SYSTEM SECURITY NETWORK Firewall Install a firewall Determine







- Slides: 55

SYSTEM SECURITY NETWORK (Firewall) Install a firewall Determine the type of network security Identify the control network is needed Design a network security system HOME

COMPETENCE MAPING Dasar Kejuruan 1 Level I ( Kelas X ) 2 Level II ( Kelas XI ) 3 Level III ( Kelas XII ) Merakit Personal Komputer Menerapkan teknik elektronika analog dan digital dasar Melakukan instalasi perangkat jaringan lokal (Local Area Network) Melakukan instalasi perangkat jaringan berbasis luas (Wide Area Network) Melakukan instalasi sistem operasi dasar Menerapkan fungsi peripheral dan instalasi PC Mendiagnosis permasalahan pengoperasian PC yang tersambung jaringangnosis Mendiagnosis permasalahan perangkat yang tersambung jaringan berbasis luas (Wide Area Network) Menerapkan K 3 LH Mendiagnosis permasalahan pengoperasian PC dan periferal Melakukan perbaikan dan/ atau setting ulang koneksi jaringan an Melakukan perbaikan dan/ atau setting ulang sistem PC Melakukan instalasi sistem operasi jaringan berbasis GUI (Graphical User Interface) dan Text Melakukan perbaikan periferal Melakukan perawatan PC Melakukan instalasi sistem operasi berbasis graphical user interface (GUI) dan command line interface (CLI) Klik Dis in i Melakukan perbaikan dan/ atau setting ulang koneksi jaringan berbasis luas (Wan) Melakukan perbaikan dan/ atau setting ulang koneksi jaringan berbasis luas (Wide Area Network) Mengadministrasi server dalam jaringan Merancang bangun dan menganalisa Wide Area Network Merancang web data base untuk content server Melakukan instalasi software Lulus HOME

Destination: The discussion aims to: 1. Students understand the types of firewall 2. Students understand how to implement a firewall on the network Main discussion: In this discussion include: 1. Type the type of network security, firewall, network Control. 2. How to Design a network security system. HOME Module 15 System Security Network (Firewall)

Determine The Type of Network Security In computer networks, especially related to applications that involve a variety of interests, many things happen that can disrupt the stability in computer network connection, whether related to hardware (physical security, electrical power source) and related software (systems, configuration, system access, etc. ). Module 15 System Security Network (Firewall)

Interference in the system can occur due to factors inadvertence committed by the manager (human error), but not a few of them are caused by third parties. Interference can be a destruction, infiltration, theft of access rights, data or abuse the system, until the criminal action through the computer network applications. Module 15 System Security Network (Firewall)

Internetworking in some type of interference is known by the term: 1. Hacking, in the form of network infrastructure that already exists, for example, of the system from a server. 2. Physing, a forgery of official data to be related pemanfaataanya. 3. Deface, changes to the look of a website is illegal. 4. Carding, identity theft of banking data to someone, such as stealing credit card numbers, used to take advantage of the balance of the account for online shopping. 5. And many terms in the network security system relating to the abuse and destruction of existing systems. Module 15 System Security Network (Firewall)

In the preparation of the security system should be prepared in the form below: 1. Regroup terminal is enabled as a network control center or access point (server) on a network, which should be given special security. 2. Provide a physical space for the special security device called the point number 1. Room can be given a label Network Operating Center (NOC) by limiting the personnel allowed to enter. 3. Separate power source for the NOC from the other. Please also enabled Uninteruptable Power Supply (UPS) and the stabilizer for maintaining the stability of the power supply device is required on the NOC. 4. Tidy rooms and wiring label and classification cable. 5. Giving a Soft Security System Firewall is enabled on the device in the network. 6. Maintenance plan and prepare the Back Up system. Module 15 System Security Network (Firewall)

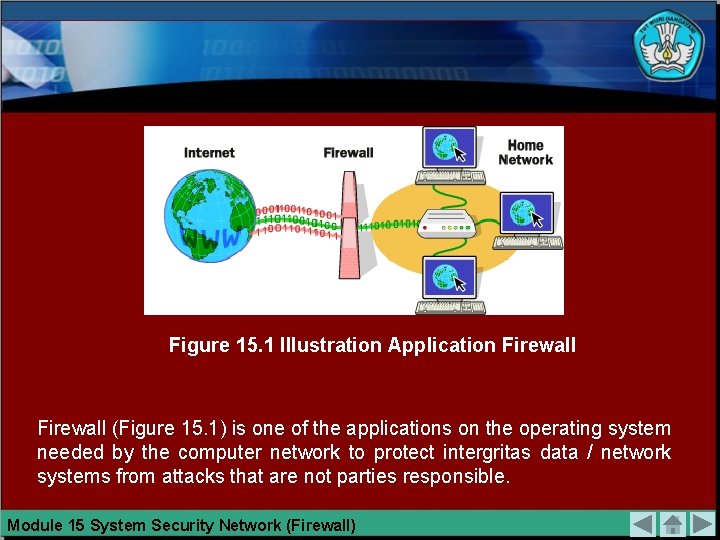
Figure 15. 1 Illustration Application Firewall (Figure 15. 1) is one of the applications on the operating system needed by the computer network to protect intergritas data / network systems from attacks that are not parties responsible. Module 15 System Security Network (Firewall)

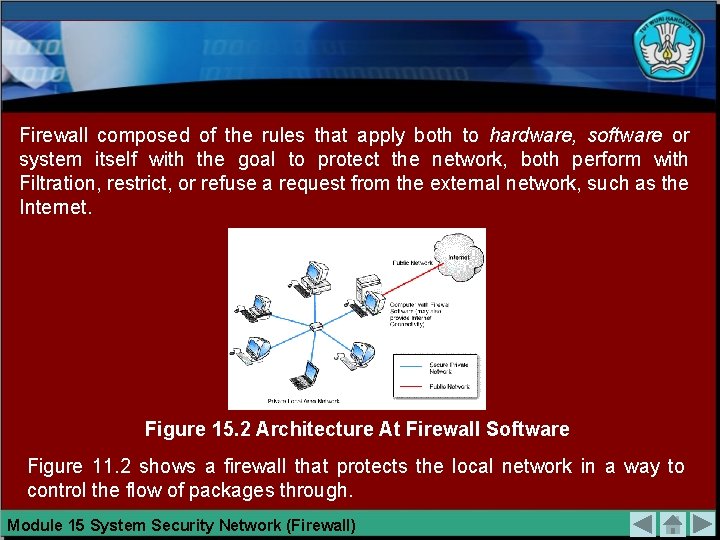
Firewall composed of the rules that apply both to hardware, software or system itself with the goal to protect the network, both perform with Filtration, restrict, or refuse a request from the external network, such as the Internet. Figure 15. 2 Architecture At Firewall Software Figure 11. 2 shows a firewall that protects the local network in a way to control the flow of packages through. Module 15 System Security Network (Firewall)

Occurred on the firewall that allow multiple processes to protect the network. There are three kinds of process that occurred in the firewall, is: 1. Packet header modification, modification is used to modify the quality of service bits before the TCP packet routing process. 2. Translation of a translation can occur one to one (one to one), that is a private IP address mapped to one or public IP address translation many to one (many to one) that some private IP address mapped to one address public, and 3. A packet filter, filter is used for determination whether the package can be forwarded or not. Module 15 System Security Network (Firewall)

Install a Firewall HOME

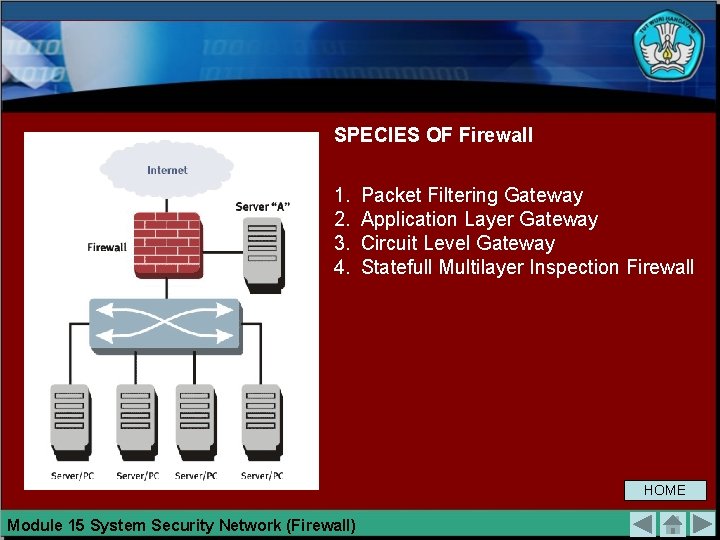
SPECIES OF Firewall 1. 2. 3. 4. Packet Filtering Gateway Application Layer Gateway Circuit Level Gateway Statefull Multilayer Inspection Firewall HOME Module 15 System Security Network (Firewall)

