Welcome Up in the Cloudz with AWS A

















- Slides: 30

Welcome! Up in the Cloudz with AWS: A Breakfast Briefing

Agenda for the morning 8. 30 am – The importance of GDPR: a business and technology perspective 8. 50 am – AWS: A practical guide 9. 20 am – Done. Deal: A Case Study 9. 55 am – AWS and the General Data Protection Regulation (GDPR) 10. 30 am – Q & A Session

Objective of Regulation (GDPR) • “Effective protection of personal data throughout the Union requires the strengthening and setting out in detail of the rights of data subjects and the obligations of those [in the public and private sectors] who process and determine the processing of personal data, as well as equivalent powers for monitoring and ensuring compliance with the rules for the protection of personal data and equivalent sanctions for infringements in the Member States”

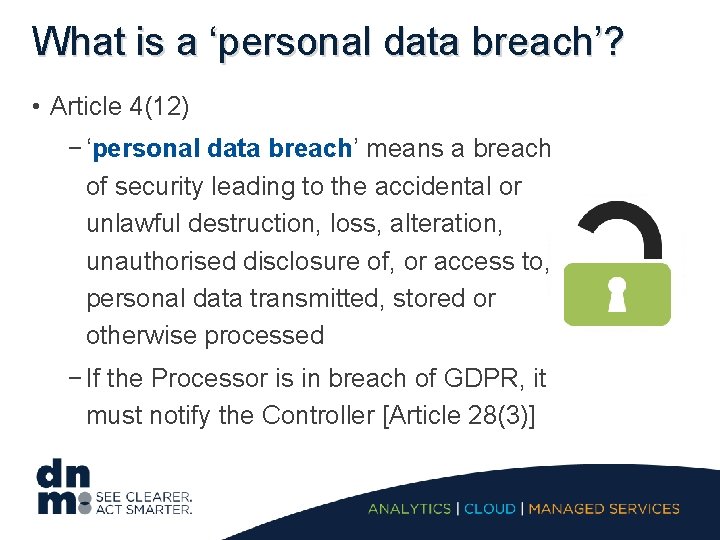
What is a ‘personal data breach’? • Article 4(12) − ‘personal data breach’ means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed − If the Processor is in breach of GDPR, it must notify the Controller [Article 28(3)]

DATA BREACHES

Data Breaches Why is it important? • There is currently no mechanism we are aware of that can protect potential targets from a cyber-attack 100% of the time (need to be able to respond to events) • Trend Micro predicted that 2016 would be the year of online extortion. They were proved correct as ransomware attacks increased by 400% • This appeared to level out until the recent Wanna. Cry and Petya worldwide attacks. Ransomware is but one form of cyber-attack. • In 2016 - 2, 301 data breach notifications were made to the ODPC of which 77 (3. 3%) were classified as non-breaches under the Personal Data Security Breach Code of Practice.

RIGHTS OF DATA SUBJECTS

Rights of Data Subjects Why is it important? 1. Controllers have a legal obligation to give effect to the rights of data subjects • Recital 59 “Modalities should be provided for facilitating the exercise of the data subject's rights under this Regulation, including mechanisms to request and, if applicable, obtain, free of charge, in particular, access to and rectification or erasure of personal data and the exercise of the right to object. The controller should also provide means for requests to be made electronically, especially where personal data are processed by electronic means. The controller should be obliged to respond to requests from the data subject without undue delay and at the latest within one month and to give reasons where the controller does not intend to comply with any such requests. ” • Article 12(2) − “The controller shall facilitate the exercise of data subject rights under Articles 15 to 22. ”

2. Time limits for complying with the rights of data subjects Article 12(3) to 12(4) A controller must, within one month of receiving a request made under those rights, provide any requested information in relation to any of the rights of data subjects. If the controller fails to meet this deadline, the data subject may complain to the relevant DPA and may seek a judicial remedy. Where a controller receives large numbers of requests, or especially complex requests, the time limit may be extended by a maximum of two further months.

Right of Access (DSAR) • 1, 479 complaints to ODPC in 2016 – 835 related to access rights • Data subjects have the right to obtain the following information: − confirmation by controller of whether, and where, is the processing; − the purposes of the processing; − the categories of data being processed; − the categories of recipients with whom the data is shared, esp, third countries; − where possible, the period for which the data will be stored (or the criteria used to determine that period); − information about the existence of the rights to erasure, to rectification, to restriction of processing and to object to processing; − the existence of the right to complain to the Supervisory Authority; − where the data were not collected from the data subject, information as to the source of the data; and − information about the existence of, and an explanation of the logic involved in, any automated processing that has a significant effect on data subjects.

