Network Security CPSC 6128 Lecture 5 Cryptography CPSC














![Symmetric Key Crypto: DES: Data Encryption Standard q. US encryption standard [NIST 1993] q Symmetric Key Crypto: DES: Data Encryption Standard q. US encryption standard [NIST 1993] q](https://slidetodoc.com/presentation_image_h/942d06bb897b794c262843e71ea5feaa/image-35.jpg)














- Slides: 81

Network Security CPSC 6128 – Lecture 5 Cryptography CPSC 6128 - Network Security 1

Cryptography q. Overview q. Symmetric Key Cryptography q. Public Key Cryptography q. Message integrity and digital signatures q. References: v. Stamp v. Schneier CPSC 6128 - Network Security 2

Cryptography basics q. The process of converting plaintext into ciphertext v. Plaintext ØReadable text v. Ciphertext ØUnreadable or encrypted text q. It is used to hide information from unauthorized users q. Decryption vthe process of converting ciphertext back to plaintext CPSC 6128 - Network Security 3

History of Cryptography q. Substitution Cipher v. Replaces one letter with another letter based on some key v. Example: Julius Ceasar’s Cipher ØKey value of 3 ØABCDEFGHIJKLMNOPQRSTUVWXYZ ØDEFGHIJKLMNOPQRSTUVWXYZABC CPSC 6128 - Network Security 4

History of Cryptography (cont) q. Cryptanalysis vstudies the process of breaking encryption algorithms q. When a new encryption algorithm is developed v cryptanalysts study it and try to break it v. This is an important part of the development cycle of a new encryption algorithm CPSC 6128 - Network Security 5

World War I q Zimmerman Telegram ØEncrypted telegram from foreign secretary of the German empire to German ambassador in Mexico ØIntercepted and decrypted by the British ØIndicated that unrestricted sub warfare would commence ØProposed an alliance with Mexico to reclaim lost land to US. ØPivotal in US entering WWI Cortesty: Wikipedia CPSC 6128 - Network Security 6

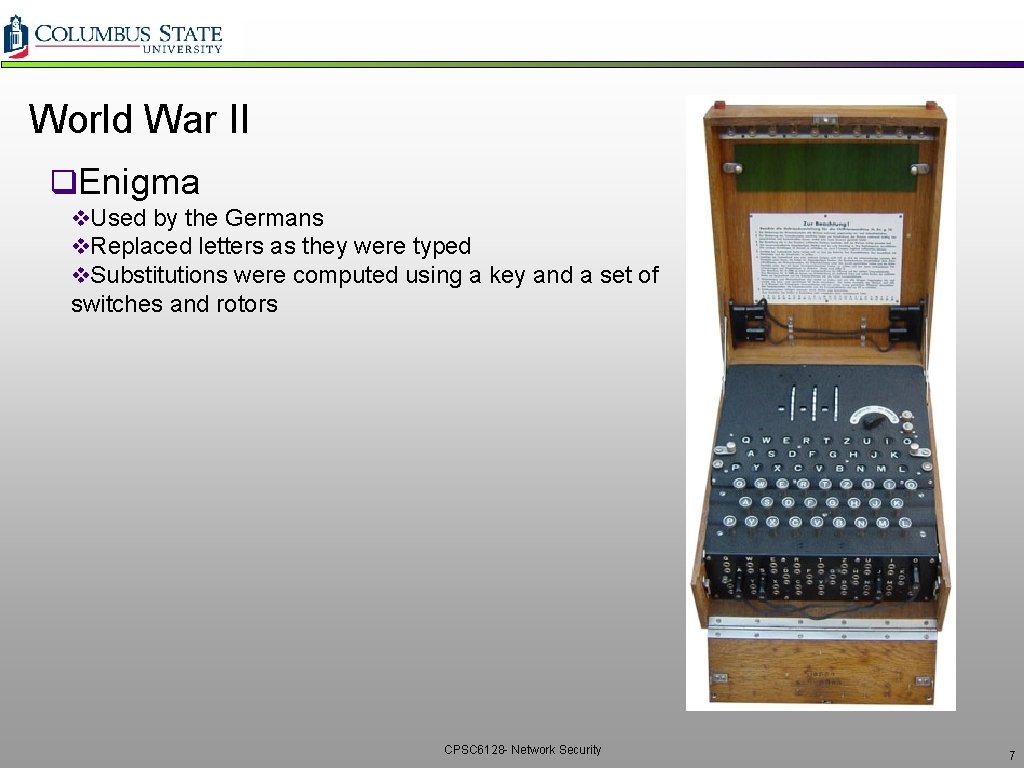
World War II q. Enigma v. Used by the Germans v. Replaced letters as they were typed v. Substitutions were computed using a key and a set of switches and rotors CPSC 6128 - Network Security 7

Cryptography Issues q. Confidentiality vonly sender, intended receiver should “understand” message contents: Øsender encrypts message Øreceiver decrypts message q. End-Point Authentication vsend, receiver want to confirm identity of each other. q. Message Integrity vsender, receiver want to ensure message not altered CPSC 6128 - Network Security 8

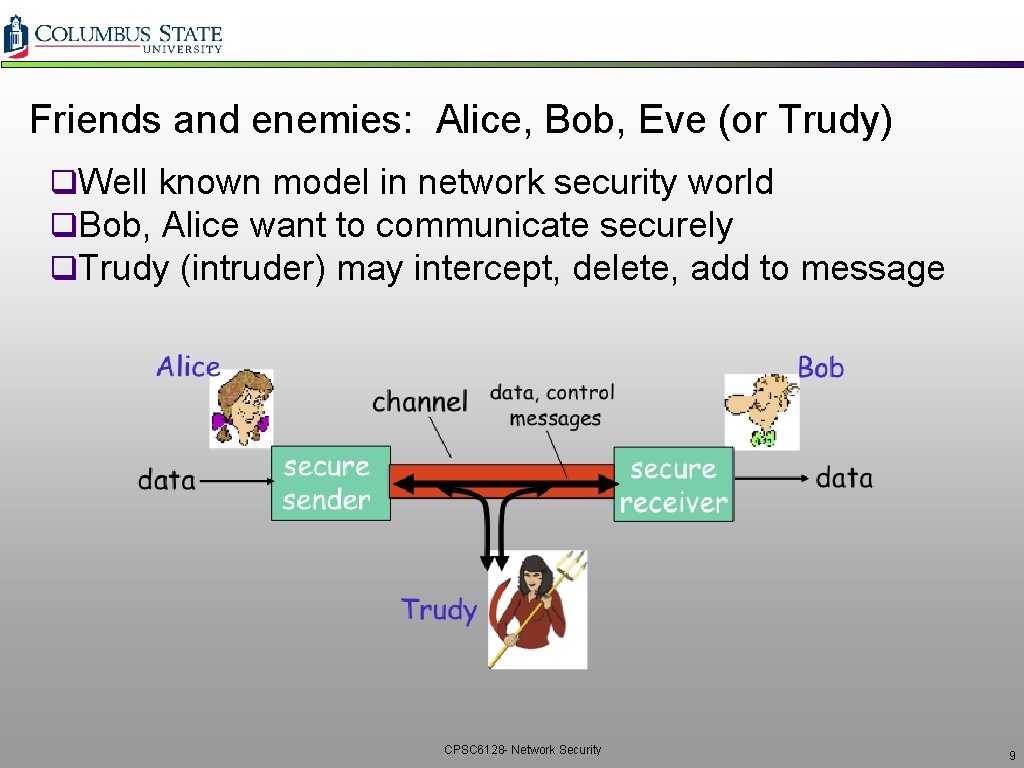
Friends and enemies: Alice, Bob, Eve (or Trudy) q. Well known model in network security world q. Bob, Alice want to communicate securely q. Trudy (intruder) may intercept, delete, add to message CPSC 6128 - Network Security 9

Who might Bob, Alice be? q. . . well, real-life Bobs and Alices ØWeb browsers/server for electronic transactions Øonline banking client/server ØDNS servers Ørouters exchanging routing table updates CPSC 6128 - Network Security 10

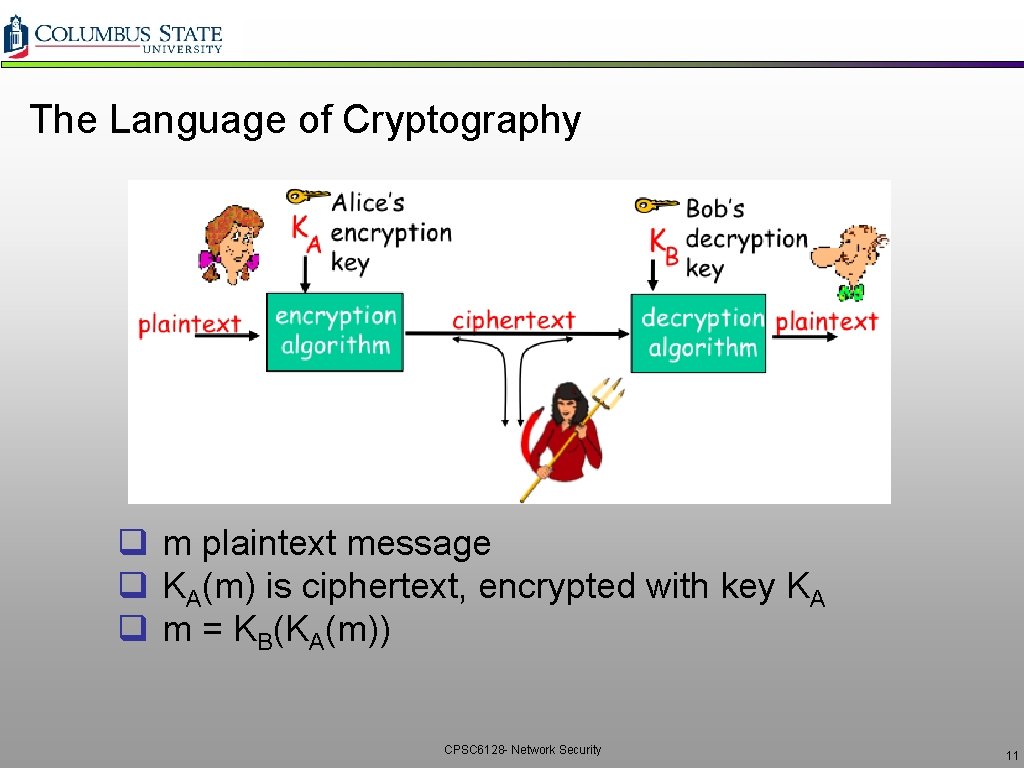
The Language of Cryptography q m plaintext message q KA(m) is ciphertext, encrypted with key KA q m = KB(KA(m)) CPSC 6128 - Network Security 11

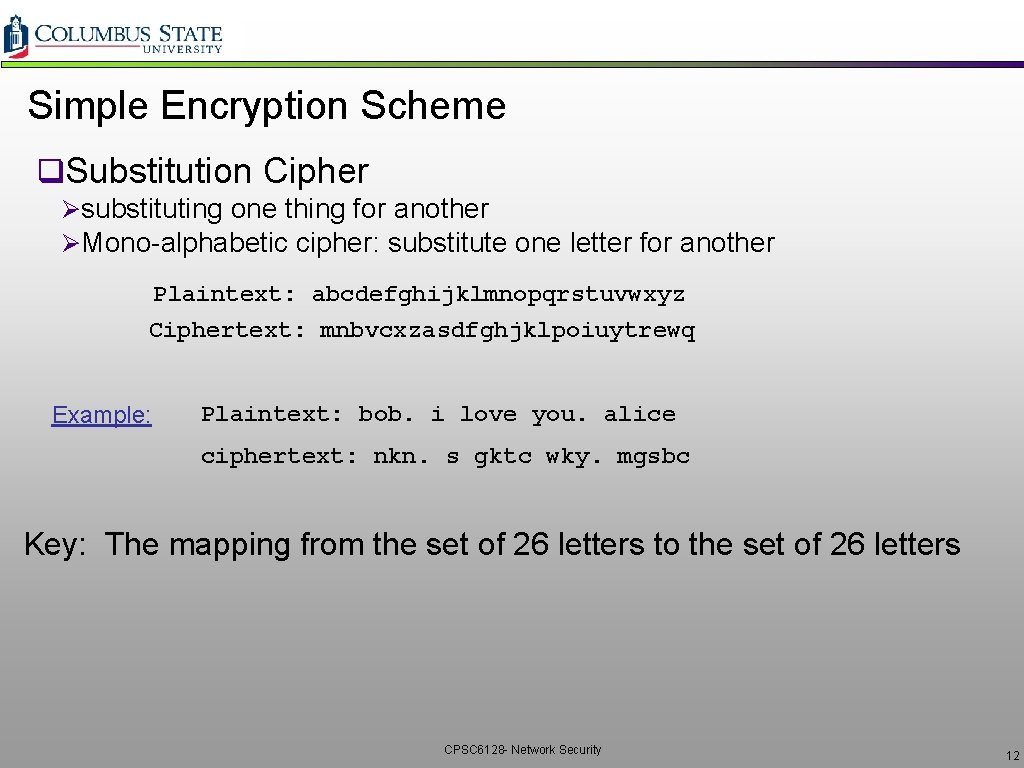
Simple Encryption Scheme q. Substitution Cipher Øsubstituting one thing for another ØMono-alphabetic cipher: substitute one letter for another Plaintext: abcdefghijklmnopqrstuvwxyz Ciphertext: mnbvcxzasdfghjklpoiuytrewq Example: Plaintext: bob. i love you. alice ciphertext: nkn. s gktc wky. mgsbc Key: The mapping from the set of 26 letters to the set of 26 letters CPSC 6128 - Network Security 12

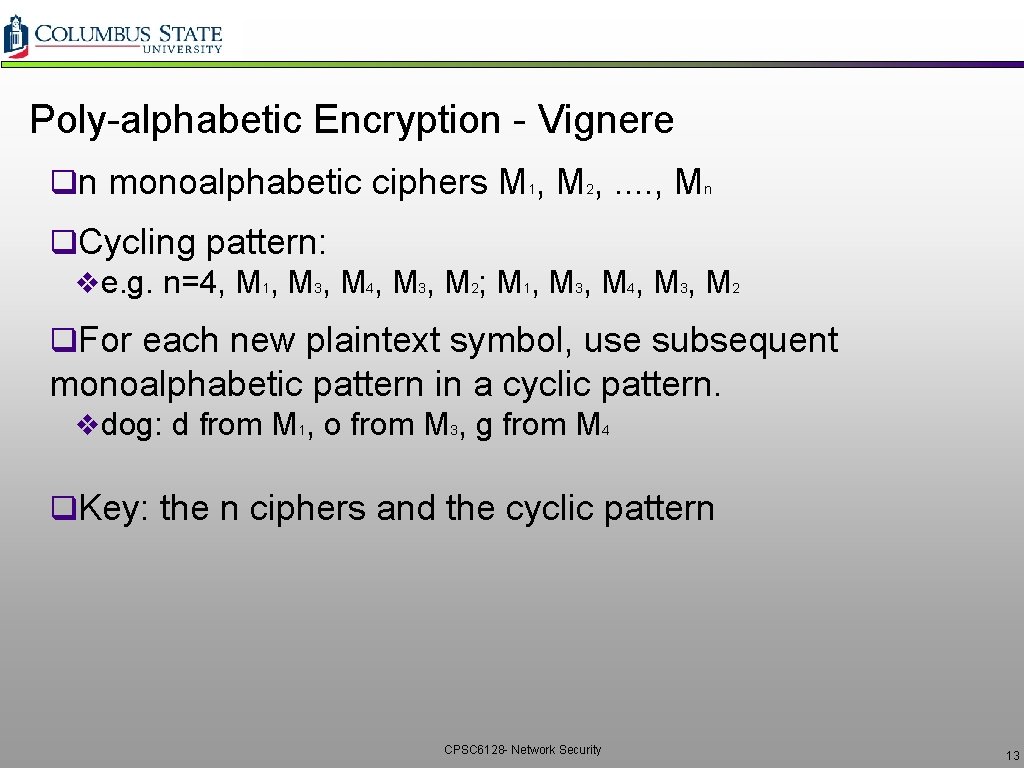
Poly-alphabetic Encryption - Vignere qn monoalphabetic ciphers M 1, M 2, . . , Mn q. Cycling pattern: ve. g. n=4, M 1, M 3, M 4, M 3, M 2; M 1, M 3, M 4, M 3, M 2 q. For each new plaintext symbol, use subsequent monoalphabetic pattern in a cyclic pattern. vdog: d from M 1, o from M 3, g from M 4 q. Key: the n ciphers and the cyclic pattern CPSC 6128 - Network Security 13