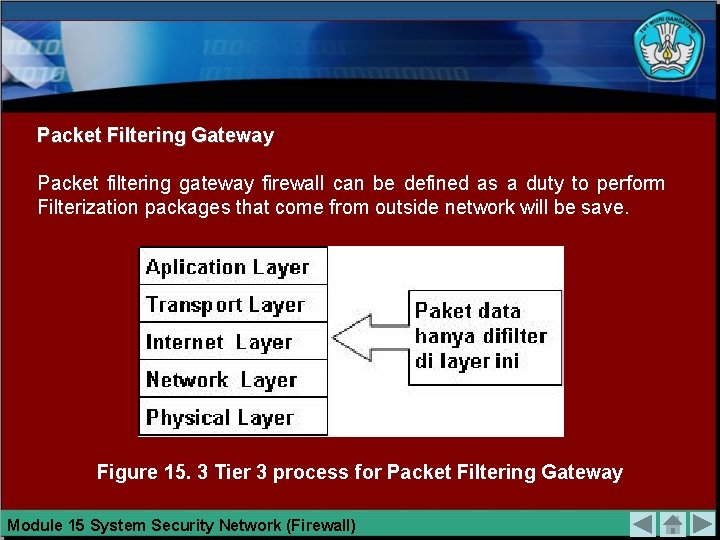
Packet Filtering Gateway Packet filtering gateway firewall can be defined as a duty to perform Filterization packages that come from outside network will be save. Figure 15. 3 Tier 3 process for Packet Filtering Gateway Module 15 System Security Network (Firewall)

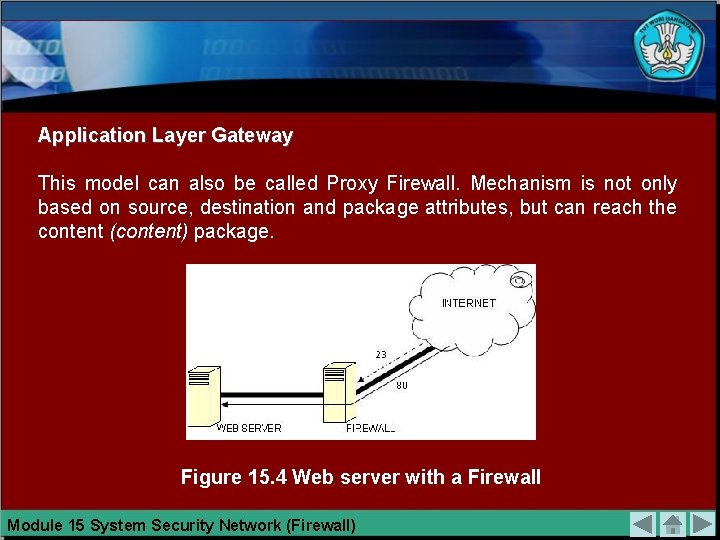
Application Layer Gateway This model can also be called Proxy Firewall. Mechanism is not only based on source, destination and package attributes, but can reach the content (content) package. Figure 15. 4 Web server with a Firewall Module 15 System Security Network (Firewall)

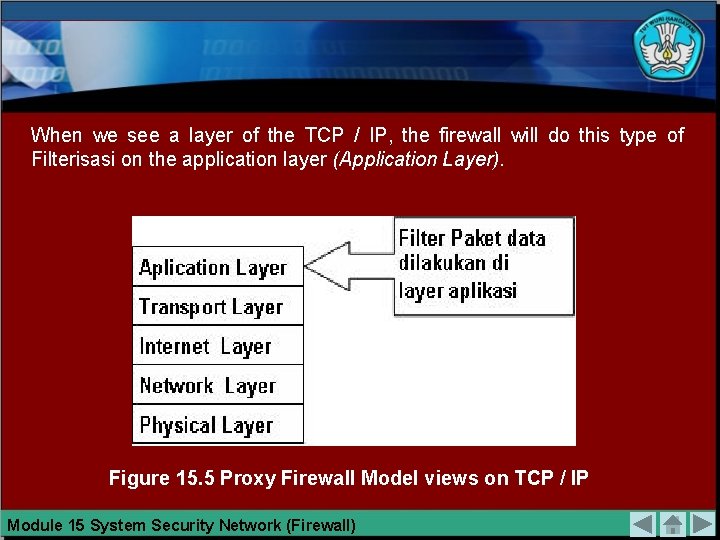
When we see a layer of the TCP / IP, the firewall will do this type of Filterisasi on the application layer (Application Layer). Figure 15. 5 Proxy Firewall Model views on TCP / IP Module 15 System Security Network (Firewall)

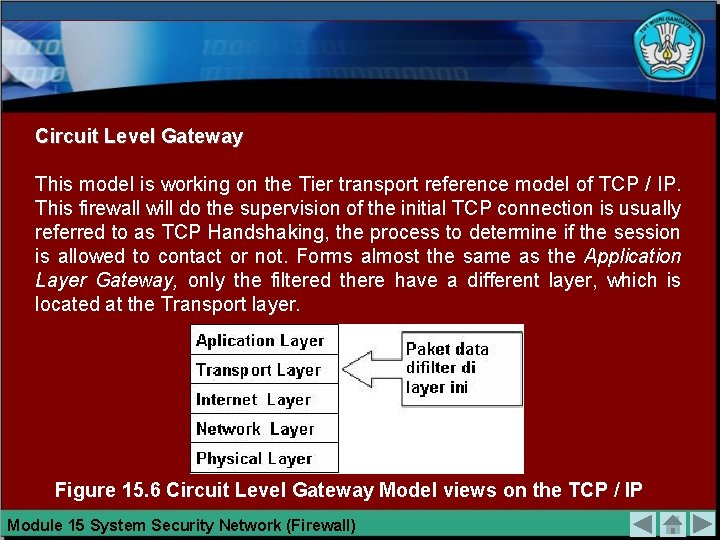
Circuit Level Gateway This model is working on the Tier transport reference model of TCP / IP. This firewall will do the supervision of the initial TCP connection is usually referred to as TCP Handshaking, the process to determine if the session is allowed to contact or not. Forms almost the same as the Application Layer Gateway, only the filtered there have a different layer, which is located at the Transport layer. Figure 15. 6 Circuit Level Gateway Model views on the TCP / IP Module 15 System Security Network (Firewall)

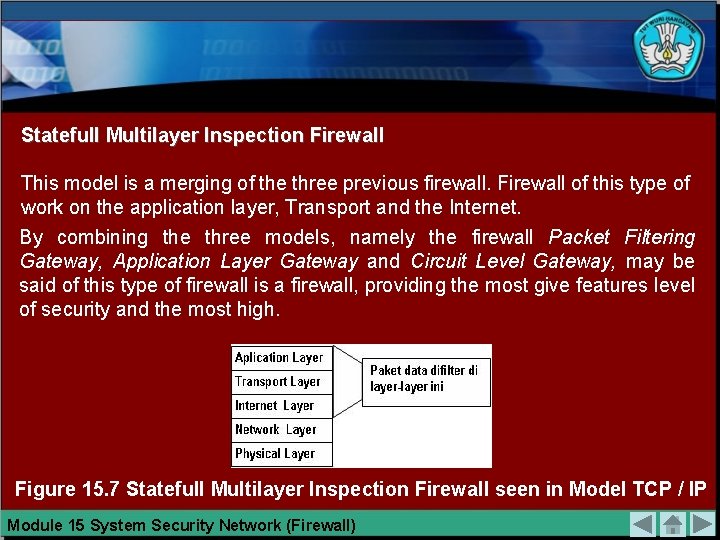
Statefull Multilayer Inspection Firewall This model is a merging of the three previous firewall. Firewall of this type of work on the application layer, Transport and the Internet. By combining the three models, namely the firewall Packet Filtering Gateway, Application Layer Gateway and Circuit Level Gateway, may be said of this type of firewall is a firewall, providing the most give features level of security and the most high. Figure 15. 7 Statefull Multilayer Inspection Firewall seen in Model TCP / IP Module 15 System Security Network (Firewall)