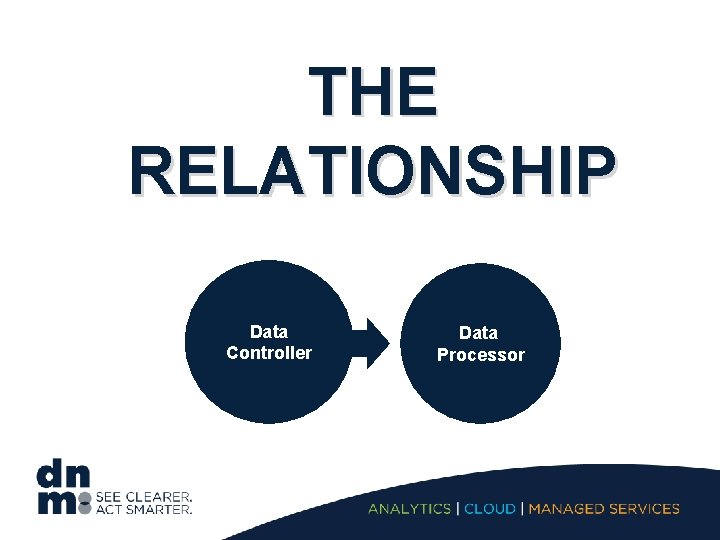
THE RELATIONSHIP Data Controller Data Processor

Controller / Processor relationship Shared responsibility model • Article 28(1) − “Where processing is to be carried out on behalf of a controller, the controller shall use only processors providing sufficient guarantees to implement appropriate technical and organisational measures [TOMs] in such a manner that processing will meet the requirements of this Regulation and ensure the protection of the rights of the data subject. ” • Article 28(3) Appointment = a binding written agreement which states that the Processor must: (a) only act on the documented instructions from the Controller (b) commit to confidentiality (c) take all security measures as prescribed by Article 32 (d) abide by the rules for engaging a sub-processor (e) assist Controller in complying with rights of data subjects (f) assist Controller with security requirements, breach notifications and PIAs (g) delete or return personal data to the Controller (h) demonstrate compliance with the above (through audits and inspections)

The impact remedies, liability and penalties • Administrative fines • Reputational damage • Right to compensation – NEW! − Current law – quantifiable loss, financial loss, material damage vs. − Article 82(1): o “Any person who has suffered material or non-material damage as a result of an infringement of this Regulation shall have the right to receive compensation from the controller or processor for the damage suffered” − Article 82(2): o Any Controller involved in processing shall be liable for the damage caused by processing which infringes this Regulation. o A Processor shall be liable for the damage caused by processing only where it has not complied with its obligations specifically directed to Processors or where it has acted outside or contrary to lawful instructions of the Controller.

Top tips • Accountability and Transparency − The data lifecycle is not the same for all personal data − Data discovery and classification – the ‘what’ and ‘where’ tests − Data mapping – the ‘why’ test • Controller / Processor relationship − Review Data Processing Agreements to ensure compliance with Article 28…find yourself a certified processor • Rights of Data Subjects − Policies and procedures – the perfect storm of combination requests − Data minimisation − DSARS o Consider reducing scope o Exemptions (for example, third party data, legal privilege, opinion in confidence, non personal data)

Data breach management A consideration Key – Develop a system for early detection and deployment of a response team as quickly as possible. • There are numerous ways to implement appropriate security measures to try and prevent a breach. − Completing an audit of the company’s data structure and processes, − Conducting privacy impact assessments, (Admin, Finance, HR, IT) − Implementing privacy by design to ensure data at every level of your business is protected, − Engage with a processor - guarantees to implement appropriate technical and organisational measures − Employee training and Awareness − Preparation of a Data Breach Management Plan. Be proactive, not reactive!