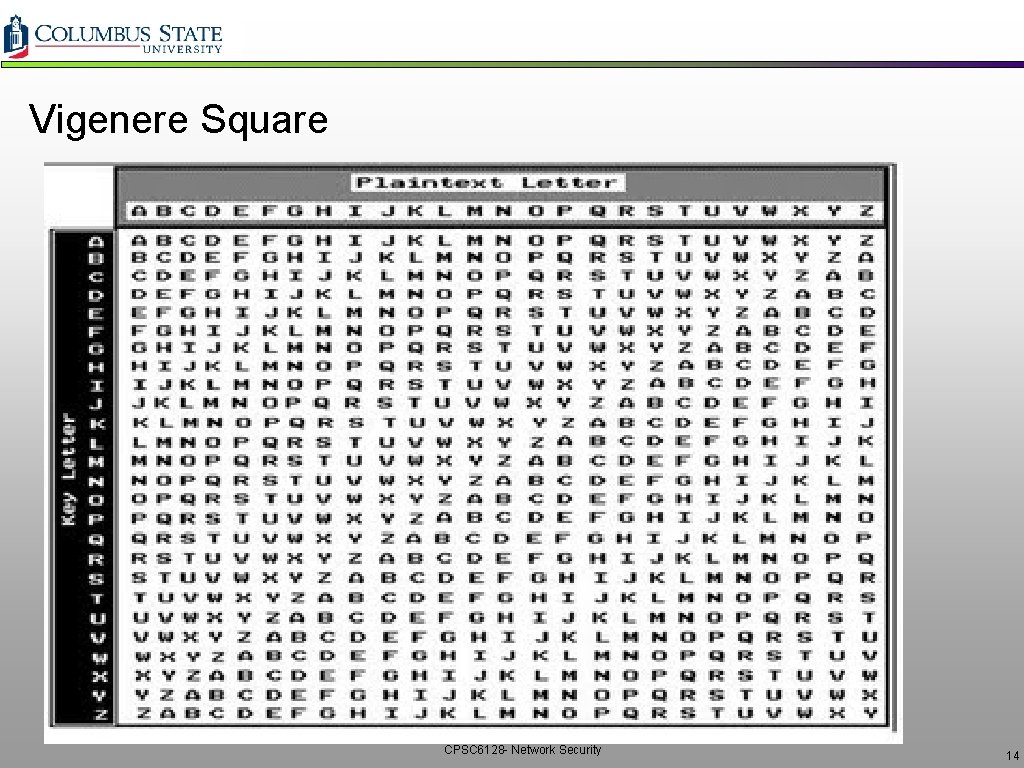
Vigenere Square CPSC 6128 - Network Security 14

Vernam – Perfect Substitution Cipher q If we use Vignere with keylength as long as the plaintext vthen cryptanalysis will become very difficult. q If we change key every time we encrypt vthen cryptanalyst’s job becomes even more difficult v. One-time pad or Vernam Cipher q How do we get such long keys? v. A large book shared by transmitter and receiver v. Initial key followed by previous messages themselves!! v. Random number sequence based on common shared and secret seed q Such a cipher is difficult to break v but not very practical CPSC 6128 - Network Security 15

Breaking an Encryption Scheme q. Ciphertext only attack v. Eve has ciphertext that she can analyze q. Two approaches v. Search through all keys Ømust be able to differentiate resulting plaintext from gibbersh v. Statistical analysis q. Know-plaintext attack v. Eve has some plaintext corresponding to some ciphertext veg, in monoalphabetic cipher, trudy determines pairings for a, l, i, c, e, b, o q. Chosen-plaintext attack v. Eve can get the ciphertext from some chosen plaintext CPSC 6128 - Network Security 16

Computational Effort Required q. Time ØNumber of primitive operations required ØComputational time required for the attack ØSome attacks become more feasible as computing power becomes cheaper and faster q. Memory ØAmount of storage required to complete the attack ØThis can be either hard disk or memory q. Data ØAmount of captured data required to complete the attack CPSC 6128 - Network Security 17

Rainbow Tables attack q. Time/Memory Tradeoff q. Used to recover the plaintext from a given HASH value q. Commonly used to attack HASHed password q. SALT Ørandom number concatenated to the HASH value to prevent Rainbow table attacks Øsaltedhash(password) = hash(password. salt) ØSince SALT is a random number Øthe attacker would have to compute a Rainbow table for each SALT value ØLarge SALT value is critical q. More on Hashes Later CPSC 6128 - Network Security 18

Types of Cryptography q. Crypto often uses keys: ØAlgorithm is known to everyone ØOnly “keys” are secret üKerckhoff’s Principle üCan be extended to security systems design in general q. Public Key Cryptography v. Involves the use of two keys q. Symmetric key cryptography v. Involves the use of one key q. Hash functions v. Involves the use of no keys v. Nothing secret: How can this be useful? CPSC 6128 - Network Security 19

Shannon Characteristics of Good Ciphers q. The amount of secrecy needed should determine Øthe amount of labor appropriate for encryption and decryption q. The set of keys and enciphering algorithms Øshould be free from complexity q. The implementation of the process Øshould be as simple as possible q. Errors in ciphering should not Øpropagate and cause corruption of future information in the message q. The size of enciphered text ØShould not be longer than the text of the original message CPSC 6128 - Network Security 20

Confusion and Diffusion q. Confusion ØThe cryptanalyst should not be able to predict what changing one character in the plaintext will do to the ciphertext q. Diffusion ØChanges in the key should affect many parts in the ciphertext CPSC 6128 - Network Security 21

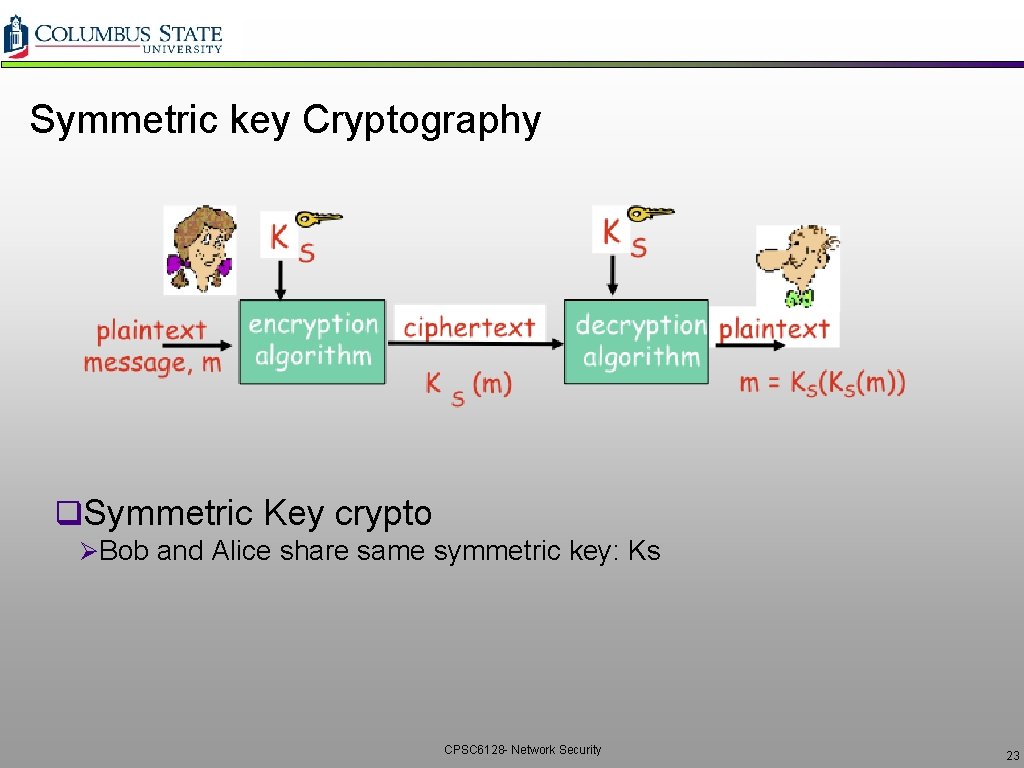
Symmetric Key Cryptography CPSC 6128 - Network Security 22

Symmetric key Cryptography q. Symmetric Key crypto ØBob and Alice share same symmetric key: Ks CPSC 6128 - Network Security 23

Two Types of Symmetric Ciphers q. Stream Ciphers ØEncrypt one bit at a time q. Block Ciphers ØBreak plaintext message into equal-size blocks ØEncrypt each block as a unit CPSC 6128 - Network Security 24

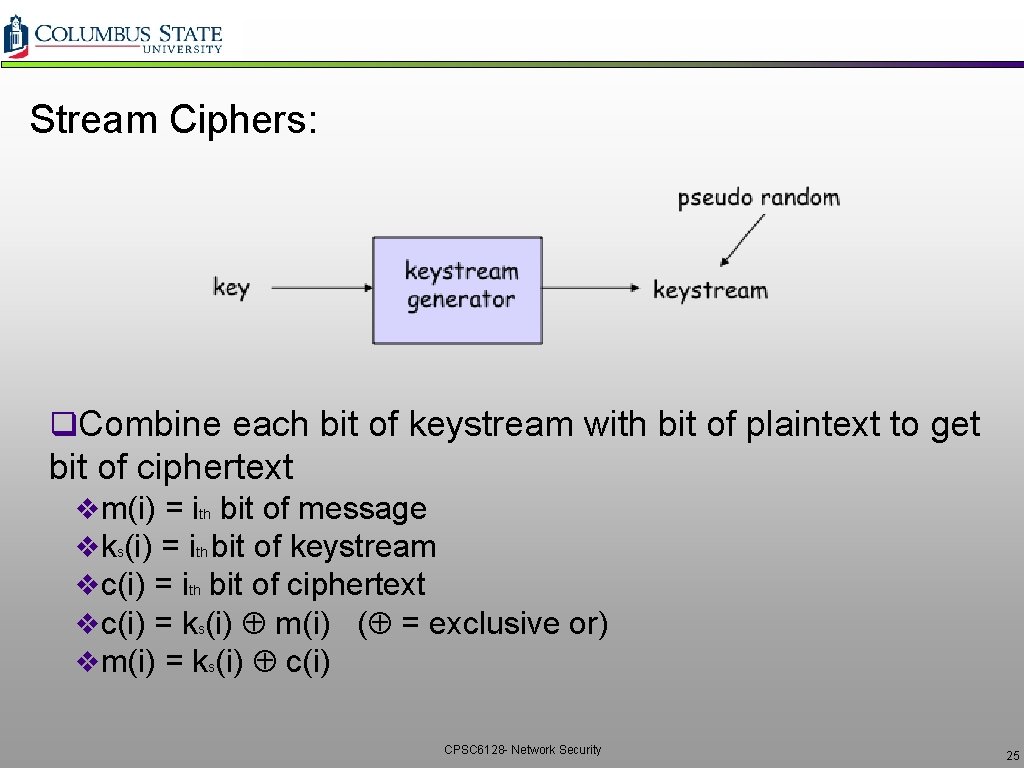
Stream Ciphers: q. Combine each bit of keystream with bit of plaintext to get bit of ciphertext vm(i) = ith bit of message vks(i) = ith bit of keystream vc(i) = ith bit of ciphertext vc(i) = ks(i) m(i) ( = exclusive or) vm(i) = ks(i) c(i) CPSC 6128 - Network Security 25

Problems With Stream Ciphers q. Known plain-text attack ØThere’s often predictable and repetitive data in communication messages Øattacker receives some cipher text c and correctly guesses corresponding plaintext m Øks = m c ØAttacker now observes c', obtained with same sequence ks ØM' = ks c' q Even easier Ø Attacker obtains two ciphertexts, c and c', generating with same key sequence Ø c c' = m m' ü There are well known methods for decrypting 2 plaintexts given their XOR q Integrity problem too Ø Ø suppose attacker knows c and m (eg, plaintext attack); wants to change m to m' calculates c' = c (m m') sends c' to destination CPSC 6128 - Network Security 26

Example: RC 4 Stream Cipher q. RC 4 is a popular stream cipher v. Extensively analyzed and considered good v. Key can be from 1 to 256 bytes v. Used in WEP for 802. 11 v. Can be used in SSL CPSC 6128 - Network Security 27

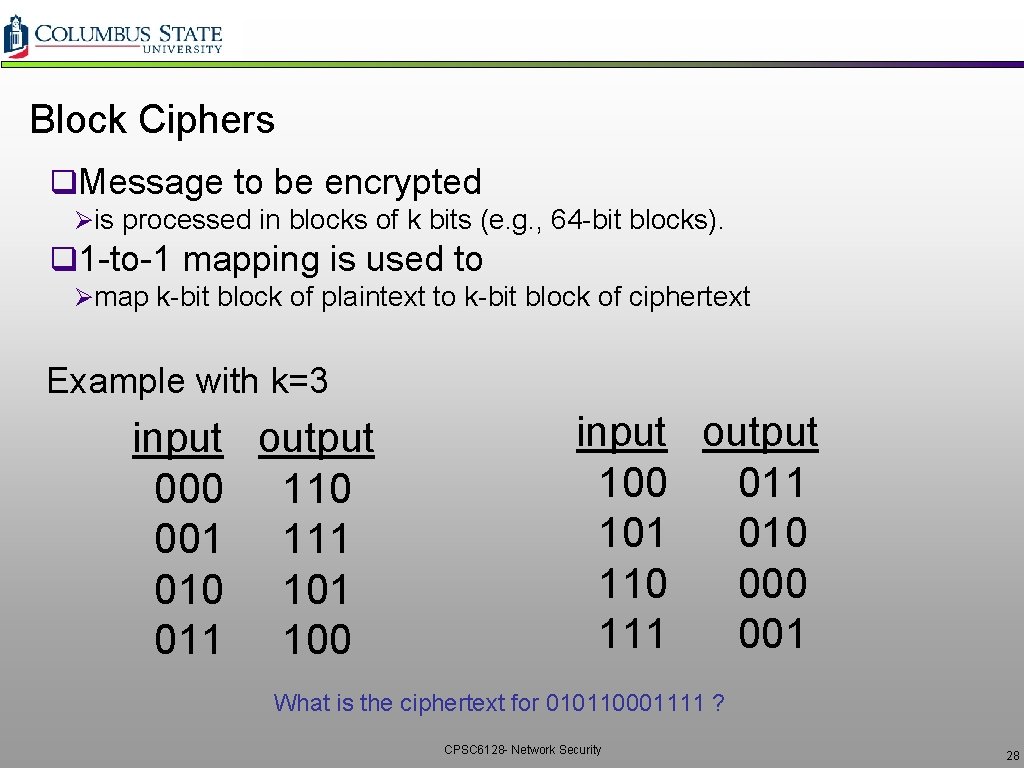
Block Ciphers q. Message to be encrypted Øis processed in blocks of k bits (e. g. , 64 -bit blocks). q 1 -to-1 mapping is used to Ømap k-bit block of plaintext to k-bit block of ciphertext Example with k=3 input output 000 110 001 111 010 101 011 100 input output 100 011 101 010 110 000 111 001 What is the ciphertext for 010110001111 ? CPSC 6128 - Network Security 28