Identify The Control Network is Needed HOME

The application control network using the firewall can be implemented with a number of implementing rules (chains) on the existing topology. In the case of a network using iptables, there are two things that must be considered, namely: 1. Connection package that implements a firewall that is used. 2. The concept of a firewall is implemented. With these two things are expected as the iptables rules that defines the firewall can identify whether a connection that happens a new connection (NEW), which has no connection (Establish), connections that have relationships with other connections (RELATED), or the connection is not valid (invalid). The four types of connections that make IPTables called Statefull Protocol. HOME Module 15 System Security Network (Firewall)

Connection Package Connection packet in the process of sending from the sender to the recipient must go through the firewall rules, can be grouped connection to the three groups, namely: 1. TCP connections 2. IP Connection 3. UDP connections Module 15 System Security Network (Firewall)

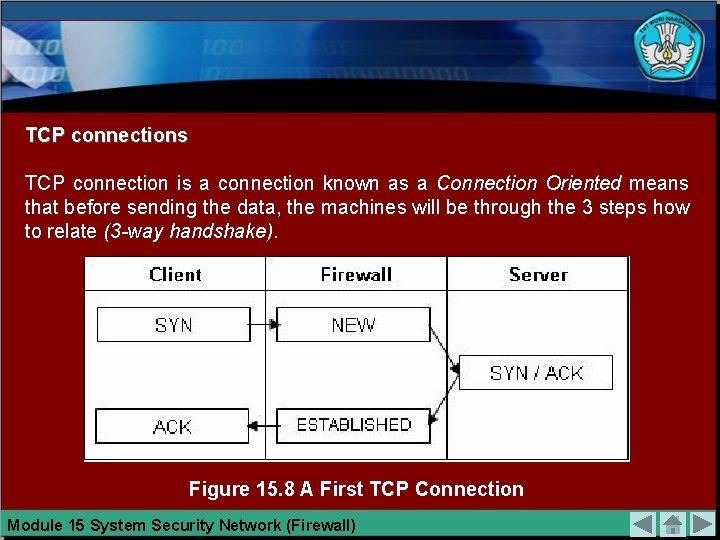
TCP connections TCP connection is a connection known as a Connection Oriented means that before sending the data, the machines will be through the 3 steps how to relate (3 -way handshake). Figure 15. 8 A First TCP Connection Module 15 System Security Network (Firewall)

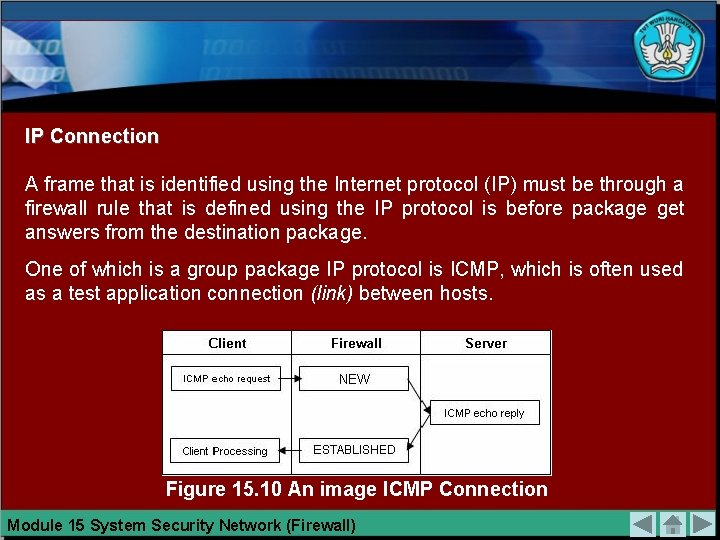
IP Connection A frame that is identified using the Internet protocol (IP) must be through a firewall rule that is defined using the IP protocol is before package get answers from the destination package. One of which is a group package IP protocol is ICMP, which is often used as a test application connection (link) between hosts. Figure 15. 10 An image ICMP Connection Module 15 System Security Network (Firewall)

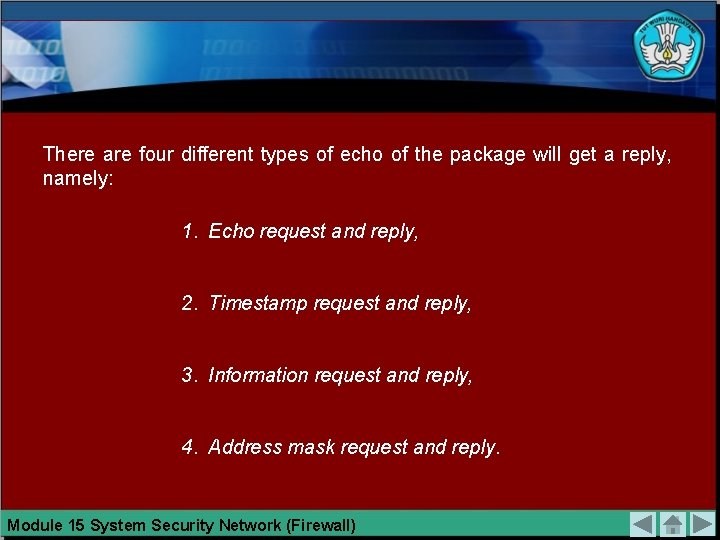
There are four different types of echo of the package will get a reply, namely: 1. Echo request and reply, 2. Timestamp request and reply, 3. Information request and reply, 4. Address mask request and reply. Module 15 System Security Network (Firewall)

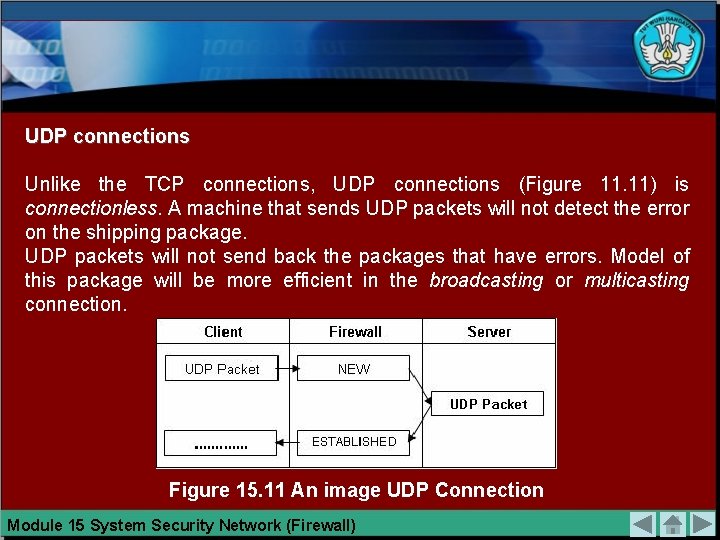
UDP connections Unlike the TCP connections, UDP connections (Figure 11. 11) is connectionless. A machine that sends UDP packets will not detect the error on the shipping package. UDP packets will not send back the packages that have errors. Model of this package will be more efficient in the broadcasting or multicasting connection. Figure 15. 11 An image UDP Connection Module 15 System Security Network (Firewall)

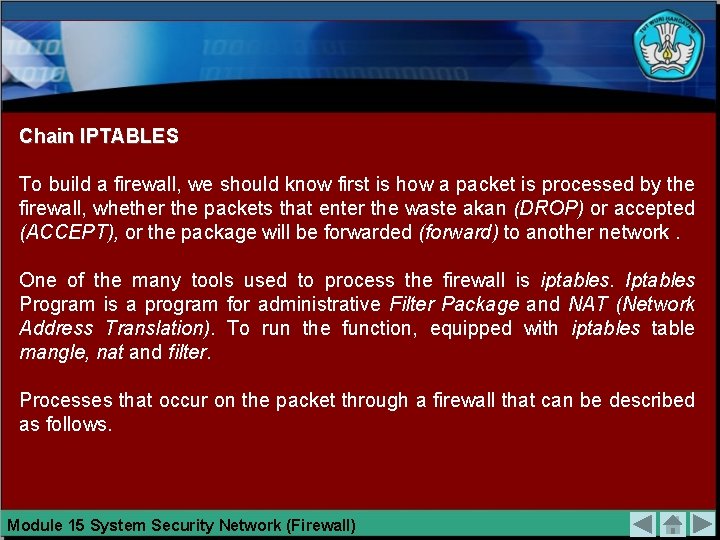
Chain IPTABLES To build a firewall, we should know first is how a packet is processed by the firewall, whether the packets that enter the waste akan (DROP) or accepted (ACCEPT), or the package will be forwarded (forward) to another network. One of the many tools used to process the firewall is iptables. Iptables Program is a program for administrative Filter Package and NAT (Network Address Translation). To run the function, equipped with iptables table mangle, nat and filter. Processes that occur on the packet through a firewall that can be described as follows. Module 15 System Security Network (Firewall)

