput Solution • PA-4000 Series deployed as primary enterprise firewall • Policy control by application and user - No longer struggle to keep up with new/changed applications Industry: K-12 Education Statistics: Largest district in TX, 57, 000 students, 12, 000 employees, 74 sites Page 36 | © 2008 Palo Alto Networks. Proprietary and Confidential. • Improved performance • Saved $80 K in year one

Palo Alto Networks - Competitive Advantages • Application Level Visibility & Control (700+ Signatures) • User-based & Group-based Visibility & Policy Control via Microsoft AD Integration • Tightly integrated and Comprehensive Threat Prevention (URL filtering, Anti. Virus, Anti-Spyware, Anti-Malware & Anti-Vulnerability Protection) • Aggressive Platform-based Subscription Pricing (vs. Costly User-based!) • Embedded Virtual System Support (VSYS) • Embedded Zone Protection (Denial of Service, Reconnaissance Port Scan) • User-based Activity Reports and Ad-Hoc and Scheduled Reports • Single Management Interface for all features on a single appliance • Built-in Hardware/Software SSL Decryption capabilities • 100% security protection during failover to the standby system • Sensitive Data Protection - SSN & Credit Card numbers (Q 4, 2008) • Traffic Tagging Capability Now – Full Traffic Shaping Coming (1 H, 2009) Page 37 | © 2007 Palo Alto Networks. Proprietary and Confidential

Thank You!