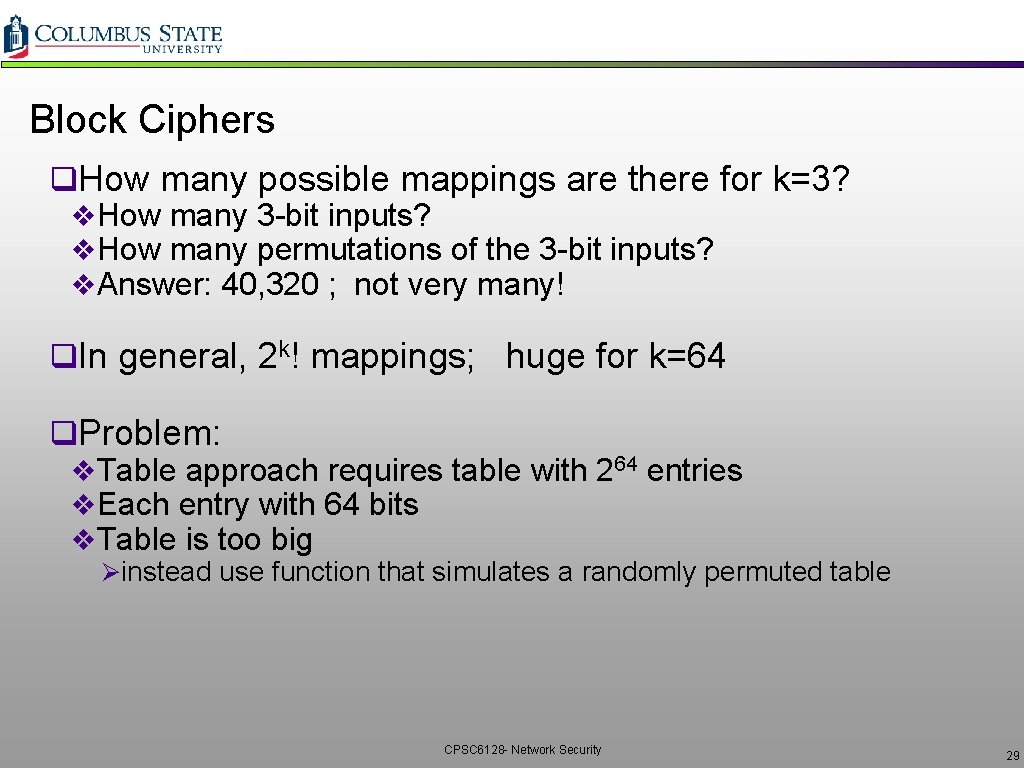
Block Ciphers q. How many possible mappings are there for k=3? v. How many 3 -bit inputs? v. How many permutations of the 3 -bit inputs? v. Answer: 40, 320 ; not very many! q. In general, 2 k! mappings; huge for k=64 q. Problem: v. Table approach requires table with 264 entries v. Each entry with 64 bits v. Table is too big Øinstead use function that simulates a randomly permuted table CPSC 6128 - Network Security 29

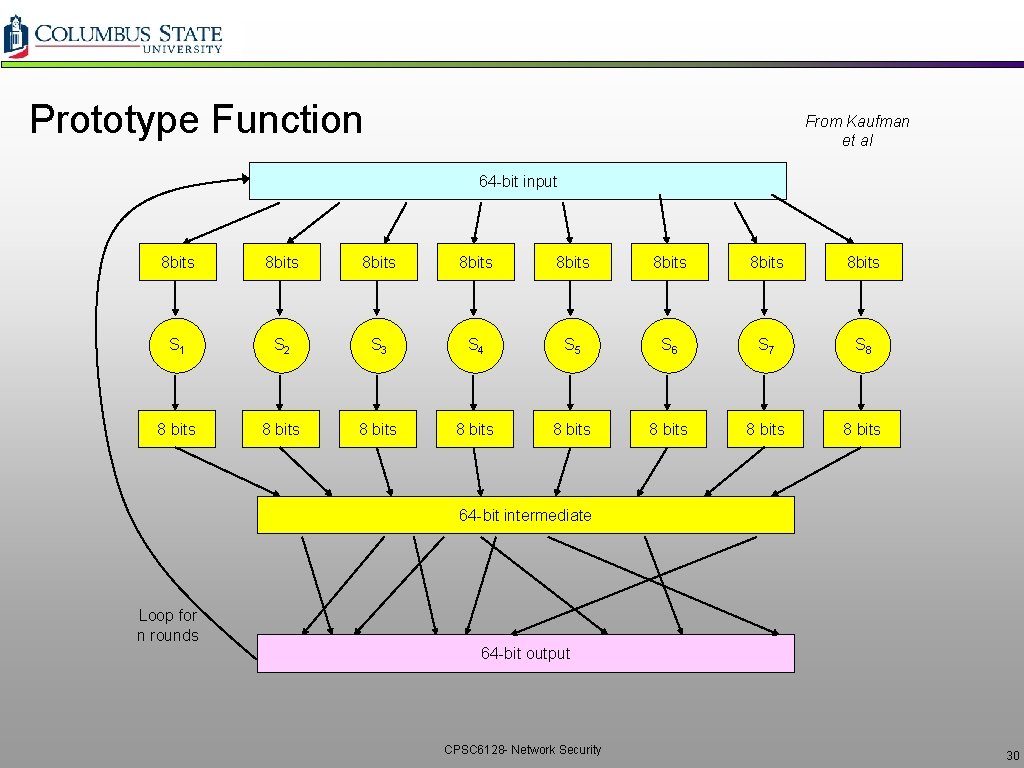
Prototype Function From Kaufman et al 64 -bit input 8 bits 8 bits S 1 S 2 S 3 S 4 S 5 S 6 S 7 S 8 8 bits 8 bits 64 -bit intermediate Loop for n rounds 64 -bit output CPSC 6128 - Network Security 30

Why Rounds in Prototype? q. If only a single round, then one bit of input affects at most 8 bits of output. q. In 2 nd round, the 8 affected bits get scattered and inputted into multiple substitution boxes. q. How many rounds? v. How many times do you need to shuffle cards? v. Becomes less efficient as n increases CPSC 6128 - Network Security 31

Encrypting a Large Message q. Why not just break message in 64 -bit blocks, encrypt each block separately? ØIf same block of plaintext appears twice, will give same cyphertext q. How to fix it? ØGenerate random 64 -bit number r(i) for each plaintext block m(i) ØCalculate c(i) = KS( m(i) r(i) ) ØTransmit c(i), r(i), i=1, 2, … ØAt receiver: m(i) = KS(c(i)) r(i) ØProblem: inefficient, need to send c(i) and r(i) CPSC 6128 - Network Security 32

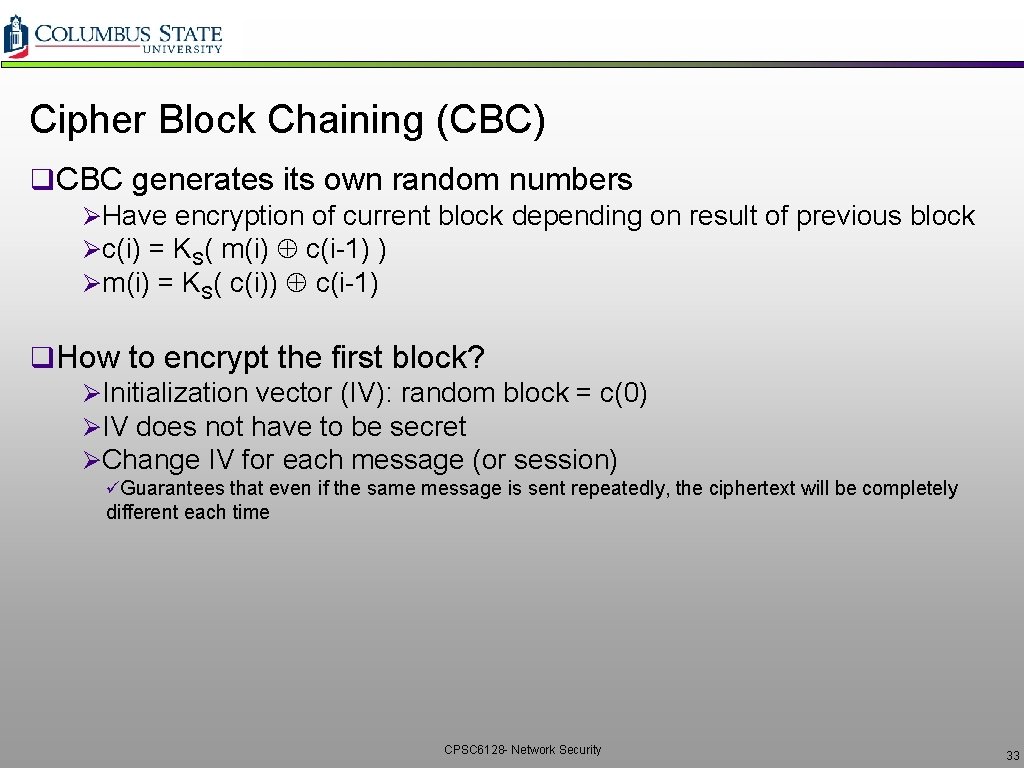
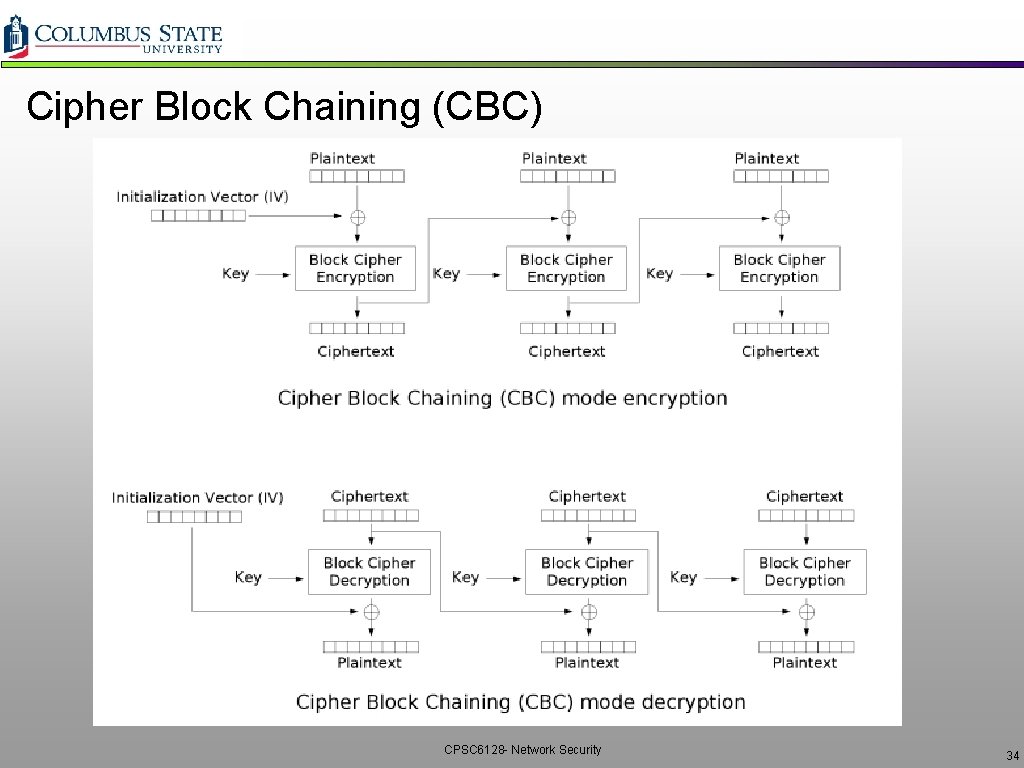
Cipher Block Chaining (CBC) q. CBC generates its own random numbers ØHave encryption of current block depending on result of previous block Øc(i) = KS( m(i) c(i-1) ) Øm(i) = KS( c(i)) c(i-1) q. How to encrypt the first block? ØInitialization vector (IV): random block = c(0) ØIV does not have to be secret ØChange IV for each message (or session) üGuarantees that even if the same message is sent repeatedly, the ciphertext will be completely different each time CPSC 6128 - Network Security 33

Cipher Block Chaining (CBC) CPSC 6128 - Network Security 34
![Symmetric Key Crypto DES Data Encryption Standard q US encryption standard NIST 1993 q Symmetric Key Crypto: DES: Data Encryption Standard q. US encryption standard [NIST 1993] q](https://slidetodoc.com/presentation_image_h/942d06bb897b794c262843e71ea5feaa/image-35.jpg)
Symmetric Key Crypto: DES: Data Encryption Standard q. US encryption standard [NIST 1993] q 56 -bit symmetric key, 64 -bit plaintext input q. Block cipher with cipher block chaining q. How secure is DES? ØDES Challenge: 56 -bit-key-encrypted phrase decrypted (brute force) in less than a day ØNo known good analytic attack making DES more secure Ø 3 DES: encrypt/decrypt 3 times with 3 different keys üciphertext = EK 3(DK 2(EK 1(plaintext))) CPSC 6128 - Network Security 35

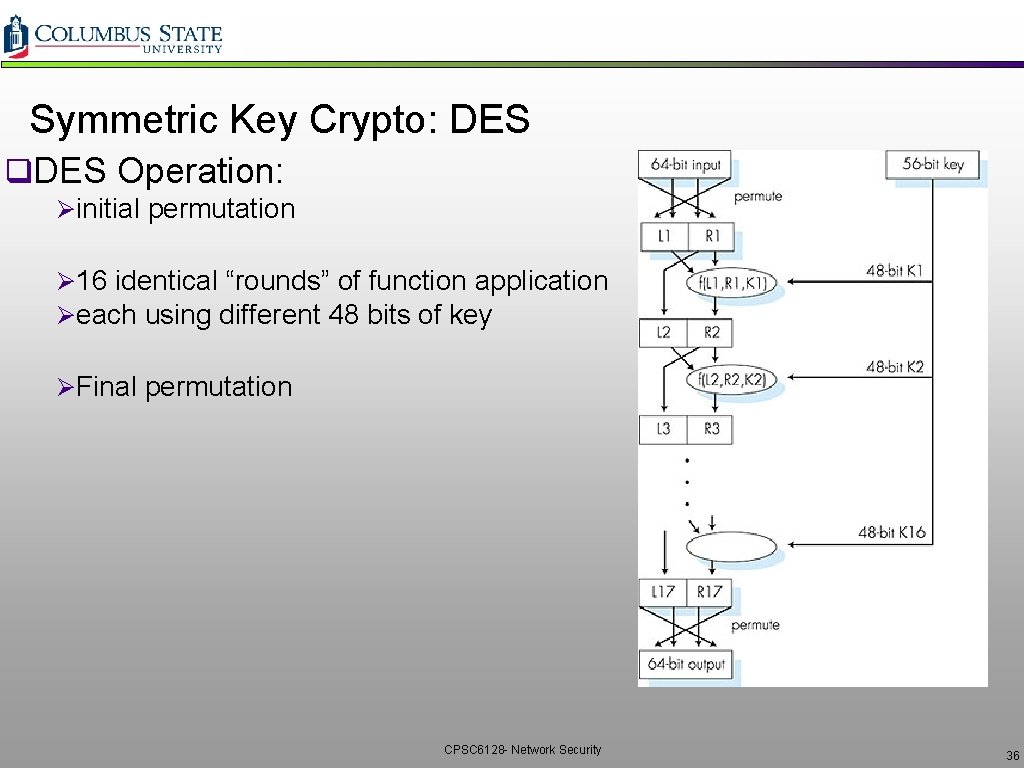
Symmetric Key Crypto: DES q. DES Operation: Øinitial permutation Ø 16 identical “rounds” of function application Øeach using different 48 bits of key ØFinal permutation CPSC 6128 - Network Security 36