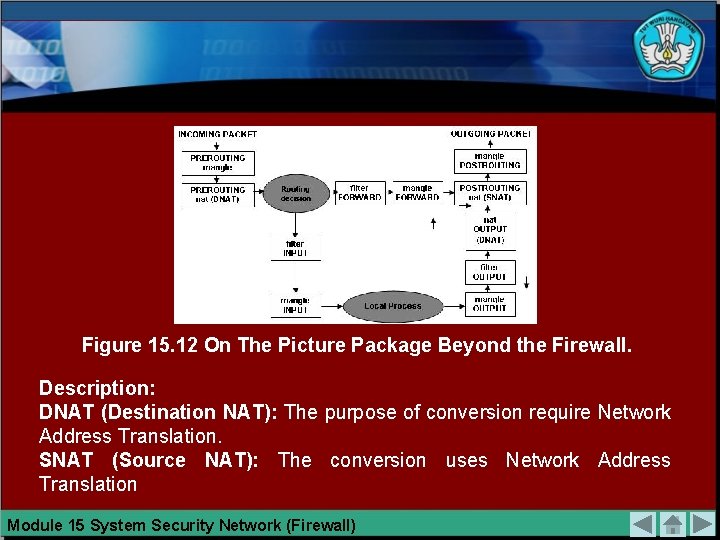
Figure 15. 12 On The Picture Package Beyond the Firewall. Description: DNAT (Destination NAT): The purpose of conversion require Network Address Translation. SNAT (Source NAT): The conversion uses Network Address Translation Module 15 System Security Network (Firewall)

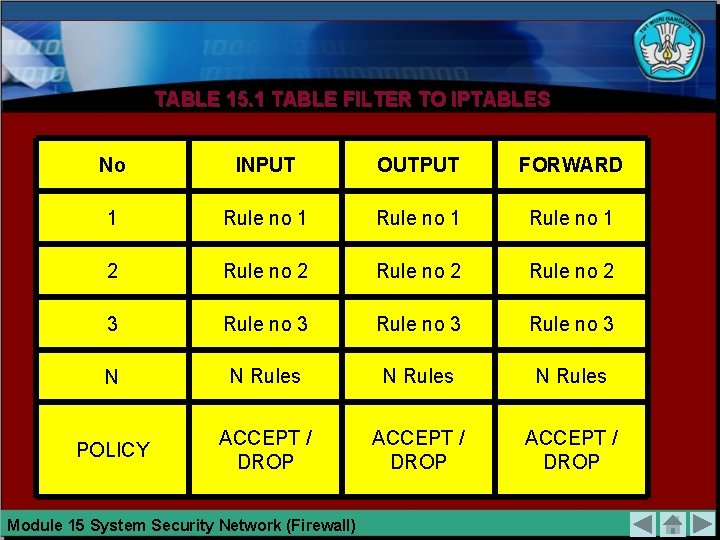
TABLE 15. 1 TABLE FILTER TO IPTABLES No INPUT OUTPUT FORWARD 1 Rule no 1 2 Rule no 2 3 Rule no 3 N N Rules POLICY ACCEPT / DROP Module 15 System Security Network (Firewall)

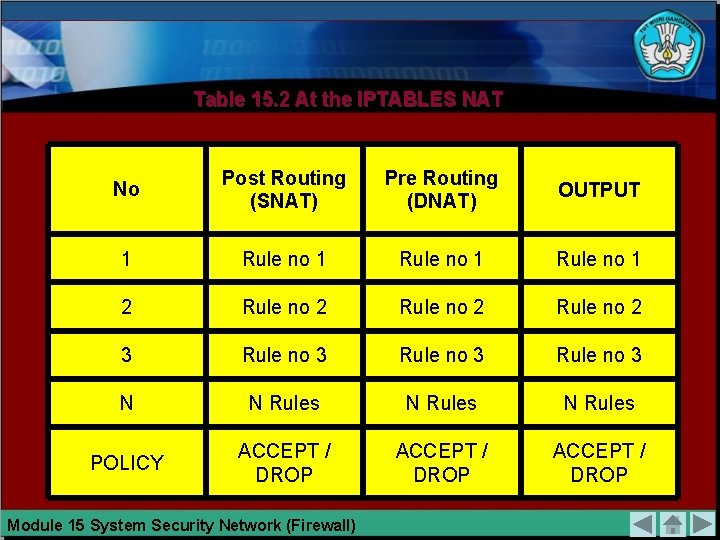
Table 15. 2 At the IPTABLES NAT No Post Routing (SNAT) Pre Routing (DNAT) OUTPUT 1 Rule no 1 2 Rule no 2 3 Rule no 3 N N Rules POLICY ACCEPT / DROP Module 15 System Security Network (Firewall)

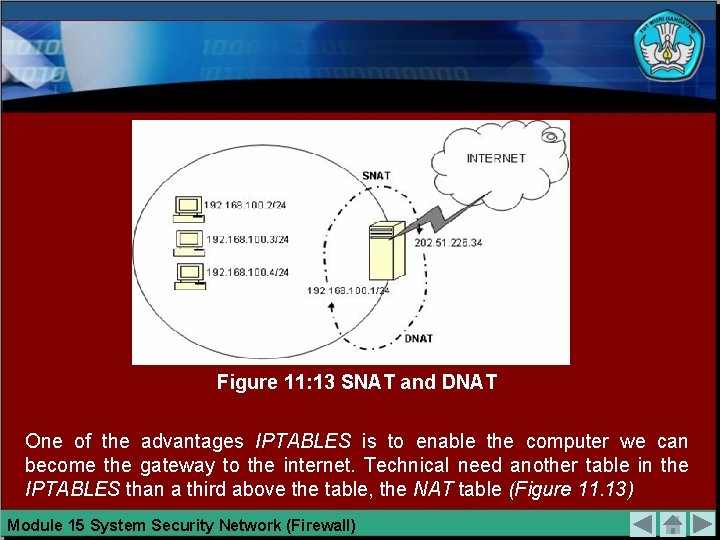
Figure 11: 13 SNAT and DNAT One of the advantages IPTABLES is to enable the computer we can become the gateway to the internet. Technical need another table in the IPTABLES than a third above the table, the NAT table (Figure 11. 13) Module 15 System Security Network (Firewall)

SNAT is used to change the IP address of the sender (source IP address). SNAT usually useful to make the computer as a gateway to the internet. For example, we use the computer IP address 192. 168. 0. 1. IP is the local IP. SNAT will change the local IP is a public IP, such as 202. 51. 226. 35. As well as vice versa, if the local computer can access the internet from the DNAT to be used. Mangle on IPTABLES used to mark (marking) packages for use in the processes further. Mangle most in use for limiting the bandwidth, or bandwidth. Module 15 System Security Network (Firewall)

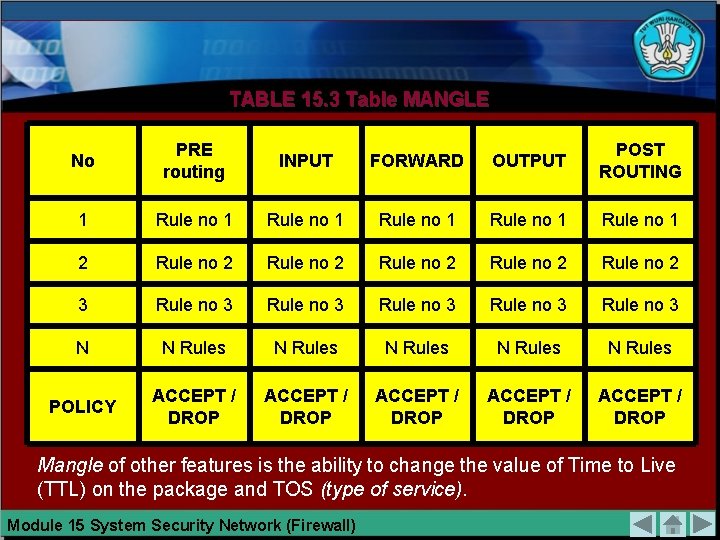
TABLE 15. 3 Table MANGLE No PRE routing INPUT FORWARD OUTPUT POST ROUTING 1 Rule no 1 Rule no 1 2 Rule no 2 Rule no 2 3 Rule no 3 Rule no 3 N N Rules N Rules POLICY ACCEPT / DROP ACCEPT / DROP Mangle of other features is the ability to change the value of Time to Live (TTL) on the package and TOS (type of service). Module 15 System Security Network (Firewall)