Amazon Web Services a practical guide

The importance of being Well- Architected • Our responsibilities and demands: − Preserve information and service o Confidentiality o Integrity o Availability − Manage Costs and Efficiencies o Elastic and Dynamic Resources − Agility ≠ Lack of Governance

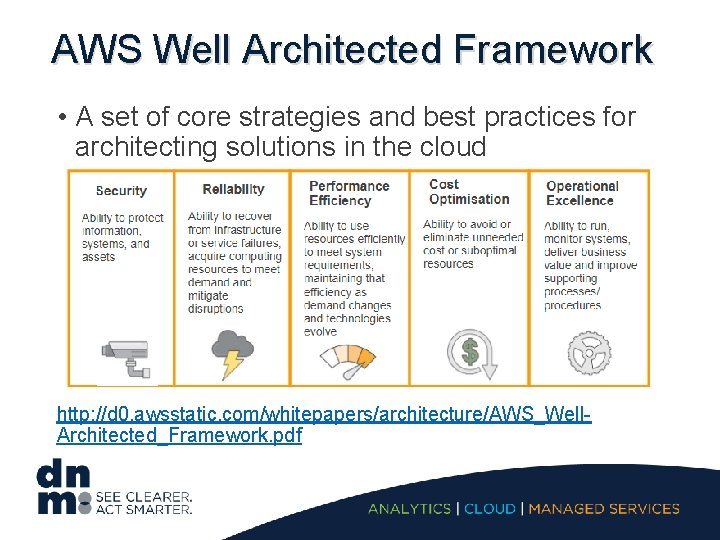
AWS Well Architected Framework • A set of core strategies and best practices for architecting solutions in the cloud http: //d 0. awsstatic. com/whitepapers/architecture/AWS_Well. Architected_Framework. pdf

Mass Migration - a proven approach

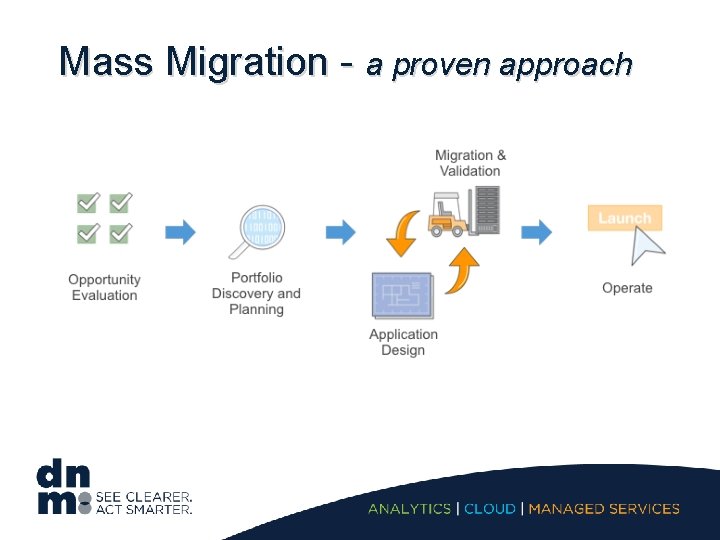
Mass Migration - a proven approach

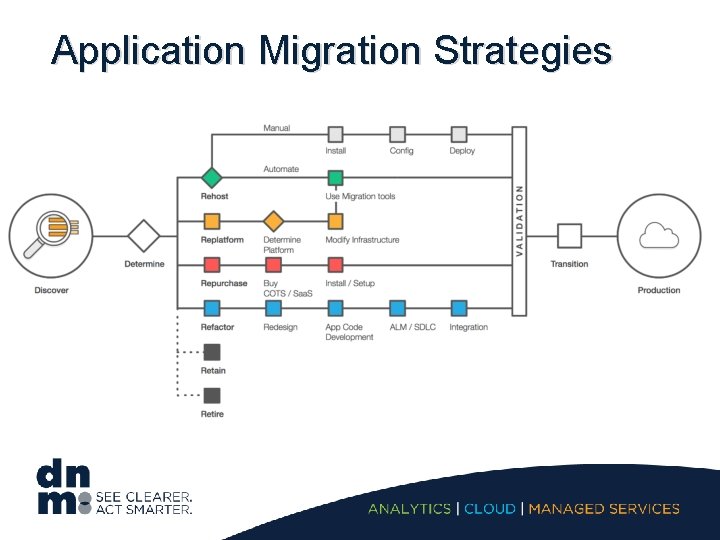
Application Migration Strategies

My new Dev. Ops Team • Transform the delivery of solutions by using automation to ensure a consistent result, enforcing best practices with faster turn around times and greater autonomy • Iterate, learn, improve

Dev. Ops Tools • A few options : − Ansible, Chef, Salt, Puppet. . − AWS Cloudformation, Terraform. . • Considerations − Speed to introduce new AWS features − Standalone vs Central Manager − Pre-reqs : ruby / python … • Not exclusive: − Ansible managed Cloudformation − Cloudformation with embedded Ansible