Advanced Encryption Standard q. New (Nov. 2001) symmetric-key NIST standard q. Used to replace DES q. Processes data in 128 bit blocks q 128, 192, or 256 bit keys q. Brute force decryption (try each key) Øtakes 1 day on DES, but 149 trillion years for AES CPSC 6128 - Network Security 37

Public Key Cryptography CPSC 6128 - Network Security 38

Why Public Key Cryptography q Symmetric Key Cryptography v Requires Sender and Receiver know shared key v Q: How do we agree on the key in the first place? q. Public Key Cryptography vradically different approach [Diffie-Hellman 76, RSA 78] v. Sender and receiver do not share secret key Øpublic encryption key known to all Øprivate decryption key known only to receiver CPSC 6128 - Network Security 39

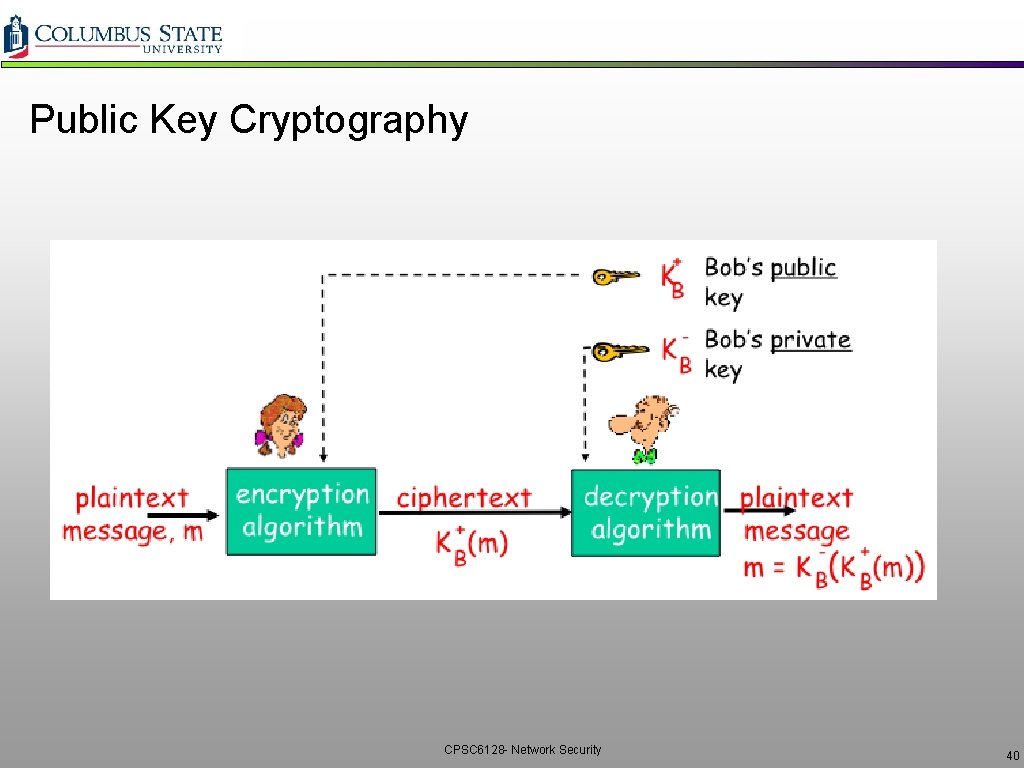
Public Key Cryptography CPSC 6128 - Network Security 40

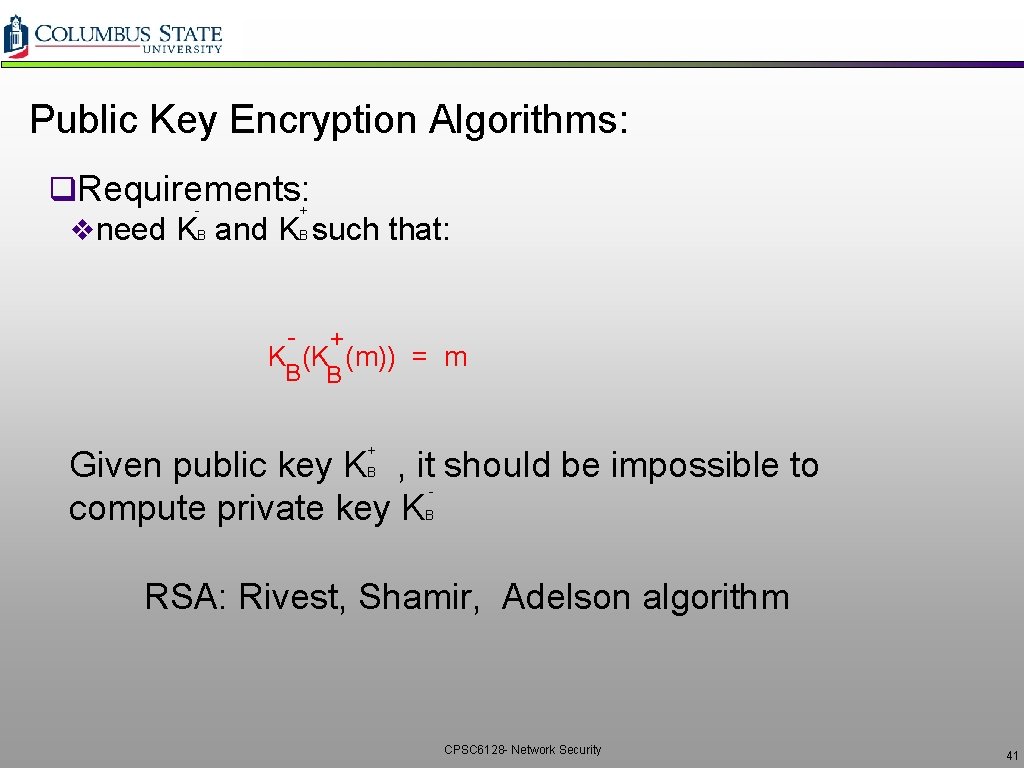
Public Key Encryption Algorithms: q. Requirements: + vneed KB and KB such that: - + K (K (m)) = m B B + Given public key K , it should be impossible to compute private key K B - B RSA: Rivest, Shamir, Adelson algorithm CPSC 6128 - Network Security 41

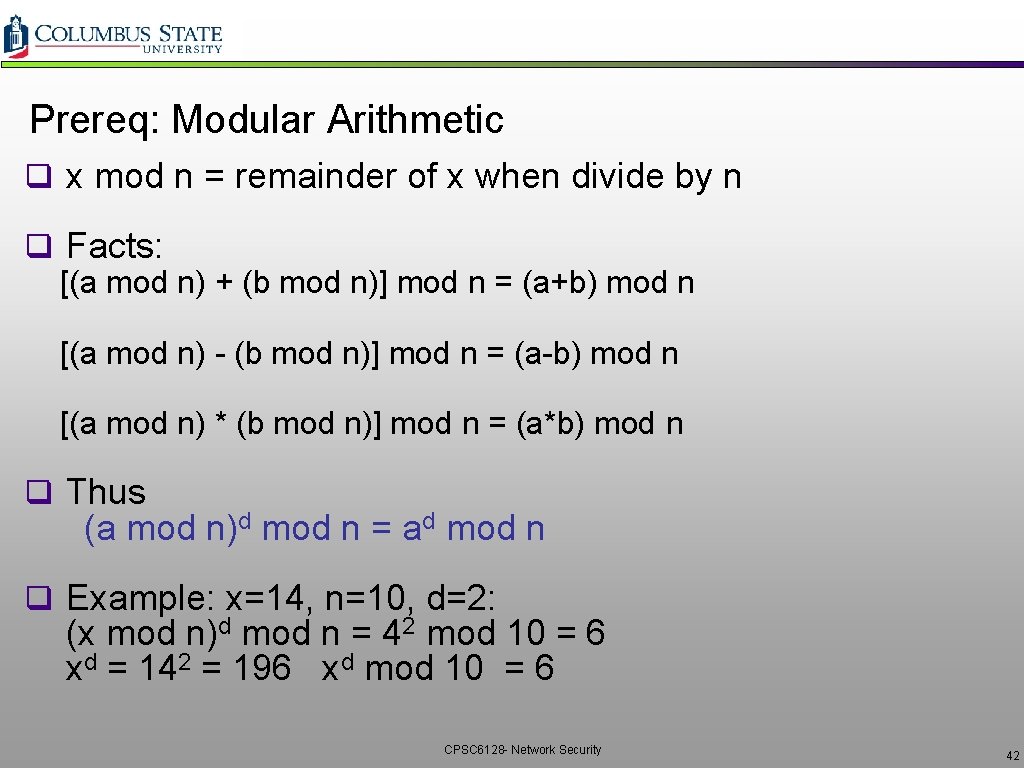
Prereq: Modular Arithmetic q x mod n = remainder of x when divide by n q Facts: [(a mod n) + (b mod n)] mod n = (a+b) mod n [(a mod n) - (b mod n)] mod n = (a-b) mod n [(a mod n) * (b mod n)] mod n = (a*b) mod n q Thus (a mod n)d mod n = ad mod n q Example: x=14, n=10, d=2: (x mod n)d mod n = 42 mod 10 = 6 xd = 142 = 196 xd mod 10 = 6 CPSC 6128 - Network Security 42

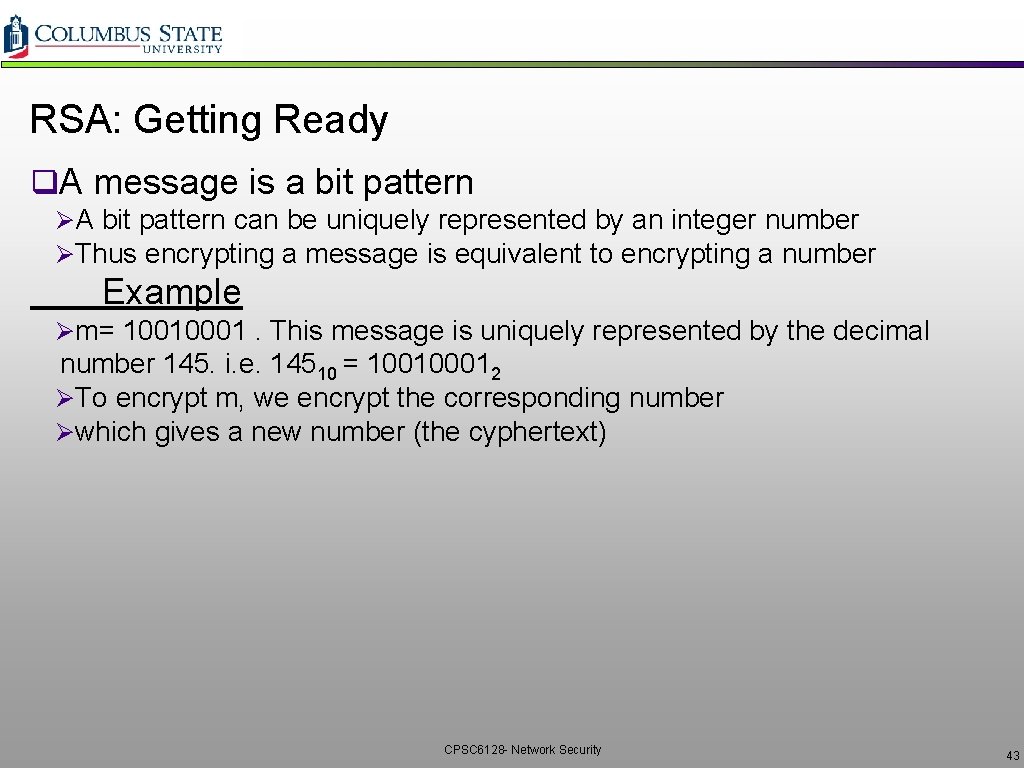
RSA: Getting Ready q. A message is a bit pattern ØA bit pattern can be uniquely represented by an integer number ØThus encrypting a message is equivalent to encrypting a number Example Øm= 10010001. This message is uniquely represented by the decimal number 145. i. e. 14510 = 100100012 ØTo encrypt m, we encrypt the corresponding number Øwhich gives a new number (the cyphertext) CPSC 6128 - Network Security 43

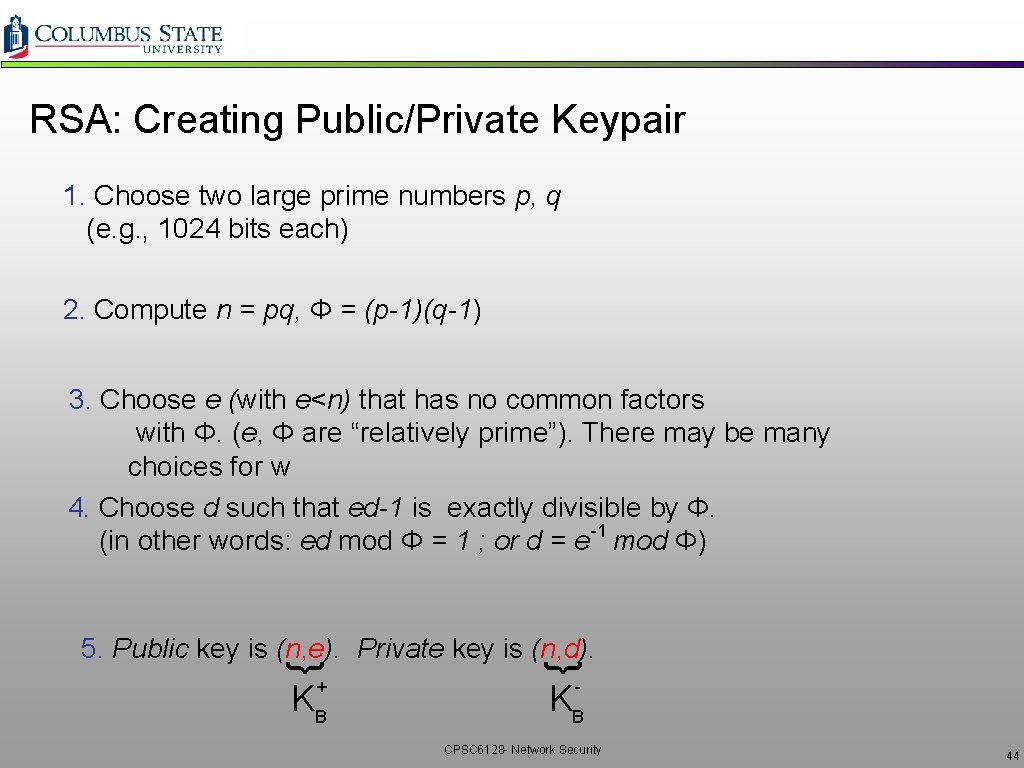
RSA: Creating Public/Private Keypair 1. Choose two large prime numbers p, q (e. g. , 1024 bits each) 2. Compute n = pq, Φ = (p-1)(q-1) 3. Choose e (with e<n) that has no common factors with Φ. (e, Φ are “relatively prime”). There may be many choices for w 4. Choose d such that ed-1 is exactly divisible by Φ. -1 (in other words: ed mod Φ = 1 ; or d = e mod Φ) { { 5. Public key is (n, e). Private key is (n, d). + - KB KB CPSC 6128 - Network Security 44