Design a Network Security System HOME

Here are the steps required to build a firewall: 1. Determine the network topology that will be used. 2. Determine policy or policy. 3. Determine the application - the application or service, what services will run. 4. Users determine which will be worn by one or more firewall rules. 5. Implement the policies, rules, and procedures in the implementation of the firewall. 6. Socialization policies, rules, and procedures that have been applied. HOME Module 15 System Security Network (Firewall)

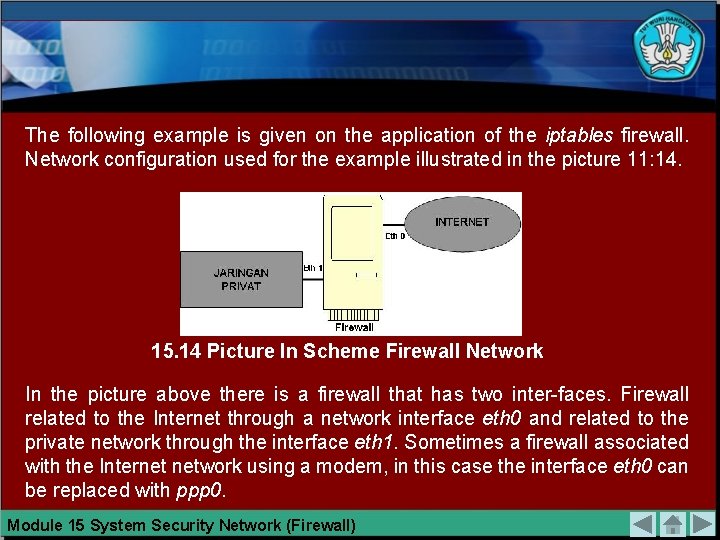
The following example is given on the application of the iptables firewall. Network configuration used for the example illustrated in the picture 11: 14. 15. 14 Picture In Scheme Firewall Network In the picture above there is a firewall that has two inter-faces. Firewall related to the Internet through a network interface eth 0 and related to the private network through the interface eth 1. Sometimes a firewall associated with the Internet network using a modem, in this case the interface eth 0 can be replaced with ppp 0. Module 15 System Security Network (Firewall)

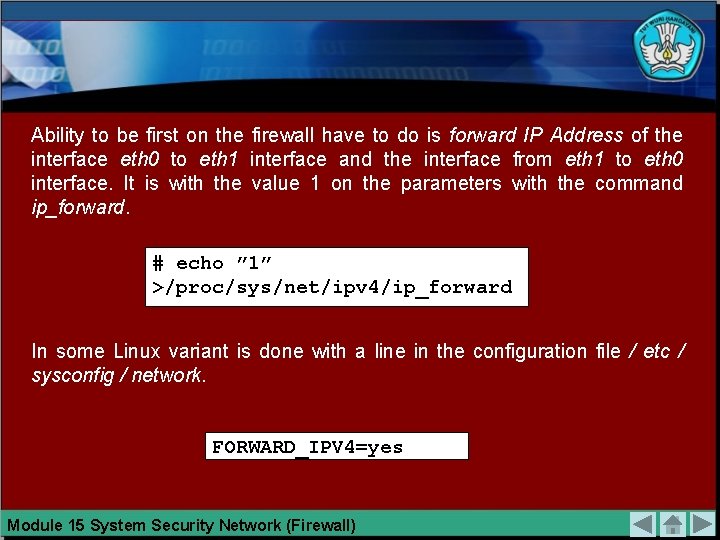
Ability to be first on the firewall have to do is forward IP Address of the interface eth 0 to eth 1 interface and the interface from eth 1 to eth 0 interface. It is with the value 1 on the parameters with the command ip_forward. # echo ” 1” >/proc/sys/net/ipv 4/ip_forward In some Linux variant is done with a line in the configuration file / etc / sysconfig / network. FORWARD_IPV 4=yes Module 15 System Security Network (Firewall)

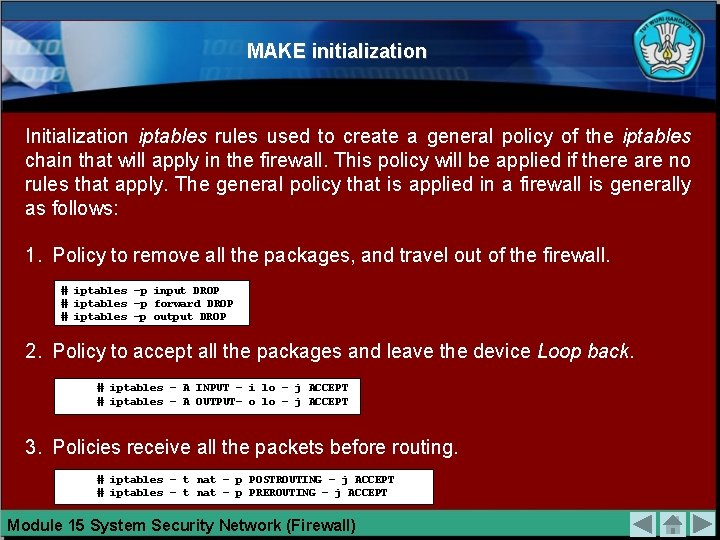
MAKE initialization Initialization iptables rules used to create a general policy of the iptables chain that will apply in the firewall. This policy will be applied if there are no rules that apply. The general policy that is applied in a firewall is generally as follows: 1. Policy to remove all the packages, and travel out of the firewall. # iptables –p input DROP # iptables –p forward DROP # iptables –p output DROP 2. Policy to accept all the packages and leave the device Loop back. # iptables – A INPUT – i lo – j ACCEPT # iptables – A OUTPUT– o lo – j ACCEPT 3. Policies receive all the packets before routing. # iptables – t nat – p POSTROUTING – j ACCEPT # iptables – t nat – p PREROUTING – j ACCEPT Module 15 System Security Network (Firewall)

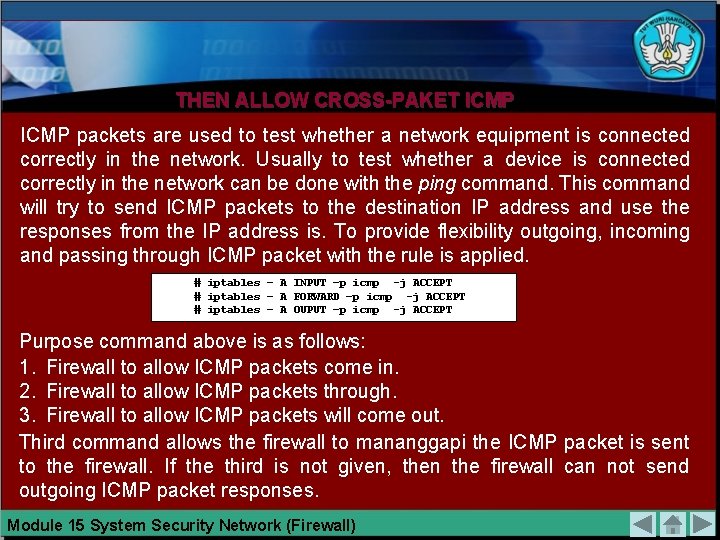
THEN ALLOW CROSS-PAKET ICMP packets are used to test whether a network equipment is connected correctly in the network. Usually to test whether a device is connected correctly in the network can be done with the ping command. This command will try to send ICMP packets to the destination IP address and use the responses from the IP address is. To provide flexibility outgoing, incoming and passing through ICMP packet with the rule is applied. # iptables – A INPUT –p icmp -j ACCEPT # iptables – A FORWARD –p icmp -j ACCEPT # iptables – A OUPUT –p icmp -j ACCEPT Purpose command above is as follows: 1. Firewall to allow ICMP packets come in. 2. Firewall to allow ICMP packets through. 3. Firewall to allow ICMP packets will come out. Third command allows the firewall to mananggapi the ICMP packet is sent to the firewall. If the third is not given, then the firewall can not send outgoing ICMP packet responses. Module 15 System Security Network (Firewall)

Note: Sometimes the ICMP packet is used for purposes that are not true, so that sometimes the firewall is closed to traffic package. If a firewall is not permitted to receive the ICMP packet traffic, the above command does not need to be included. Module 15 System Security Network (Firewall)