A new class of Service AWS Next Gen Managed Service • Visibility into the whole stack ↕↔ • Manage dynamic and highly automated environments • Detect abnormal states and patterns of behaviour • Insight into application and service performance

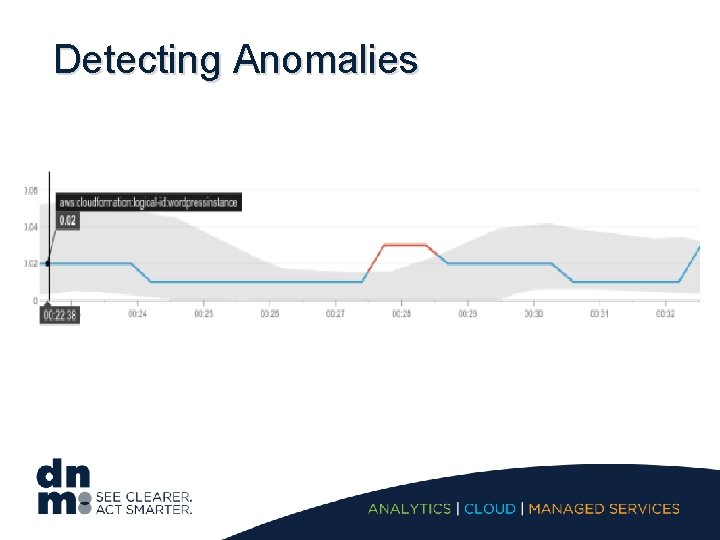
Detecting Anomalies

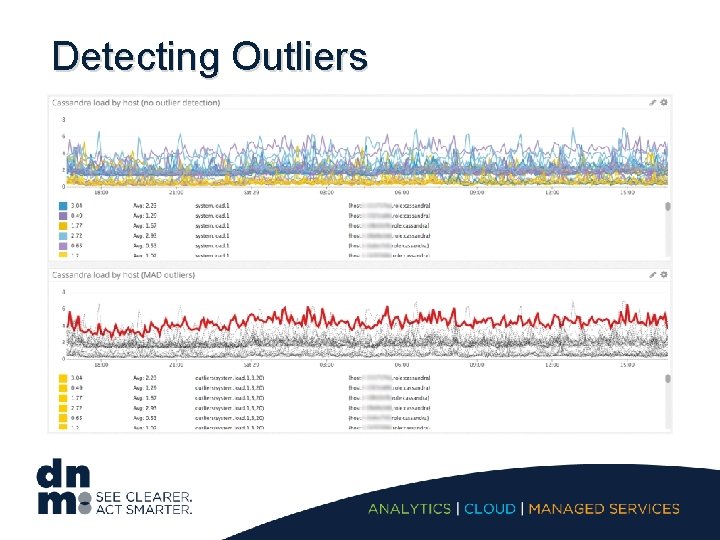
Detecting Outliers

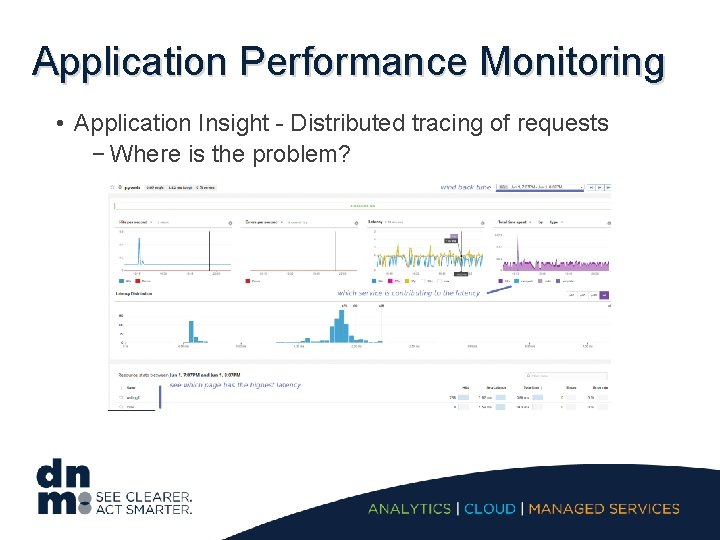
Application Performance Monitoring • Application Insight - Distributed tracing of requests − Where is the problem?

Composite Views • Multiple sources / type of events and metrics: + • Statistical analyses of past behaviour to automate the detection of unusual behaviour = The insight to ensure information Confidentiality, Integrity and Availability

Q&A Session

Thanks for coming! Fancy a free Discovery Workshop? Come talk to us!