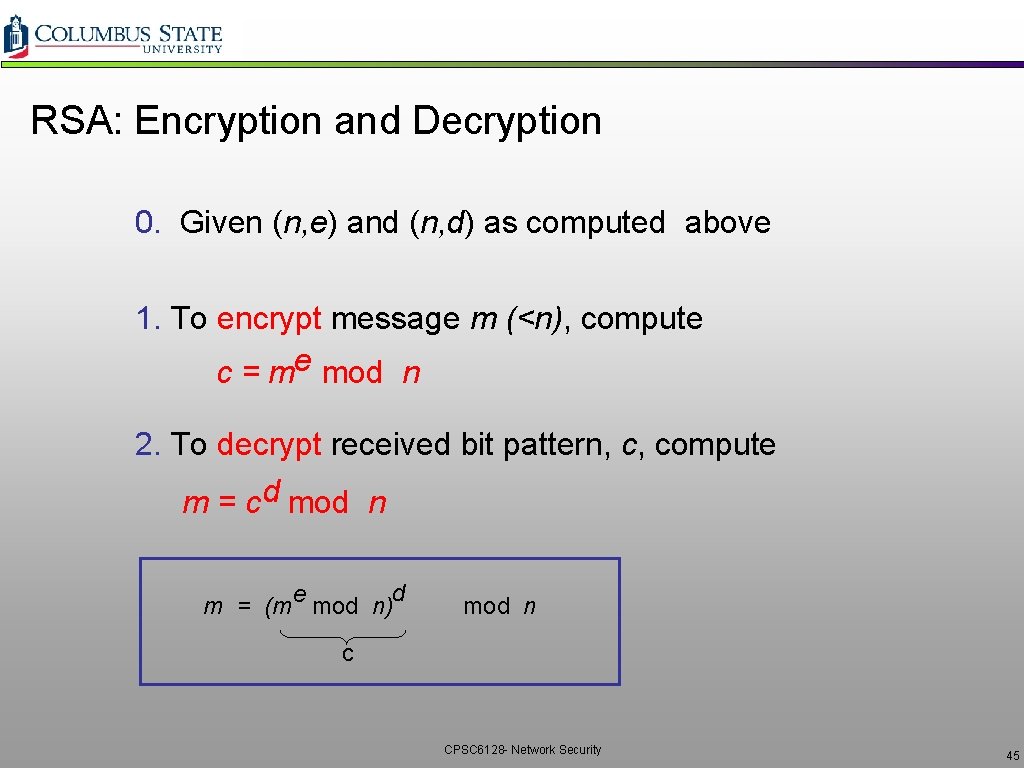
RSA: Encryption and Decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt message m (<n), compute e c = m mod n 2. To decrypt received bit pattern, c, compute d m = c mod n d e m = (m mod n) mod n c CPSC 6128 - Network Security 45

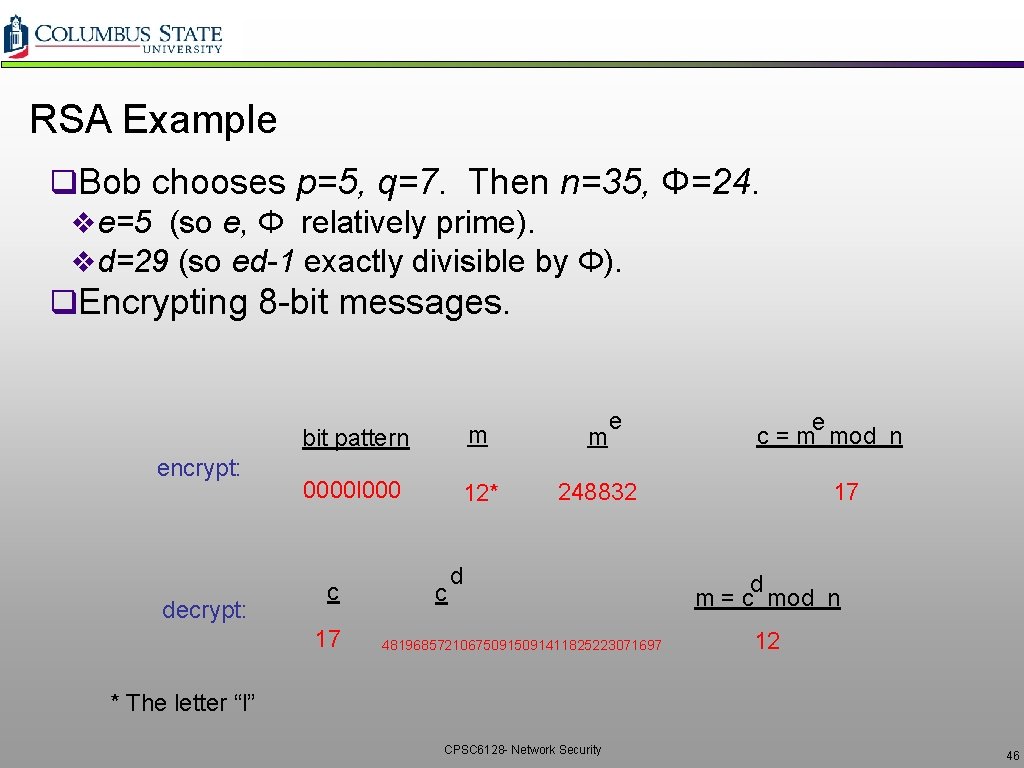
RSA Example q. Bob chooses p=5, q=7. Then n=35, Φ=24. ve=5 (so e, Φ relatively prime). vd=29 (so ed-1 exactly divisible by Φ). q. Encrypting 8 -bit messages. encrypt: decrypt: e bit pattern m m 0000 l 000 12* 248832 c 17 c d 48196857210675091411825223071697 e c = m mod n 17 d m = c mod n 12 * The letter “l” CPSC 6128 - Network Security 46

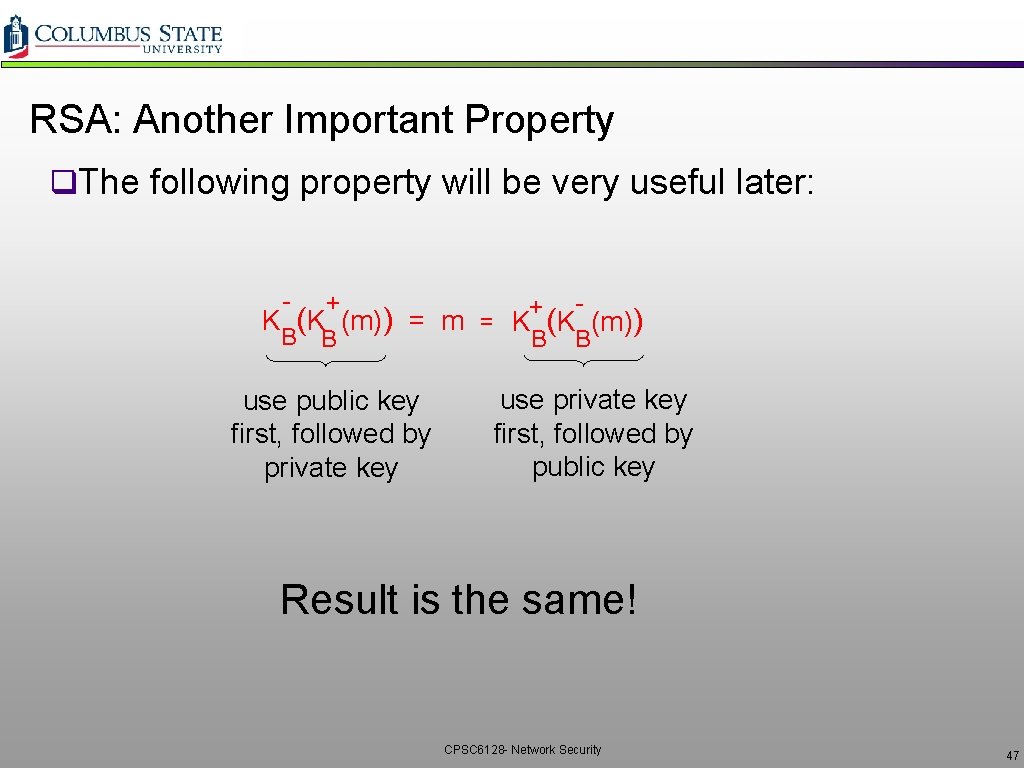
RSA: Another Important Property q. The following property will be very useful later: - + + K (K (m)) = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! CPSC 6128 - Network Security 47

Why Does RSA Work? q. Must show that cd mod n = m where c = me mod n q. Fact: for any x and y: xy mod n = x(y mod z) mod n Øwhere n= pq and z = (p-1)(q-1) q. Thus, cd mod n = (me mod n)d mod n = med mod n = m(ed mod z) mod n = m 1 mod n = m CPSC 6128 - Network Security 48

Why is RSA Secure? q. Suppose you know Bob’s public key (n, e) ØHow hard is it to determine d? ØEssentially need to find factors of n without knowing the two factors p and q q. Fact: factoring a big number is hard. ØRemember e is not unique!! Recent literature Generating RSA Keys q Have to find big primes p and q q Approach: make good guess then apply testing rules CPSC 6128 - Network Security 49

Session Keys KS q. Exponentiation is computationally intensive q. DES is at least 100 times faster than RSA q. Bob and Alice use RSA to exchange a symmetric key KS q. Once both have KS, they use symmetric key cryptography CPSC 6128 - Network Security 50

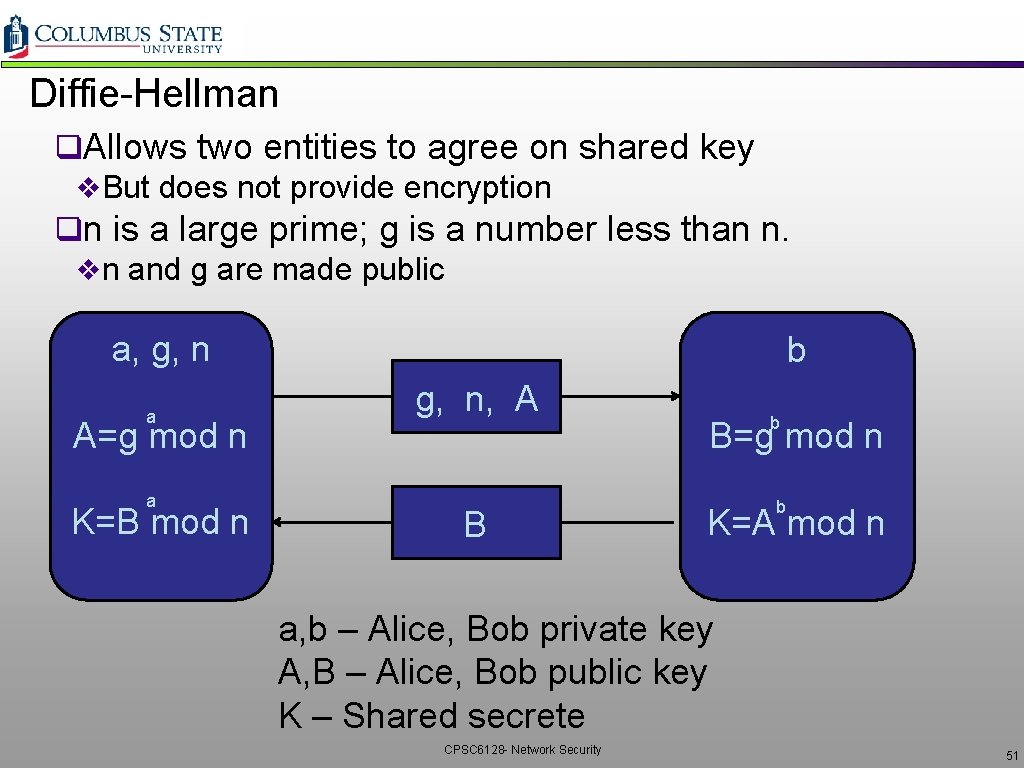
Diffie-Hellman q. Allows two entities to agree on shared key v. But does not provide encryption qn is a large prime; g is a number less than n. vn and g are made public a, g, n a A=g mod n a K=B mod n b g, n, A B b B=g mod n b K=A mod n a, b – Alice, Bob private key A, B – Alice, Bob public key K – Shared secrete CPSC 6128 - Network Security 51

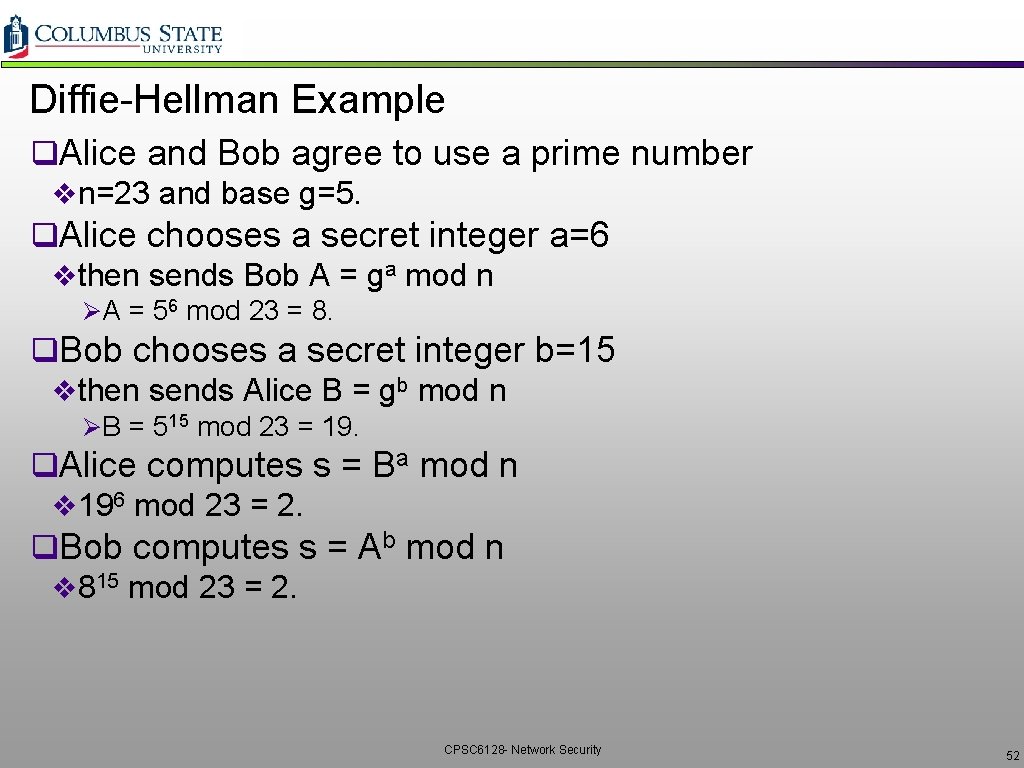
Diffie-Hellman Example q. Alice and Bob agree to use a prime number vn=23 and base g=5. q. Alice chooses a secret integer a=6 vthen sends Bob A = ga mod n ØA = 56 mod 23 = 8. q. Bob chooses a secret integer b=15 vthen sends Alice B = gb mod n ØB = 515 mod 23 = 19. q. Alice computes s = Ba mod n v 196 mod 23 = 2. q. Bob computes s = Ab mod n v 815 mod 23 = 2. CPSC 6128 - Network Security 52

Message Integrity and Digital Signatures CPSC 6128 - Network Security 53

Message Integrity q. Allows communicating parties to verify the received messages are authentic v. Content of message has not been altered v. Source of message is who/what you think it is v. Message has not been artificially delayed (playback attack) v. Sequence of messages is maintained q. Let’s first talk about message digests CPSC 6128 - Network Security 54