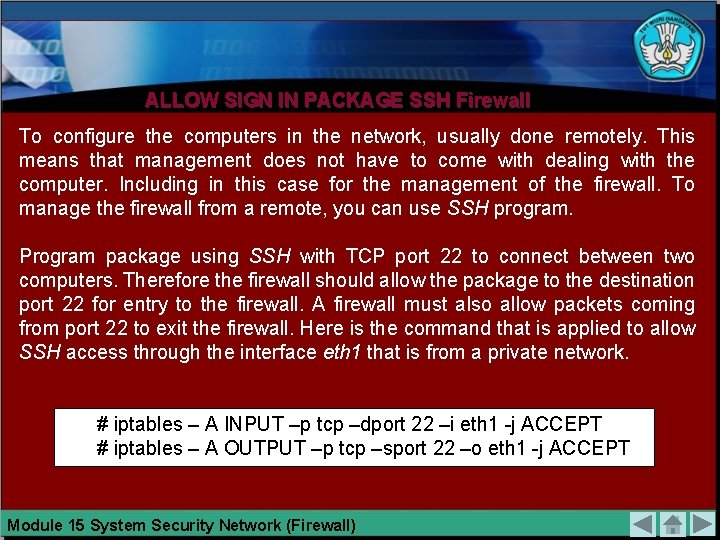
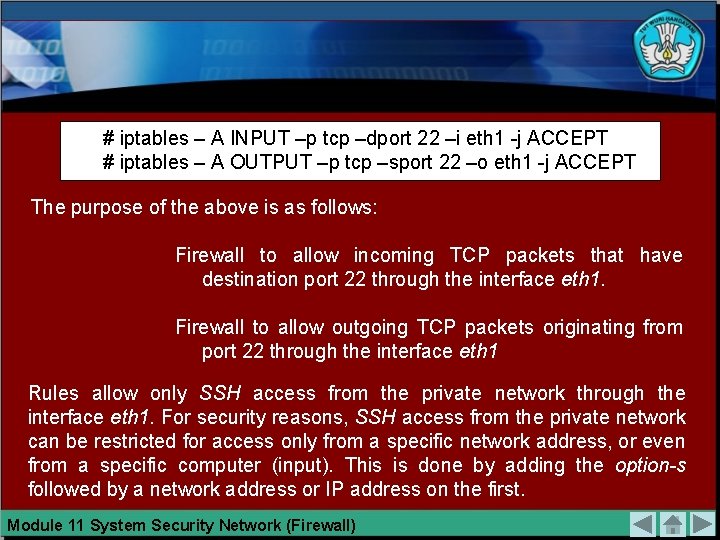
ALLOW SIGN IN PACKAGE SSH Firewall To configure the computers in the network, usually done remotely. This means that management does not have to come with dealing with the computer. Including in this case for the management of the firewall. To manage the firewall from a remote, you can use SSH program. Program package using SSH with TCP port 22 to connect between two computers. Therefore the firewall should allow the package to the destination port 22 for entry to the firewall. A firewall must also allow packets coming from port 22 to exit the firewall. Here is the command that is applied to allow SSH access through the interface eth 1 that is from a private network. # iptables – A INPUT –p tcp –dport 22 –i eth 1 -j ACCEPT # iptables – A OUTPUT –p tcp –sport 22 –o eth 1 -j ACCEPT Module 15 System Security Network (Firewall)

# iptables – A INPUT –p tcp –dport 22 –i eth 1 -j ACCEPT # iptables – A OUTPUT –p tcp –sport 22 –o eth 1 -j ACCEPT The purpose of the above is as follows: Firewall to allow incoming TCP packets that have destination port 22 through the interface eth 1. Firewall to allow outgoing TCP packets originating from port 22 through the interface eth 1 Rules allow only SSH access from the private network through the interface eth 1. For security reasons, SSH access from the private network can be restricted for access only from a specific network address, or even from a specific computer (input). This is done by adding the option-s followed by a network address or IP address on the first. Module 11 System Security Network (Firewall)

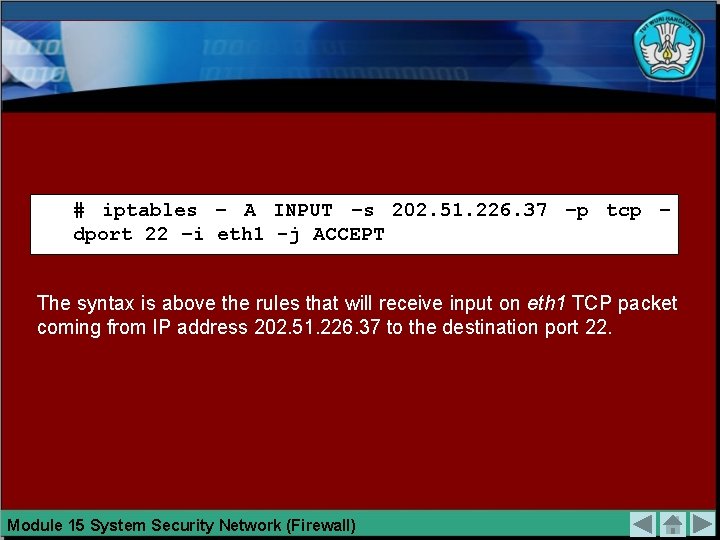
# iptables – A INPUT –s 202. 51. 226. 37 –p tcp – dport 22 –i eth 1 -j ACCEPT The syntax is above the rules that will receive input on eth 1 TCP packet coming from IP address 202. 51. 226. 37 to the destination port 22. Module 15 System Security Network (Firewall)

ALLOW ACCESS HTTP through Firewall Http protocol access is the most widely used for surfing the internet. The information presented on the Internet generally use this http access. Access using http port 80 with the type of TCP packet. Firewalls usually allow http access through the firewall, especially a good exit or enter the private network. Http access to the private network out to use for http provide access for computers that are in the private network. While the http access from the internet on the network occurs when there is a private web server accessible from the Internet network. Module 15 System Security Network (Firewall)

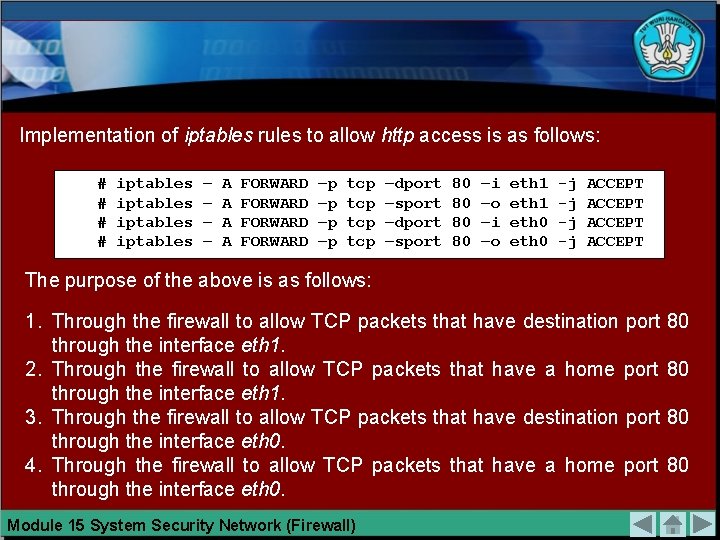
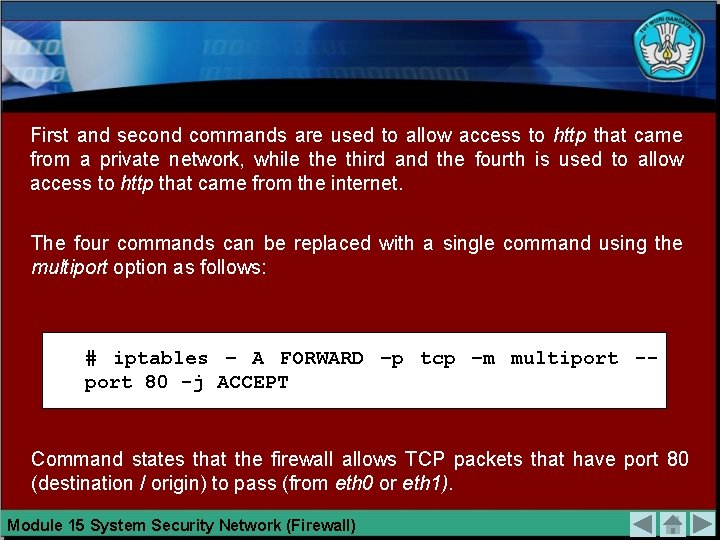
Implementation of iptables rules to allow http access is as follows: # # iptables – – A A FORWARD –p –p tcp tcp –dport –sport 80 80 –i –o eth 1 eth 0 -j -j ACCEPT The purpose of the above is as follows: 1. Through the firewall to allow TCP packets that have destination port through the interface eth 1. 2. Through the firewall to allow TCP packets that have a home port through the interface eth 1. 3. Through the firewall to allow TCP packets that have destination port through the interface eth 0. 4. Through the firewall to allow TCP packets that have a home port through the interface eth 0. Module 15 System Security Network (Firewall) 80 80