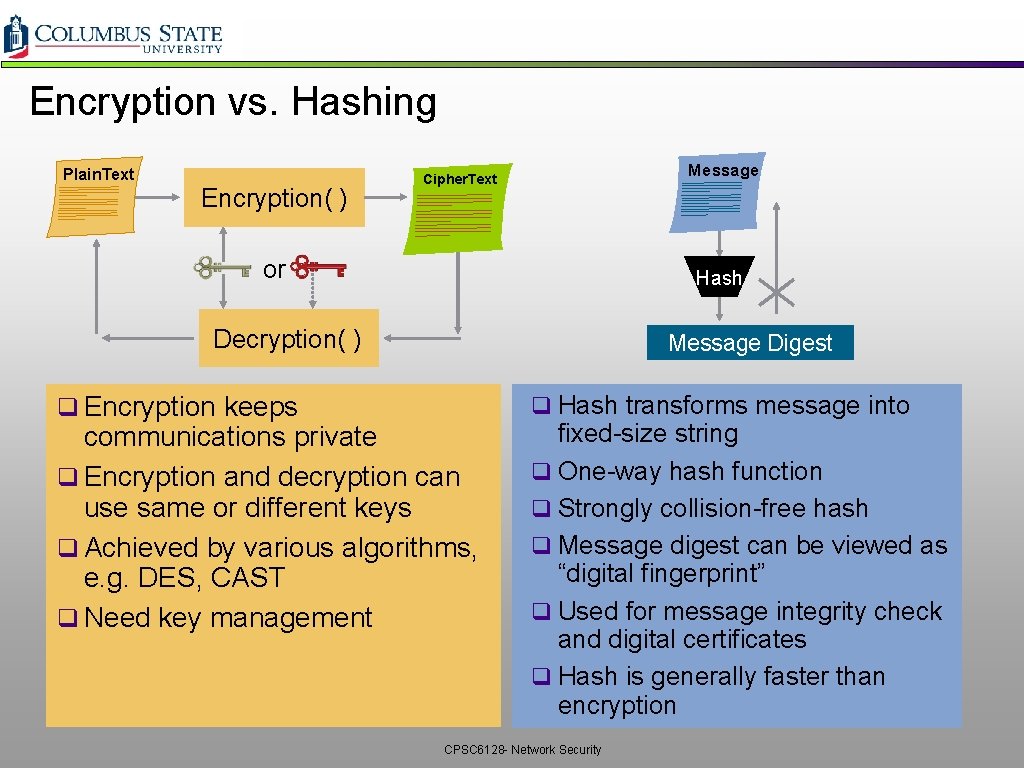
Encryption vs. Hashing Plain. Text Encryption( ) Message Cipher. Text or Hash Decryption( ) q Encryption keeps Message Digest q Hash transforms message into communications private q Encryption and decryption can use same or different keys q Achieved by various algorithms, e. g. DES, CAST q Need key management fixed-size string q One-way hash function q Strongly collision-free hash q Message digest can be viewed as “digital fingerprint” q Used for message integrity check and digital certificates q Hash is generally faster than encryption CPSC 6128 - Network Security

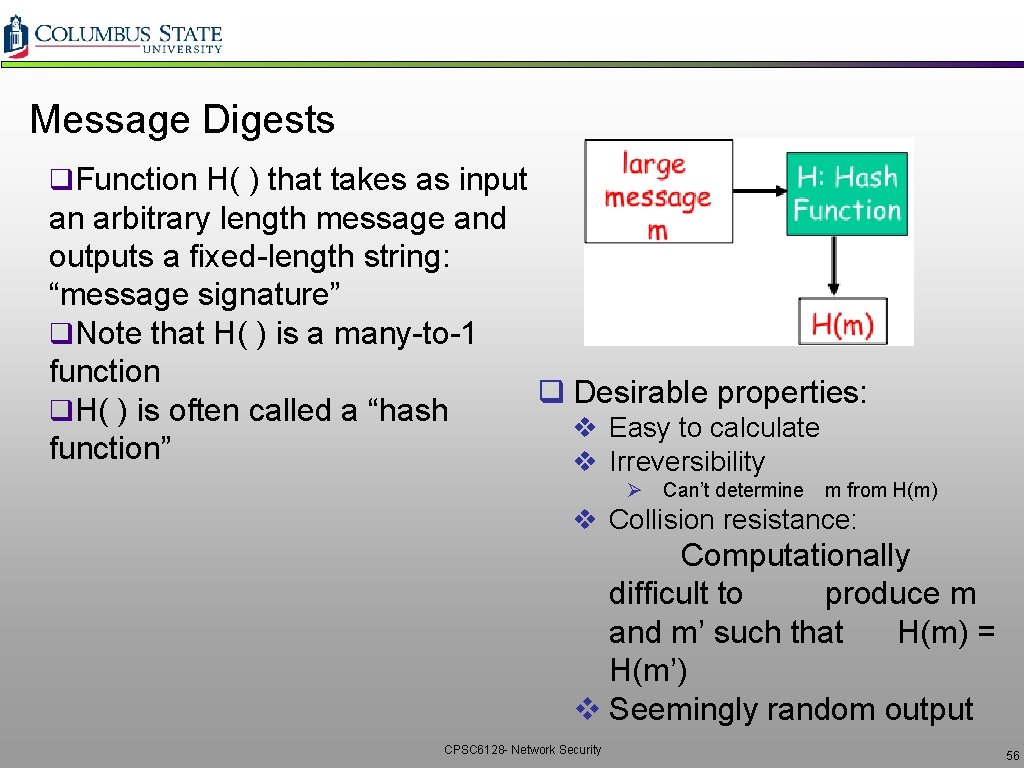
Message Digests q. Function H( ) that takes as input an arbitrary length message and outputs a fixed-length string: “message signature” q. Note that H( ) is a many-to-1 function q Desirable properties: q. H( ) is often called a “hash v Easy to calculate function” v Irreversibility Ø Can’t determine m from H(m) v Collision resistance: Computationally difficult to produce m and m’ such that H(m) = H(m’) v Seemingly random output CPSC 6128 - Network Security 56

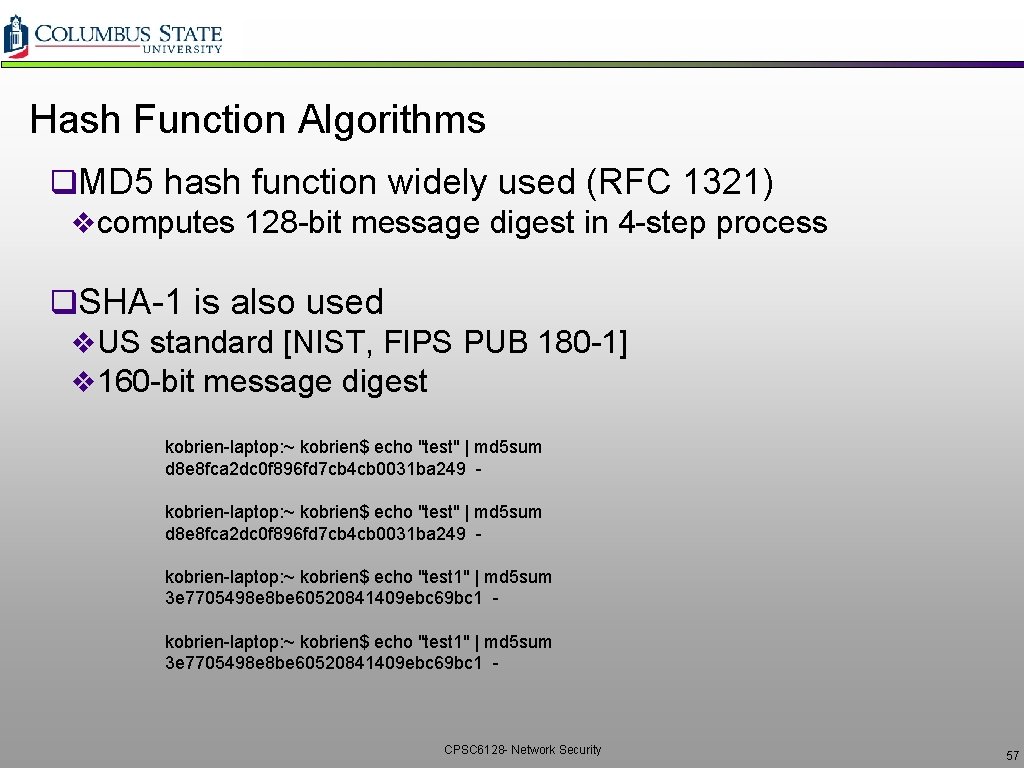
Hash Function Algorithms q. MD 5 hash function widely used (RFC 1321) vcomputes 128 -bit message digest in 4 -step process q. SHA-1 is also used v. US standard [NIST, FIPS PUB 180 -1] v 160 -bit message digest kobrien-laptop: ~ kobrien$ echo "test" | md 5 sum d 8 e 8 fca 2 dc 0 f 896 fd 7 cb 4 cb 0031 ba 249 kobrien-laptop: ~ kobrien$ echo "test 1" | md 5 sum 3 e 7705498 e 8 be 60520841409 ebc 69 bc 1 - CPSC 6128 - Network Security 57

Commonly Used Hash Functions (MD 5 and SHA) q Both MD 5 and SHA are derived based on MD 4 Ø MD 5 provides 128 -bit output Ø SHA provide 160 -bit output (only first 96 bits used in IPSec) q Both of MD 5 and SHA are considered Ø one-way strongly collision-free hash functions q SHA is computationally slower than MD 5, but more secure q. MD 5, SHA 1 not collision resistant ØRelevance to non-repudiation, commitment CPSC 6128 - Network Security

So What Does This Mean? q. SHA 1 is still much safer than MD 5 v. Best known attack has effort > 2^64 q. HMAC SHA 1 (keyed SHA 1) vbelieved to be unaffected by current attacks q. Industry making a move towards SHA 256 vand other secure crypto methods q. Actual transition will take place within standard groups first v. IETF and NIST among others addressing this issue CPSC 6128 - Network Security

Birthday Attack q. If 23 people are in the room, what is the chance that they all have different birthdays? 365 364 363 362 361 360 343 x x x. . . 365 365 365 = 49% q. So there is a 51% chance that two of them have the same birthday CPSC 6128 - Network Security 60

Birthday Attack (Cont) q. If there are N possible hash values, v. You’ll find collisions when you have calculated 1. 2 x sqrt(N) values q. SHA-1 uses a 160 -bit key v. Theoretically, it would require 280 computations to break v. SHA-1 has already been broken, because of other weaknesses CPSC 6128 - Network Security 61

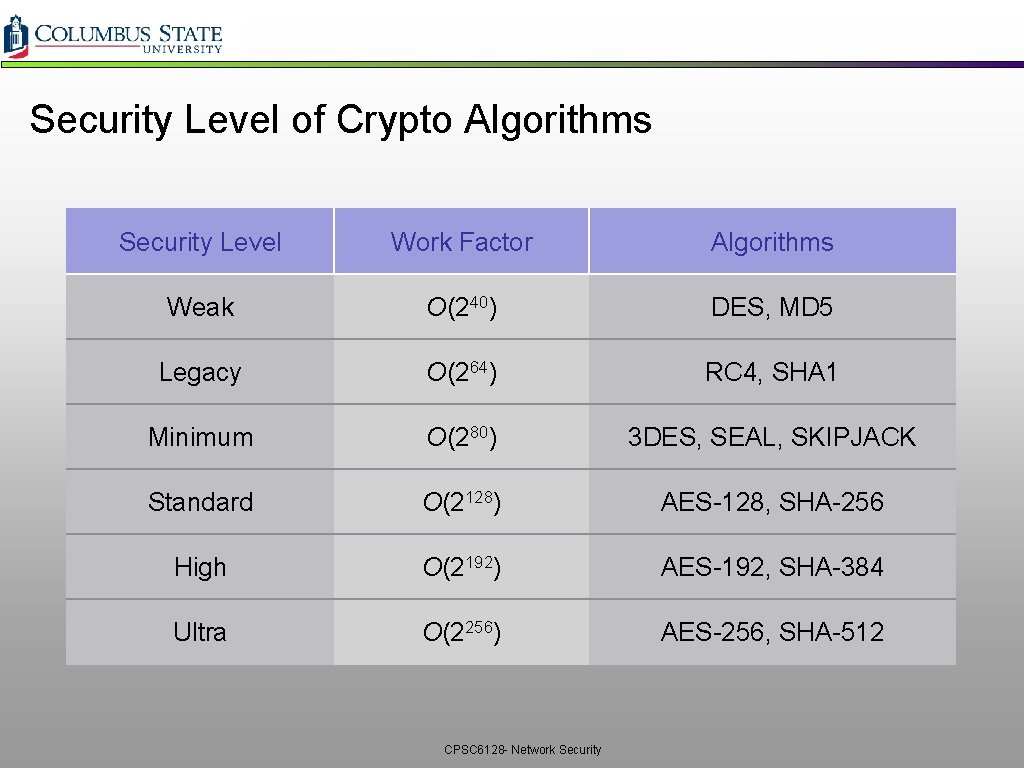
Security Level of Crypto Algorithms Security Level Work Factor Algorithms Weak O(240) DES, MD 5 Legacy O(264) RC 4, SHA 1 Minimum O(280) 3 DES, SEAL, SKIPJACK Standard O(2128) AES-128, SHA-256 High O(2192) AES-192, SHA-384 Ultra O(2256) AES-256, SHA-512 CPSC 6128 - Network Security

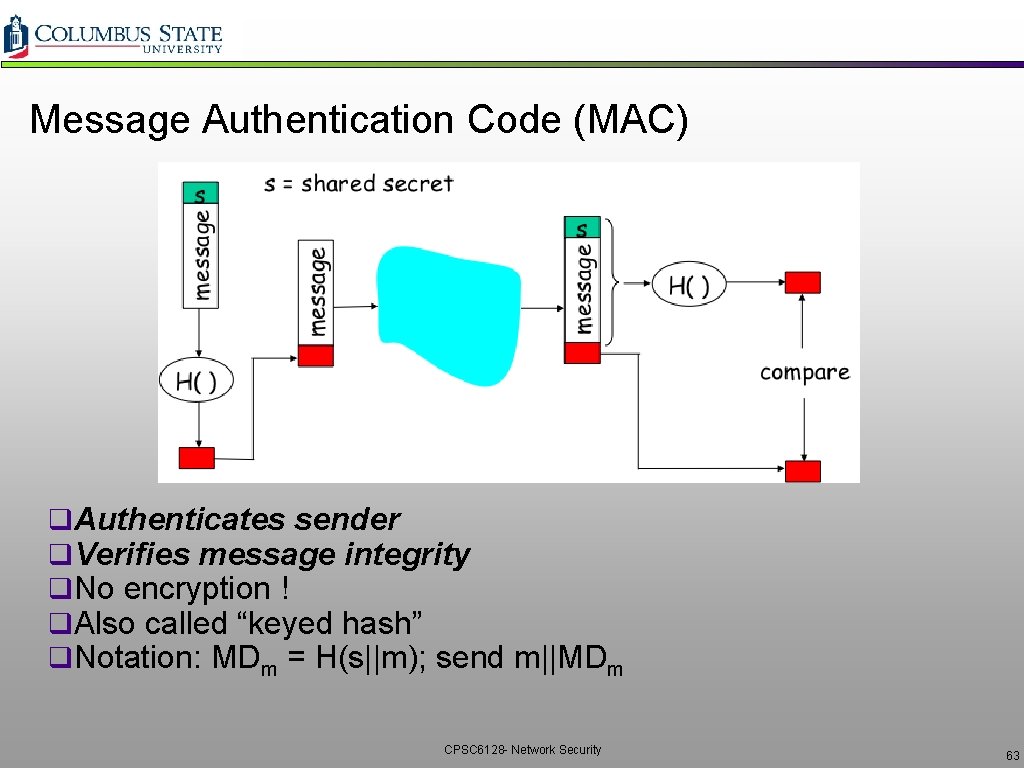
Message Authentication Code (MAC) q. Authenticates sender q. Verifies message integrity q. No encryption ! q. Also called “keyed hash” q. Notation: MDm = H(s||m); send m||MDm CPSC 6128 - Network Security 63