First and second commands are used to allow access to http that came from a private network, while third and the fourth is used to allow access to http that came from the internet. The four commands can be replaced with a single command using the multiport option as follows: # iptables – A FORWARD –p tcp –m multiport -port 80 -j ACCEPT Command states that the firewall allows TCP packets that have port 80 (destination / origin) to pass (from eth 0 or eth 1). Module 15 System Security Network (Firewall)

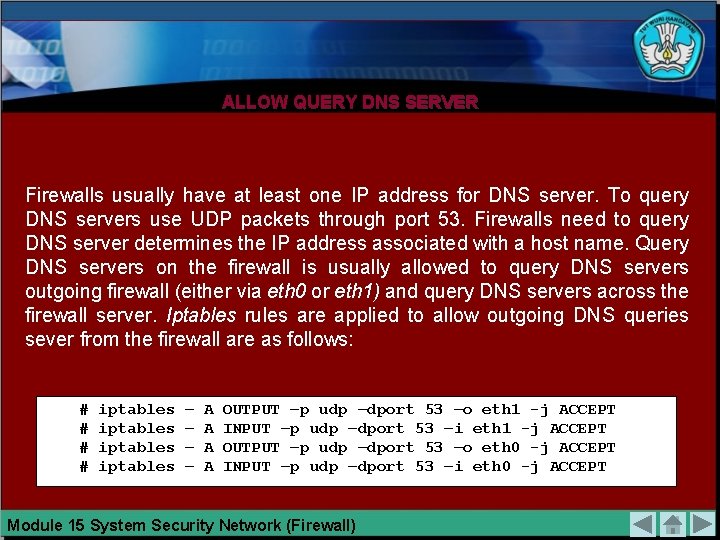
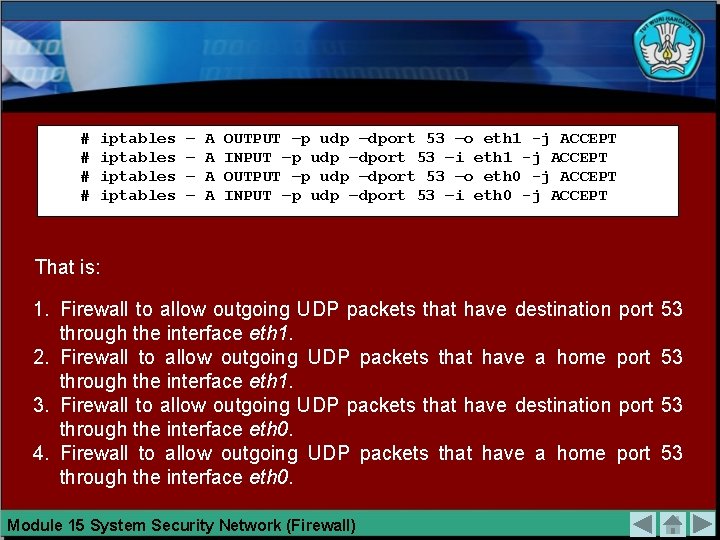
ALLOW QUERY DNS SERVER Firewalls usually have at least one IP address for DNS server. To query DNS servers use UDP packets through port 53. Firewalls need to query DNS server determines the IP address associated with a host name. Query DNS servers on the firewall is usually allowed to query DNS servers outgoing firewall (either via eth 0 or eth 1) and query DNS servers across the firewall server. Iptables rules are applied to allow outgoing DNS queries sever from the firewall are as follows: # # iptables – – A A OUTPUT –p udp –dport 53 –o eth 1 -j ACCEPT INPUT –p udp –dport 53 –i eth 1 -j ACCEPT OUTPUT –p udp –dport 53 –o eth 0 -j ACCEPT INPUT –p udp –dport 53 –i eth 0 -j ACCEPT Module 15 System Security Network (Firewall)

# # iptables – – A A OUTPUT –p udp –dport 53 –o eth 1 -j ACCEPT INPUT –p udp –dport 53 –i eth 1 -j ACCEPT OUTPUT –p udp –dport 53 –o eth 0 -j ACCEPT INPUT –p udp –dport 53 –i eth 0 -j ACCEPT That is: 1. Firewall to allow outgoing UDP packets that have destination port through the interface eth 1. 2. Firewall to allow outgoing UDP packets that have a home port through the interface eth 1. 3. Firewall to allow outgoing UDP packets that have destination port through the interface eth 0. 4. Firewall to allow outgoing UDP packets that have a home port through the interface eth 0. Module 15 System Security Network (Firewall) 53 53

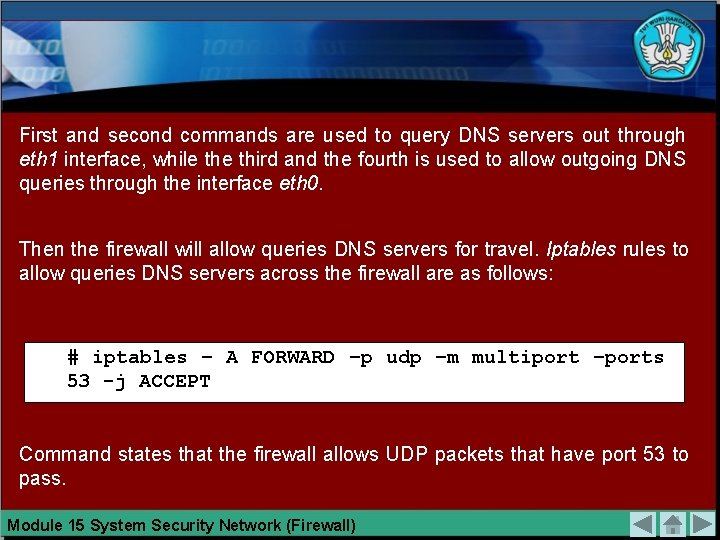
First and second commands are used to query DNS servers out through eth 1 interface, while third and the fourth is used to allow outgoing DNS queries through the interface eth 0. Then the firewall will allow queries DNS servers for travel. Iptables rules to allow queries DNS servers across the firewall are as follows: # iptables – A FORWARD –p udp –m multiport –ports 53 -j ACCEPT Command states that the firewall allows UDP packets that have port 53 to pass. Module 15 System Security Network (Firewall)

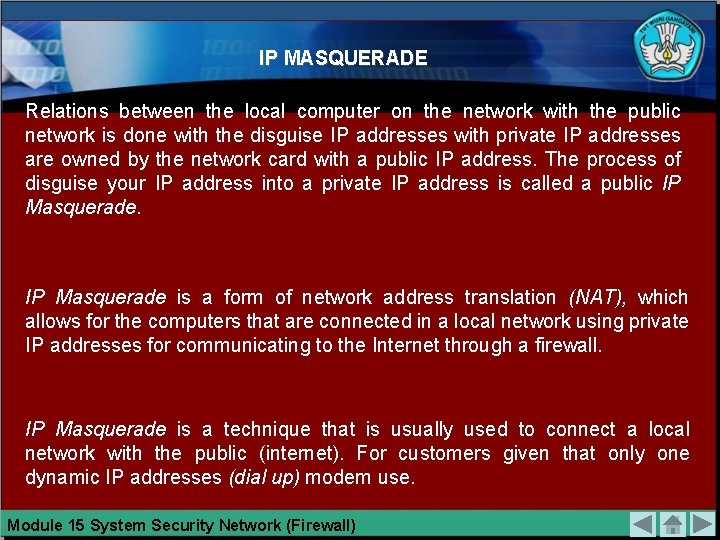
IP MASQUERADE Relations between the local computer on the network with the public network is done with the disguise IP addresses with private IP addresses are owned by the network card with a public IP address. The process of disguise your IP address into a private IP address is called a public IP Masquerade is a form of network address translation (NAT), which allows for the computers that are connected in a local network using private IP addresses for communicating to the Internet through a firewall. IP Masquerade is a technique that is usually used to connect a local network with the public (internet). For customers given that only one dynamic IP addresses (dial up) modem use. Module 15 System Security Network (Firewall)