HMAC q Popular MAC standard q Addresses some subtle security flaws 1. 2. 3. 4. Concatenates secret to front of message Hashes concatenated message Concatenates the secret to front of digest Hashes the combination again CPSC 6128 - Network Security 64

Example: OSPF q. Recall that OSPF is an intra-AS routing protocol q. Each router creates map of entire AS (or area) and Øruns shortest path algorithm over map q. Router receives link-state advertisements (LSAs) from all other routers in AS q Attacks: v v Message insertion Message deletion Message modification How do we know if an OSPF message is authentic? CPSC 6128 - Network Security 65

OSPF Authentication q. Within an Autonomous ØSystem, routers send OSPF messages to each other q. OSPF provides authentication choices ØNo authentication ØShared password üinserted in clear in 64 -bit authentication field in OSPF packet ØCryptographic hash q Cryptographic hash with MD 5 Ø Ø 64 -bit authentication field includes 32 -bit sequence number MD 5 is run over a concatenation of the OSPF packet and shared secret key MD 5 hash then appended to OSPF packet encapsulated in IP datagram CPSC 6128 - Network Security 66

End Point Authentication q. Want to be sure of the originator of the message Ø end-point authentication q. Assuming Alice and Bob have a shared secret, but will MAC provide message authentication? v. We do know that Alice created the message v. But did she send it? CPSC 6128 - Network Security 67

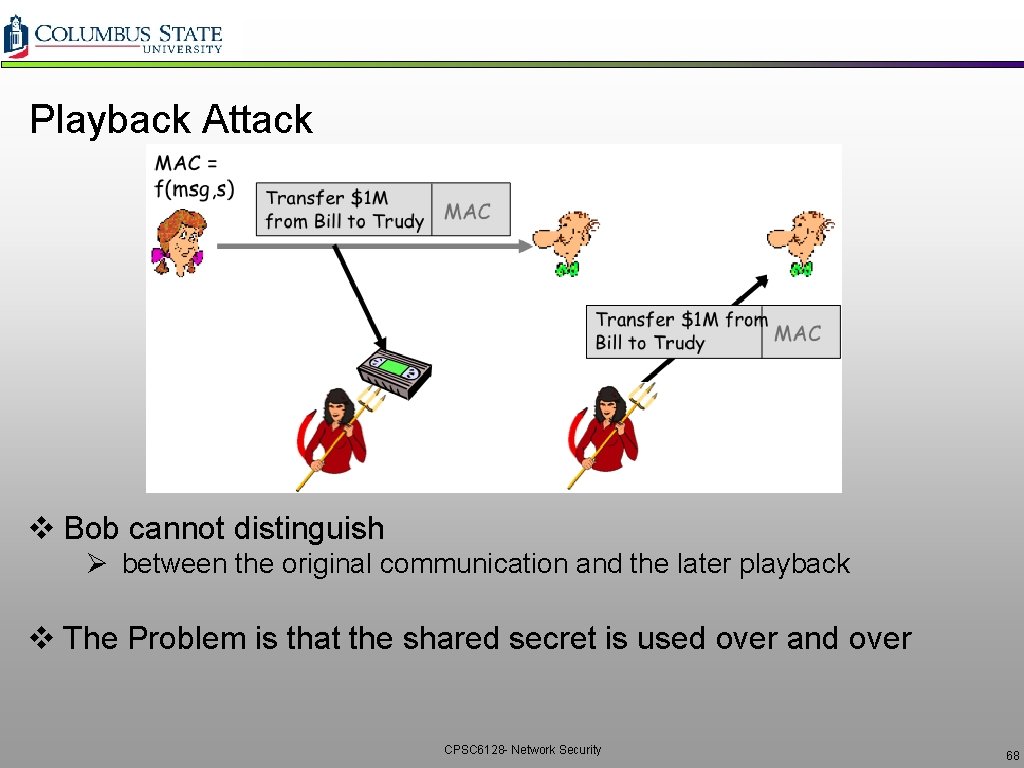
Playback Attack v Bob cannot distinguish Ø between the original communication and the later playback v The Problem is that the shared secret is used over and over CPSC 6128 - Network Security 68

Defending Against Playback Attack: Nonce 1) Alice sends the message, ”I am Alice, " to Bob 2) Bob chooses a nonce, R, and sends it to Alice 3) Alice encrypts the nonce using Alice and Bob's symmetric secret key, KA-B. , and sends the encrypted nonce, KA-B (R) back to Bob. A nonce is a number that a protocol will only ever use once-in-a -lifetime CPSC 6128 - Network Security 69

Nonce (con’t) q. It is the fact that Alice knows KA-B and uses it to encrypt a value that lets Bob know that the message he receives was generated by Alice. q. The nonce is used to insure that Alice is "live. " v. Bob decrypts the received message v. If the decrypted nonce equals the nonce he sent Alice Ø then Alice is authenticated. CPSC 6128 - Network Security 70

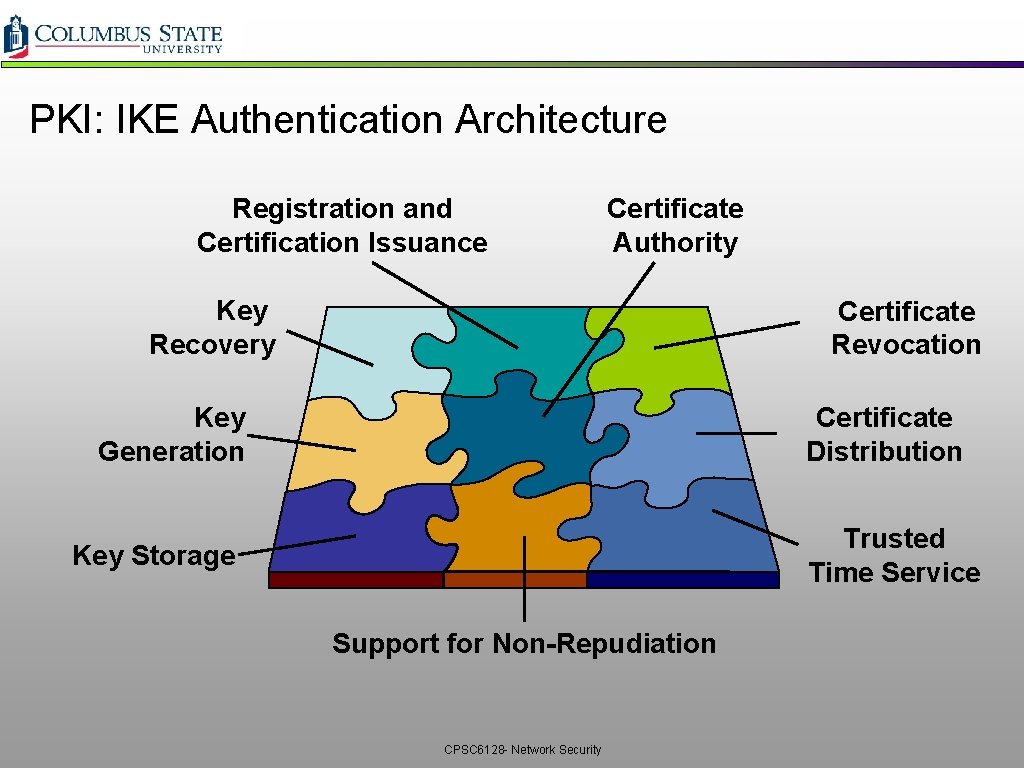
PKI: IKE Authentication Architecture Registration and Certification Issuance Certificate Authority Key Recovery Certificate Revocation Key Generation Certificate Distribution Trusted Time Service Key Storage Support for Non-Repudiation CPSC 6128 - Network Security

Digital Signatures Public Private q. Entity authentication q. Data origin authentication q. Integrity q. Non-repudiation CPSC 6128 - Network Security

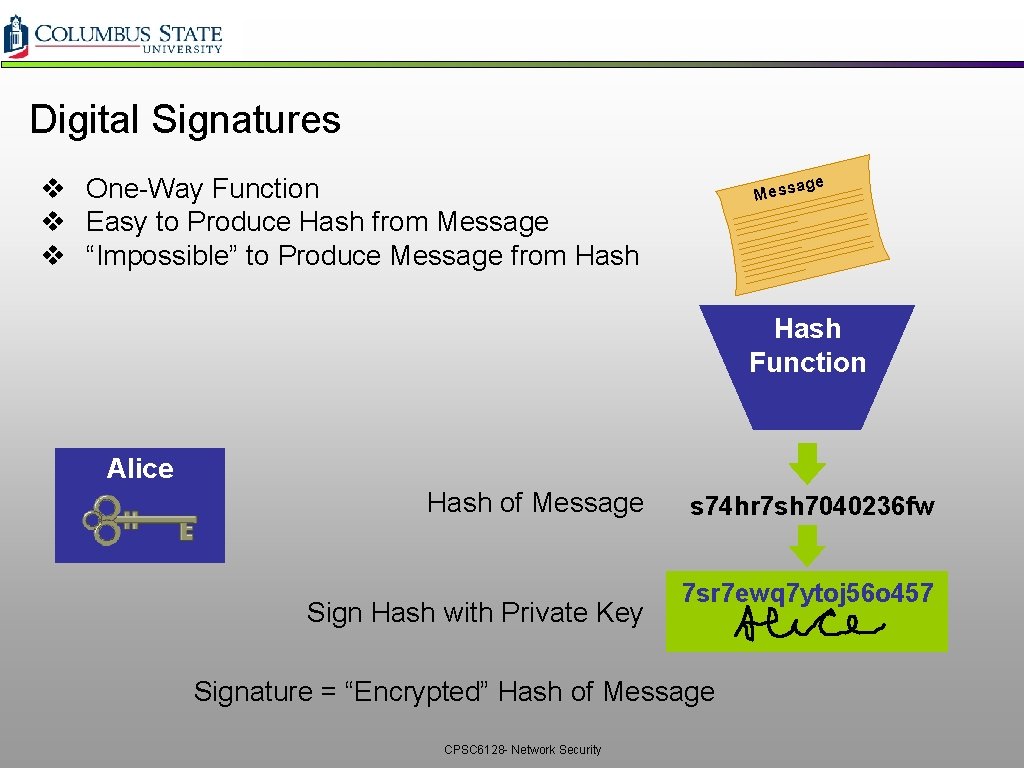
Digital Signatures v One-Way Function v Easy to Produce Hash from Message v “Impossible” to Produce Message from Hash e ag Mess Hash Function Alice Hash of Message Sign Hash with Private Key s 74 hr 7 sh 7040236 fw 7 sr 7 ewq 7 ytoj 56 o 457 Signature = “Encrypted” Hash of Message CPSC 6128 - Network Security

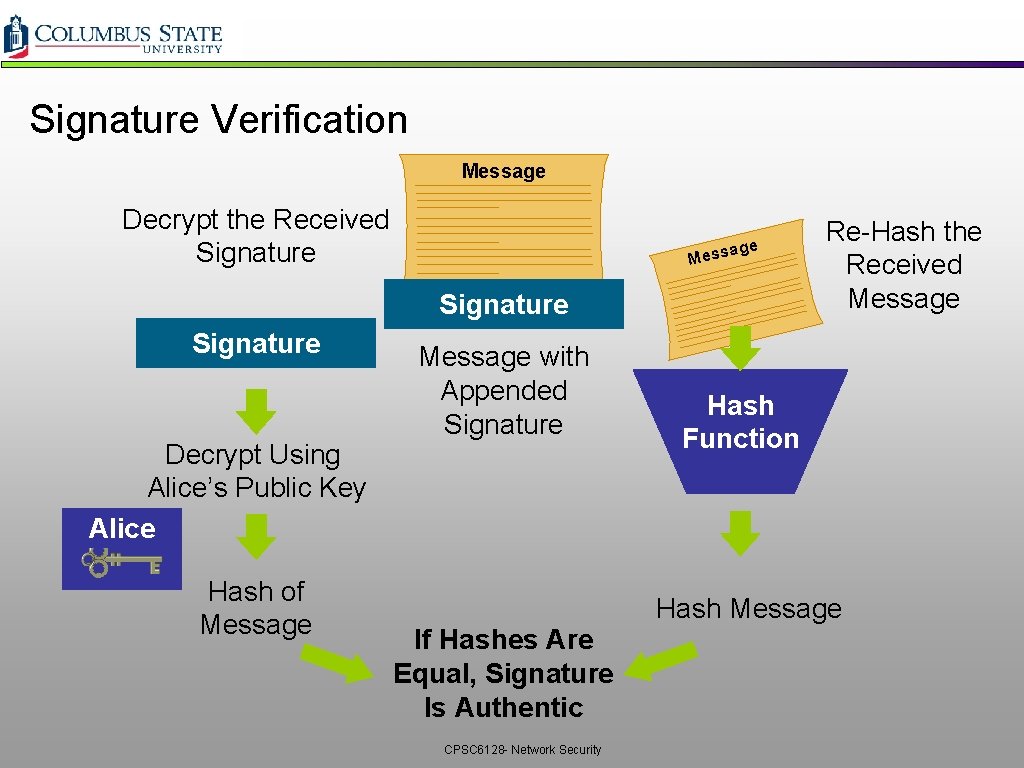
Signature Verification Message Decrypt the Received Signature e essag M Signature Decrypt Using Alice’s Public Key Alice Hash of Message with Appended Signature Re-Hash the Received Message Hash Function Hash Message If Hashes Are Equal, Signature Is Authentic CPSC 6128 - Network Security

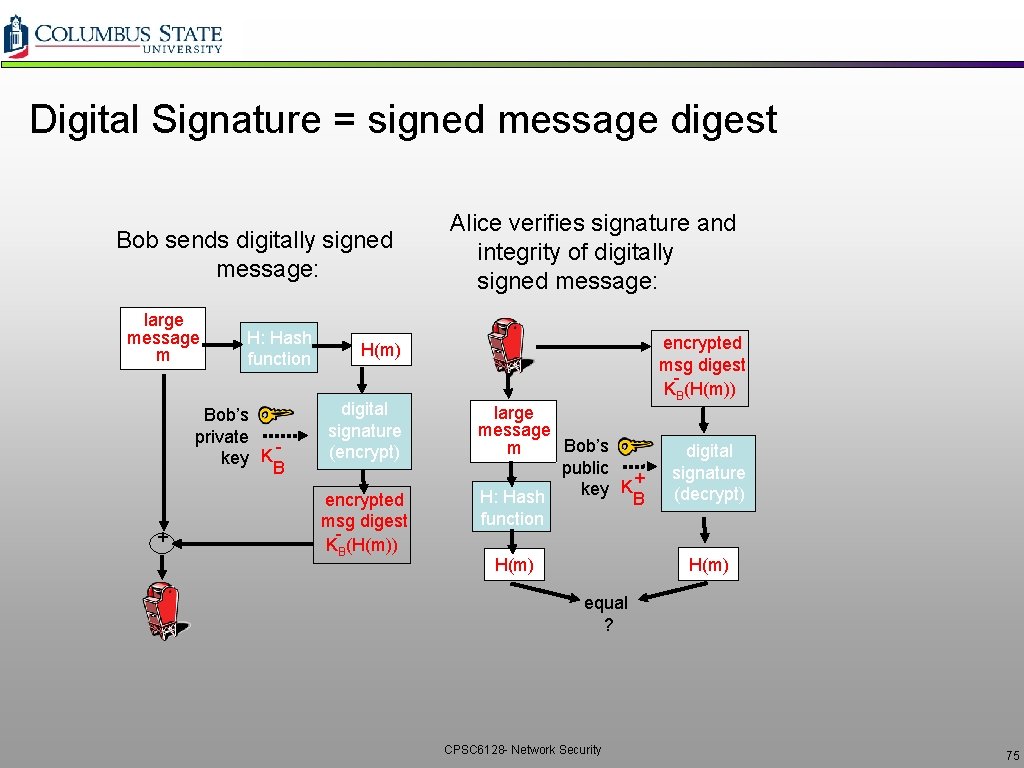
Digital Signature = signed message digest Bob sends digitally signed message: large message m H: Hash function Bob’s private key K B + Alice verifies signature and integrity of digitally signed message: encrypted msg digest KB(H(m)) H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message Bob’s m public K + key H: Hash B function digital signature (decrypt) H(m) equal ? CPSC 6128 - Network Security 75

Digital Signatures (more) Alice thus verifies that: m was signed by Bob (or some else used Bob’s private key) by applying Bob’s public key KB to KB(m) then checks KB(KB(m) ) = m. • Bob signed m. • No one else signed m. • Bob signed m and not m’. Non-repudiation: • Alice can take m, and signature KB(m) to court and prove that Bob signed m. CPSC 6128 - Network Security 76

Public Key Certifcation q. Motivation v. Trudy plays pizza prank on Bob ØTrudy creates e-mail order: Dear Pizza Store, Please deliver to me four pepperoni pizzas. Thank you, Bob ØTrudy signs order with her private key ØTrudy sends order to Pizza Store ØTrudy sends to Pizza Store her public key, but says it’s Bob’s public key. ØPizza Store verifies signature; then delivers four pizzas to Bob. ØBob doesn’t even like Pepperoni CPSC 6128 - Network Security 77

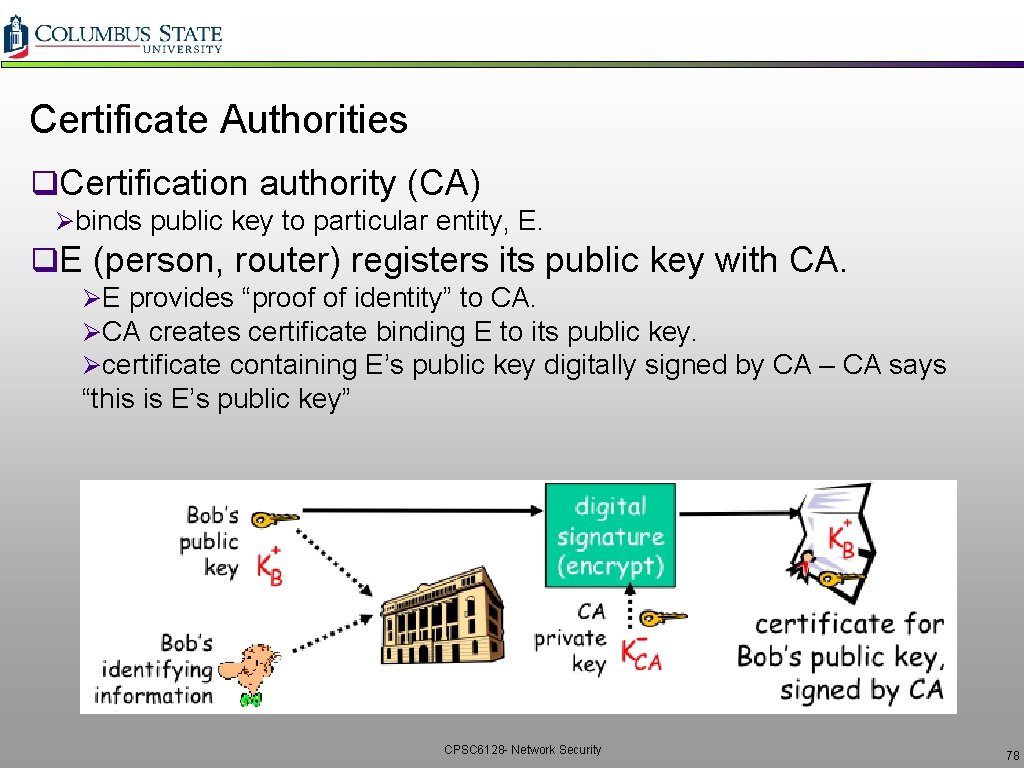
Certificate Authorities q. Certification authority (CA) Øbinds public key to particular entity, E. q. E (person, router) registers its public key with CA. ØE provides “proof of identity” to CA. ØCA creates certificate binding E to its public key. Øcertificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” CPSC 6128 - Network Security 78

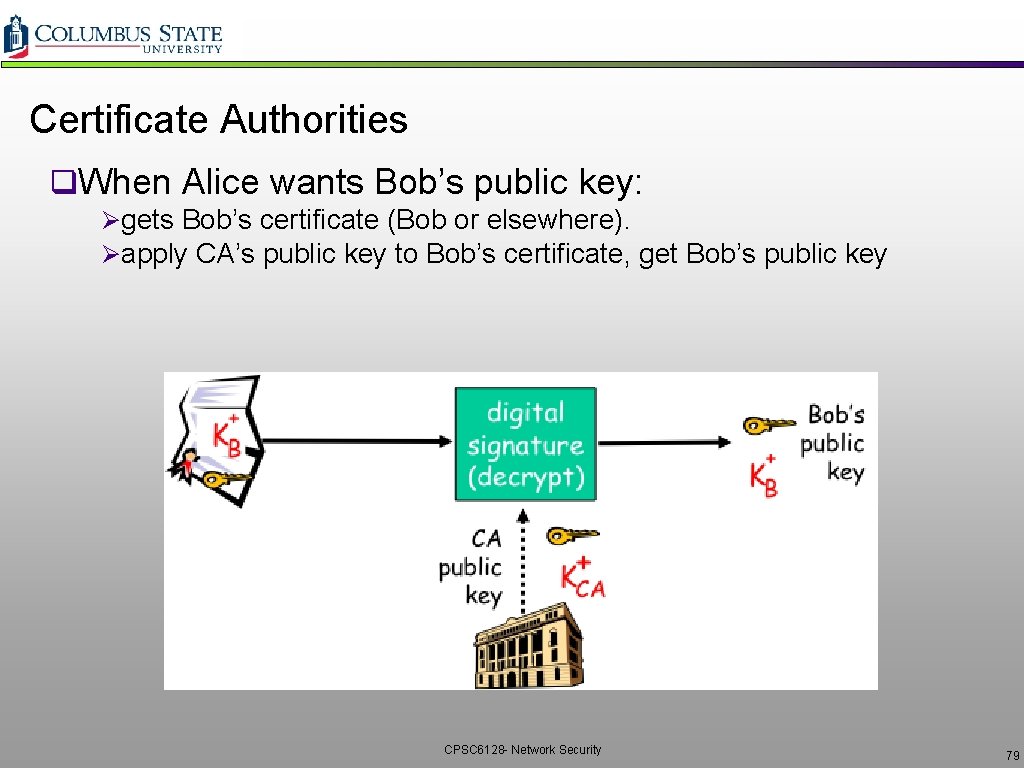
Certificate Authorities q. When Alice wants Bob’s public key: Øgets Bob’s certificate (Bob or elsewhere). Øapply CA’s public key to Bob’s certificate, get Bob’s public key CPSC 6128 - Network Security 79

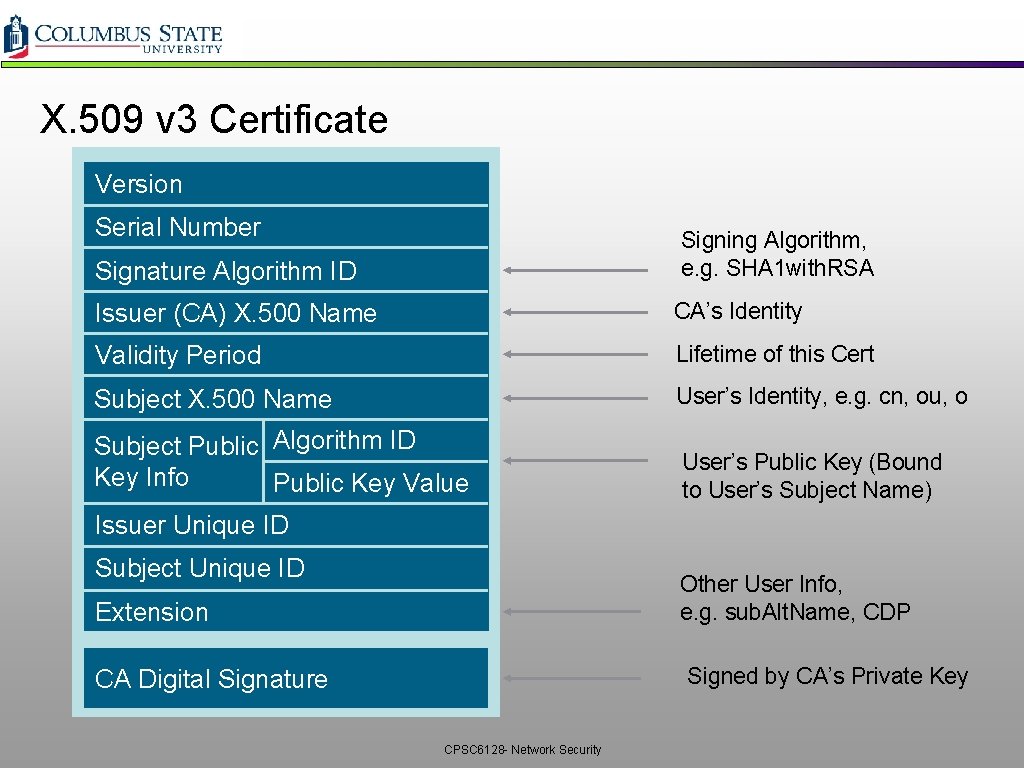
X. 509 v 3 Certificate Version Serial Number Signing Algorithm, e. g. SHA 1 with. RSA Signature Algorithm ID Issuer (CA) X. 500 Name CA’s Identity Validity Period Lifetime of this Cert Subject X. 500 Name User’s Identity, e. g. cn, ou, o Subject Public Algorithm ID Key Info Public Key Value User’s Public Key (Bound to User’s Subject Name) Issuer Unique ID Subject Unique ID Other User Info, e. g. sub. Alt. Name, CDP Extension Signed by CA’s Private Key CA Digital Signature CPSC 6128 - Network Security

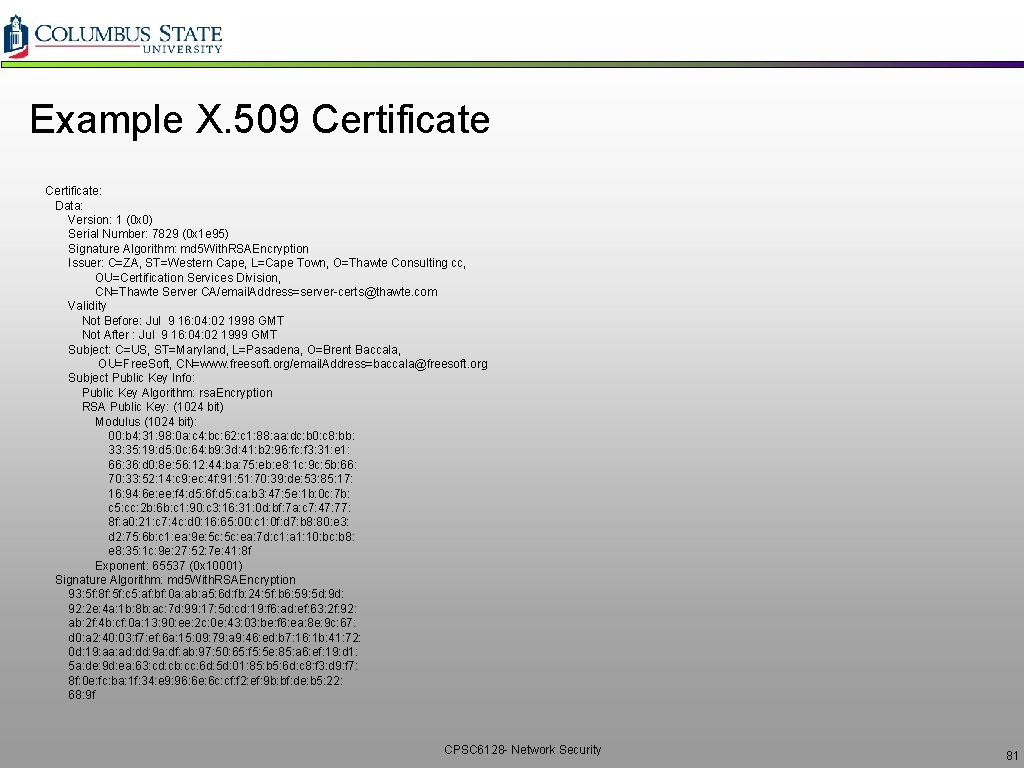
Example X. 509 Certificate: Data: Version: 1 (0 x 0) Serial Number: 7829 (0 x 1 e 95) Signature Algorithm: md 5 With. RSAEncryption Issuer: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting cc, OU=Certification Services Division, CN=Thawte Server CA/email. Address=server-certs@thawte. com Validity Not Before: Jul 9 16: 04: 02 1998 GMT Not After : Jul 9 16: 04: 02 1999 GMT Subject: C=US, ST=Maryland, L=Pasadena, O=Brent Baccala, OU=Free. Soft, CN=www. freesoft. org/email. Address=baccala@freesoft. org Subject Public Key Info: Public Key Algorithm: rsa. Encryption RSA Public Key: (1024 bit) Modulus (1024 bit): 00: b 4: 31: 98: 0 a: c 4: bc: 62: c 1: 88: aa: dc: b 0: c 8: bb: 33: 35: 19: d 5: 0 c: 64: b 9: 3 d: 41: b 2: 96: fc: f 3: 31: e 1: 66: 36: d 0: 8 e: 56: 12: 44: ba: 75: eb: e 8: 1 c: 9 c: 5 b: 66: 70: 33: 52: 14: c 9: ec: 4 f: 91: 51: 70: 39: de: 53: 85: 17: 16: 94: 6 e: ee: f 4: d 5: 6 f: d 5: ca: b 3: 47: 5 e: 1 b: 0 c: 7 b: c 5: cc: 2 b: 6 b: c 1: 90: c 3: 16: 31: 0 d: bf: 7 a: c 7: 47: 77: 8 f: a 0: 21: c 7: 4 c: d 0: 16: 65: 00: c 1: 0 f: d 7: b 8: 80: e 3: d 2: 75: 6 b: c 1: ea: 9 e: 5 c: ea: 7 d: c 1: a 1: 10: bc: b 8: e 8: 35: 1 c: 9 e: 27: 52: 7 e: 41: 8 f Exponent: 65537 (0 x 10001) Signature Algorithm: md 5 With. RSAEncryption 93: 5 f: 8 f: 5 f: c 5: af: bf: 0 a: ab: a 5: 6 d: fb: 24: 5 f: b 6: 59: 5 d: 9 d: 92: 2 e: 4 a: 1 b: 8 b: ac: 7 d: 99: 17: 5 d: cd: 19: f 6: ad: ef: 63: 2 f: 92: ab: 2 f: 4 b: cf: 0 a: 13: 90: ee: 2 c: 0 e: 43: 03: be: f 6: ea: 8 e: 9 c: 67: d 0: a 2: 40: 03: f 7: ef: 6 a: 15: 09: 79: a 9: 46: ed: b 7: 16: 1 b: 41: 72: 0 d: 19: aa: ad: dd: 9 a: df: ab: 97: 50: 65: f 5: 5 e: 85: a 6: ef: 19: d 1: 5 a: de: 9 d: ea: 63: cd: cb: cc: 6 d: 5 d: 01: 85: b 5: 6 d: c 8: f 3: d 9: f 7: 8 f: 0 e: fc: ba: 1 f: 34: e 9: 96: 6 e: 6 c: cf: f 2: ef: 9 b: bf: de: b 5: 22: 68: 9 f CPSC 6128 - Network Security 81