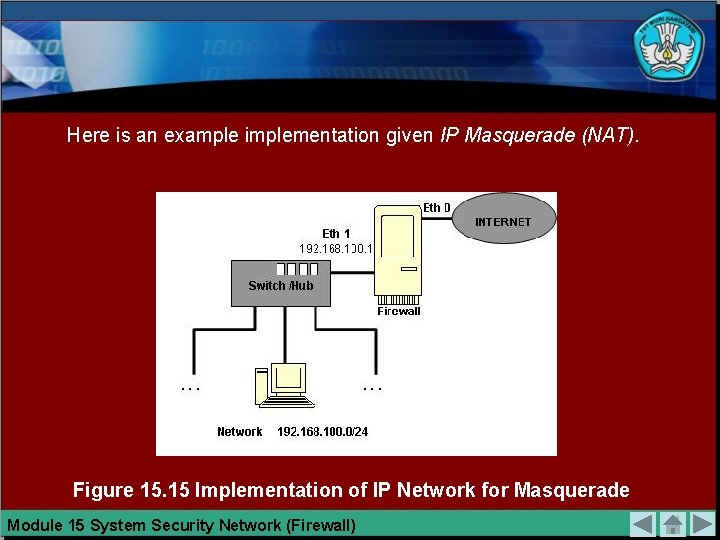
Here is an example implementation given IP Masquerade (NAT). Figure 15. 15 Implementation of IP Network for Masquerade Module 15 System Security Network (Firewall)

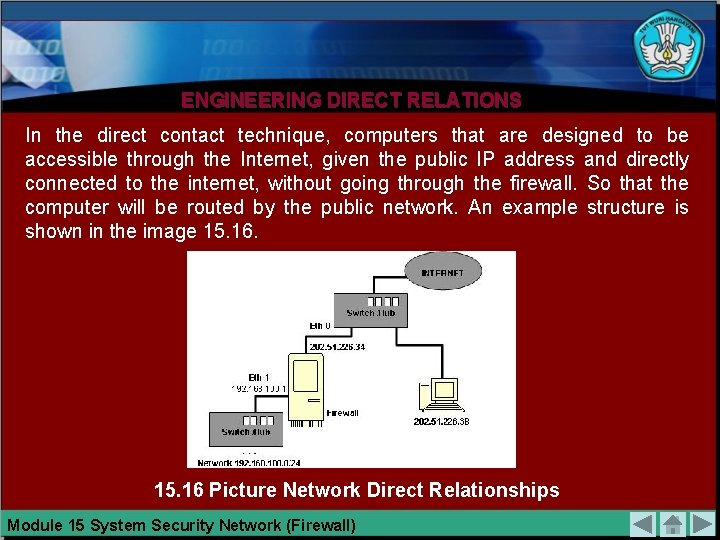
ENGINEERING DIRECT RELATIONS In the direct contact technique, computers that are designed to be accessible through the Internet, given the public IP address and directly connected to the internet, without going through the firewall. So that the computer will be routed by the public network. An example structure is shown in the image 15. 16 Picture Network Direct Relationships Module 15 System Security Network (Firewall)

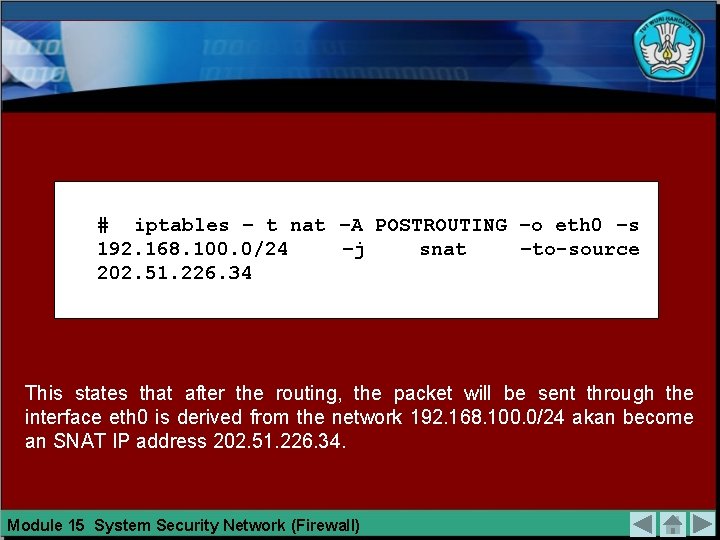
# iptables – t nat –A POSTROUTING –o eth 0 –s 192. 168. 100. 0/24 –j snat –to-source 202. 51. 226. 34 This states that after the routing, the packet will be sent through the interface eth 0 is derived from the network 192. 168. 100. 0/24 akan become an SNAT IP address 202. 51. 226. 34. Module 15 System Security Network (Firewall)

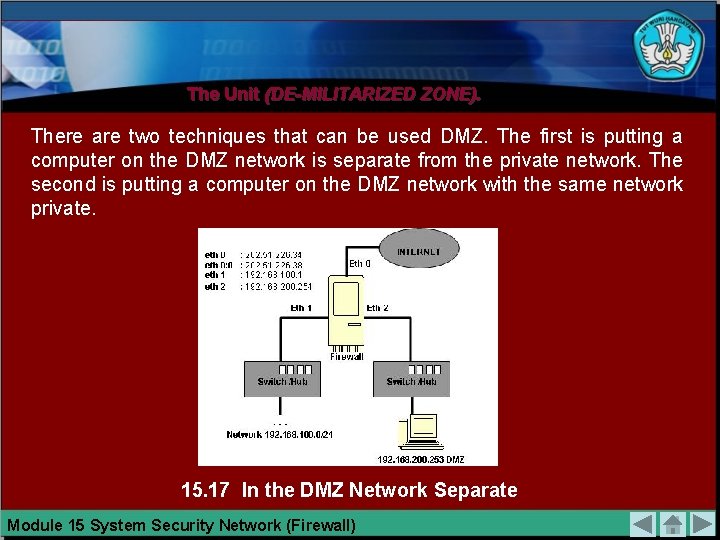
The Unit (DE-MILITARIZED ZONE). There are two techniques that can be used DMZ. The first is putting a computer on the DMZ network is separate from the private network. The second is putting a computer on the DMZ network with the same network private. 15. 17 In the DMZ Network Separate Module 15 System Security Network (Firewall)

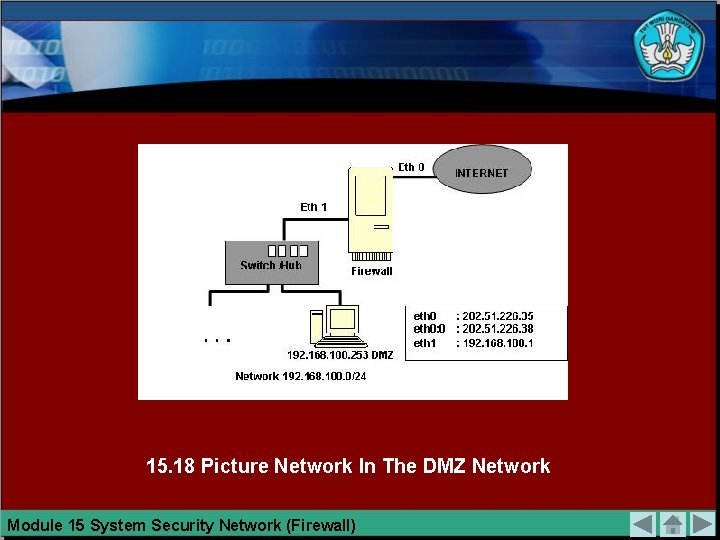
15. 18 Picture Network In The DMZ Network Module 15 System Security Network (Firewall)

Firewall WITH SPECIAL HARDWARE Firewall functions such as mentioned above can also be done with the use of special hardware vendors that have been designed for the purpose of making certain chains. Nevertheless, the technique and its application using the same IP Tables. On special hardware firewall chains to its implementation are designed in such a way that eases the administrator in implementing the rule / policy firewall. One thing that distinguishes the device is a firewall vendor's only designed for other functions without the chains, while the PC firewall can be used in addition to the firewall function to the other network terminals. Module 15 System Security Network (Firewall)

Exercise Answer the question below correctly. 1. What is a Firewall? 2. Describe the type of firewall for computer networks. 3. Please draw Firewall working relationship with the order of layer Reference Model TCP / IP. 4. From the four types of firewall, which impalements easily but have a high reliability? 5. Explain the difference between Pre routing and Post routing. 6. How to implement a rule / policy to allow access to an http server? 7. What is a DMZ? 8. How to implement NAT for 192. 168. 0. 0/24 with Private IP and Public IP 202. 203. 204. 2/30 9. Please draw topology to number 8. 10. What is a Firewall with hardware-specific HOME Module 15 System Security Network (Firewall)